| File name: | OpenSSH-Win64-v9.8.1.0.msi |
| Full analysis: | https://app.any.run/tasks/bd71d5b4-55b1-4c5e-98ba-6bacc8ffd7ce |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2024, 06:52:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: OpenSSH, Author: Microsoft Corporation, Keywords: Installer, Comments: This installer database contains the logic and data required to install OpenSSH., Template: x64;1033, Revision Number: {26A385CD-79E9-4C06-BC1E-88ECA005EC4F}, Create Time/Date: Thu Oct 10 14:30:54 2024, Last Saved Time/Date: Thu Oct 10 14:30:54 2024, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.14.1.8722), Security: 2 |
| MD5: | 6A09B54F687938992C76E7098251759F |
| SHA1: | 2970856C7857C296606CA48E61601DDA91B3FACE |
| SHA256: | 0B9D5910956DC4616BCE2F8FC86ED27187F0B0FBAF4C3DDA26F8FAA7C291BDD0 |
| SSDEEP: | 98304:+VtaSafY/CwViCKv2Oxyxag0oeXKN4kKL2zSOdmFDtvwPJYRd8Lm4Y/mBWzxrzDH:NrAMVfq |
MALICIOUS
No malicious indicators.SUSPICIOUS
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- msiexec.exe (PID: 7664)
- wevtutil.exe (PID: 7720)
Executes as Windows Service
- ssh-agent.exe (PID: 7960)
- VSSVC.exe (PID: 3952)
- sshd.exe (PID: 7988)
Application launched itself
- ssh-agent.exe (PID: 7960)
INFO
An automatically generated document
- msiexec.exe (PID: 6804)
Creates files or folders in the user directory
- msiexec.exe (PID: 6804)
Manages system restore points
- SrTasks.exe (PID: 7432)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6804)
Reads the software policy settings
- msiexec.exe (PID: 6804)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1376)
Manual execution by a user
- msiexec.exe (PID: 2428)
- scp.exe (PID: 7616)
- sshd.exe (PID: 2132)
- ssh.exe (PID: 7924)
- sftp-server.exe (PID: 7712)
- ssh-add.exe (PID: 8060)
- sftp.exe (PID: 7704)
- ssh-agent.exe (PID: 3744)
- sshd-session.exe (PID: 2808)
- ssh-keyscan.exe (PID: 2000)
- ssh-sk-helper.exe (PID: 4292)
- ssh-shellhost.exe (PID: 4232)
- ssh-pkcs11-helper.exe (PID: 1748)
- ssh-keygen.exe (PID: 7456)
- cmd.exe (PID: 7240)
- notepad++.exe (PID: 7928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | OpenSSH |
| Author: | Microsoft Corporation |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install OpenSSH. |
| Template: | x64;1033 |
| RevisionNumber: | {26A385CD-79E9-4C06-BC1E-88ECA005EC4F} |
| CreateDate: | 2024:10:10 14:30:54 |
| ModifyDate: | 2024:10:10 14:30:54 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.14.1.8722) |
| Security: | Read-only recommended |
Total processes
206
Monitored processes
57
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ssh-shellhost.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 692 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ssh-pkcs11-helper.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 824 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1376 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) | ||||
| 1748 | "C:\Program Files\OpenSSH\ssh-pkcs11-helper.exe" | C:\Program Files\OpenSSH\ssh-pkcs11-helper.exe | explorer.exe | |
User: admin Integrity Level: HIGH Exit code: 0 Version: 9.8.1.0 | ||||
| 2000 | "C:\Program Files\OpenSSH\ssh-keyscan.exe" | C:\Program Files\OpenSSH\ssh-keyscan.exe | explorer.exe | |
User: admin Integrity Level: HIGH Exit code: 1 Version: 9.8.1.0 | ||||
| 2132 | "C:\Program Files\OpenSSH\sshd.exe" | C:\Program Files\OpenSSH\sshd.exe | explorer.exe | |
User: admin Integrity Level: HIGH Exit code: 0 Version: 9.8.1.0 | ||||
| 2428 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\OpenSSH-Win64-v9.8.1.0.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) | ||||
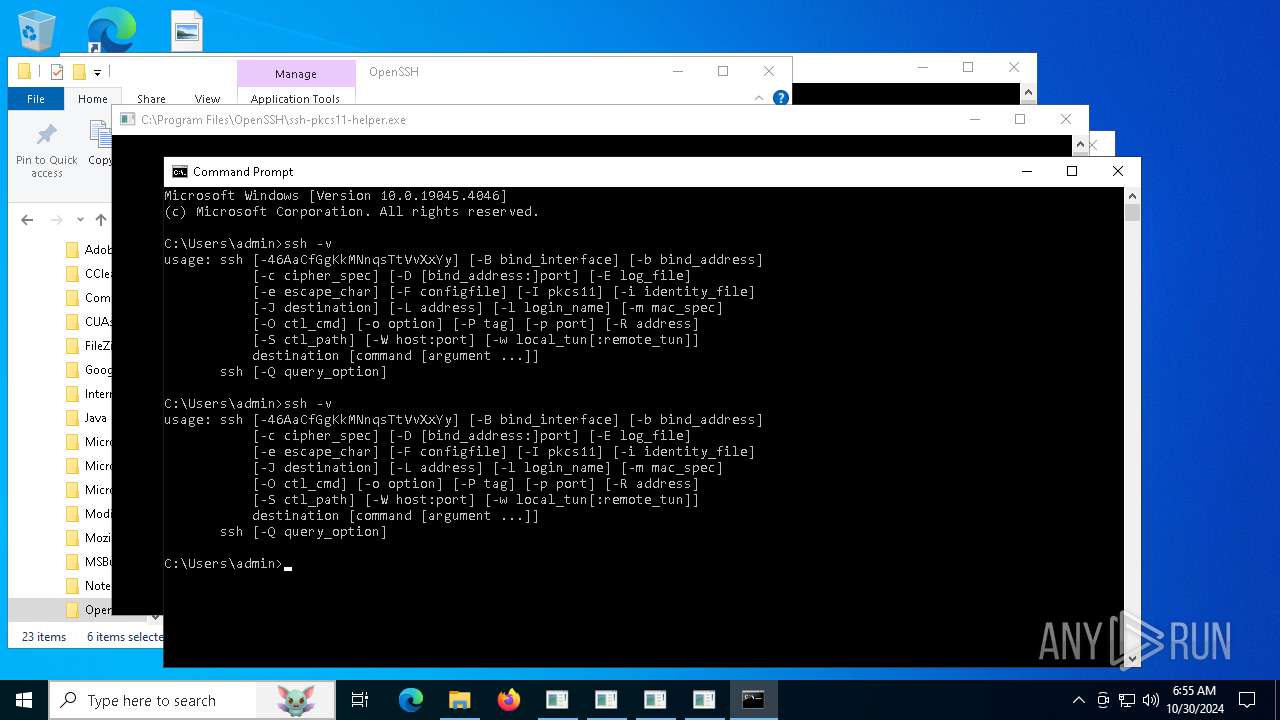
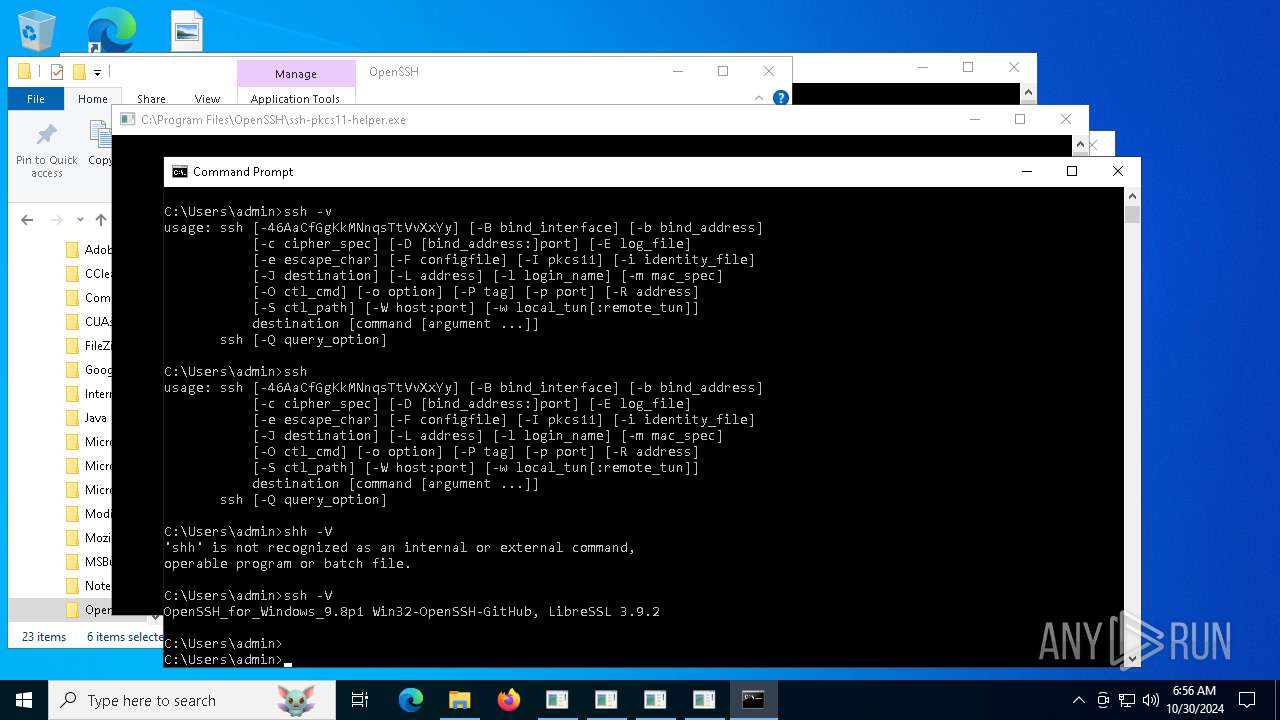
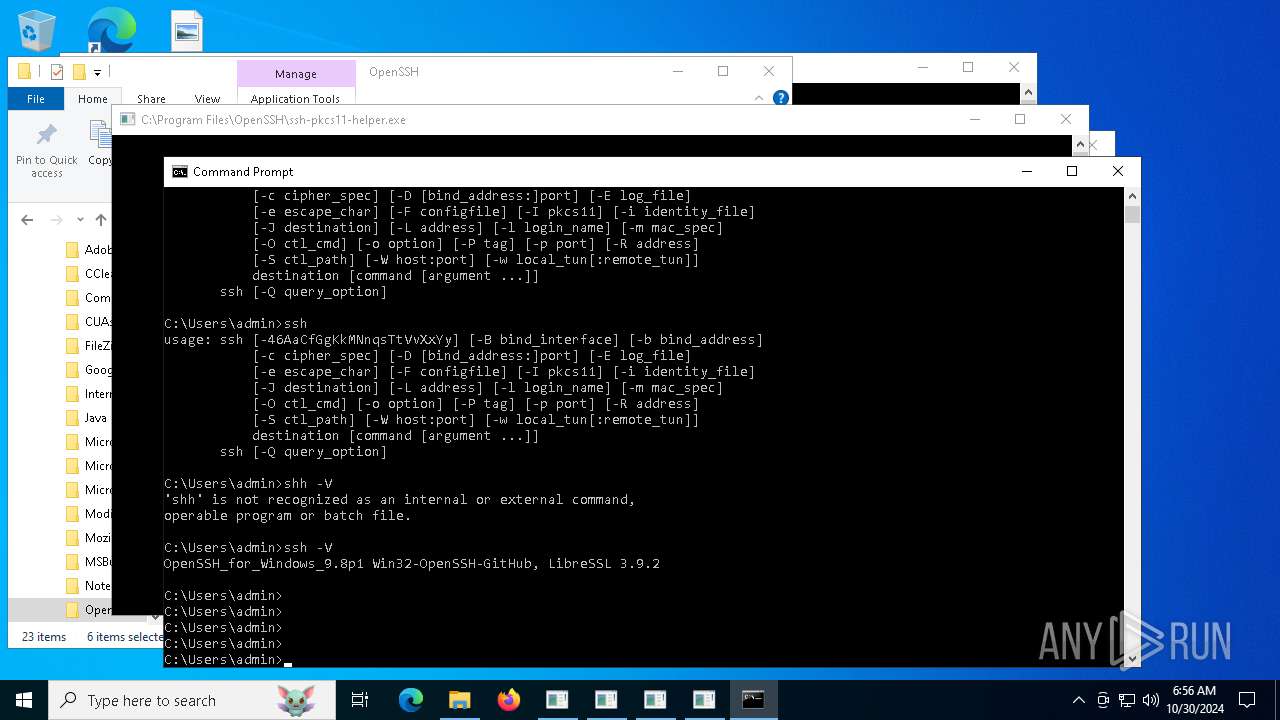
| 2576 | ssh -v | C:\Program Files\OpenSSH\ssh.exe | — | cmd.exe |
User: admin Integrity Level: MEDIUM Exit code: 255 Version: 9.8.1.0 | ||||
| 2808 | "C:\Program Files\OpenSSH\sshd-session.exe" | C:\Program Files\OpenSSH\sshd-session.exe | explorer.exe | |
User: admin Integrity Level: HIGH Exit code: 255 Version: 9.8.1.0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
32
Suspicious files
36
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1376 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1376 | msiexec.exe | C:\Windows\Installer\93dc8.msi | — | |
MD5:— | SHA256:— | |||
| 6804 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C0018BB1B5834735BFA60CD063B31956 | binary | |
MD5:AED93172B2224B5E204EBAA995F57A68 | SHA256:ECBA07B48A11D25F466A2AE4430C980337CC146F056AA8D1AFE7DAE826C448C2 | |||
| 1376 | msiexec.exe | C:\Windows\Installer\MSI4088.tmp | executable | |
MD5:65A7BA0C797CD22E7C4E7E9AEC4D1C40 | SHA256:C9090349C993552D3E49F3D13B03EADED5022803F662C7CF3DF73873C2DC4C72 | |||
| 6804 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C0018BB1B5834735BFA60CD063B31956 | der | |
MD5:732CFEB76B91C4D13978A00B8C666ED7 | SHA256:9FAB9FC0A1DA813E6DDB93904C1FCFA6546CFBE70747FF8468DDD14D2552DBD2 | |||
| 1376 | msiexec.exe | C:\Windows\Installer\MSI4154.tmp | executable | |
MD5:02E45C930EA91CC9B3C9977404B1003E | SHA256:87EA6200A9DB47422F5A4732E7D2F930F819E308F3D41C0C10921F195F1656AF | |||
| 1376 | msiexec.exe | C:\Windows\Temp\~DF86508BF54B63158C.TMP | binary | |
MD5:805C1A31E1AB3A33E3F594A5EE34E14D | SHA256:5D37C0F16756BCA24087E5DAC4CC71D98D1EC376124FE52FA0D94F73E4033649 | |||
| 1376 | msiexec.exe | C:\Windows\Installer\MSI41B4.tmp | executable | |
MD5:60E8C139E673B9EB49DC83718278BC88 | SHA256:B181B6B4D69A53143A97A306919BA1ADBC0B036A48B6D1D41AE7A01E8EF286CB | |||
| 1376 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{5c82fb9d-63b9-4dd9-bc31-91aa77d7ae5b}_OnDiskSnapshotProp | binary | |
MD5:88A71BB86C4B26190D0642488B51C556 | SHA256:BC76CBE0CC2560ED88EEE5D1A1511E9013C38E903485EE6B8DF04E8732D6E6D0 | |||
| 1376 | msiexec.exe | C:\Windows\Installer\MSI4078.tmp | binary | |
MD5:9220729C352365CFF6104617AD5F2A07 | SHA256:8FEB53FE830B2807C7B37DE0BCB09C7BAEAA5ABBA7E45202EE6F1CA1061918D2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
62
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |