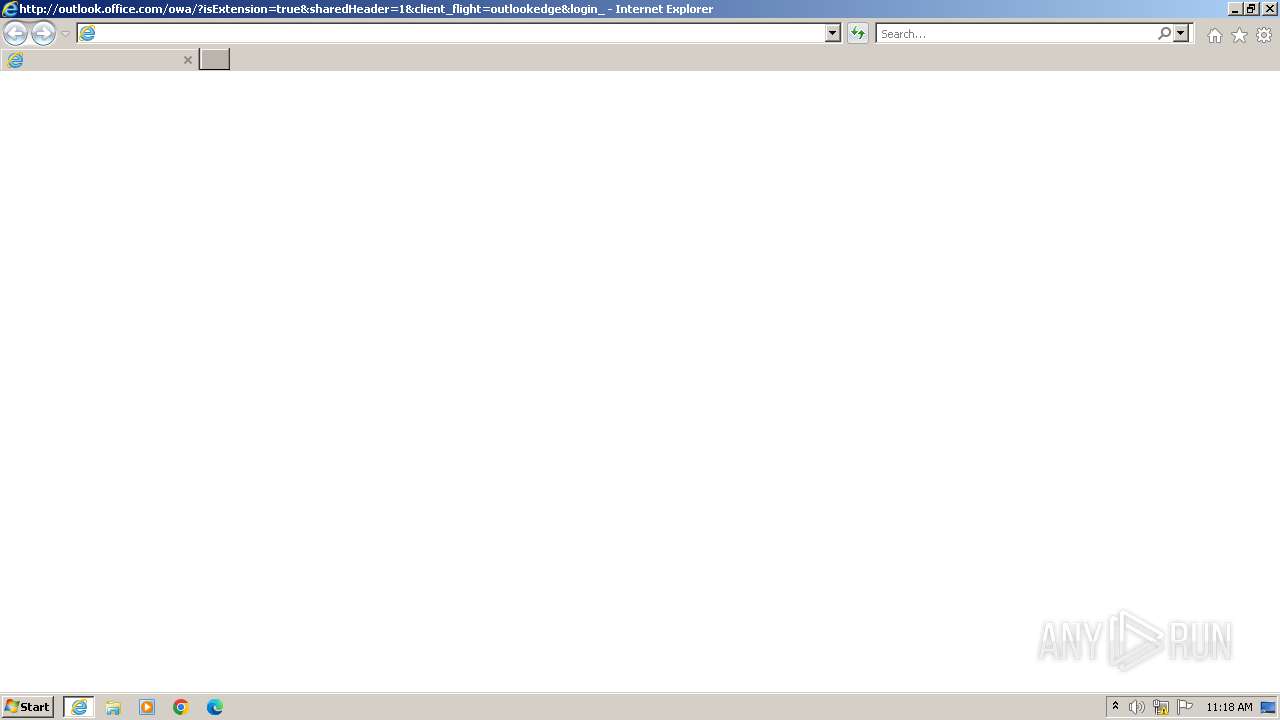
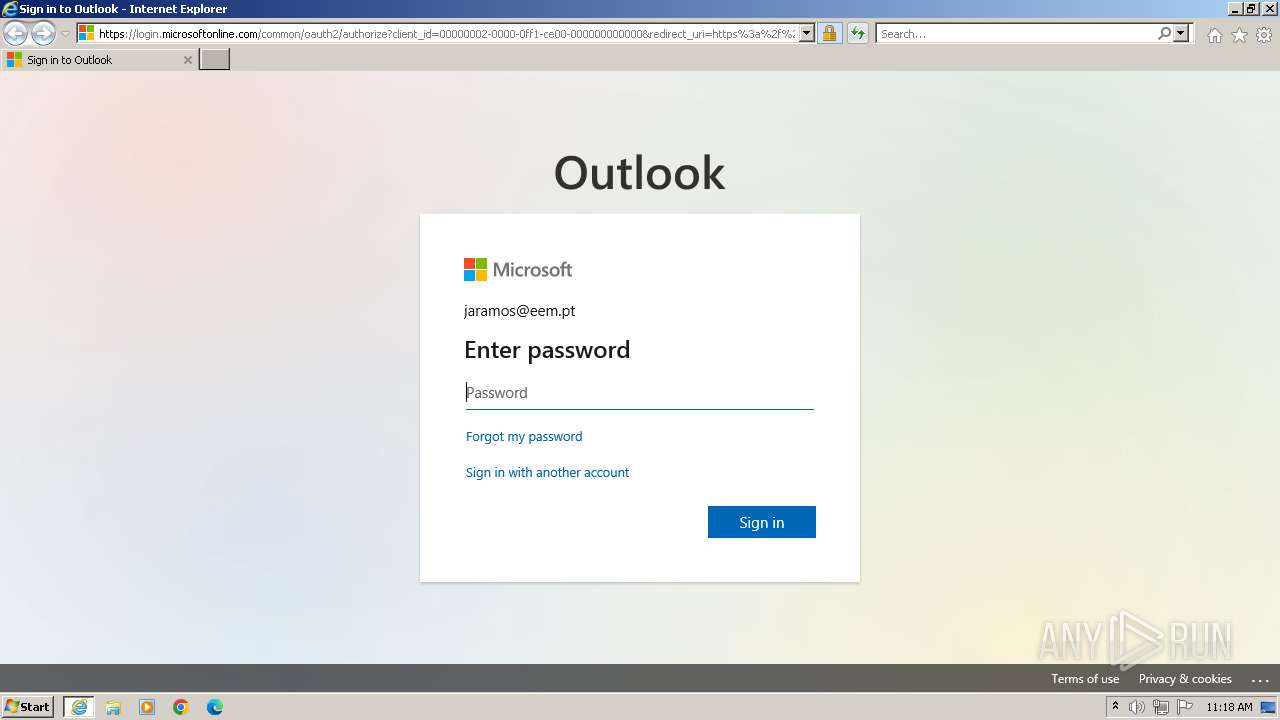
| URL: | outlook.office.com/owa/?isExtension=true&sharedHeader=1&client_flight=outlookedge&login_hint=jaramos@eem.pt&state=1&redirectTo=aHR0cHM6Ly9vdXRsb29rLm9mZmljZS5jb20vbWFpbC9BQU1tQUh0RFFURkNSVGMzTmkwNU9EVXdMVFE0UVVFdFFVRTNNaTAxUmpaQk5rTkdRVEV4UkRsOUFDNEFBQUFBQU43MldwUnVYa1pOaHF2Wmx2QmE1QzhCQVAwV3NwWmpybXRIaG5XTWwwNU9PcllBQUFBVE1VTUFBQT09L2lkL0FBUW1BSHREUVRGQ1JUYzNOaTA1T0RVd0xUUTRRVUV0UVVFM01pMDFSalpCTmtOR1FURXhSRGw5QUJBQVVFeW1kZXE0VmtDS25UZ2RrZFRVQ0E9PS9pdGVtSWQvQUFNbUFIdERRVEZDUlRjM05pMDVPRFV3TFRRNFFVRXRRVUUzTWkwMVJqWkJOa05HUVRFeFJEbDlBRVlBQUFBQUFONzJXcFJ1WGtaTmhxdlpsdkJhNUM4SEFQMFdzcFpqcm10SGhuV01sMDVPT3JZQUFBQVRNVU1BQUd4MmlsQmhKRUJIdmJhMExnYlJNTzhBQjArdmxxRUFBQT09P2lzRXh0ZW5zaW9uPXRydWUmc2hhcmVkSGVhZGVyPTEmY2xpZW50X2ZsaWdodD1vdXRsb29rZWRnZQ |
| Full analysis: | https://app.any.run/tasks/ab184006-4c81-4330-b776-de45ddadc182 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2024, 10:18:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C4F86D3A8935428D9F1EE9BF1C08B7FD |
| SHA1: | 87A7413835D5A8B7480EEBB3B76108D64F3D70A8 |
| SHA256: | 0D33EF2C5BB2695807B54FEEA7019EE7097809A408A4E55424183EC1D19FA294 |
| SSDEEP: | 12:ZzT+uC/lGiIovPyFH+ZKzoyn3nl6L9ZqS6dXny3FencdMwEtyCMfepQworrf8n:ZzTMGFoXGVVVEHeC3FecdMjyL2Vof8 |
MALICIOUS
PHISHING has been detected (SURICATA)
- iexplore.exe (PID: 4020)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- wmpnscfg.exe (PID: 2024)
Reads the computer name
- wmpnscfg.exe (PID: 2024)
Application launched itself
- iexplore.exe (PID: 3964)
Manual execution by a user
- wmpnscfg.exe (PID: 2024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2024 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3964 | "C:\Program Files\Internet Explorer\iexplore.exe" "outlook.office.com/owa/?isExtension=true&sharedHeader=1&client_flight=outlookedge&login_hint=jaramos@eem.pt&state=1&redirectTo=aHR0cHM6Ly9vdXRsb29rLm9mZmljZS5jb20vbWFpbC9BQU1tQUh0RFFURkNSVGMzTmkwNU9EVXdMVFE0UVVFdFFVRTNNaTAxUmpaQk5rTkdRVEV4UkRsOUFDNEFBQUFBQU43MldwUnVYa1pOaHF2Wmx2QmE1QzhCQVAwV3NwWmpybXRIaG5XTWwwNU9PcllBQUFBVE1VTUFBQT09L2lkL0FBUW1BSHREUVRGQ1JUYzNOaTA1T0RVd0xUUTRRVUV0UVVFM01pMDFSalpCTmtOR1FURXhSRGw5QUJBQVVFeW1kZXE0VmtDS25UZ2RrZFRVQ0E9PS9pdGVtSWQvQUFNbUFIdERRVEZDUlRjM05pMDVPRFV3TFRRNFFVRXRRVUUzTWkwMVJqWkJOa05HUVRFeFJEbDlBRVlBQUFBQUFONzJXcFJ1WGtaTmhxdlpsdkJhNUM4SEFQMFdzcFpqcm10SGhuV01sMDVPT3JZQUFBQVRNVU1BQUd4MmlsQmhKRUJIdmJhMExnYlJNTzhBQjArdmxxRUFBQT09P2lzRXh0ZW5zaW9uPXRydWUmc2hhcmVkSGVhZGVyPTEmY2xpZW50X2ZsaWdodD1vdXRsb29rZWRnZQ" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4020 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3964 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
13 987
Read events
13 853
Write events
97
Delete events
37
Modification events
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31103518 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31103518 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
10
Text files
35
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4020 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\F28N89R0.txt | text | |
MD5:702466DB6A9AAC95214CA964BD656B2A | SHA256:823B50545EFF7DC3149EFB9E6433F49CA43FD0F447A65CFB2A7064ECE5D9E8AC | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:C575ADA04CCB0E7F1BBF6DE7D647331E | SHA256:415243AF5C18FF2828327884212211CD80AFB5BC3CDA806EB5E98FB234EF53D0 | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_1941775A515122A167E3FBACF08992E1 | binary | |
MD5:3F0FED861E7FFA0188F4F48371E51833 | SHA256:F47A8600F8F0B055D4D500215FB10000BD860AA1FF8CC58C59111D3FA1F314F5 | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\5NWVUUYV.txt | text | |
MD5:C302A83CF2ADC33087A2494D61401AD6 | SHA256:3C48437884EF3105A488224CD83ED442C6A39151737705BFA99131C94265A151 | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:A1852EE38CD3084A003EDCDCF6E5AB26 | SHA256:85A5C9FFA349561E5F1E1C81E24F96A88A48110FBA4FE630FDAF415267E02561 | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\Y1955KNZ.txt | text | |
MD5:AF1629AD466F227CA7E1A7E569798C3F | SHA256:216341FE2C0C72A980FD351D783F8295E79E0B7081F5A0D19C031EABF7AD9048 | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ConvergedLogin_PCore_jHSrlUosdD1xxbmcR_lMNA2[1].js | s | |
MD5:8C74AB954A2C743D71C5B99C47F94C34 | SHA256:B449CE27BB6C0352DC780DBA81B4D323D4808DAEEE064DD934CEC65B67BE8D46 | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B94E0EBCCC24C135EFFBC0CDB89CA425 | SHA256:C62A93706A28DE71A0482786715388FB4311A24A5EA4943C7DE902B19E953010 | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\E7ZHPXXE.txt | text | |
MD5:C054F3F3C872CEDDD257276ED038EAEB | SHA256:C06BE1F90B14C6B2B7F25695C3E237C7844CA44D04695A707F0D2DBE1C4B7939 | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\H343CWIS.txt | text | |
MD5:9A140C70BBDC38B8D177715D820F9A6C | SHA256:550BC2544EBBF355C3B93D765B3E2DCF5CDE7A62A00C3DB11A5E8E31D2722B89 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4020 | iexplore.exe | GET | 301 | 40.99.157.18:80 | http://outlook.office.com/owa/?isExtension=true&sharedHeader=1&client_flight=outlookedge&login_hint=jaramos@eem.pt&state=1&redirectTo=aHR0cHM6Ly9vdXRsb29rLm9mZmljZS5jb20vbWFpbC9BQU1tQUh0RFFURkNSVGMzTmkwNU9EVXdMVFE0UVVFdFFVRTNNaTAxUmpaQk5rTkdRVEV4UkRsOUFDNEFBQUFBQU43MldwUnVYa1pOaHF2Wmx2QmE1QzhCQVAwV3NwWmpybXRIaG5XTWwwNU9PcllBQUFBVE1VTUFBQT09L2lkL0FBUW1BSHREUVRGQ1JUYzNOaTA1T0RVd0xUUTRRVUV0UVVFM01pMDFSalpCTmtOR1FURXhSRGw5QUJBQVVFeW1kZXE0VmtDS25UZ2RrZFRVQ0E9PS9pdGVtSWQvQUFNbUFIdERRVEZDUlRjM05pMDVPRFV3TFRRNFFVRXRRVUUzTWkwMVJqWkJOa05HUVRFeFJEbDlBRVlBQUFBQUFONzJXcFJ1WGtaTmhxdlpsdkJhNUM4SEFQMFdzcFpqcm10SGhuV01sMDVPT3JZQUFBQVRNVU1BQUd4MmlsQmhKRUJIdmJhMExnYlJNTzhBQjArdmxxRUFBQT09P2lzRXh0ZW5zaW9uPXRydWUmc2hhcmVkSGVhZGVyPTEmY2xpZW50X2ZsaWdodD1vdXRsb29rZWRnZQ | unknown | — | — | unknown |
4020 | iexplore.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?99c9fdafe1a1de72 | unknown | — | — | unknown |
4020 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA8XGkjG8iOAkhjNLtbdwOg%3D | unknown | — | — | unknown |
4020 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?32a7a8361135dd15 | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0d685e1cf011c38b | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4020 | iexplore.exe | 40.99.157.18:80 | outlook.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | DE | unknown |
4020 | iexplore.exe | 40.99.157.18:443 | outlook.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | DE | unknown |
4020 | iexplore.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
4020 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
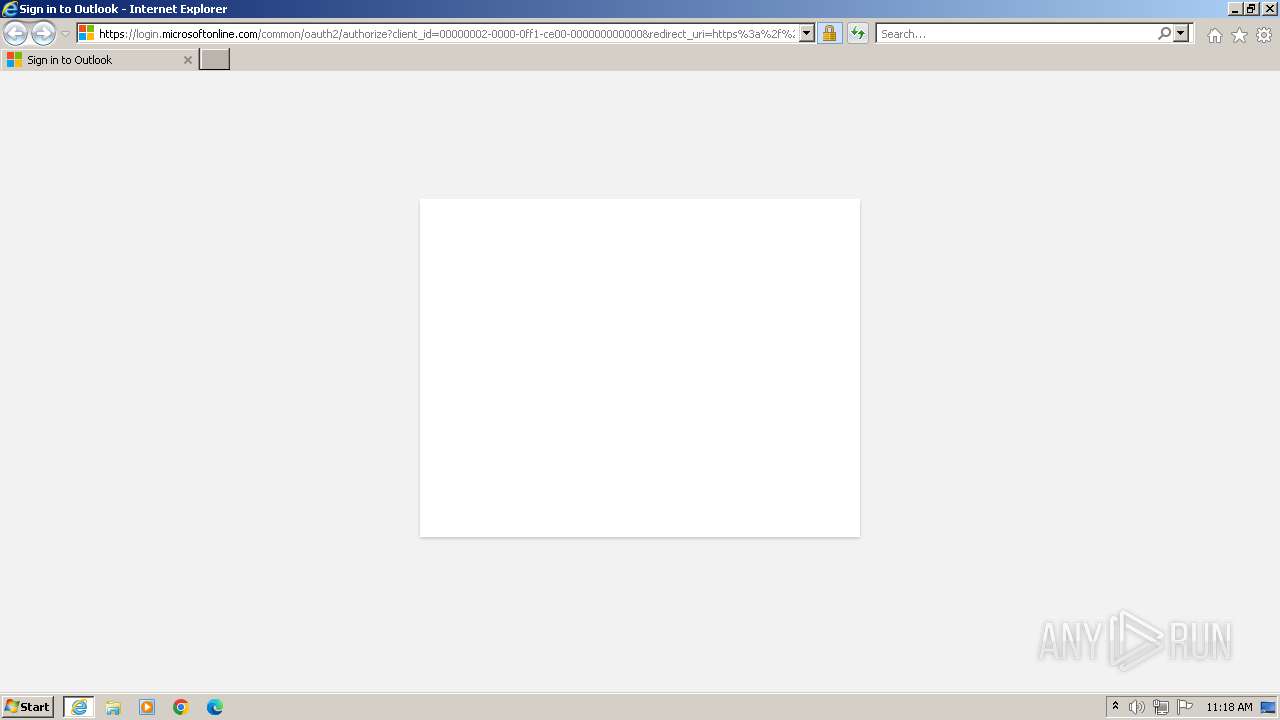
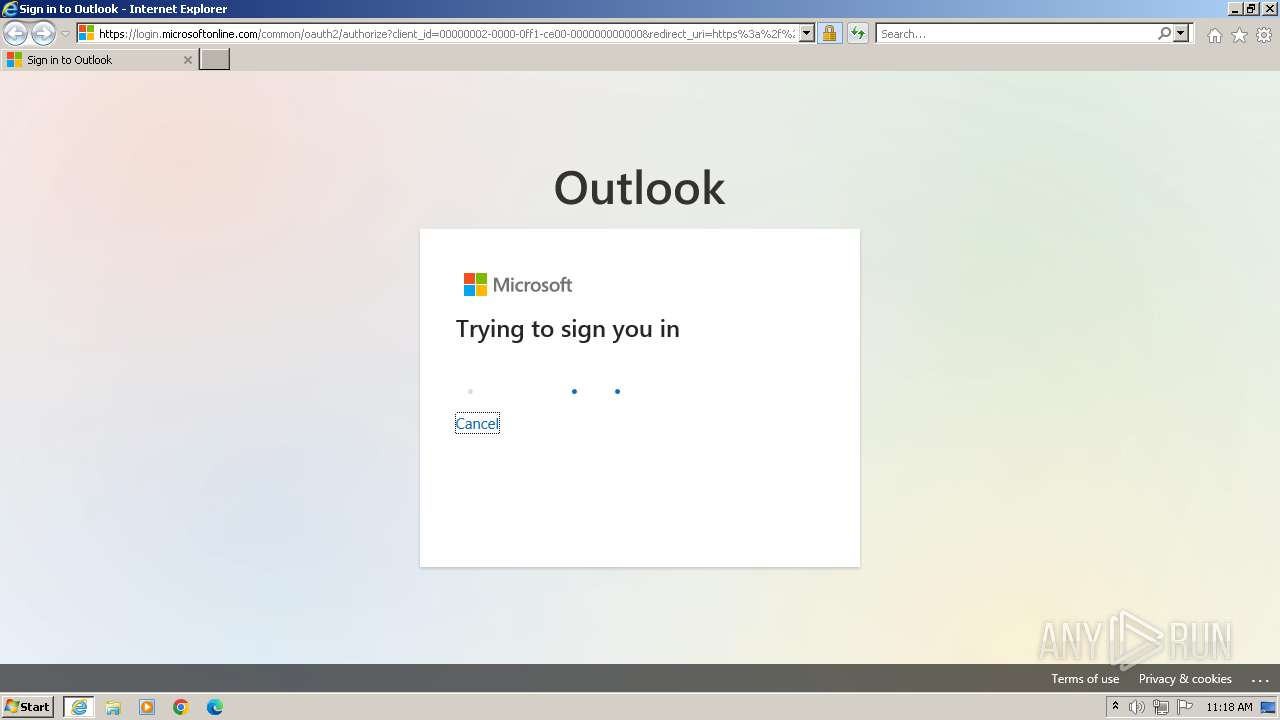
4020 | iexplore.exe | 20.190.159.64:443 | login.microsoftonline.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4020 | iexplore.exe | 152.199.23.37:443 | aadcdn.msftauth.net | EDGECAST | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
outlook.office.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
aadcdn.msftauth.net |
| whitelisted |
outlook.office365.com |
| whitelisted |
login.live.com |
| whitelisted |
r4.res.office365.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4020 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] A suspicious URI containing an email address |