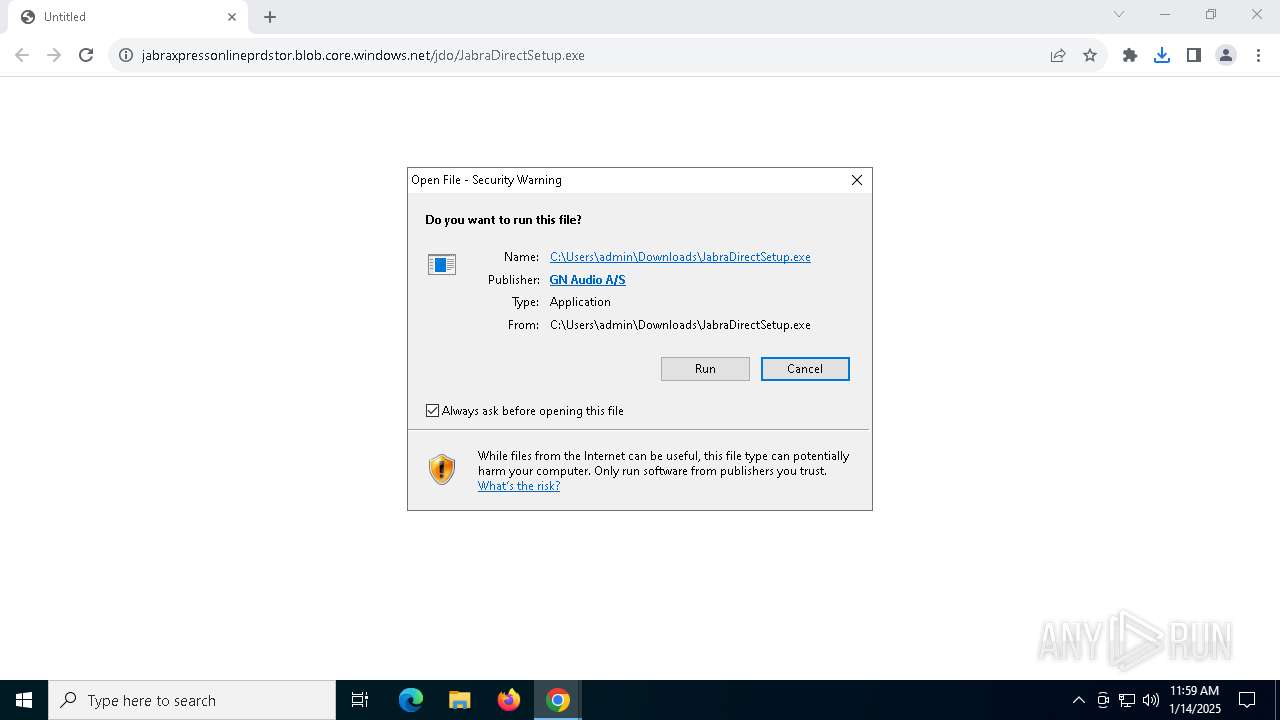
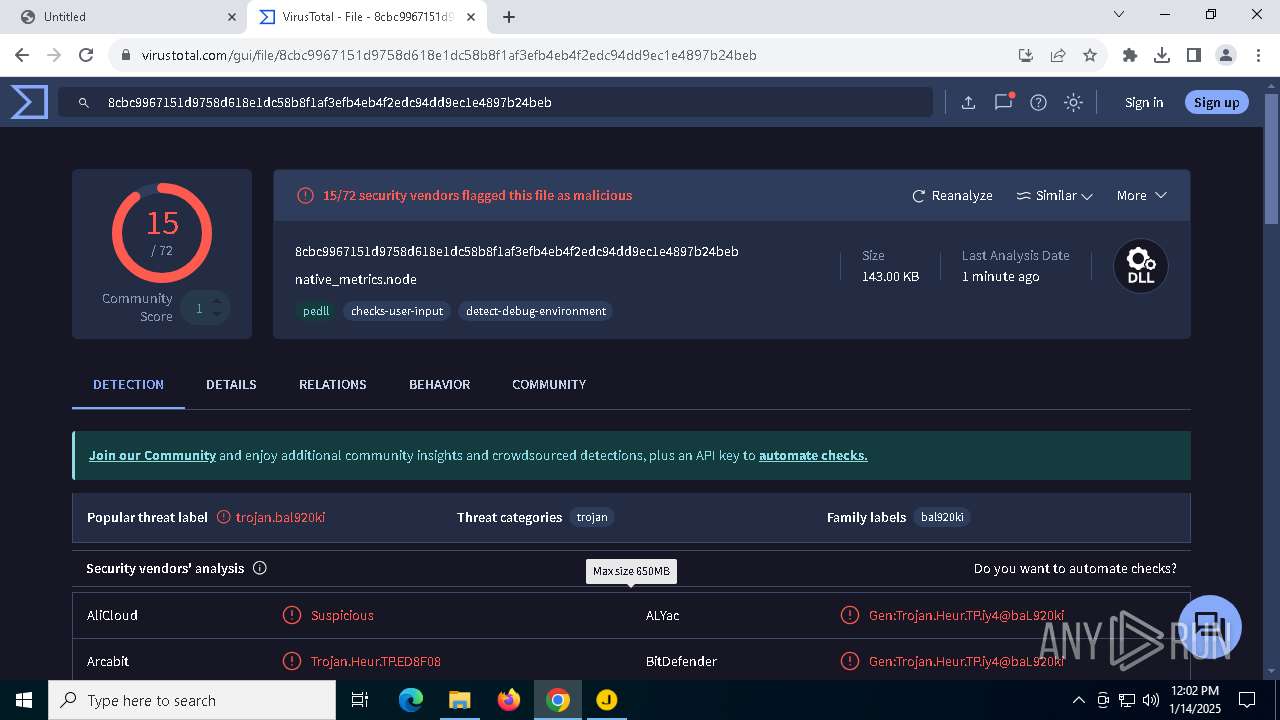
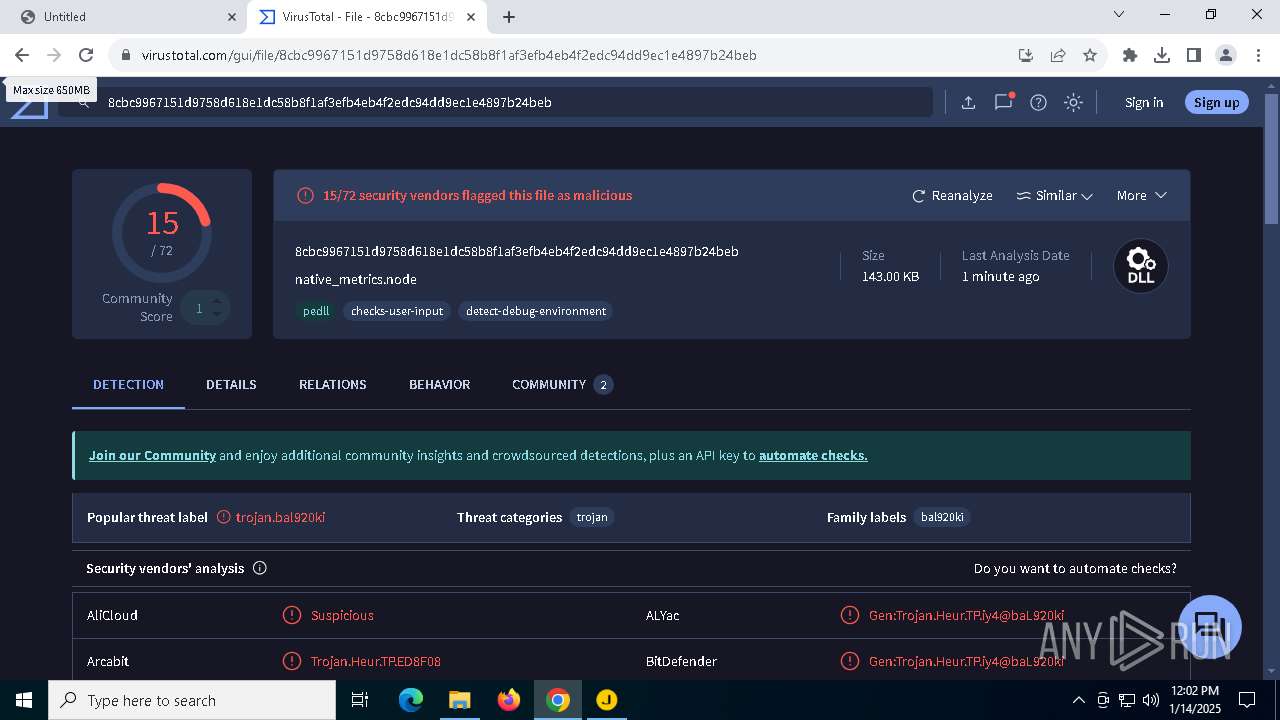
| URL: | https://jabraxpressonlineprdstor.blob.core.windows.net/jdo/JabraDirectSetup.exe |
| Full analysis: | https://app.any.run/tasks/3a037efe-1294-4873-9290-40581863877a |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2025, 11:58:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C7D1B49DF76251725E73EAD3BEE4FE1E |
| SHA1: | 887D6C525434BA504459AF734EE0DC214A97903D |
| SHA256: | 0C487829A3AB9491DE1AF4A5260624E1115124980D957DF0FE07318D811AAA2B |
| SSDEEP: | 3:N80E9AyMmF4GwYWadA:2p9AfUWIA |
MALICIOUS
Changes the autorun value in the registry
- JabraDirectSetup.exe (PID: 2008)
SUSPICIOUS
Executable content was dropped or overwritten
- JabraDirectSetup.exe (PID: 4444)
- JabraDirectSetup.exe (PID: 2144)
- JabraDirectSetup.exe (PID: 2008)
- rundll32.exe (PID: 5536)
- drvinst.exe (PID: 900)
Searches for installed software
- JabraDirectSetup.exe (PID: 2144)
Reads security settings of Internet Explorer
- JabraDirectSetup.exe (PID: 2144)
- SoftphoneIntegrations.exe (PID: 7248)
Starts itself from another location
- JabraDirectSetup.exe (PID: 2144)
Executes as Windows Service
- VSSVC.exe (PID: 396)
Creates a software uninstall entry
- JabraDirectSetup.exe (PID: 2008)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1076)
Checks Windows Trust Settings
- msiexec.exe (PID: 1076)
- SoftphoneIntegrations.exe (PID: 7248)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 4672)
The process drops C-runtime libraries
- msiexec.exe (PID: 1076)
Process drops legitimate windows executable
- msiexec.exe (PID: 1076)
Suspicious use of NETSH.EXE
- msiexec.exe (PID: 3816)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 1076)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 1076)
- drvinst.exe (PID: 900)
Starts CMD.EXE for commands execution
- jabra-direct.exe (PID: 3992)
- cmd.exe (PID: 5160)
Application launched itself
- jabra-direct.exe (PID: 3992)
INFO
The process uses the downloaded file
- chrome.exe (PID: 4076)
- chrome.exe (PID: 4592)
- JabraDirectSetup.exe (PID: 2144)
- SoftphoneIntegrations.exe (PID: 7248)
Application launched itself
- chrome.exe (PID: 4076)
- msiexec.exe (PID: 1076)
Checks supported languages
- JabraDirectSetup.exe (PID: 4444)
- JabraDirectSetup.exe (PID: 2144)
- msiexec.exe (PID: 1076)
- msiexec.exe (PID: 7112)
- msiexec.exe (PID: 4672)
- msiexec.exe (PID: 3816)
- msiexec.exe (PID: 5572)
- jabra-direct.exe (PID: 3992)
- jabra-direct.exe (PID: 1220)
- ShellExperienceHost.exe (PID: 6424)
- SoftphoneIntegrations.exe (PID: 7248)
- jabra-direct.exe (PID: 6868)
- jabra-direct.exe (PID: 7040)
The sample compiled with english language support
- JabraDirectSetup.exe (PID: 2144)
- JabraDirectSetup.exe (PID: 4444)
- JabraDirectSetup.exe (PID: 2008)
- msiexec.exe (PID: 1076)
- drvinst.exe (PID: 900)
Create files in a temporary directory
- JabraDirectSetup.exe (PID: 4444)
- JabraDirectSetup.exe (PID: 2144)
Reads the computer name
- JabraDirectSetup.exe (PID: 2144)
- JabraDirectSetup.exe (PID: 2008)
- msiexec.exe (PID: 1076)
- msiexec.exe (PID: 7112)
- msiexec.exe (PID: 4672)
- msiexec.exe (PID: 3816)
- msiexec.exe (PID: 5572)
- jabra-direct.exe (PID: 3992)
- jabra-direct.exe (PID: 6304)
Executable content was dropped or overwritten
- chrome.exe (PID: 4076)
- msiexec.exe (PID: 1076)
Process checks computer location settings
- JabraDirectSetup.exe (PID: 2144)
- jabra-direct.exe (PID: 7040)
- jabra-direct.exe (PID: 3992)
Manages system restore points
- SrTasks.exe (PID: 3988)
Reads the software policy settings
- msiexec.exe (PID: 1076)
- drvinst.exe (PID: 900)
- SoftphoneIntegrations.exe (PID: 7248)
Reads the machine GUID from the registry
- msiexec.exe (PID: 1076)
- drvinst.exe (PID: 900)
- jabra-direct.exe (PID: 3992)
- SoftphoneIntegrations.exe (PID: 7248)
Creates a software uninstall entry
- msiexec.exe (PID: 1076)
Creates files in the program directory
- JabraDirectSetup.exe (PID: 2008)
The sample compiled with czech language support
- msiexec.exe (PID: 1076)
Creates files or folders in the user directory
- jabra-direct.exe (PID: 3992)
- jabra-direct.exe (PID: 3824)
- SoftphoneIntegrations.exe (PID: 7248)
Checks proxy server information
- jabra-direct.exe (PID: 3992)
Sends debugging messages
- ShellExperienceHost.exe (PID: 6424)
- SoftphoneIntegrations.exe (PID: 7248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
208
Monitored processes
67
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | DrvInst.exe "4" "1" "C:\Program Files (x86)\Jabra\Drivers\DFU Drivers\CSR_Win10\JabraBcDfu.inf" "9" "44c606253" "00000000000001DC" "WinSta0\Default" "00000000000001EC" "208" "C:\Program Files (x86)\Jabra\Drivers\DFU Drivers\CSR_Win10" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | C:\WINDOWS\System32\REG.exe QUERY HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography /v MachineGuid | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1220 | "C:\Program Files (x86)\Jabra\Direct6\jabra-direct.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Jabra Direct" --app-user-model-id=com.jabra.directonline --app-path="C:\Program Files (x86)\Jabra\Direct6\resources\app.asar" --no-sandbox --no-zygote --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --field-trial-handle=2956,i,13984941643765754044,17248912459374736830,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2952 /prefetch:1 | C:\Program Files (x86)\Jabra\Direct6\jabra-direct.exe | — | jabra-direct.exe | |||||||||||
User: admin Company: GN Audio A/S Integrity Level: MEDIUM Description: Jabra Direct Version: 6.20.34801 Modules
| |||||||||||||||
| 1536 | "C:\WINDOWS\\System32\taskkill.exe" /F /IM jabra-direct.exe | C:\Windows\SysWOW64\taskkill.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | "C:\Users\admin\AppData\Local\Temp\{85BEDCBD-EA5F-47A8-8907-FBA23CAB2760}\.be\JabraDirectSetup.exe" -q -burn.elevated BurnPipe.{351B5C1C-B379-4114-BE80-BEB506BBC029} {8B1367FB-74EB-4168-89D0-C30993EBC521} 2144 | C:\Users\admin\AppData\Local\Temp\{85BEDCBD-EA5F-47A8-8907-FBA23CAB2760}\.be\JabraDirectSetup.exe | JabraDirectSetup.exe | ||||||||||||
User: admin Company: GN Audio A/S Integrity Level: HIGH Description: Jabra Direct Exit code: 0 Version: 6.20.34801 Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\AppData\Local\Temp\{430F4D74-F81C-420A-877D-8FA948322B57}\.cr\JabraDirectSetup.exe" -burn.clean.room="C:\Users\admin\Downloads\JabraDirectSetup.exe" -burn.filehandle.attached=556 -burn.filehandle.self=664 | C:\Users\admin\AppData\Local\Temp\{430F4D74-F81C-420A-877D-8FA948322B57}\.cr\JabraDirectSetup.exe | JabraDirectSetup.exe | ||||||||||||
User: admin Company: GN Audio A/S Integrity Level: MEDIUM Description: Jabra Direct Exit code: 0 Version: 6.20.34801 Modules
| |||||||||||||||
| 2164 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5576 --field-trial-handle=1924,i,5200075701657842766,625030961931294956,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3436 | C:\Windows\System32\MsiExec.exe -Embedding CC583B795FB99DA54389B42E2FC17EE2 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
44 281
Read events
42 986
Write events
1 195
Delete events
100
Modification events
| (PID) Process: | (4076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4076) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4592) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000086A30CB87B66DB01 | |||
| (PID) Process: | (6856) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000EB8888C07B66DB01C81A000070130000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6856) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000000F21C4C07B66DB01C81A000070130000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (396) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C4C23DC17B66DB018C010000301B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (396) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000002A2640C17B66DB018C010000C0190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
234
Suspicious files
682
Text files
72
Unknown types
64
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF13696b.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF13697b.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF13698b.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF13698b.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF13698b.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
125
DNS requests
121
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6180 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4076 | chrome.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
4076 | chrome.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6916 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4076 | chrome.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA4qYcIKPG%2FTjQFkjSXGTg0%3D | unknown | — | — | whitelisted |
4576 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fw4ggtylvtq6i65ti33m4vqijm_2024.12.14.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.12.14.01_all_e3s3pxuydvrca43mi6hdgphvru.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2220 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4076 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
jabraxpressonlineprdstor.blob.core.windows.net |
| whitelisted |
accounts.google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6432 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |
6432 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |
3824 | jabra-direct.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |
3824 | jabra-direct.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |
Process | Message |
|---|---|
SoftphoneIntegrations.exe | UsbDeviceScanner.Start Starting scanner
|
SoftphoneIntegrations.exe | UsbDeviceScanner.Start Scanner started
|