| URL: | https://whatismyipaddress.com/ |
| Full analysis: | https://app.any.run/tasks/3a11d7c1-c0f3-4d91-92d3-1c7cdcf92ab2 |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2024, 16:56:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A91E2CDB8B2DEB7CB65020F6FFA88ADC |
| SHA1: | 8CB87E0815CEF00F9B2319522836AEC221D7F35D |
| SHA256: | 0C78CACC19CCEB5A501F6B7571AE1B1AA253F48FF92CFD90F81DED9268F6BB9F |
| SSDEEP: | 3:N8cERMPcMuBs:2c4KuBs |
MALICIOUS
No malicious indicators.SUSPICIOUS
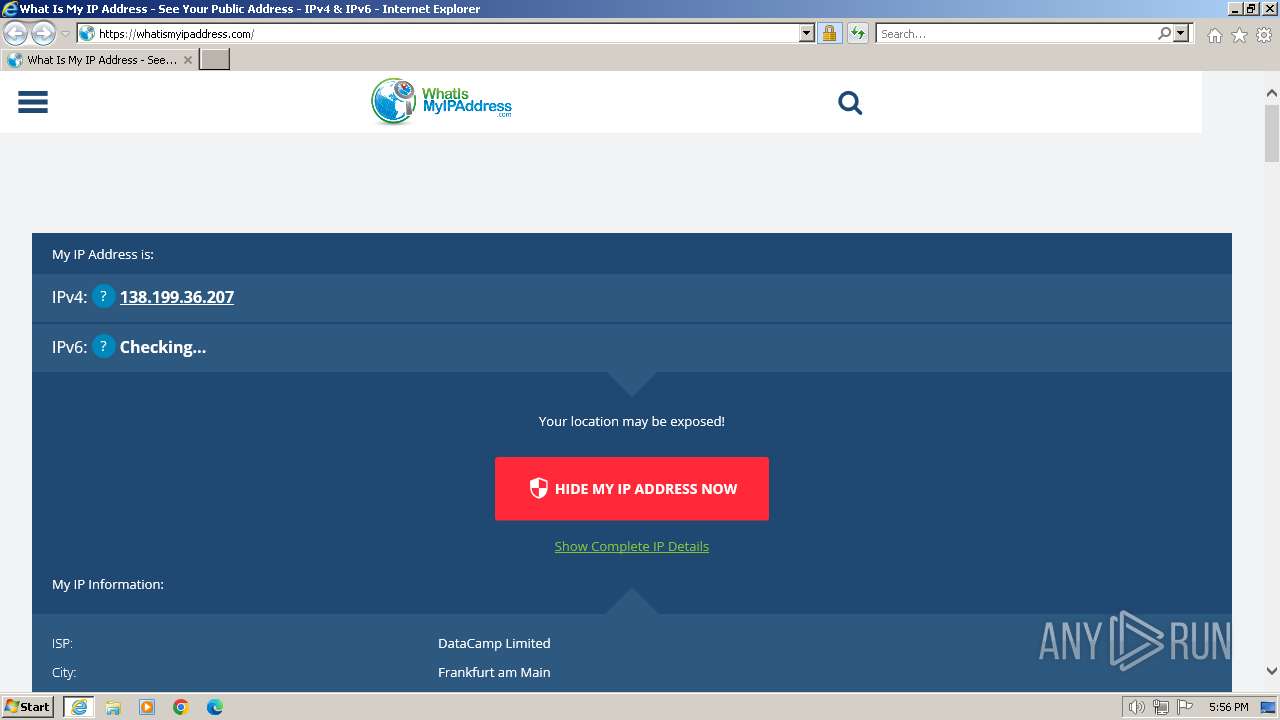
Checks for external IP
- svchost.exe (PID: 1060)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 976)
Checks supported languages
- wmpnscfg.exe (PID: 976)
Reads the computer name
- wmpnscfg.exe (PID: 976)
Application launched itself
- iexplore.exe (PID: 2712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 976 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1060 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2712 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://whatismyipaddress.com/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3052 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2712 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 819
Read events
19 694
Write events
96
Delete events
29
Modification events
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31125702 | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31125702 | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
46
Text files
46
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:0A8A545642E79AC2464A46493A26A92D | SHA256:5E8AA1F4F38B6CCD7059EDE25CC0C28FABFA5431D5935CB2E16A8020CCD8975D | |||
| 3052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:1FE34D90E21092AD70F236A403564F80 | SHA256:4336BBA92B4F20B3806A7297534AFBD38D600AD31115E153FB81661ECE116C3B | |||
| 3052 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\85XHKZUN.txt | text | |
MD5:D398FD7462E59861F6DEE542FFDD9106 | SHA256:DC9C137A620E2AC4F09847CD769CE1A75B172925A7CDE5FC9A4AF7F463A8BAAA | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\Cab269F.tmp | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1060 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:FEBFDEA0DD1E38F890835930AFE1CC26 | SHA256:EBFB54C7065640EE418E20E71CD83679131ED3A1EDC854C76B8EC2A3F41513CA | |||
| 3052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 3052 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\base.min[1].css | text | |
MD5:CBD0FB866214542B799F99B57B7A92FE | SHA256:1E8DCAEC98F99C2B1B43FF8B8655680B69BBF150470B20ECBDD1CB45570A0587 | |||
| 3052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:DEC0F0A433E9B0D153A5680A13353CDD | SHA256:AD9B5BA38D2AF1D1FFC9EEF08F55A9BEB3E7258296FC993C909C481FE5B8A270 | |||
| 3052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:7FB5FA1534DCF77F2125B2403B30A0EE | SHA256:33A39E9EC2133230533A686EC43760026E014A3828C703707ACBC150FE40FD6F | |||
| 3052 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\styles[1].css | text | |
MD5:0CEFB2A503915EC1A05603C3B30ACB70 | SHA256:E537A87B676EAC8644814D795E9369A00BF5544181F56F6E4CF7DDABF6D6AF82 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
55
DNS requests
28
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3052 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?30cdbbd33f011840 | unknown | — | — | whitelisted |
3052 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
3052 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9ddc32e441b27907 | unknown | — | — | whitelisted |
3052 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
3052 | iexplore.exe | GET | 200 | 104.110.191.177:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgNlby3FRLR0l62he2gW%2BYbFqQ%3D%3D | unknown | — | — | whitelisted |
3052 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDAezvzBOn2FxIghPLaMkP6 | unknown | — | — | whitelisted |
3052 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
3052 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEDW%2BdGOMs%2BneKAVwt5eAs2c%3D | unknown | — | — | whitelisted |
3052 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEFISB6AKY0OzCbS%2BEJ1LbPY%3D | unknown | — | — | whitelisted |
2712 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?52cc169ac156b656 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3052 | iexplore.exe | 104.19.223.79:443 | whatismyipaddress.com | CLOUDFLARENET | — | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3052 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3052 | iexplore.exe | 216.58.206.35:80 | c.pki.goog | GOOGLE | US | whitelisted |
3052 | iexplore.exe | 142.250.184.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
whatismyipaddress.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
c.pki.goog |
| whitelisted |
maps.whatismyipaddress.info |
| unknown |
cmp.inmobi.com |
| whitelisted |
a.pub.network |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
app.fusebox.fm |
| unknown |
a.omappapi.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
3052 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
3052 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
3052 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
1060 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
3052 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
3052 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
3052 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
2712 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
2712 | iexplore.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |