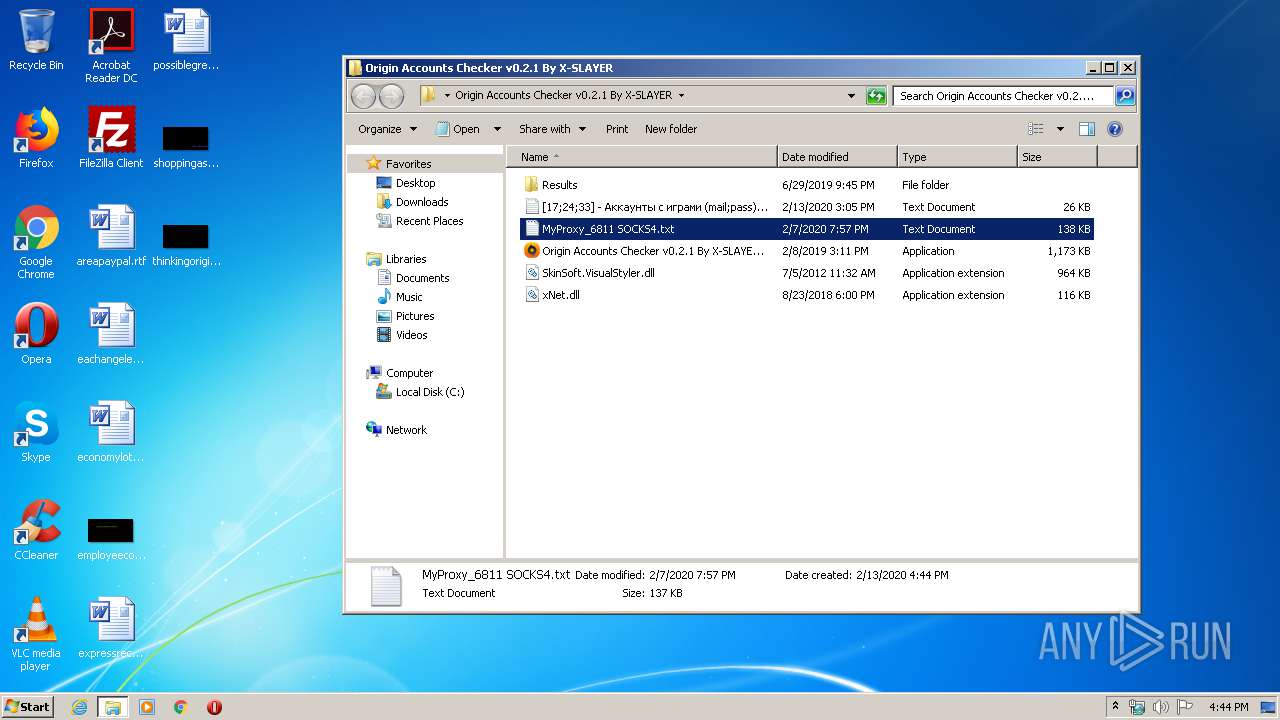
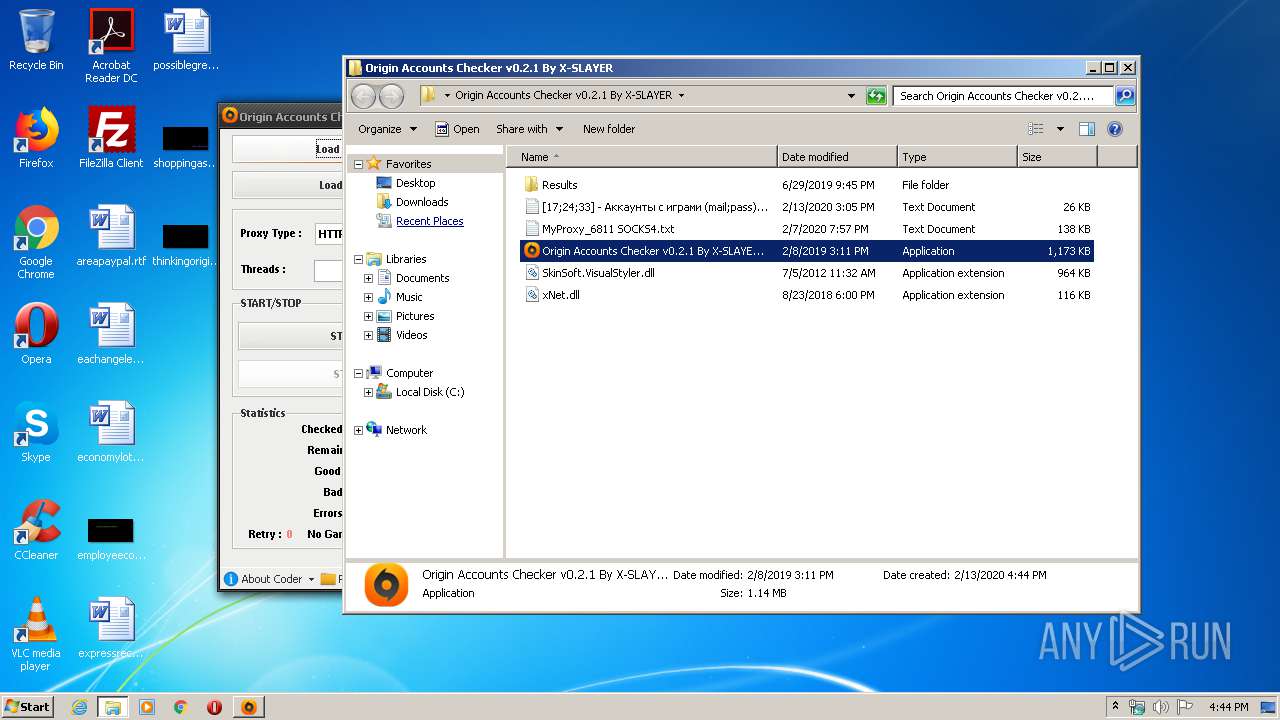
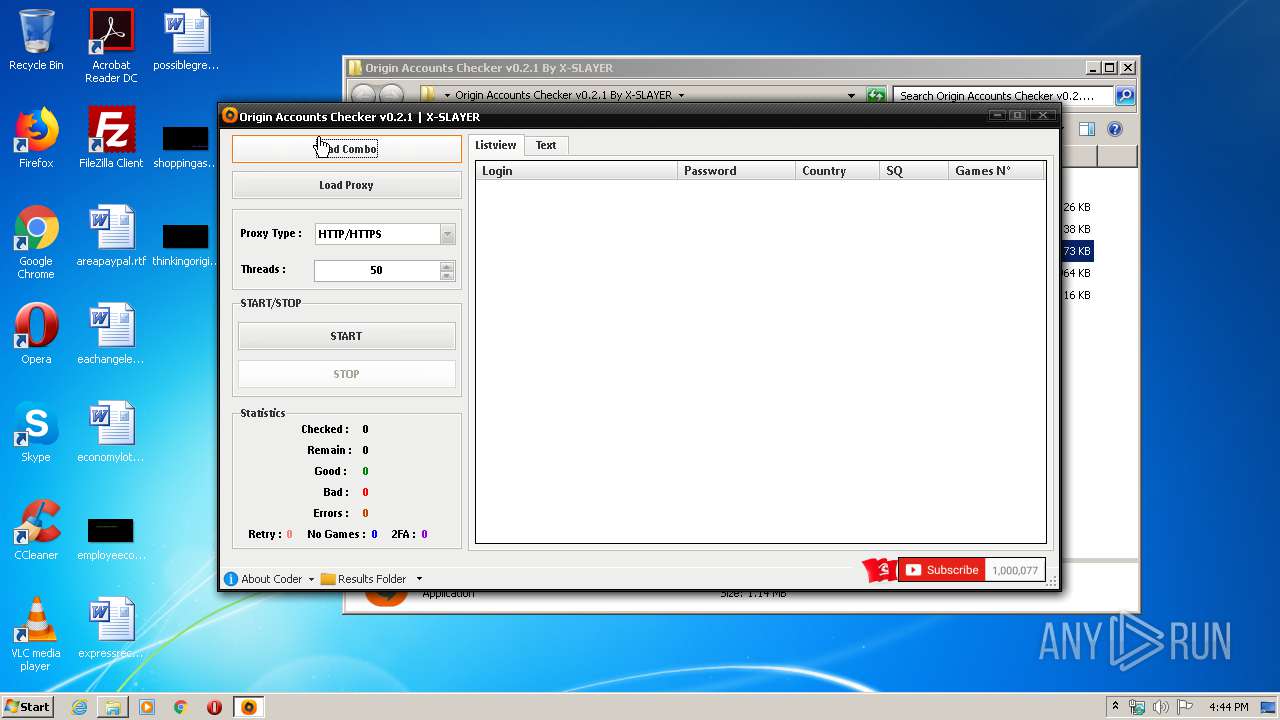
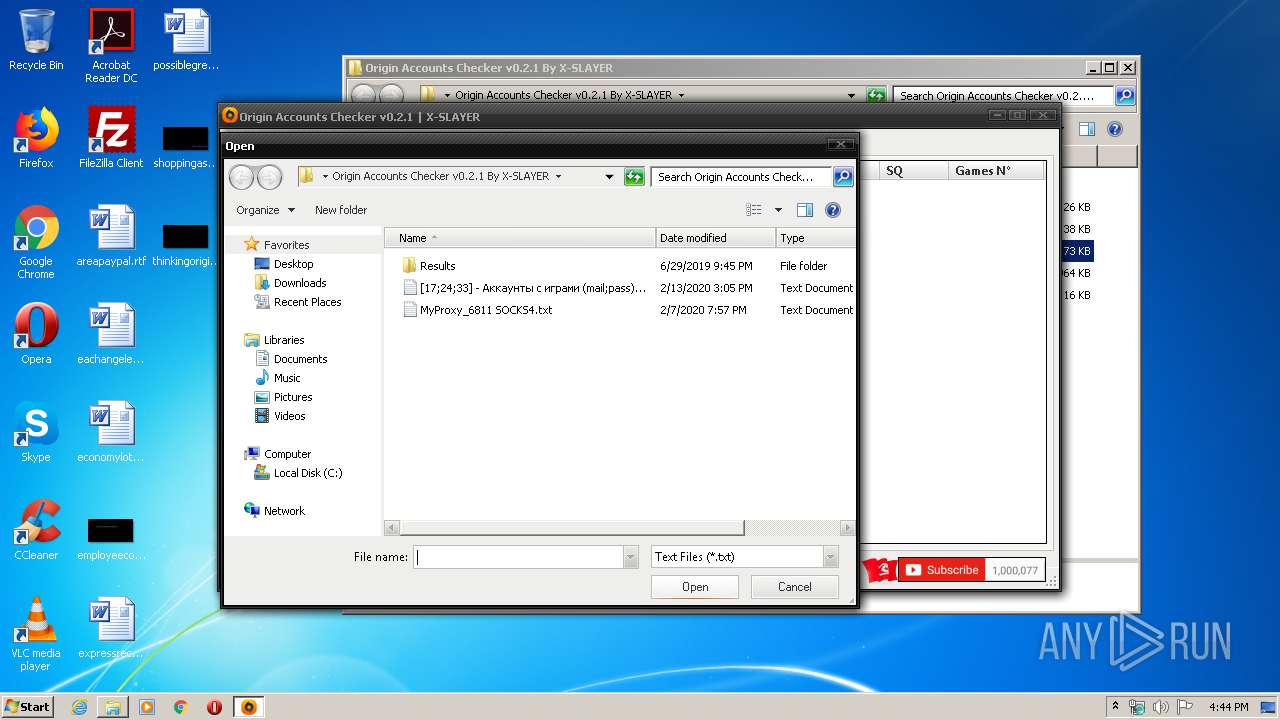
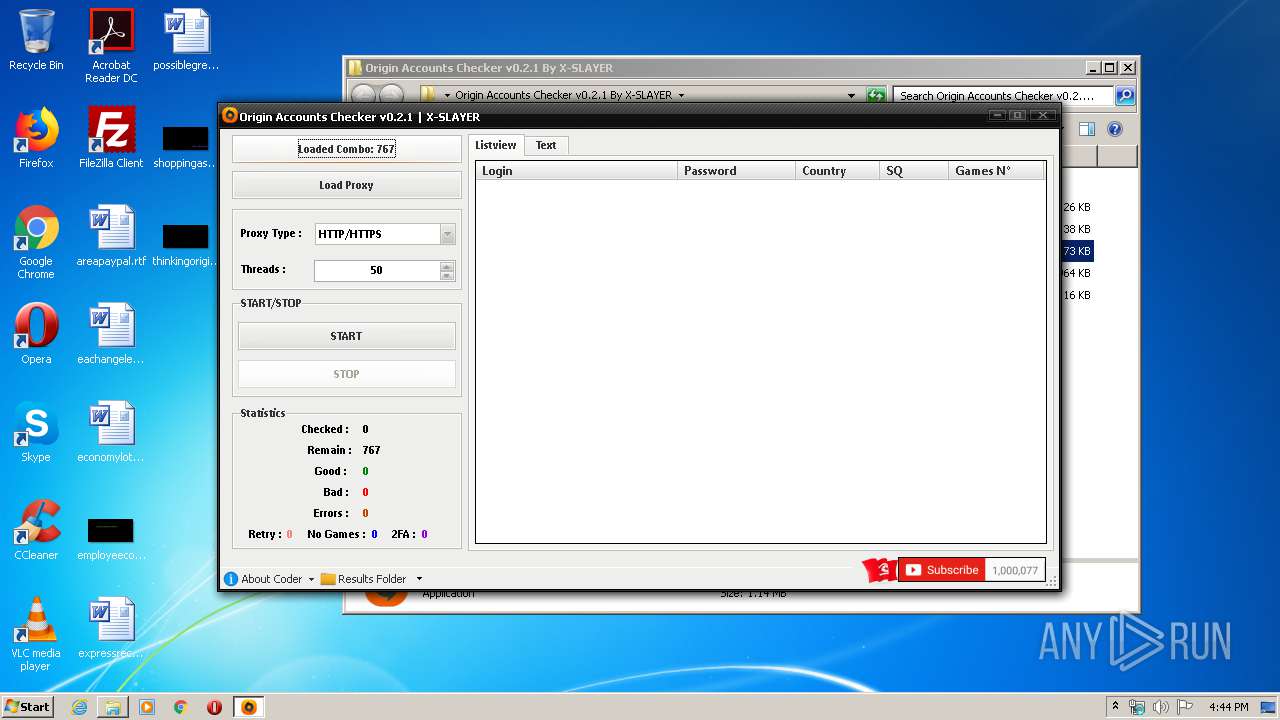
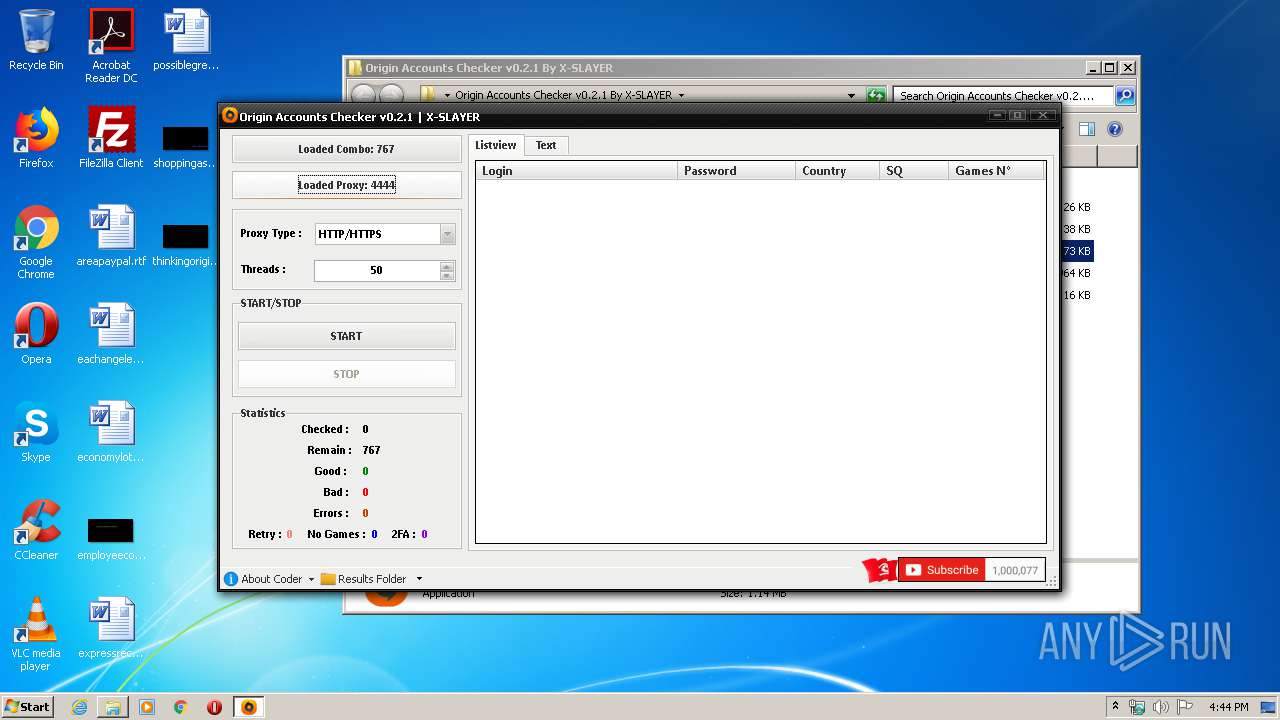
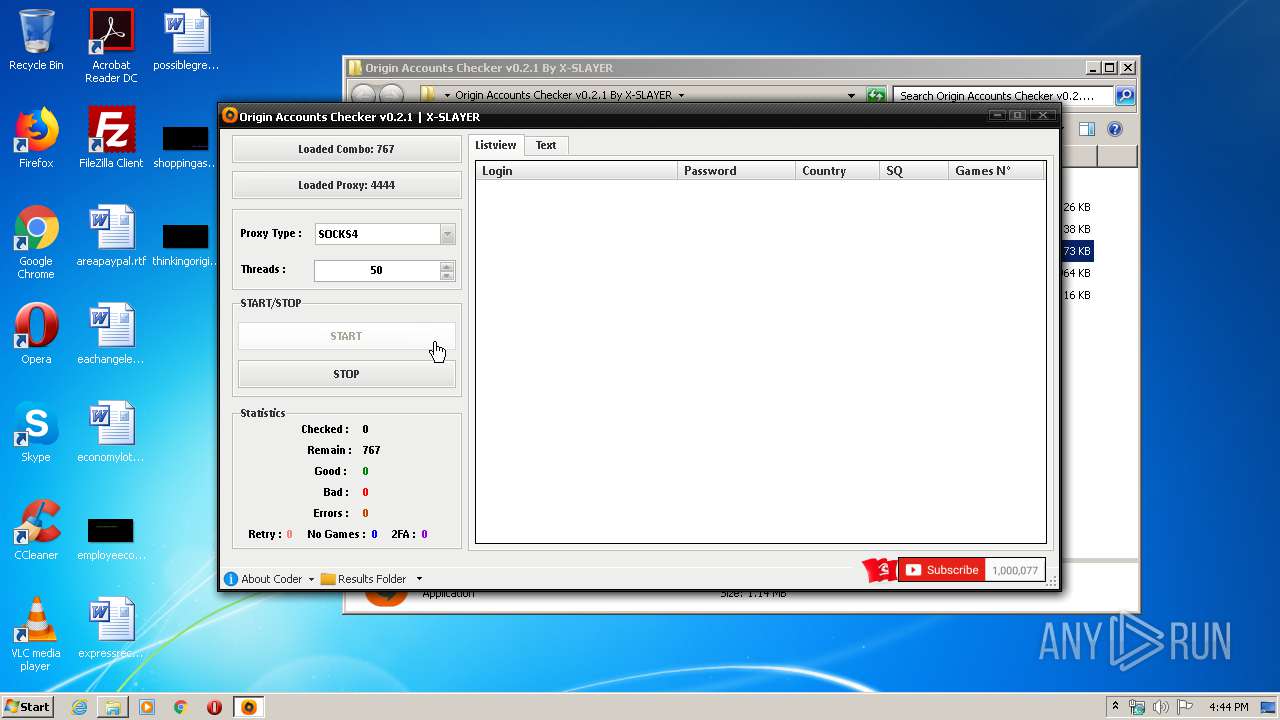
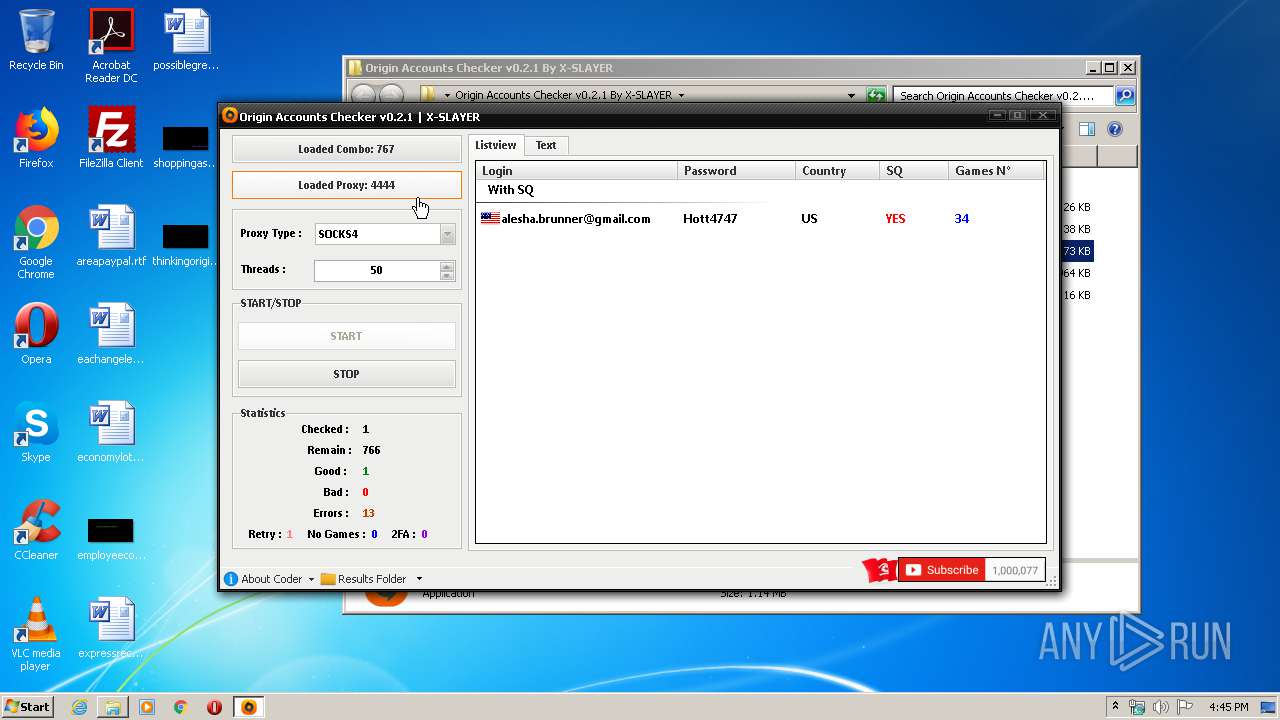
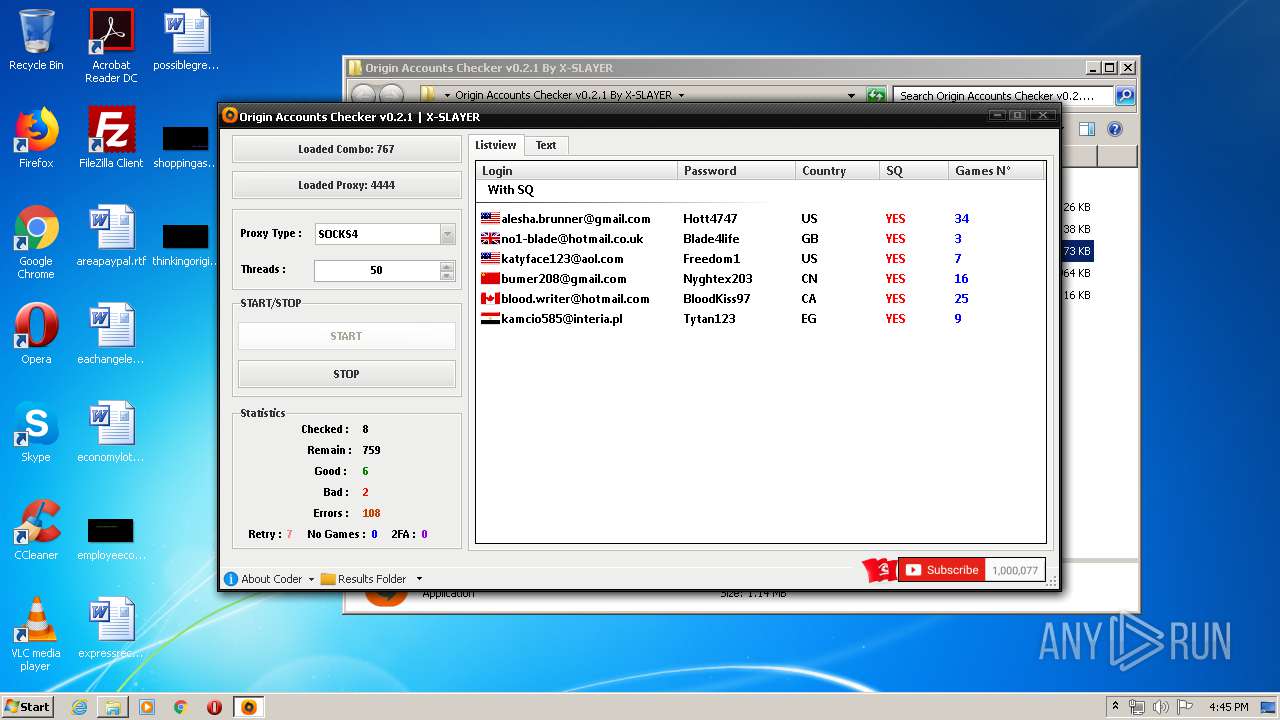
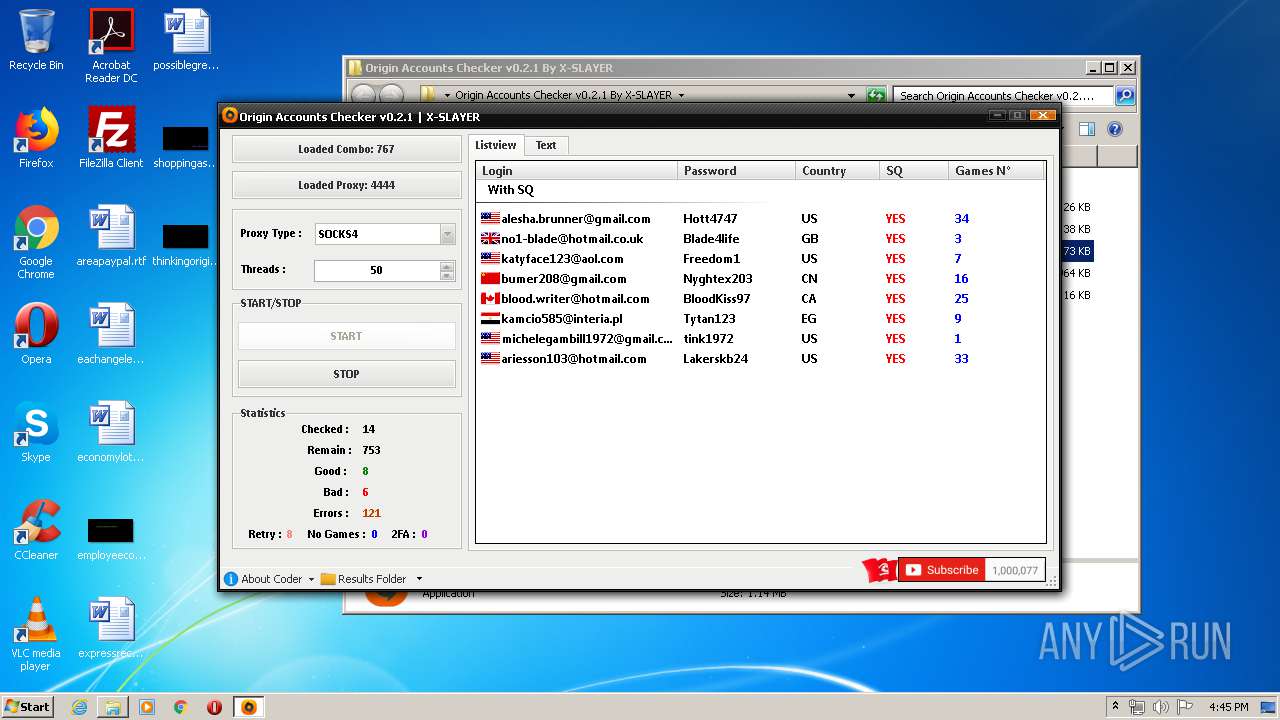
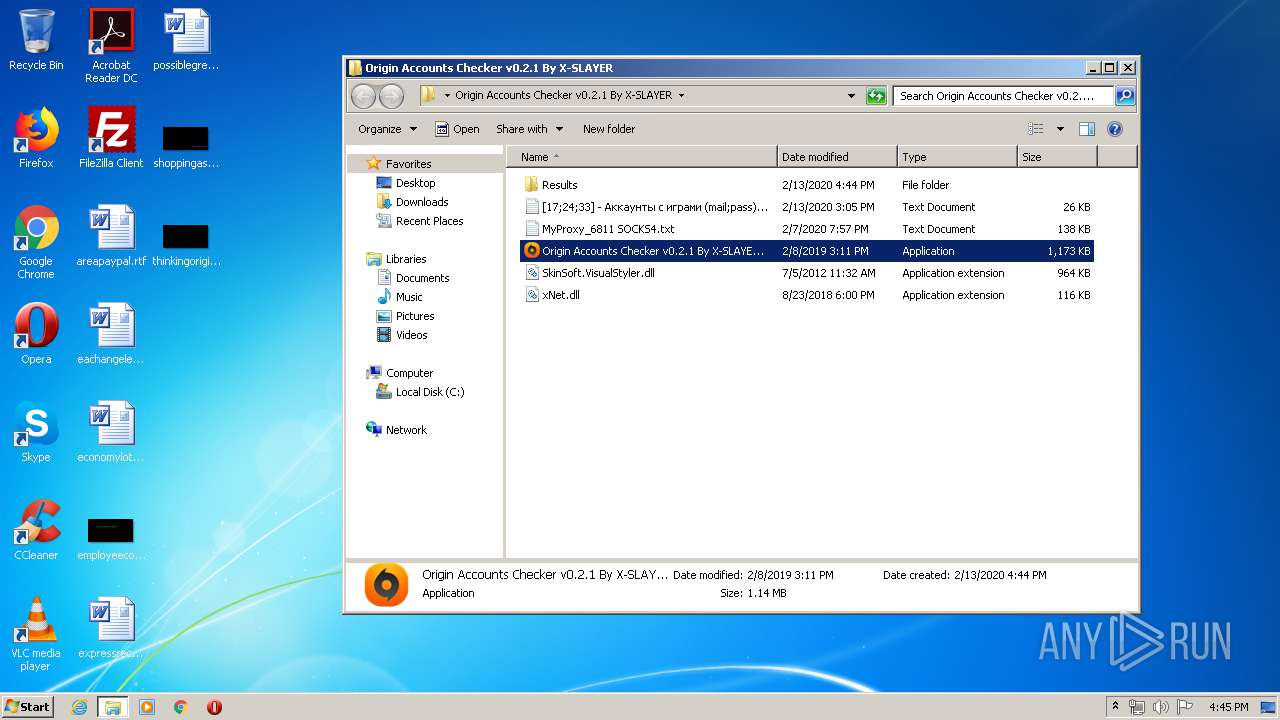
| File name: | Origin Accounts Checker v0.2.1 By X-SLAYER.rar |
| Full analysis: | https://app.any.run/tasks/e363f247-23ec-4d95-89a0-a4f52dd4faaf |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2020, 16:44:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1D08B03755072B02701B605B772DD298 |
| SHA1: | 088669D1D6AB46E3B1887964F84A7EEC7A4BFA2A |
| SHA256: | 0D1BB5D2EA32C22EF3C92B1D3C91B2CB1703FD7DCAFD7701C029ADCCCB7C5F98 |
| SSDEEP: | 24576:yaYRaXZxPFq9sbQSLT13bPCv+QL6cgWhXtio3onEXVgGtzbi3PxotV3M/mqUvHoD:FYeZksbQeT13bTShf4IJG/xotdXQ |
MALICIOUS
Loads dropped or rewritten executable
- Origin Accounts Checker v0.2.1 By X-SLAYER.exe (PID: 3560)
SUSPICIOUS
Executable content was dropped or overwritten
- Origin Accounts Checker v0.2.1 By X-SLAYER.exe (PID: 3560)
Reads Environment values
- Origin Accounts Checker v0.2.1 By X-SLAYER.exe (PID: 3560)
Connects to unusual port
- Origin Accounts Checker v0.2.1 By X-SLAYER.exe (PID: 3560)
INFO
Manual execution by user
- Origin Accounts Checker v0.2.1 By X-SLAYER.exe (PID: 3560)
Reads settings of System Certificates
- Origin Accounts Checker v0.2.1 By X-SLAYER.exe (PID: 3560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3540 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Origin Accounts Checker v0.2.1 By X-SLAYER.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3560 | "C:\Users\admin\Desktop\Origin Accounts Checker v0.2.1 By X-SLAYER\Origin Accounts Checker v0.2.1 By X-SLAYER.exe" | C:\Users\admin\Desktop\Origin Accounts Checker v0.2.1 By X-SLAYER\Origin Accounts Checker v0.2.1 By X-SLAYER.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Checker By X-SLAYER Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 076
Read events
973
Write events
99
Delete events
4
Modification events
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Origin Accounts Checker v0.2.1 By X-SLAYER.rar | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
1
Suspicious files
0
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3540.27296\Origin Accounts Checker v0.2.1 By X-SLAYER\Origin Accounts Checker v0.2.1 By X-SLAYER.exe | — | |
MD5:— | SHA256:— | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3540.27296\Origin Accounts Checker v0.2.1 By X-SLAYER\SkinSoft.VisualStyler.dll | — | |
MD5:— | SHA256:— | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3540.27296\Origin Accounts Checker v0.2.1 By X-SLAYER\xNet.dll | — | |
MD5:— | SHA256:— | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3540.27296\Origin Accounts Checker v0.2.1 By X-SLAYER\[17;24;33] - Аккаунты с играми (mail;pass).txt | — | |
MD5:— | SHA256:— | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3540.27296\Origin Accounts Checker v0.2.1 By X-SLAYER\MyProxy_6811 SOCKS4.txt | — | |
MD5:— | SHA256:— | |||
| 3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | C:\Users\admin\Desktop\Origin Accounts Checker v0.2.1 By X-SLAYER\Results\Result 13-02-20 16-44-53\Good.txt | text | |
MD5:— | SHA256:— | |||
| 3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | C:\Users\admin\Desktop\Origin Accounts Checker v0.2.1 By X-SLAYER\Results\Result 13-02-20 16-44-53\Bad.txt | text | |
MD5:— | SHA256:— | |||
| 3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | C:\Users\admin\AppData\Local\SkinSoft\VisualStyler\2.3.5.0\x86\ssapihook.dll | executable | |
MD5:D7F644C06B4CDE60651D02AED6B4174D | SHA256:A99EA2F5759B34859B484AFA3A58CE82A7F3BF792886A6C838DB852D517D9C0D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
455
DNS requests
12
Threats
366
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 1.20.100.227:52900 | — | TOT Public Company Limited | TH | suspicious |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 177.38.161.35:4145 | — | C2 TELECOM | BR | suspicious |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 86.57.167.132:4145 | — | Republican Unitary Telecommunication Enterprise Beltelecom | BY | suspicious |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 167.11.246.202:2199 | — | — | CA | unknown |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 195.128.118.44:4145 | — | Robert Jerzy Oplielinski trading as NETCOM COMPUTERS | PL | suspicious |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 201.62.54.156:4145 | — | Click Tecnologia e Telecomunicação Ltda | BR | suspicious |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 37.17.169.80:46768 | — | Szervernet Ltd | HU | suspicious |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 202.148.31.174:44611 | — | PT. Dutakom Wibawa Putra | ID | suspicious |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 31.209.104.197:4145 | — | Multimax Iletisim Limited | CY | suspicious |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | 43.252.158.21:49934 | — | PT Media Sarana Data | ID | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
signin.ea.com |
| whitelisted |
accounts.ea.com |
| unknown |
www.origin.com |
| suspicious |
myaccount.ea.com |
| unknown |
gateway.ea.com |
| unknown |
api2.origin.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |
3560 | Origin Accounts Checker v0.2.1 By X-SLAYER.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Socks4 Connection |