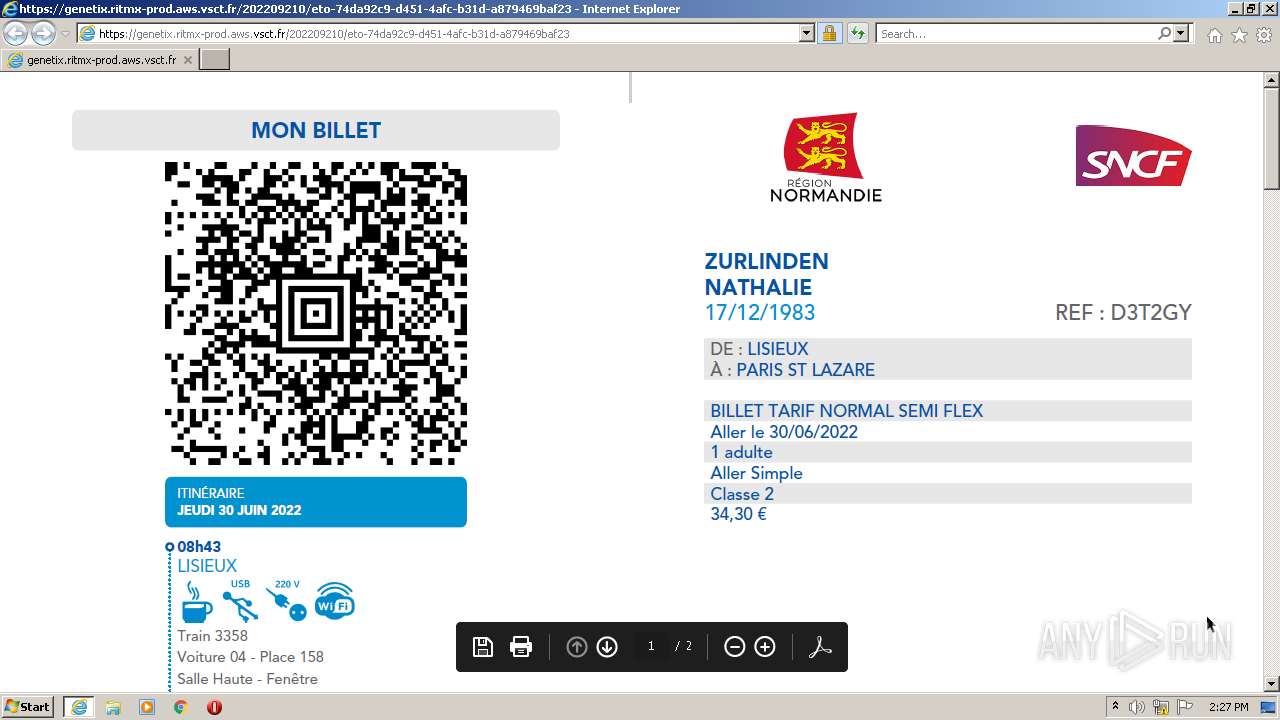
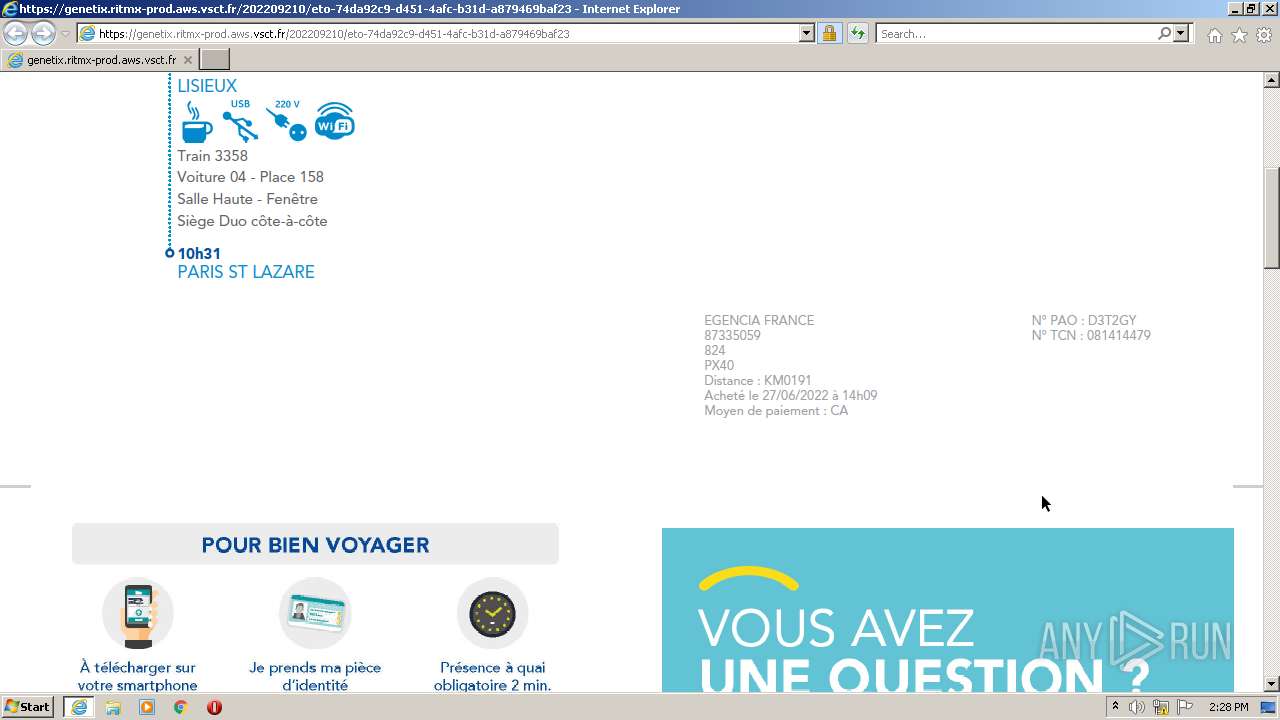
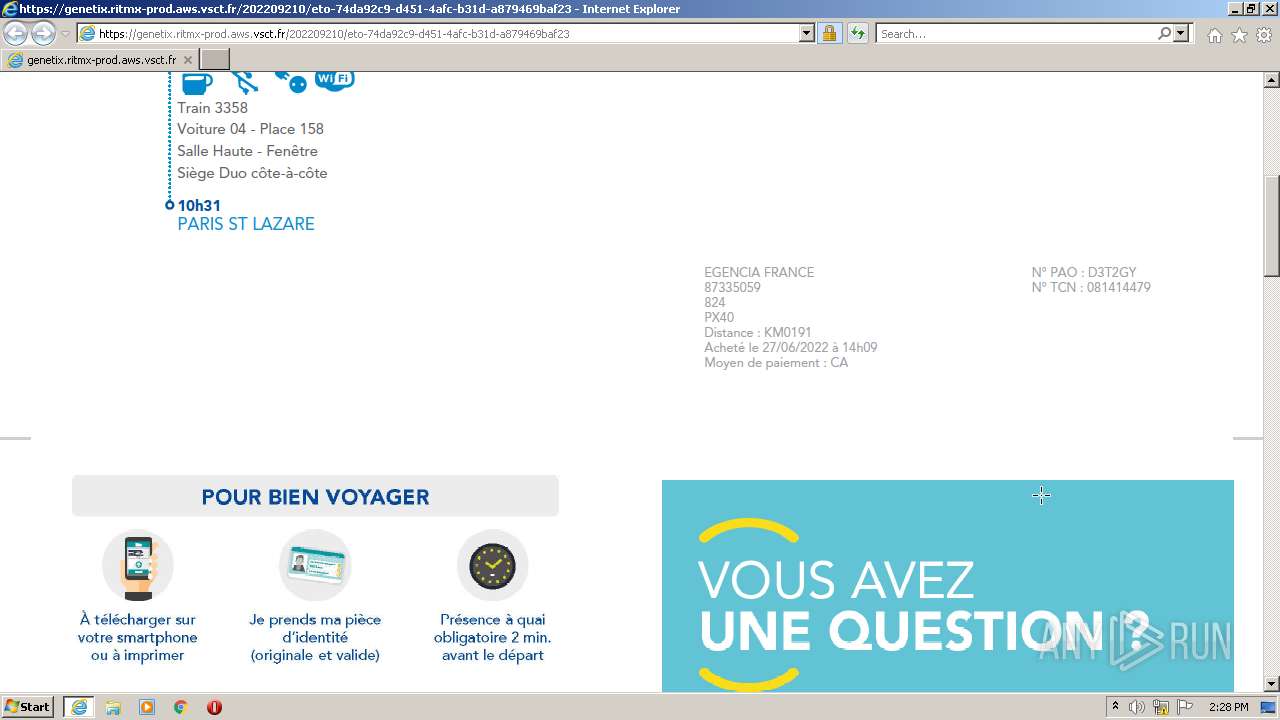
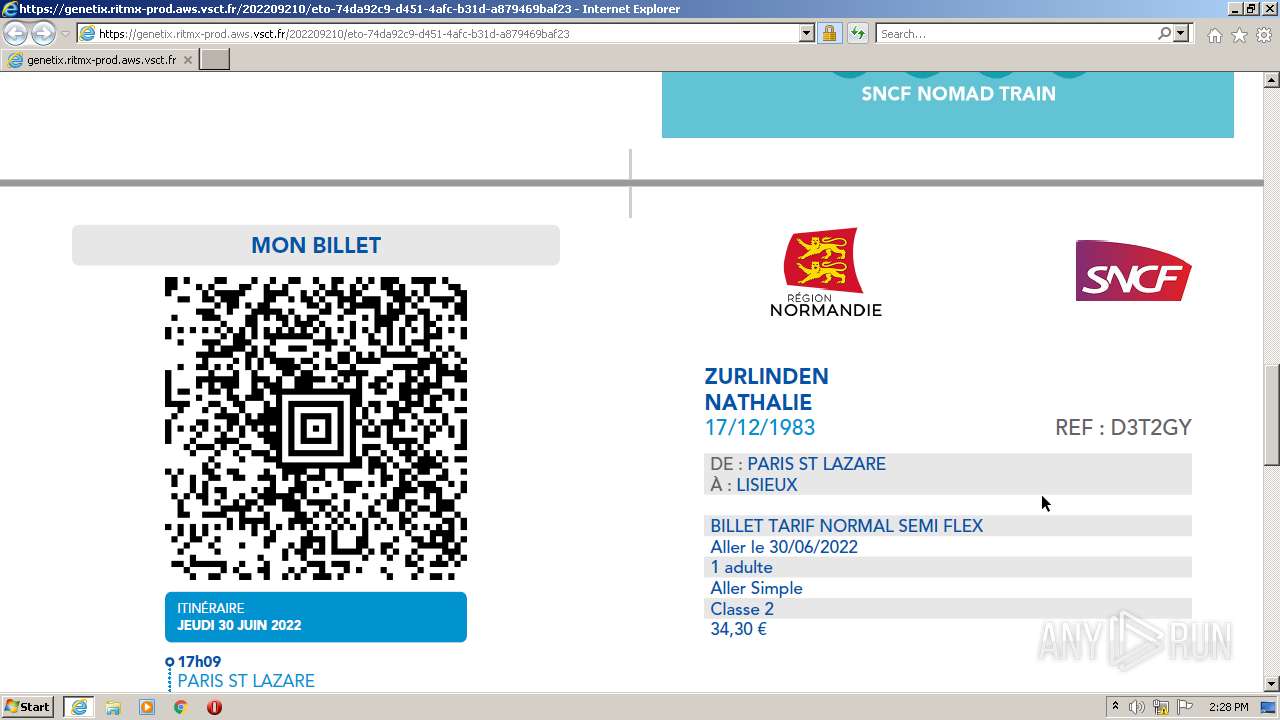
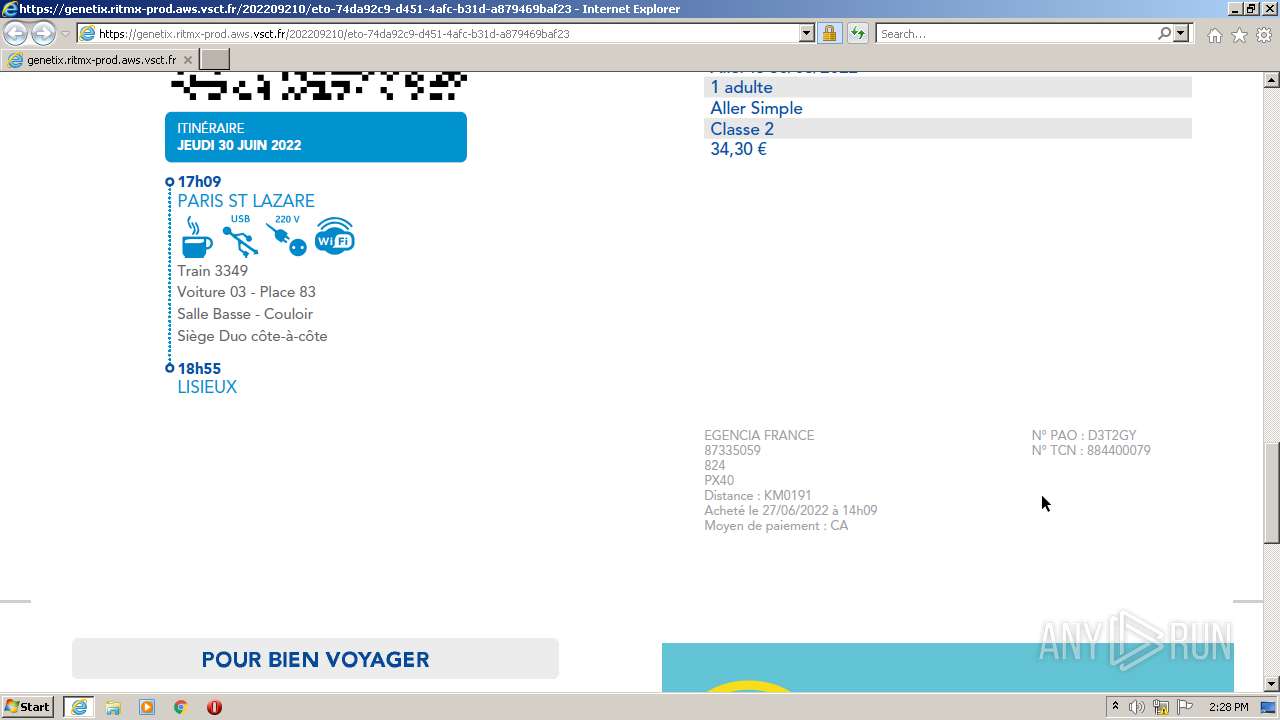
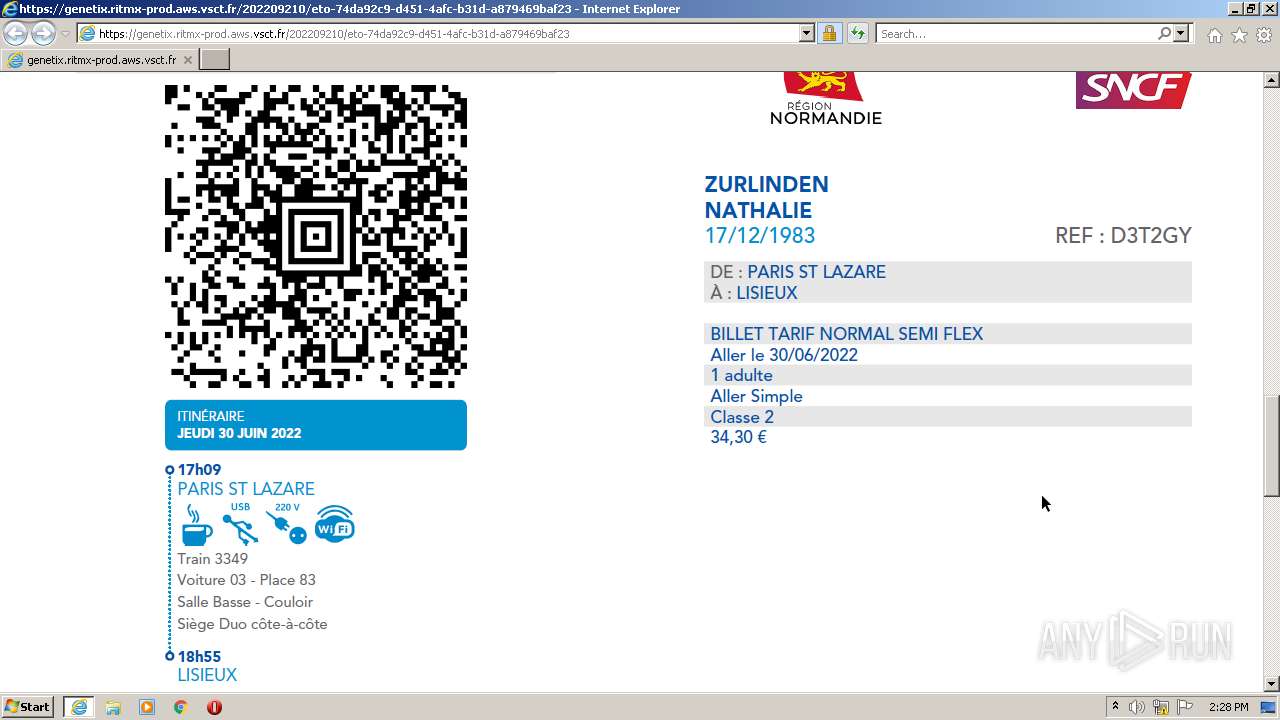
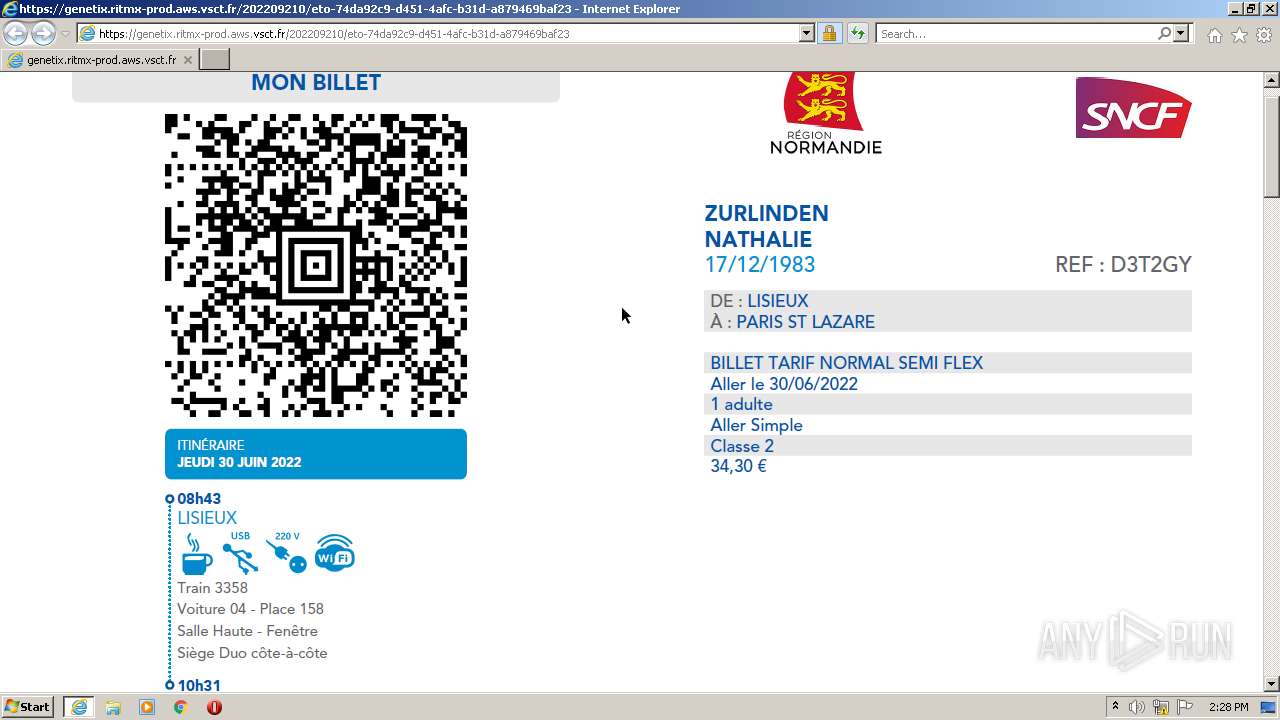
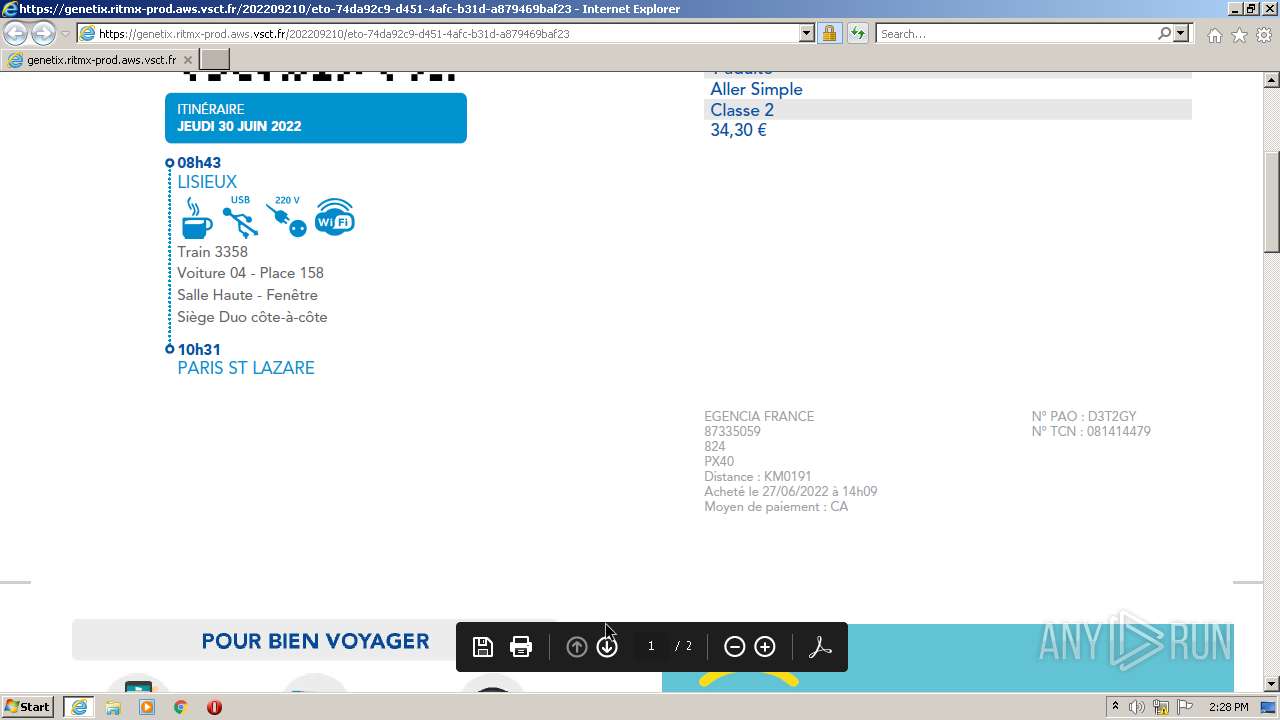
| URL: | https://genetix.ritmx-prod.aws.vsct.fr/202209210/eto-74da92c9-d451-4afc-b31d-a879469baf23 |
| Full analysis: | https://app.any.run/tasks/febecb5f-ddc8-41d0-9b5e-80ea659f012b |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 13:27:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B8AC0F24FD10FEA115360AD532929FAB |
| SHA1: | 0837A034454D076BA7820603260E7E312FF57C32 |
| SHA256: | 0D5ACFF65313658C043768FFD976F4663E41C2A970B0BBAA148869B6F852C2B2 |
| SSDEEP: | 3:N8hRLdnLEdDXM1VmLbEdRQUs8Wlrc1cMW:2jhLqDXMfmLbEdRQU9Wlrc0 |
MALICIOUS
Drops executable file immediately after starts
- RdrCEF.exe (PID: 2804)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2980)
Drops a file with a compile date too recent
- RdrCEF.exe (PID: 2804)
Reads the computer name
- AdobeARM.exe (PID: 2732)
Checks supported languages
- AdobeARM.exe (PID: 2732)
- Reader_sl.exe (PID: 188)
Creates files in the program directory
- AdobeARM.exe (PID: 2732)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 2732)
INFO
Reads the computer name
- iexplore.exe (PID: 1416)
- iexplore.exe (PID: 2980)
- RdrCEF.exe (PID: 2804)
- AcroRd32.exe (PID: 3296)
- AcroRd32.exe (PID: 3576)
Checks supported languages
- iexplore.exe (PID: 1416)
- iexplore.exe (PID: 2980)
- AcroRd32.exe (PID: 3296)
- AcroRd32.exe (PID: 3576)
- RdrCEF.exe (PID: 2804)
- RdrCEF.exe (PID: 3236)
- RdrCEF.exe (PID: 2348)
- RdrCEF.exe (PID: 3348)
- RdrCEF.exe (PID: 2008)
- RdrCEF.exe (PID: 3320)
- RdrCEF.exe (PID: 340)
Application launched itself
- iexplore.exe (PID: 1416)
- RdrCEF.exe (PID: 2804)
- AcroRd32.exe (PID: 3576)
Checks Windows Trust Settings
- iexplore.exe (PID: 2980)
- AcroRd32.exe (PID: 3576)
- AdobeARM.exe (PID: 2732)
- iexplore.exe (PID: 1416)
Reads settings of System Certificates
- iexplore.exe (PID: 1416)
- RdrCEF.exe (PID: 2804)
- AcroRd32.exe (PID: 3576)
- AdobeARM.exe (PID: 2732)
- iexplore.exe (PID: 2980)
Searches for installed software
- AcroRd32.exe (PID: 3576)
- AcroRd32.exe (PID: 3296)
Reads CPU info
- AcroRd32.exe (PID: 3296)
Reads internet explorer settings
- iexplore.exe (PID: 2980)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2980)
Reads the hosts file
- RdrCEF.exe (PID: 2804)
Creates files in the user directory
- iexplore.exe (PID: 1416)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1416)
Changes settings of System certificates
- iexplore.exe (PID: 1416)
Changes internet zones settings
- iexplore.exe (PID: 1416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
14
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 20.12.20041.394260 Modules
| |||||||||||||||
| 268 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /o /eo /l /b /id 2980 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | iexplore.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 340 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1188,5840886565637737298,12822449951000136209,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15481482360414477024 --renderer-client-id=7 --mojo-platform-channel-handle=1508 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1416 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://genetix.ritmx-prod.aws.vsct.fr/202209210/eto-74da92c9-d451-4afc-b31d-a879469baf23" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2008 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1188,5840886565637737298,12822449951000136209,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=5807690268571661909 --mojo-platform-channel-handle=1392 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1188,5840886565637737298,12822449951000136209,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=8605921637773493631 --mojo-platform-channel-handle=1244 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2732 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:20.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.39.9311 Modules
| |||||||||||||||
| 2804 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2980 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1416 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3236 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1188,5840886565637737298,12822449951000136209,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6138521902239129913 --renderer-client-id=2 --mojo-platform-channel-handle=1196 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
32 250
Read events
32 023
Write events
223
Delete events
4
Modification events
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30968361 | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30968361 | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
119
Text files
18
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:— | SHA256:— | |||
| 1416 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\82CB34DD3343FE727DF8890D352E0D8F | der | |
MD5:— | SHA256:— | |||
| 1416 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\620BEF1064BD8E252C599957B3C91896 | binary | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7D6243C18F0F8F9AEC6638DD210F1984_21FD840265C87364CA59E9179DBA678B | binary | |
MD5:— | SHA256:— | |||
| 2980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7D6243C18F0F8F9AEC6638DD210F1984_21FD840265C87364CA59E9179DBA678B | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
37
DNS requests
29
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1416 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | — | — | whitelisted |
2980 | iexplore.exe | GET | 200 | 108.156.0.115:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
1416 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
2980 | iexplore.exe | GET | 200 | 108.156.0.68:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2980 | iexplore.exe | GET | 200 | 18.66.200.188:80 | http://crl.rootca1.amazontrust.com/rootca1.crl | US | der | 493 b | whitelisted |
3576 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2980 | iexplore.exe | GET | 200 | 178.79.242.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a6ce02787dda06d2 | DE | compressed | 4.70 Kb | whitelisted |
2980 | iexplore.exe | GET | 200 | 108.156.0.73:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2980 | iexplore.exe | GET | 200 | 18.66.200.193:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAQ8voHbxx%2Buih9m1ys1U6s%3D | US | der | 471 b | whitelisted |
2980 | iexplore.exe | GET | 200 | 178.79.242.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?97a1382d4b79da6c | DE | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1416 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2980 | iexplore.exe | 108.156.0.68:80 | o.ss2.us | — | US | unknown |
1416 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2980 | iexplore.exe | 108.156.0.73:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
2980 | iexplore.exe | 18.66.200.188:80 | crl.rootca1.amazontrust.com | Massachusetts Institute of Technology | US | whitelisted |
2980 | iexplore.exe | 18.66.218.109:443 | genetix.ritmx-prod.aws.vsct.fr | Massachusetts Institute of Technology | US | unknown |
2980 | iexplore.exe | 178.79.242.0:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | DE | whitelisted |
2804 | RdrCEF.exe | 23.35.228.137:443 | armmf.adobe.com | Zayo Bandwidth Inc | US | suspicious |
1416 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3576 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
genetix.ritmx-prod.aws.vsct.fr |
| malicious |
dns.msftncsi.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO TLS Handshake Failure |