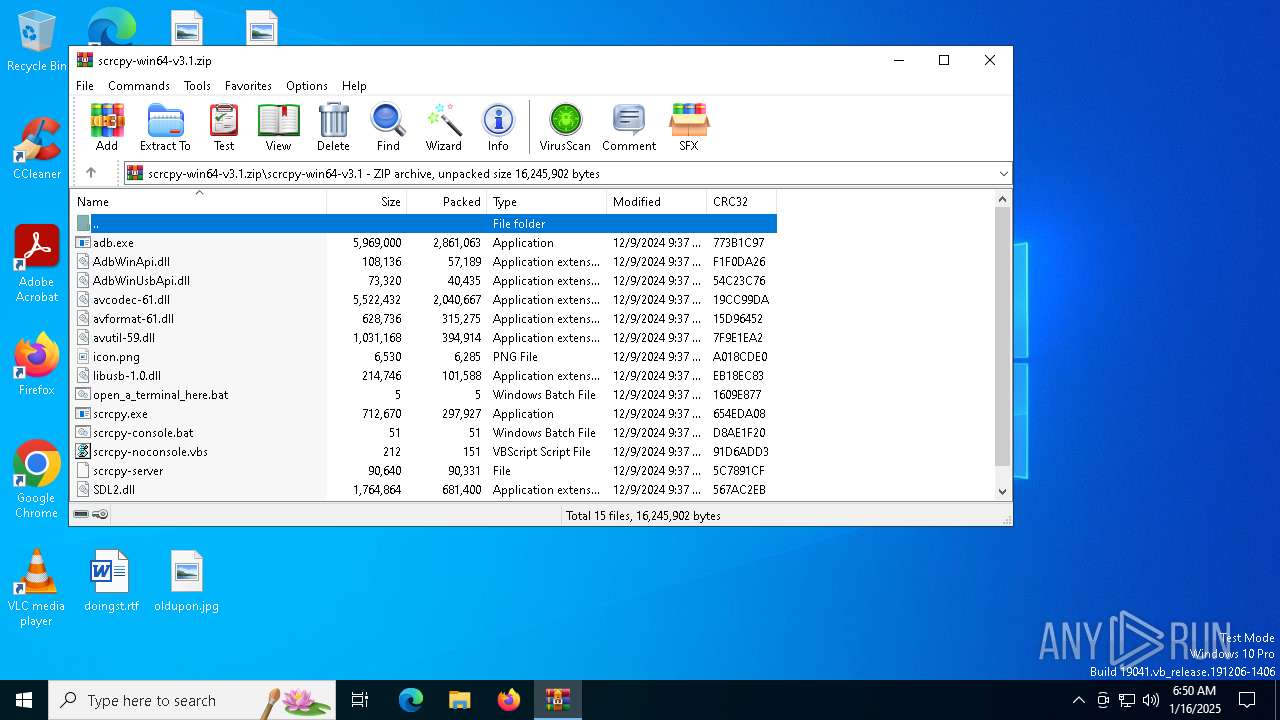
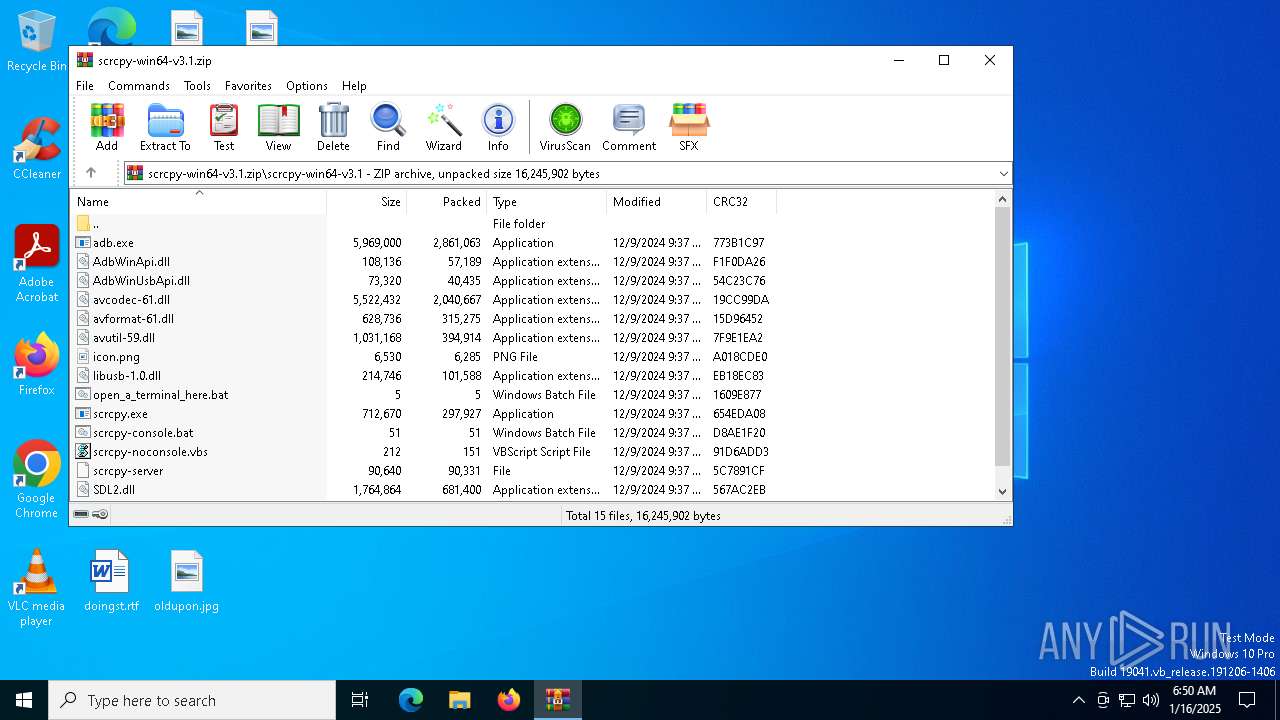
| File name: | scrcpy-win64-v3.1.zip |
| Full analysis: | https://app.any.run/tasks/e8eefd38-9600-48dc-9c42-dd154fd5c750 |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2025, 06:50:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 6CFA2B01081F0B0B8922A4A167B01FCB |
| SHA1: | 5821C5E59D05BE601A610EBFEC885B5780BFF275 |
| SHA256: | 0C05EA395D95CFE36BEE974EEB435A3DB87EA5594FF738370D5DC3068A9538CA |
| SSDEEP: | 98304:eihTxViznt7pYcfaJpOr4QJFLIr+Pbvem3HYMYqQrTGHEdcu1vpgvVC8k2N19I75:qiMwgfJ6p |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 644)
SUSPICIOUS
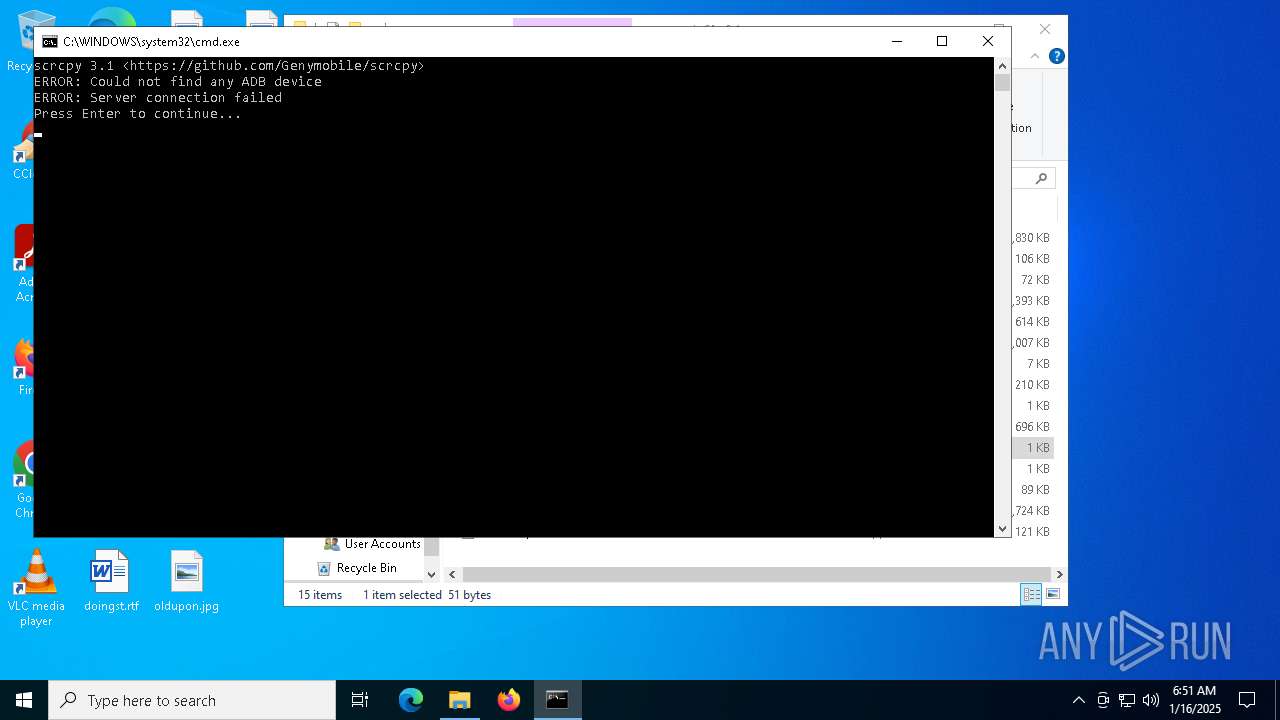
Application launched itself
- adb.exe (PID: 6932)
- cmd.exe (PID: 6220)
- cmd.exe (PID: 5748)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6220)
- wscript.exe (PID: 4840)
- cmd.exe (PID: 5748)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4840)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 644)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 644)
The sample compiled with english language support
- WinRAR.exe (PID: 644)
Reads the computer name
- adb.exe (PID: 7076)
- scrcpy.exe (PID: 4128)
Create files in a temporary directory
- adb.exe (PID: 7076)
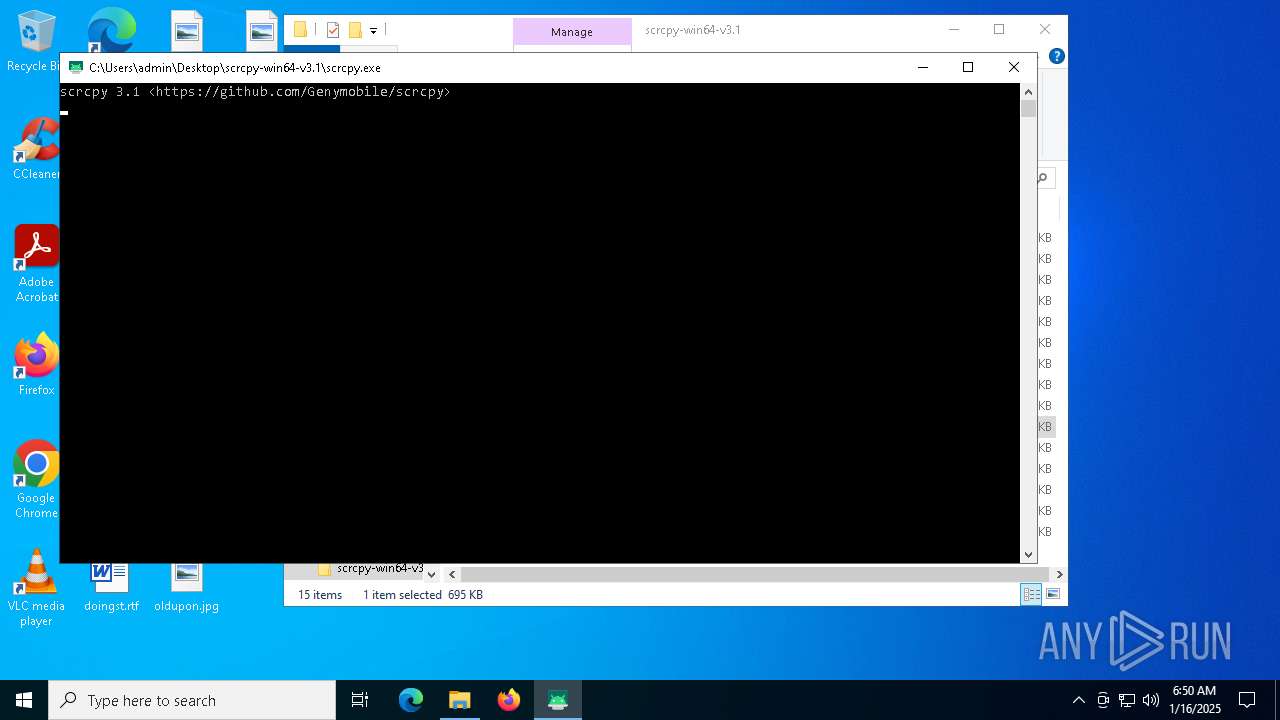
Manual execution by a user
- scrcpy.exe (PID: 6864)
- cmd.exe (PID: 6220)
- adb.exe (PID: 2088)
- scrcpy.exe (PID: 4128)
- wscript.exe (PID: 4840)
- cmd.exe (PID: 6376)
- cmd.exe (PID: 5748)
Checks supported languages
- scrcpy.exe (PID: 4128)
- adb.exe (PID: 5460)
- scrcpy.exe (PID: 2136)
- adb.exe (PID: 5604)
- scrcpy.exe (PID: 6344)
- adb.exe (PID: 3700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:09 21:37:44 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | scrcpy-win64-v3.1/ |
Total processes
154
Monitored processes
30
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\scrcpy-win64-v3.1.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\Users\admin\Desktop\scrcpy-win64-v3.1\adb.exe" | C:\Users\admin\Desktop\scrcpy-win64-v3.1\adb.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2136 | scrcpy.exe | C:\Users\admin\Desktop\scrcpy-win64-v3.1\scrcpy.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2996 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3288 | adb start-server | C:\Users\admin\Desktop\scrcpy-win64-v3.1\adb.exe | — | scrcpy.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3688 | "C:\Windows\System32\cmd.exe" /c scrcpy.exe | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3700 | adb devices -l | C:\Users\admin\Desktop\scrcpy-win64-v3.1\adb.exe | — | scrcpy.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | scrcpy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | "C:\Users\admin\Desktop\scrcpy-win64-v3.1\scrcpy.exe" | C:\Users\admin\Desktop\scrcpy-win64-v3.1\scrcpy.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
5 359
Read events
5 341
Write events
18
Delete events
0
Modification events
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\scrcpy-win64-v3.1.zip | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
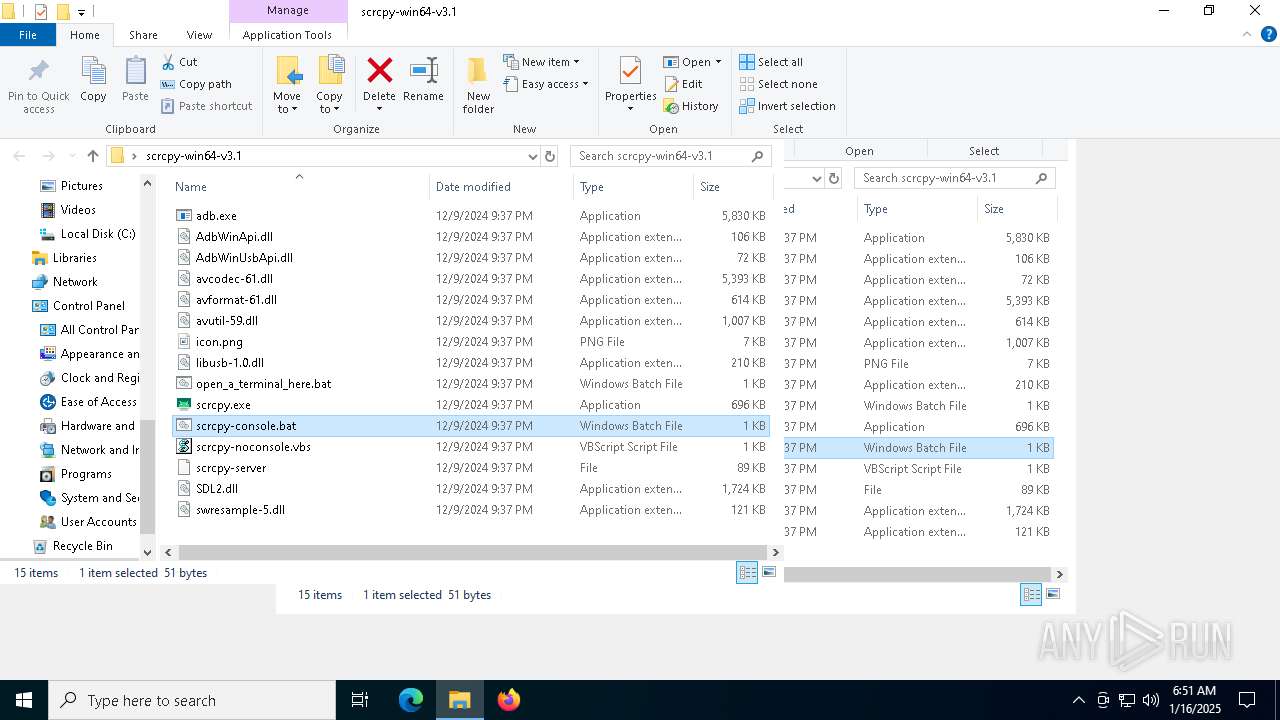
Executable files
10
Suspicious files
1
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\AdbWinApi.dll | executable | |
MD5:D2C034449BE65653AEC2459D9AB83AE5 | SHA256:DB92F418F6C384FAEEBCCADBC592FB339AF3D51ECFEC3EC04BD3572080247BAE | |||
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\SDL2.dll | executable | |
MD5:8B97D08C5A30FC30600E3A8824209BAF | SHA256:03F7A29385B62D347F99BB0DC478EC363B42DD2C3FD2A7C372344BB953C280B7 | |||
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\AdbWinUsbApi.dll | executable | |
MD5:93A6075B7AE7D0DF52EC55017A2F8214 | SHA256:3BA13420D47C60D958E0D5B333440F9895704879BB7C983B55F195717F621A3E | |||
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\avformat-61.dll | executable | |
MD5:253AA9A030CE5FC6FDE064CB0706F95B | SHA256:FD0FE520480170A4A94519D34FBA8DDA1D1478160B736761F4B63FD3FFD042EA | |||
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\avcodec-61.dll | executable | |
MD5:475D2B95355C04CF7A45381FF1E0641A | SHA256:0625683C79407F14C29A94236CEF304896272042E802796CE0D57D2A2626B486 | |||
| 7076 | adb.exe | C:\Users\admin\.android\adbkey.pub | text | |
MD5:76CB40F908E79DC1788363F323B90148 | SHA256:472AE7B8536B1CFB9B87C418AA393242664E84B691637C5B44011D0BF80978F5 | |||
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\scrcpy.exe | executable | |
MD5:B19A6030CF56CA7646940F9BD7DD0CCB | SHA256:831CB2317E7040C7A2693C5F495B963883B9CDC8A9C40C5719CACBCC5DE40AC3 | |||
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\adb.exe | executable | |
MD5:AE6975E7C2211152F5FA54A1FDDF414D | SHA256:0E606318957BAAC81B997CCD8EE4BCDFF79964A9921DA07C716AEA3E8D856AF7 | |||
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\swresample-5.dll | executable | |
MD5:864DE3BC8A59611059971D6A9AC0DC09 | SHA256:33278F72119FF5BB51B053838B6E14F18D6349D4BF91FE74167919FF8E82DD90 | |||
| 644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa644.5231\scrcpy-win64-v3.1\scrcpy-server | compressed | |
MD5:B2D1245F74FC7D77C3370E847002CC95 | SHA256:958F0944A62F23B1F33A16E9EB14844C1A04B882CA175A738C16D23CB22B86C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6508 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.21.65.132:443 | — | Akamai International B.V. | NL | unknown |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4864 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |