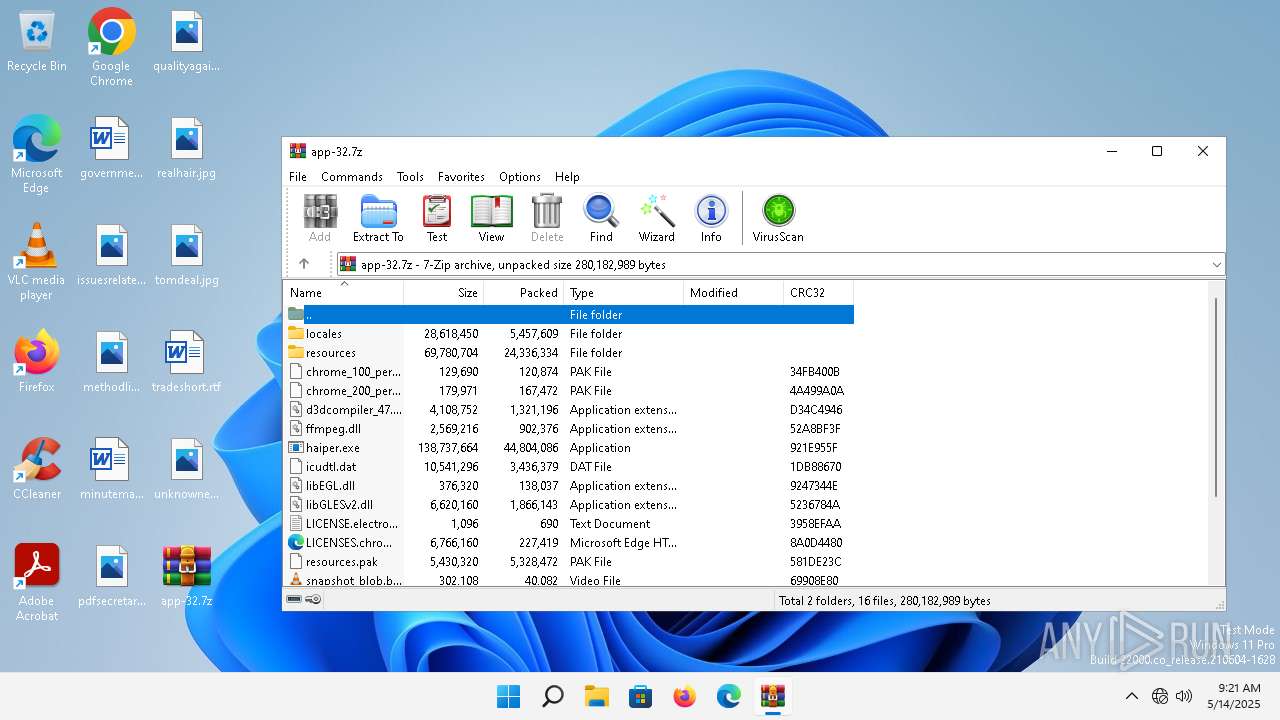
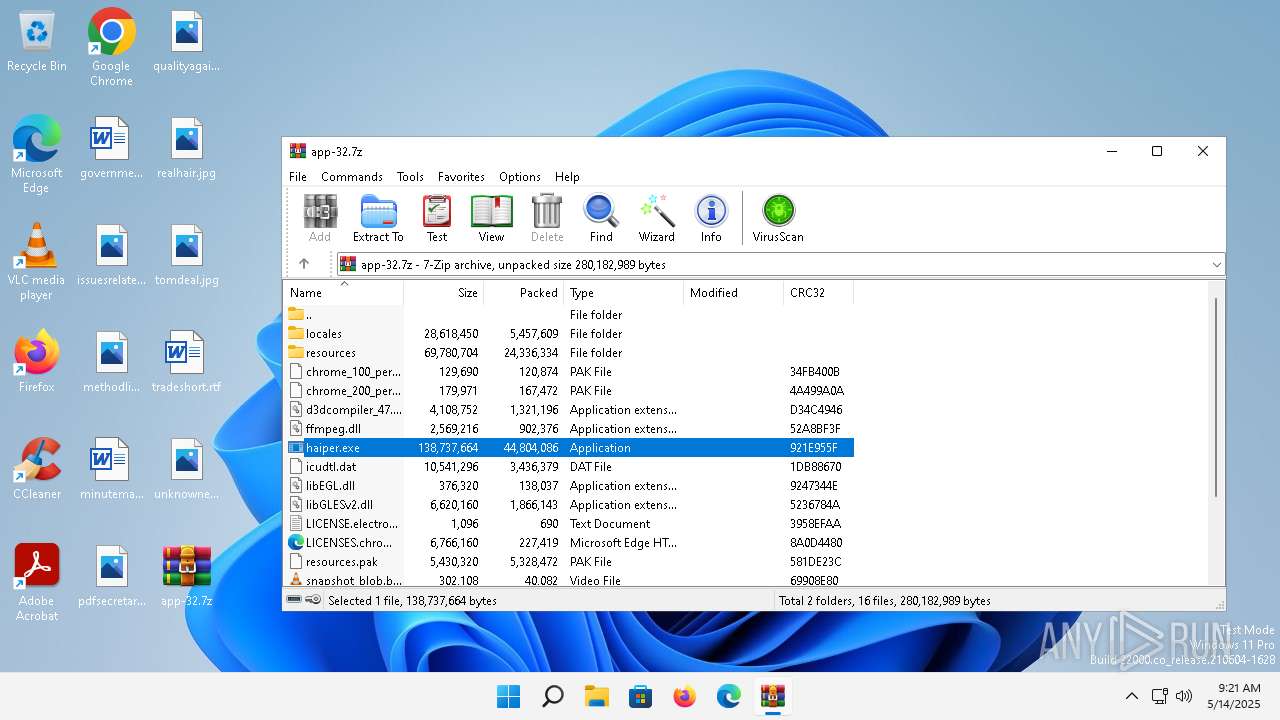
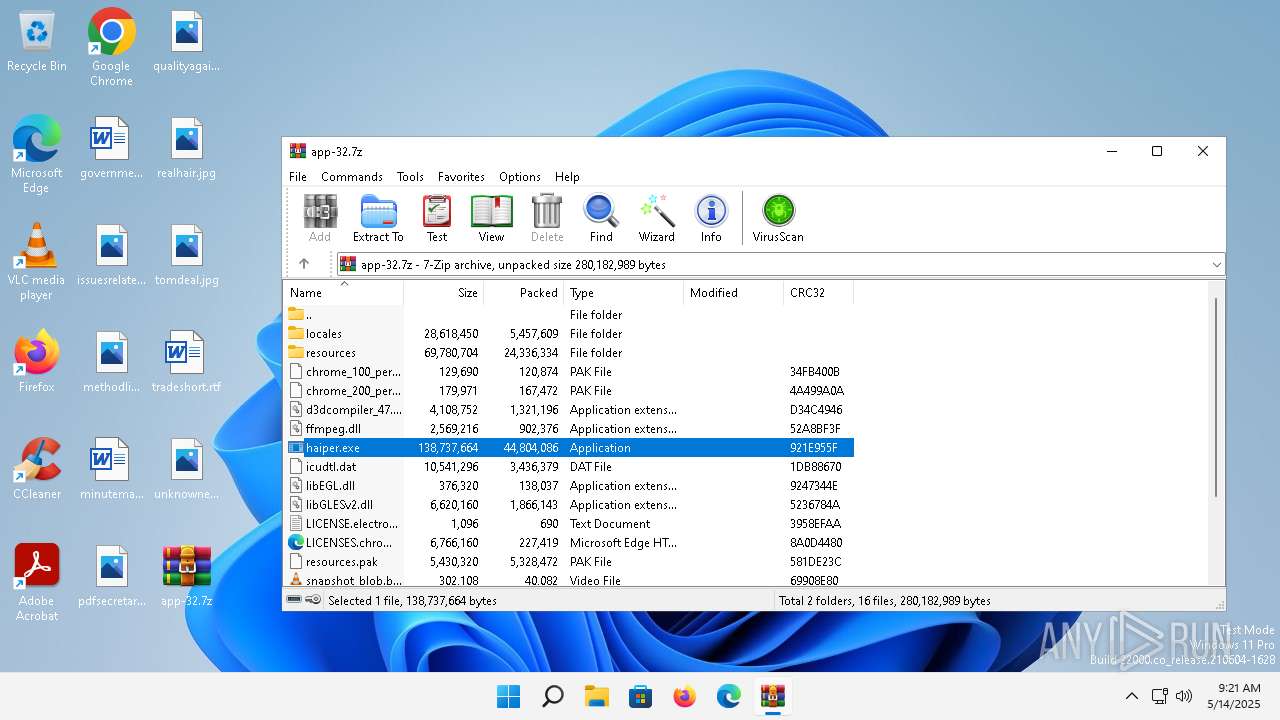
| File name: | app-32.7z |
| Full analysis: | https://app.any.run/tasks/608316c5-3c60-48d2-936f-7224042c39da |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2025, 09:20:33 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 76ED5C32835C7CFC57674C3F70BC0242 |
| SHA1: | A8E7D5F7BC79C04C86836883106EA96DC320903E |
| SHA256: | 0C202337D3FAA9FAFFE2E0930F22382B4B43C8EC34BBF6BCA5E2053954BABED7 |
| SSDEEP: | 1572864:LxvfDp271oX1fLj1W/ULya91fPiQJbHakJ:lHDp2hSVlW/AiQJbHVJ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3460)
SUSPICIOUS
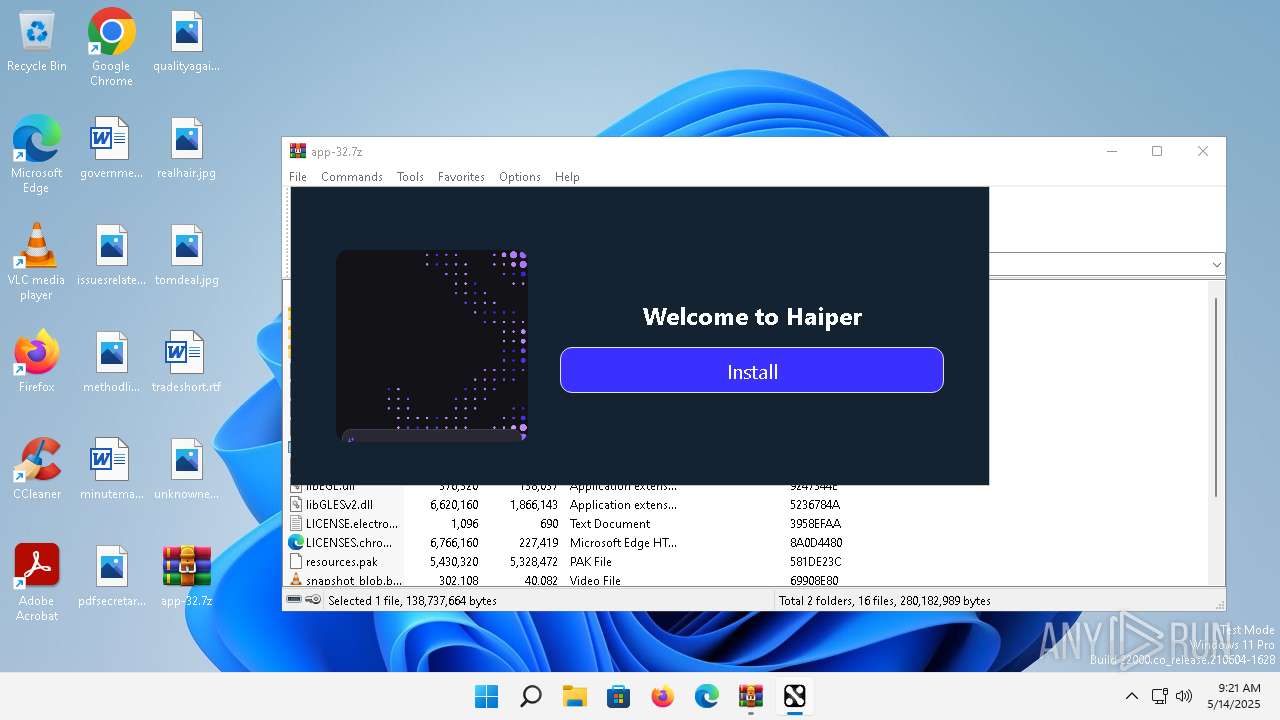
Process drops legitimate windows executable
- WinRAR.exe (PID: 3460)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3460)
Reads the Internet Settings
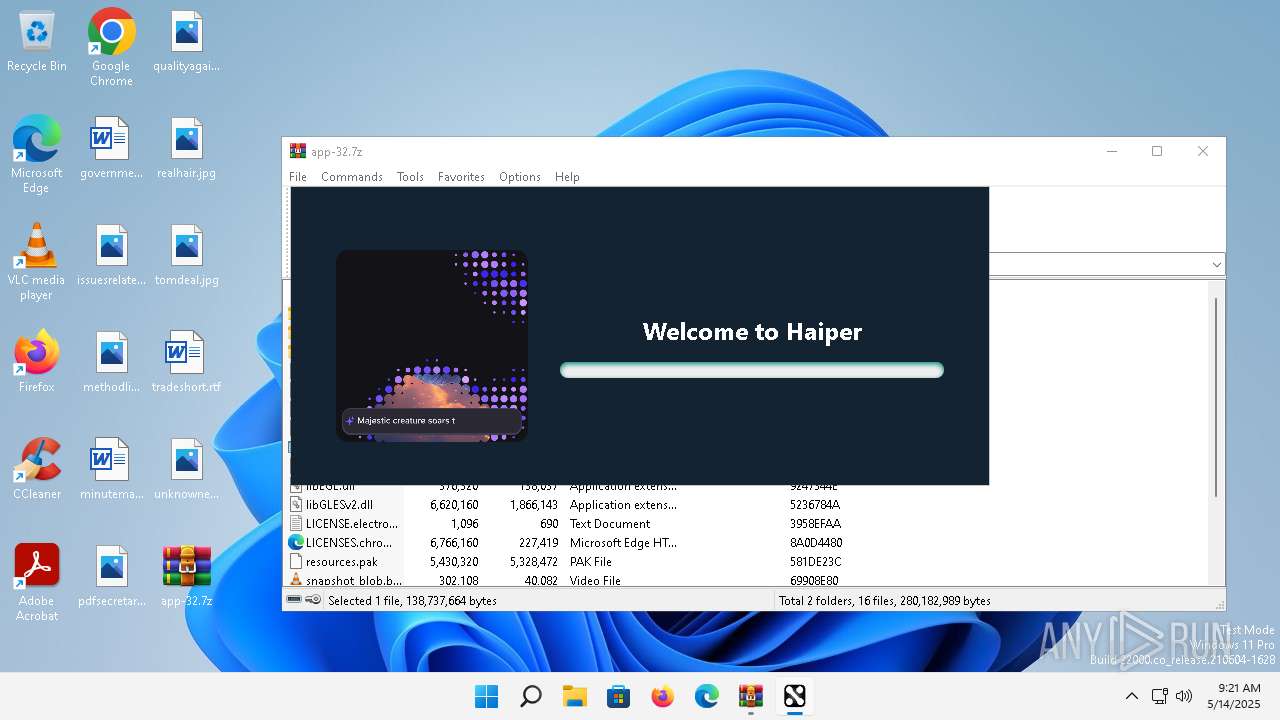
- haiper.exe (PID: 3944)
Application launched itself
- haiper.exe (PID: 3944)
Reads settings of System Certificates
- haiper.exe (PID: 3944)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3460)
The sample compiled with english language support
- WinRAR.exe (PID: 3460)
Checks supported languages
- haiper.exe (PID: 3944)
- haiper.exe (PID: 1944)
- haiper.exe (PID: 4908)
- haiper.exe (PID: 4832)
Reads the computer name
- haiper.exe (PID: 1944)
- haiper.exe (PID: 3944)
- haiper.exe (PID: 4908)
Checks proxy server information
- haiper.exe (PID: 3944)
Creates files or folders in the user directory
- haiper.exe (PID: 3944)
- haiper.exe (PID: 4908)
Reads the machine GUID from the registry
- haiper.exe (PID: 3944)
Create files in a temporary directory
- haiper.exe (PID: 3944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
106
Monitored processes
6
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1944 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\default" --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1592 --field-trial-handle=1636,i,12779782897818529924,16558881945362708231,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:2 | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe | — | haiper.exe | |||||||||||
User: admin Company: haiper App Integrity Level: LOW Description: haiper Exit code: 0 Version: 1.8.2 Modules
| |||||||||||||||
| 3424 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe | — | WinRAR.exe | |||||||||||
User: admin Company: haiper App Integrity Level: MEDIUM Description: haiper Exit code: 3221226540 Version: 1.8.2 Modules
| |||||||||||||||
| 3460 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\app-32.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3944 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe | WinRAR.exe | ||||||||||||
User: admin Company: haiper App Integrity Level: HIGH Description: haiper Exit code: 0 Version: 1.8.2 Modules
| |||||||||||||||
| 4832 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\default" --app-path="C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\resources\app.asar" --no-sandbox --no-zygote --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=2956 --field-trial-handle=1636,i,12779782897818529924,16558881945362708231,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe | — | haiper.exe | |||||||||||
User: admin Company: haiper App Integrity Level: HIGH Description: haiper Exit code: 0 Version: 1.8.2 Modules
| |||||||||||||||
| 4908 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\default" --mojo-platform-channel-handle=2052 --field-trial-handle=1636,i,12779782897818529924,16558881945362708231,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\haiper.exe | haiper.exe | ||||||||||||
User: admin Company: haiper App Integrity Level: HIGH Description: haiper Exit code: 0 Version: 1.8.2 Modules
| |||||||||||||||
Total events
5 777
Read events
5 742
Write events
17
Delete events
18
Modification events
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\app-32.7z | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
7
Suspicious files
103
Text files
24
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\chrome_100_percent.pak | binary | |
MD5:8626E1D68E87F86C5B4DABDF66591913 | SHA256:2CAA1DA9B6A6E87BDB673977FEE5DD771591A1B6ED5D3C5F14B024130A5D1A59 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\locales\af.pak | binary | |
MD5:464E5EEABA5EFF8BC93995BA2CB2D73F | SHA256:0AD547BB1DC57907ADEB02E1BE3017CCE78F6E60B8B39395FE0E8B62285797A1 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\locales\ar.pak | binary | |
MD5:FDBAD4C84AC66EE78A5C8DD16D259C43 | SHA256:A62B848A002474A8EA37891E148CBAF4AF09BDBA7DAFEBDC0770C9A9651F7E3B | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\LICENSE.electron.txt | text | |
MD5:4D42118D35941E0F664DDDBD83F633C5 | SHA256:5154E165BD6C2CC0CFBCD8916498C7ABAB0497923BAFCD5CB07673FE8480087D | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\chrome_200_percent.pak | binary | |
MD5:48515D600258D60019C6B9C6421F79F6 | SHA256:07BEE34E189FE9A8789AED78EA59AD41414B6E611E7D74DA62F8E6CA36AF01CE | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\locales\ca.pak | binary | |
MD5:4CD6B3A91669DDCFCC9EEF9B679AB65C | SHA256:56EFFF228EE3E112357D6121B2256A2C3ACD718769C89413DE82C9D4305459C6 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\locales\am.pak | binary | |
MD5:2C933F084D960F8094E24BEE73FA826C | SHA256:FA1E44215BD5ACC7342C431A3B1FDDB6E8B6B02220B4599167F7D77A29F54450 | |||
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3460.30544\locales\bg.pak | binary | |
MD5:38BCABB6A0072B3A5F8B86B693EB545D | SHA256:898621731AC3471A41F8B3A7BF52E7F776E8928652B37154BC7C1299F1FD92E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
12
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4816 | smartscreen.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b4a6f557eec89c52 | unknown | — | — | whitelisted |
4816 | smartscreen.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1352 | svchost.exe | GET | 200 | 23.53.42.64:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
3640 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3944 | haiper.exe | GET | 200 | 140.82.54.223:80 | http://140.82.54.223:80/ebYCOhjfCA4TqFs1IVH4Nw%3D%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 23.53.42.66:80 | — | Akamai International B.V. | DE | unknown |
4816 | smartscreen.exe | 51.137.3.145:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4816 | smartscreen.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
4816 | smartscreen.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1352 | svchost.exe | 23.53.42.64:80 | — | Akamai International B.V. | DE | unknown |
3568 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3640 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3640 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2776 | svchost.exe | 52.168.117.168:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
calendar.app.google |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |