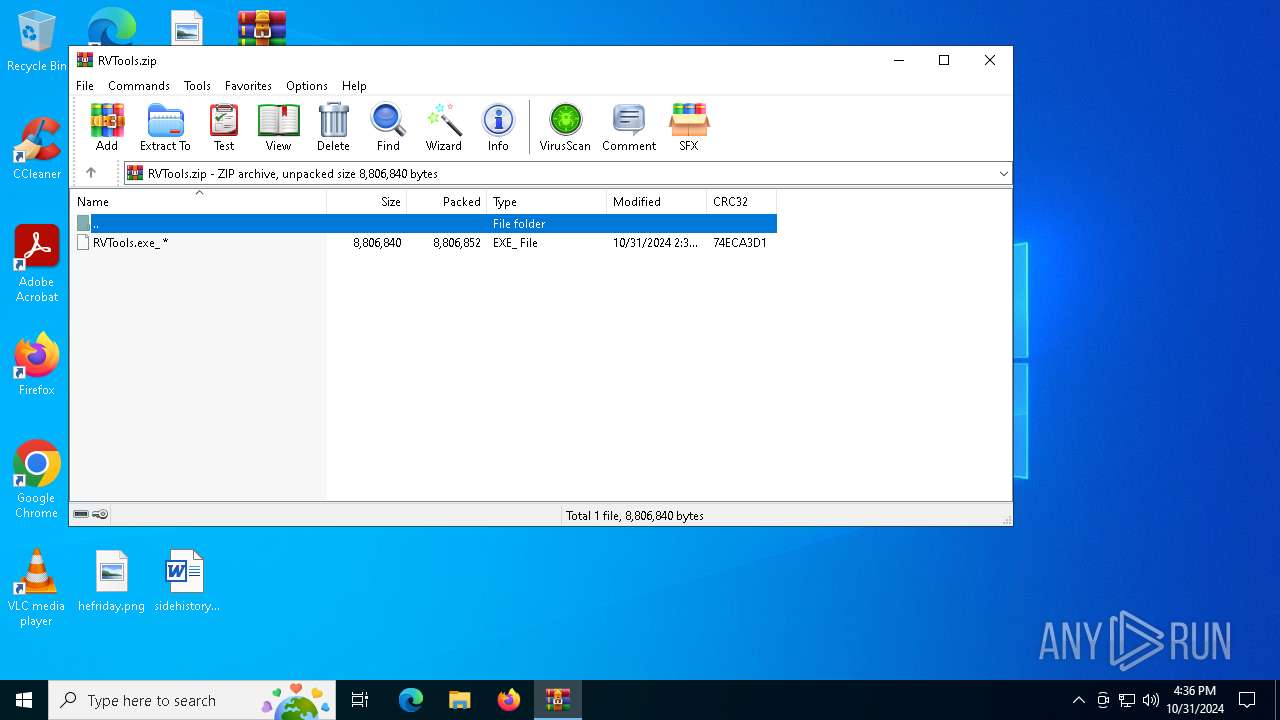
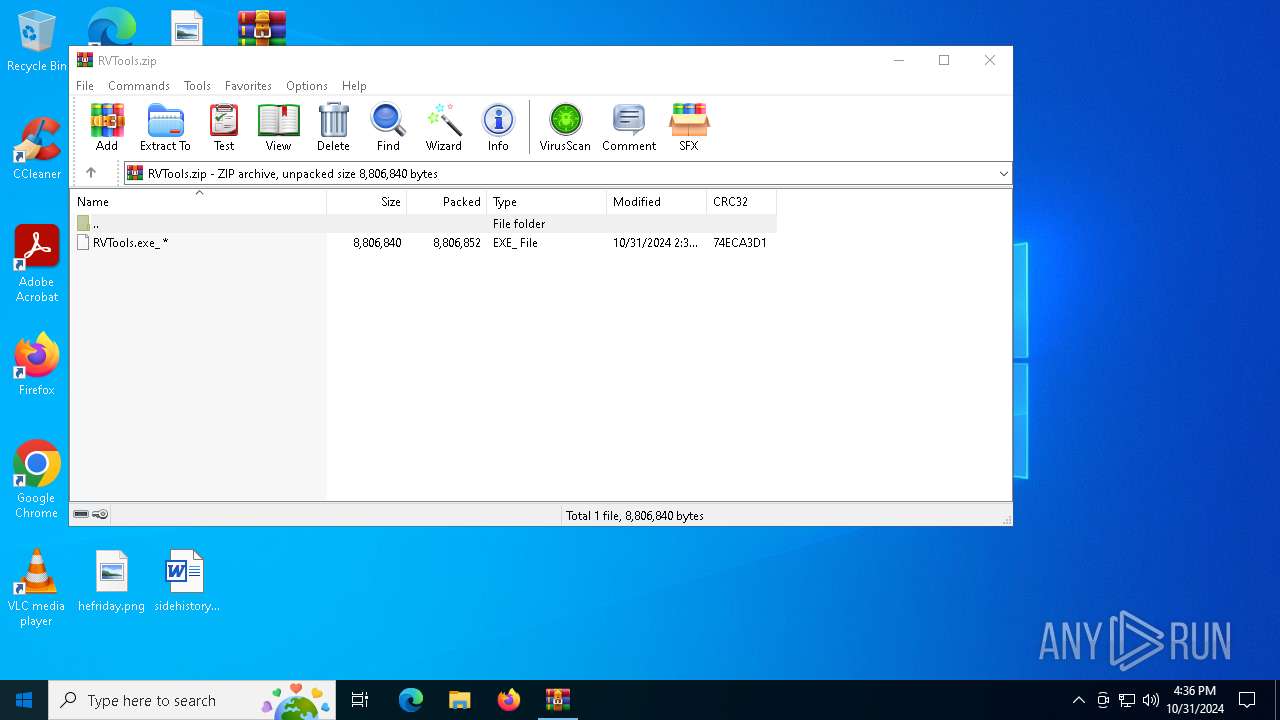
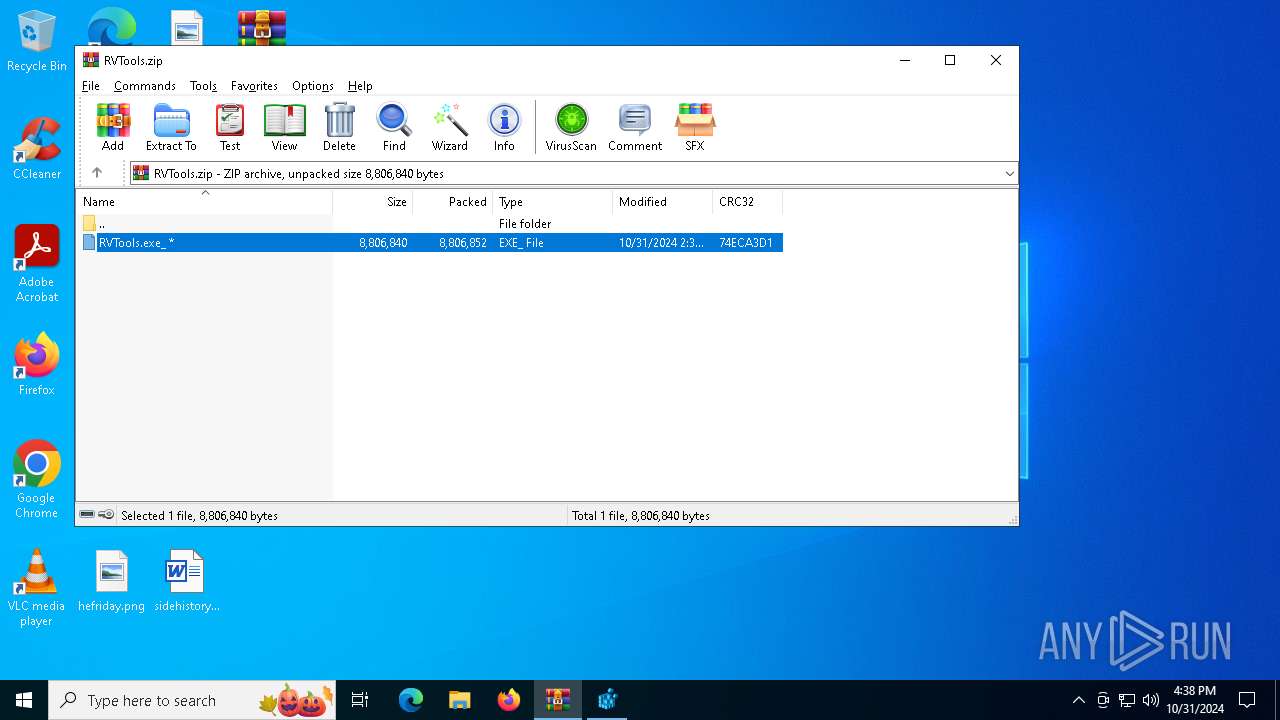
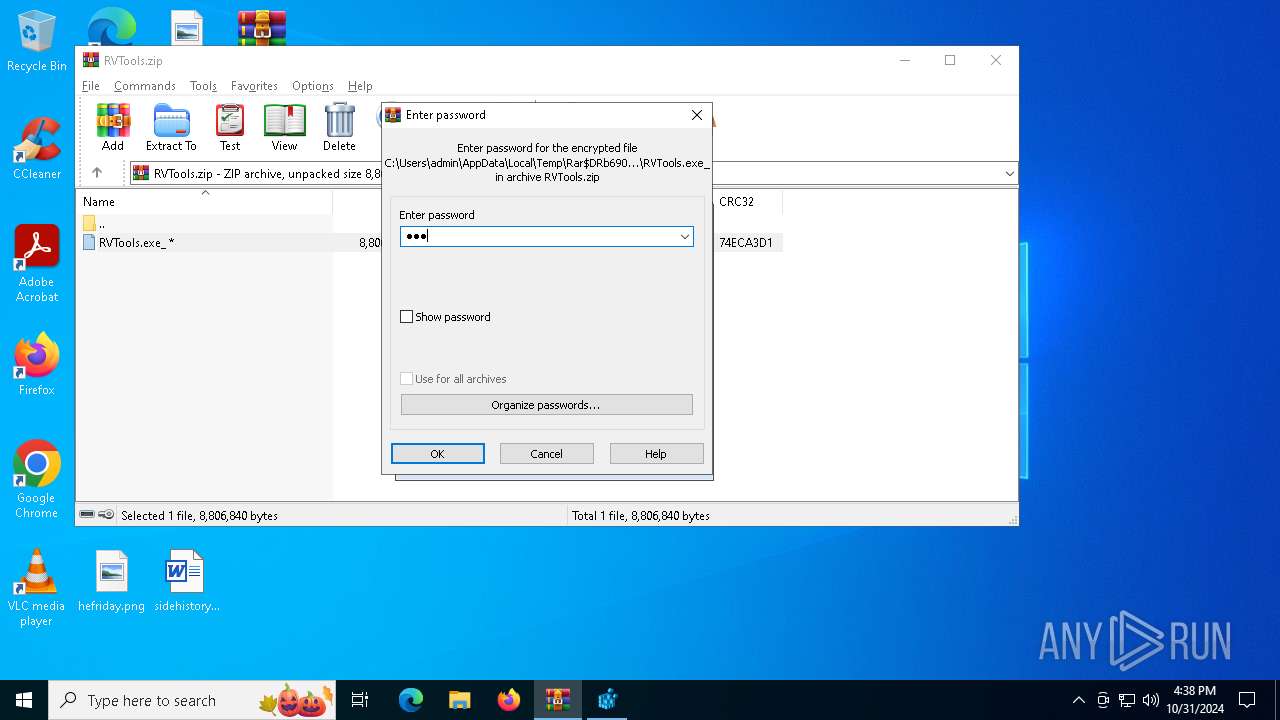
| File name: | RVTools.zip |
| Full analysis: | https://app.any.run/tasks/4b3fd600-4dcf-46a8-a6cb-3fbcd534563f |
| Verdict: | Malicious activity |
| Analysis date: | October 31, 2024, 16:36:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 6810702B85DA4D6478F0374A9FBFD96F |
| SHA1: | 6977619EF689EA236C2C06ED76E2C0E4B5842EBF |
| SHA256: | 0BC3A05692B2BF72A327AD7C63FF5747D137EFBDC2D82AA22C9E1FB077FF36D3 |
| SSDEEP: | 98304:8L16y03N55dFX128kqSAlO50l8LMp7SaTxHCM2qrxXyYGsvIk3MAHVQTiaPR9WWZ:JhXoBuIHK1aOIuqVW+ |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6708)
SUSPICIOUS
Executable content was dropped or overwritten
- RVTools.exe (PID: 7984)
- 7za.exe (PID: 8160)
- csc.exe (PID: 3076)
Drops 7-zip archiver for unpacking
- RVTools.exe (PID: 7984)
Process drops legitimate windows executable
- RVTools.exe (PID: 7984)
- msiexec.exe (PID: 6556)
- 7za.exe (PID: 8160)
Executes as Windows Service
- VSSVC.exe (PID: 6584)
Identifying current user with WHOAMI command
- powershell.exe (PID: 6708)
Starts POWERSHELL.EXE for commands execution
- oleview.exe (PID: 2576)
CSC.EXE is used to compile C# code
- csc.exe (PID: 3076)
INFO
Manual execution by a user
- RVTools.exe (PID: 7936)
- regedit.exe (PID: 6956)
- regedit.exe (PID: 4144)
- RVTools.exe (PID: 7984)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6900)
- msiexec.exe (PID: 8152)
- msiexec.exe (PID: 6556)
Creates or changes the value of an item property via Powershell
- oleview.exe (PID: 2576)
Manages system restore points
- SrTasks.exe (PID: 7572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:31 15:39:14 |
| ZipCRC: | 0x74eca3d1 |
| ZipCompressedSize: | 8806852 |
| ZipUncompressedSize: | 8806852 |
| ZipFileName: | RVTools.exe_ |
Total processes
156
Monitored processes
26
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1376 | sc config msdtc obj= "LocalSystem" | C:\Windows\SysWOW64\sc.exe | — | RVTools.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | C:\Windows\syswow64\MsiExec.exe -Embedding 43F1220CF0C17E4F392874A71A66F0C7 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 2484 | "C:\WINDOWS\system32\whoami.exe" | C:\Windows\System32\whoami.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2576 | C:\ProgramData\Microsoft\WindowsUpdate24\oleview.exe | C:\ProgramData\Microsoft\WindowsUpdate24\oleview.exe | — | RVTools.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: OLE/COM Object Viewer Version: 10.0.26100.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\w14nodc5\w14nodc5.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 | |||||||||||||||
| 3764 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4144 | "C:\WINDOWS\regedit.exe" | C:\Windows\regedit.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6356 | sc config msdtc start= demand | C:\Windows\SysWOW64\sc.exe | — | RVTools.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 706
Read events
11 642
Write events
47
Delete events
17
Modification events
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\RVTools.zip | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
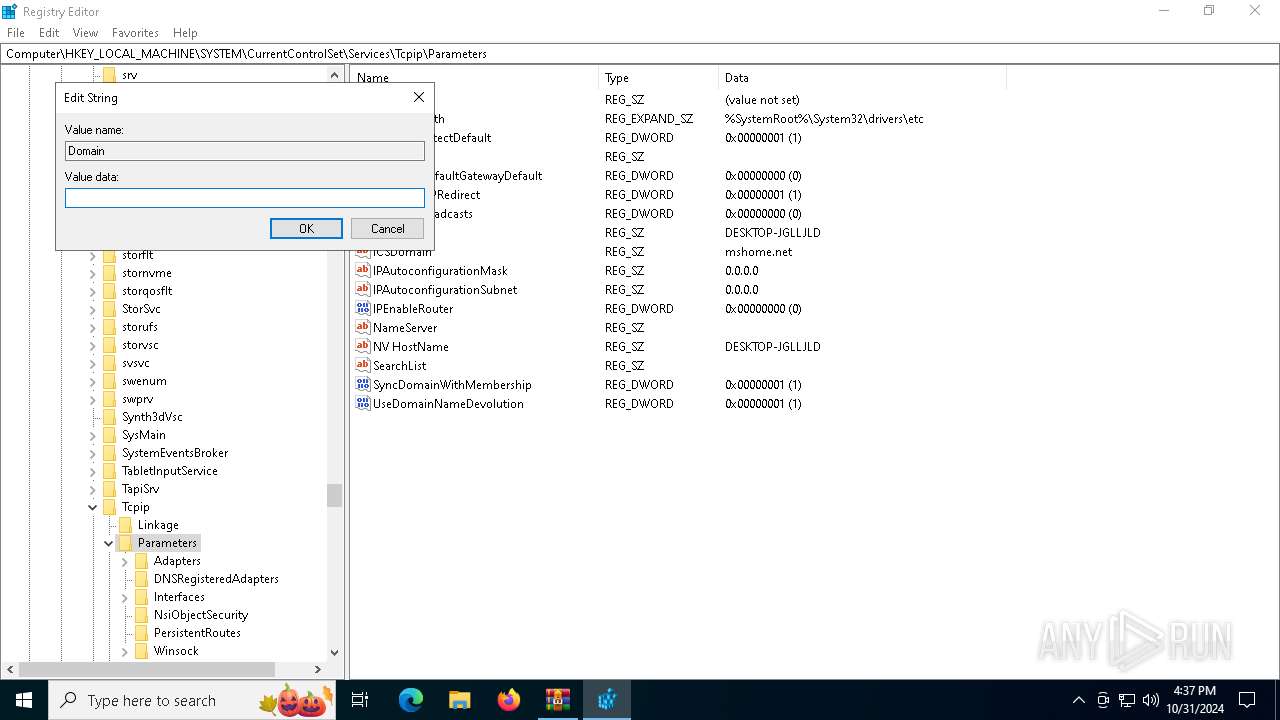
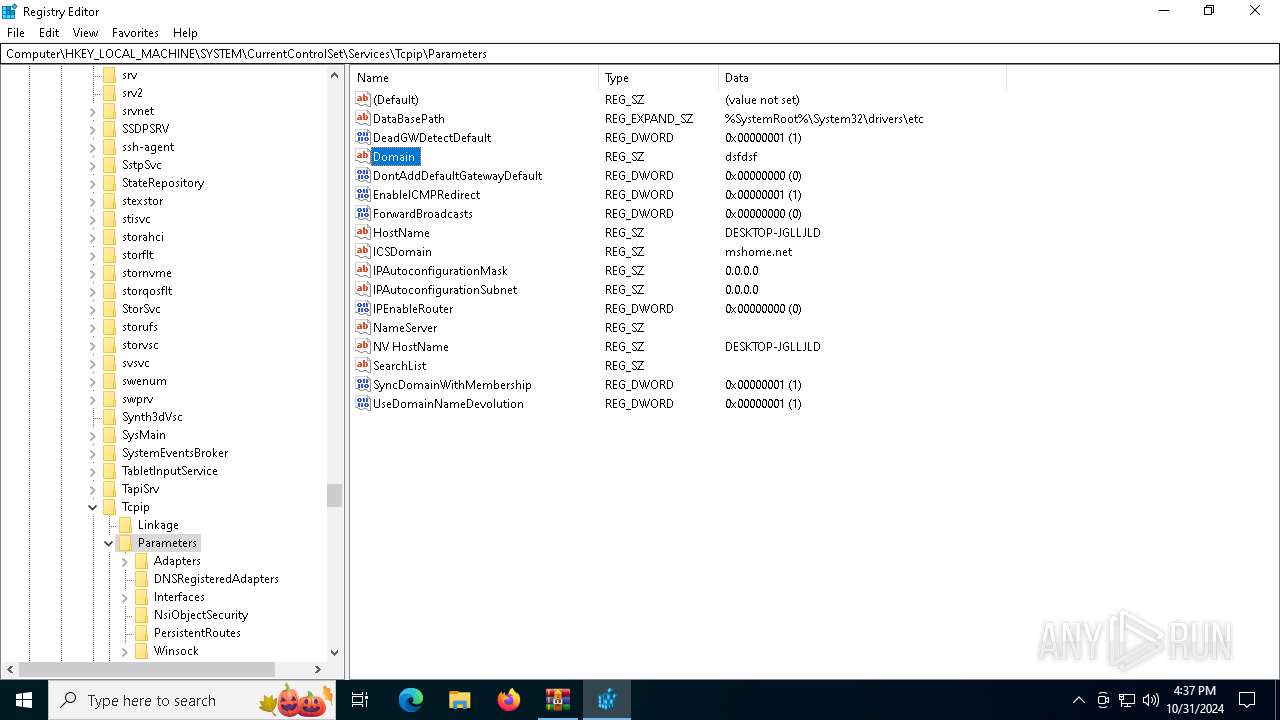
| (PID) Process: | (4144) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | Domain |
Value: dsfdsf | |||
| (PID) Process: | (6900) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (8152) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 503006091D97D4F5AE39F7CBE7927D7D652D3431 |
Value: | |||
| (PID) Process: | (8152) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\503006091D97D4F5AE39F7CBE7927D7D652D3431 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000EE2931BC327E9AE6E8B5F751B43471901D0000000100000010000000E871723E266F38AF5D49CDA2A502669C0B000000010000001E00000045006E0074007200750073007400200028003200300034003800290000007F000000010000002C000000302A060A2B0601040182370A030406082B0601050507030506082B0601050507030606082B06010505070307090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F0000000100000014000000327FC447408DE9BF596F83D4B2FA4B8E3E7097D8030000000100000014000000503006091D97D4F5AE39F7CBE7927D7D652D343119000000010000001000000091FAD483F14848A8A69B18B805CDBB3A530000000100000041000000303F3020060A6086480186FA6C0A010230123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C06200000001000000200000006DC47172E01CBCB0BF62580D895FE2B8AC9AD4F873801E0C10B9C837D21EB17714000000010000001400000055E481D11180BED889B908A331F9A1240916B9707E000000010000000800000000C001B39667D60120000000010000002E0400003082042A30820312A00302010202043863DEF8300D06092A864886F70D01010505003081B431143012060355040A130B456E74727573742E6E65743140303E060355040B14377777772E656E74727573742E6E65742F4350535F3230343820696E636F72702E206279207265662E20286C696D697473206C6961622E2931253023060355040B131C286329203139393920456E74727573742E6E6574204C696D69746564313330310603550403132A456E74727573742E6E65742043657274696669636174696F6E20417574686F7269747920283230343829301E170D3939313232343137353035315A170D3239303732343134313531325A3081B431143012060355040A130B456E74727573742E6E65743140303E060355040B14377777772E656E74727573742E6E65742F4350535F3230343820696E636F72702E206279207265662E20286C696D697473206C6961622E2931253023060355040B131C286329203139393920456E74727573742E6E6574204C696D69746564313330310603550403132A456E74727573742E6E65742043657274696669636174696F6E20417574686F726974792028323034382930820122300D06092A864886F70D01010105000382010F003082010A0282010100AD4D4BA91286B2EAA320071516642A2B4BD1BF0B4A4D8EED8076A567B77840C07342C868C0DB532BDD5EB8769835938B1A9D7C133A0E1F5BB71ECFE524141EB181A98D7DB8CC6B4B03F1020CDCABA54024007F7494A19D0829B3880BF587779D55CDE4C37ED76A64AB851486955B9732506F3DC8BA660CE3FCBDB849C176894919FDC0A8BD89A3672FC69FBC711960B82DE92CC99076667B94E2AF78D665535D3CD69CB2CF2903F92FA450B2D448CE0532558AFDB2644C0EE4980775DB7FDFB9085560853029F97B48A46986E3353F1E865D7A7A15BDEF008E1522541700902693BC0E496891BFF847D39D9542C10E4DDF6F26CFC3182162664370D6D5C007E10203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041455E481D11180BED889B908A331F9A1240916B970300D06092A864886F70D010105050003820101003B9B8F569B30E753997C7A79A74D97D7199590FB061FCA337C46638F966624FA401B2127CAE67273F24FFE3199FDC80C4C6853C680821398FAB6ADDA5D3DF1CE6EF6151194820CEE3F95AF11AB0FD72FDE1F038F572C1EC9BB9A1A4495EB184FA61FCD7D57102F9B04095A84B56ED81D3AE1D69ED16C795E791C14C5E3D04C933B653CEDDF3DBEA6E5951AC3B519C3BD5E5BBBFF23EF6819CB1293275C032D6F30D01EB61AACDE5AF7D1AAA827A6FE7981C479993357BA12B0A9E0426C93CA56DEFE6D840B088B7E8DEAD79821C6F3E73C792F5E9CD14C158DE1EC2237CC9A430B97DC80908DB3679B6F48081556CFBFF12B7C5E9A76E95990C57C8335116551 | |||
Executable files
35
Suspicious files
30
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7984 | RVTools.exe | C:\ProgramData\Microsoft\WindowsUpdate24\tools.7z | — | |
MD5:— | SHA256:— | |||
| 8028 | 7za.exe | C:\ProgramData\Microsoft\WindowsUpdate24\RVTools.msi | — | |
MD5:— | SHA256:— | |||
| 7984 | RVTools.exe | C:\Users\admin\AppData\Local\Temp\nsdE6EA.tmp\nsExec.dll | executable | |
MD5:11092C1D3FBB449A60695C44F9F3D183 | SHA256:2CD3A2D4053954DB1196E2526545C36DFC138C6DE9B81F6264632F3132843C77 | |||
| 7984 | RVTools.exe | C:\ProgramData\Microsoft\WindowsUpdate24\7za.exe | executable | |
MD5:A5B1537D0E569AC9402B3F68238ACD76 | SHA256:2C39B62EDF81F576DCB1A80679B0EBFC67787761236E38C78466AF026C8A60FA | |||
| 8152 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\026A86A161D256DBB33076EDF20C0E5E_586120603910E6A9024E2F8513B0F104 | binary | |
MD5:DCC42568CE85C60D41002E3D91DF4C78 | SHA256:8D0AA6653A7E28950C864BDA5FE114E2233D9DF7F1CA901669CC69B4B6D2B236 | |||
| 7984 | RVTools.exe | C:\ProgramData\Microsoft\WindowsUpdate24\UpdateFull.7z | compressed | |
MD5:D22B627B5FBB5B1EBFFE0372D052144E | SHA256:54BE52B80B881F6DE2270E1FA5F062FDB8CB51599FF72FA1B0FFFB0EA1745D5B | |||
| 8160 | 7za.exe | C:\ProgramData\Microsoft\WindowsUpdate24\kautix2aeX.t | text | |
MD5:28468E78EFEDC6000F40D582C7E1D8DB | SHA256:B2B953BB7424B73AF385615CEECE9742F75F3954B81B30163402B15BADA8C18E | |||
| 7984 | RVTools.exe | C:\ProgramData\Microsoft\WindowsUpdate24\7za.dll | executable | |
MD5:BDA80D260EE69E6075E68F8C34F328E3 | SHA256:C4E3F8F2852314864B2B51C049C327F399395ACF52F1BB8CA18B358BCEDB4143 | |||
| 8160 | 7za.exe | C:\ProgramData\Microsoft\WindowsUpdate24\aclui-2.dll | executable | |
MD5:FE20BF13EBB9157226FDF3670E01231A | SHA256:556D3DCEA423E658A53CDBD43CDE2DDD1C29590706F926B4D8F210C4F17B4670 | |||
| 6556 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
67
DNS requests
35
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2364 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7556 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8152 | msiexec.exe | GET | 200 | 69.192.162.201:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRr2bwARTxMtEy9aspRAZg5QFhagQQUgrrWPZfOn89x6JI3r%2F2ztWk1V88CEHHvVXSvNVTDWixp9m9La80%3D | unknown | — | — | whitelisted |
8152 | msiexec.exe | GET | 200 | 69.192.162.201:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRRKiO2Poi0XFwdRr1PZXruPzTMZAQU75%2B6ebBz8iUeeJwDUpwbU4Teje0CEErhypfEK2Gwjfs6YRuPAPk%3D | unknown | — | — | whitelisted |
8152 | msiexec.exe | GET | 200 | 69.192.162.201:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCEE5A5DdU7eaMAAAAAFHTlH8%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4292 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 104.126.37.184:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] DNS Query to Cloudflare Worker App |
— | — | Misc activity | ET INFO Observed Cloudflare workers.dev Domain in TLS SNI |
— | — | Misc activity | ET INFO Observed DNS Query to Cloudflare workers.dev Domain |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |