| File name: | svchost.exe |
| Full analysis: | https://app.any.run/tasks/23927c14-eeb3-4299-94a0-276b162c1301 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2024, 03:57:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows |
| MD5: | A5DA0408270400A87E84D92C5282F5AC |
| SHA1: | A0509C919F52ACD6FC9EF0CAF16557D0CBECBAA5 |
| SHA256: | 0CD9F4E81C2940DFC863919D9080A657B4A910F100CCCB89624CB5AA2577B2DC |
| SSDEEP: | 98304:YjWnS9culcZCocgWgbzl9wEBFs2QOX0GQ8WDI5mPTaRHdjkHmXjXXRvgZlL9Ijek:u21 |
MALICIOUS
Drops the executable file immediately after the start
- svchost.exe (PID: 1128)
SUSPICIOUS
Process drops legitimate windows executable
- svchost.exe (PID: 1128)
Reads the BIOS version
- svchost.exe (PID: 1128)
The process checks if it is being run in the virtual environment
- svchost.exe (PID: 1128)
Starts a Microsoft application from unusual location
- svchost.exe (PID: 1128)
Read disk information to detect sandboxing environments
- svchost.exe (PID: 1128)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 1128)
- cmd.exe (PID: 3660)
Application launched itself
- cmd.exe (PID: 3660)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5140)
INFO
Checks supported languages
- svchost.exe (PID: 1128)
Reads the computer name
- svchost.exe (PID: 1128)
Reads the machine GUID from the registry
- svchost.exe (PID: 1128)
Reads Environment values
- svchost.exe (PID: 1128)
Reads the software policy settings
- svchost.exe (PID: 1128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win16/32 Executable Delphi generic (34.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (32.9) |
| .exe | | | DOS Executable Generic (32.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2104:07:13 03:24:40+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 2491392 |
| InitializedDataSize: | 81408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.19041.4355 |
| ProductVersionNumber: | 10.0.19041.4355 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Host Process for Windows Services |
| FileVersion: | 10.0.19041.4355 (WinBuild.160101.0800) |
| InternalName: | svchost.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | svchost.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.19041.4355 |
Total processes
126
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | "C:\Users\admin\Desktop\svchost.exe" | C:\Users\admin\Desktop\svchost.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
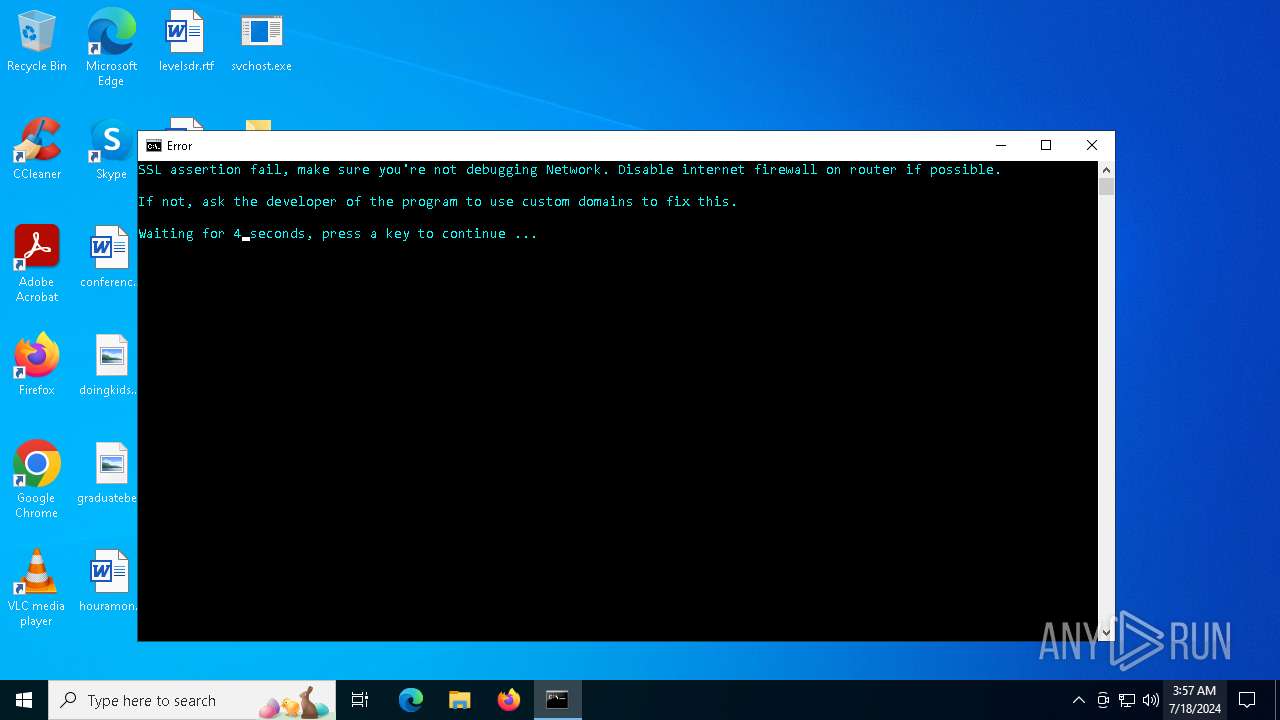
| 3660 | "cmd.exe" /c start cmd /C "color b && title Error && echo SSL assertion fail, make sure you're not debugging Network. Disable internet firewall on router if possible. & echo: & echo If not, ask the developer of the program to use custom domains to fix this. && timeout /t 5" | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4104 | timeout /t 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5140 | cmd /C "color b && title Error && echo SSL assertion fail, make sure you're not debugging Network. Disable internet firewall on router if possible. & echo: & echo If not, ask the developer of the program to use custom domains to fix this. && timeout /t 5" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 410
Read events
4 410
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1128 | svchost.exe | C:\Users\admin\Desktop\Logs\ErrorLogs.txt | text | |
MD5:9C35397532323694ABFD1626EB5022FD | SHA256:383071320C44E7308D2F48664B3CA4CD04C0625CF34AF370EE3037D72A2B27E9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
32
DNS requests
11
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4392 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4780 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4392 | svchost.exe | GET | — | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1700 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4780 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.50.80.213:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4780 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1700 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4392 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 184.86.251.19:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1128 | svchost.exe | 104.26.0.5:443 | keyauth.win | CLOUDFLARENET | US | unknown |
4780 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4392 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
keyauth.win |
| malicious |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain in DNS Lookup (keyauth .win) |
1128 | svchost.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain (keyauth .win) in TLS SNI |
1128 | svchost.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain (keyauth .win) in TLS SNI |