| File name: | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe |
| Full analysis: | https://app.any.run/tasks/93e56cc2-e519-471b-ac32-23a1fed2b12a |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2024, 23:32:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 044B5657529471E023EE2DA2DAD94CFA |
| SHA1: | 0F12B86643DD9261D030616FE73FEE8D927F1B32 |
| SHA256: | 0C6ED6426C29681B003B89BD43CB5A2CEB88D8EBB5A282A69FBA0694C00FAA5E |
| SSDEEP: | 393216:qI72l4zSmorkHQV2nq6AzpBku4rKcoSQjSUkRf:qIiiOrkHQV2nq5rMrKrS6SPF |
MALICIOUS
Drops the executable file immediately after the start
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
- Installer.exe (PID: 4216)
Steals credentials from Web Browsers
- Installer.exe (PID: 4216)
Actions looks like stealing of personal data
- Installer.exe (PID: 4216)
SUSPICIOUS
Process drops SQLite DLL files
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
Reads security settings of Internet Explorer
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
- Installer.exe (PID: 4216)
Executable content was dropped or overwritten
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
- Installer.exe (PID: 4216)
Checks Windows Trust Settings
- Installer.exe (PID: 4216)
Reads the BIOS version
- Installer.exe (PID: 4216)
Reads the Windows owner or organization settings
- Installer.exe (PID: 4216)
INFO
Process checks computer location settings
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
- Installer.exe (PID: 4216)
Checks supported languages
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
- Installer.exe (PID: 4216)
Create files in a temporary directory
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
- Installer.exe (PID: 4216)
Reads the computer name
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
- Installer.exe (PID: 4216)
Checks proxy server information
- 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe (PID: 6788)
- Installer.exe (PID: 4216)
Reads the machine GUID from the registry
- Installer.exe (PID: 4216)
Reads the software policy settings
- Installer.exe (PID: 4216)
- slui.exe (PID: 5344)
Creates files or folders in the user directory
- Installer.exe (PID: 4216)
Reads Windows Product ID
- Installer.exe (PID: 4216)
Creates files in the program directory
- Installer.exe (PID: 4216)
Reads Microsoft Office registry keys
- Installer.exe (PID: 4216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (79.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.9) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:01:04 23:51:25+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 143872 |
| InitializedDataSize: | 330240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x24530 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.7.242.28648 |
| ProductVersionNumber: | 1.7.242.28648 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
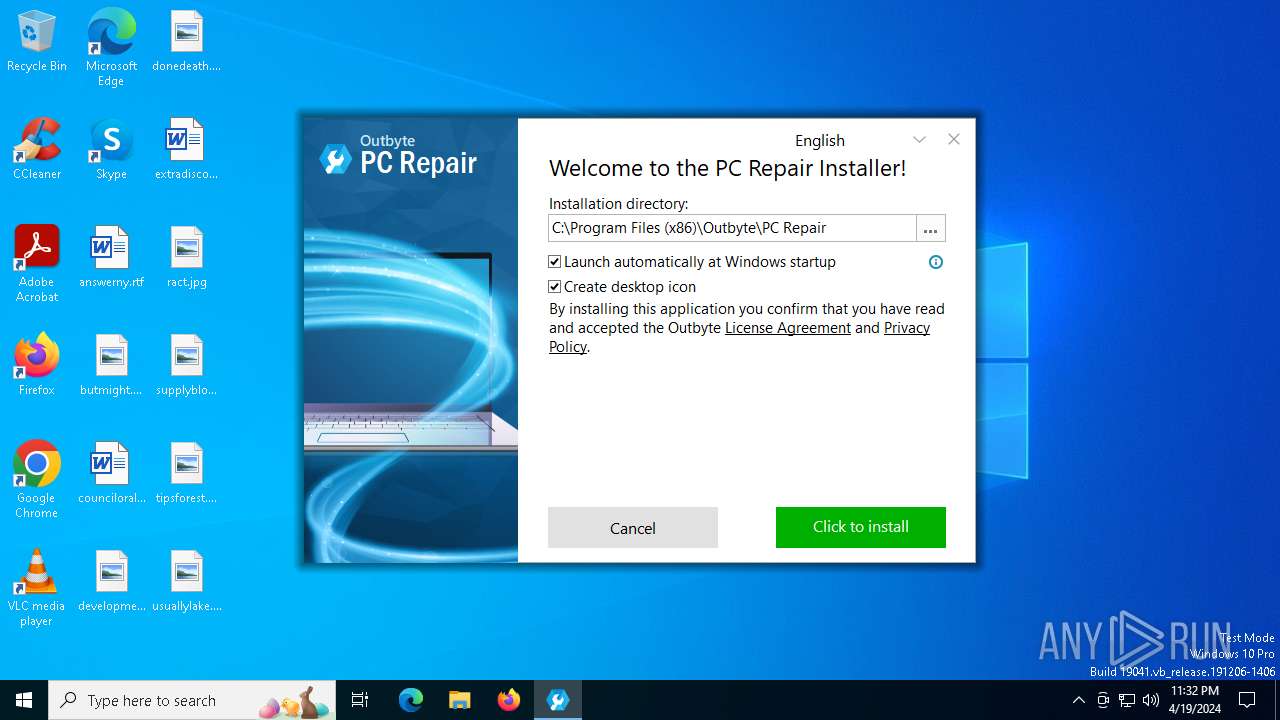
| Comments: | PC Repair |
| CompanyName: | Outbyte |
| FileDescription: | Outbyte PC Repair Installation File |
| FileVersion: | 1.7.242.28648 |
| LegalCopyright: | Copyright © 2016-2024 Outbyte Computing Pty Ltd |
| OriginalFileName: | Outbyte-pc-repair-setup.exe |
| ProductName: | PC Repair |
| ProductVersion: | 1.x |
Total processes
127
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2000 | "C:\Users\admin\AppData\Local\Temp\0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe" | C:\Users\admin\AppData\Local\Temp\0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | — | explorer.exe | |||||||||||
User: admin Company: Outbyte Integrity Level: MEDIUM Description: Outbyte PC Repair Installation File Exit code: 3221226540 Version: 1.7.242.28648 Modules
| |||||||||||||||
| 2012 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4216 | "C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Installer.exe" /spid:6788 /splha:37200704 | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Installer.exe | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | ||||||||||||
User: admin Company: Outbyte Integrity Level: HIGH Description: Installer Version: 1.7.242.28648 Modules
| |||||||||||||||
| 4612 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5344 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | "C:\Users\admin\AppData\Local\Temp\0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe" | C:\Users\admin\AppData\Local\Temp\0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | explorer.exe | ||||||||||||
User: admin Company: Outbyte Integrity Level: HIGH Description: Outbyte PC Repair Installation File Version: 1.7.242.28648 Modules
| |||||||||||||||
Total events
10 184
Read events
10 141
Write events
43
Delete events
0
Modification events
| (PID) Process: | (6788) 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\PC Repair\1.x\Settings |
| Operation: | write | Name: | General.CustomClientId |
Value: 1036007967.981010011572 | |||
| (PID) Process: | (6788) 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\PC Repair\1.x\Settings |
| Operation: | write | Name: | General.URLClientId |
Value: 1036007967.981010011572 | |||
| (PID) Process: | (6788) 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6788) 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6788) 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4216) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{6D484312-05A6-96B5-2103-32846EE2CF0B}\Version |
| Operation: | write | Name: | Assembly |
Value: 3D817AA9BB848ED0E896232FE2910D8C3D817AA9BB848ED0E896232FE2910D8C88AD8CBB5ED3F66B83A8A2CDF194269C890BB34AEBD806E41A50D3BD9C0B4765219909F09E75DEC0927FF4E8152284CD219909F09E75DEC0927FF4E8152284CD59B5414605BAE21E9735786EB516D3F8DE1283C2AFF9BF99D33ED2740C86BBD2F8157495FE950FA4A01046BB55F00DAD0F20AA1B1ADFE602954529934D03147D | |||
| (PID) Process: | (4216) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\PC Repair\1.x\Settings |
| Operation: | write | Name: | General.TrackingIV.CID |
Value: 1719231800.1713569563 | |||
| (PID) Process: | (4216) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\PC Repair\1.x\Settings |
| Operation: | write | Name: | General.TrackingIV.SID |
Value: dBoaCjcc0V | |||
| (PID) Process: | (4216) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\PC Repair\1.x\Settings |
| Operation: | write | Name: | Application.GAIV.FunnelDate |
Value: CE04D7643F2BE640 | |||
| (PID) Process: | (4216) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\PC Repair\1.x\Settings |
| Operation: | write | Name: | General.Language |
Value: ENU | |||
Executable files
17
Suspicious files
21
Text files
1
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\SetupHelper.dll | executable | |
MD5:5FF89E1E693481156D601F1FF5A48A02 | SHA256:1A0EDD4BE6F74B1D8A996E27CE7DB50A7992B496270D924426FAC251833F3735 | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Lang\ita.lng | binary | |
MD5:5994A2EF0127AE4412C47E29CF254879 | SHA256:25BDD6871F8ACBEE1D406065FC95795F7C2311DA0D14AFACB701B32DEBDFA67E | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\InstallerUtils.dll | executable | |
MD5:F67E9ED9D329D6FA58DDCBAF8908C9D2 | SHA256:F5DB91B086AB2ECD3EC592E496DD2E912B3C6392AEF839219AFE8CE359DAF435 | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Lang\rus.lng | binary | |
MD5:F4B3DDA42B6B6009ADBAB38123F44E61 | SHA256:3CA7A122D8DC1141F046C32C7F6BF1CFC3923FCD58297E79FF5CE3718724F37F | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Lang\plk.lng | binary | |
MD5:DB1D15C2804D32279968330EA0AFC616 | SHA256:DB8A61756C371C76F8AD4B1DA88FA7B91CF9F4B548B12B014C13F72A14B424CF | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Lang\enu.lng | binary | |
MD5:3EA629679D7C0A5884898F74773C0F7E | SHA256:2DAB13DD98E252F4CA38FFFC32F5EDC54AA19B7FDA601C02C97D6D80B70F8777 | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Lang\dan.lng | binary | |
MD5:9291C0B3EED2E4FD8747B75958AFCE3B | SHA256:2CAB2DD825E26FAE7B4F9C813A13ED610D408718848205AE32EAD769E2933A8C | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Lang\deu.lng | binary | |
MD5:B1202F383797E6A8A38419016F5906B2 | SHA256:9580897707DC8024470BED4C030C602784D27D8E7A1B4C4D1EF9D7B31C9B9486 | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Lang\trk.lng | binary | |
MD5:B32E87588CE1CE710FE6E26C82F0E260 | SHA256:6498487C9B065A5276759B854C502FB7EE69653DAD8421BC7D8A25E9A556ED30 | |||
| 6788 | 0c6ed6426c29681b003b89bd43cb5a2ceb88d8ebb5a282a69fba0694c00faa5e.exe | C:\Users\admin\AppData\Local\Temp\is-1209004.tmp\Installer.exe | binary | |
MD5:C8FCCE141F1A49CB00D6E3425344FCB7 | SHA256:7AF4101DD2C1CCDEF5F1F81D70A8B956C13156D238AF5704BA5A9D510BAE2AD7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
37
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
984 | SIHClient.exe | GET | 200 | 23.214.173.122:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2980 | svchost.exe | GET | 200 | 23.214.173.122:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | unknown |
2980 | svchost.exe | GET | 200 | 23.214.173.122:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.3.crl | unknown | — | — | unknown |
2980 | svchost.exe | GET | 200 | 23.214.173.122:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2980 | svchost.exe | GET | 200 | 23.214.173.122:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | unknown |
2980 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
2980 | svchost.exe | GET | 200 | 23.214.173.122:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
6416 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4216 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | unknown |
4216 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4008 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6968 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5152 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6416 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6416 | svchost.exe | 192.229.221.95:80 | status.rapidssl.com | EDGECAST | US | whitelisted |
4216 | Installer.exe | 192.229.221.95:80 | status.rapidssl.com | EDGECAST | US | whitelisted |
4216 | Installer.exe | 45.33.97.245:443 | outbyte.com | Linode, LLC | US | unknown |
4216 | Installer.exe | 172.217.18.14:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
outbyte.com |
| unknown |
status.rapidssl.com |
| shared |
www.google-analytics.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |