| File name: | OlympicScreensaver.zip |
| Full analysis: | https://app.any.run/tasks/db6f469a-ad18-4c8c-a84a-337970cf1276 |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2022, 23:45:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B9AEDB353706D551EFCBED81FC88F221 |
| SHA1: | 1AA7A8F95C08CFF37B0B4131E8D4518BF0771CA3 |
| SHA256: | 0BA6A0019C7E8A31A0525A4774295D15D2A70CFA9EAFD692793167C0F0A71953 |
| SSDEEP: | 98304:NXh3/iAQn1imuG7BLA+0E9PmdSDfpngDVQeaOZlB:NxvV2uIB6EgMfyDaOh |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3328)
- ntvdm.exe (PID: 1692)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3328)
Reads the computer name
- WinRAR.exe (PID: 3328)
Executes application which crashes
- csrstub.exe (PID: 3100)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3328)
- ntvdm.exe (PID: 1692)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3328)
- ntvdm.exe (PID: 1692)
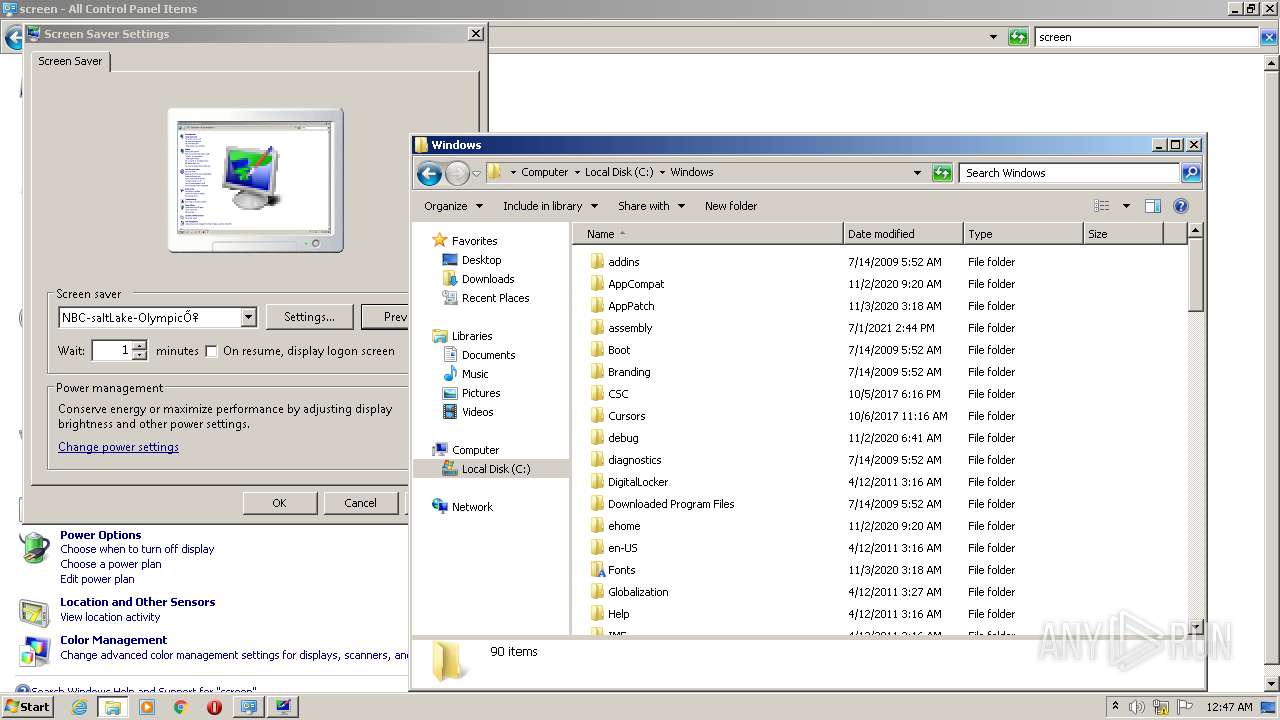
Creates files in the Windows directory
- ntvdm.exe (PID: 1692)
INFO
Checks supported languages
- csrstub.exe (PID: 3100)
- ntvdm.exe (PID: 1692)
- rundll32.exe (PID: 2032)
- explorer.exe (PID: 3044)
Manual execution by user
- csrstub.exe (PID: 3100)
- rundll32.exe (PID: 2032)
- explorer.exe (PID: 3044)
Reads the computer name
- rundll32.exe (PID: 2032)
- explorer.exe (PID: 3044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
46
Monitored processes
5
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1692 | "C:\Windows\system32\ntvdm.exe" -i1 -ws | C:\Windows\system32\ntvdm.exe | csrstub.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
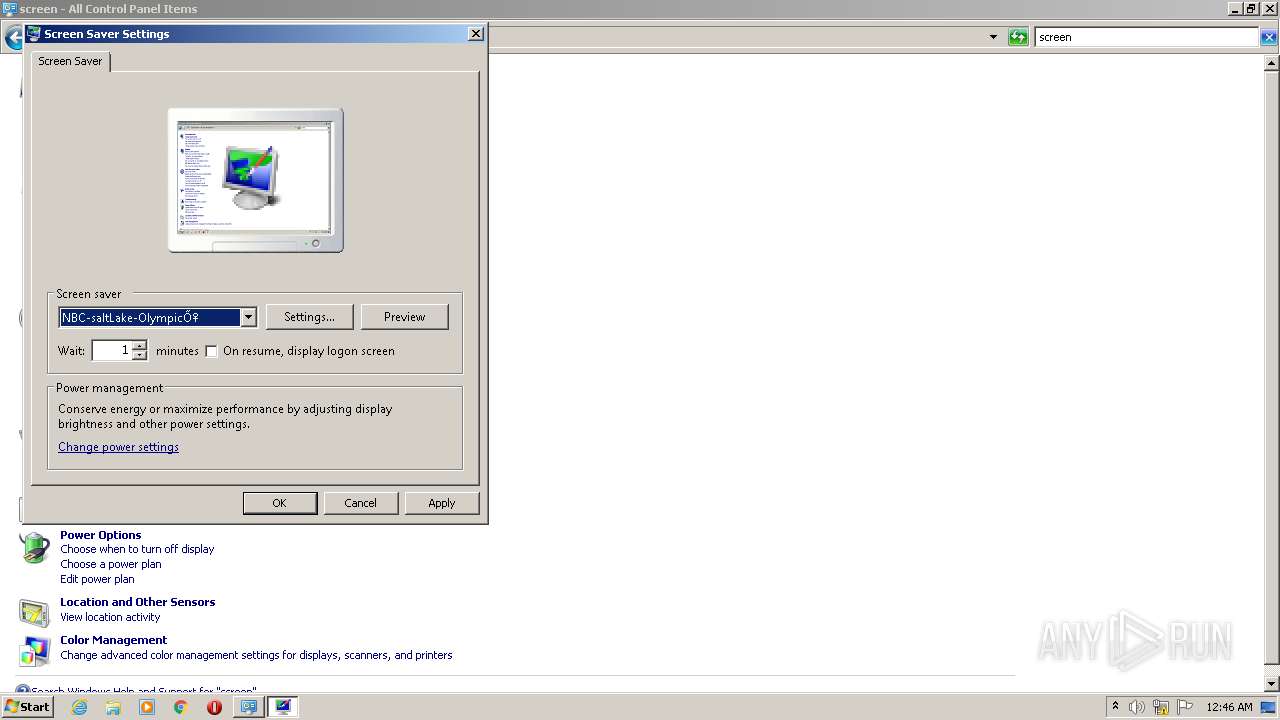
| 2032 | "C:\Windows\system32\rundll32.exe" shell32.dll,Control_RunDLL desk.cpl,screensaver,@screensaver | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3044 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3100 | C:\Windows\system32\csrstub.exe 67634196 -P "C:\Users\admin\Desktop\NBCSETUP.EXE" | C:\Windows\system32\csrstub.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: allows lua to launch 16-bit applications Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3328 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\OlympicScreensaver.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 092
Read events
1 051
Write events
41
Delete events
0
Modification events
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\OlympicScreensaver.zip | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1692 | ntvdm.exe | C:\Windows\NBCSETUP.scr | executable | |
MD5:— | SHA256:— | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\NBCSETUP.EXE | executable | |
MD5:— | SHA256:— | |||
| 1692 | ntvdm.exe | C:\Windows\NBCSETUP.exe | executable | |
MD5:— | SHA256:— | |||
| 2032 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Themes\Custom.theme | text | |
MD5:C1FCF55A48CAF02CBC0FEC89C8B44C9D | SHA256:1497F2B7237A7DAEF8DF4568F8BFEF1B7B8FEBE4082A797725C410DF1CE3B961 | |||
| 1692 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsB682.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 1692 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsB692.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report