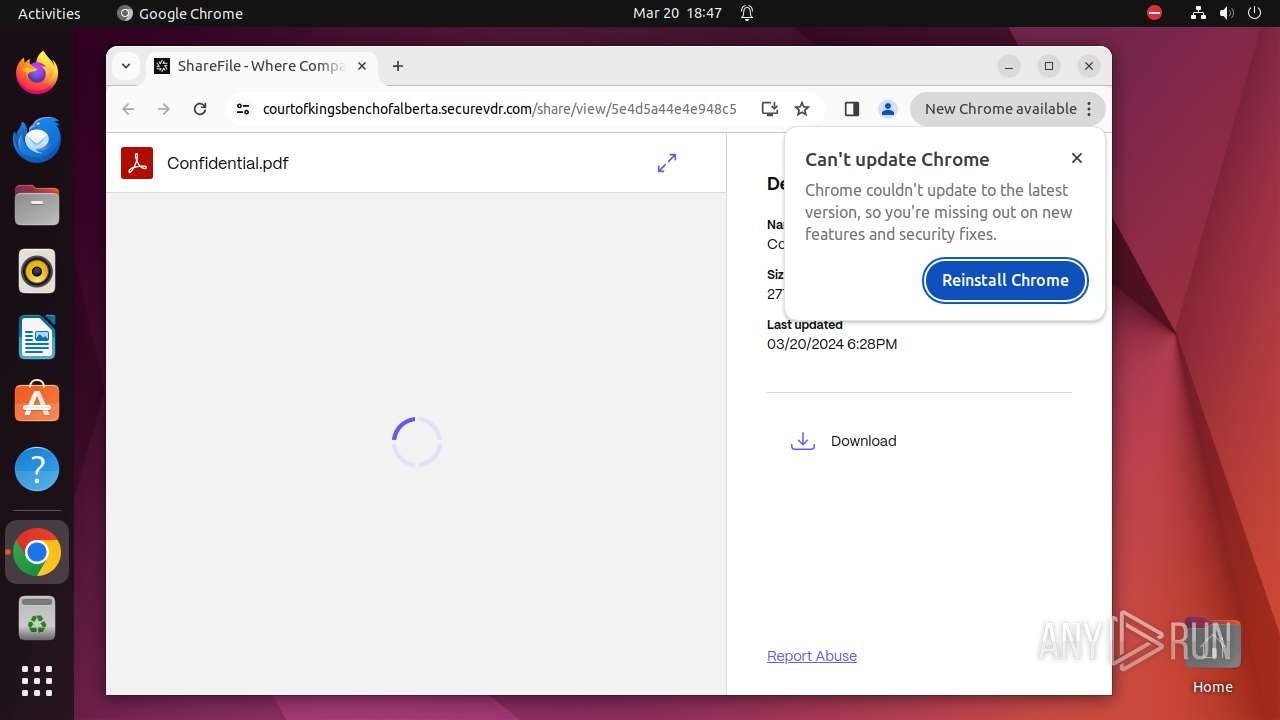
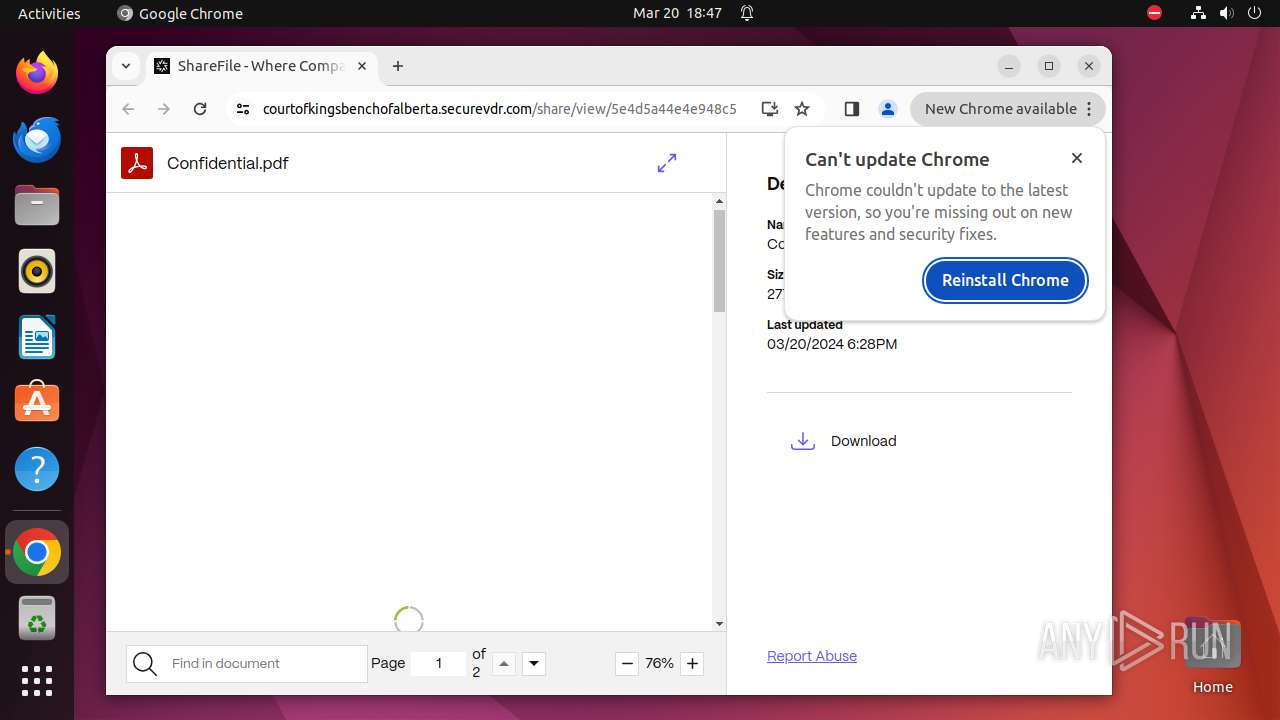
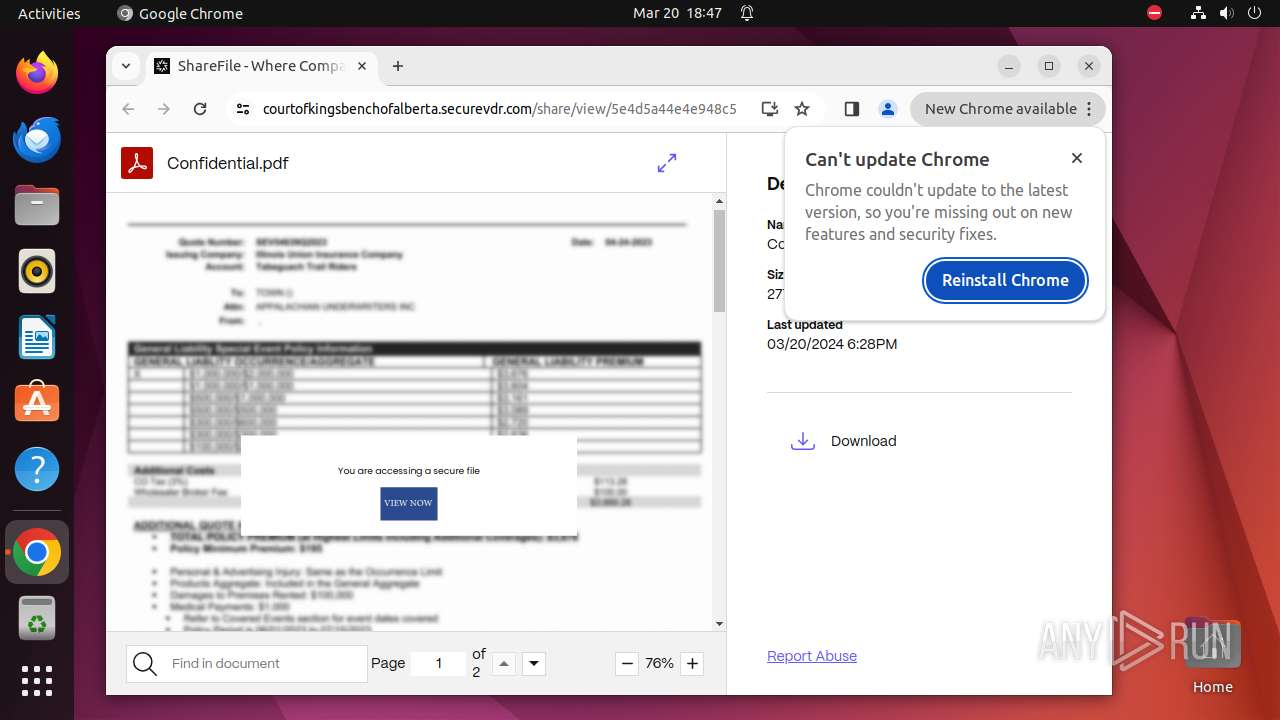
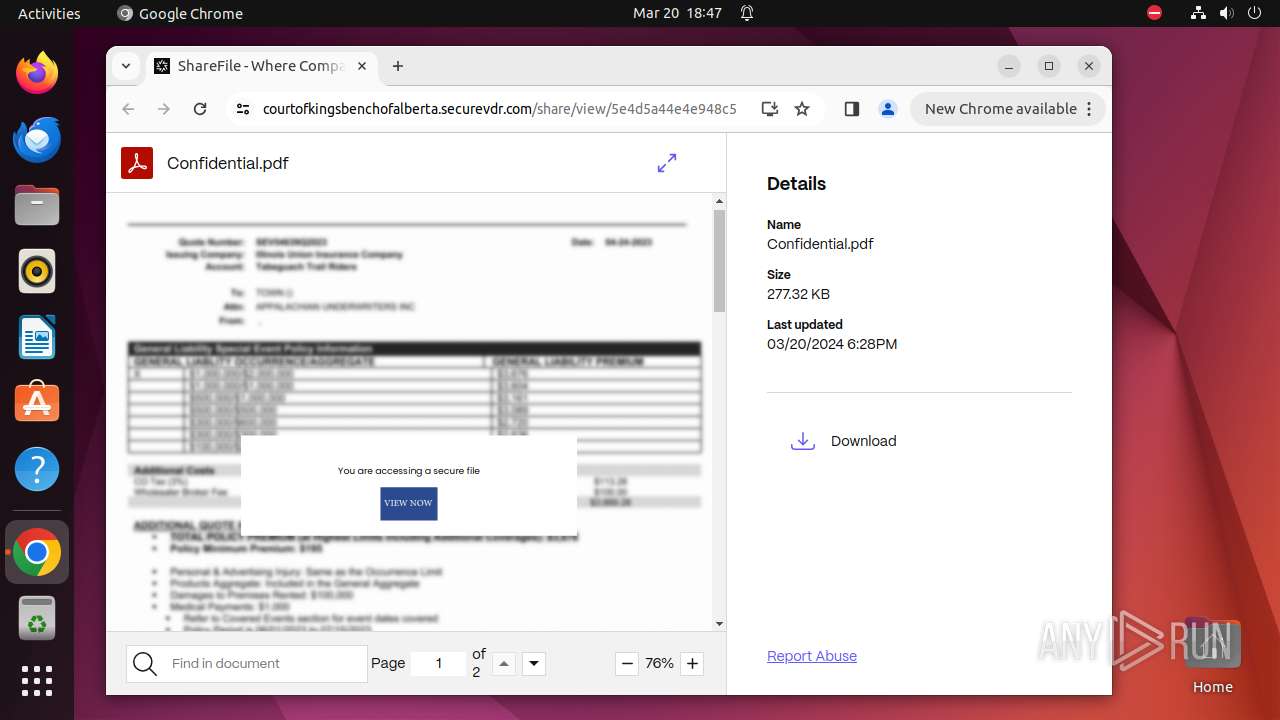
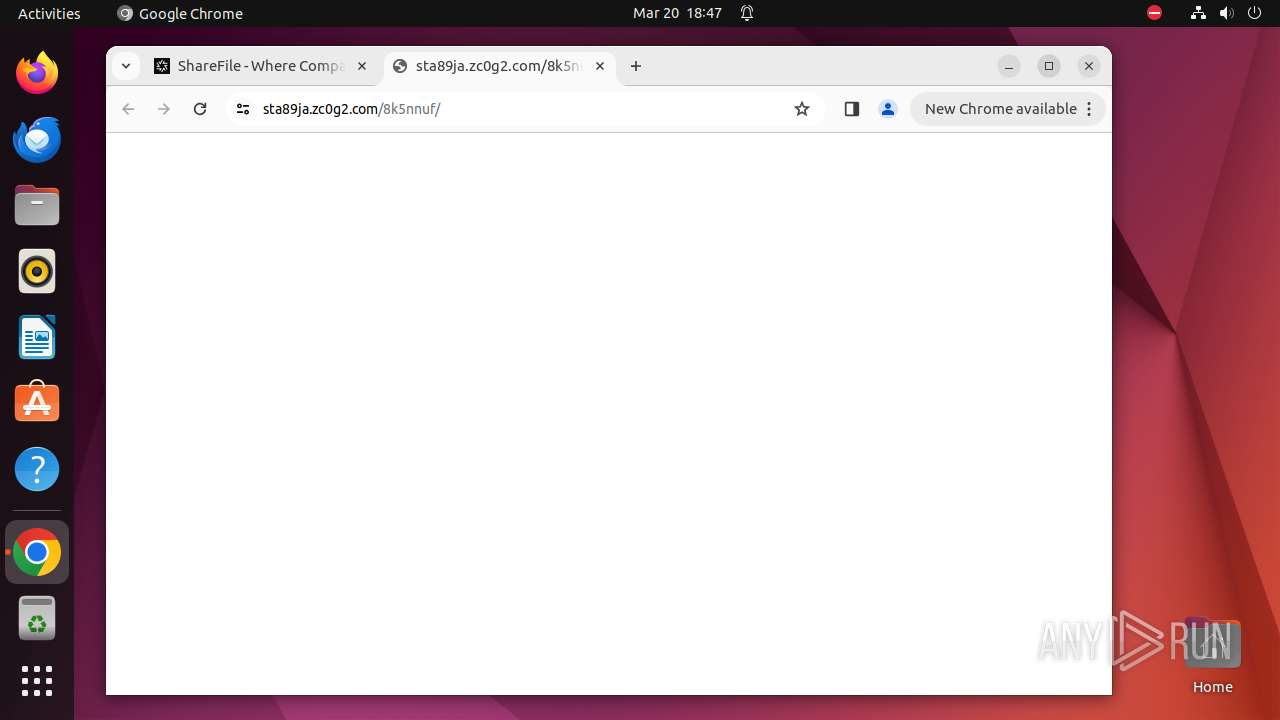
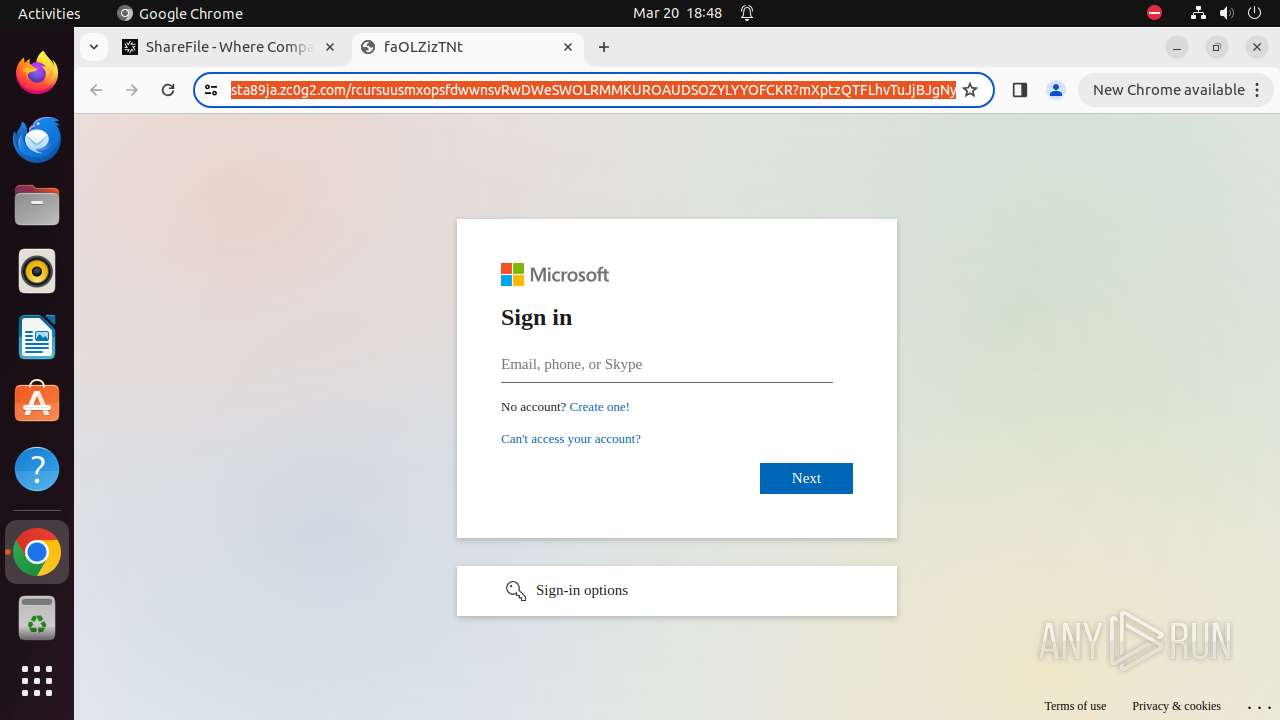
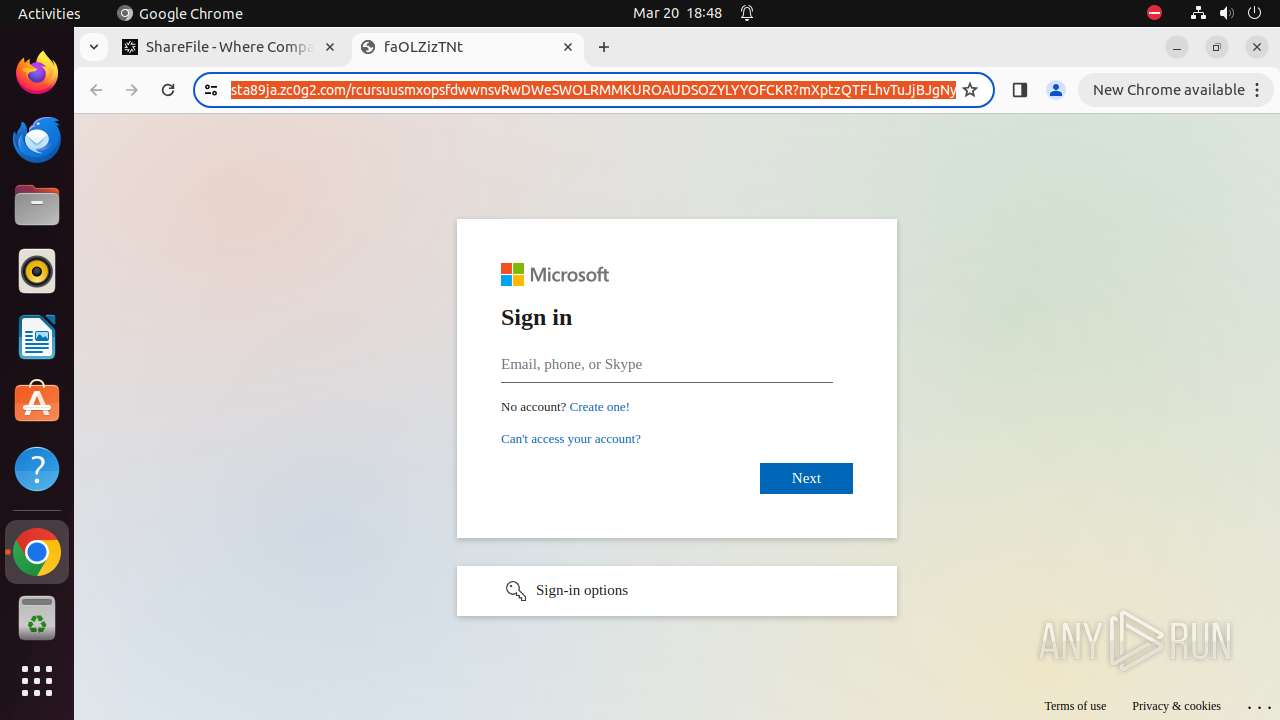
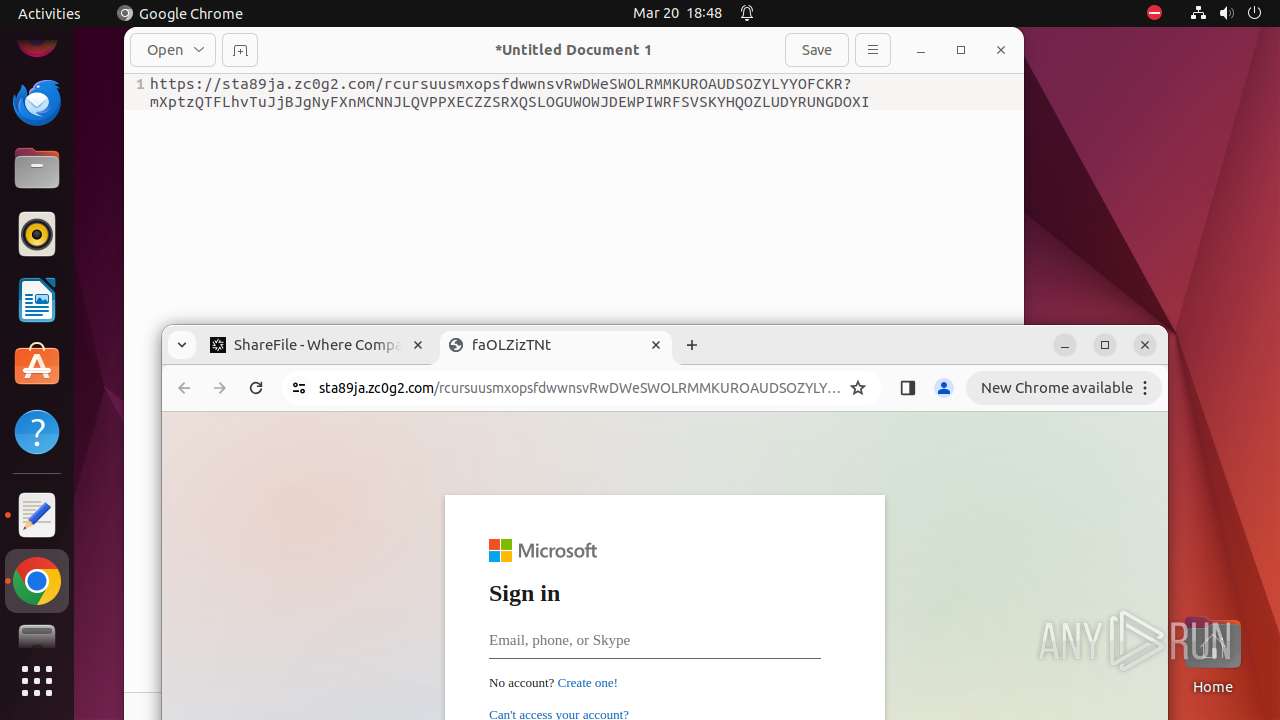
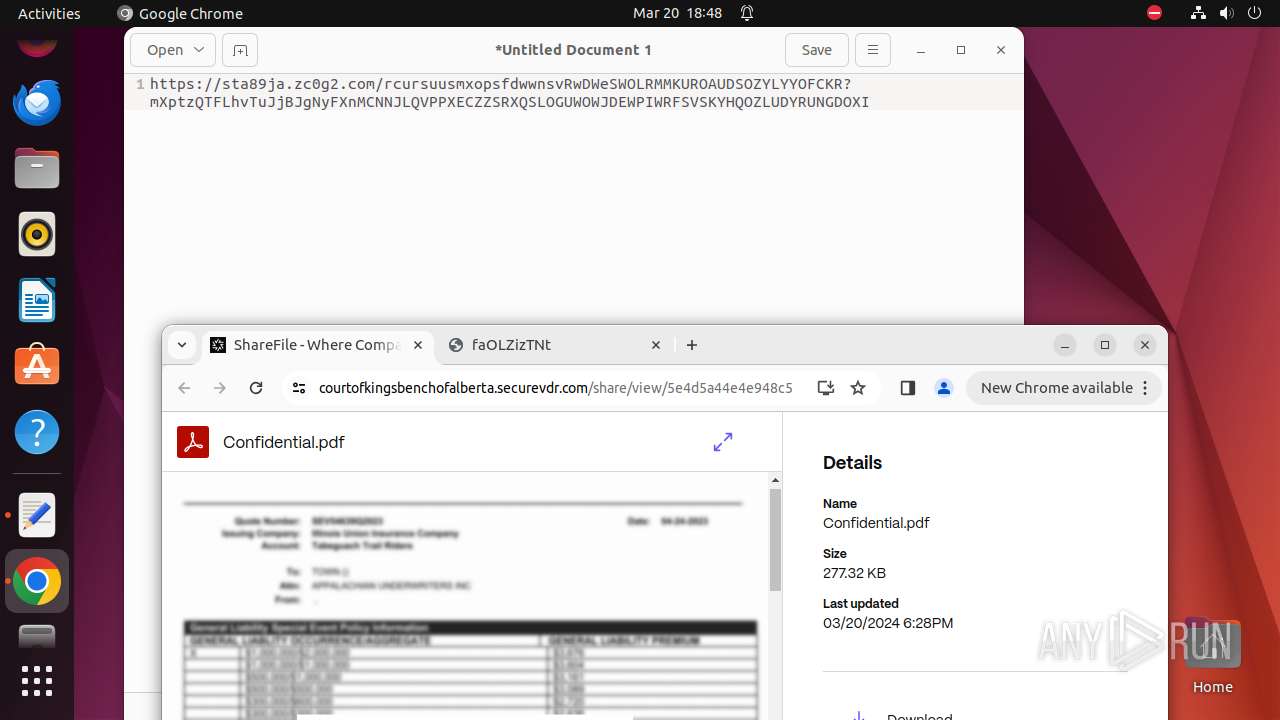
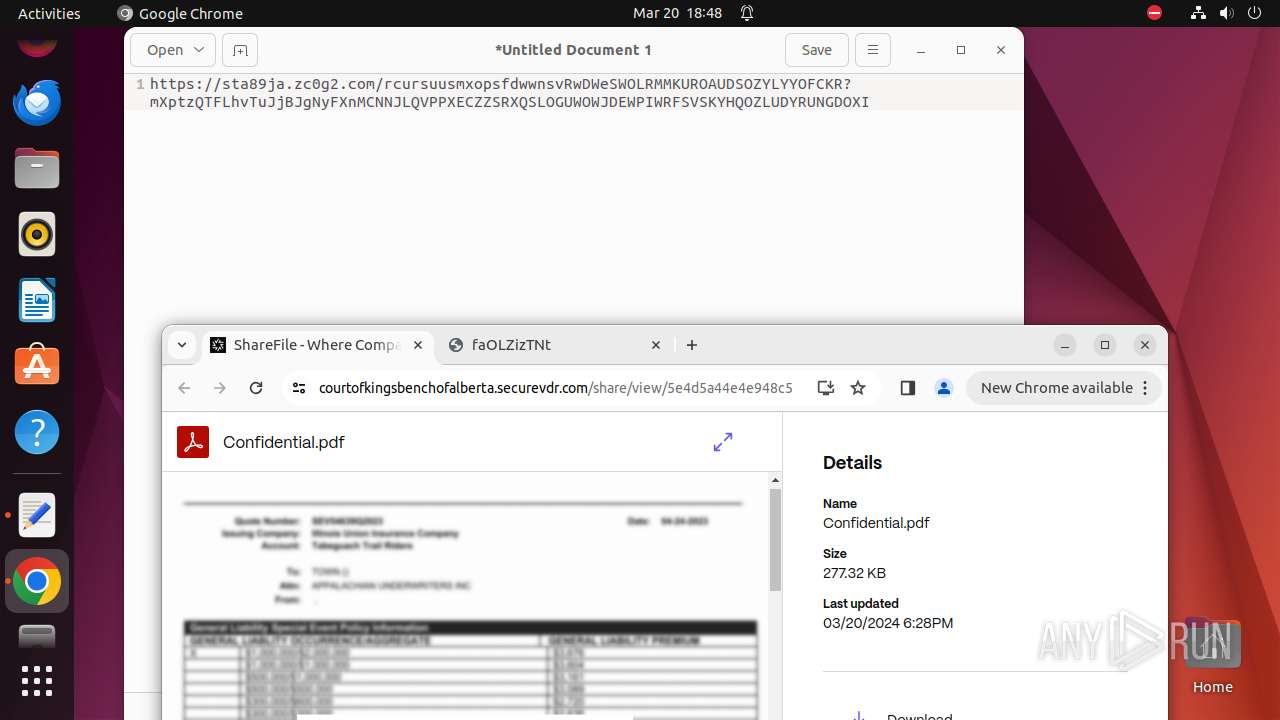
| URL: | courtofkingsbenchofalberta.securevdr.com/public/share/web-5e4d5a44e4e948c5 |
| Full analysis: | https://app.any.run/tasks/b6ff70fd-85fe-49c2-91d9-fa098253bcd6 |
| Verdict: | Malicious activity |
| Analysis date: | March 20, 2024, 18:47:08 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| MD5: | 73B7CDBE477BD77A07A86CC8B6386015 |
| SHA1: | 47C4D273B5E1F66789B8D0AB0959ED5D3A79A4BB |
| SHA256: | 0D131D3493AED3716F9196DE837A83C8A7F2A0AE4E3529B429DA9FEF1EC1F15C |
| SSDEEP: | 3:kR0NFmhLd36HJqkR0n:Y0NFmz6HJ9On |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
315
Monitored processes
94
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 9299 | /bin/sh -c "DISPLAY=:0 sudo -iu user google-chrome \"courtofkingsbenchofalberta\.securevdr\.com/public/share/web-5e4d5a44e4e948c5\" " | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9300 | sudo -iu user google-chrome courtofkingsbenchofalberta.securevdr.com/public/share/web-5e4d5a44e4e948c5 | /usr/bin/sudo | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9301 | /usr/bin/google-chrome courtofkingsbenchofalberta.securevdr.com/public/share/web-5e4d5a44e4e948c5 | /opt/google/chrome/chrome | — | sudo |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9302 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9303 | readlink -f /usr/bin/google-chrome | /usr/bin/readlink | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9304 | dirname /opt/google/chrome/google-chrome | /usr/bin/dirname | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9305 | mkdir -p /home/user/.local/share/applications | /usr/bin/mkdir | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9306 | cat | /usr/bin/cat | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9307 | cat | /usr/bin/cat | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9308 | /opt/google/chrome/chrome | — | chrome | |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 9301 | chrome | /9301/fd/63 | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /home/user/.config/google-chrome/BrowserMetrics/BrowserMetrics-65FB2F34-2455.pma | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /.com.google.Chrome.SKAuSv | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /.com.google.Chrome.s4OrWp | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /home/user/.config/google-chrome/Default/Session Storage/LOG | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /home/user/.config/google-chrome/Default/shared_proto_db/metadata/LOG | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /home/user/.config/google-chrome/Default/shared_proto_db/LOG | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /home/user/.config/google-chrome/WidevineCdm/.com.google.Chrome.Fw2t9j | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /.com.google.Chrome.YSbFAU | — | |
MD5:— | SHA256:— | |||
| 9301 | chrome | /.com.google.Chrome.HDriK5 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
72
DNS requests
84
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/lmelglejhemejginpboagddgdfbepgmp/1.0e9dd6d00d587e379d8ee83954d38f0b17b61c223fe18349ffaaa1d76213ee59/1.1c9ef13b7a63abd8f89d0cbad98858b9e8f54fc3951160950403c72b45812d07/f8225ba46f227b089d6c72ecd2eb5ef28e91fc79cbe9e611d5e0fd8087119cfc.puff | unknown | binary | 2.29 Kb | unknown |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adpcjrerslcdrrpka6hp6nr5j2la_2024.3.18.0/niikhdgajlphfehepabhhblakbdgeefj_2024.03.18.00_all_acsvmgenbc66wqntywry4z4w4bca.crx3 | unknown | binary | 5.91 Kb | unknown |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/cq5haj3i3yskoyvh2ofhzbtywe_8608/hfnkpimlhhgieaddgfemjhofmfblmnib_8608_all_ac57jefoze7eizrd3uyu34qyviia.crx3 | unknown | binary | 25.9 Kb | unknown |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | binary | 3.07 Kb | unknown |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/efniojlnjndmcbiieegkicadnoecjjef/1.81edfe5c9bcd5c93a7431df1cf92255bb705c56adeb8c1167fc2571494b02794/1.6fcc02a365d39485c49c9da8679a9fd979832315b2d47ff7f0ab395b10e303bd/e9b2d40c051400dde730a4513c31c6d190deb9bbab06617af1a35a2f80e79aa3.puff | unknown | binary | 22.2 Kb | unknown |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/jflookgnkcckhobaglndicnbbgbonegd/1.c7f445d90541e46806f932c860cf78e900b7949c56ccb45c53681b7dfc9270a7/1.ab8da5b849ba36382f26992fe1b52d72aa457549f31246a0c386d6880fca8afc/30b8ef13d7a852a769e41fddfbce995cfbf508643a3b68249eaf8cda4232245b.puff | unknown | binary | 51.9 Kb | unknown |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/knnjrc2u2hzvqcpzumoy6ct22u_2024.3.19.1/jflhchccmppkfebkiaminageehmchikm_2024.03.19.01_all_pes2ce37uzhjrmuog4ilbbxphy.crx3 | unknown | binary | 9.10 Kb | unknown |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad4yknbrdmxnjphevalkpmskvcsq_2024.3.13.0/gonpemdgkjcecdgbnaabipppbmgfggbe_2024.03.13.00_all_ack2pxafcv3s2bkxcbzzqpvqownq.crx3 | unknown | binary | 6.45 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 156.146.33.140:443 | — | Datacamp Limited | DE | unknown |
— | — | 216.58.206.67:443 | clientservices.googleapis.com | GOOGLE | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 173.194.79.84:443 | accounts.google.com | GOOGLE | US | unknown |
— | — | 76.223.1.166:80 | courtofkingsbenchofalberta.securevdr.com | AMAZON-02 | US | unknown |
— | — | 76.223.1.166:443 | courtofkingsbenchofalberta.securevdr.com | AMAZON-02 | US | unknown |
— | — | 13.32.121.91:443 | 0093b71e39a6.us-east-1.sdk.awswaf.com | AMAZON-02 | US | unknown |
— | — | 18.173.205.42:443 | 0093b71e39a6.11de9b12.us-east-1.token.awswaf.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.snapcraft.io |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
courtofkingsbenchofalberta.securevdr.com |
| unknown |
0093b71e39a6.us-east-1.sdk.awswaf.com |
| unknown |
0093b71e39a6.11de9b12.us-east-1.token.awswaf.com |
| unknown |
app.launchdarkly.com |
| shared |
c3.shared.global.fastly.net |
| unknown |
courtofkingsbenchofalberta.sf-api.com |
| unknown |
citrix-sharefile-content.customer.pendo.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO External File Sharing Service in DNS Lookup (sharefile .com) |
— | — | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
— | — | Misc activity | ET INFO External File Sharing Service in DNS Lookup (sharefile .com) |
— | — | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
— | — | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
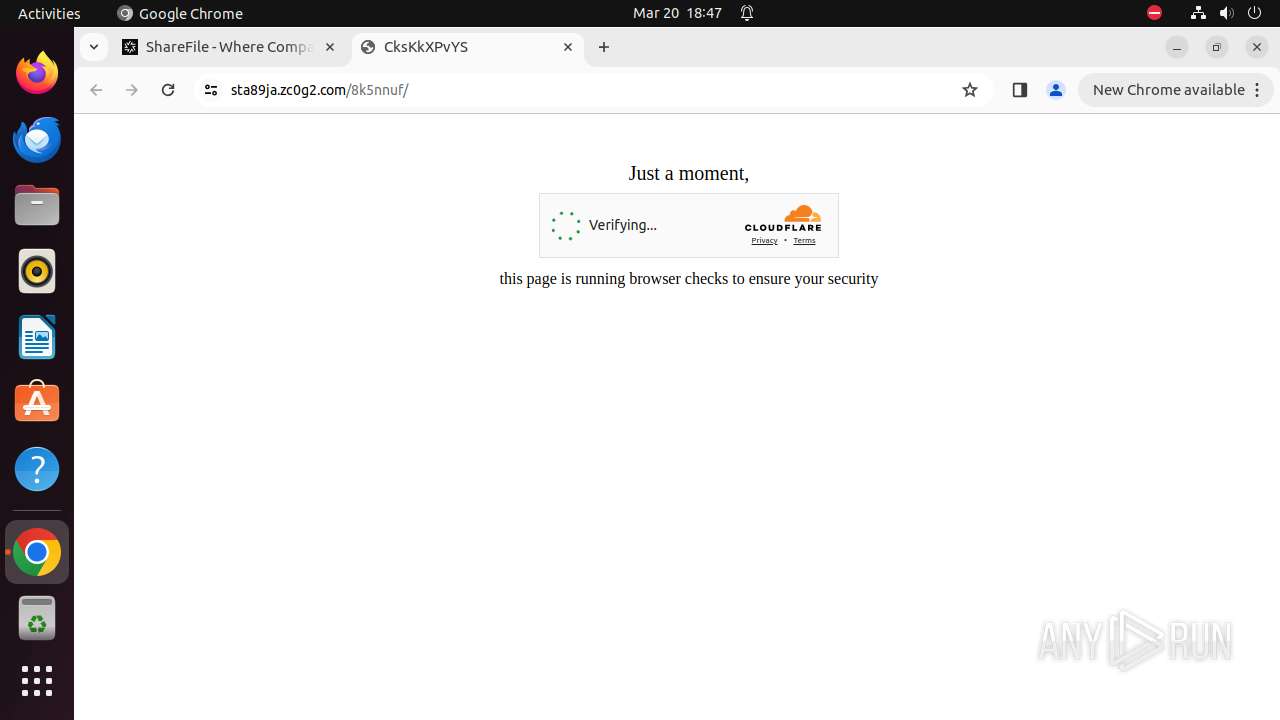
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
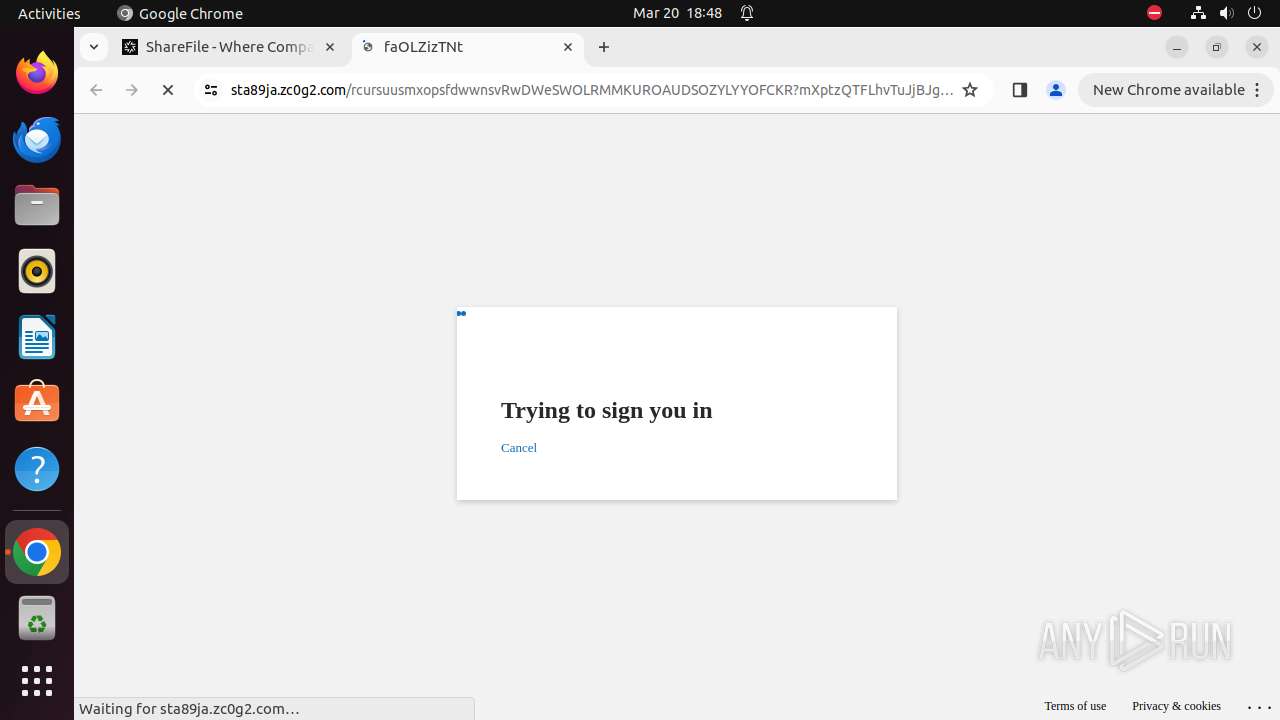
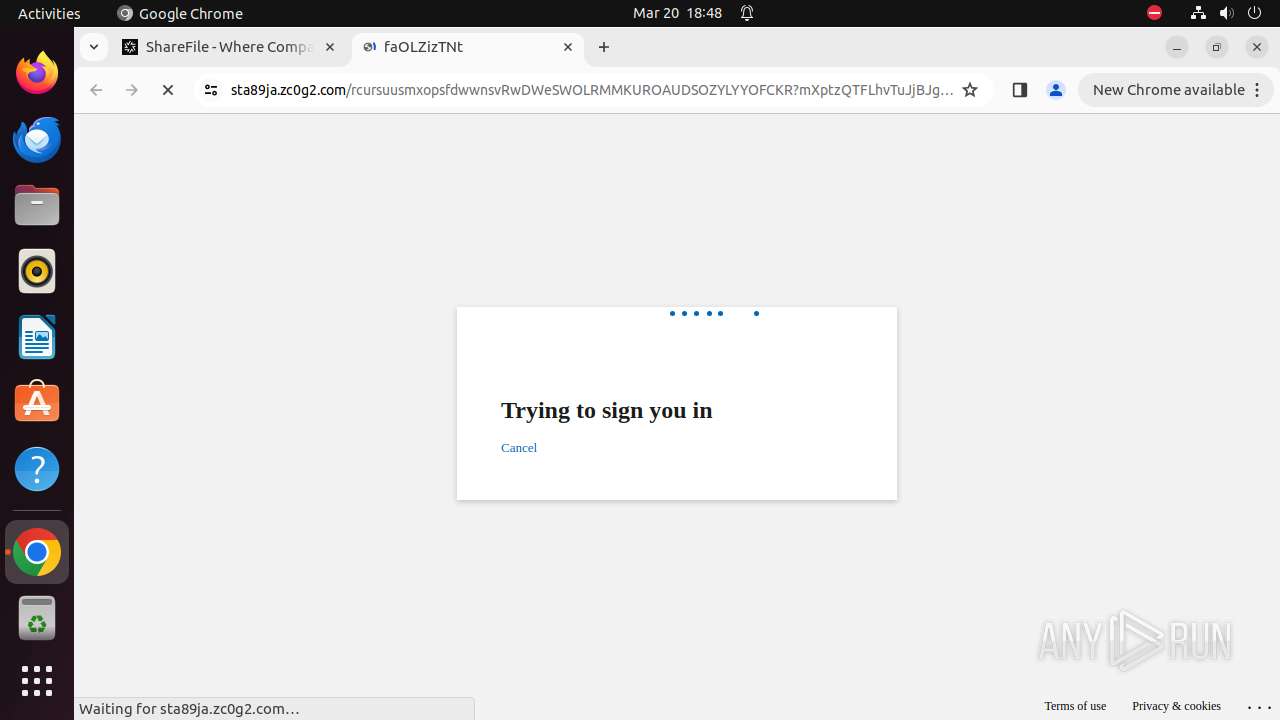
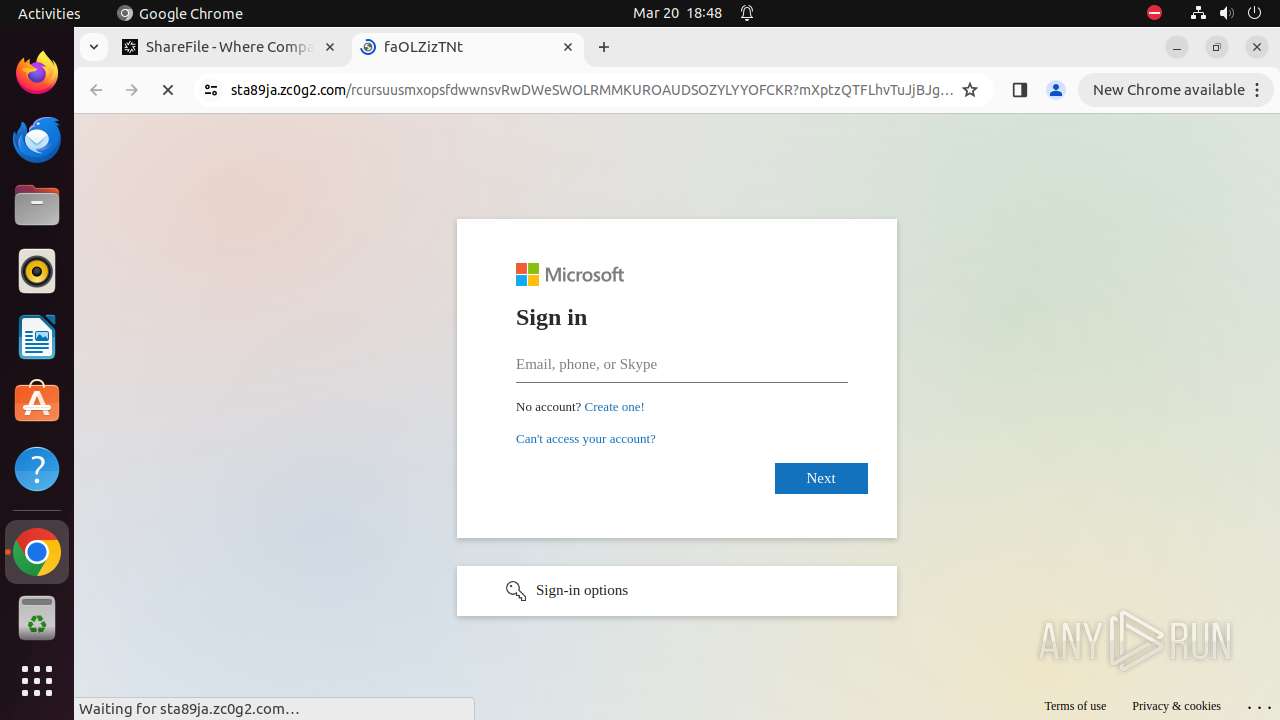
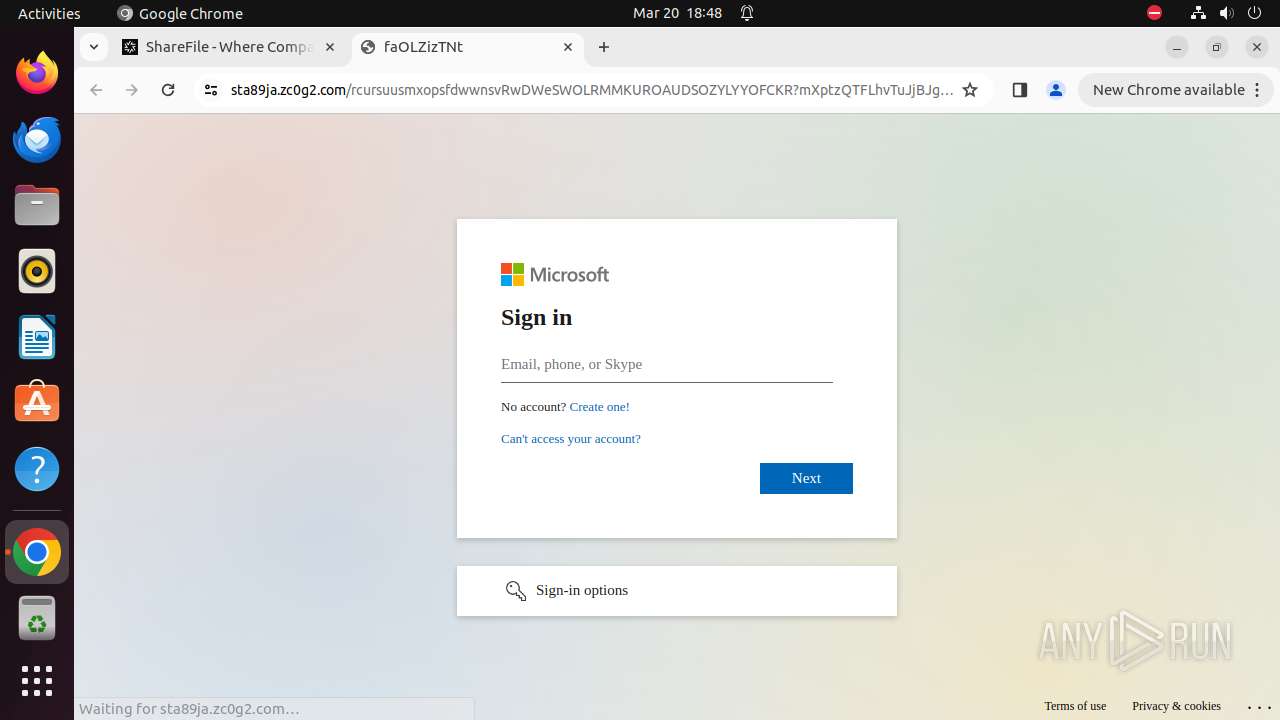
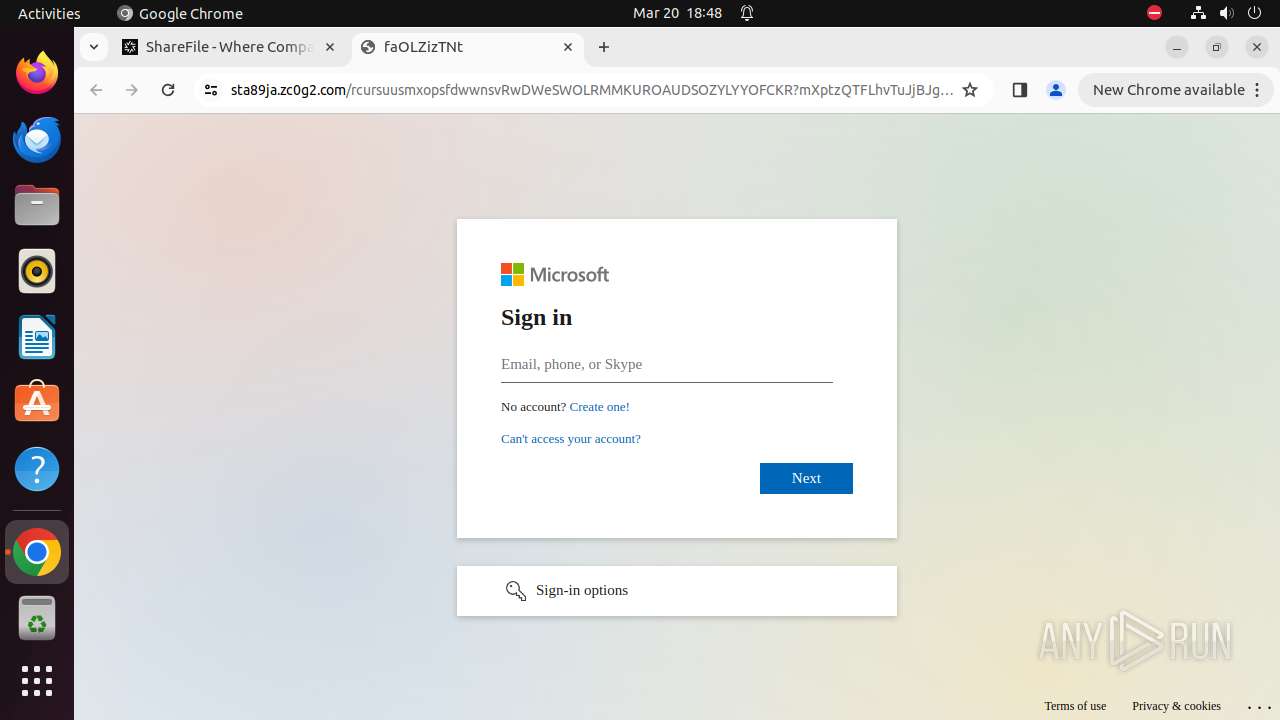
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain chain detected (Tycoon 2FA) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Client-Server Socket.IO CDN communication (cdn.socket .io) |