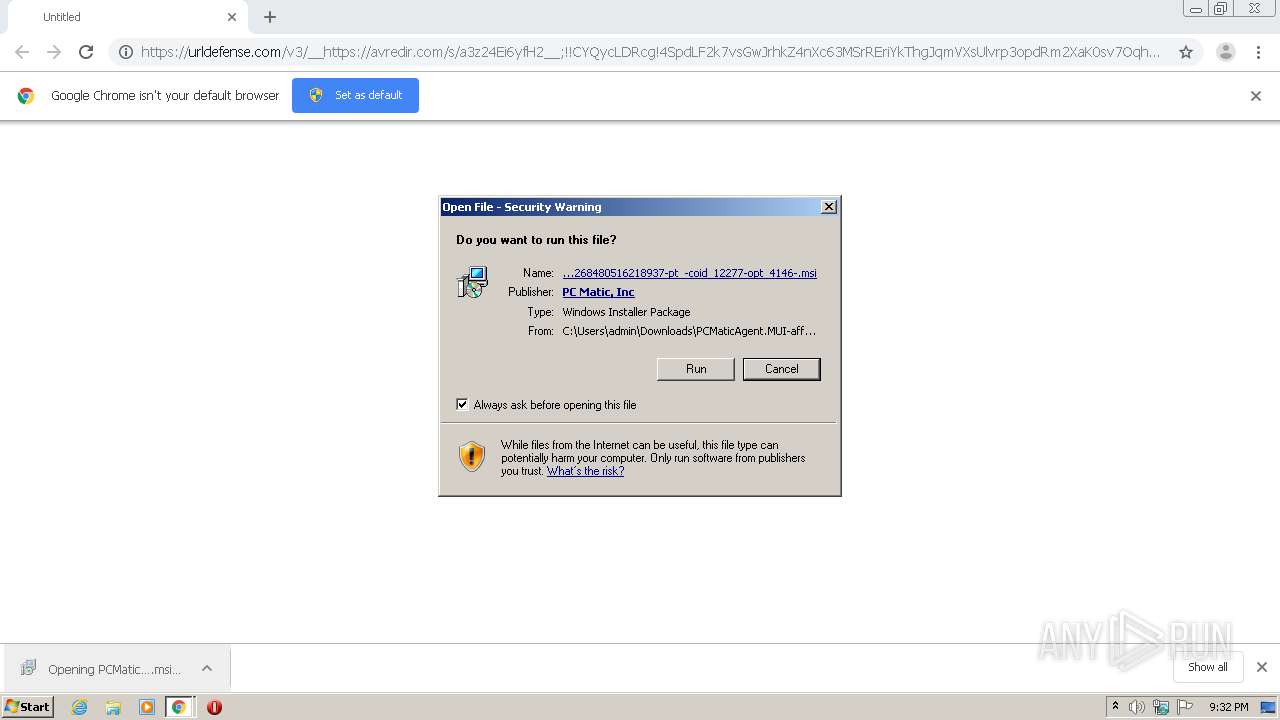
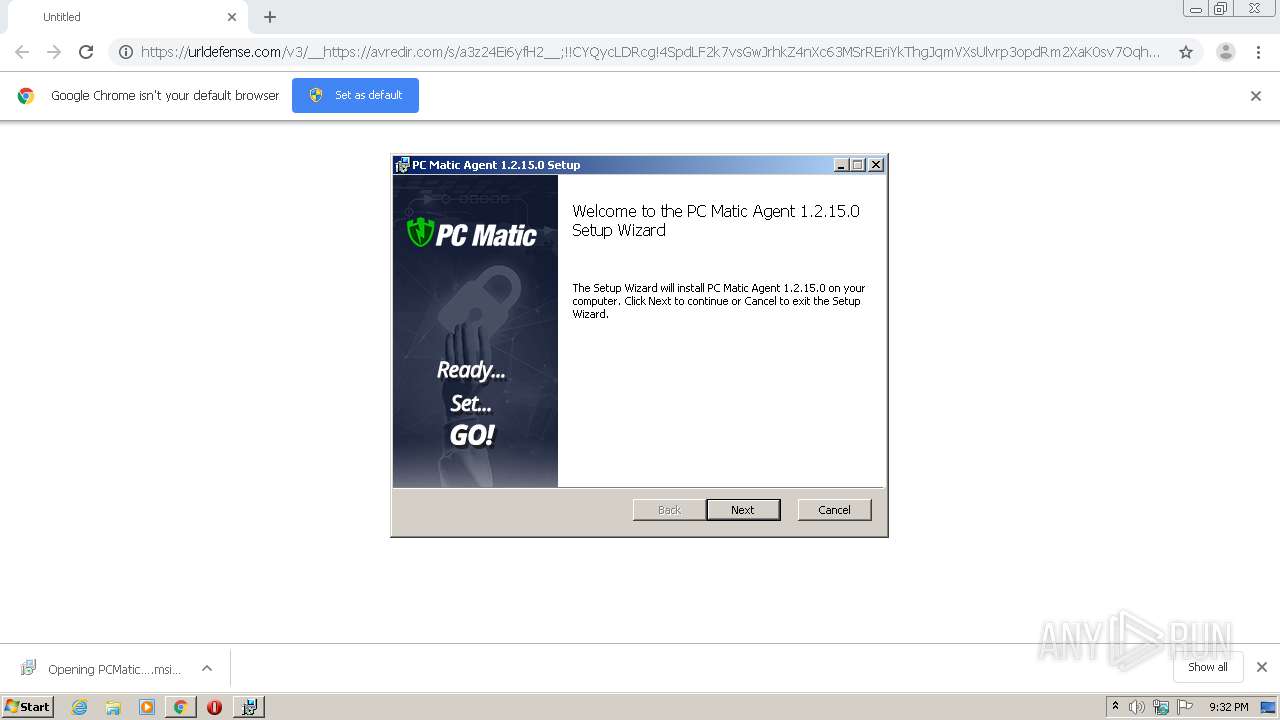
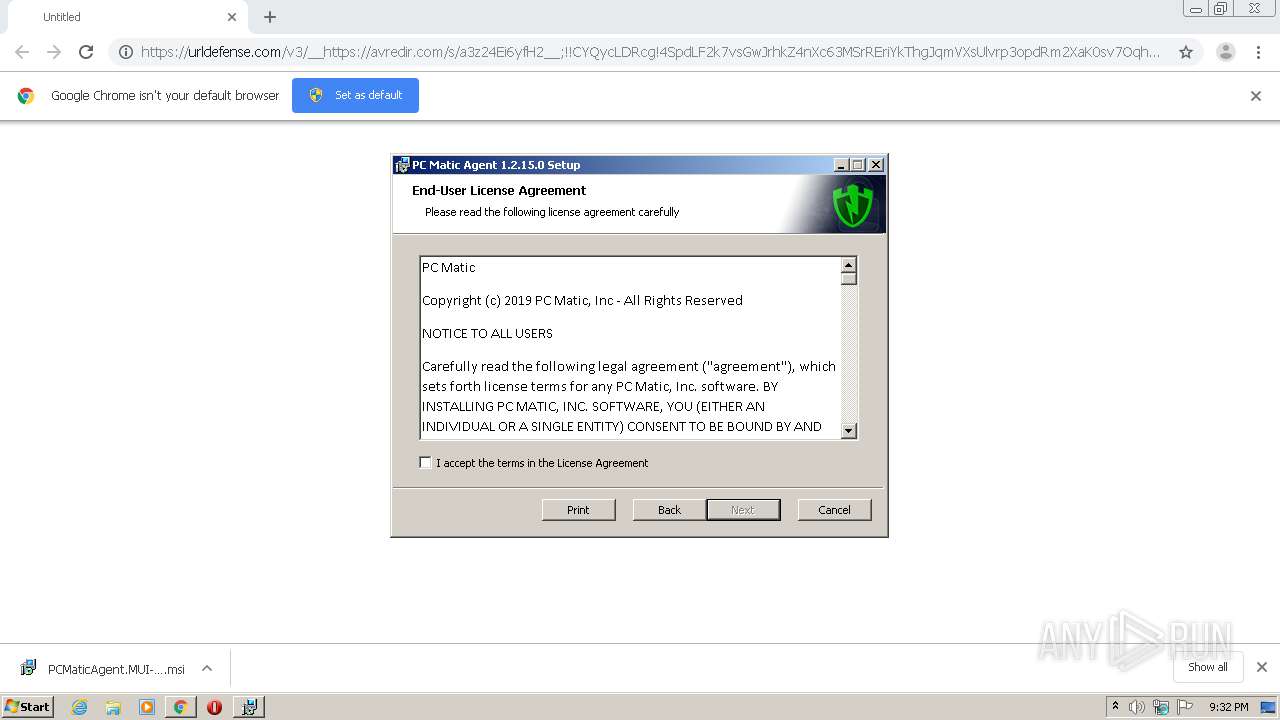
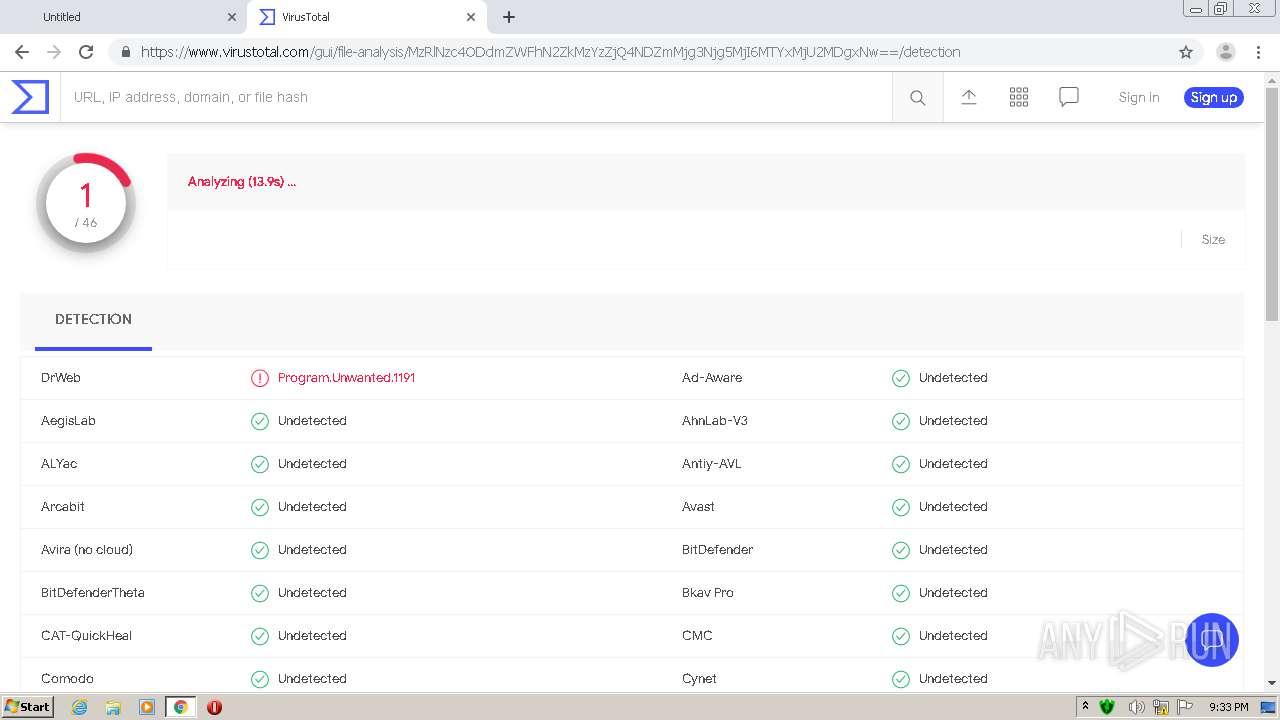
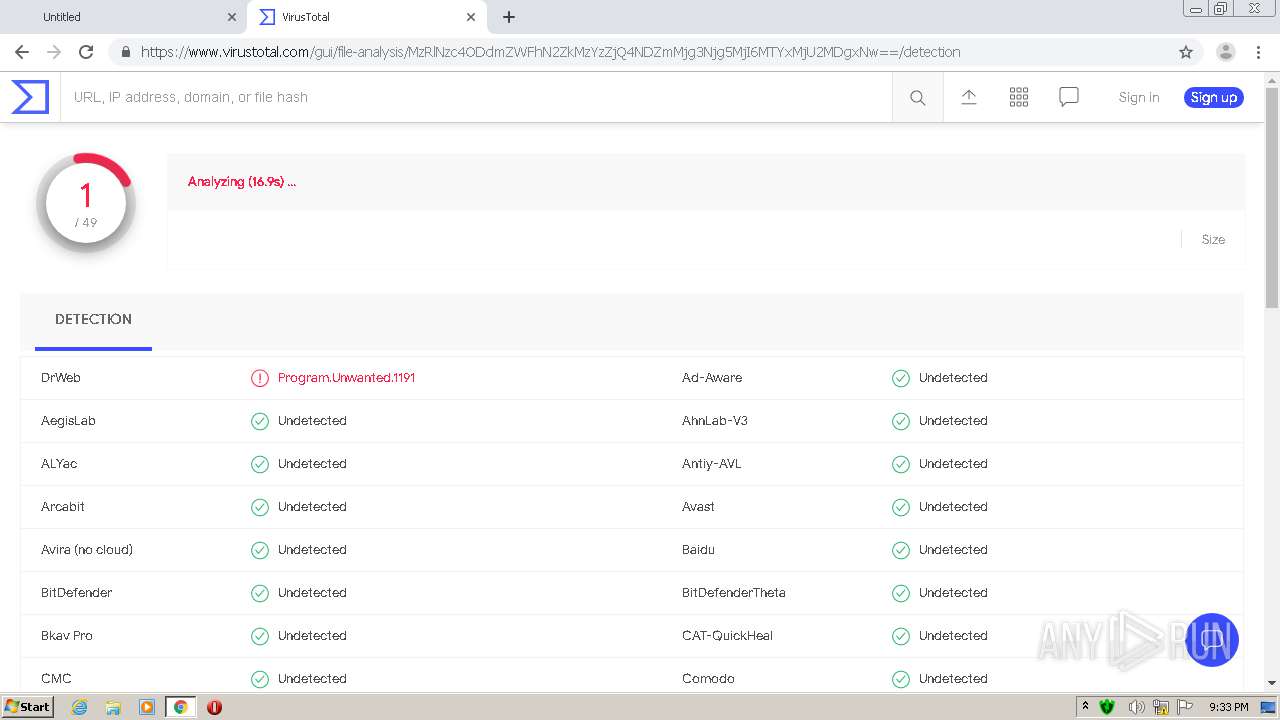
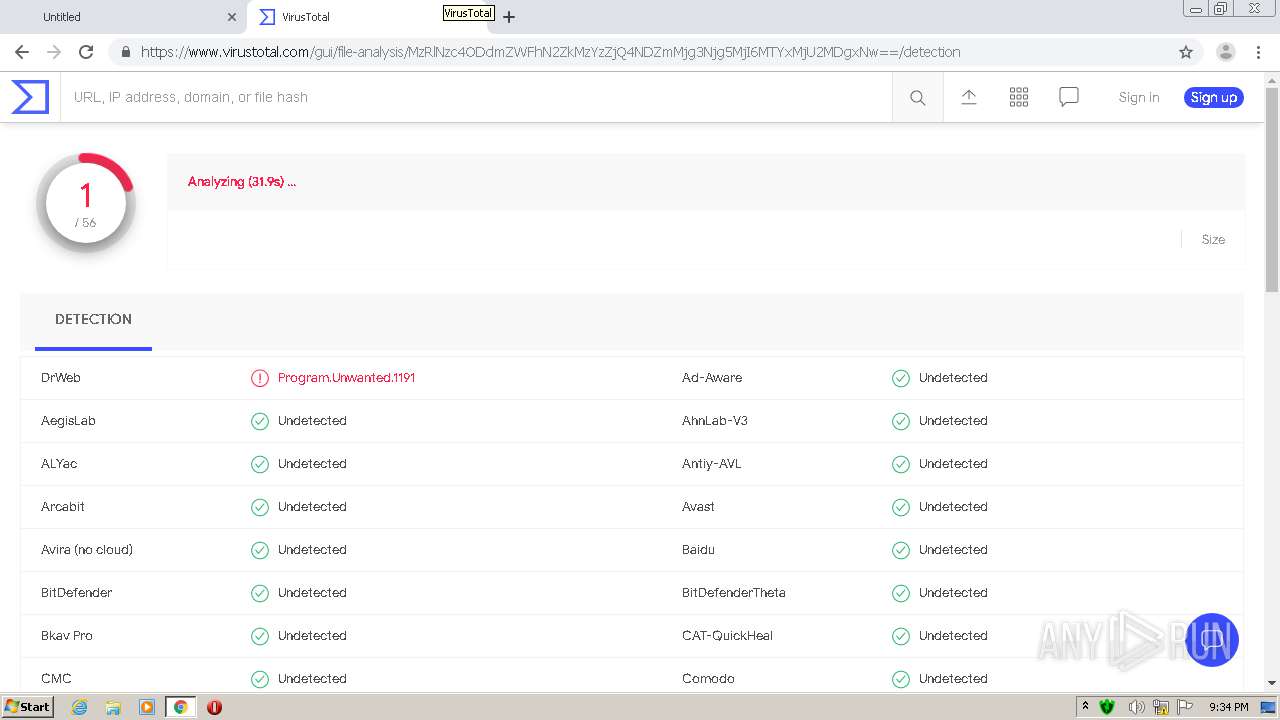
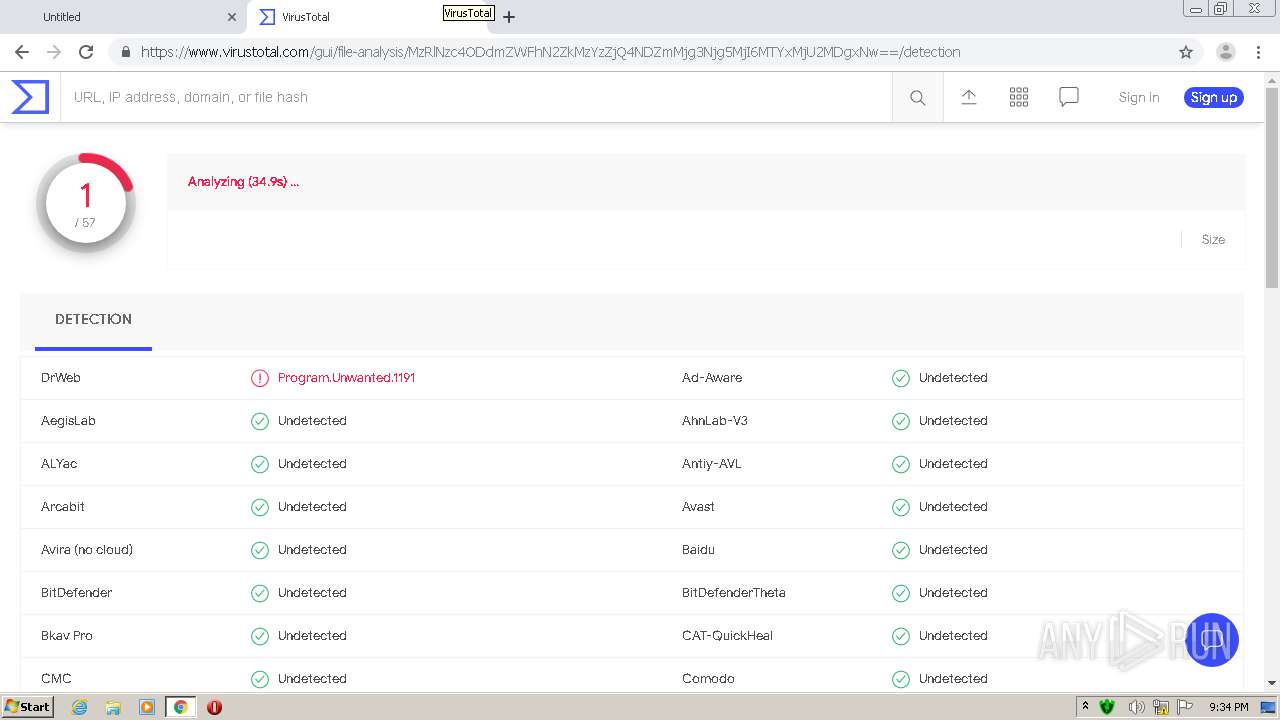
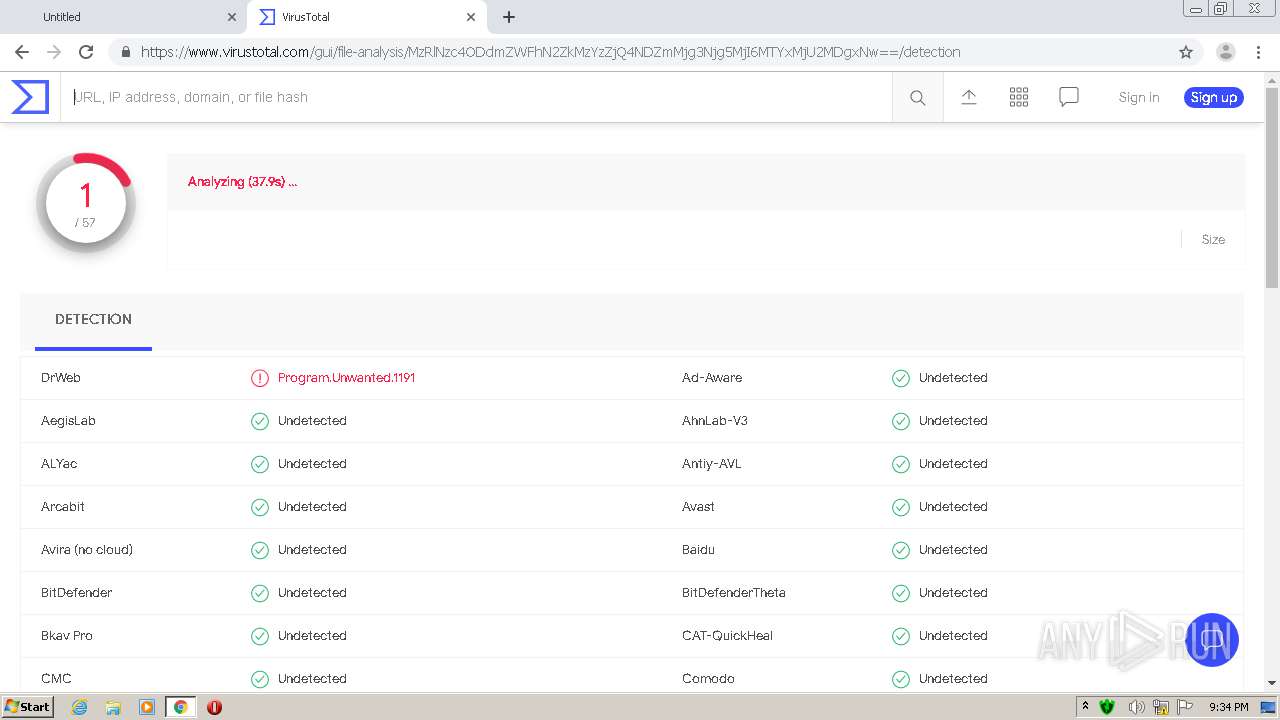
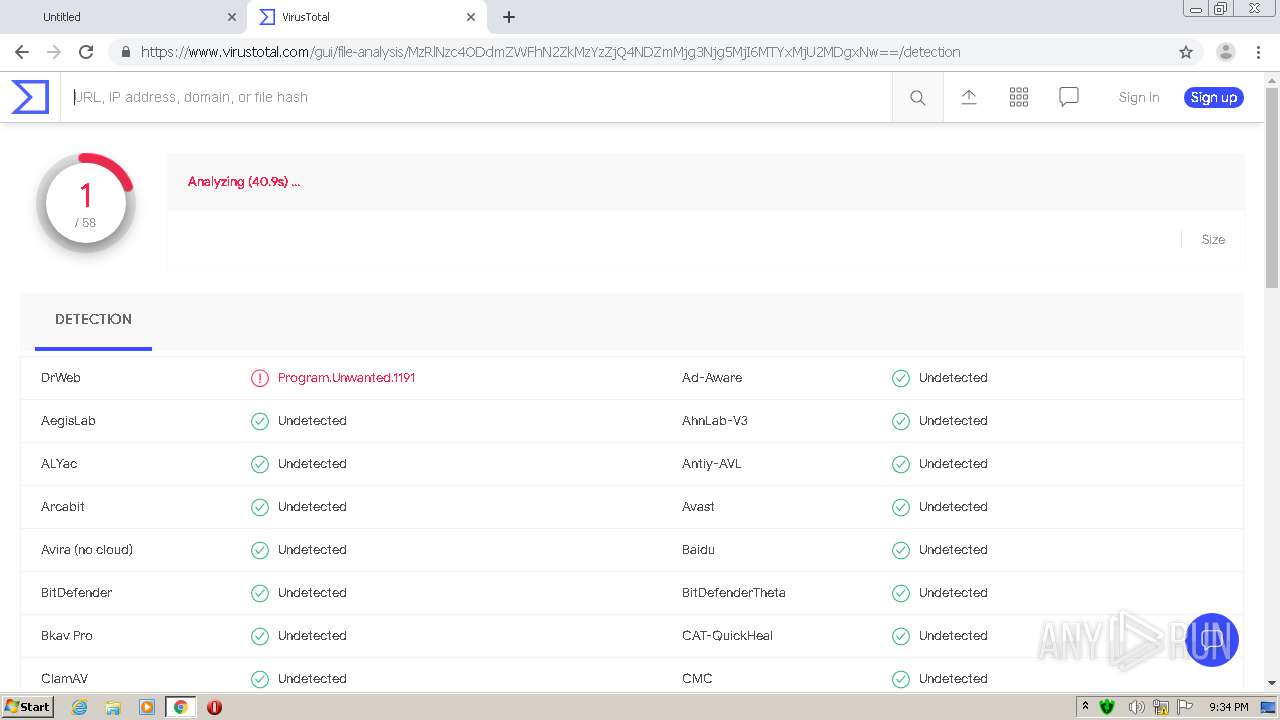
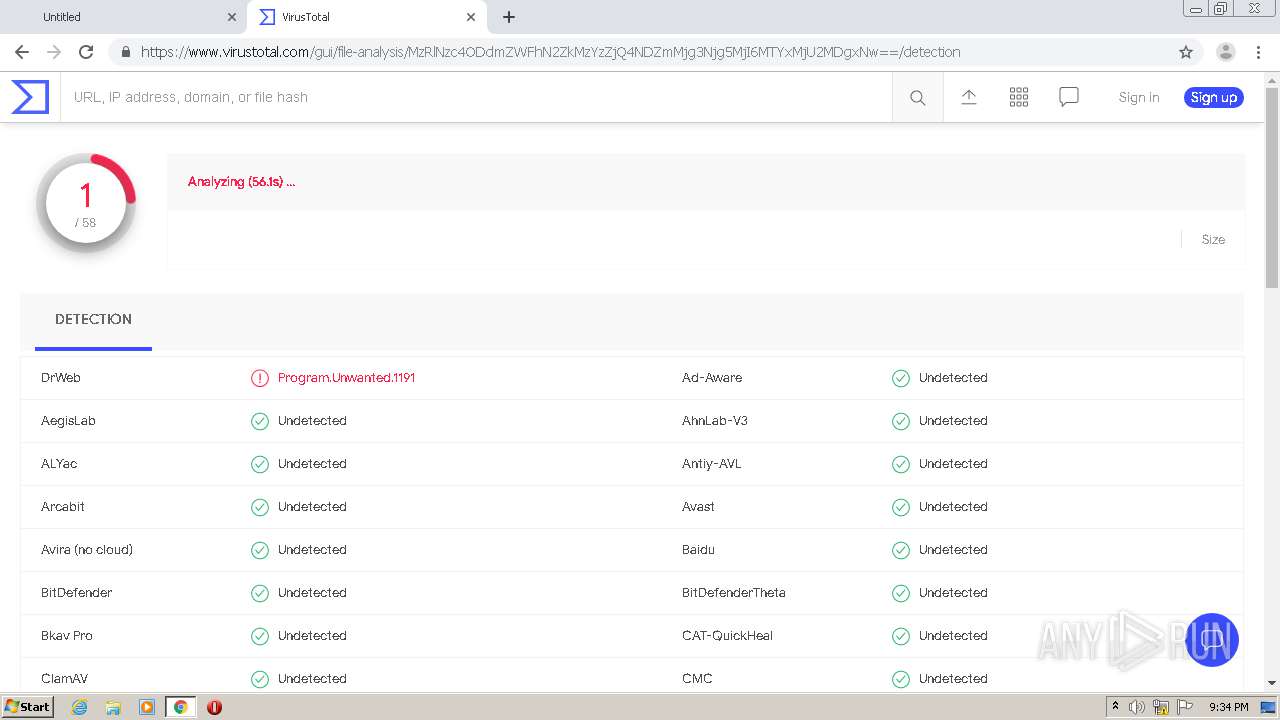
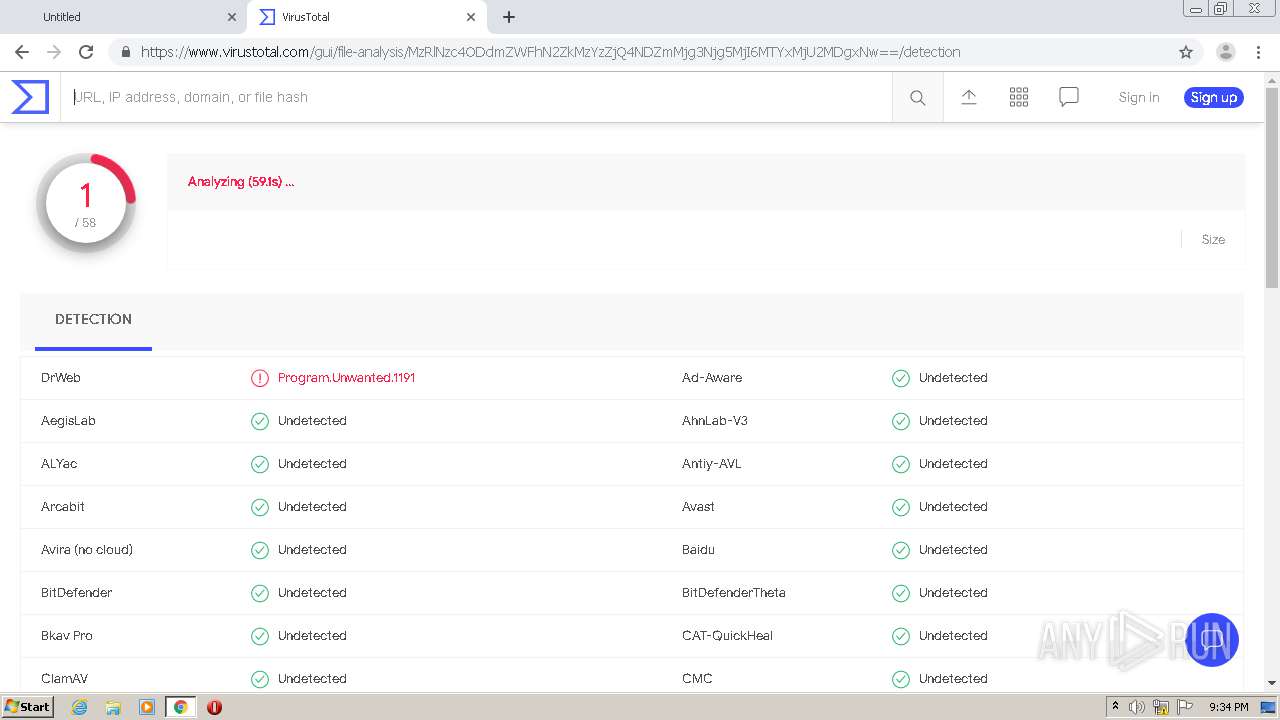
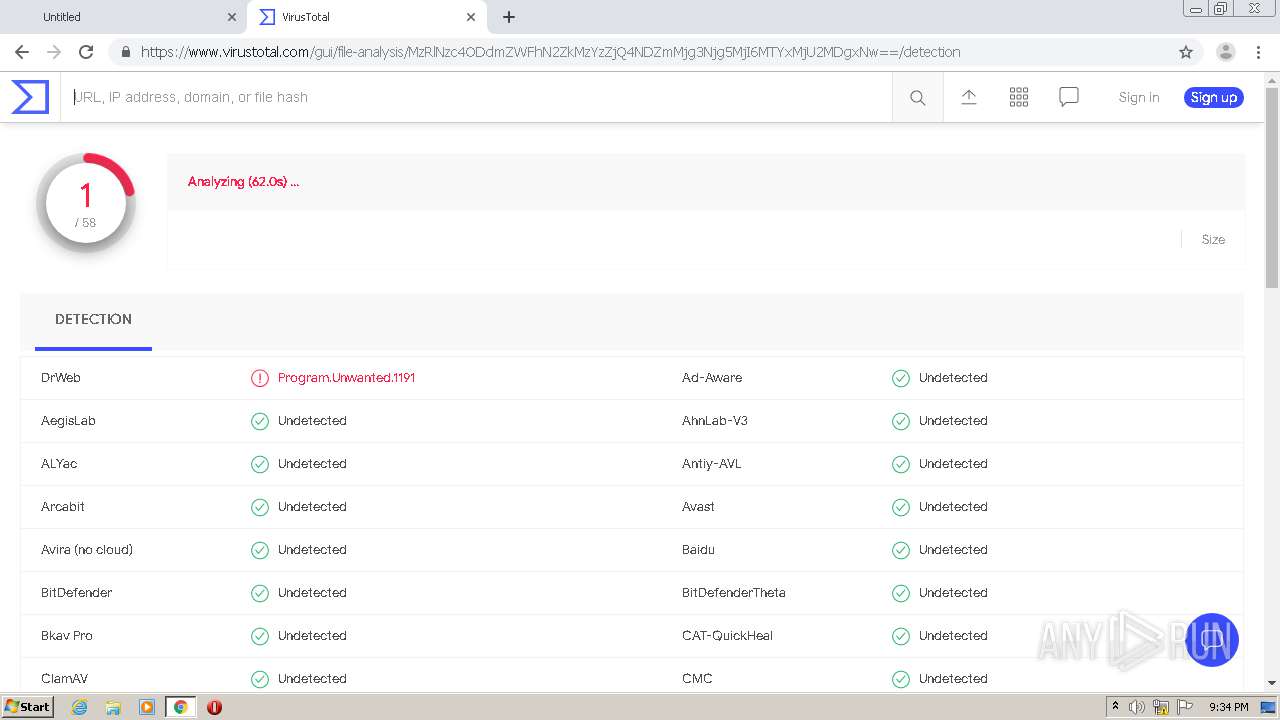
| URL: | https://urldefense.com/v3/__https://avredir.com/s/a3z24Ei6yfH2__;!!CYQycLDRcg!4SpdLF2k7vsGwJrhkZ4nXc63MSrREriYkThgJqmVXsUlvrp3opdRm2XaK0sv7Oqh2Bs4gfQ$ |
| Full analysis: | https://app.any.run/tasks/19cbb2ed-4260-43db-9617-864cf63c75c9 |
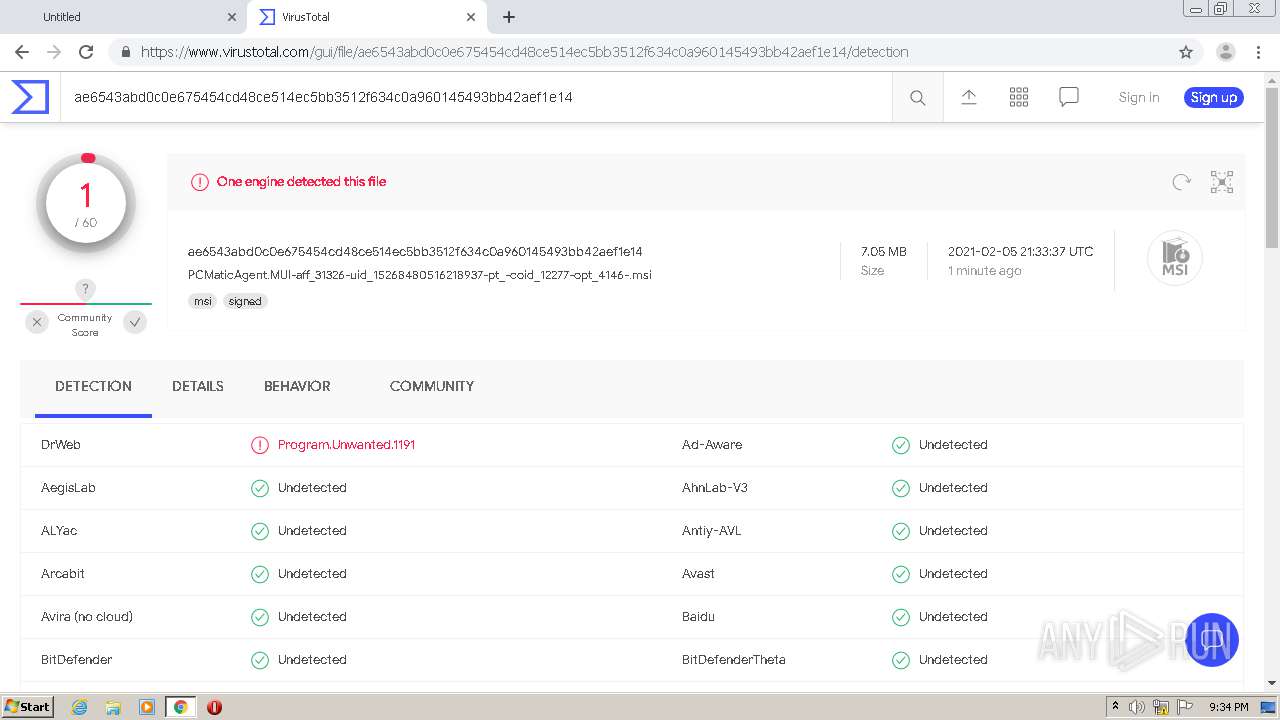
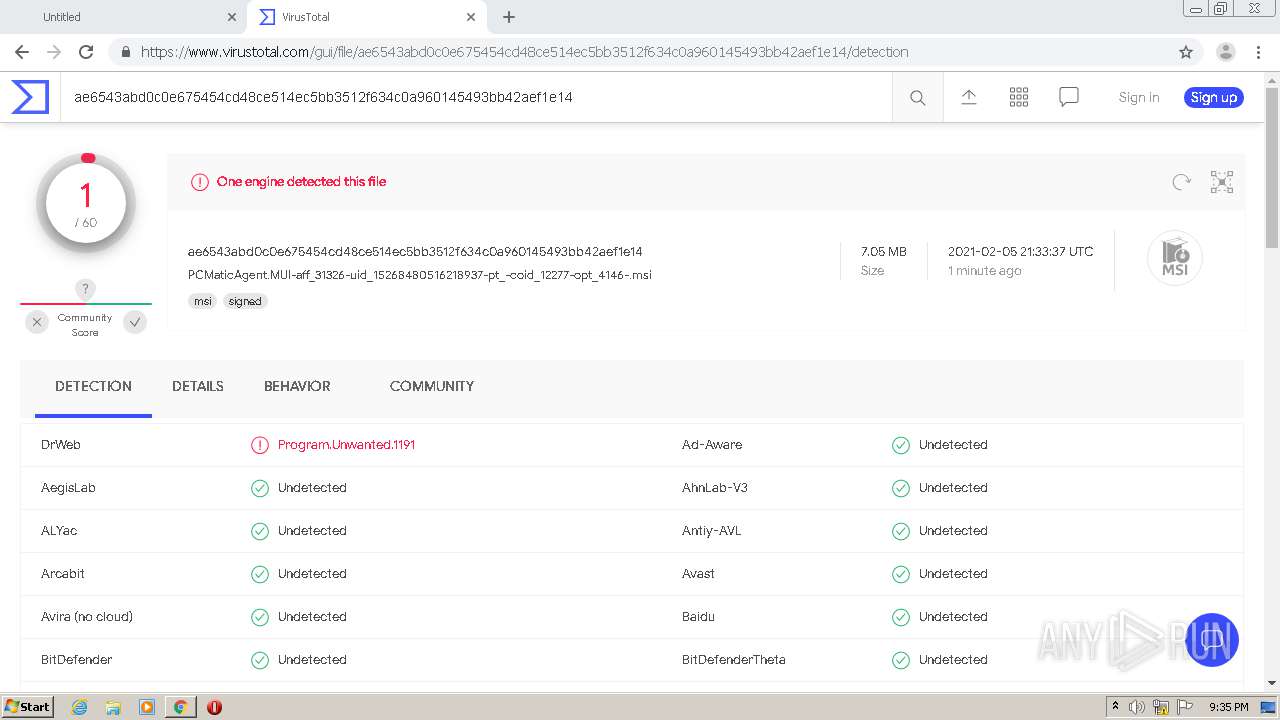
| Verdict: | Malicious activity |
| Analysis date: | February 05, 2021, 21:31:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4AF86C4F9C2FC1C55FD90F1E7FD6692B |
| SHA1: | 7102FA0E55C0C8CA1B8F4F37F401D92DDDF0E1DC |
| SHA256: | 0BC9479B7B92ACFE4DFBD313DA85F6A341FB215093C1B1D257F81A7818A04A15 |
| SSDEEP: | 3:N8U2DAL5IKTWK66NR0mRe61tm8cPO2r0pTa3xN1OHToXrUZl:2UJtIrhVElry09aBNwzF |
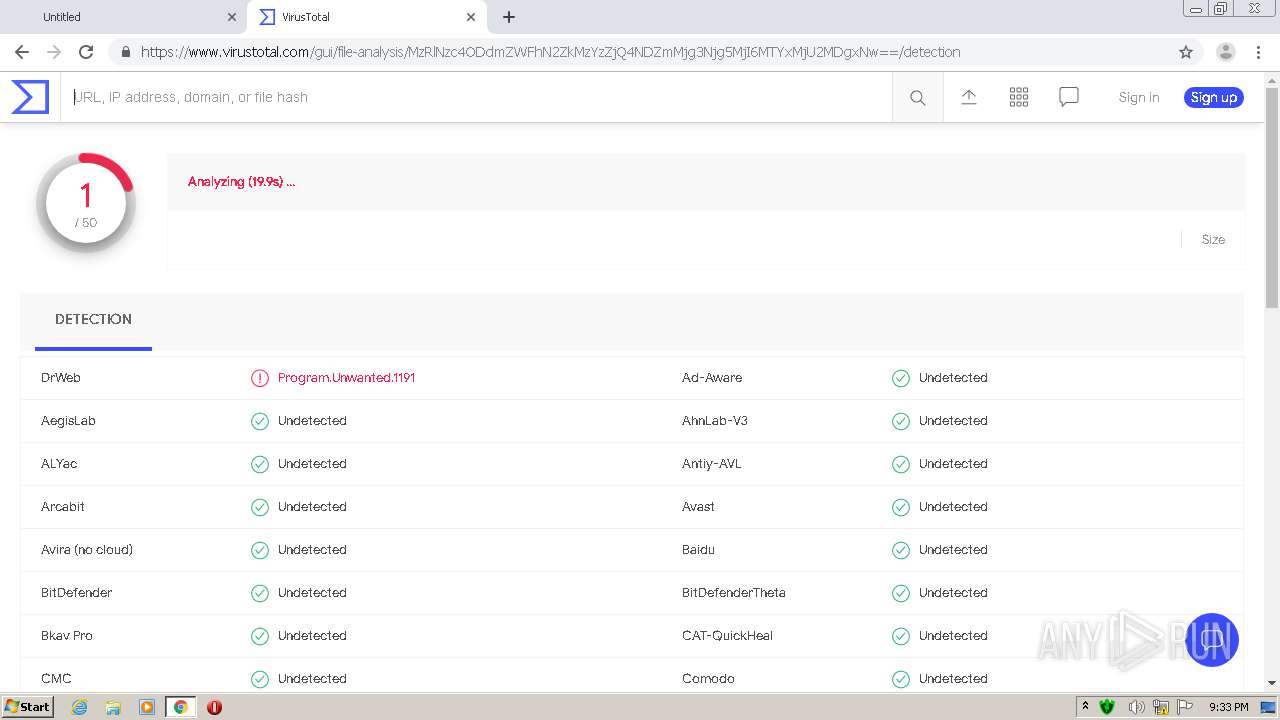
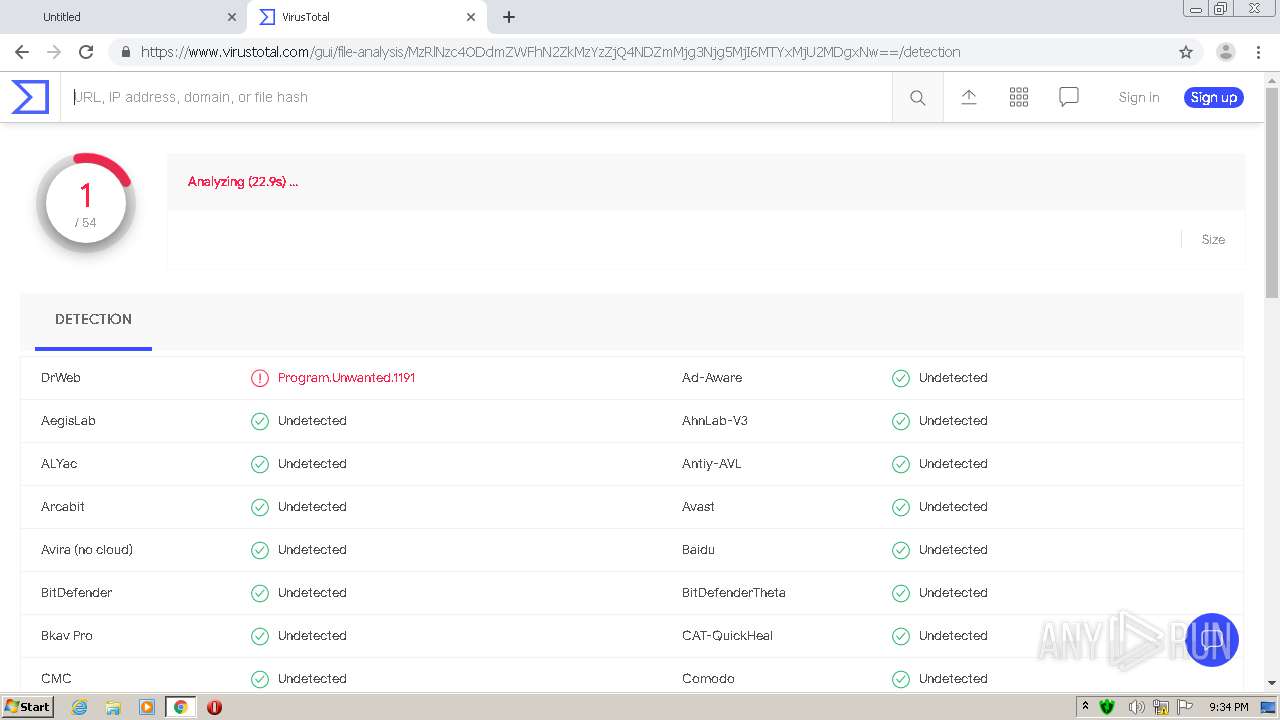
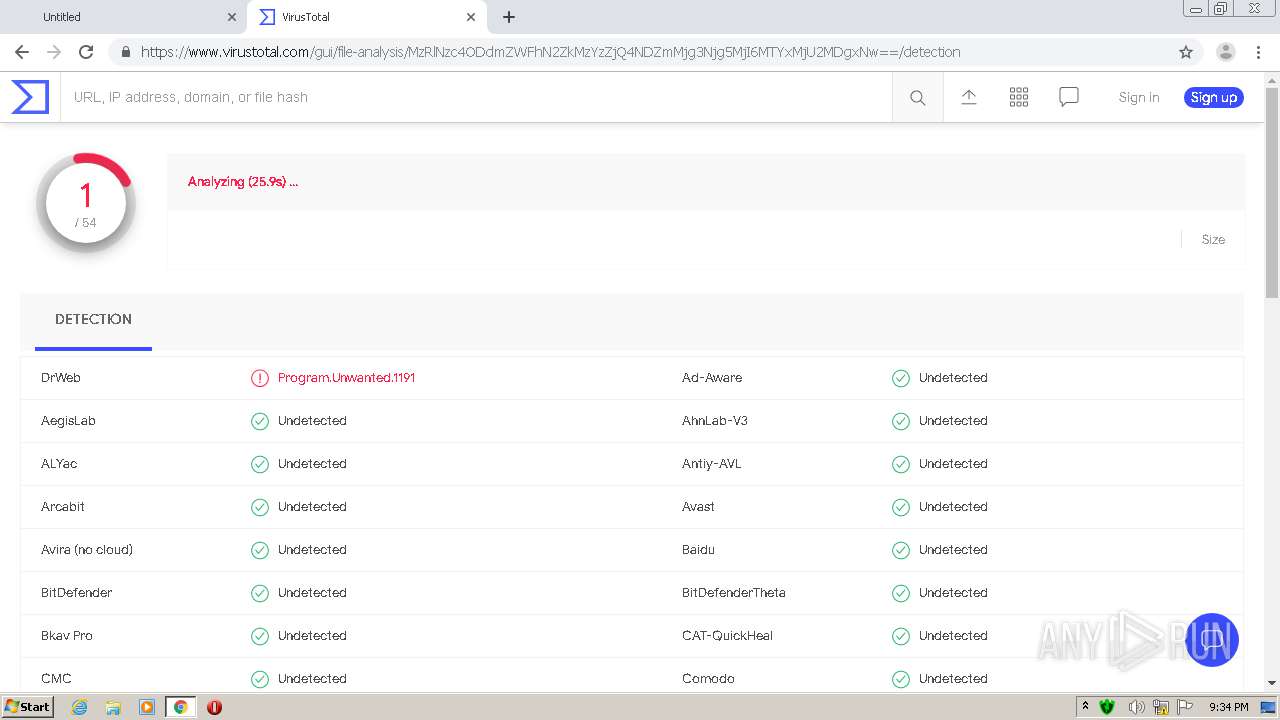
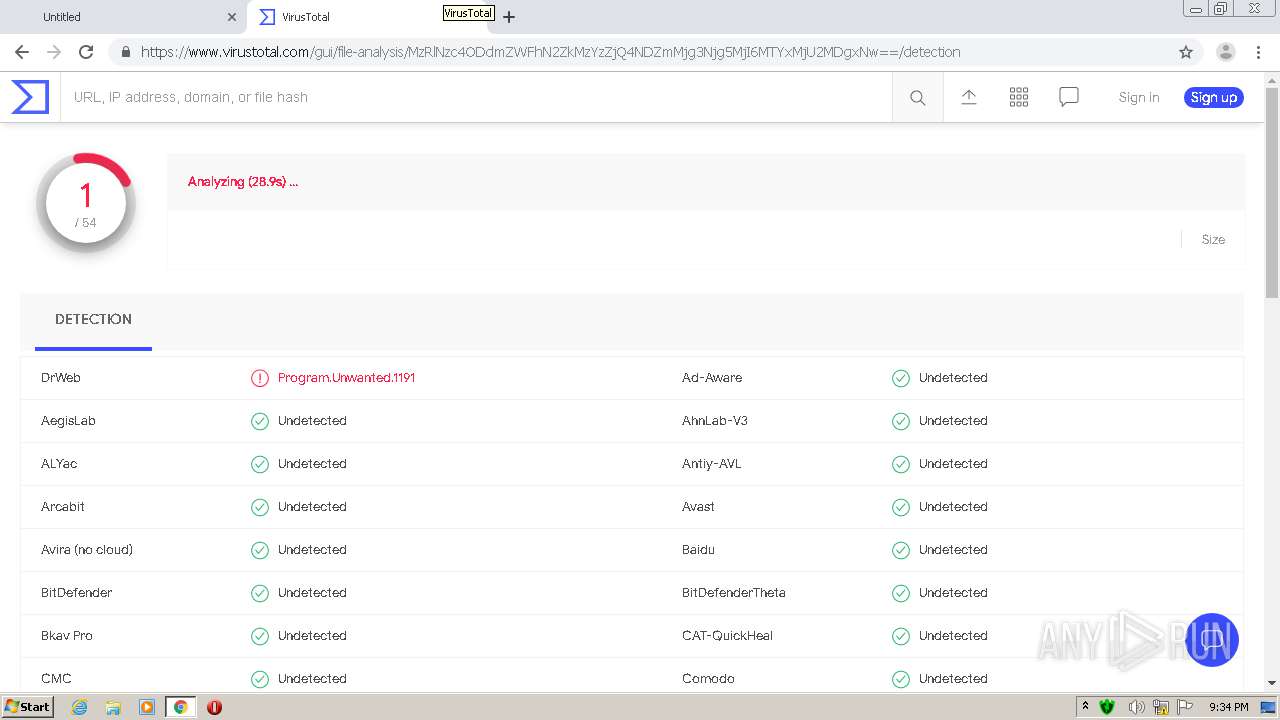
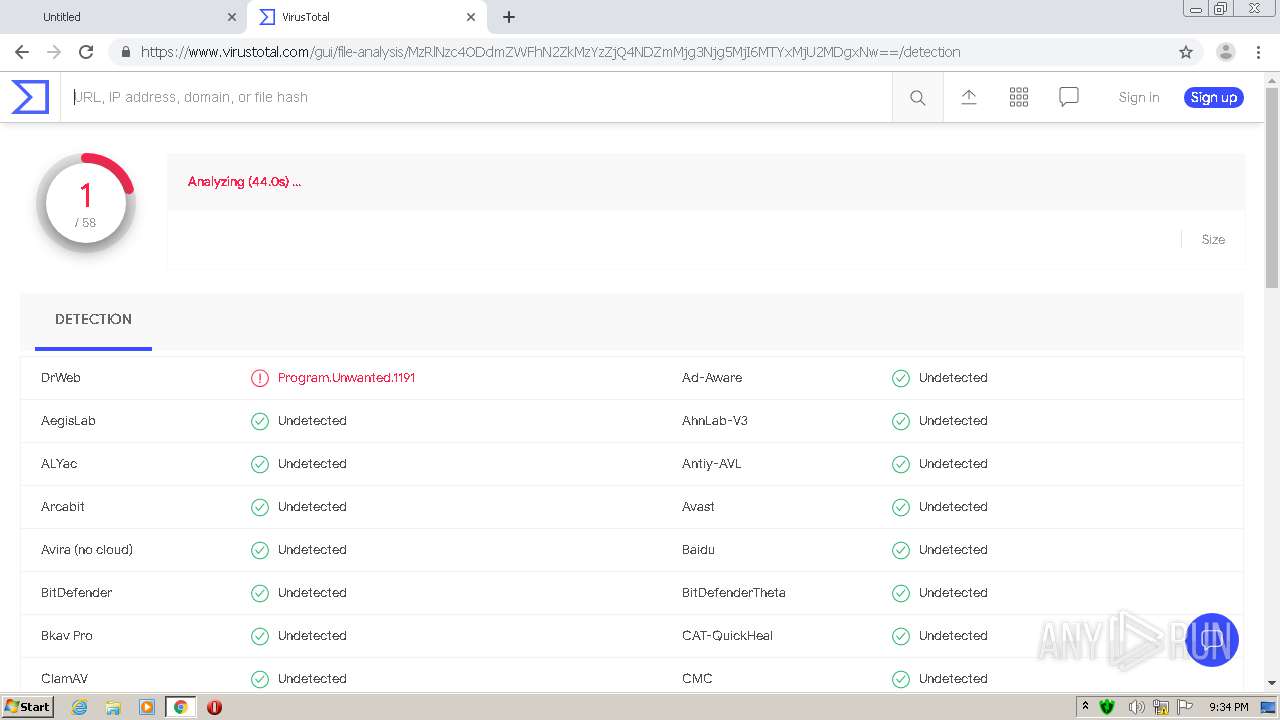
MALICIOUS
Changes settings of System certificates
- MsiExec.exe (PID: 1848)
- AppRemover_CLI.exe (PID: 884)
- svchost.exe (PID: 1048)
Loads the Task Scheduler COM API
- rundll32.exe (PID: 960)
- DllHost.exe (PID: 2640)
Loads dropped or rewritten executable
- rundll32.exe (PID: 4032)
- PCMaticRemoteDesktopServer.exe (PID: 2948)
- PCPitstopRTService.exe (PID: 4056)
- PCMaticRT.exe (PID: 2356)
- PCPitstopRTService.exe (PID: 1792)
- cscript.exe (PID: 3452)
- csrss.exe (PID: 348)
- lsm.exe (PID: 500)
- services.exe (PID: 476)
- svchost.exe (PID: 856)
- lsass.exe (PID: 492)
- wininit.exe (PID: 384)
- svchost.exe (PID: 596)
- svchost.exe (PID: 676)
- svchost.exe (PID: 768)
- svchost.exe (PID: 804)
- IMEDICTUPDATE.EXE (PID: 1376)
- svchost.exe (PID: 1224)
- svchost.exe (PID: 1048)
- svchost.exe (PID: 828)
- spoolsv.exe (PID: 1196)
- WmiPrvSE.exe (PID: 2484)
- SearchFilterHost.exe (PID: 3316)
- SearchProtocolHost.exe (PID: 3296)
- svchost.exe (PID: 1804)
- SearchIndexer.exe (PID: 1996)
- svchost.exe (PID: 2152)
- svchost.exe (PID: 3256)
- wmiprvse.exe (PID: 4044)
- vssvc.exe (PID: 756)
- wmiprvse.exe (PID: 536)
- taskhost.exe (PID: 1984)
- explorer.exe (PID: 376)
- ctfmon.exe (PID: 824)
- host.exe (PID: 3632)
- chrome.exe (PID: 2176)
- chrome.exe (PID: 1236)
- chrome.exe (PID: 496)
- chrome.exe (PID: 3720)
- chrome.exe (PID: 2208)
- taskeng.exe (PID: 2004)
- dwm.exe (PID: 236)
- msiexec.exe (PID: 2592)
- SearchFilterHost.exe (PID: 3796)
- DllHost.exe (PID: 2640)
- wscript.exe (PID: 2792)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 2972)
- reg.exe (PID: 764)
- sc.exe (PID: 3704)
- cmd.exe (PID: 3800)
- sc.exe (PID: 996)
- sc.exe (PID: 3060)
- cmd.exe (PID: 2504)
- cmd.exe (PID: 3168)
- cmd.exe (PID: 2708)
- cmd.exe (PID: 3324)
- net.exe (PID: 3228)
- cmd.exe (PID: 2052)
- sc.exe (PID: 3592)
- net1.exe (PID: 2404)
- cmd.exe (PID: 2984)
- net.exe (PID: 3108)
- net1.exe (PID: 3068)
- pcmaticpushcontroller.exe (PID: 2876)
- cmd.exe (PID: 3136)
- sc.exe (PID: 3900)
- cmd.exe (PID: 2832)
- sc.exe (PID: 2956)
- sc.exe (PID: 2868)
Application was dropped or rewritten from another process
- PCMaticRemoteDesktopServer.exe (PID: 2948)
- pcmaticss-setup.exe (PID: 1160)
- PCPitstopRTService.exe (PID: 4056)
- PCMaticRT.exe (PID: 2356)
- PCPitstopRTService.exe (PID: 1792)
- SuperShieldProcessHooker32.exe (PID: 4016)
- SuperShieldProcessHooker32.exe (PID: 2724)
- PCPitstopScheduleService.exe (PID: 1368)
- PCPitstopScheduleService.exe (PID: 3744)
- PCPitstopScheduleService.exe (PID: 2720)
- SuperShieldProcessHooker32.exe (PID: 2456)
- SuperShieldProcessHooker32.exe (PID: 3200)
- ntrights.exe (PID: 1276)
- ntrights.exe (PID: 2220)
- ntrights.exe (PID: 3876)
- ntrights.exe (PID: 336)
- ntrights.exe (PID: 1920)
- ntrights.exe (PID: 2860)
- ntrights.exe (PID: 1916)
- ntrights.exe (PID: 2000)
- PCPitstopScheduleService.exe (PID: 3032)
- ntrights.exe (PID: 2168)
- ntrights.exe (PID: 1416)
- node.exe (PID: 2464)
- node.exe (PID: 2748)
- node.exe (PID: 2964)
- pcmaticpushcontroller.exe (PID: 2604)
- pcmaticpushcontroller.exe (PID: 2876)
- node.exe (PID: 2256)
- node.exe (PID: 1360)
- SuperShieldProcessHooker32.exe (PID: 3800)
- SuperShieldProcessHooker32.exe (PID: 820)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2284)
Drops executable file immediately after starts
- pcmaticss-setup.exe (PID: 1160)
- pcmaticss-setup.tmp (PID: 1708)
- rundll32.exe (PID: 4032)
Changes the autorun value in the registry
- pcmaticss-setup.tmp (PID: 1708)
Application was injected by another process
- winlogon.exe (PID: 432)
- smss.exe (PID: 264)
- csrss.exe (PID: 392)
- taskeng.exe (PID: 2004)
- explorer.exe (PID: 376)
- srvpost.exe (PID: 1448)
- dwm.exe (PID: 236)
- ctfmon.exe (PID: 824)
- csrss.exe (PID: 348)
- SearchFilterHost.exe (PID: 3316)
- svchost.exe (PID: 768)
- svchost.exe (PID: 804)
- WmiPrvSE.exe (PID: 2484)
- svchost.exe (PID: 1048)
- svchost.exe (PID: 1224)
- svchost.exe (PID: 828)
- SearchProtocolHost.exe (PID: 3296)
- wininit.exe (PID: 384)
- svchost.exe (PID: 596)
- spoolsv.exe (PID: 1196)
- services.exe (PID: 476)
- SearchIndexer.exe (PID: 1996)
- svchost.exe (PID: 676)
- svchost.exe (PID: 1804)
- svchost.exe (PID: 3256)
- svchost.exe (PID: 856)
- host.exe (PID: 3632)
- wmiprvse.exe (PID: 4044)
- lsm.exe (PID: 500)
- wmiprvse.exe (PID: 536)
- lsass.exe (PID: 492)
- svchost.exe (PID: 2152)
- IMEDICTUPDATE.EXE (PID: 1376)
Runs injected code in another process
- SuperShieldProcessHooker32.exe (PID: 4016)
Starts NET.EXE for service management
- cmd.exe (PID: 3880)
- cmd.exe (PID: 1948)
- wscript.exe (PID: 3016)
- wscript.exe (PID: 2612)
- wscript.exe (PID: 1908)
- cmd.exe (PID: 3324)
- cmd.exe (PID: 2984)
Registers / Runs the DLL via REGSVR32.EXE
- PCPitstopScheduleService.exe (PID: 2720)
- PCPitstopScheduleService.exe (PID: 3032)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 2924)
- wscript.exe (PID: 1000)
- cmd.exe (PID: 820)
- cmd.exe (PID: 3476)
Starts NET.EXE to view/change users localgroup
- cmd.exe (PID: 2456)
- cmd.exe (PID: 956)
SUSPICIOUS
Starts Microsoft Installer
- chrome.exe (PID: 1236)
- cmd.exe (PID: 2712)
Executed as Windows Service
- vssvc.exe (PID: 756)
- PCPitstopRTService.exe (PID: 1792)
Starts CMD.EXE for commands execution
- MsiExec.exe (PID: 484)
- MsiExec.exe (PID: 1848)
- cmd.exe (PID: 3232)
- cmd.exe (PID: 2844)
- cmd.exe (PID: 2476)
- cscript.exe (PID: 3452)
- wscript.exe (PID: 1000)
- wscript.exe (PID: 2792)
- MsiExec.exe (PID: 1680)
- node.exe (PID: 2464)
- node.exe (PID: 2748)
- node.exe (PID: 2964)
- node.exe (PID: 2256)
- node.exe (PID: 1360)
- cmd.exe (PID: 3444)
- cmd.exe (PID: 3168)
Adds / modifies Windows certificates
- MsiExec.exe (PID: 1848)
- AppRemover_CLI.exe (PID: 884)
- svchost.exe (PID: 1048)
Starts SC.EXE for service management
- cmd.exe (PID: 3876)
- cmd.exe (PID: 556)
- cmd.exe (PID: 3228)
- cmd.exe (PID: 1944)
- cmd.exe (PID: 3168)
- cmd.exe (PID: 3800)
- cmd.exe (PID: 2504)
- cmd.exe (PID: 2708)
- cmd.exe (PID: 3136)
- cmd.exe (PID: 2052)
- cmd.exe (PID: 764)
- cmd.exe (PID: 2832)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3836)
- rundll32.exe (PID: 4032)
- MsiExec.exe (PID: 1848)
- pcmaticss-setup.exe (PID: 1160)
- pcmaticss-setup.tmp (PID: 1708)
- PCPitstopRTService.exe (PID: 1792)
- node.exe (PID: 2964)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 3836)
- rundll32.exe (PID: 4032)
- pcmaticss-setup.tmp (PID: 1708)
- node.exe (PID: 2964)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2640)
- cmd.exe (PID: 3232)
- cmd.exe (PID: 536)
- cmd.exe (PID: 2440)
- cmd.exe (PID: 3372)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 2796)
- cmd.exe (PID: 2120)
- cmd.exe (PID: 1824)
- cmd.exe (PID: 4092)
- cmd.exe (PID: 184)
- cmd.exe (PID: 2264)
- cmd.exe (PID: 2460)
- cmd.exe (PID: 3832)
- cmd.exe (PID: 692)
- cmd.exe (PID: 3316)
- cmd.exe (PID: 3700)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 3340)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 3952)
- cmd.exe (PID: 2904)
- node.exe (PID: 2464)
- cmd.exe (PID: 2972)
- node.exe (PID: 2748)
- node.exe (PID: 2964)
- node.exe (PID: 1360)
Drops a file with too old compile date
- msiexec.exe (PID: 3836)
Drops a file with a compile date too recent
- msiexec.exe (PID: 3836)
- pcmaticss-setup.tmp (PID: 1708)
- PCPitstopRTService.exe (PID: 1792)
Application launched itself
- cmd.exe (PID: 3232)
- cmd.exe (PID: 2844)
- cmd.exe (PID: 2476)
- node.exe (PID: 2256)
- cmd.exe (PID: 3168)
- cmd.exe (PID: 3444)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 3232)
- cmd.exe (PID: 572)
Changes default file association
- msiexec.exe (PID: 3836)
Creates files in the program directory
- rundll32.exe (PID: 4032)
- PCMaticRT.exe (PID: 2356)
- PCPitstopRTService.exe (PID: 4056)
- cscript.exe (PID: 3452)
- SearchIndexer.exe (PID: 1996)
- PCPitstopRTService.exe (PID: 1792)
- PCPitstopScheduleService.exe (PID: 1368)
- wscript.exe (PID: 1000)
- DllHost.exe (PID: 2640)
- cmd.exe (PID: 3036)
- node.exe (PID: 2464)
- node.exe (PID: 2964)
- pcmaticpushcontroller.exe (PID: 2876)
- node.exe (PID: 1360)
Creates a directory in Program Files
- msiexec.exe (PID: 3836)
- pcmaticss-setup.tmp (PID: 1708)
- node.exe (PID: 2964)
Removes files from Windows directory
- rundll32.exe (PID: 4032)
- PCPitstopRTService.exe (PID: 1792)
- svchost.exe (PID: 1048)
Creates files in the Windows directory
- rundll32.exe (PID: 4032)
- MsiExec.exe (PID: 1848)
- lsass.exe (PID: 492)
- PCPitstopRTService.exe (PID: 1792)
- svchost.exe (PID: 1048)
- svchost.exe (PID: 768)
Creates/Modifies COM task schedule object
- rundll32.exe (PID: 4032)
- regsvr32.exe (PID: 344)
- regsvr32.exe (PID: 3680)
Creates files in the user directory
- explorer.exe (PID: 376)
Creates or modifies windows services
- services.exe (PID: 476)
- pcmaticpushcontroller.exe (PID: 2604)
Reads Windows owner or organization settings
- pcmaticss-setup.tmp (PID: 1708)
Reads the Windows organization settings
- pcmaticss-setup.tmp (PID: 1708)
Executed via COM
- unsecapp.exe (PID: 1712)
Searches for installed software
- AppRemover_CLI.exe (PID: 884)
- pcmaticss-setup.tmp (PID: 1708)
- reg.exe (PID: 2184)
Uses TASKKILL.EXE to kill process
- pcmaticss-setup.tmp (PID: 1708)
Executes scripts
- cmd.exe (PID: 3576)
- PCPitstopScheduleService.exe (PID: 2720)
- PCPitstopScheduleService.exe (PID: 3032)
- cmd.exe (PID: 1724)
- cmd.exe (PID: 1944)
- cmd.exe (PID: 3088)
- cmd.exe (PID: 1352)
- cmd.exe (PID: 1756)
Writes to a desktop.ini file (may be used to cloak folders)
- svchost.exe (PID: 856)
Reads Environment values
- reg.exe (PID: 3828)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 2504)
INFO
Application launched itself
- chrome.exe (PID: 1236)
- msiexec.exe (PID: 3836)
Reads the hosts file
- chrome.exe (PID: 2208)
- chrome.exe (PID: 1236)
Low-level read access rights to disk partition
- vssvc.exe (PID: 756)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 1848)
- AppRemover_CLI.exe (PID: 884)
- pcmaticss-setup.tmp (PID: 1708)
- msiexec.exe (PID: 3836)
- MsiExec.exe (PID: 1680)
Application was dropped or rewritten from another process
- pcmaticss-setup.tmp (PID: 1708)
- AppRemover_CLI.exe (PID: 884)
Reads settings of System Certificates
- AppRemover_CLI.exe (PID: 884)
Creates files in the program directory
- pcmaticss-setup.tmp (PID: 1708)
- AppRemover_CLI.exe (PID: 884)
- msiexec.exe (PID: 3836)
- MsiExec.exe (PID: 1848)
- MsiExec.exe (PID: 1680)
Creates a software uninstall entry
- pcmaticss-setup.tmp (PID: 1708)
- msiexec.exe (PID: 3836)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 3836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
486
Monitored processes
459
Malicious processes
66
Suspicious processes
17
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | cmd /c reg query "HKLM\Software\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-20" /v ProfileImagePath | C:\Windows\system32\cmd.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 184 | \??\C:\Windows\system32\conhost.exe "-73684062418934071513944517091849645272008767169-932283602-557567937-1467260456" | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 236 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 264 | \SystemRoot\System32\smss.exe | C:\Windows\System32\smss.exe | System | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Session Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | cmd /c echo %PROCESSOR_ARCHITEW6432% | C:\Windows\system32\cmd.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 320 | \??\C:\Windows\system32\conhost.exe "-1644028916137653106-382274838-18416767111155376076-2067736481261866964-556627205" | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 336 | "C:\Program Files\PCMatic\PC Matic\\ntrights.exe" +r SeCreateGlobalPrivilege -u PCPitstopSVC | C:\Program Files\PCMatic\PC Matic\ntrights.exe | — | cmd.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 344 | sc query "PCPitstop Scheduling" | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 344 | regsvr32.exe /s jscript.dll | C:\Windows\system32\regsvr32.exe | — | PCPitstopScheduleService.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 348 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
21 564
Read events
14 186
Write events
7 176
Delete events
202
Modification events
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2176) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1236-13257034316626500 |
Value: 259 | |||
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
73
Suspicious files
143
Text files
4 266
Unknown types
61
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-601DB94D-4D4.pma | — | |
MD5:— | SHA256:— | |||
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\80bc75a3-f529-4f2b-8f62-291c86434891.tmp | — | |
MD5:— | SHA256:— | |||
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 828 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\~FontCache-S-1-5-21-1302019708-1500728564-335382590-1000.dat | — | |
MD5:— | SHA256:— | |||
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFced34.TMP | text | |
MD5:— | SHA256:— | |||
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | text | |
MD5:— | SHA256:— | |||
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT~RFcede0.TMP | text | |
MD5:— | SHA256:— | |||
| 1236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFced34.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
75
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2208 | chrome.exe | GET | 302 | 216.239.36.21:80 | http://virustotal.com/ | US | — | — | whitelisted |
1848 | MsiExec.exe | GET | 200 | 23.51.123.27:80 | http://tl.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFBjxN%2BWY73bfUnSOp7HDKJ%2Fbx0wQUV4abVLi%2BpimK5PbC4hMYiYXN3LcCEAkk53ol4NPmnzTXlIvuJVw%3D | NL | der | 1.40 Kb | whitelisted |
1048 | svchost.exe | GET | 200 | 8.241.122.126:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.7 Kb | whitelisted |
2792 | wscript.exe | GET | 200 | 23.51.123.27:80 | http://tl.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFBjxN%2BWY73bfUnSOp7HDKJ%2Fbx0wQUV4abVLi%2BpimK5PbC4hMYiYXN3LcCEAkk53ol4NPmnzTXlIvuJVw%3D | NL | der | 1.40 Kb | whitelisted |
1848 | MsiExec.exe | GET | 200 | 23.51.123.27:80 | http://t2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQwF4prw9S7mCbCEHD%2Fyl6nWPkczAQUe1tFz6%2FOy3r9MZIaarbzRutXSFACEHGgtzaV3bGvwjsrmhjuVMs%3D | NL | der | 1.52 Kb | whitelisted |
2792 | wscript.exe | GET | 200 | 23.51.123.27:80 | http://t2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQwF4prw9S7mCbCEHD%2Fyl6nWPkczAQUe1tFz6%2FOy3r9MZIaarbzRutXSFACEHGgtzaV3bGvwjsrmhjuVMs%3D | NL | der | 1.52 Kb | whitelisted |
1792 | PCPitstopRTService.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/WinPCA.crl | unknown | der | 530 b | whitelisted |
1792 | PCPitstopRTService.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 781 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2208 | chrome.exe | 52.71.28.102:443 | urldefense.com | Amazon.com, Inc. | US | suspicious |
2208 | chrome.exe | 64.233.177.84:443 | accounts.google.com | Google Inc. | US | unknown |
2208 | chrome.exe | 104.21.9.82:443 | avredir.com | Cloudflare Inc | US | unknown |
2208 | chrome.exe | 104.20.82.39:443 | www.pcpitstop.com | Cloudflare Inc | US | shared |
2208 | chrome.exe | 142.250.185.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 52.204.90.22:443 | urldefense.com | Amazon.com, Inc. | US | suspicious |
2208 | chrome.exe | 172.217.18.110:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
— | — | 216.239.36.21:80 | virustotal.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 142.250.185.142:443 | apis.google.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 142.250.185.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urldefense.com |
| shared |
accounts.google.com |
| shared |
avredir.com |
| unknown |
www.pcpitstop.com |
| suspicious |
files.pcpitstop.com |
| suspicious |
ssl.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
PCMaticRT.exe | PidOwner.cpp(49) : [21:33:29] Unicode; Domain:|NT AUTHORITY| User:|SYSTEM|
|
PCMaticRT.exe | Realtime.cpp(339) : [21:33:29] Log file path 'C:\ProgramData\PCPitstop'
|
PCMaticRT.exe | LimitSingleInstance.h(35) : [21:33:29] CLimitSingleInstance: m_hMutex=140 m_dwLastError=0
|
PCMaticRT.exe | Realtime.cpp(392) : [21:33:29] PCMaticRT directory location=C:\Program Files\PCPitstop\Super Shield
|
PCMaticRT.exe | Realtime.cpp(416) : [21:33:29] Load language library dll C:\Program Files\PCPitstop\Super Shield\PCMaticRTen.dll
|
PCMaticRT.exe | ClientComm.cpp(699) : [21:33:29] pid=2356
|
PCMaticRT.exe | PidOwner.cpp(49) : [21:33:29] Unicode; Domain:|NT AUTHORITY| User:|SYSTEM|
|
PCMaticRT.exe | NamedPipe.cpp(120) : [21:33:29] Client opening pipes
|
PCMaticRT.exe | NamedPipe.cpp(125) : [21:33:29] Pipes not ready, sleeping for 5 seconds. Error=2
|
PCPitstopRTService.exe | NTService.cpp(588) : [21:33:29.489] (3600) Start PCMATICRTService
|