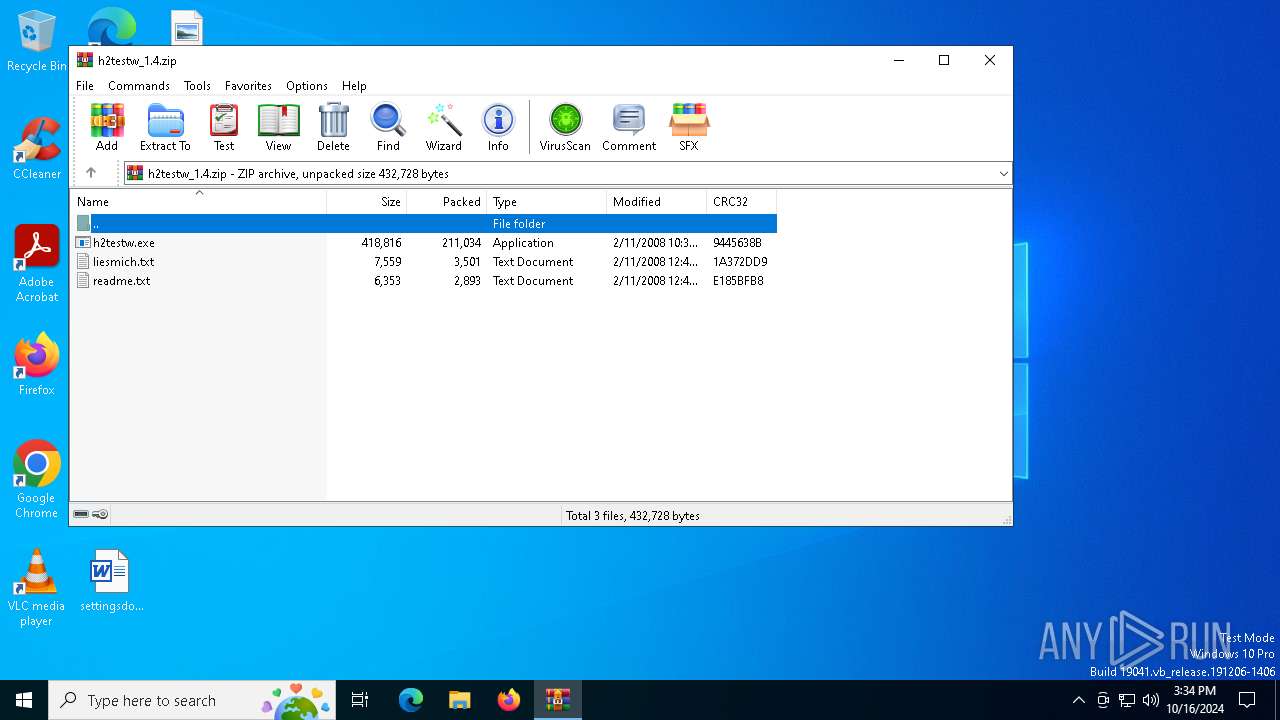
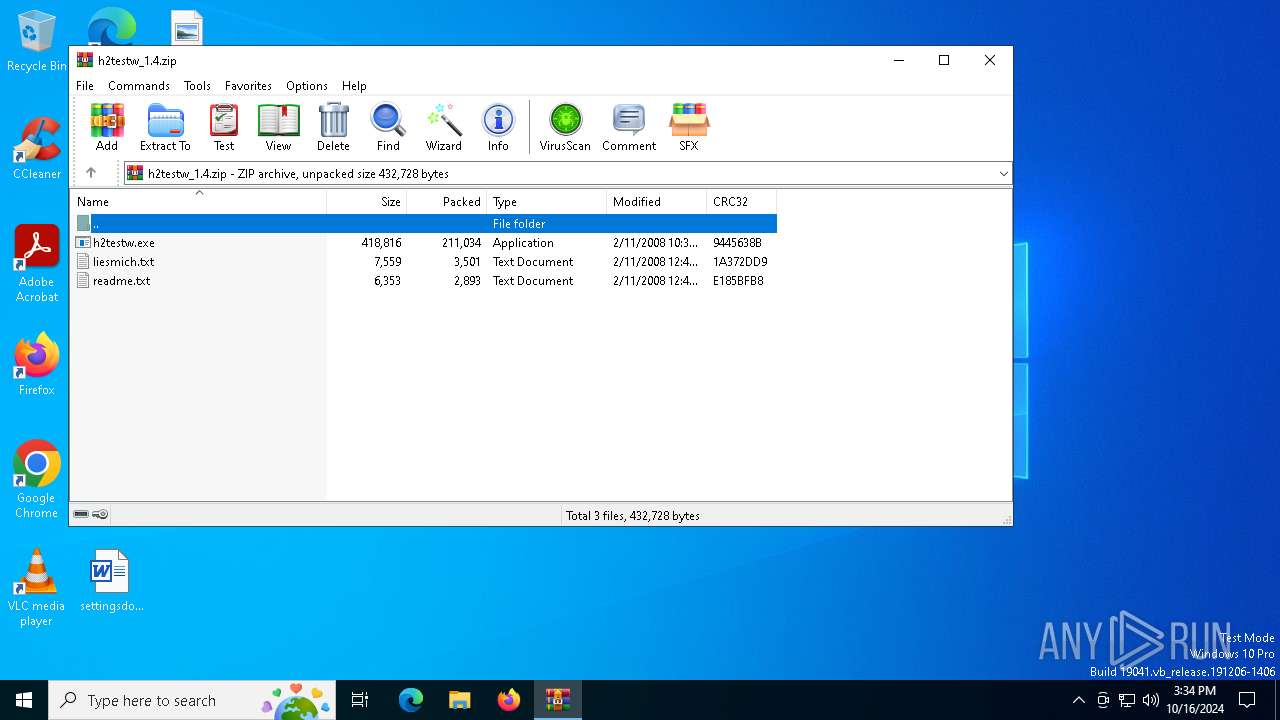
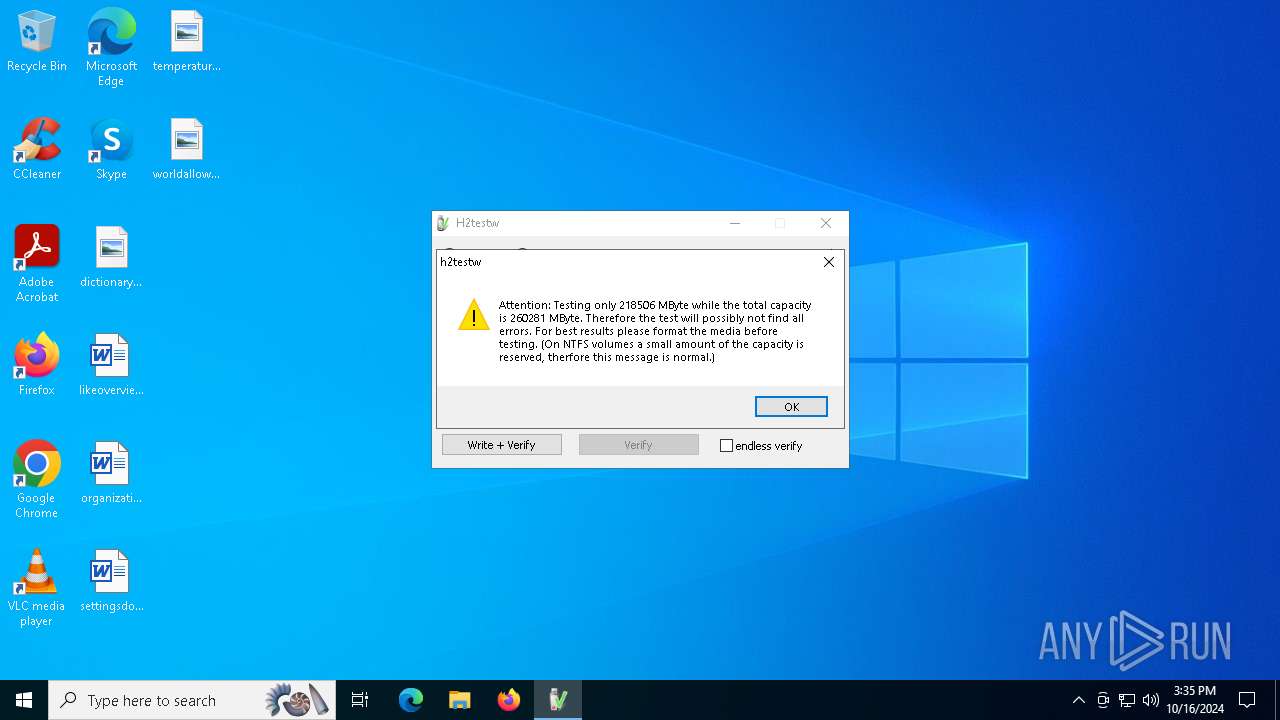
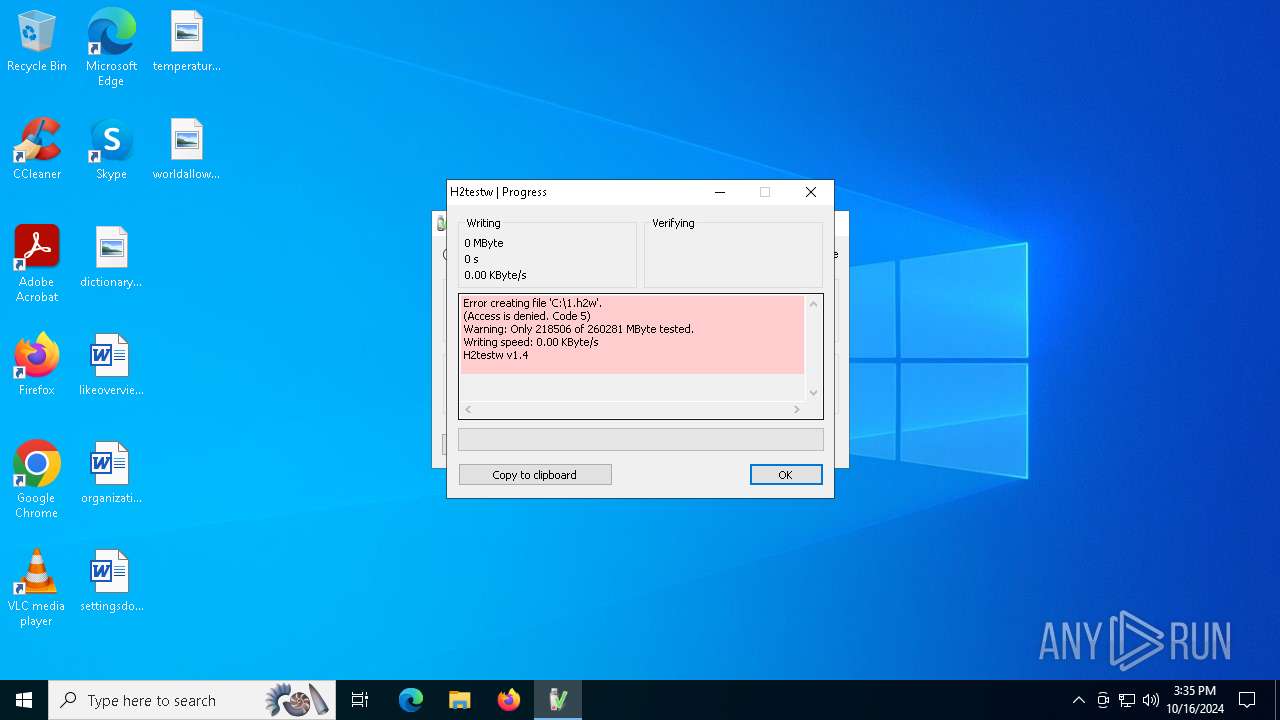
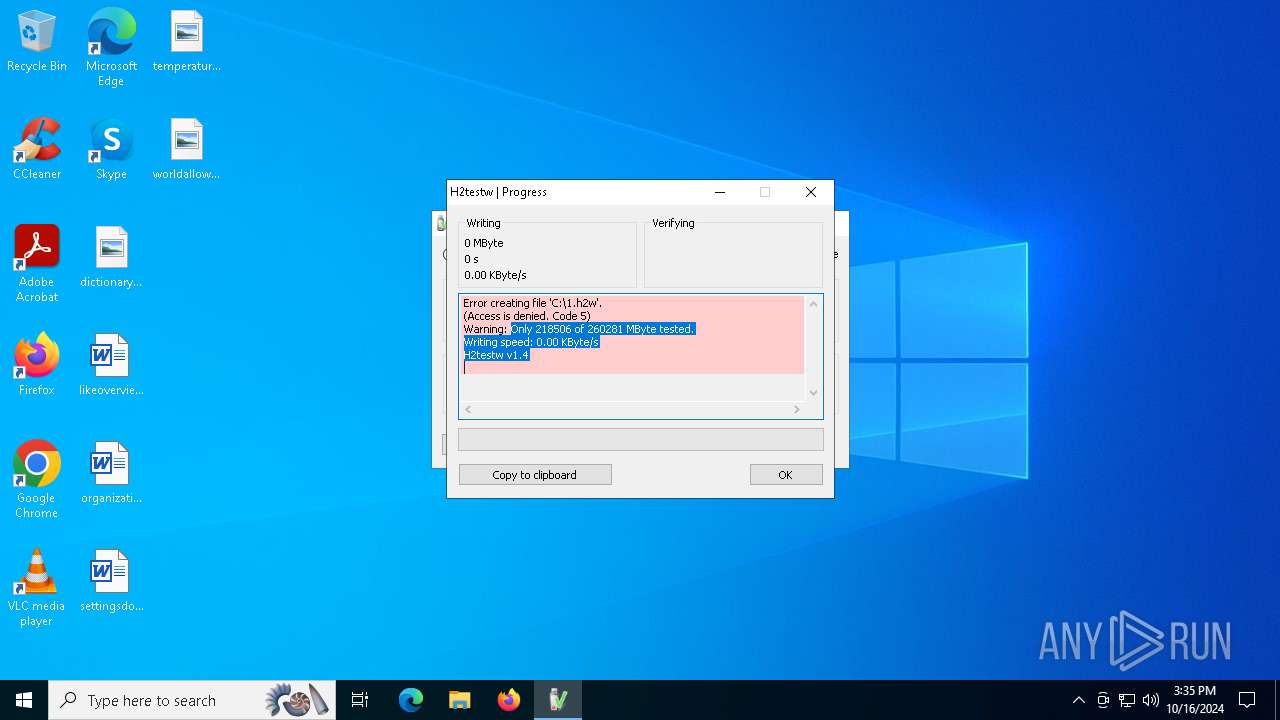
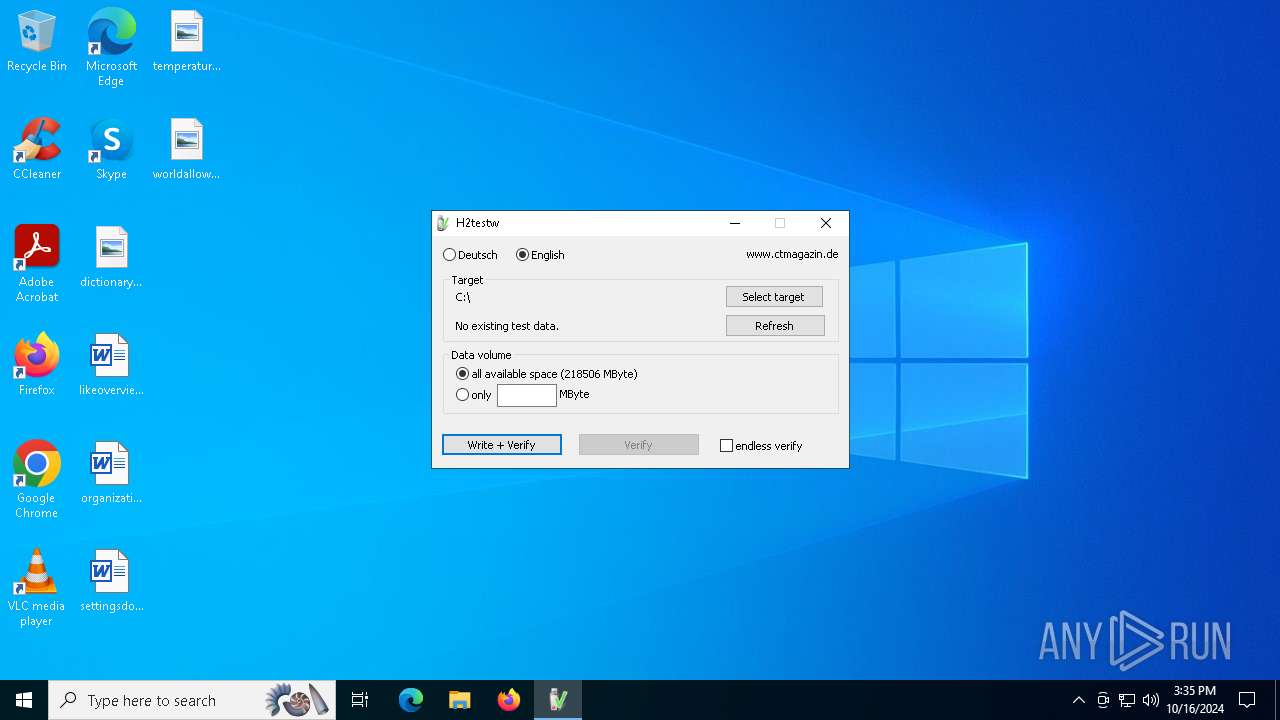
| File name: | h2testw_1.4.zip |
| Full analysis: | https://app.any.run/tasks/fa3e808c-ade7-4ead-9d70-30d5a2619a53 |
| Verdict: | Malicious activity |
| Analysis date: | October 16, 2024, 15:34:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E56FBCBC6F0A2C7AE125869951C63992 |
| SHA1: | 6123AF83ACC20F962CE23179E1E2111AC0DF036D |
| SHA256: | 0D54B8BECA3BC2EBFAB543DBE793D52658D278538F9062B816FB77ABE2DAC187 |
| SSDEEP: | 3072:RwCXlmJWhIjZR5P9IrnKzKuE7fEeozOyfEjhAVy6tqPzxqFHIJ45O+LBh0dEQ:R+UhIpUnKzKuE78RQMYxKIJrCBhNQ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5512)
SUSPICIOUS
Application launched itself
- CCleaner64.exe (PID: 5824)
- CCleaner64.exe (PID: 6132)
Executable content was dropped or overwritten
- CCleaner64.exe (PID: 6132)
- CCleaner64.exe (PID: 6752)
Checks for external IP
- CCleaner64.exe (PID: 6132)
Executes as Windows Service
- CCleanerPerformanceOptimizerService.exe (PID: 2128)
INFO
Manual execution by a user
- h2testw.exe (PID: 944)
- CCleaner64.exe (PID: 5824)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2008:02:11 11:33:36 |
| ZipCRC: | 0x9445638b |
| ZipCompressedSize: | 211034 |
| ZipUncompressedSize: | 418816 |
| ZipFileName: | h2testw.exe |
Total processes
143
Monitored processes
10
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 944 | "C:\Users\admin\Downloads\h2testw_1.4\h2testw.exe" | C:\Users\admin\Downloads\h2testw_1.4\h2testw.exe | — | explorer.exe | |||||||||||
User: admin Company: c't Magazin für Computertechnik Integrity Level: MEDIUM Description: Integritätstest für USB-Sticks und andere Datenträger Exit code: 2 Version: 1.0.4.0 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\CCleaner\CCleanerPerformanceOptimizerService.exe" | C:\Program Files\CCleaner\CCleanerPerformanceOptimizerService.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Piriform Software Ltd Integrity Level: SYSTEM Description: CCleaner Performance Optimizer Service Version: 6.20.0.10897 | |||||||||||||||
| 5512 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\h2testw_1.4.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5592 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5824 | "C:\Program Files\CCleaner\CCleaner64.exe" | C:\Program Files\CCleaner\CCleaner64.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 6132 | "C:\Program Files\CCleaner\CCleaner64.exe" /uac | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Version: 6.20.0.10897 Modules
| |||||||||||||||
| 6256 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6356 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6616 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6752 | "C:\Program Files\CCleaner\CCleaner64.exe" /monitor | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Version: 6.20.0.10897 Modules
| |||||||||||||||
Total events
26 973
Read events
26 772
Write events
130
Delete events
71
Modification events
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\h2testw_1.4.zip | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
6
Suspicious files
41
Text files
30
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5512 | WinRAR.exe | C:\Users\admin\Downloads\h2testw_1.4\h2testw.exe | executable | |
MD5:303D10037DBBD1F502AD01AD829A6DF8 | SHA256:98D7B2530DCD13BCD784C3A9C67B664BCD6290F6F8DE0F4FF8123488F0C9BBE4 | |||
| 6132 | CCleaner64.exe | C:\Program Files\CCleaner\gcapi_17290929566132.dll | executable | |
MD5:F17F96322F8741FE86699963A1812897 | SHA256:8B6CE3A640E2D6F36B0001BE2A1ABB765AE51E62C314A15911E75138CBB544BB | |||
| 6132 | CCleaner64.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\33FQY62M7TF1JXC3P7QY.temp | binary | |
MD5:289B5BDF83A3FE8EA011D33B430912AD | SHA256:ACD12C4140B27856D26CFEBE83179F7D75F3FDAEF2432A337B755AA4364C1187 | |||
| 6132 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:F1FAF29782B14AB190852BB5A8DEF0B4 | SHA256:5D180146F04517BB92689B7EA49484A8EF7BFA2E4963896D329958FDD43EA93C | |||
| 6132 | CCleaner64.exe | C:\Program Files\CCleaner\gcapi_dll.dll | executable | |
MD5:F17F96322F8741FE86699963A1812897 | SHA256:8B6CE3A640E2D6F36B0001BE2A1ABB765AE51E62C314A15911E75138CBB544BB | |||
| 6132 | CCleaner64.exe | — | ||
MD5:— | SHA256:— | |||
| 6132 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:8F7EA867F568C45C23DC61DD633CE25E | SHA256:B0EC3013EE7B9D34486901A9CDD16B9CD25B16382FDCDEB3C1BF58265B68D3E5 | |||
| 6132 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E573CDF4C6D731D56A665145182FD759_AFB3BE9383420FBAFF24AD413EEA555E | binary | |
MD5:446053449AA1A05DE56BD4CB1DF4D41A | SHA256:C684A11F5FA53941AB44C972DDF744ADFD360B953061320600CA3A8869E45FC3 | |||
| 6132 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:94DD667B241315B665FDADB90315C0B3 | SHA256:8F88F43B9055CBEA7B1FFA95D72E047D377AB7F3F400771645AEB015B064AF6F | |||
| 6132 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E573CDF4C6D731D56A665145182FD759_AFB3BE9383420FBAFF24AD413EEA555E | binary | |
MD5:914F7D4D14A5F81F96FAE082F761D529 | SHA256:D98EA008783550D7A59267522DBACF5A84BA9CBFB492F934D4D6FBE6798FAF14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
84
DNS requests
42
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1584 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1584 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6132 | CCleaner64.exe | GET | 200 | 2.19.126.142:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
2484 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6132 | CCleaner64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
6132 | CCleaner64.exe | GET | 200 | 172.217.16.131:80 | http://o.pki.goog/s/wr3/70Q/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEQDvREseTpN%2BJxCI23i31F5J | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6908 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
6132 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
CCleaner64.exe | [2024-10-16 15:35:56.353] [error ] [settings ] [ 6132: 2684] [000000: 0] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2024-10-16 15:35:56.353] [error ] [ini_access ] [ 6132: 2684] [000000: 0] Incorrect ini_accessor configuration! Fixing relative input path to avoid recursion. Input was: Setup
|
CCleaner64.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner64.exe | OnLanguage - en
|
CCleaner64.exe | [2024-10-16 15:35:57.056] [error ] [settings ] [ 6132: 3848] [D2EC45: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2024-10-16 15:35:57.088] [error ] [Burger ] [ 6132: 3848] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | [2024-10-16 15:35:57.088] [error ] [Burger ] [ 6132: 3848] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | file:///tis/optimizer.tis(1131) : warning :'await' should be used only inside 'async' or 'event'
|
CCleaner64.exe | file:///tis/optimizer.tis(1288) : warning :'async' does not contain any 'await'
|
CCleaner64.exe | startCheckingLicense()
|