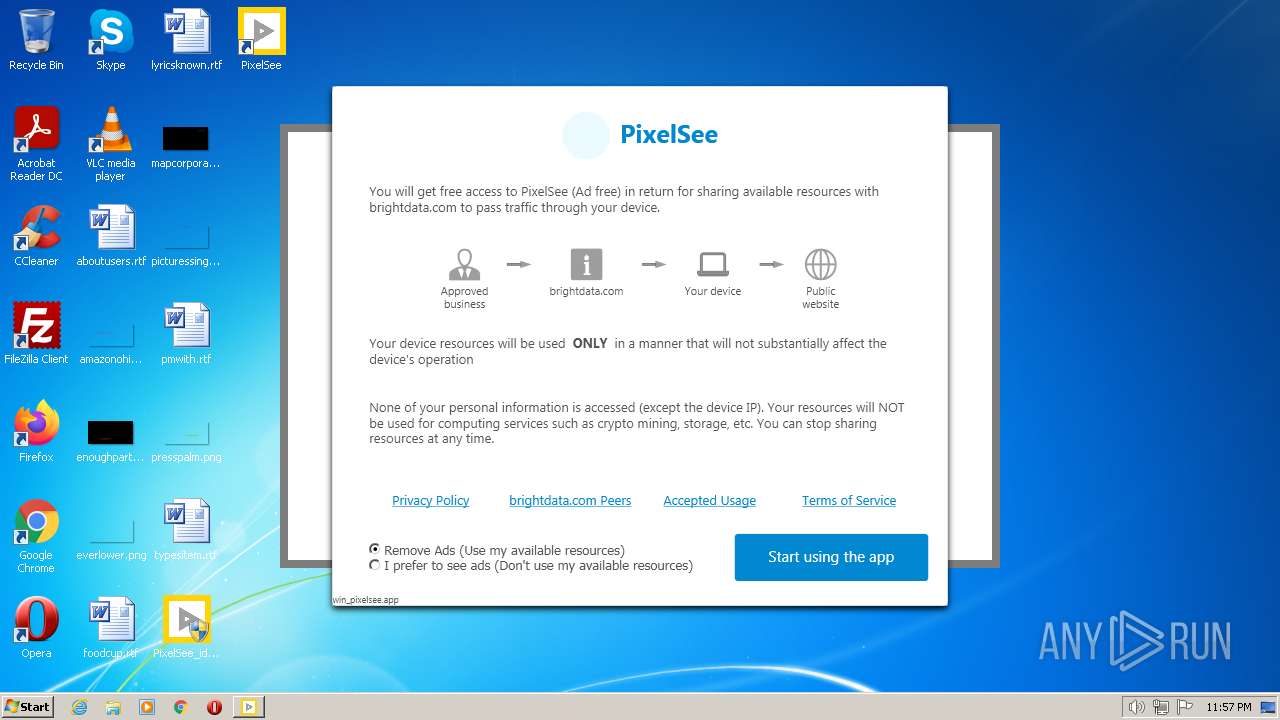
| File name: | PixelSee_id247007id.exe.7z |
| Full analysis: | https://app.any.run/tasks/995fb863-a229-4e36-8b7a-5fc6e35b2d54 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2023, 23:55:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 310B37601E5E3B8F8D1C1941A2E231F0 |
| SHA1: | 32A6753337E5D382D3FEBB343AB818A021B4581A |
| SHA256: | 0D1E143AB85DD44AC7AB62EDE9C13B72145B4958704ECF5FBB7294011C945091 |
| SSDEEP: | 49152:D3ndVb+FtwUY7juHVJrBWe2yqXZBBAbVa70IA:7d1+jl66VBBL2nwK0V |
MALICIOUS
Application was dropped or rewritten from another process
- PixelSee_id247007id.exe (PID: 2484)
- PixelSee_id247007id.exe (PID: 3524)
- lum_inst.exe (PID: 2800)
- net_updater32.exe (PID: 3504)
- test_wpf.exe (PID: 1784)
- net_updater32.exe (PID: 2120)
- pixelsee.exe (PID: 3064)
- net_updater32.exe (PID: 3380)
- pixelsee_crashpad_handler.exe (PID: 1236)
- test_wpf.exe (PID: 2800)
- luminati-m-controller.exe (PID: 4084)
- test_wpf.exe (PID: 3496)
- idle_report.exe (PID: 1968)
Actions looks like stealing of personal data
- PixelSee_id247007id.exe (PID: 3524)
The DLL Hijacking
- SearchProtocolHost.exe (PID: 2688)
Drops the executable file immediately after the start
- lum_inst.exe (PID: 2800)
- PixelSee_id247007id.exe (PID: 3524)
- lum_inst.tmp (PID: 708)
- net_updater32.exe (PID: 3504)
- net_updater32.exe (PID: 3380)
- luminati-m-controller.exe (PID: 4084)
Changes the autorun value in the registry
- pixelsee.exe (PID: 3064)
SUSPICIOUS
Reads Microsoft Outlook installation path
- PixelSee_id247007id.exe (PID: 3524)
Reads the Internet Settings
- PixelSee_id247007id.exe (PID: 3524)
- lum_inst.tmp (PID: 708)
- net_updater32.exe (PID: 3504)
Reads Internet Explorer settings
- PixelSee_id247007id.exe (PID: 3524)
The process drops C-runtime libraries
- PixelSee_id247007id.exe (PID: 3524)
- net_updater32.exe (PID: 3504)
Creates a software uninstall entry
- PixelSee_id247007id.exe (PID: 3524)
Executable content was dropped or overwritten
- lum_inst.exe (PID: 2800)
- PixelSee_id247007id.exe (PID: 3524)
- lum_inst.tmp (PID: 708)
- net_updater32.exe (PID: 3504)
- net_updater32.exe (PID: 3380)
- luminati-m-controller.exe (PID: 4084)
Reads the Windows owner or organization settings
- lum_inst.tmp (PID: 708)
Drops a file with too old compile date
- PixelSee_id247007id.exe (PID: 3524)
Reads settings of System Certificates
- net_updater32.exe (PID: 3504)
- net_updater32.exe (PID: 2120)
- net_updater32.exe (PID: 3380)
Adds/modifies Windows certificates
- lum_inst.tmp (PID: 708)
Checks Windows Trust Settings
- net_updater32.exe (PID: 3504)
- net_updater32.exe (PID: 3380)
Reads security settings of Internet Explorer
- net_updater32.exe (PID: 3504)
Detected use of alternative data streams (AltDS)
- net_updater32.exe (PID: 3504)
Application launched itself
- net_updater32.exe (PID: 3504)
- net_svc.exe (PID: 528)
Changes default file association
- PixelSee_id247007id.exe (PID: 3524)
- pixelsee.exe (PID: 3064)
Executes as Windows Service
- net_updater32.exe (PID: 3380)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3512)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3512)
Manual execution by a user
- PixelSee_id247007id.exe (PID: 2484)
- PixelSee_id247007id.exe (PID: 3524)
Checks proxy server information
- PixelSee_id247007id.exe (PID: 3524)
- net_updater32.exe (PID: 3504)
Checks supported languages
- PixelSee_id247007id.exe (PID: 3524)
- lum_inst.tmp (PID: 708)
- lum_inst.exe (PID: 2800)
- net_updater32.exe (PID: 3504)
- test_wpf.exe (PID: 1784)
- net_updater32.exe (PID: 2120)
- pixelsee.exe (PID: 3064)
- net_updater32.exe (PID: 3380)
- pixelsee_crashpad_handler.exe (PID: 1236)
The process checks LSA protection
- PixelSee_id247007id.exe (PID: 3524)
- lum_inst.tmp (PID: 708)
- net_updater32.exe (PID: 3504)
- test_wpf.exe (PID: 1784)
- WISPTIS.EXE (PID: 928)
- net_updater32.exe (PID: 2120)
- pixelsee.exe (PID: 3064)
- net_updater32.exe (PID: 3380)
Reads the computer name
- PixelSee_id247007id.exe (PID: 3524)
- lum_inst.tmp (PID: 708)
- net_updater32.exe (PID: 3504)
- test_wpf.exe (PID: 1784)
- net_updater32.exe (PID: 2120)
- pixelsee.exe (PID: 3064)
- net_updater32.exe (PID: 3380)
Reads the machine GUID from the registry
- PixelSee_id247007id.exe (PID: 3524)
- net_updater32.exe (PID: 3504)
- test_wpf.exe (PID: 1784)
- lum_inst.tmp (PID: 708)
- net_updater32.exe (PID: 2120)
- pixelsee.exe (PID: 3064)
- net_updater32.exe (PID: 3380)
Create files in a temporary directory
- lum_inst.exe (PID: 2800)
- PixelSee_id247007id.exe (PID: 3524)
Creates files or folders in the user directory
- PixelSee_id247007id.exe (PID: 3524)
- net_updater32.exe (PID: 3504)
- pixelsee.exe (PID: 3064)
- pixelsee_crashpad_handler.exe (PID: 1236)
Drops a file that was compiled in debug mode
- lum_inst.tmp (PID: 708)
- PixelSee_id247007id.exe (PID: 3524)
- net_updater32.exe (PID: 3504)
- net_updater32.exe (PID: 3380)
- luminati-m-controller.exe (PID: 4084)
Application was dropped or rewritten from another process
- lum_inst.tmp (PID: 708)
Creates files in the program directory
- net_updater32.exe (PID: 3504)
Reads Environment values
- net_updater32.exe (PID: 3504)
- pixelsee.exe (PID: 3064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
71
Monitored processes
21
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Users\admin\PixelSee\Luminati-m\luminati\net_svc.exe" --workdir C:/Users/admin/PixelSee/Luminati-m/luminati --no-root --parent-die-stdin --sdk --sdk-version 1.240.55 --appid win_pixelsee.app --uuid sdk-win-dcfab149a585482688c4dddae6aa9495 | C:\Users\admin\PixelSee\Luminati-m\luminati\net_svc.exe | — | net_updater32.exe | |||||||||||
User: SYSTEM Company: Luminati Networks Ltd. Integrity Level: SYSTEM Description: Luminati SDK Engine Exit code: 0 Version: 1.245.997 | |||||||||||||||
| 708 | "C:\Users\admin\AppData\Local\Temp\is-SSKAO.tmp\lum_inst.tmp" /SL5="$4014C,2213348,121344,C:\Users\admin\AppData\Local\Temp\luminati\lum_inst.exe" /verysilent | C:\Users\admin\AppData\Local\Temp\is-SSKAO.tmp\lum_inst.tmp | lum_inst.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 101 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 928 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\SYSTEM32\WISPTIS.EXE | — | net_updater32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 24 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | C:\Users\admin\PixelSee\pixelsee_crashpad_handler.exe --no-rate-limit "--database=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps" "--metrics-dir=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps" --url=https://o612922.ingest.sentry.io:443/api/6420364/minidump/?sentry_client=sentry.native/0.4.6&sentry_key=297ce3230e5f4bcf957dbf23e9597dc9 "--attachment=C:/Users/admin/AppData/Local/PixelSee LLC/PixelSee/crashdumps/logs/log" "--attachment=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps\0d50a752-abb7-40ad-8000-fcfd5c4b89ff.run\__sentry-event" "--attachment=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps\0d50a752-abb7-40ad-8000-fcfd5c4b89ff.run\__sentry-breadcrumb1" "--attachment=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps\0d50a752-abb7-40ad-8000-fcfd5c4b89ff.run\__sentry-breadcrumb2" --initial-client-data=0x38c,0x390,0x394,0x360,0x398,0x6deb7b7c,0x6deb7b90,0x6deb7ba0 | C:\Users\admin\PixelSee\pixelsee_crashpad_handler.exe | — | pixelsee.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1784 | C:\Users\admin\PixelSee\Luminati-m\test_wpf.exe | C:\Users\admin\PixelSee\Luminati-m\test_wpf.exe | — | net_updater32.exe | |||||||||||
User: admin Company: Luminati Networks Ltd. Integrity Level: HIGH Description: test_wpf Exit code: 0 Version: 1.240.55 Modules
| |||||||||||||||
| 1968 | C:\Users\admin\PixelSee\Luminati-m\luminati\idle_report.exe 55944 | C:\Users\admin\PixelSee\Luminati-m\luminati\idle_report.exe | — | net_updater32.exe | |||||||||||
User: admin Company: Luminati Networks Ltd. Integrity Level: MEDIUM Description: idle_report Exit code: 0 Version: 1.240.55 | |||||||||||||||
| 2120 | "C:\Users\admin\PixelSee\Luminati-m\net_updater32.exe" --install win_pixelsee.app --no-cleanup | C:\Users\admin\PixelSee\Luminati-m\net_updater32.exe | net_updater32.exe | ||||||||||||
User: admin Company: Luminati Networks Ltd. Integrity Level: HIGH Description: Luminati SDK Updater Exit code: 0 Version: 1.240.55 Modules
| |||||||||||||||
| 2216 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\SYSTEM32\WISPTIS.EXE | — | net_updater32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2280 | "C:\Users\admin\PixelSee\Luminati-m\luminati\net_svc.exe" --report-idle | C:\Users\admin\PixelSee\Luminati-m\luminati\net_svc.exe | — | net_svc.exe | |||||||||||
User: admin Company: Luminati Networks Ltd. Integrity Level: MEDIUM Description: Luminati SDK Engine Exit code: 0 Version: 1.245.997 | |||||||||||||||
| 2484 | "C:\Users\admin\Desktop\PixelSee_id247007id.exe" | C:\Users\admin\Desktop\PixelSee_id247007id.exe | — | Explorer.EXE | |||||||||||
User: admin Company: PixelSee Integrity Level: MEDIUM Description: PixelSee Player Exit code: 3221226540 Modules
| |||||||||||||||
Total events
37 822
Read events
37 108
Write events
582
Delete events
132
Modification events
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PixelSee_id247007id.exe.7z | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
930
Suspicious files
108
Text files
242
Unknown types
256
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3512 | WinRAR.exe | C:\Users\admin\Desktop\PixelSee_id247007id.exe | executable | |
MD5:60849A8FF219BE4BEC52709173984455 | SHA256:B2A96537B627CC5F7ED63B4B9491B9EA15B08C88DFDD5AEB7A00D903DD4D0176 | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\Montserrat-Regular.eot | eot | |
MD5:2DD0A1DE870AF34D48D43B7CAD82B8D9 | SHA256:057BC6C47C47AACCDF31ADC48A6B401F6090A02C28E354099EFF80907DC2AF32 | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\main-icon-big.png | image | |
MD5:0E5FEA82CC4F4A8225532E5B2F45C6C8 | SHA256:81B5F50491579127D13E050847EF6D817265AB4B70D2796FB74021463B778BB9 | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\preloader.html | html | |
MD5:37A05031BEC9D3E093388407848AF66F | SHA256:CF38F4F8663028BEFF3A7650A9D426B4116891E8547029B66B8D2A13FAD63A48 | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\img2\cancel-page-new1-ru.png | image | |
MD5:E5A8DCB5948856CC1ADBC95E9ABCDEA9 | SHA256:9B89878B847BDAD03A4024AD4C78DCC3C1F8174B4803130105A7C275B0E52966 | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\img2\bundle2-check-on.png | image | |
MD5:0B5B7C97006E28013557CEE9E922D7DB | SHA256:3EBD2BEA7B3E1D9A09EDF27B3AAE63195D5DAE08D6581713BEC25C193C6A04CB | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\img2\bundle2-check-off.png | image | |
MD5:32B3447C944FEBD3927E607FF60C7FA6 | SHA256:FFC40BD54DD7A0010B1FEE3270133A0E9B917B925F461E5E09C0B3FBC0B638F6 | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\img2\bundle1-check-off.png | image | |
MD5:A5E92D07D4F8804726D7D8429791DD48 | SHA256:F2541446FDD1AA134A66B9A6F91EBF7F880F0A6120E0BFBC85E7BEE3A6D49DB7 | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\img2\close-lightgray.png | image | |
MD5:77C4A2277FE3EA35957C67485821BBCF | SHA256:53291723D1CDC12D654EEE233873B3BBAB71E719C8B7285A3C8B1677B10831FF | |||
| 3524 | PixelSee_id247007id.exe | C:\Users\admin\AppData\Local\Temp\pixelsee-installer-tmp\img2\bundle1-check-on.png | image | |
MD5:3E30B7AE8F178D065D094AAE7829ECA8 | SHA256:F894CCDDA93A17A8B7B0DCE1D295E490C2B66444E05A8F5B319515CF83378361 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
53
DNS requests
15
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 104.18.32.68:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 1.42 Kb | whitelisted |
— | — | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEB2iSDBvmyYY0ILgln0z02o%3D | US | der | 2.18 Kb | whitelisted |
— | — | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQ5suEceKjAJbxseAmHFkQ9FrhTWQQUDuE6qFM6MdWKvsG7rWcaA4WtNA4CEQDvy%2BOQ74w4P7l1LJtfioaI | US | der | 510 b | whitelisted |
3380 | net_updater32.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?608170ec6df1bff7 | US | compressed | 4.70 Kb | whitelisted |
— | — | GET | 200 | 3.94.72.89:80 | http://lumtest.com/myip.json | US | binary | 263 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3524 | PixelSee_id247007id.exe | 51.158.190.232:443 | pixelsee.app | Online S.a.s. | FR | suspicious |
3504 | net_updater32.exe | 161.35.48.195:443 | perr.l-err.biz | DIGITALOCEAN-ASN | US | unknown |
3504 | net_updater32.exe | 192.81.214.145:443 | perr.l-err.biz | DIGITALOCEAN-ASN | US | suspicious |
3504 | net_updater32.exe | 3.228.177.90:443 | clientsdk.lum-sdk.io | AMAZON-AES | US | suspicious |
3504 | net_updater32.exe | 51.158.190.232:443 | pixelsee.app | Online S.a.s. | FR | suspicious |
2120 | net_updater32.exe | 161.35.48.195:443 | perr.l-err.biz | DIGITALOCEAN-ASN | US | unknown |
2120 | net_updater32.exe | 162.125.66.18:443 | www.dropbox.com | DROPBOX | DE | suspicious |
— | — | 142.250.74.206:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
— | — | 3.228.177.90:443 | clientsdk.lum-sdk.io | AMAZON-AES | US | suspicious |
— | — | 161.35.48.195:443 | perr.l-err.biz | DIGITALOCEAN-ASN | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pixelsee.app |
| suspicious |
www.dropbox.com |
| shared |
perr.l-err.biz |
| suspicious |
perr.lum-sdk.io |
| suspicious |
clientsdk.lum-sdk.io |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3504 | net_updater32.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
3504 | net_updater32.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
pixelsee.exe | QWindowsEGLStaticContext::create: When using ANGLE, check if d3dcompiler_4x.dll is available
|
pixelsee.exe | QWindowsEGLStaticContext::create: Could not initialize EGL display: error 0x3001
|
pixelsee.exe | QWindowsEGLStaticContext::create: Could not initialize EGL display: error 0x3001
|
pixelsee.exe | QWindowsEGLStaticContext::create: When using ANGLE, check if d3dcompiler_4x.dll is available
|
pixelsee.exe | > __thiscall Application::Application(int &,char *[])
|
pixelsee.exe | > __thiscall Application::Application(int &,char *[])
|
pixelsee.exe | os version: "6.1.7601v" __ os name: "Windows 7 Version 6.1 (Build 7601: SP 1)"
|
pixelsee.exe | os version: "6.1.7601v" __ os name: "Windows 7 Version 6.1 (Build 7601: SP 1)"
|
pixelsee.exe | > __thiscall PixelseeSettings::PixelseeSettings(void)
|
pixelsee.exe | > int __thiscall Application::exec(void)
|