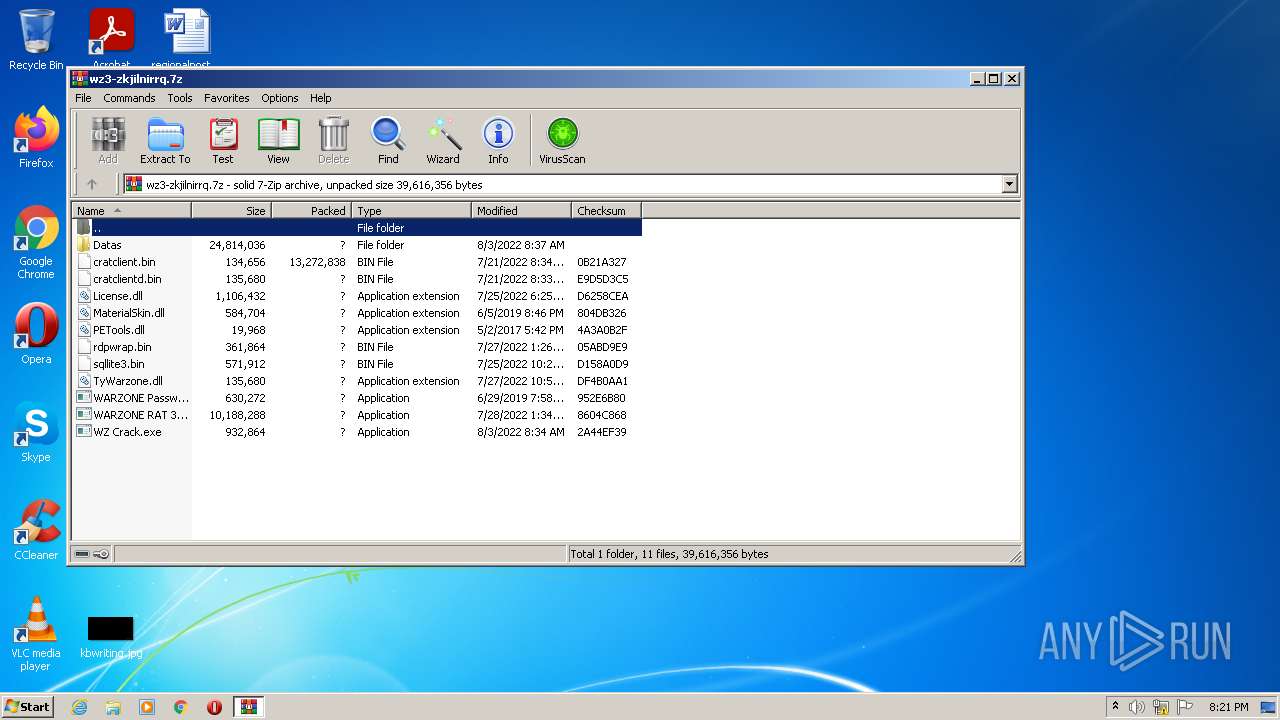
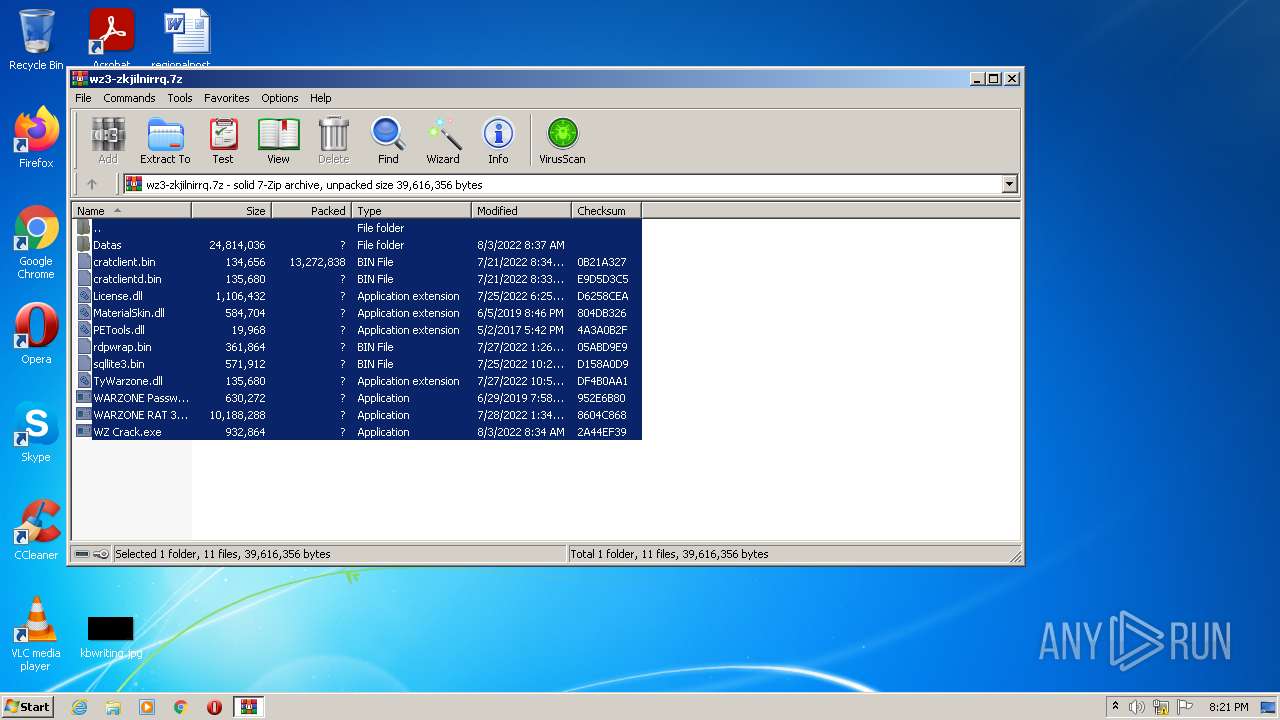
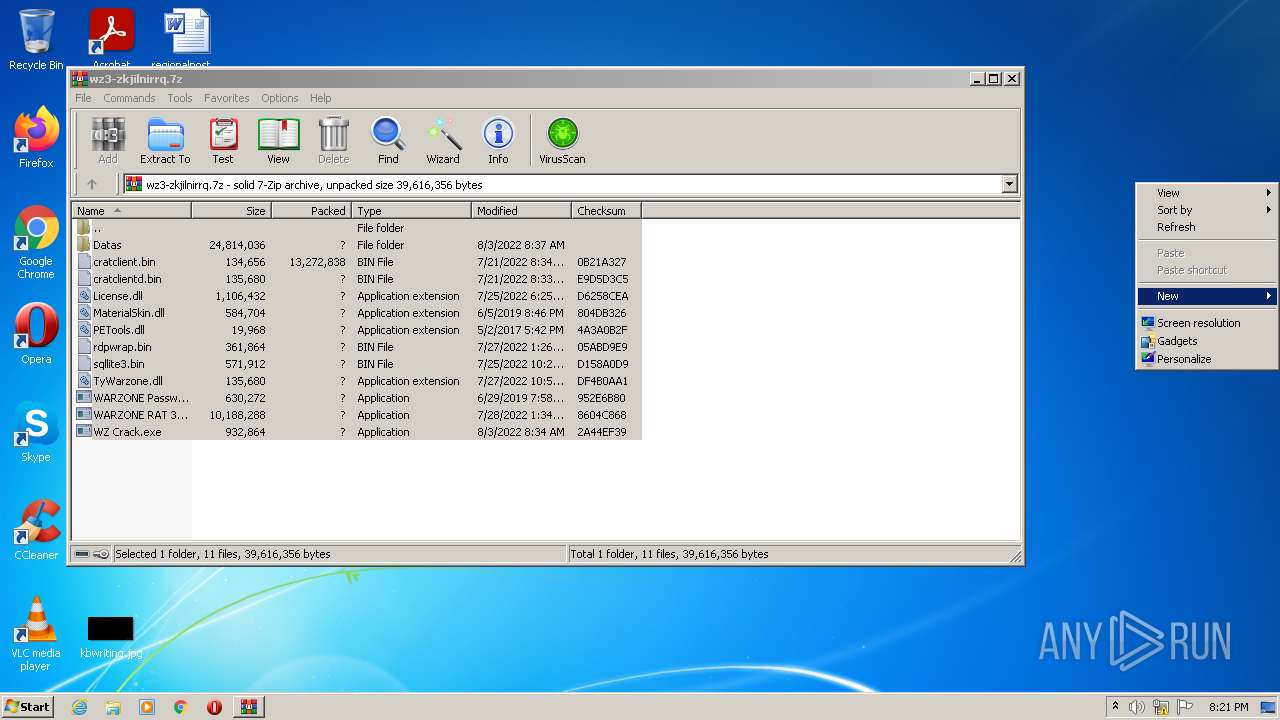
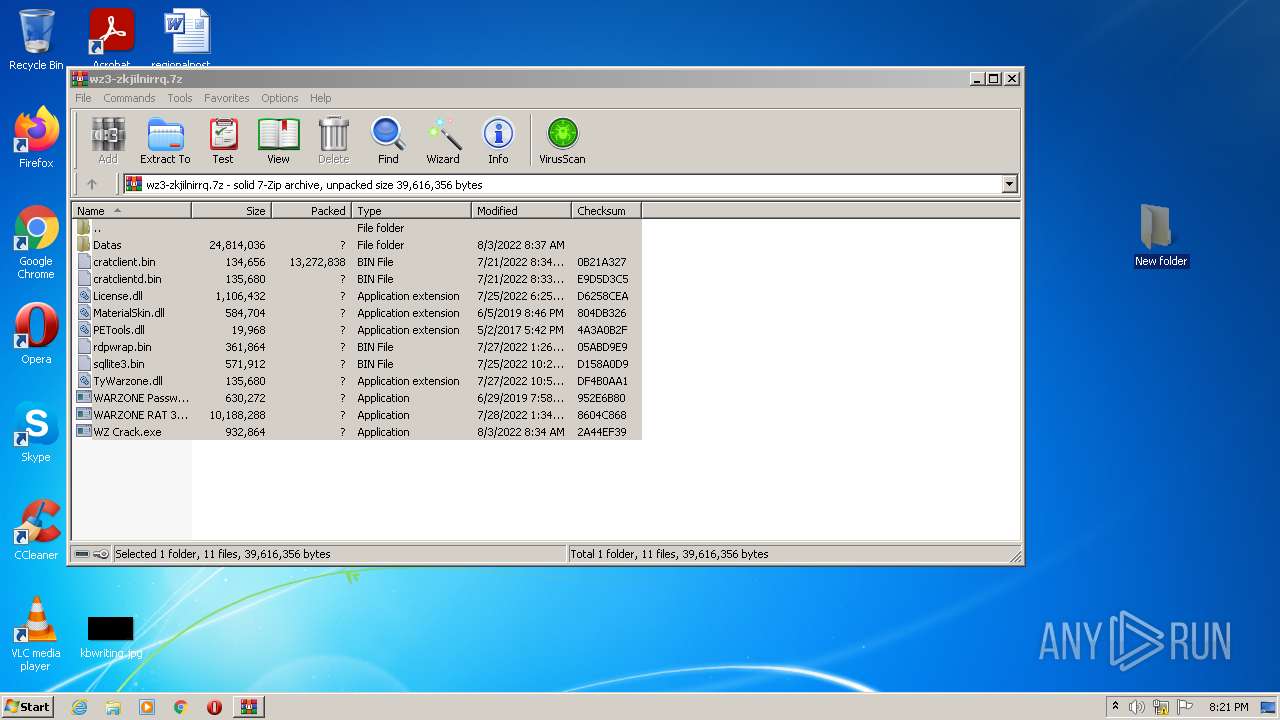
| File name: | wz3-zkjilnirrq.7z |
| Full analysis: | https://app.any.run/tasks/abd0c033-2c2d-43ce-a0ea-f7c0c17129e7 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2022, 19:21:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.3 |
| MD5: | ABEE2FCD919C28FE38AE12F81ADA3DFD |
| SHA1: | 72A6805C2AFEAB0FB8CC88B54405BA2B246B10FA |
| SHA256: | 0CAB1919953BAA9375F99A7876634E32E01F4BE76CC43B222EDAB65ADFF0C83B |
| SSDEEP: | 393216:QaL47swyqhqZyqv3MnsmO914Lbtl5AHml+VrHAl5S4oRW8iz:bwyMqxkn9DSrHAl5AWXz |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3460)
- WARZONE RAT 3.03.exe (PID: 1292)
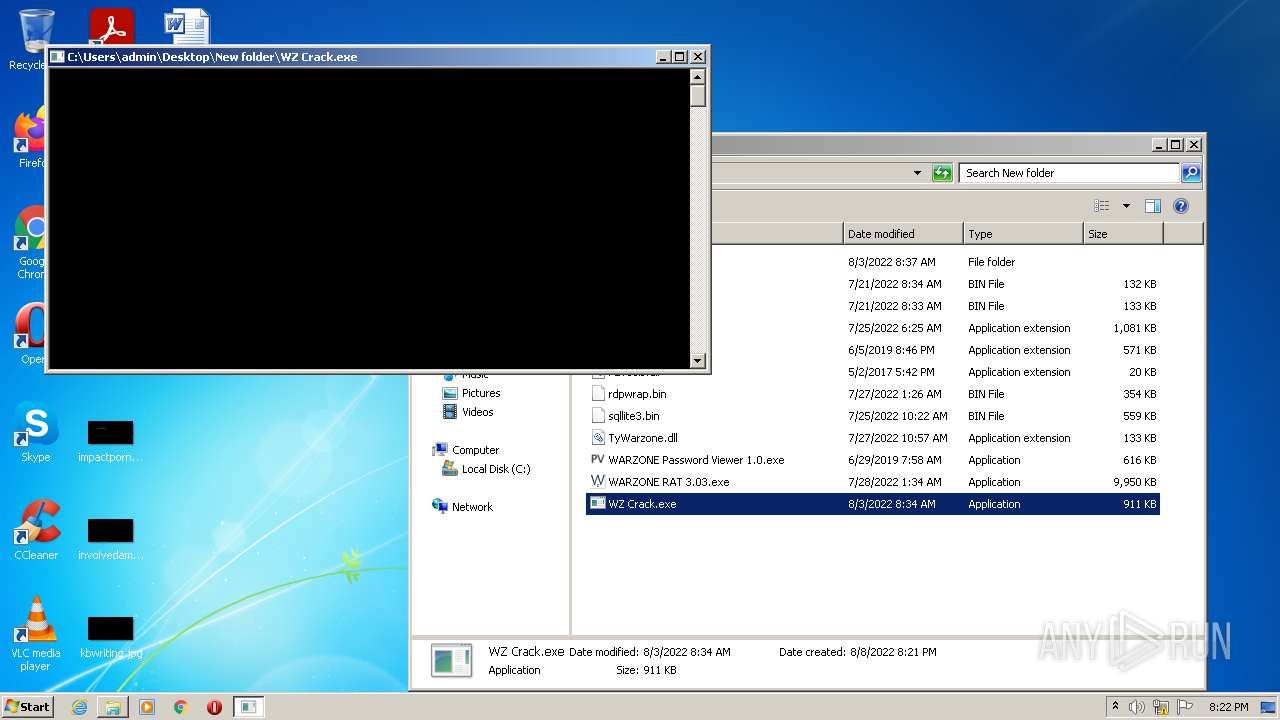
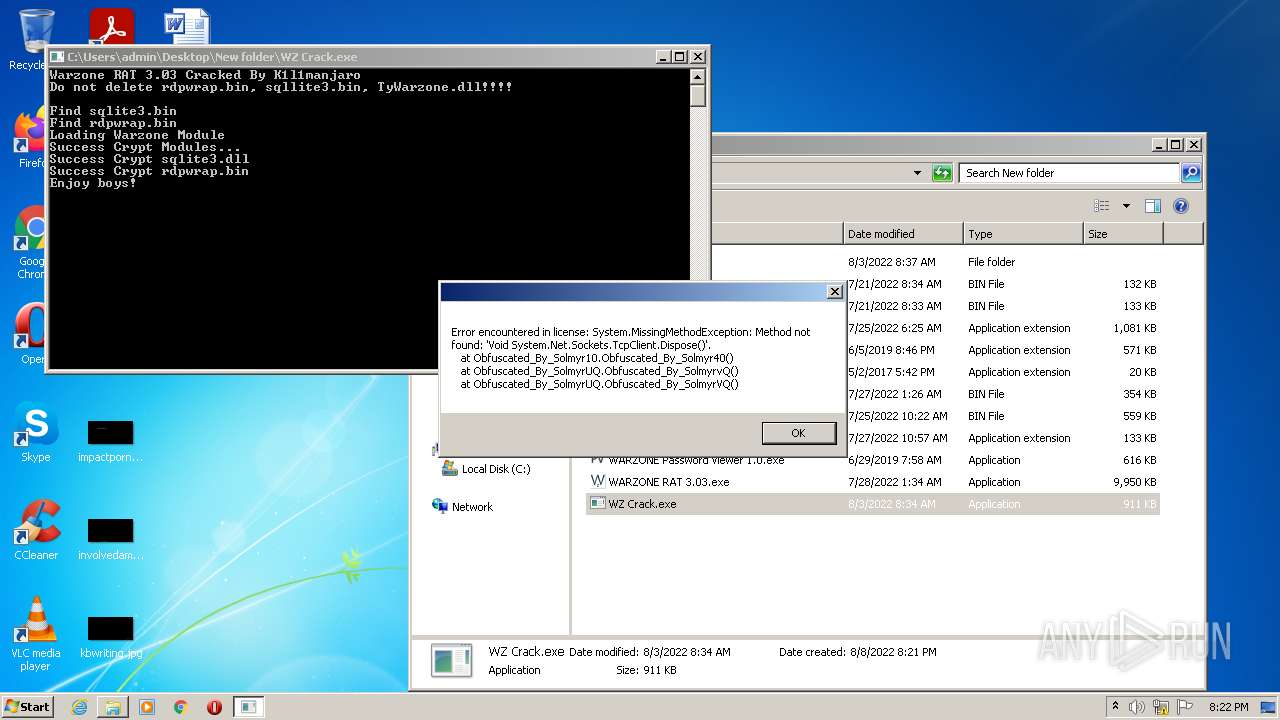
- WZ Crack.exe (PID: 2876)
- WARZONE RAT 3.03.exe (PID: 1340)
- WZ Crack.exe (PID: 3592)
- WARZONE Password Viewer 1.0.exe (PID: 928)
- WARZONE RAT 3.03.exe (PID: 2632)
Application was dropped or rewritten from another process
- WARZONE RAT 3.03.exe (PID: 1292)
- WZ Crack.exe (PID: 2876)
- WARZONE RAT 3.03.exe (PID: 1340)
- WZ Crack.exe (PID: 3592)
- WARZONE RAT 3.03.exe (PID: 2632)
- WARZONE Password Viewer 1.0.exe (PID: 928)
Drops executable file immediately after starts
- WinRAR.exe (PID: 3112)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3112)
Checks supported languages
- WinRAR.exe (PID: 3112)
- WARZONE RAT 3.03.exe (PID: 1292)
- WZ Crack.exe (PID: 2876)
- WARZONE RAT 3.03.exe (PID: 1340)
- WZ Crack.exe (PID: 3592)
- WARZONE Password Viewer 1.0.exe (PID: 928)
- WARZONE RAT 3.03.exe (PID: 2632)
Reads the computer name
- WinRAR.exe (PID: 3112)
- WZ Crack.exe (PID: 2876)
- WARZONE RAT 3.03.exe (PID: 1292)
- WARZONE RAT 3.03.exe (PID: 1340)
- WARZONE Password Viewer 1.0.exe (PID: 928)
- WZ Crack.exe (PID: 3592)
- WARZONE RAT 3.03.exe (PID: 2632)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3112)
INFO
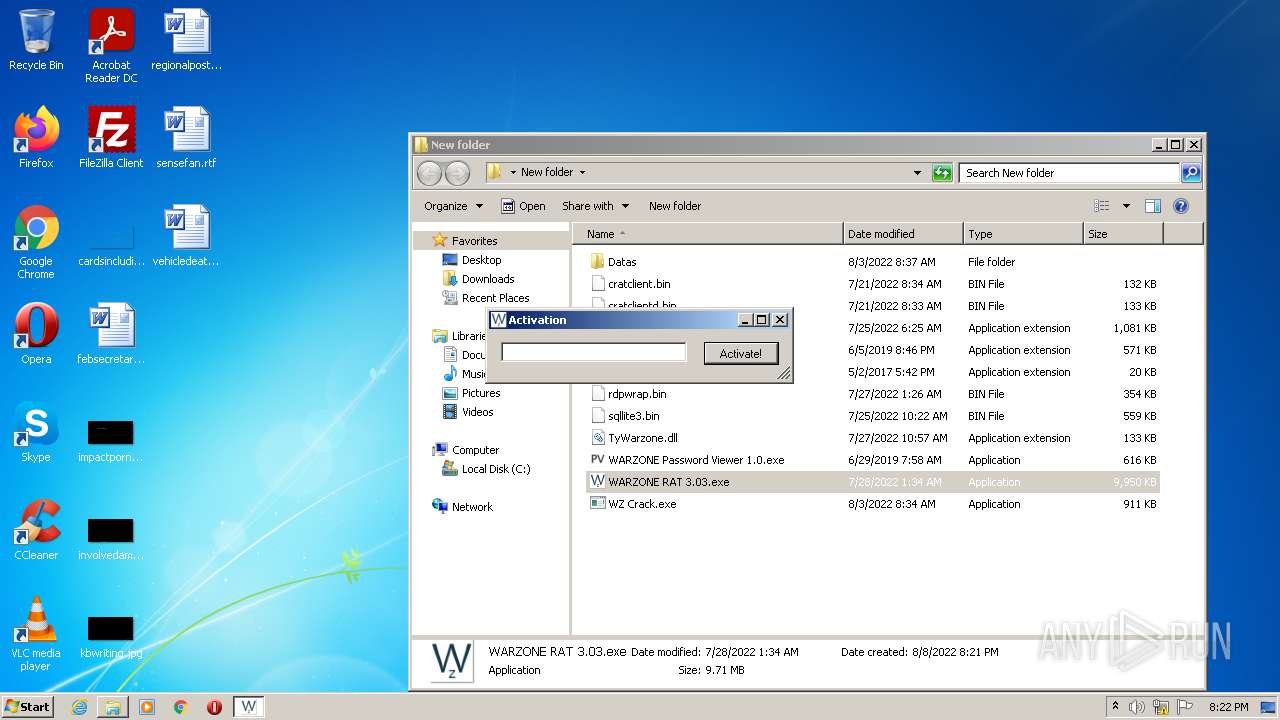
Manual execution by user
- WARZONE RAT 3.03.exe (PID: 1292)
- WZ Crack.exe (PID: 2876)
- WZ Crack.exe (PID: 3592)
- WARZONE Password Viewer 1.0.exe (PID: 928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (gen) (100) |
|---|
Total processes
44
Monitored processes
8
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
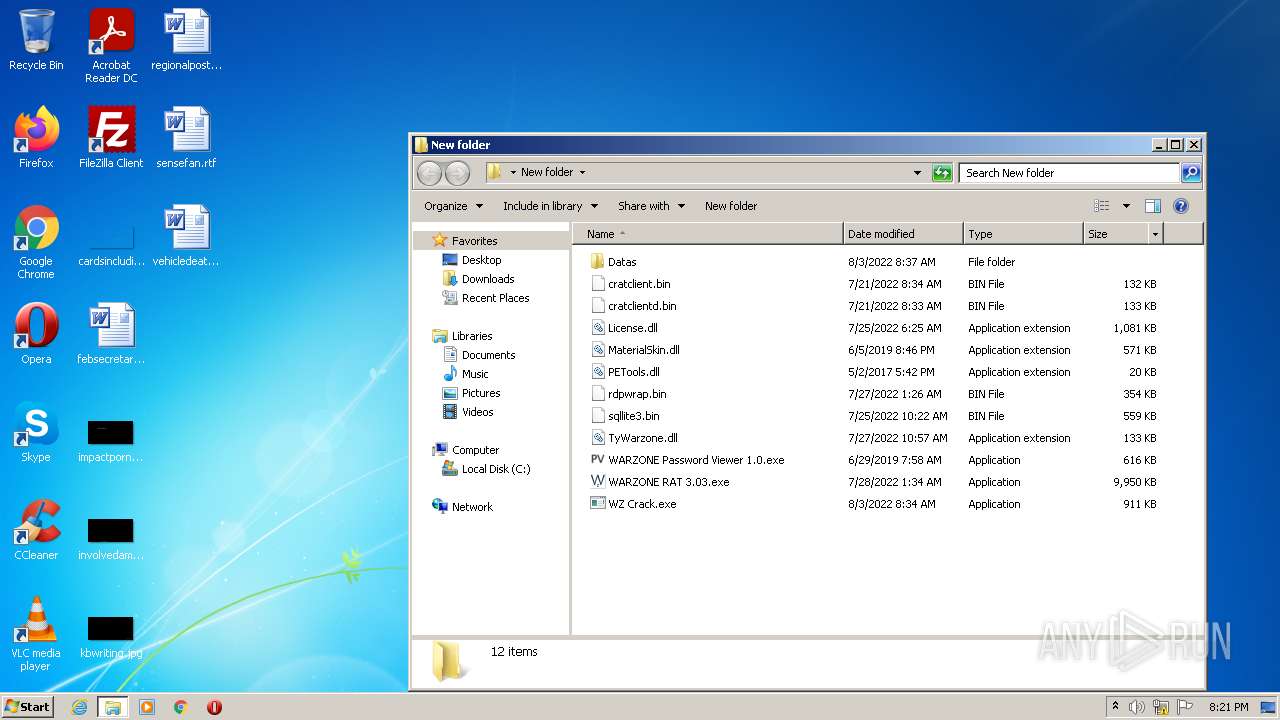
| 928 | "C:\Users\admin\Desktop\New folder\WARZONE Password Viewer 1.0.exe" | C:\Users\admin\Desktop\New folder\WARZONE Password Viewer 1.0.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: WARZONE Password Viewer 1.0 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1292 | "C:\Users\admin\Desktop\New folder\WARZONE RAT 3.03.exe" | C:\Users\admin\Desktop\New folder\WARZONE RAT 3.03.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: WARZONE RAT 3.00 Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 1340 | "WARZONE RAT 3.03.exe" | C:\Users\admin\Desktop\New folder\WARZONE RAT 3.03.exe | — | WZ Crack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WARZONE RAT 3.00 Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 2632 | "WARZONE RAT 3.03.exe" | C:\Users\admin\Desktop\New folder\WARZONE RAT 3.03.exe | — | WZ Crack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WARZONE RAT 3.00 Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 2876 | "C:\Users\admin\Desktop\New folder\WZ Crack.exe" | C:\Users\admin\Desktop\New folder\WZ Crack.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
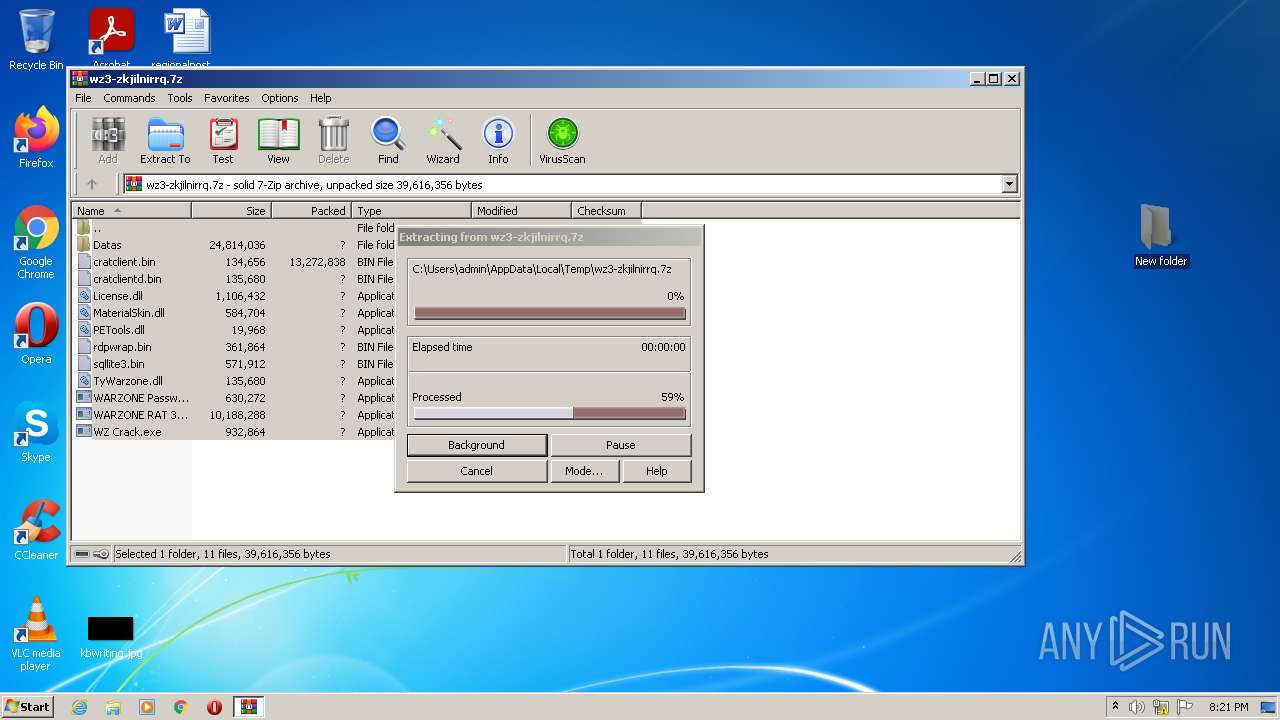
| 3112 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\wz3-zkjilnirrq.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3460 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3592 | "C:\Users\admin\Desktop\New folder\WZ Crack.exe" | C:\Users\admin\Desktop\New folder\WZ Crack.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 210
Read events
2 189
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\wz3-zkjilnirrq.7z | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
17
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\License.dll | executable | |
MD5:— | SHA256:— | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\Datas\rdpwrap64.dll | executable | |
MD5:C4063372AFE486D5E9A11C5B68E0524F | SHA256:FC1F3FC182CEF9BCEF5192E4FA4569697E27852CBFFB7A55EA6118C603DDC420 | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\sqllite3.bin | binary | |
MD5:3FF5EB1505911A17716FE10A9CA96CB4 | SHA256:467B77FB1D8559AB4A6D9C2DE21575E81E39D07E617F1AA2E5F47FA86F80D92C | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\cratclientd.bin | executable | |
MD5:F6DBE80A1B68A734C92375FBBCF4BE88 | SHA256:D364FE03510F34C22E8B5D25784BA80DECAE568BD939DB66E4CD8B90538D60BE | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\PETools.dll | executable | |
MD5:DB7101A0E92CD476B587AFB9C55586D0 | SHA256:B39BBD6D8EE84743834741AAE0A39159F62DB829678E5BB0D915B09EDC27B41E | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\MaterialSkin.dll | executable | |
MD5:ED99FA9FDDE37B7BACCE5FB11B61DFDD | SHA256:50D82FC44A5EE228FFACC36F5BABC51985ED229B0E0C88DFA806E08A56EC989A | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\Datas\geoip\GeoIP.dat | binary | |
MD5:42368516B6BD3C337AA64A012FBA8C3D | SHA256:57B31E52D36571CF8D52BA6ECAB8D0DC8C6705B5ED94D9F7F98B01F40863E5A0 | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\Datas\rdpwrap32.dll | executable | |
MD5:F5C6A32EE3BD88AE44C0C0DFAE950CF0 | SHA256:B9828995474F7E6A6B5C160E5160C5FF49495654A5B89654B6A0F9B8664F82FC | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\Datas\SocksManager.exe | executable | |
MD5:E659818D6EFE1953E14C9ECE3B24A14C | SHA256:28195831F7E09DDF9BBE28EC957C1F380D27CF9CC3EBF538BEAADA0E4E74886A | |||
| 3112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3112.16831\Datas\upnp.exe | executable | |
MD5:CA96229390A0E6A53E8F2125F2C01114 | SHA256:0DF3D05900E7B530F6C2A281D43C47839F2CF2A5D386553C8DC46E463A635A2C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3592 | WZ Crack.exe | 20.112.52.29:80 | microsoft.com | — | US | malicious |
2876 | WZ Crack.exe | 20.112.52.29:80 | microsoft.com | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2876 | WZ Crack.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3592 | WZ Crack.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |