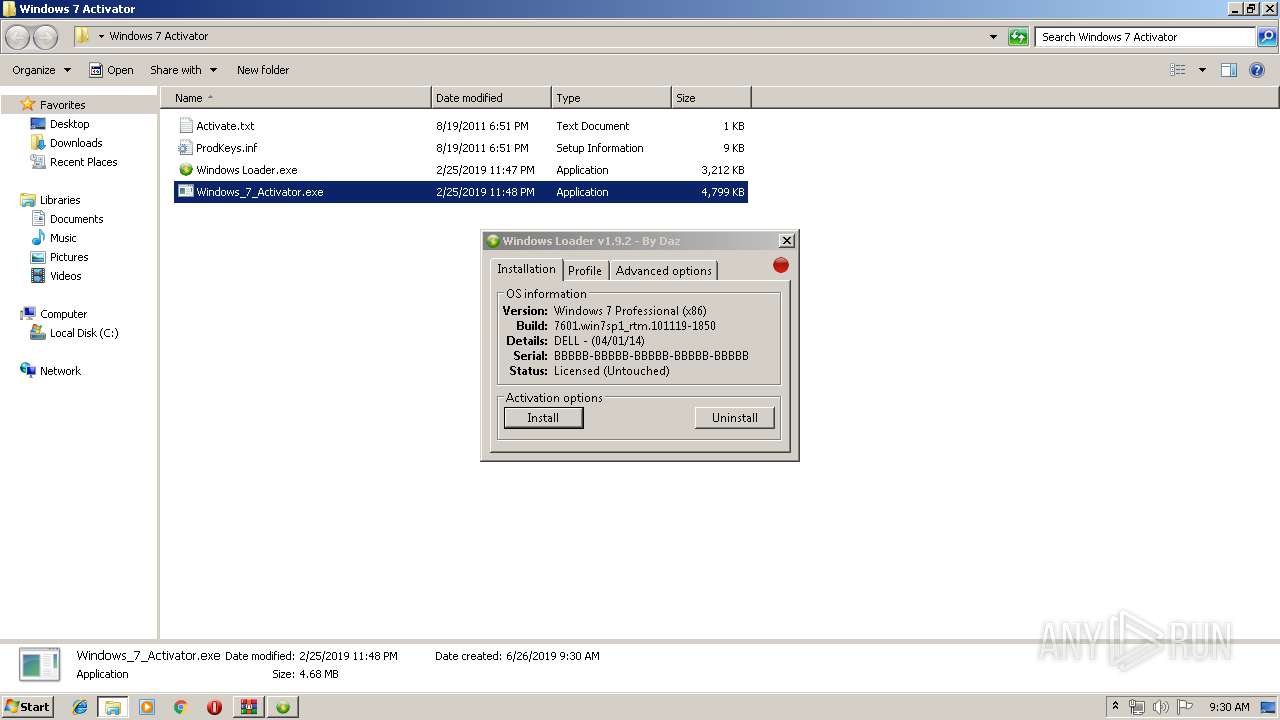
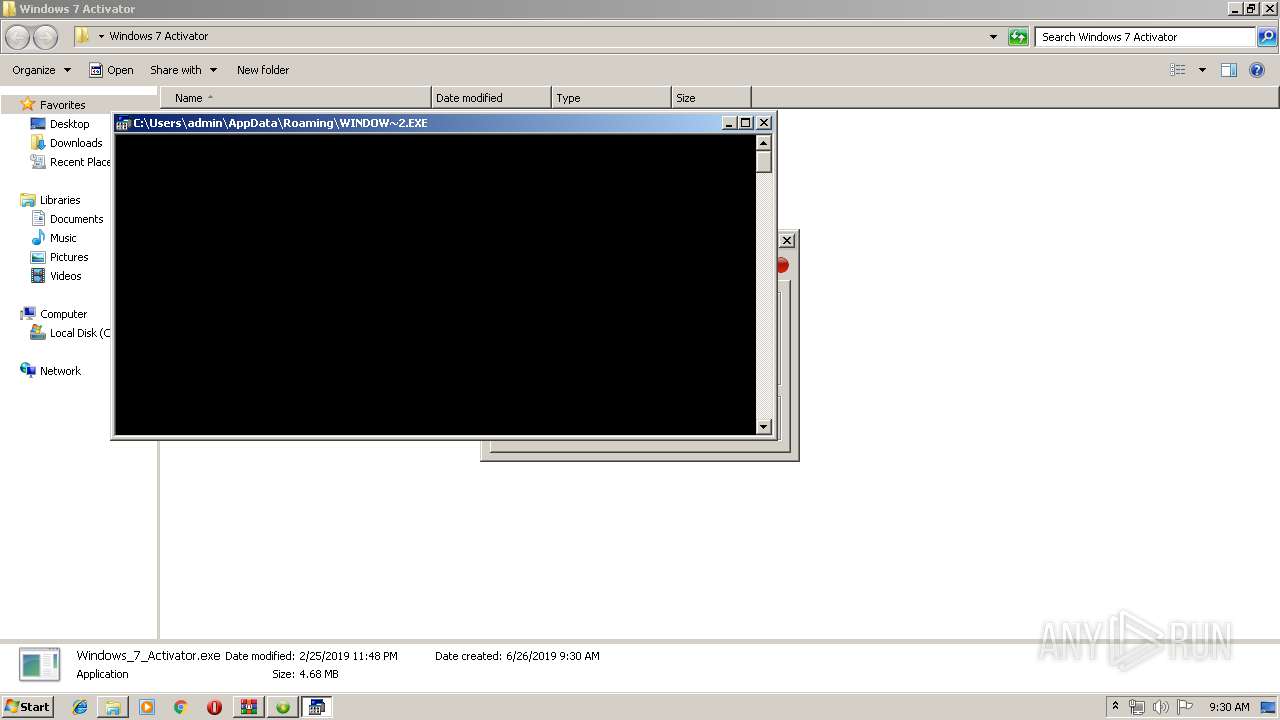
| File name: | Windows 7 Activator Reloaded [Team Rjaa].zip |
| Full analysis: | https://app.any.run/tasks/453f8e8c-540b-4b1e-8926-8ecb48370a4d |
| Verdict: | Malicious activity |
| Analysis date: | June 26, 2019, 08:29:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4FD8D270F84C4D4323FF4C20BF29D2C5 |
| SHA1: | 9604C38D673B4BB6CCACB9242B8FA5CC3C7F0748 |
| SHA256: | 0B9EE7718817A386DE36EB1CA34EF78E81E3761FE63097E245C613FDF994C90B |
| SSDEEP: | 196608:dEyaJJRbr2POiWWD4wWxju+OMmjkU8m5zgq:za/RmPOD4au+OTjkURgq |
MALICIOUS
Application was dropped or rewritten from another process
- SeafkoAgent.exe (PID: 3112)
- SeafkoAgent.exe (PID: 1904)
- Windows Loader.exe (PID: 2088)
Changes the autorun value in the registry
- SeafkoAgent.exe (PID: 1904)
- SeafkoAgent.exe (PID: 3112)
Changes settings of System certificates
- SeafkoAgent.exe (PID: 3112)
SUSPICIOUS
Creates files in the user directory
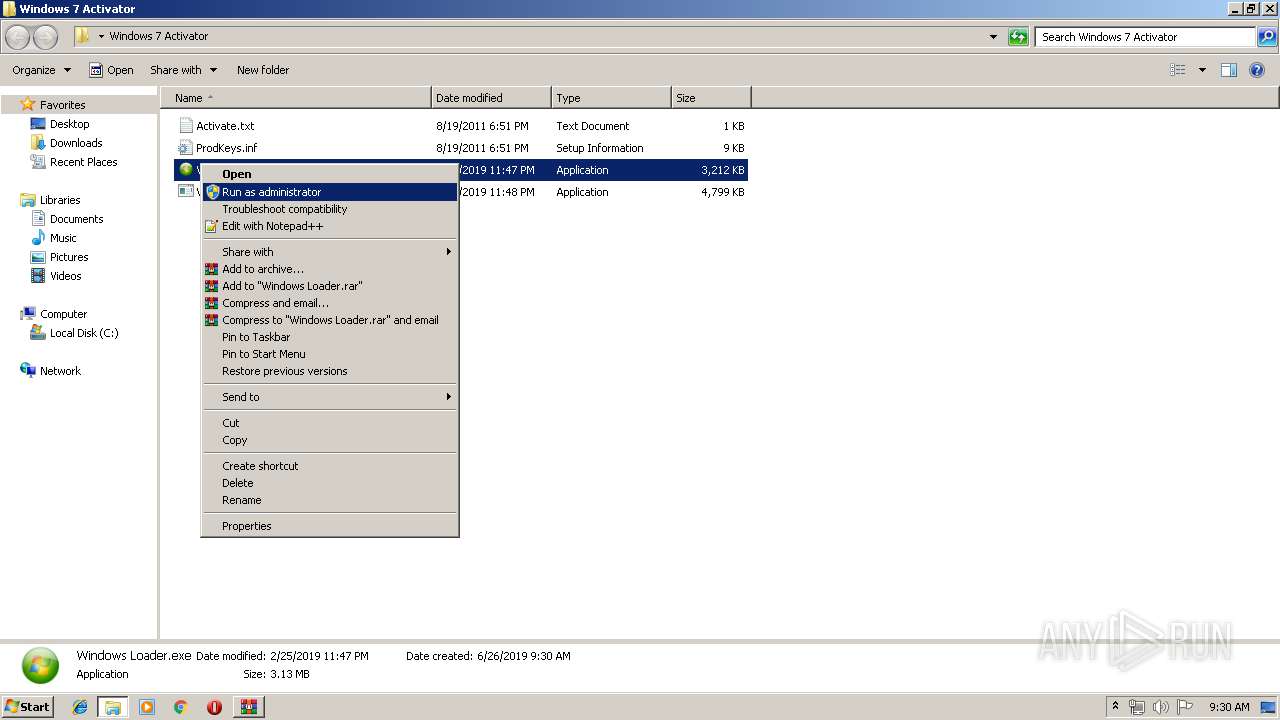
- Windows Loader.exe (PID: 3208)
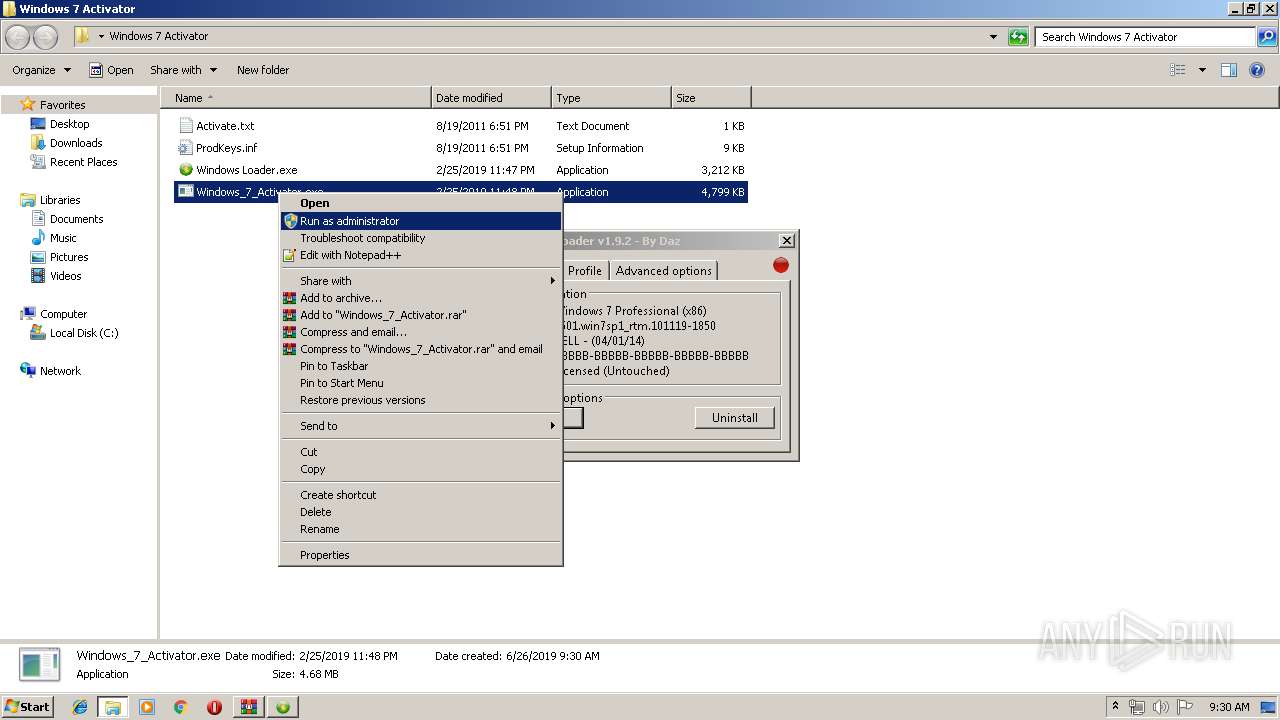
- Windows_7_Activator.exe (PID: 3272)
Executable content was dropped or overwritten
- Windows Loader.exe (PID: 3208)
- SeafkoAgent.exe (PID: 3112)
Checks for external IP
- SeafkoAgent.exe (PID: 3112)
Executes application which crashes
- Windows_7_Activator.exe (PID: 3272)
Creates executable files which already exist in Windows
- SeafkoAgent.exe (PID: 3112)
Executed as Windows Service
- WmiApSrv.exe (PID: 1524)
Adds / modifies Windows certificates
- SeafkoAgent.exe (PID: 3112)
INFO
Manual execution by user
- Windows Loader.exe (PID: 3208)
- Windows_7_Activator.exe (PID: 3272)
Reads settings of System Certificates
- SeafkoAgent.exe (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2011:08:19 18:51:10 |
| ZipCRC: | 0xdc52d4ca |
| ZipCompressedSize: | 133 |
| ZipUncompressedSize: | 172 |
| ZipFileName: | Windows 7 Activator/Activate.txt |
Total processes
50
Monitored processes
8
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Windows 7 Activator Reloaded [Team Rjaa].zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1524 | C:\Windows\system32\wbem\WmiApSrv.exe | C:\Windows\system32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | "C:\Users\admin\AppData\Roaming\SeafkoAgent.exe" | C:\Users\admin\AppData\Roaming\SeafkoAgent.exe | Windows_7_Activator.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
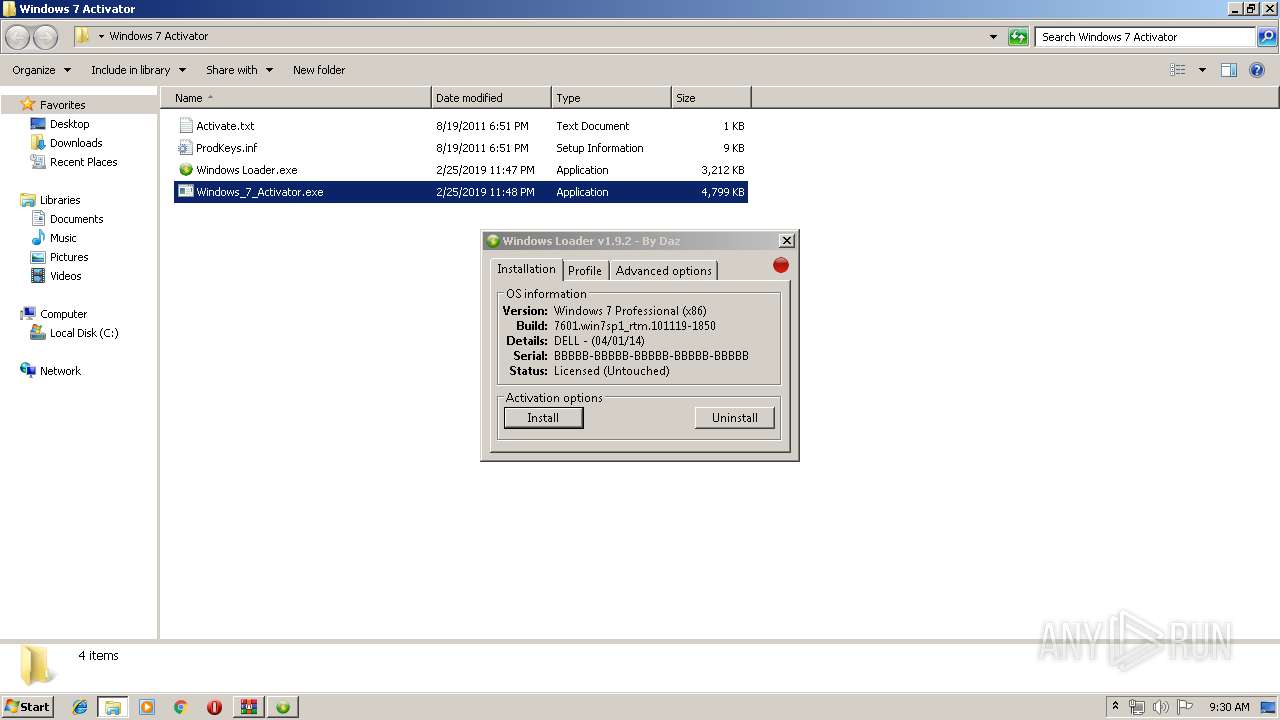
| 2088 | "C:\Users\admin\AppData\Roaming\Windows Loader.exe" | C:\Users\admin\AppData\Roaming\Windows Loader.exe | — | Windows Loader.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2968 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | Windows_7_Activator.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3112 | "C:\Users\admin\AppData\Roaming\SeafkoAgent.exe" | C:\Users\admin\AppData\Roaming\SeafkoAgent.exe | Windows Loader.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3208 | "C:\Users\admin\Desktop\Windows 7 Activator\Windows Loader.exe" | C:\Users\admin\Desktop\Windows 7 Activator\Windows Loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3272 | "C:\Users\admin\Desktop\Windows 7 Activator\Windows_7_Activator.exe" | C:\Users\admin\Desktop\Windows 7 Activator\Windows_7_Activator.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
1 381
Read events
1 327
Write events
54
Delete events
0
Modification events
| (PID) Process: | (296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (296) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows 7 Activator Reloaded [Team Rjaa].zip | |||
| (PID) Process: | (296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3112) SeafkoAgent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | explorer |
Value: C:\Users\admin\AppData\Local\explorer.exe | |||
| (PID) Process: | (3112) SeafkoAgent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SeafkoAgent_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
3
Suspicious files
0
Text files
2
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
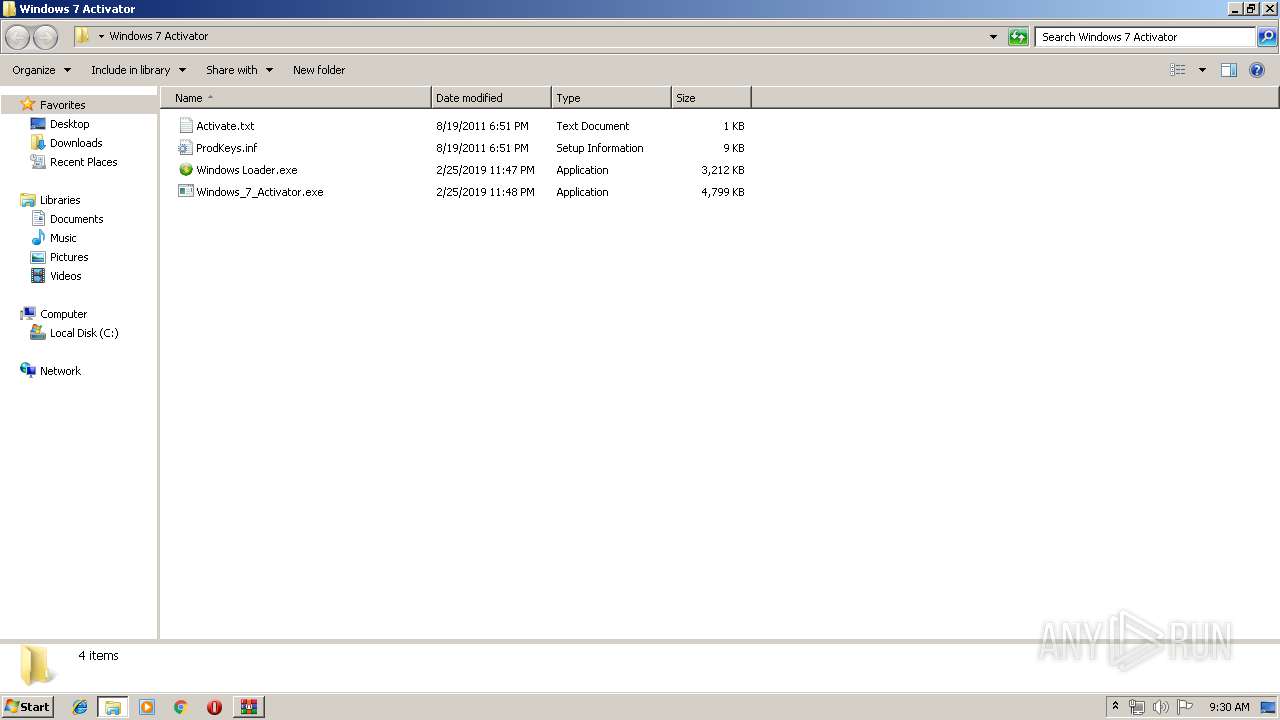
| 296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa296.31562\Windows 7 Activator\Activate.txt | — | |
MD5:— | SHA256:— | |||
| 296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa296.31562\Windows 7 Activator\ProdKeys.inf | — | |
MD5:— | SHA256:— | |||
| 296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa296.31562\Windows 7 Activator\Windows Loader.exe | — | |
MD5:— | SHA256:— | |||
| 296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa296.31562\Windows 7 Activator\Windows_7_Activator.exe | — | |
MD5:— | SHA256:— | |||
| 3208 | Windows Loader.exe | C:\Users\admin\AppData\Roaming\data.xml | — | |
MD5:— | SHA256:— | |||
| 3272 | Windows_7_Activator.exe | C:\Users\admin\AppData\Roaming\data.xml | — | |
MD5:— | SHA256:— | |||
| 3272 | Windows_7_Activator.exe | C:\Users\admin\AppData\Roaming\Windows_7_Activator.exe | — | |
MD5:— | SHA256:— | |||
| 2968 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs6E14.tmp | — | |
MD5:— | SHA256:— | |||
| 2968 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs6E15.tmp | — | |
MD5:— | SHA256:— | |||
| 3112 | SeafkoAgent.exe | C:\Users\admin\AppData\Local\Microsoft\SeafkoAgent.exe_Url_k2ifdwiijzcfo45vluw4asoq2xxwupwh\1.0.0.0\dqkewlhp.newcfg | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
7
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3112 | SeafkoAgent.exe | GET | 204 | 216.58.205.238:80 | http://clients3.google.com/generate_204 | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3112 | SeafkoAgent.exe | 216.58.205.238:80 | clients3.google.com | Google Inc. | US | whitelisted |
3112 | SeafkoAgent.exe | 216.239.36.21:443 | ipinfo.io | Google Inc. | US | whitelisted |
3112 | SeafkoAgent.exe | 145.14.144.143:443 | mired-intensity.000webhostapp.com | Hostinger International Limited | US | shared |
3112 | SeafkoAgent.exe | 192.186.136.206:6669 | irc.abjects.net | B2 Net Solutions Inc. | CA | malicious |
3112 | SeafkoAgent.exe | 5.9.164.48:6667 | irc.alphachat.net | Hetzner Online GmbH | DE | unknown |
3112 | SeafkoAgent.exe | 92.61.32.19:6667 | irc.data.lt | Telia Lietuva, AB | LT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients3.google.com |
| whitelisted |
ipinfo.io |
| shared |
mired-intensity.000webhostapp.com |
| shared |
irc.data.lt |
| unknown |
irc.abjects.net |
| malicious |
irc.alphachat.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3112 | SeafkoAgent.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3112 | SeafkoAgent.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
1048 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
3112 | SeafkoAgent.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
Process | Message |
|---|---|
SeafkoAgent.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
SeafkoAgent.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|