| File name: | 15.exe |
| Full analysis: | https://app.any.run/tasks/e6f0977a-0dac-40f7-8592-7293dced2e6b |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2024, 10:13:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 16D202AAC28076F3C4C1BEC60F356F7B |
| SHA1: | 4D9592F4B3F4EA12B245C531B93082CCFD6FD292 |
| SHA256: | 0CD7440CA94D31212E21867439F38F0828823B76C94D566E81F5DFAF71574EBC |
| SSDEEP: | 49152:PkMDPSb0+u327G88988Nt81QHG63yHoDeSfSm5fjss3pw9IRaVXT4TWCfCfCXalQ:PkMDPSb0+BXoG0heSfSm5fjsZ9VVERts |
MALICIOUS
Drops the executable file immediately after the start
- runas.exe (PID: 240)
- 15.exe (PID: 4456)
Antivirus name has been found in the command line (generic signature)
- taskkill.exe (PID: 2052)
SUSPICIOUS
Reads security settings of Internet Explorer
- 15.exe (PID: 4456)
Executable content was dropped or overwritten
- 15.exe (PID: 4456)
Creates file in the systems drive root
- 15.exe (PID: 4456)
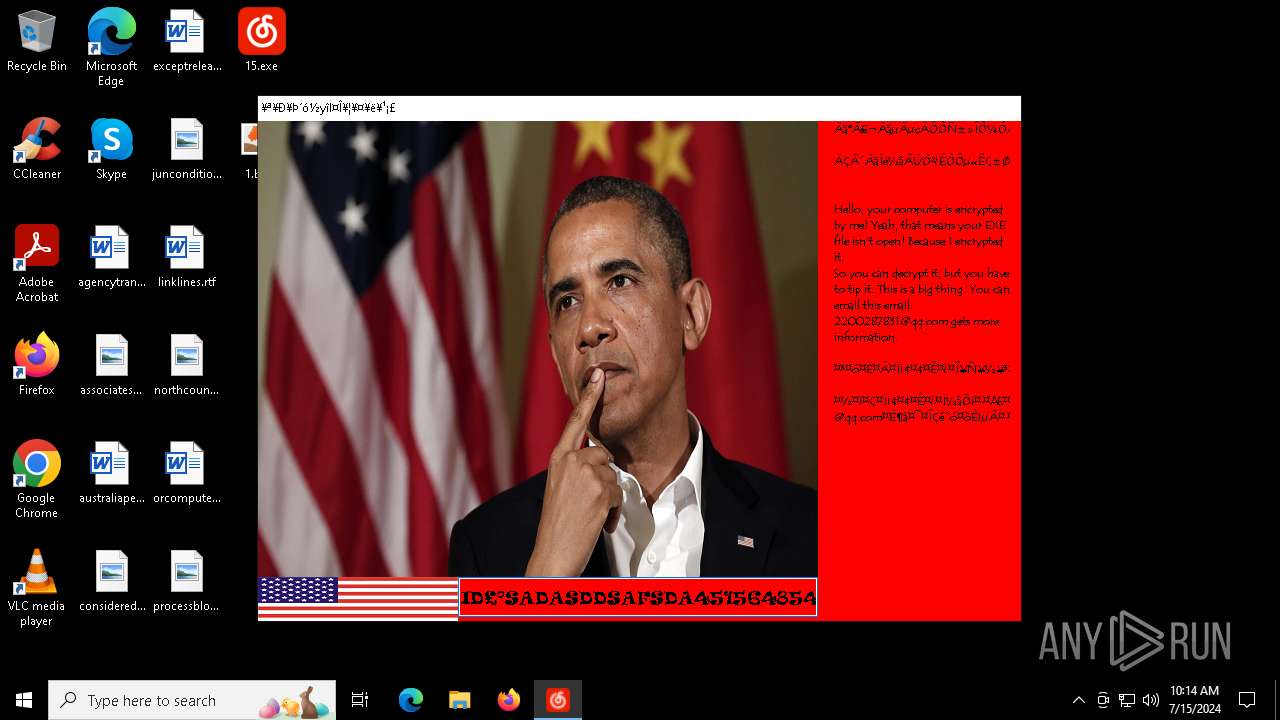
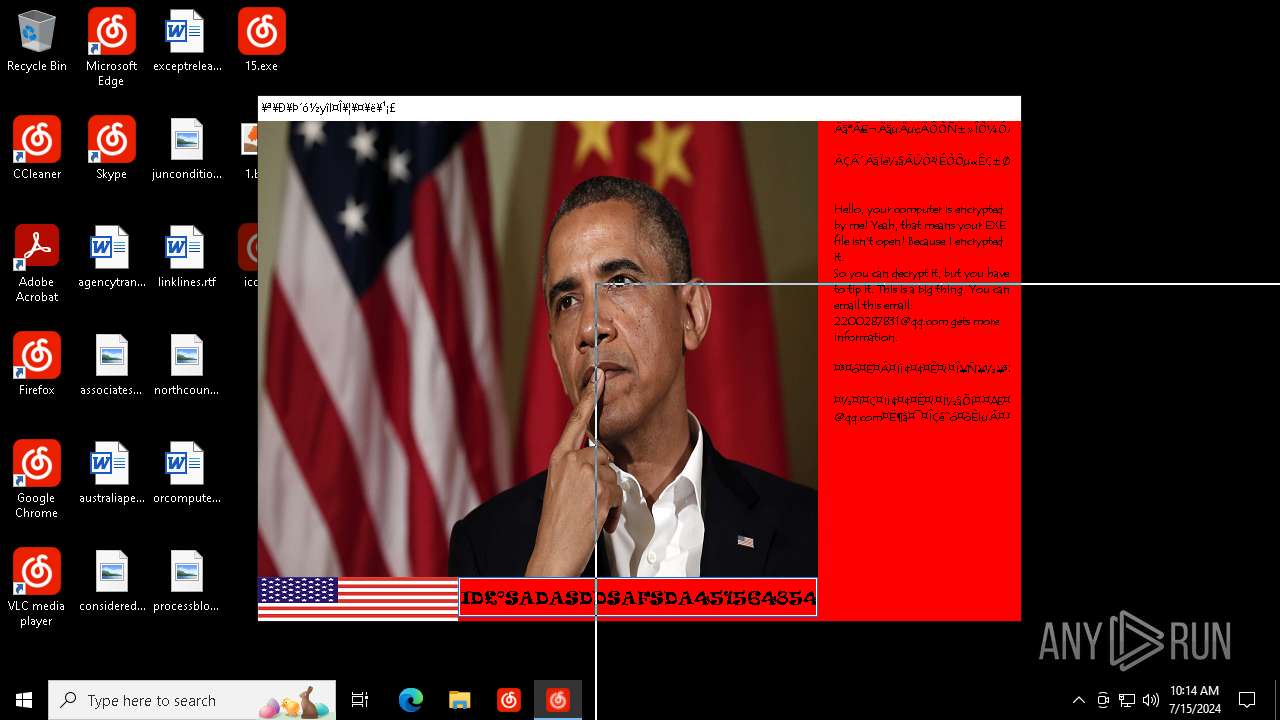
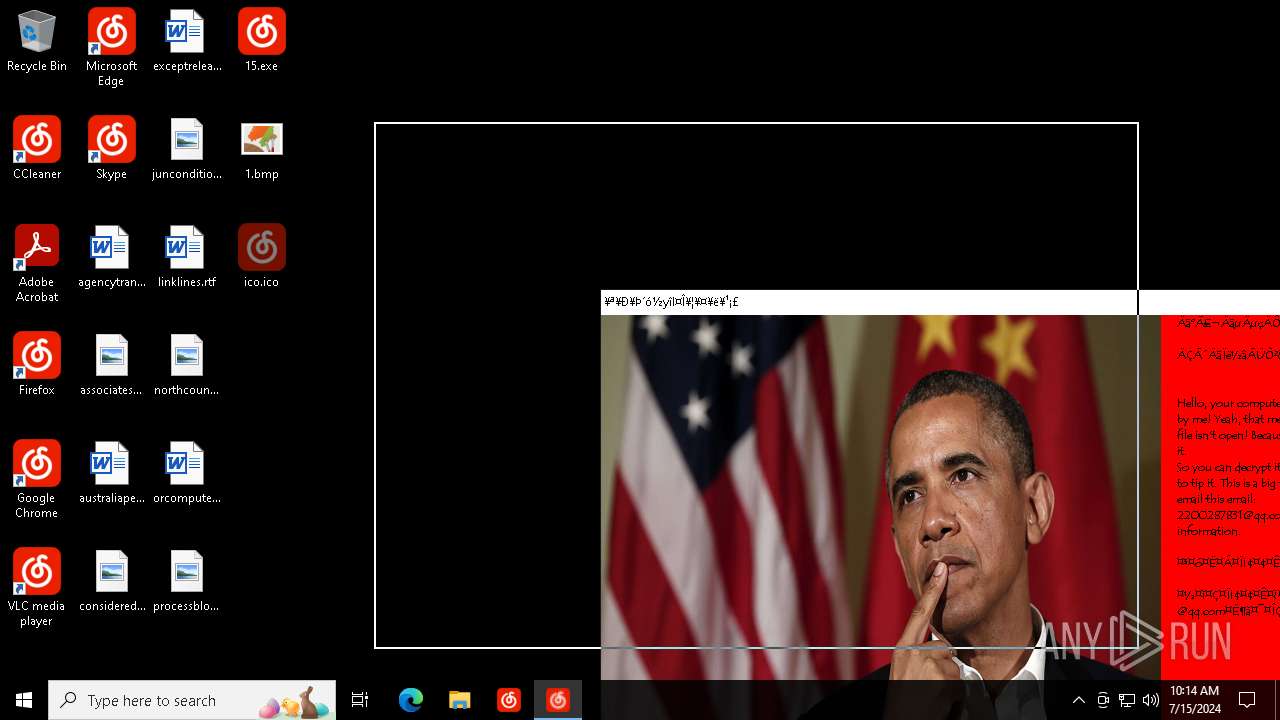
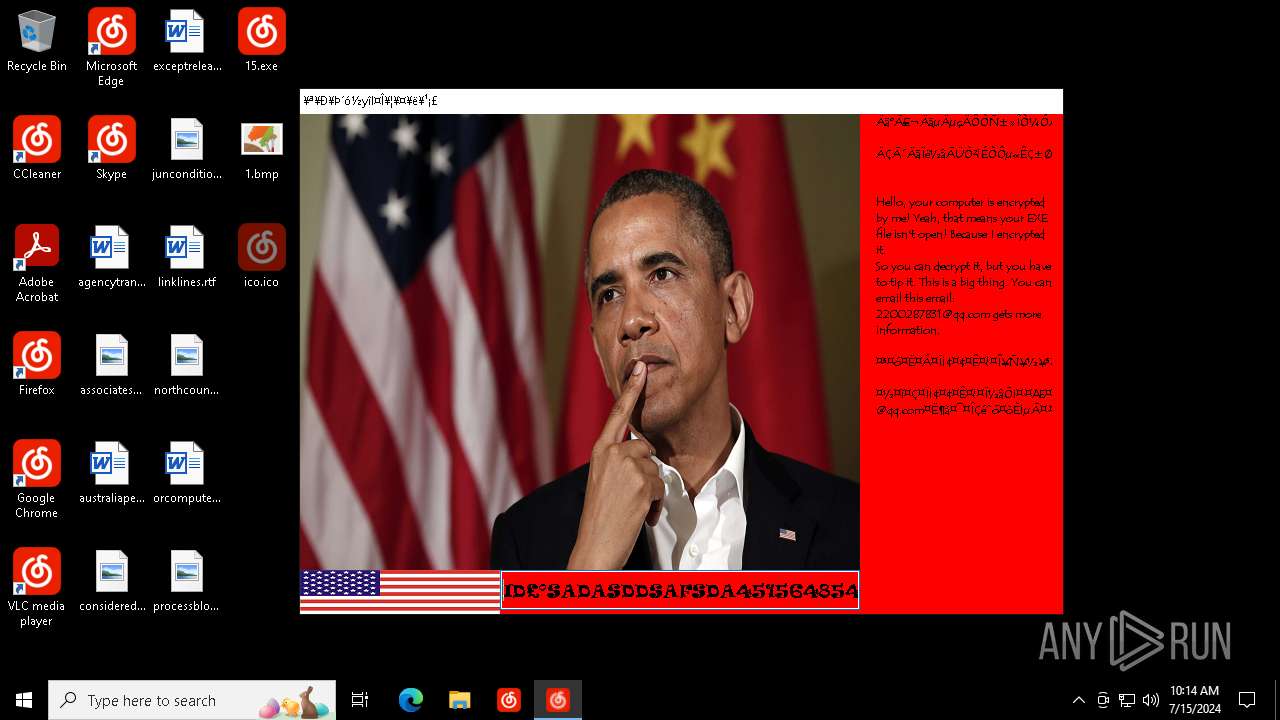
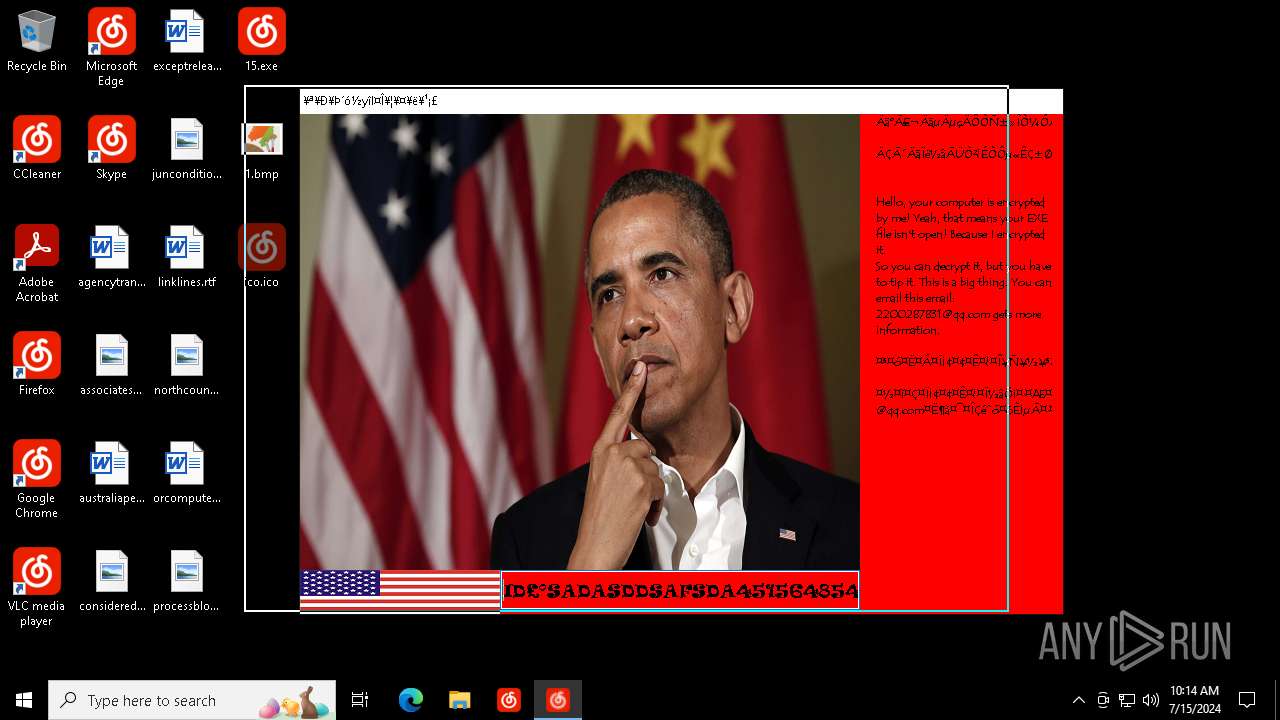
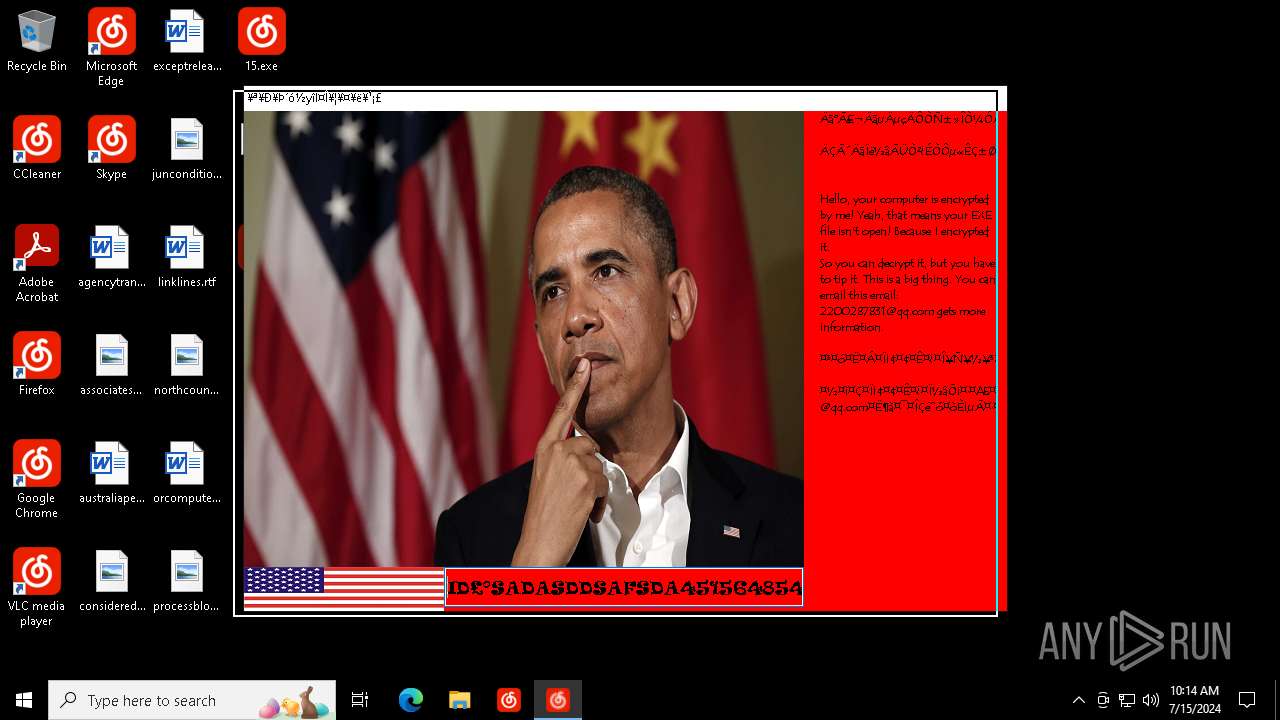
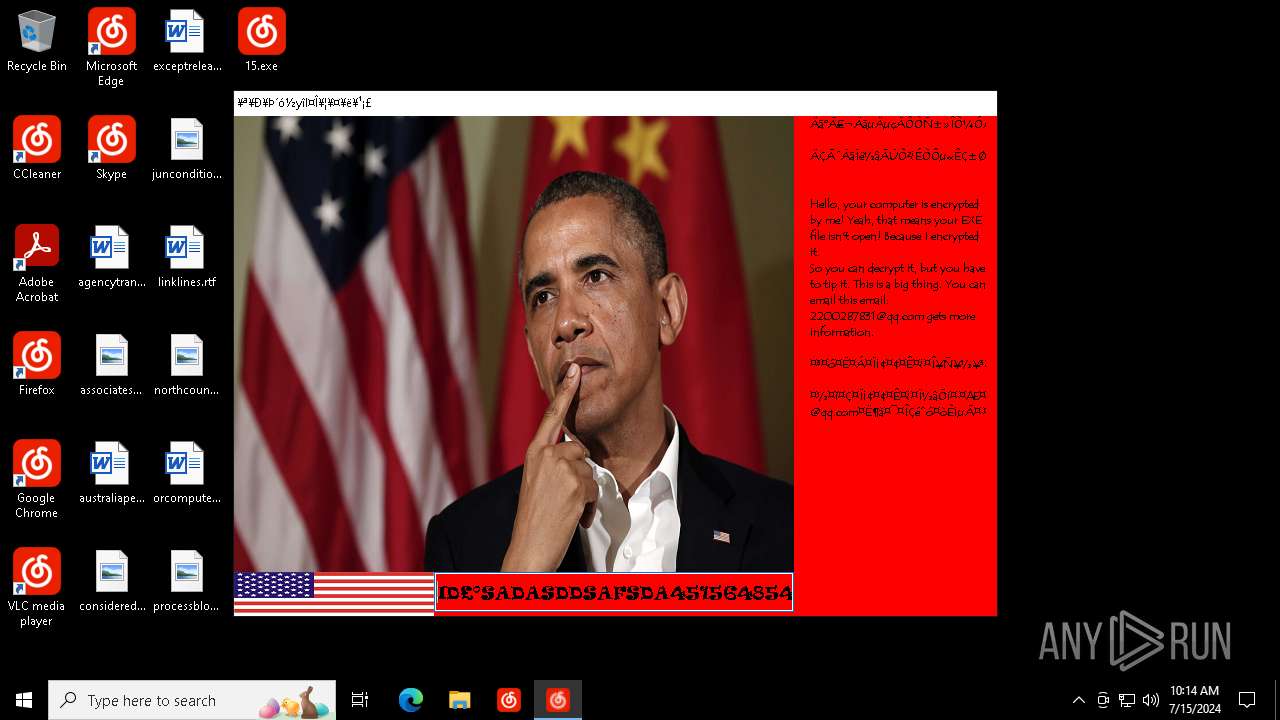
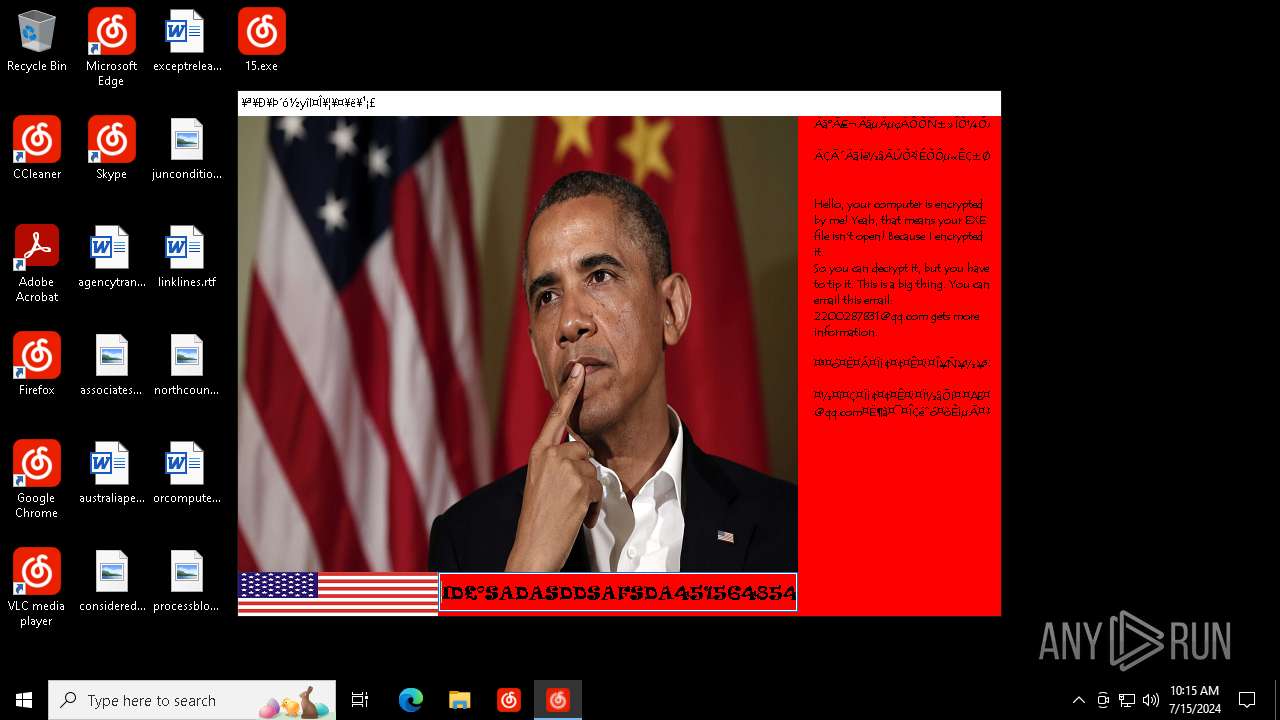
Changes the desktop background image
- 15.exe (PID: 4456)
Uses TASKKILL.EXE to kill process
- 15.exe (PID: 4456)
There is functionality for taking screenshot (YARA)
- 15.exe (PID: 4456)
INFO
Checks supported languages
- 15.exe (PID: 4456)
Reads the computer name
- 15.exe (PID: 4456)
Checks proxy server information
- 15.exe (PID: 4456)
UPX packer has been detected
- 15.exe (PID: 4456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (22.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (19.6) |
| .exe | | | UPX compressed Win32 Executable (19.2) |
| .exe | | | Win32 EXE Yoda's Crypter (18.8) |
| .scr | | | Windows screen saver (9.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:05:18 11:45:53+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 614400 |
| InitializedDataSize: | 1024000 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x75f4b |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 1.0.0.0 |
| FileDescription: | Barack Obama's Everlasting Blue Blackmail Virus |
| ProductName: | Barack Obama's Everlasting Blue Blackmail Virus |
| ProductVersion: | 1.0.0.0 |
| LegalCopyright: | Barack Obama's Everlasting Blue Blackmail Virus |
| Comments: | Barack Obama's Everlasting Blue Blackmail Virus |
Total processes
137
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\15.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1572 | taskkill /f /im Ravmon.exe | C:\Windows\SysWOW64\taskkill.exe | — | 15.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1956 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2052 | taskkill /f /im Mcshield.exe | C:\Windows\SysWOW64\taskkill.exe | — | 15.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | taskkill /f /im VsTskMgr.exe | C:\Windows\SysWOW64\taskkill.exe | — | 15.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | taskkill /f /im Rav.exe | C:\Windows\SysWOW64\taskkill.exe | — | 15.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | taskkill /f /im kavsvc.exe | C:\Windows\SysWOW64\taskkill.exe | — | 15.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 465
Read events
2 443
Write events
22
Delete events
0
Modification events
| (PID) Process: | (4456) 15.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Multimedia\DrawDib |
| Operation: | write | Name: | 1280x720x32(BGR 0) |
Value: 31,31,31,31 | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: C:\Users\admin\Desktop\1.bmp | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | WallpaperStyle |
Value: 1 | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | TileWallpaper |
Value: 1 | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\360Safe\safemon |
| Operation: | write | Name: | ExecAccess |
Value: 0 | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\360Safe\safemon |
| Operation: | write | Name: | MonAccess |
Value: 0 | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\360Safe\safemon |
| Operation: | write | Name: | SiteAccess |
Value: 0 | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\360Safe\safemon |
| Operation: | write | Name: | UDiskAccess |
Value: 0 | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exe |
| Operation: | write | Name: | EditFlags |
Value: 2 | |||
| (PID) Process: | (4456) 15.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 12 | |||
Executable files
1
Suspicious files
142
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4456 | 15.exe | — | ||
MD5:— | SHA256:— | |||
| 4456 | 15.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AdobeCollabSync.exe | — | |
MD5:— | SHA256:— | |||
| 4456 | 15.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\SingleClientServicesUpdater.exe | — | |
MD5:— | SHA256:— | |||
| 4456 | 15.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\SingleClientServicesUpdater.exe | — | |
MD5:— | SHA256:— | |||
| 4456 | 15.exe | C:\WINDOWS\ME\ÃÎ÷ÊÔ´Âë.ico | image | |
MD5:64DA46B04886AC5B67D66E70B7A9B3BD | SHA256:719F82BE101130B70F9DF2A891EEC19FEDFE177A79658E2A752DC1BE4A648332 | |||
| 4456 | 15.exe | C:\WINDOWS\SkinH_EL.dll | executable | |
MD5:147127382E001F495D1842EE7A9E7912 | SHA256:EDF679C02EA2E170E67AB20DFC18558E2BFB4EE5D59ECEEAEA4B1AD1A626C3CC | |||
| 4456 | 15.exe | C:\Users\admin\Desktop\1.bmp | binary | |
MD5:11C9AA3D4595C6AF63594ABAA0C530D4 | SHA256:AFDEACA6E9979C21AB3E5A69DBCBF889D07E58733CD993F275750B6DB05123BE | |||
| 4456 | 15.exe | C:\WINDOWS\ME\ÃÎ÷ÊÄ£¿é.ico | image | |
MD5:C1F9552D7628142E9D0E5C9C3267A98F | SHA256:AA709A476A4A1549DDD5FF1088B57098B6428C16953AD156980CF097182CA230 | |||
| 4456 | 15.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\CRLogTransport.exe | binary | |
MD5:2991C398658C8C14F20B8AF901D01C4F | SHA256:D82C7A5C8A631361A56D18F98B236941CB55C845E6CBA2E8589D2D29A58140AF | |||
| 4456 | 15.exe | C:\Users\admin\Desktop\ico.ico | image | |
MD5:11C9AA3D4595C6AF63594ABAA0C530D4 | SHA256:AFDEACA6E9979C21AB3E5A69DBCBF889D07E58733CD993F275750B6DB05123BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
14
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
528 | svchost.exe | GET | 200 | 23.206.181.130:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.211.108:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
2088 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1452 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
528 | svchost.exe | 52.183.220.149:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
528 | svchost.exe | 23.206.181.130:80 | www.microsoft.com | AKAMAI-AS | US | unknown |
2088 | MoUsoCoreWorker.exe | 52.183.220.149:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6004 | svchost.exe | 52.183.220.149:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ftp.free3v.net |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |