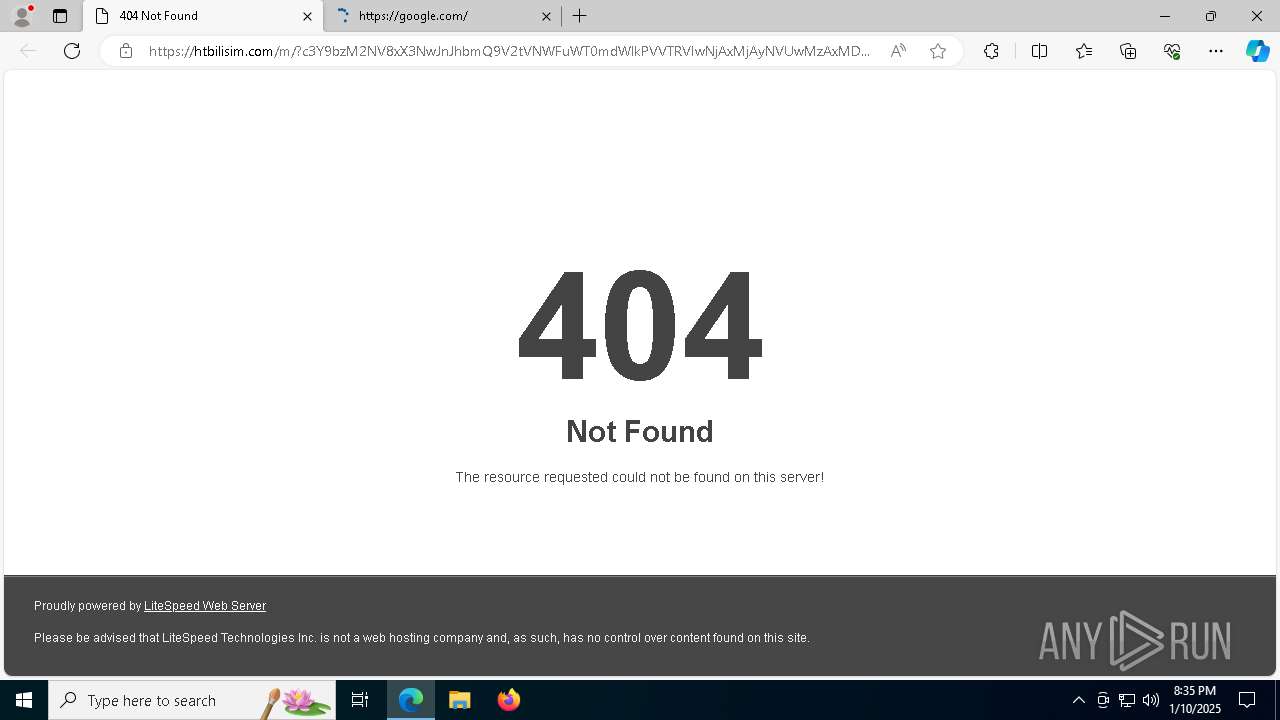
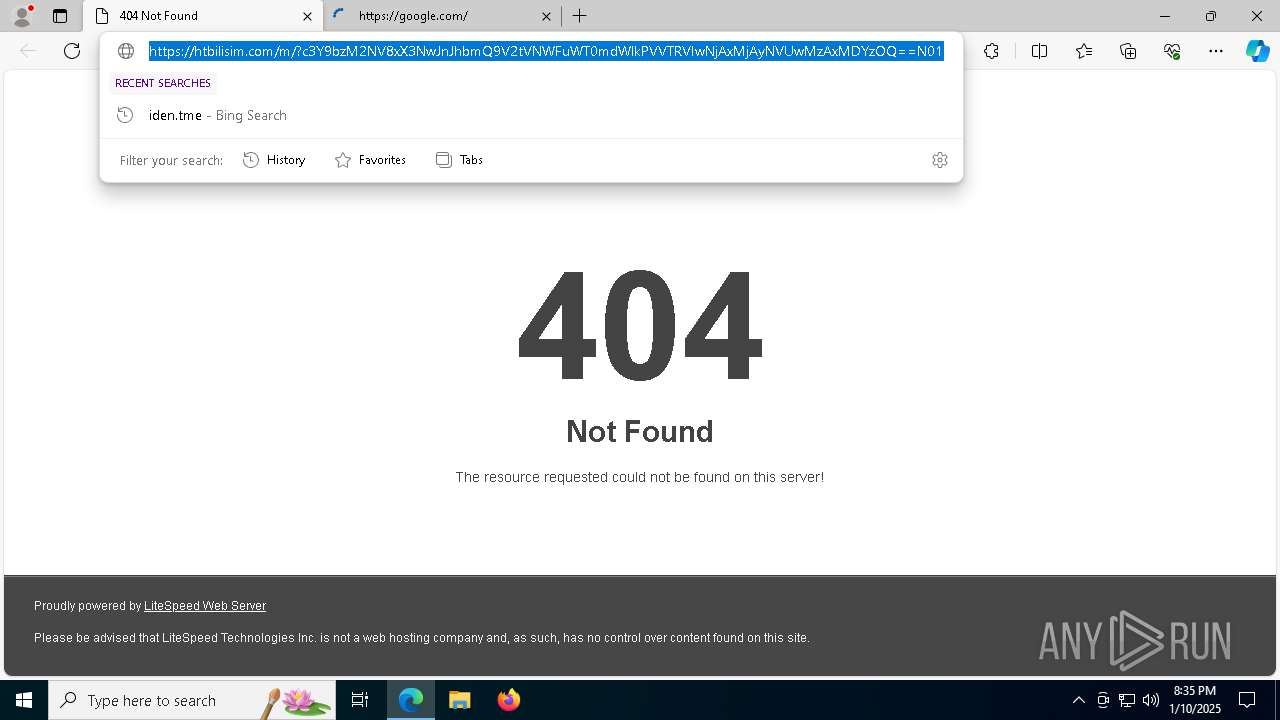
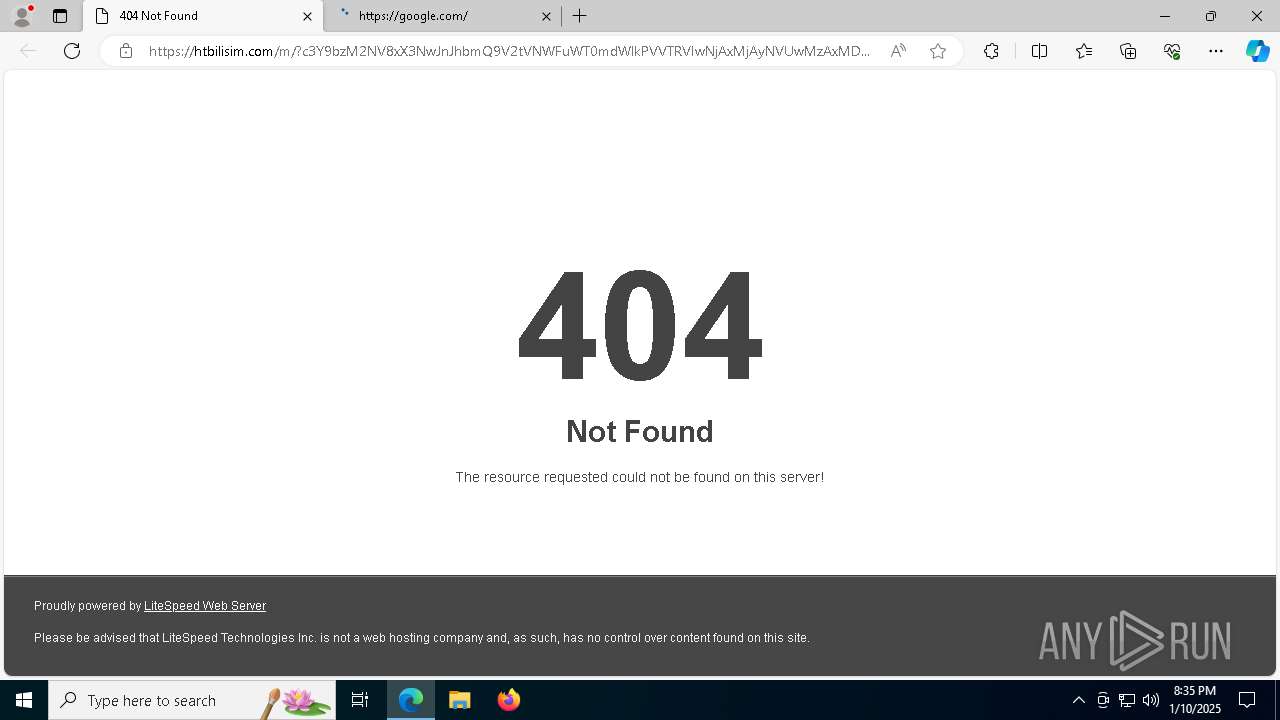
| File name: | Capture.PNG |
| Full analysis: | https://app.any.run/tasks/61877b59-e315-4637-abe7-143e8f229790 |
| Verdict: | Malicious activity |
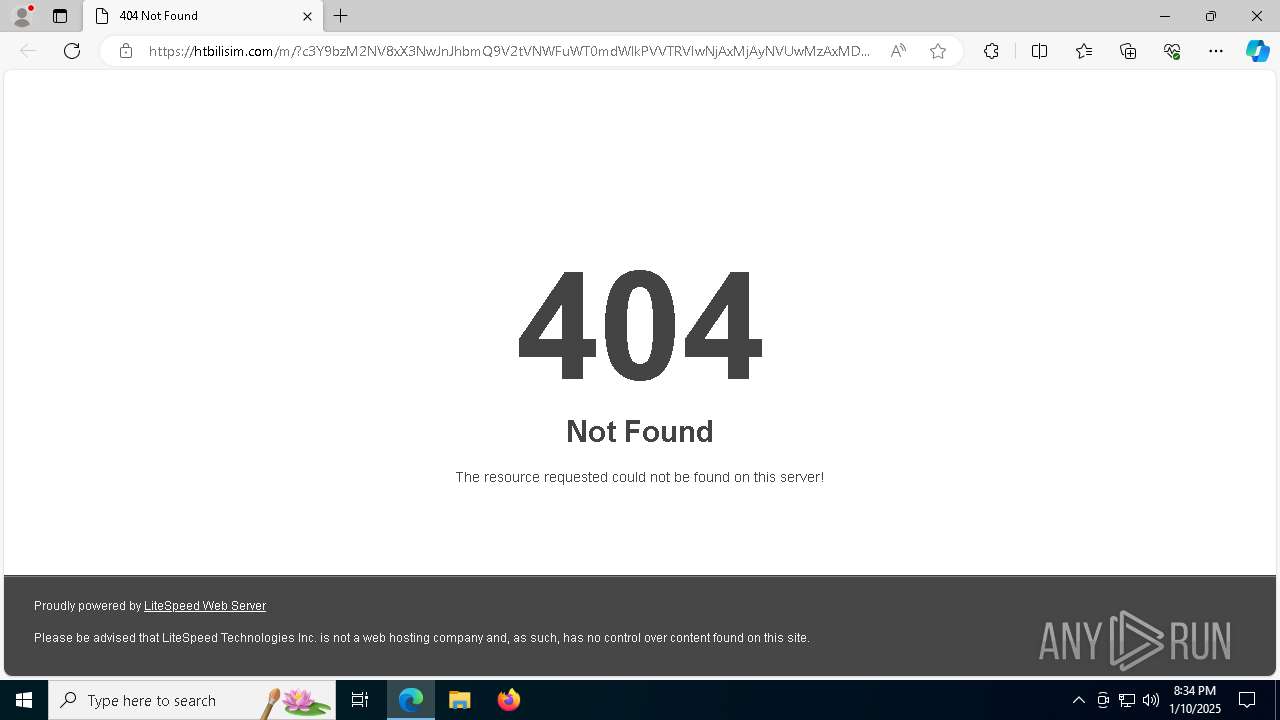
| Threats: | Mamba 2FA is an advanced phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) and target Microsoft 365 accounts. It focuses on intercepting authentication flows in real-time and enables threat actors to hijack user sessions and access sensitive systems even when additional security measures are in place. |
| Analysis date: | January 10, 2025, 20:34:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| MIME: | image/png |
| File info: | PNG image data, 948 x 479, 8-bit/color RGBA, non-interlaced |
| MD5: | 94047FBBC1FA5AB15837FBA585B64812 |
| SHA1: | FD607E827B9FAF22421E3B0C168CC72A16E9CF25 |
| SHA256: | 0C107102E33E1E55874B34A3B19DEFCFF14AA4CDBA92E599DFFA7A367F067DC2 |
| SSDEEP: | 3072:ug4+6L0GI4TLUVQ2LSiaEvaWx3FwEbJcbLEiMJr2RwvEk+k:ug4tCKoVVLS0vtx3FwgJcbLOJSR4N |
MALICIOUS
Suspicious URL found
- explorer.exe (PID: 6148)
QR code contains URL with email
- explorer.exe (PID: 6148)
SUSPICIOUS
No suspicious indicators.INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 6148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .png | | | Portable Network Graphics (100) |
|---|
EXIF
PNG
| ImageWidth: | 948 |
|---|---|
| ImageHeight: | 479 |
| BitDepth: | 8 |
| ColorType: | RGB with Alpha |
| Compression: | Deflate/Inflate |
| Filter: | Adaptive |
| Interlace: | Noninterlaced |
| SRGBRendering: | Perceptual |
| Gamma: | 2.2 |
| PixelsPerUnitX: | 3779 |
| PixelsPerUnitY: | 3779 |
| PixelUnits: | meters |
Composite
| ImageSize: | 948x479 |
|---|---|
| Megapixels: | 0.454 |
Total processes
148
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
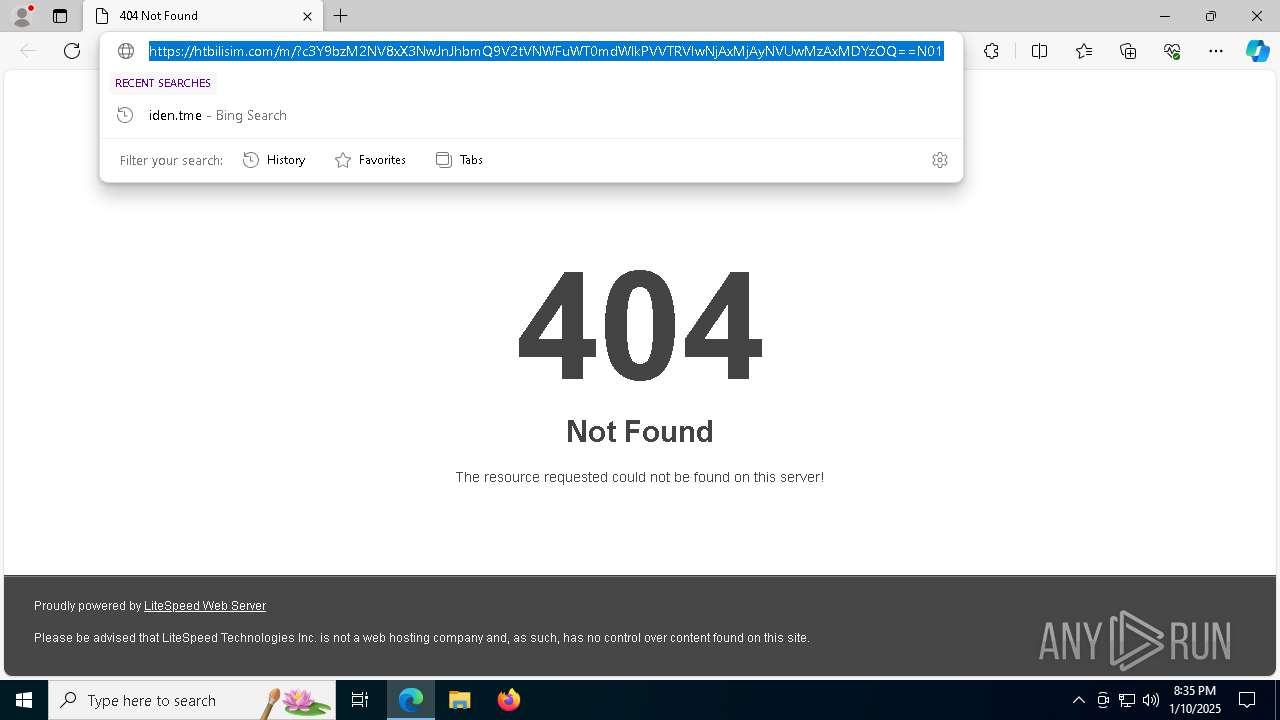
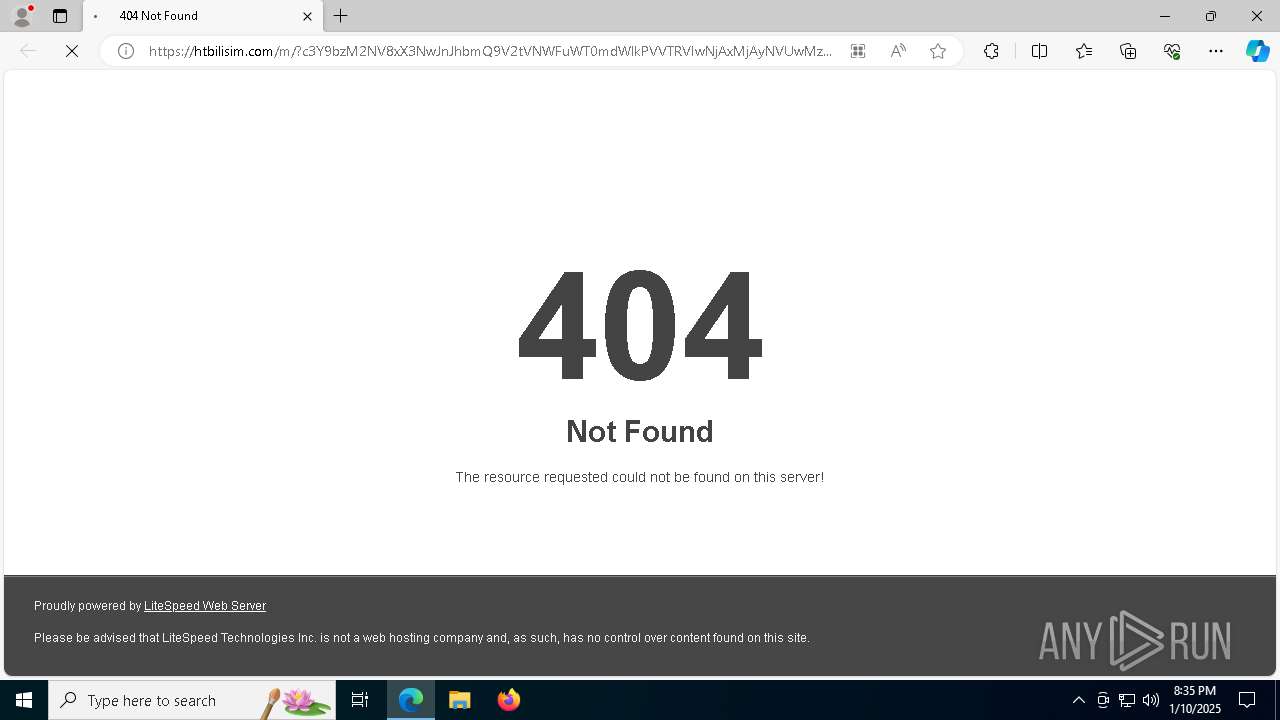
| 6148 | "C:\Windows\explorer.exe" "https://htbilisim.com/m/?c3Y9bzM2NV8xX3NwJnJhbmQ9V2tVNWFuWT0mdWlkPVVTRVIwNjAxMjAyNVUwMzAxMDYzOQ==N0123N#alockhart@seminolecountyfl.gov" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6344 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 6632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2584 --field-trial-handle=2432,i,5294958257231485215,1453246571413011409,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
Total events
131
Read events
131
Write events
0
Delete events
0
Modification events
Executable files
25
Suspicious files
30
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\SCT Auditing Pending Reports~RF1365d2.TMP | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\SCT Auditing Pending Reports~RF135e7f.TMP | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\6e8f354d-9c9f-4e37-9972-ee372eac6cf2.tmp | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\65e8cebe-d48a-4be0-80e4-913da27c3d41.tmp | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Sdch Dictionaries | binary | |
MD5:20D4B8FA017A12A108C87F540836E250 | SHA256:6028BD681DBF11A0A58DDE8A0CD884115C04CAA59D080BA51BDE1B086CE0079D | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00025a | text | |
MD5:2717FDDC7A13C7880641F1E05D1ED705 | SHA256:76189987888613349DCE615CDA17C74C7FBD0D56429BE89AB24E987CE758EAFB | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\a7fe6b26-fe8b-436d-9155-46555c1d6c2d.tmp | binary | |
MD5:20D4B8FA017A12A108C87F540836E250 | SHA256:6028BD681DBF11A0A58DDE8A0CD884115C04CAA59D080BA51BDE1B086CE0079D | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\SCT Auditing Pending Reports | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000259 | image | |
MD5:4A68983965BB0EE2328181E4AF6DA7CC | SHA256:A999576CDB4DE9CB0010A1B626595F9EE94F10206F088103253AD0273F1A30C8 | |||
| 6632 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000258 | compressed | |
MD5:BC6B691AEEE960D9D499EE9C1261ADC3 | SHA256:A85FB312A2D1F1FE45B51DF4A59EDCEFF4474FD99446D38D8A562E083563DA11 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
101
DNS requests
105
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.21.245.134:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.107.161.181:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.107.161.181:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.21.245.134:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3488 | RUXIMICS.exe | GET | 200 | 104.107.161.181:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3488 | RUXIMICS.exe | GET | 200 | 2.21.245.134:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3488 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.21.133.179:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.21.245.134:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
3488 | RUXIMICS.exe | 2.21.245.134:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 104.107.161.181:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3488 | RUXIMICS.exe | 104.107.161.181:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
htbilisim.com |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Mamba2FA`s Phishing-Kit domain by CrossDomain (htbilisim .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Mamba2FA`s Phishing-Kit domain by CrossDomain (htbilisim .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Mamba2FA`s Phishing-Kit domain by CrossDomain (htbilisim .com) |