| File name: | GB 36893-2018.pdf |
| Full analysis: | https://app.any.run/tasks/449f3698-a329-4057-9933-a5451bd229c8 |
| Verdict: | Malicious activity |
| Analysis date: | April 09, 2021, 20:18:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.7 |
| MD5: | ED4374C9F9A525619ADA0DA2F3B710E8 |
| SHA1: | 75E03BD2E49D9ED0D984FB1BABA23861524A6405 |
| SHA256: | 0D01D3AD00E22940316158C9B12DBAEA930902E8F6801E18161D726C89E2FB81 |
| SSDEEP: | 12288:U1IOADVdTvKO11GgK0IQDDhComGgcIeWIthBhFxnOBIFXNHlnsGTr/:QALT0Qh9gcIerFxOKXNhTr/ |
MALICIOUS
Application was dropped or rewritten from another process
- FileOpenManager32.exe (PID: 1320)
- FileOpenBroker32.exe (PID: 1476)
SUSPICIOUS
Executed as Windows Service
- vssvc.exe (PID: 1484)
- FileOpenManager32.exe (PID: 1320)
Starts Internet Explorer
- AcroRd32.exe (PID: 1692)
Creates files in the program directory
- AdobeARM.exe (PID: 2888)
Starts Microsoft Installer
- iexplore.exe (PID: 1684)
Drops a file with a compile date too recent
- msiexec.exe (PID: 2672)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2672)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 2672)
Creates or modifies windows services
- FileOpenManager32.exe (PID: 1320)
Creates a directory in Program Files
- msiexec.exe (PID: 2672)
Creates files in the user directory
- msiexec.exe (PID: 2672)
Changes the autorun value in the registry
- msiexec.exe (PID: 2672)
INFO
Application launched itself
- AcroRd32.exe (PID: 1692)
- iexplore.exe (PID: 1684)
- RdrCEF.exe (PID: 1884)
- msiexec.exe (PID: 2672)
Changes internet zones settings
- iexplore.exe (PID: 1684)
Reads the hosts file
- RdrCEF.exe (PID: 1884)
Reads settings of System Certificates
- iexplore.exe (PID: 3380)
- AcroRd32.exe (PID: 1692)
- iexplore.exe (PID: 1684)
- AdobeARM.exe (PID: 2888)
Creates files in the user directory
- iexplore.exe (PID: 3380)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1684)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1684)
Reads internet explorer settings
- iexplore.exe (PID: 3380)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 1692)
Changes settings of System certificates
- iexplore.exe (PID: 1684)
Low-level read access rights to disk partition
- vssvc.exe (PID: 1484)
Creates files in the program directory
- msiexec.exe (PID: 2672)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 2672)
Creates a software uninstall entry
- msiexec.exe (PID: 2672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| Encryption: | FOPN_foweb V2 |
|---|---|
| Linearized: | No |
| PDFVersion: | 1.7 |
Total processes
50
Monitored processes
14
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
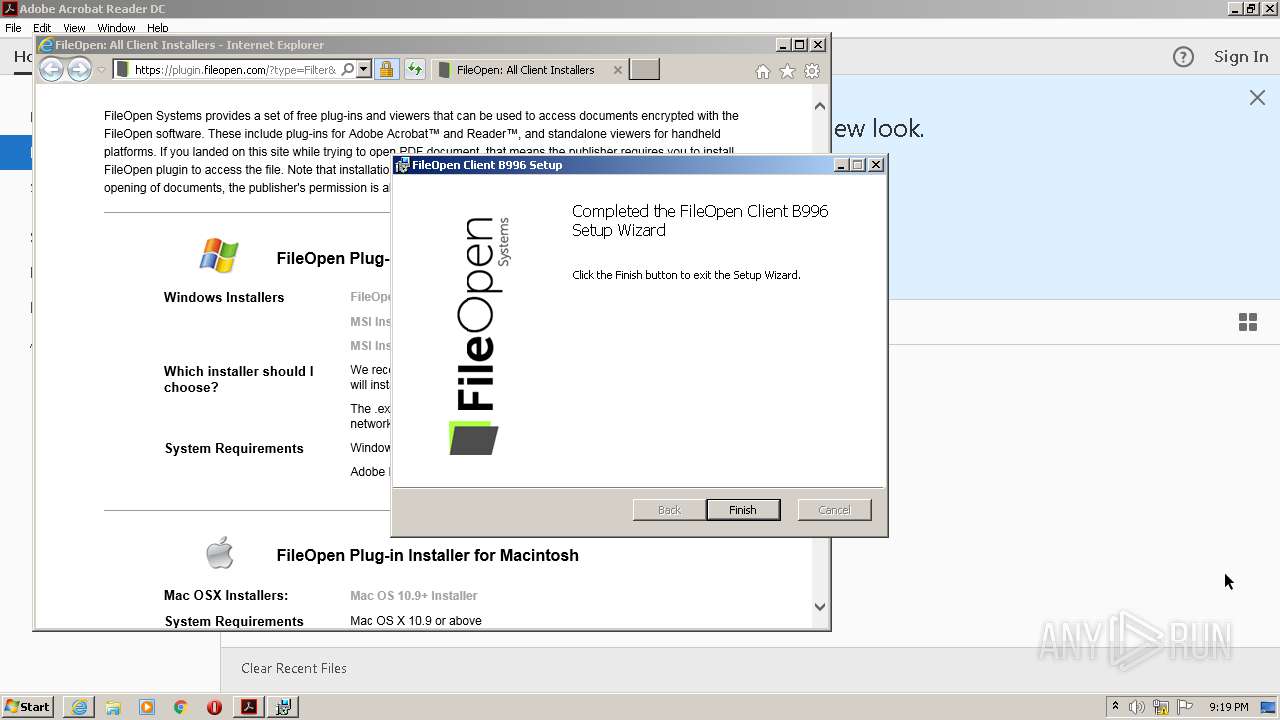
| 1320 | "C:\Program Files\FileOpen\Services\FileOpenManager32.exe" | C:\Program Files\FileOpen\Services\FileOpenManager32.exe | — | services.exe | |||||||||||
User: SYSTEM Company: FileOpen Systems Inc. Integrity Level: SYSTEM Description: FileOpen Client - Manager Service Exit code: 0 Version: 21.03.31.02 Modules
| |||||||||||||||
| 1476 | "C:\Program Files\FileOpen\Services\FileOpenBroker32.exe" | C:\Program Files\FileOpen\Services\FileOpenBroker32.exe | — | msiexec.exe | |||||||||||
User: admin Company: FileOpen Systems Inc. Integrity Level: MEDIUM Description: FileOpen Client - Broker Exit code: 0 Version: 21.03.31.02 Modules
| |||||||||||||||
| 1484 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1684 | "C:\Program Files\Internet Explorer\iexplore.exe" http://cgi1.adobe.com/special/acrobat/pluginfinder/pluginfinder.cgi?type=Filter&name=FOPN_foweb&os=Win&vers=15.0& | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1692 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\GB 36893-2018.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
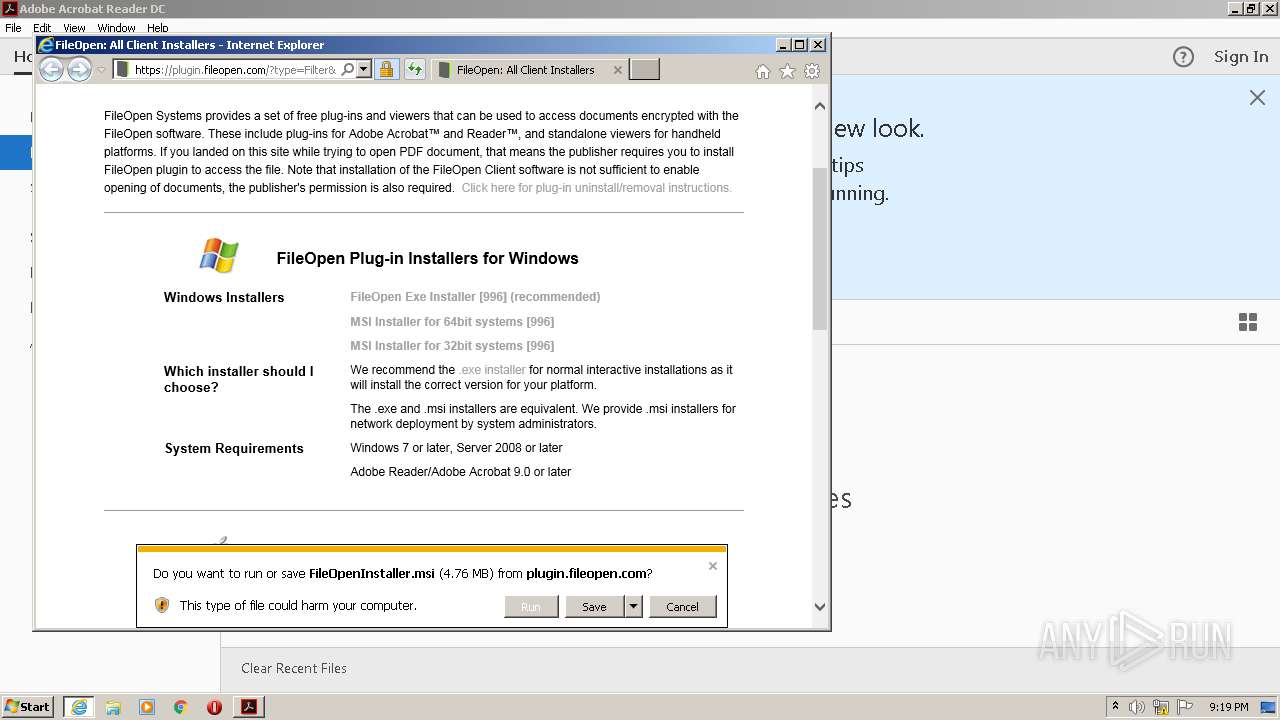
| 2416 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\FileOpenInstaller.msi" | C:\Windows\System32\msiexec.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2536 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="1884.0.195018946\1891313637" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2604 | C:\Windows\system32\MsiExec.exe -Embedding C9DCCF2427E95698C8A13CA72927F5C1 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 164
Read events
1 727
Write events
418
Delete events
19
Modification events
| (PID) Process: | (3080) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (1692) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {17FE9752-0B5A-4665-84CD-569794602F5C} {7F9185B0-CB92-43C5-80A9-92277A4F7B54} 0xFFFF |
Value: 0100000000000000250D9E987D2DD701 | |||
| (PID) Process: | (1684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2861588635 | |||
| (PID) Process: | (1684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30879101 | |||
| (PID) Process: | (1684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
7
Suspicious files
26
Text files
59
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3080 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3380 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9A.tmp | — | |
MD5:— | SHA256:— | |||
| 3380 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9B.tmp | — | |
MD5:— | SHA256:— | |||
| 3380 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\64YVC3D1.txt | — | |
MD5:— | SHA256:— | |||
| 3080 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\AdobeFnt16.lst.3080 | — | |
MD5:— | SHA256:— | |||
| 3080 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt16.lst.3080 | — | |
MD5:— | SHA256:— | |||
| 3380 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1NA43LXN.txt | text | |
MD5:— | SHA256:— | |||
| 3380 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3080 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages | sqlite | |
MD5:— | SHA256:— | |||
| 1692 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt15.lst | ps | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
39
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
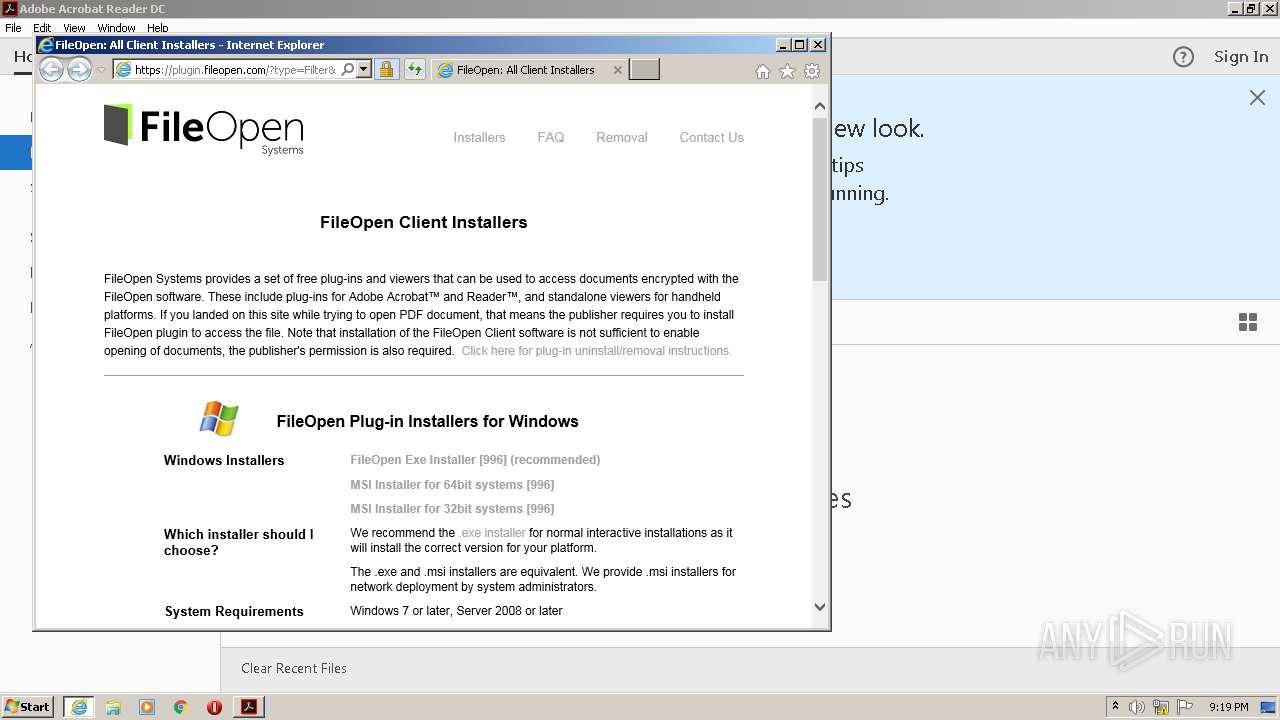
3380 | iexplore.exe | GET | 301 | 199.60.103.2:80 | http://www.fileopen.com/getplugin.asp?type=Filter&name=FOPN_foweb | CA | — | — | suspicious |
1692 | AcroRd32.exe | GET | 304 | 2.18.213.185:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
3380 | iexplore.exe | GET | 200 | 2.22.118.163:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | GB | der | 1.16 Kb | whitelisted |
3380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
1692 | AcroRd32.exe | GET | 304 | 2.18.213.185:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
1692 | AcroRd32.exe | GET | 304 | 2.18.213.185:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/279_15_23_20070.zip | unknown | — | — | whitelisted |
3380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3380 | iexplore.exe | GET | 200 | 172.217.23.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3380 | iexplore.exe | GET | 200 | 172.217.23.35:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEBvy7wrBJoLFAwAAAADLz1Y%3D | US | der | 471 b | whitelisted |
3380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 23.35.228.137:443 | armmf.adobe.com | Zayo Bandwidth Inc | US | suspicious |
— | — | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3380 | iexplore.exe | 2.22.118.137:443 | www.adobe.com | Akamai International B.V. | GB | unknown |
3380 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 199.60.103.2:80 | www.fileopen.com | — | CA | suspicious |
3380 | iexplore.exe | 199.60.103.2:443 | www.fileopen.com | — | CA | suspicious |
3380 | iexplore.exe | 64.106.211.88:80 | plugin.fileopen.com | DataPipe, Inc. | US | unknown |
3380 | iexplore.exe | 172.217.23.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
— | — | 193.104.215.58:80 | cgi1.adobe.com | Level 3 Communications, Inc. | — | malicious |
3380 | iexplore.exe | 64.106.211.88:443 | plugin.fileopen.com | DataPipe, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cgi1.adobe.com |
| whitelisted |
www.adobe.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.fileopen.com |
| suspicious |
plugin.fileopen.com |
| suspicious |
crl.identrust.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |