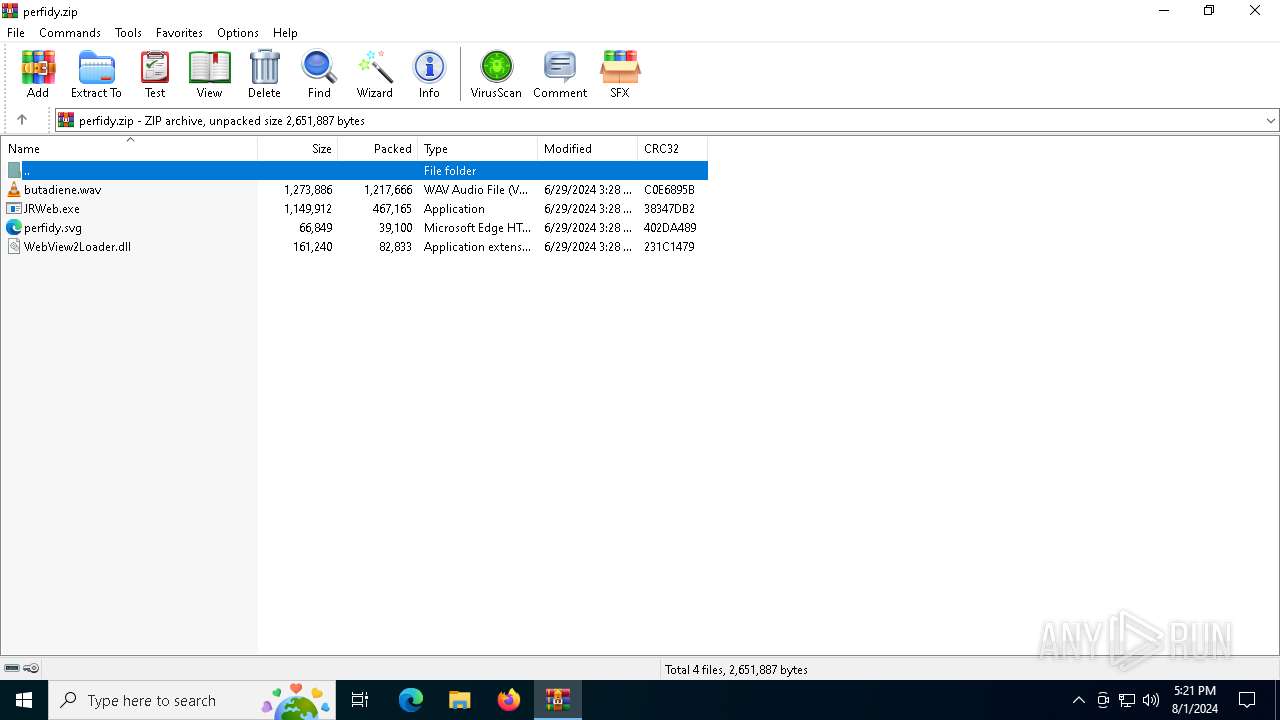
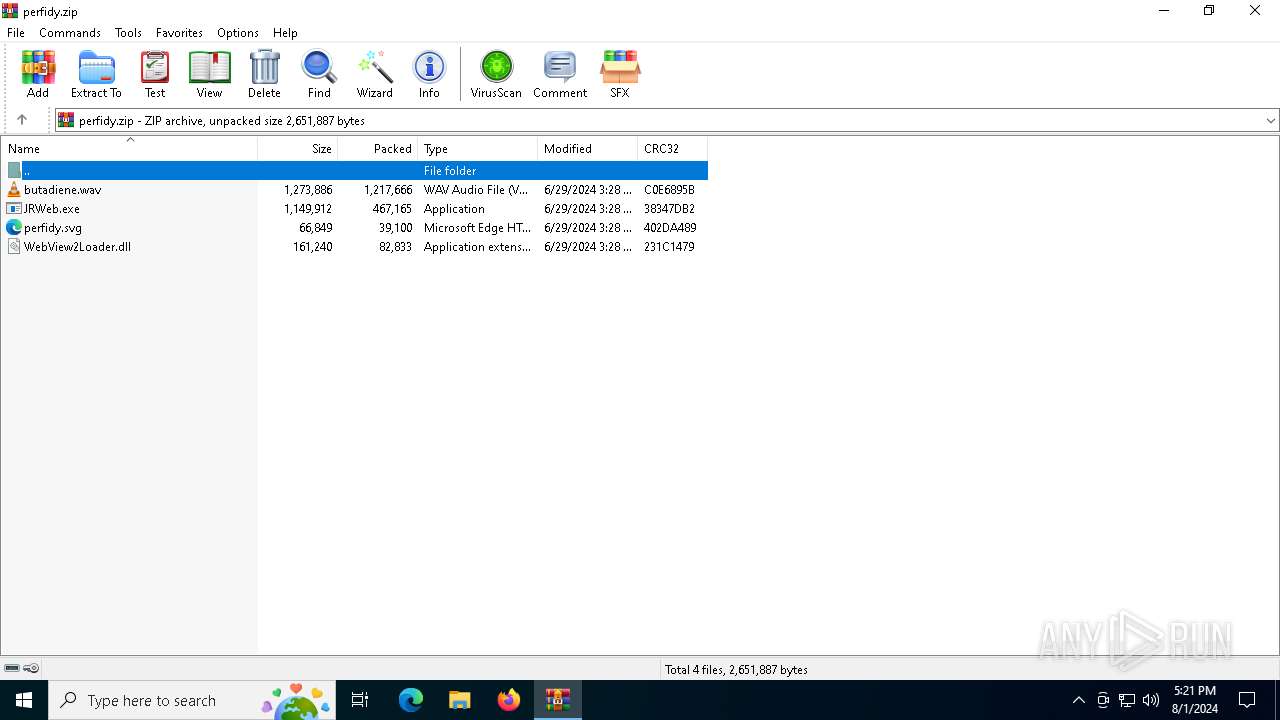
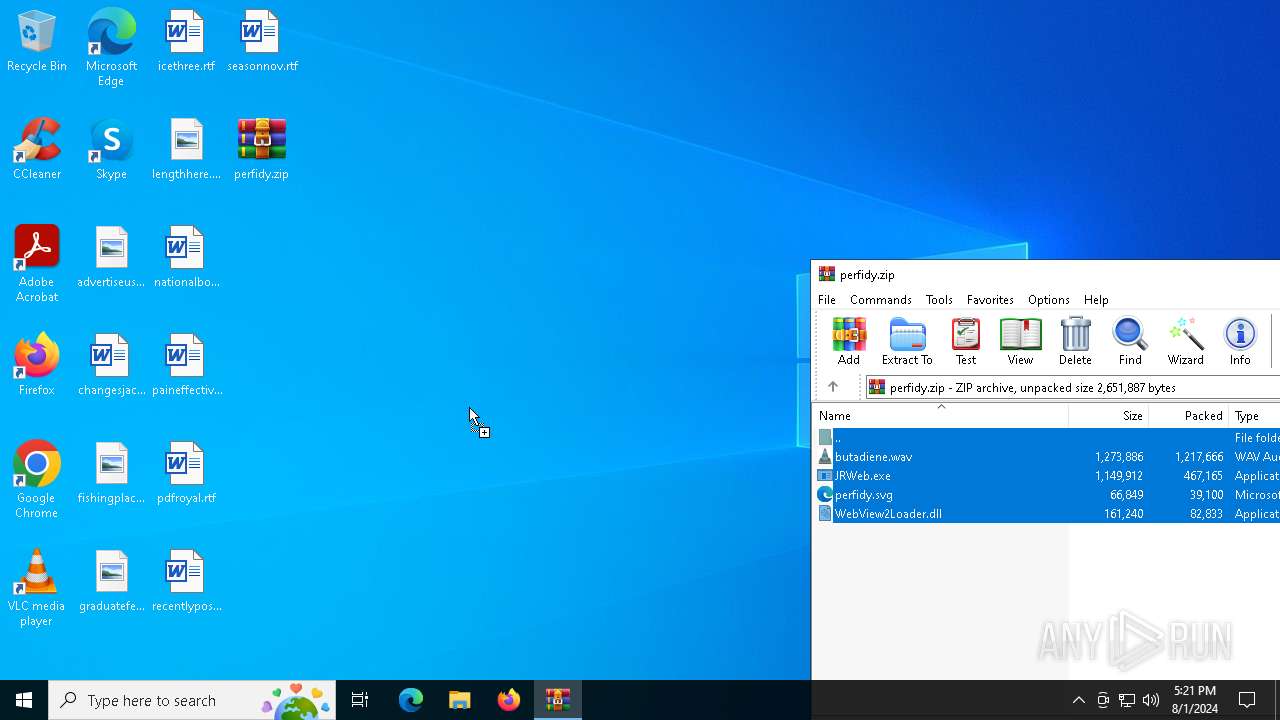
| File name: | perfidy.zip |
| Full analysis: | https://app.any.run/tasks/a1185d11-4689-428b-8a72-52ff21d46baf |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 17:21:44 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 117A616B839679188C818F5A423B53D4 |
| SHA1: | DBBC31A13BCDC55288AB373ED3821D740D07FD8B |
| SHA256: | 0C766AE0C5B45F9CDB0DF58372C287C95AE6B1FC00D8282807FDF7ECB6DADA39 |
| SSDEEP: | 98304:7uNEUvPUoFO9fiiasgyZkQqdYfQqaGkwfZupfMbbMEiLu+zyw1kdKACzb8ceRFTh:a+ |
MALICIOUS
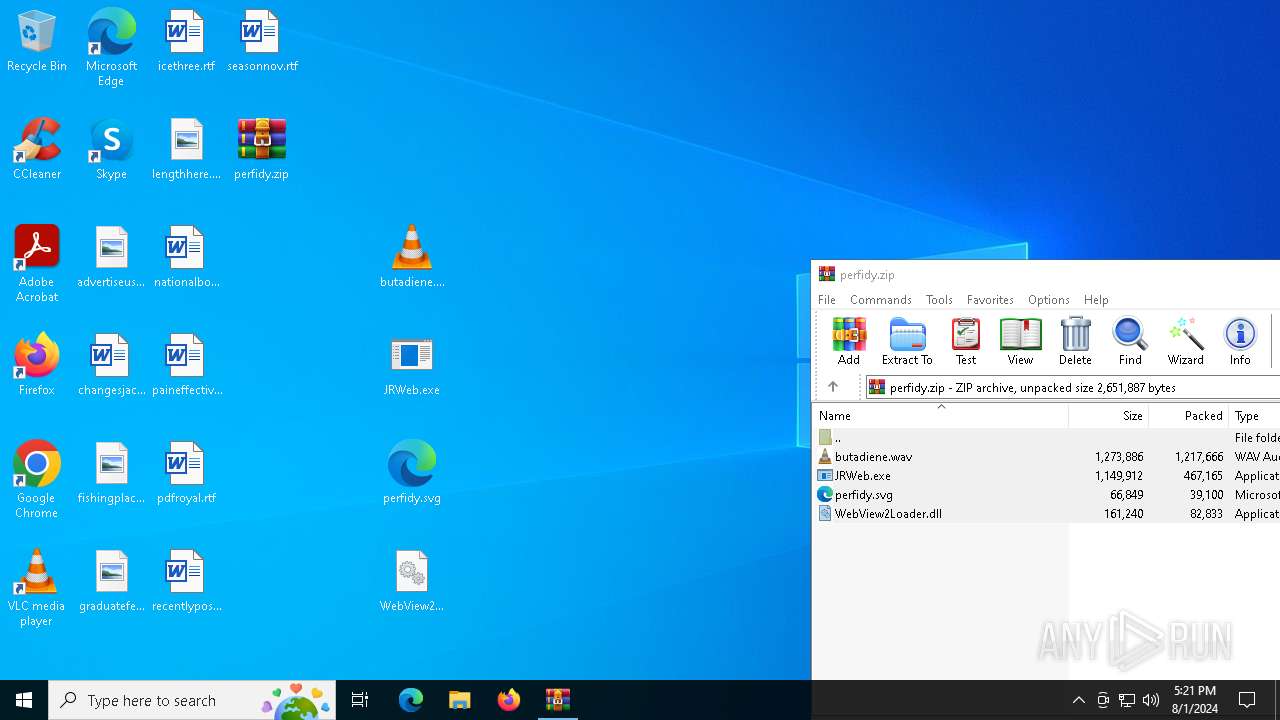
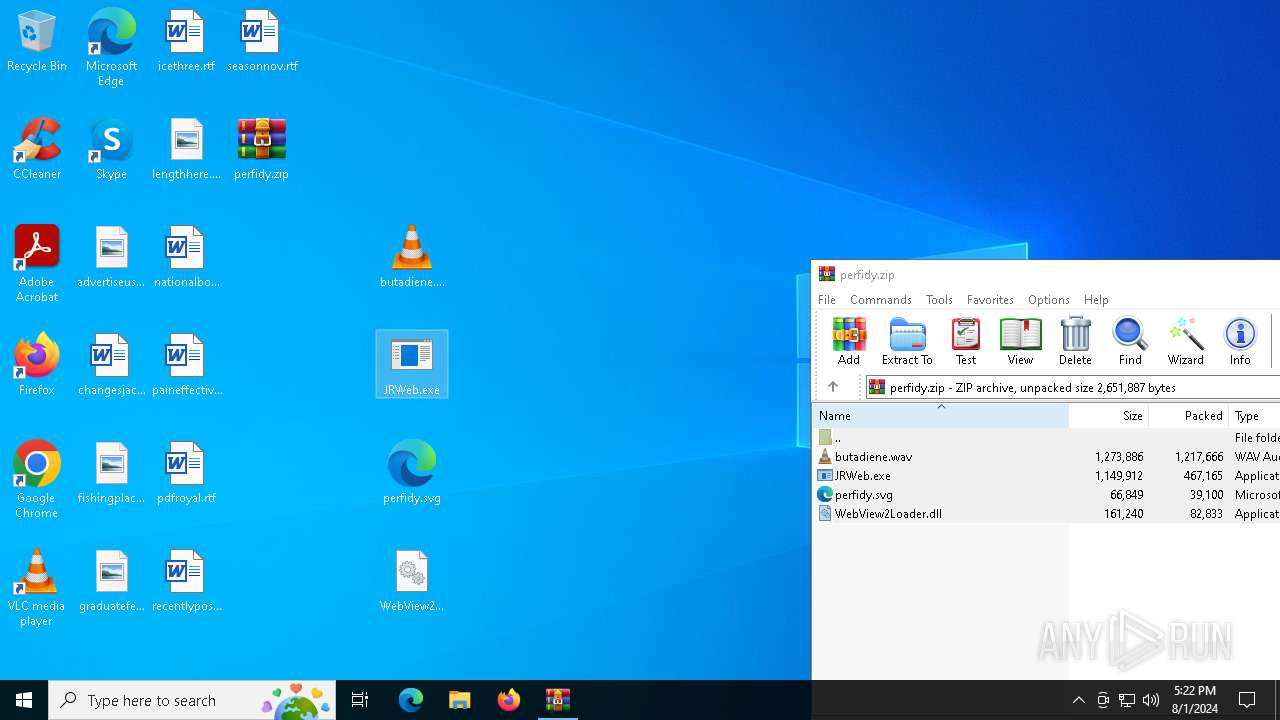
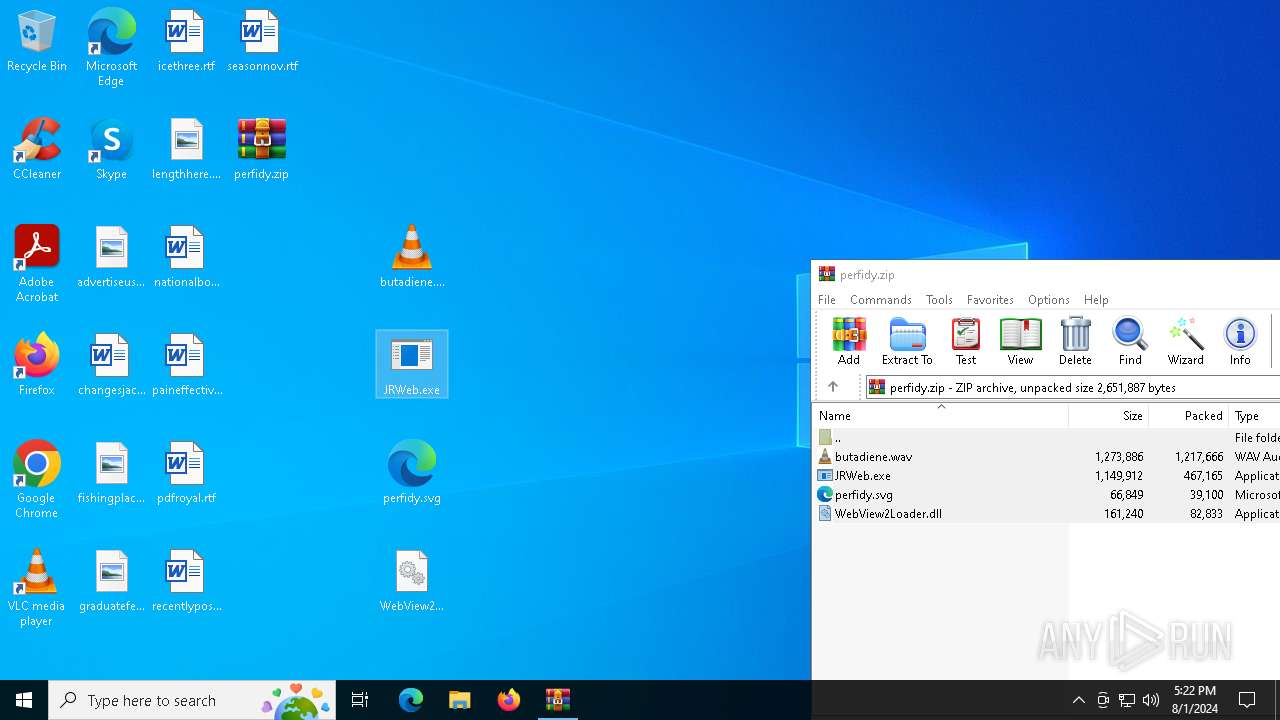
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6588)
- JRWeb.exe (PID: 7056)
- more.com (PID: 7100)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6588)
- JRWeb.exe (PID: 7056)
Executable content was dropped or overwritten
- JRWeb.exe (PID: 7056)
- more.com (PID: 7100)
Starts application with an unusual extension
- more.com (PID: 7100)
- JRWeb.exe (PID: 7076)
Starts itself from another location
- JRWeb.exe (PID: 7056)
Reads security settings of Internet Explorer
- VIDA.au3 (PID: 3992)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- VIDA.au3 (PID: 3992)
INFO
Creates files or folders in the user directory
- JRWeb.exe (PID: 7056)
Manual execution by a user
- JRWeb.exe (PID: 7056)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6588)
Checks supported languages
- JRWeb.exe (PID: 7056)
- VIDA.au3 (PID: 3992)
- JRWeb.exe (PID: 7076)
- more.com (PID: 7100)
Reads the computer name
- JRWeb.exe (PID: 7056)
- VIDA.au3 (PID: 3992)
- JRWeb.exe (PID: 7076)
- more.com (PID: 7100)
Create files in a temporary directory
- JRWeb.exe (PID: 7076)
- more.com (PID: 7100)
Creates files in the program directory
- VIDA.au3 (PID: 3992)
Checks proxy server information
- VIDA.au3 (PID: 3992)
Attempting to use instant messaging service
- VIDA.au3 (PID: 3992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:29 03:28:50 |
| ZipCRC: | 0xc0e6895b |
| ZipCompressedSize: | 1217666 |
| ZipUncompressedSize: | 1273886 |
| ZipFileName: | butadiene.wav |
Total processes
120
Monitored processes
6
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3992 | C:\Users\admin\AppData\Local\Temp\VIDA.au3 | C:\Users\admin\AppData\Local\Temp\VIDA.au3 | more.com | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 6588 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\perfidy.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7056 | "C:\Users\admin\Desktop\JRWeb.exe" | C:\Users\admin\Desktop\JRWeb.exe | explorer.exe | ||||||||||||
User: admin Company: JRiver, Inc. Integrity Level: MEDIUM Description: JRiver Web Application Exit code: 0 Version: 31.0.74.0 Modules
| |||||||||||||||
| 7076 | C:\Users\admin\AppData\Roaming\nodealt\JRWeb.exe | C:\Users\admin\AppData\Roaming\nodealt\JRWeb.exe | — | JRWeb.exe | |||||||||||
User: admin Company: JRiver, Inc. Integrity Level: MEDIUM Description: JRiver Web Application Exit code: 1 Version: 31.0.74.0 Modules
| |||||||||||||||
| 7100 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | JRWeb.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 293
Read events
4 274
Write events
19
Delete events
0
Modification events
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\perfidy.zip | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3992) VIDA.au3 | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3992) VIDA.au3 | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
5
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7100 | more.com | C:\Users\admin\AppData\Local\Temp\qmevgwlwjaltng | — | |
MD5:— | SHA256:— | |||
| 6588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6588.22949\JRWeb.exe | executable | |
MD5:C047AE13FC1E25BC494B17CA10AA179E | SHA256:6C30C8A2E827F48FCFC934DD34FB2CB10ACB8747FD11FAAE085D8AD352C01FBF | |||
| 7056 | JRWeb.exe | C:\Users\admin\AppData\Roaming\nodealt\perfidy.svg | binary | |
MD5:D7046DA347CD1C24F9AF82A326413734 | SHA256:580209F46352F01B832C81A836E72D05819D33502F51BDDA6212EEFE0B7675D6 | |||
| 7056 | JRWeb.exe | C:\Users\admin\AppData\Roaming\nodealt\JRWeb.exe | executable | |
MD5:C047AE13FC1E25BC494B17CA10AA179E | SHA256:6C30C8A2E827F48FCFC934DD34FB2CB10ACB8747FD11FAAE085D8AD352C01FBF | |||
| 6588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6588.22949\perfidy.svg | binary | |
MD5:D7046DA347CD1C24F9AF82A326413734 | SHA256:580209F46352F01B832C81A836E72D05819D33502F51BDDA6212EEFE0B7675D6 | |||
| 6588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6588.22949\WebView2Loader.dll | executable | |
MD5:4A99CB402C0D843B61A83015E0D3D731 | SHA256:4AE3F7437A6991DB64EAC8E5D2FA02E9EDCE56AD98AAA273006963FED39548A8 | |||
| 6588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6588.22949\butadiene.wav | binary | |
MD5:1ACF3A2FC94574480AEEAA875C041521 | SHA256:5C88B8BBEB0C631F7918C7E2CE9B1B7A90A84504639CF8D589D09C484625C6E2 | |||
| 7076 | JRWeb.exe | C:\Users\admin\AppData\Local\Temp\ca7c3584 | binary | |
MD5:C0B24D3A5C89E4E7C8636966407831D1 | SHA256:A27F183D00D66F5F0EC92EEE5E1A4D4B10C28A72D082F56865B4ABA532C58253 | |||
| 7056 | JRWeb.exe | C:\Users\admin\AppData\Roaming\nodealt\butadiene.wav | binary | |
MD5:1ACF3A2FC94574480AEEAA875C041521 | SHA256:5C88B8BBEB0C631F7918C7E2CE9B1B7A90A84504639CF8D589D09C484625C6E2 | |||
| 7056 | JRWeb.exe | C:\Users\admin\AppData\Roaming\nodealt\WebView2Loader.dll | executable | |
MD5:4A99CB402C0D843B61A83015E0D3D731 | SHA256:4AE3F7437A6991DB64EAC8E5D2FA02E9EDCE56AD98AAA273006963FED39548A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
3
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5600 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3992 | VIDA.au3 | 149.154.167.99:443 | t.me | Telegram Messenger Inc | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
t.me |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3992 | VIDA.au3 | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |