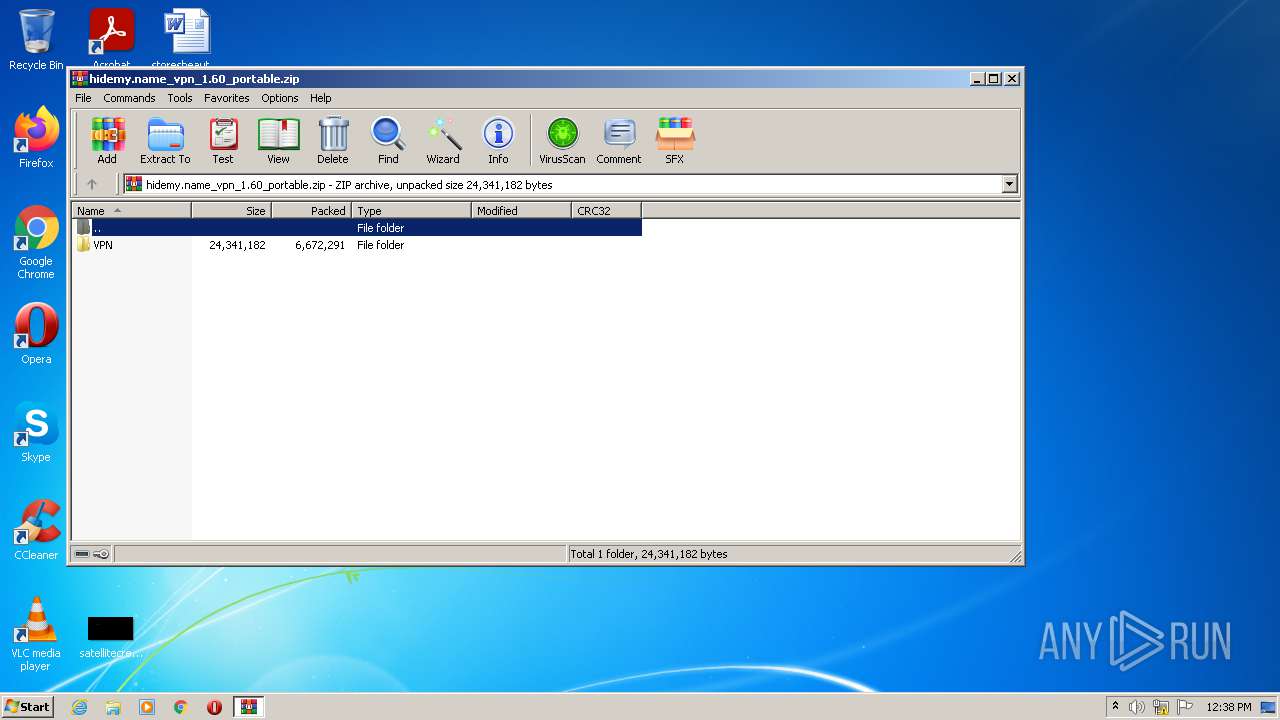
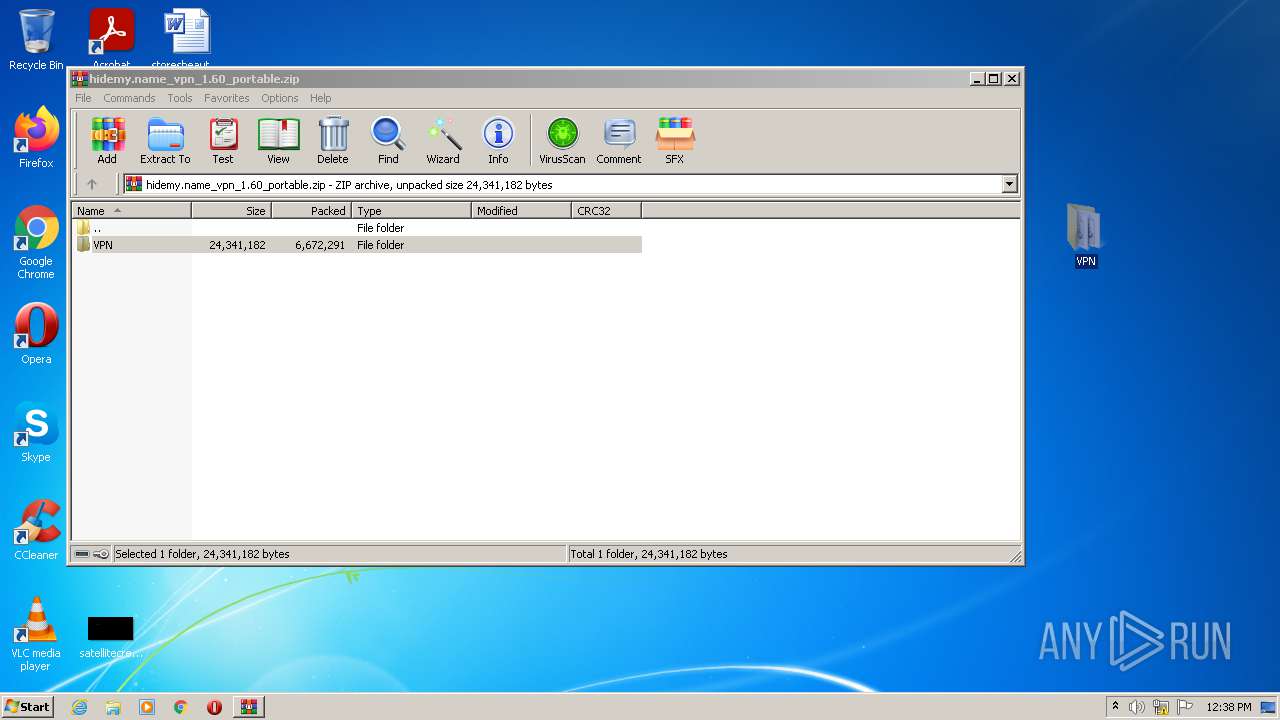
| File name: | hidemy.name_vpn_1.60_portable.zip |
| Full analysis: | https://app.any.run/tasks/4ef448c5-7f80-4b9b-8a6f-2336375132ee |
| Verdict: | Malicious activity |
| Analysis date: | September 25, 2021, 11:38:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F59F60C2119A6C17D3CE9AA3CC25F3E8 |
| SHA1: | 814BF90D5DEB8E2E3C35A7F93C4E889FA7ACEE98 |
| SHA256: | 0C8653C783F51834542CEF427CBD3374D8E6D26048906F9A142F5A836EC3892B |
| SSDEEP: | 196608:WSiqJneJuvKqA3xuKzdD65w70VpHislS25NV:LzJneJsBkxukdD6+cpHiNUX |
MALICIOUS
Application was dropped or rewritten from another process
- pkzip25.exe (PID: 3788)
- Start.exe (PID: 2868)
- Start.exe (PID: 2484)
- pkzip25.exe (PID: 2804)
- pkzip25.exe (PID: 3336)
- pkzip25.exe (PID: 968)
- pkzip25.exe (PID: 920)
- pkzip25.exe (PID: 3816)
Loads dropped or rewritten executable
- Start.exe (PID: 2484)
- SearchProtocolHost.exe (PID: 2472)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2564)
- Start.exe (PID: 2484)
Checks supported languages
- pkzip25.exe (PID: 920)
- pkzip25.exe (PID: 3788)
- WinRAR.exe (PID: 2564)
- Start.exe (PID: 2484)
- pkzip25.exe (PID: 968)
- pkzip25.exe (PID: 2804)
- pkzip25.exe (PID: 3336)
- pkzip25.exe (PID: 3816)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2564)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2564)
Drops a file with too old compile date
- WinRAR.exe (PID: 2564)
Reads default file associations for system extensions
- SearchProtocolHost.exe (PID: 2472)
INFO
Manual execution by user
- Start.exe (PID: 2868)
- Start.exe (PID: 2484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | VPN/countries.ini |
|---|---|
| ZipUncompressedSize: | 4148 |
| ZipCompressedSize: | 2296 |
| ZipCRC: | 0xa55875af |
| ZipModifyDate: | 2020:11:03 23:54:22 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
52
Monitored processes
10
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | -silent -overwrite -extract "C:\Users\admin\AppData\Local\Temp\tmp_gui\conf.zip" "C:\Users\admin\AppData\Local\Temp\tmp_gui" | C:\Users\admin\Desktop\VPN\utils\pkzip25.exe | — | Start.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 968 | -silent -overwrite -extract "C:\Users\admin\AppData\Local\Temp\tmp_gui\conf.zip" "C:\Users\admin\AppData\Local\Temp\tmp_gui" | C:\Users\admin\Desktop\VPN\utils\pkzip25.exe | — | Start.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2472 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
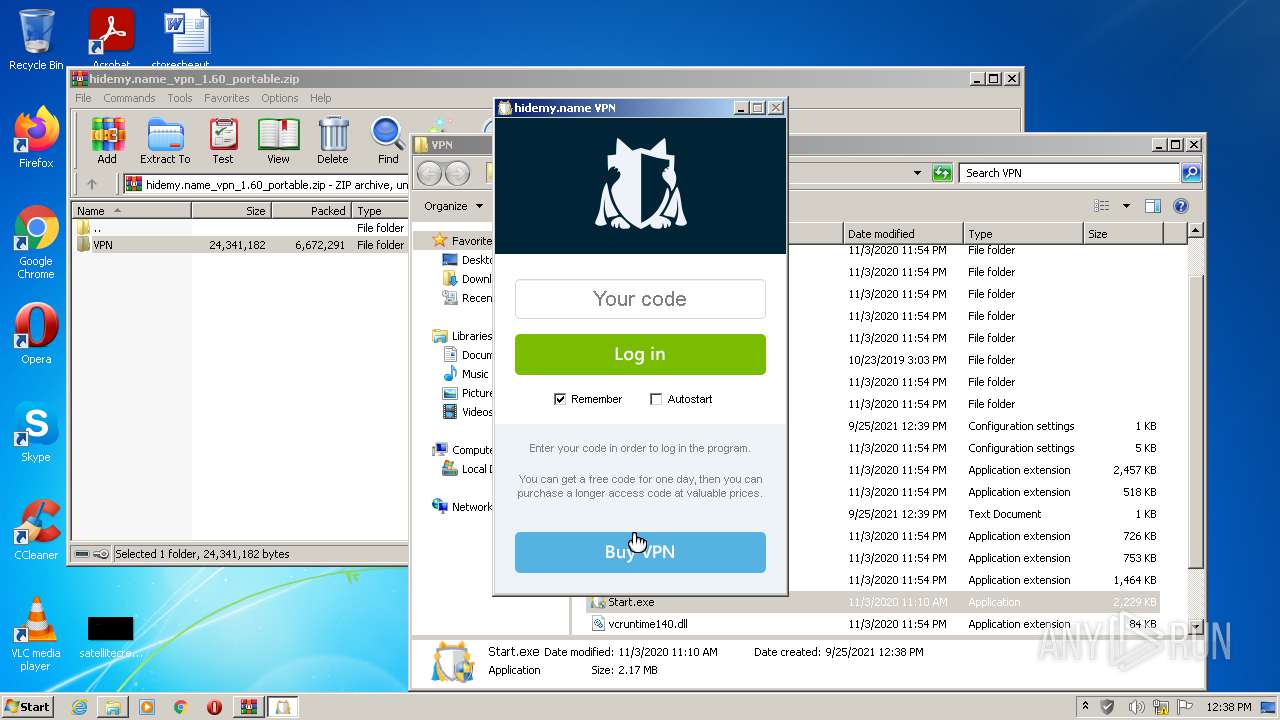
| 2484 | "C:\Users\admin\Desktop\VPN\Start.exe" | C:\Users\admin\Desktop\VPN\Start.exe | Explorer.EXE | ||||||||||||
User: admin Company: inCloak Network Ltd. Integrity Level: HIGH Exit code: 0 Version: 1.6 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\hidemy.name_vpn_1.60_portable.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2804 | -silent -overwrite -extract "C:\Users\admin\Desktop\VPN\configs\HIDEME_52530359486117.ZIP" "C:\Users\admin\Desktop\VPN\configs" | C:\Users\admin\Desktop\VPN\utils\pkzip25.exe | — | Start.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2868 | "C:\Users\admin\Desktop\VPN\Start.exe" | C:\Users\admin\Desktop\VPN\Start.exe | — | Explorer.EXE | |||||||||||
User: admin Company: inCloak Network Ltd. Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.6 Modules
| |||||||||||||||
| 3336 | -silent -overwrite -extract "C:\Users\admin\AppData\Local\Temp\tmp_gui\conf.zip" "C:\Users\admin\AppData\Local\Temp\tmp_gui" | C:\Users\admin\Desktop\VPN\utils\pkzip25.exe | — | Start.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3788 | -silent -overwrite -extract "C:\Users\admin\Desktop\VPN\ike2\cert\HIDEME_52530359486117_IPSEC.ZIP" "C:\Users\admin\Desktop\VPN\ike2\cert" | C:\Users\admin\Desktop\VPN\utils\pkzip25.exe | — | Start.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3816 | -silent -overwrite -extract "C:\Users\admin\Desktop\VPN\HIDEME_52530359486117.ZIP" "C:\Users\admin\Desktop\VPN" | C:\Users\admin\Desktop\VPN\utils\pkzip25.exe | — | Start.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 500
Read events
4 478
Write events
22
Delete events
0
Modification events
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\hidemy.name_vpn_1.60_portable.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2472) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
25
Suspicious files
18
Text files
451
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\driver\x32\tap0901.cat | cat | |
MD5:FB34D08569AF3A01758D4BF629A3AA0D | SHA256:AA83670A92681A19B6AED64CF0509C2B53B56C11352A88764FC25C7BF6F5C5F9 | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\driver\tap99update.exe | executable | |
MD5:AC9B2624EF366742C9AD32B86225A251 | SHA256:02E1013EE8D548EDC3FBAFAB672977EA8C677CF1F0B57018652FCF2A2411CBFB | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\countries.ini | text | |
MD5:49F53C48C7AC1BF851529522AD58C681 | SHA256:5465E8D706C887C2D174E5E7995B071FB0007693949F5AA98D5C0907DBC5459F | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\driver\x64\tap0901.cat | cat | |
MD5:0365C95D5BE2B3D314DCC019380C0E11 | SHA256:6F997D53ABFC991E23F08256FBDE3EB21A1680AF2E504B7ACCFEF0F1D8909503 | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\driver\x32\OemWin2k.inf | binary | |
MD5:35589B966C65A52A1C95791BBCD80543 | SHA256:8892D224AE879CC35FFE216691FC6BA3266D88B6239838F7D38B3A4FF4AD74B6 | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\flags\AD.ico | image | |
MD5:A8358B485820DE16F70EAE9BEF692FD2 | SHA256:0212D5066B17BD3988153D5F73EE039D278E4B0CFE0DF4571DA1DBE4C8590380 | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\driver\x32\tap0901.sys | executable | |
MD5:432D9D823C4C26B6070C41BAD4404CE4 | SHA256:741B41F7467D312AF4CC733EA31F647FBCD06985CBB6A14117E8A87A6F7B06F5 | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\driver\x64\tap0901.sys | executable | |
MD5:3C32FF010F869BC184DF71290477384E | SHA256:55CFCEC7F026C6E2E96A2FBE846AB513BB12BB0348735274FE1B71AF019C837B | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\flags\AR.ico | image | |
MD5:80EFFC55D8742D9AE63476263176BF32 | SHA256:E904C54D9E6A3BEBD411A7FEFFD4D44B3A8B7CBE32EFF2C42DA5386AD05EAE39 | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.8915\VPN\flags\AU.ico | image | |
MD5:2E8F294CF45E1974B5FC3514A63B9A34 | SHA256:31FB79E3ACE76A9F6E838A565C81C2E7C238B79C99F0C79F9847690B92C4CFBE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
11
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2484 | Start.exe | 104.26.9.174:443 | justapi.info | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
justapi.info |
| suspicious |