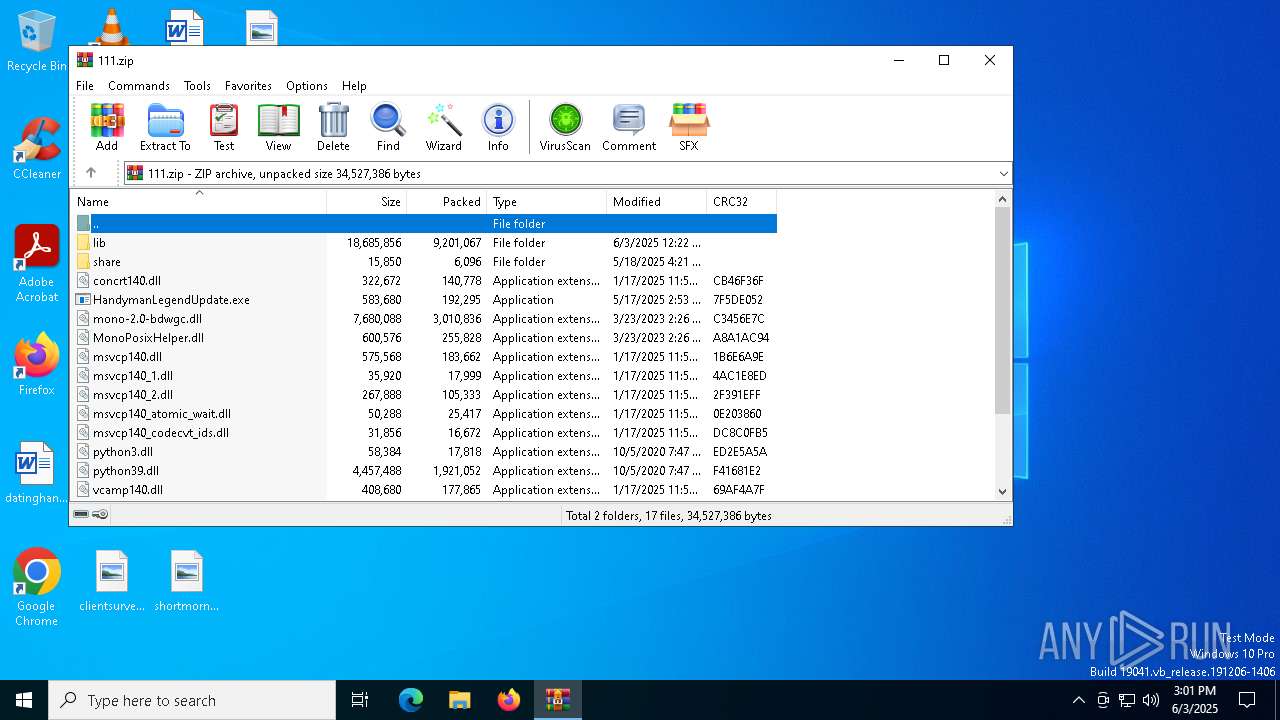
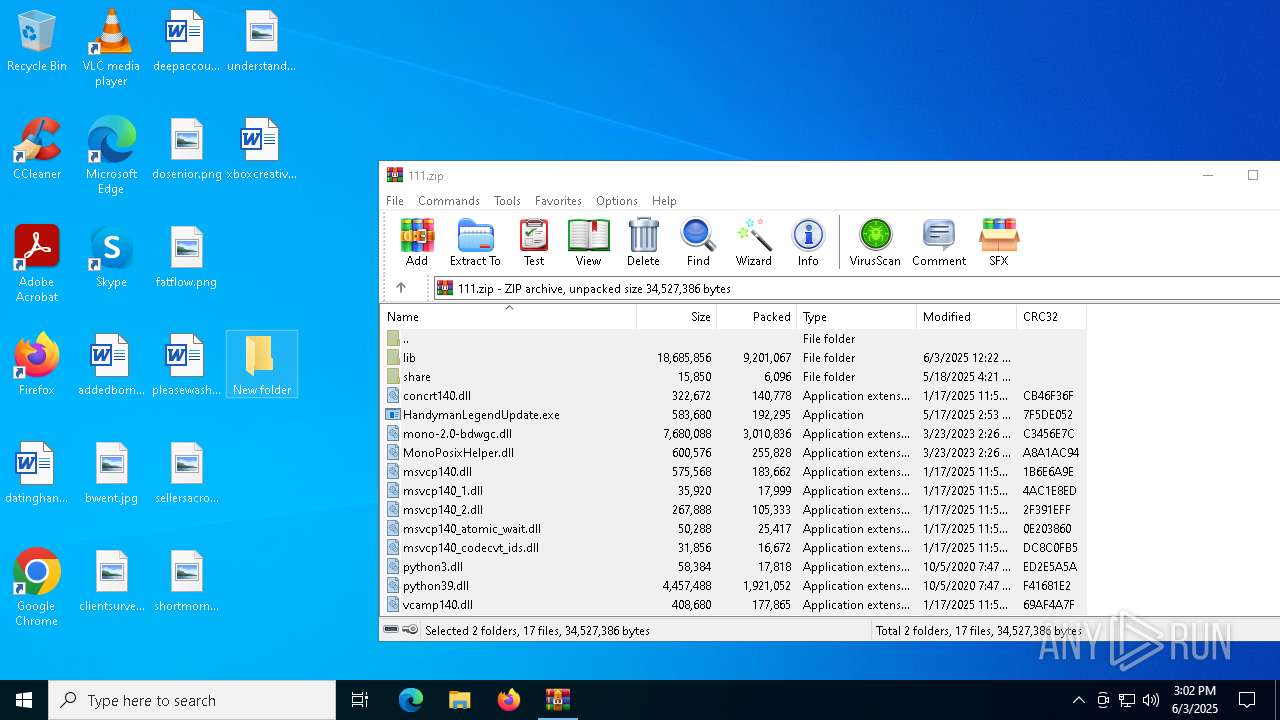
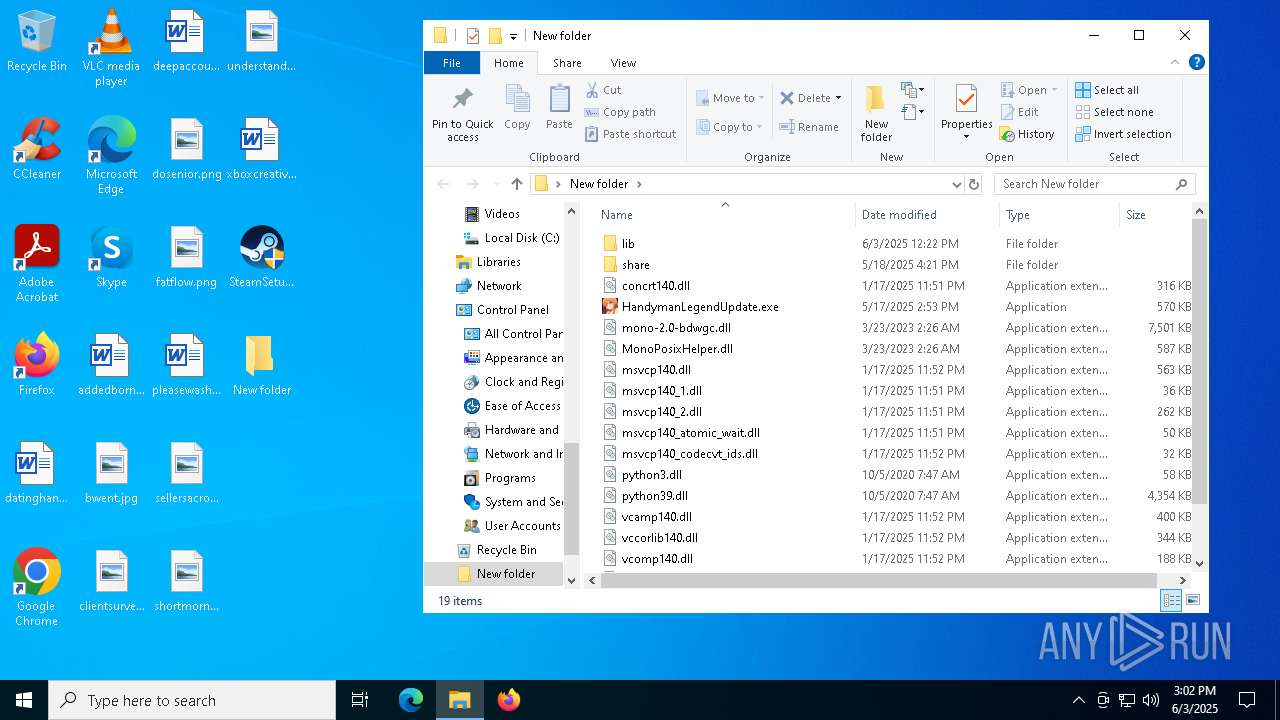
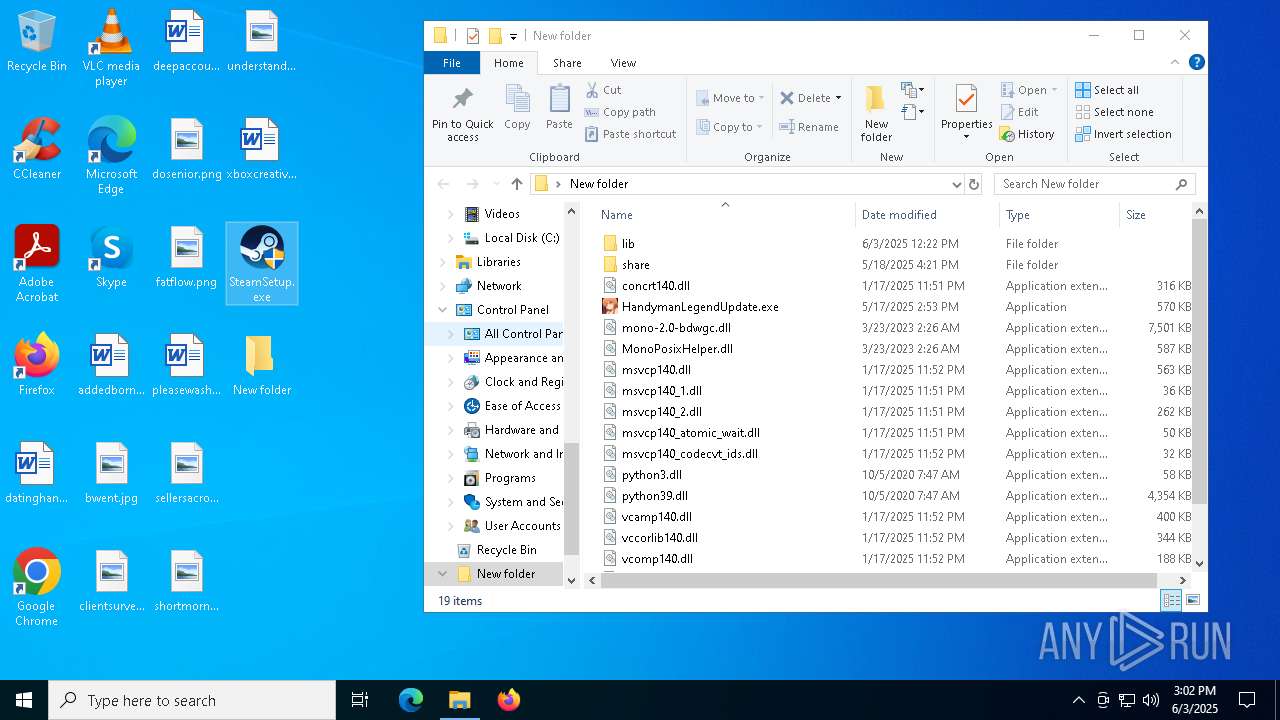
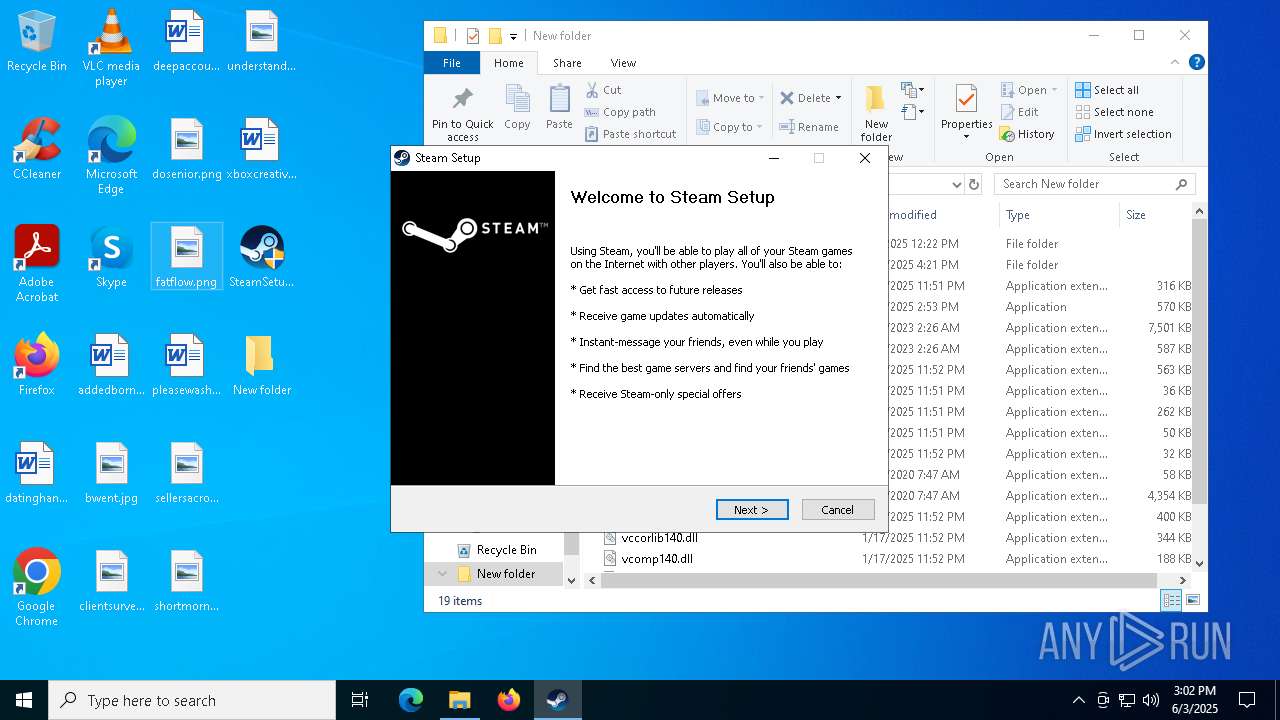
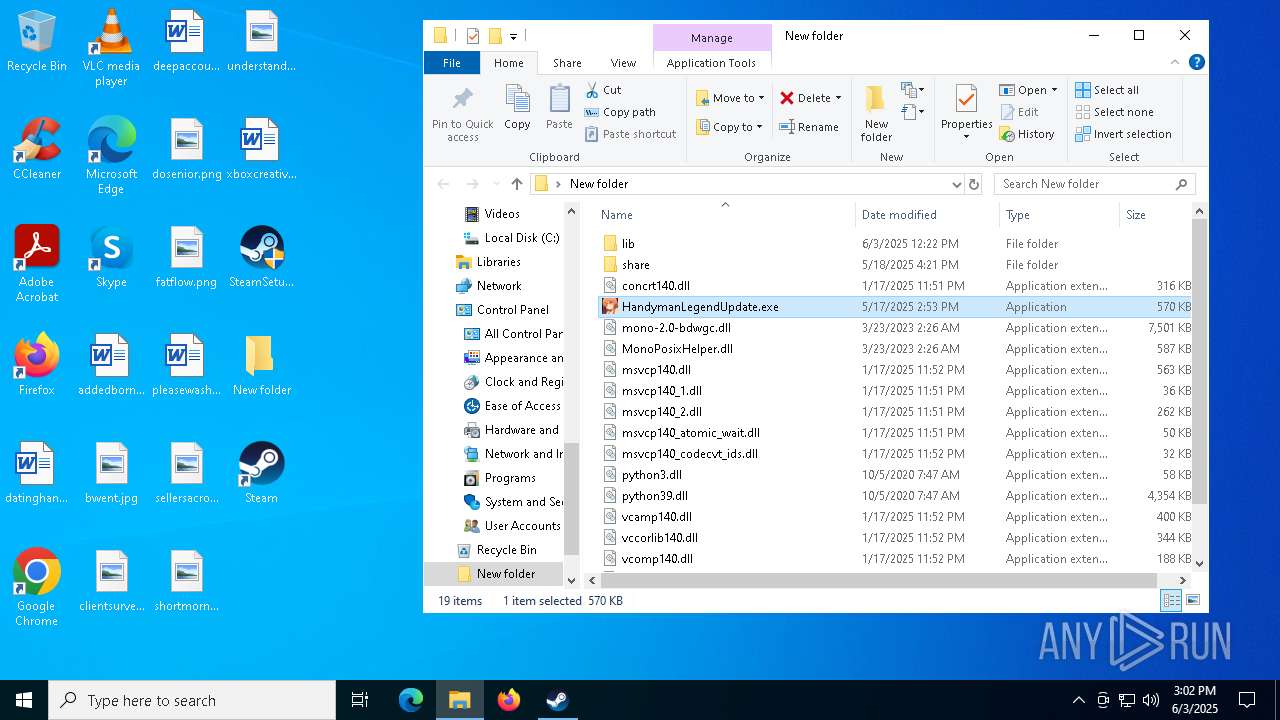
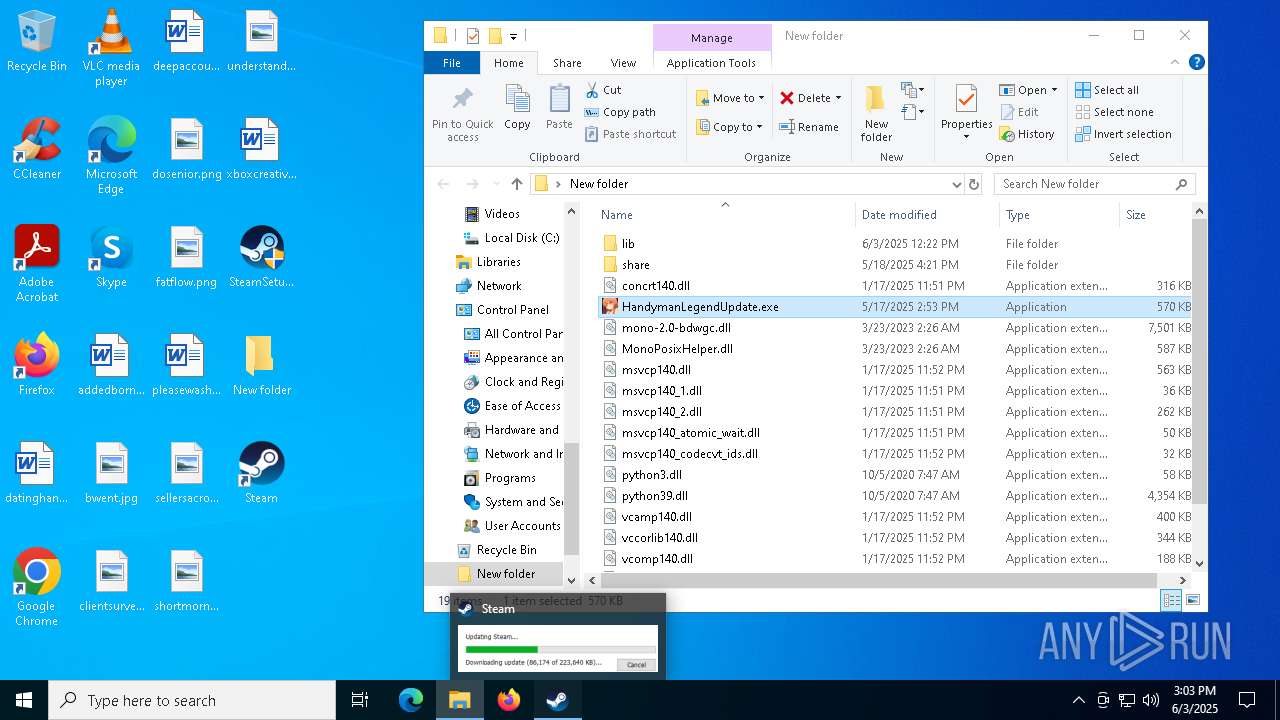
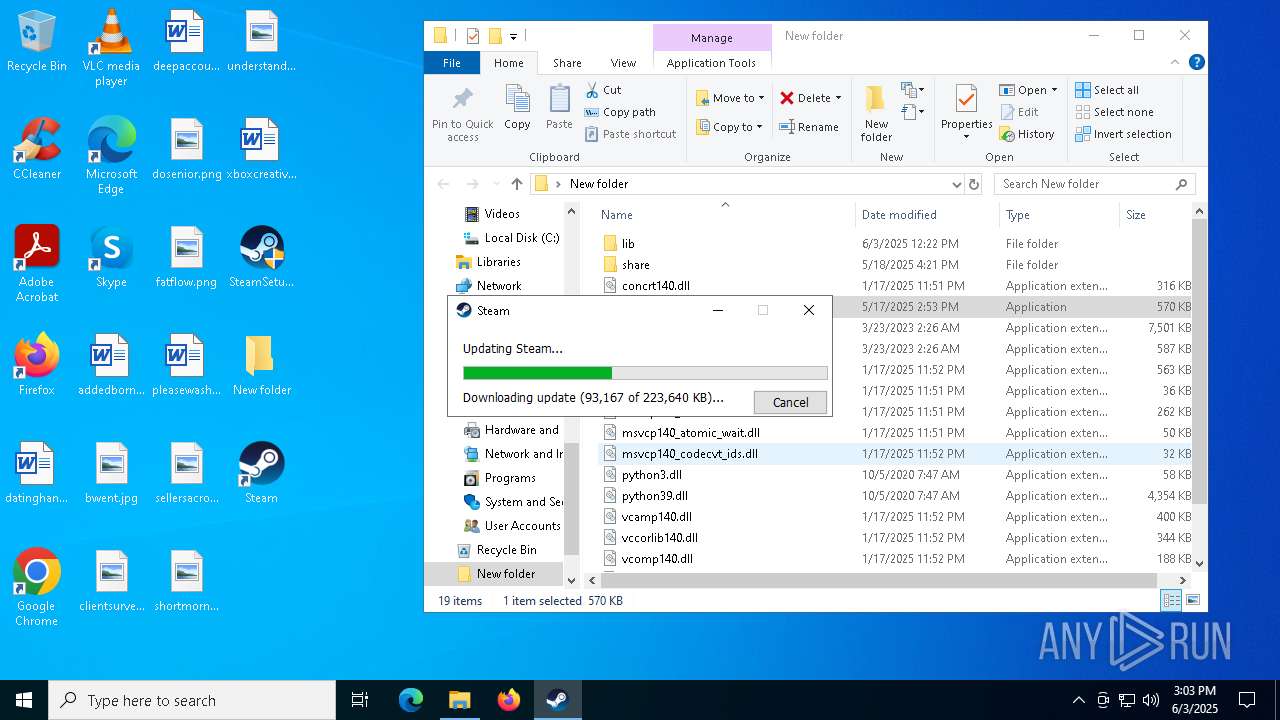
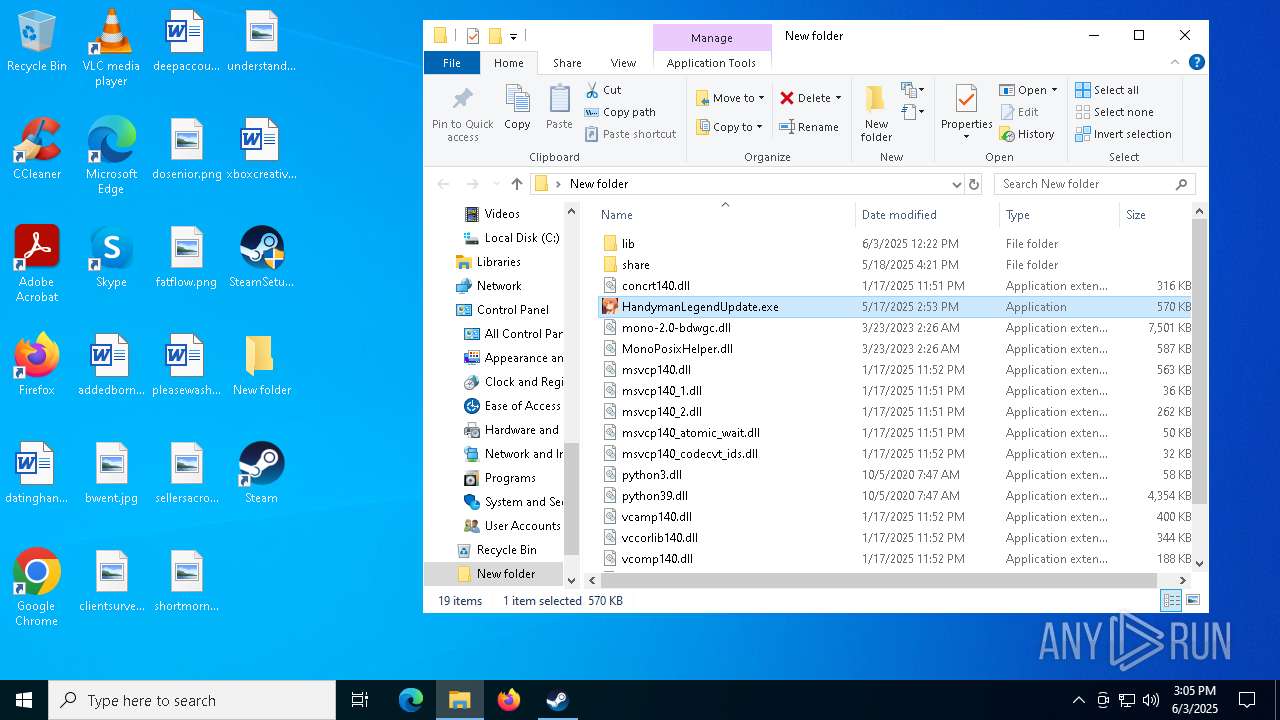
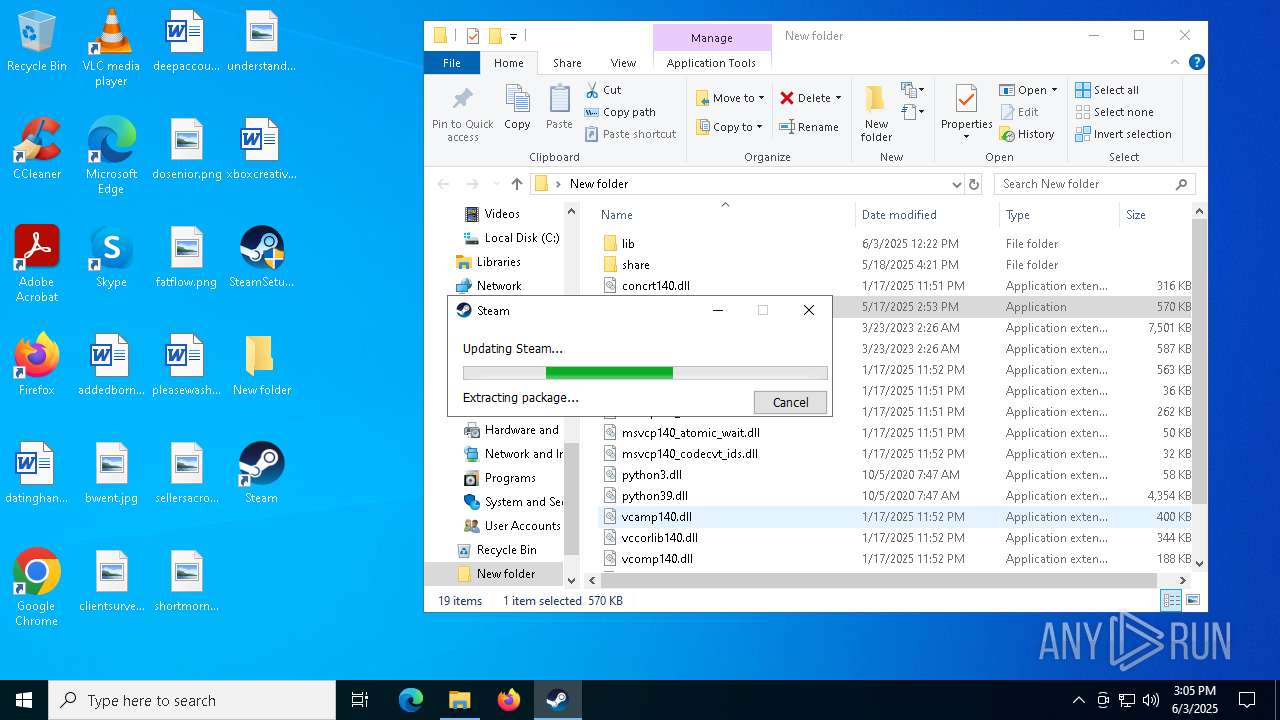
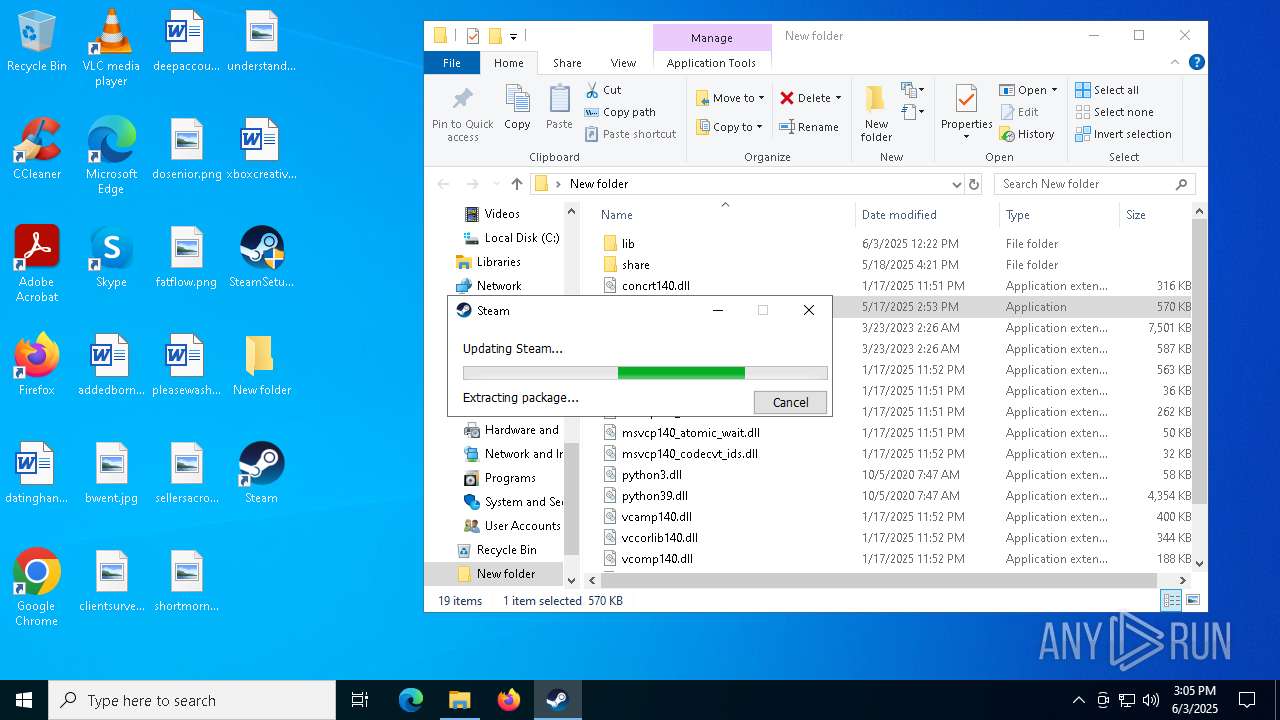
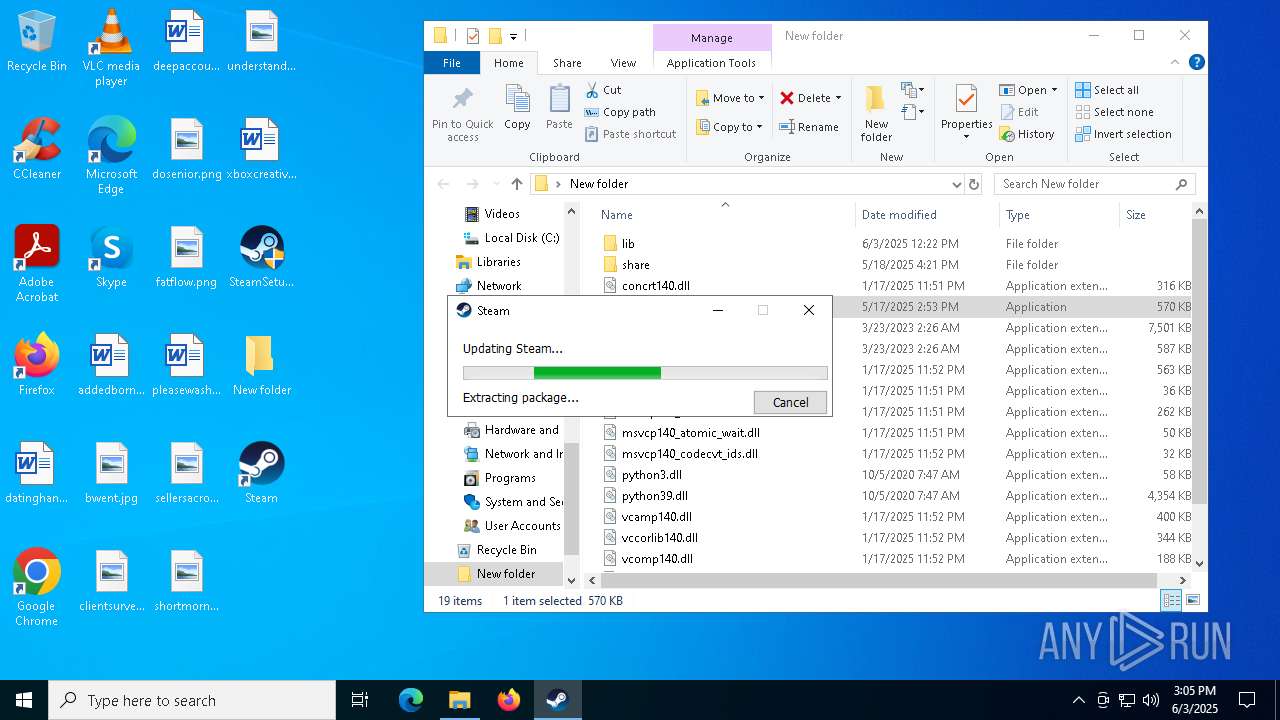
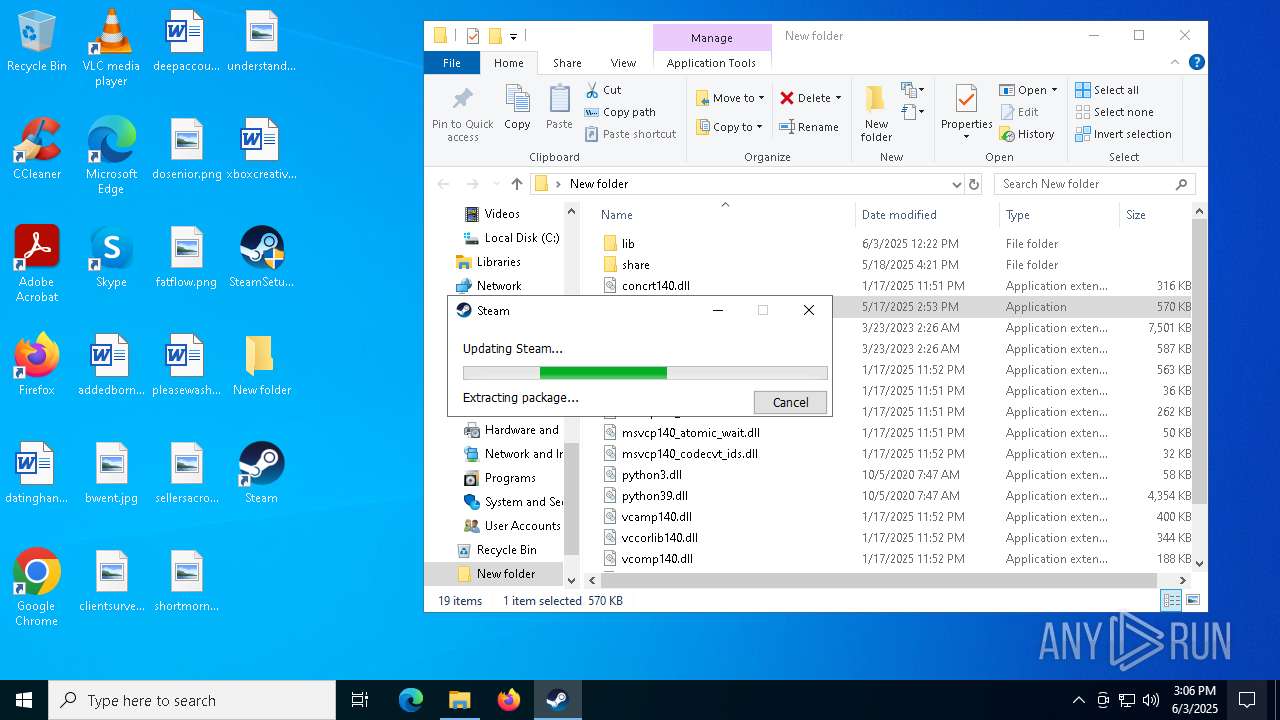
| File name: | 111.zip |
| Full analysis: | https://app.any.run/tasks/388ed1c1-ce57-4a11-9707-73635090e362 |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2025, 15:01:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 9AC45E4D9CBFB27C7519E09F5346E3B5 |
| SHA1: | C94E91265AC3376BE8D16D39F3A3B4577BADAA40 |
| SHA256: | 0B951AFD224376E159F41C9FAE1067273AC3D54714D736D5DFBEE4321D0A4E12 |
| SSDEEP: | 98304:RhTUKsdQSJwJ9eFTceBvl7AWWEC0oqUUR0W3YH/YK61O497+JYpvAPc53ge/hxvn:RKBBgWWVdxcO9j1lgbcWDzskS0 |
MALICIOUS
Changes the autorun value in the registry
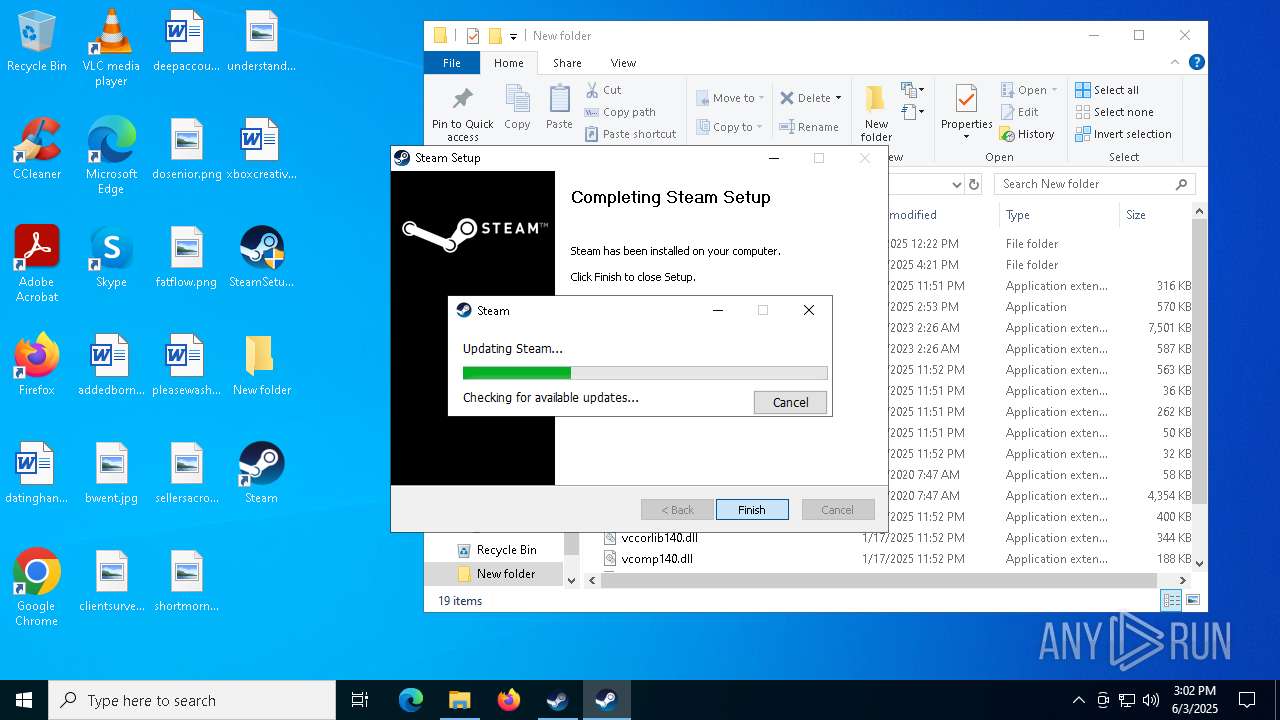
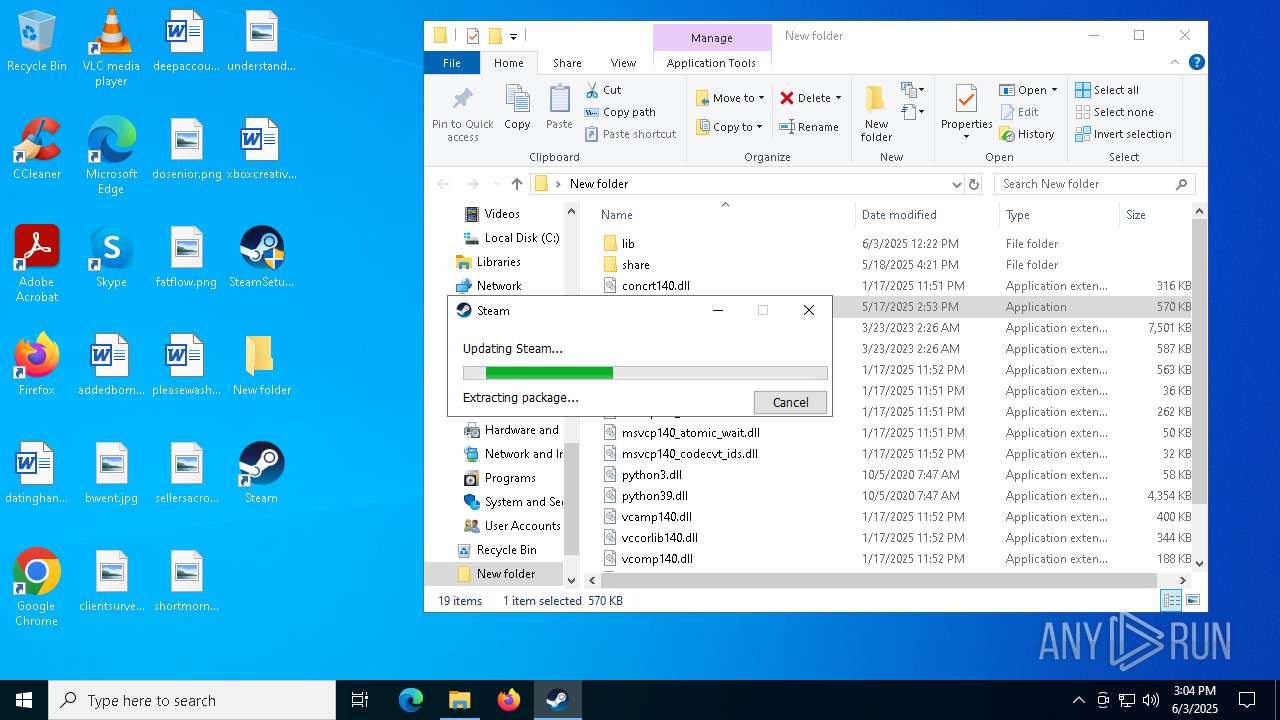
- SteamSetup.exe (PID: 4528)
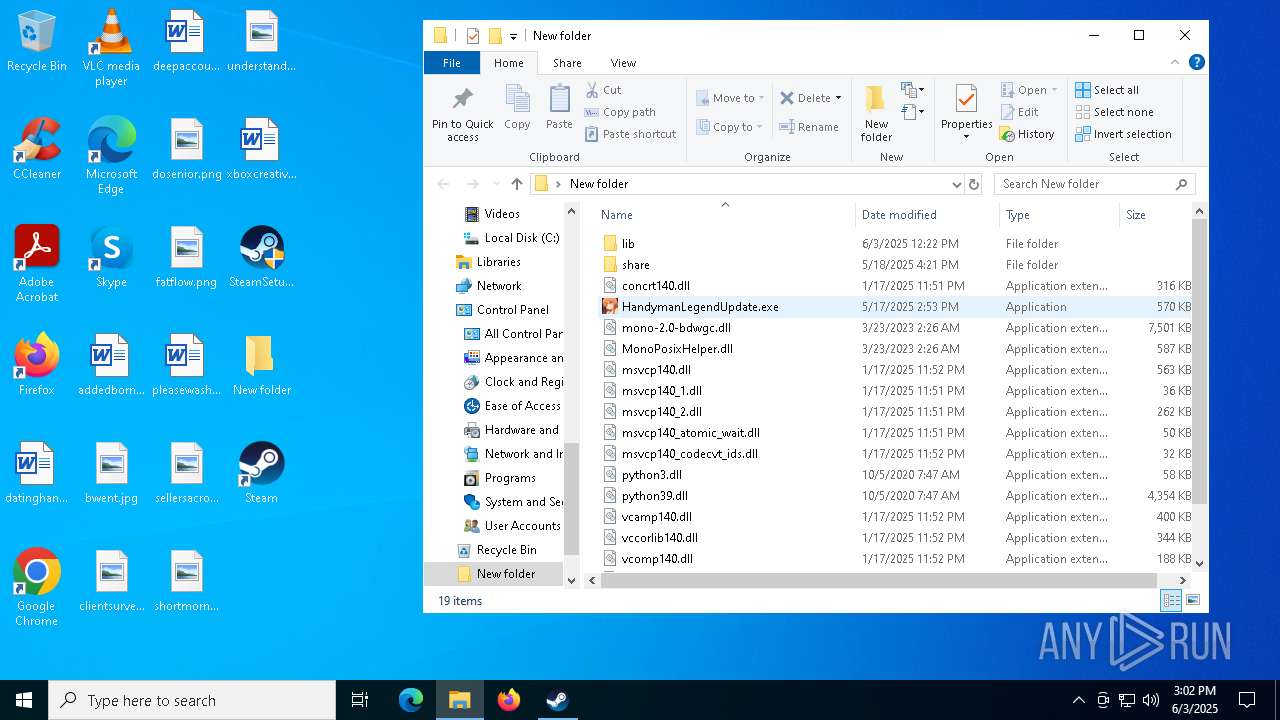
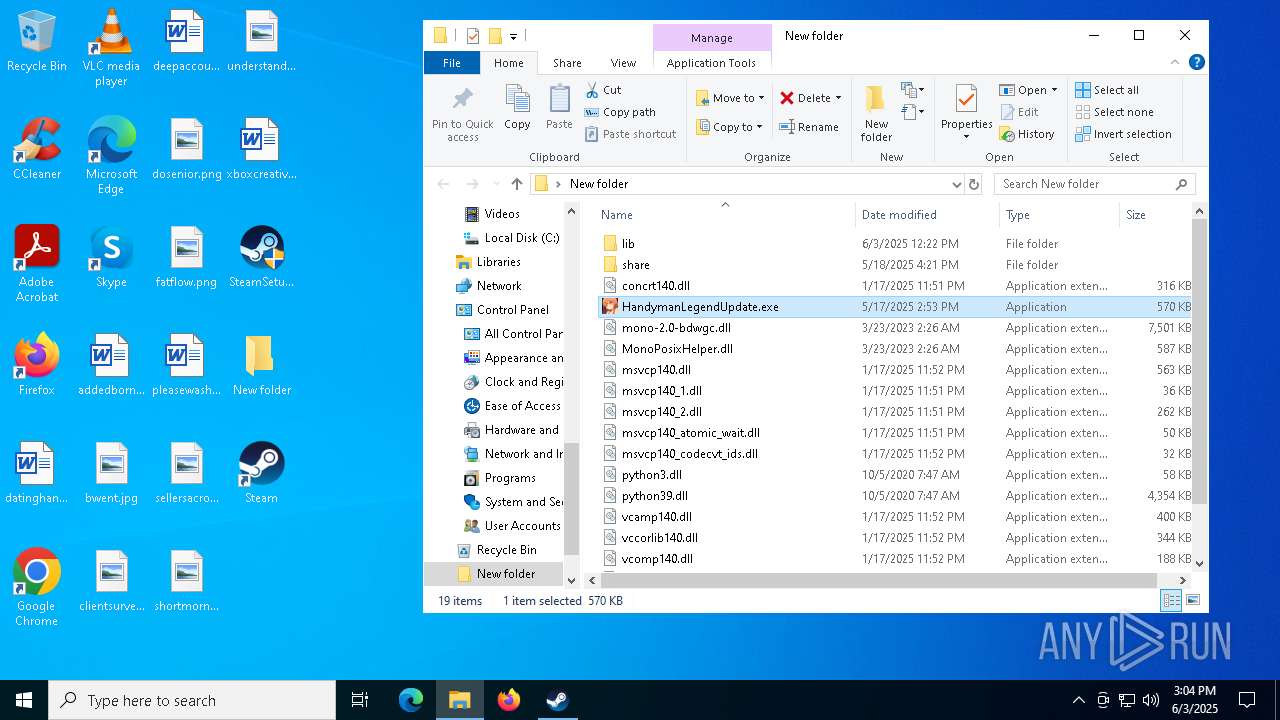
- HandymanLegendUpdate.exe (PID: 7268)
SUSPICIOUS
Process drops python dynamic module
- WinRAR.exe (PID: 3124)
Malware-specific behavior (creating "System.dll" in Temp)
- SteamSetup.exe (PID: 4528)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3124)
Executable content was dropped or overwritten
- SteamService.exe (PID: 7840)
- SteamSetup.exe (PID: 4528)
The process creates files with name similar to system file names
- SteamSetup.exe (PID: 4528)
There is functionality for taking screenshot (YARA)
- Steam.exe (PID: 2268)
- SteamSetup.exe (PID: 4528)
Creates a software uninstall entry
- SteamSetup.exe (PID: 4528)
Get information on the list of running processes
- cmd.exe (PID: 5596)
- cmd.exe (PID: 8140)
- cmd.exe (PID: 8004)
- cmd.exe (PID: 4468)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 7952)
- cmd.exe (PID: 4272)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 5212)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 8020)
- cmd.exe (PID: 7796)
- cmd.exe (PID: 1184)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 7736)
- cmd.exe (PID: 132)
- cmd.exe (PID: 8160)
- cmd.exe (PID: 7896)
- HandymanLegendUpdate.exe (PID: 7268)
- cmd.exe (PID: 7464)
- HandymanLegendUpdate.exe (PID: 7512)
- cmd.exe (PID: 5116)
- cmd.exe (PID: 1284)
- cmd.exe (PID: 472)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 5180)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 3012)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 7260)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 7460)
- cmd.exe (PID: 5416)
- cmd.exe (PID: 7692)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 4648)
- cmd.exe (PID: 1204)
- cmd.exe (PID: 3384)
- cmd.exe (PID: 3968)
- cmd.exe (PID: 7352)
- cmd.exe (PID: 7184)
- cmd.exe (PID: 7924)
- cmd.exe (PID: 800)
- cmd.exe (PID: 5056)
- cmd.exe (PID: 2740)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 7708)
- cmd.exe (PID: 7288)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 7132)
- cmd.exe (PID: 6560)
- cmd.exe (PID: 6792)
- cmd.exe (PID: 8160)
- cmd.exe (PID: 5552)
- cmd.exe (PID: 7480)
- cmd.exe (PID: 4284)
- cmd.exe (PID: 5364)
- cmd.exe (PID: 540)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 5980)
- cmd.exe (PID: 2192)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7952)
- cmd.exe (PID: 4468)
- cmd.exe (PID: 8004)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 8140)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 5212)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 8020)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 4272)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 1184)
- cmd.exe (PID: 7736)
- cmd.exe (PID: 7796)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 132)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 8160)
- cmd.exe (PID: 7464)
- cmd.exe (PID: 1284)
- cmd.exe (PID: 5180)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 3012)
- cmd.exe (PID: 472)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 7260)
- cmd.exe (PID: 3384)
- cmd.exe (PID: 7460)
- cmd.exe (PID: 7692)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 4648)
- cmd.exe (PID: 1204)
- cmd.exe (PID: 5416)
- cmd.exe (PID: 2740)
- cmd.exe (PID: 7352)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 7184)
- cmd.exe (PID: 7924)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 5056)
- cmd.exe (PID: 3968)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 7708)
- cmd.exe (PID: 7288)
- cmd.exe (PID: 7132)
- cmd.exe (PID: 800)
- cmd.exe (PID: 6792)
- cmd.exe (PID: 8160)
- cmd.exe (PID: 6560)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 2192)
- cmd.exe (PID: 7480)
- cmd.exe (PID: 4284)
- cmd.exe (PID: 5552)
- cmd.exe (PID: 5364)
- cmd.exe (PID: 540)
- cmd.exe (PID: 5980)
Loads Python modules
- HandymanLegendUpdate.exe (PID: 7268)
Starts CMD.EXE for commands execution
- HandymanLegendUpdate.exe (PID: 7268)
- HandymanLegendUpdate.exe (PID: 7512)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 3124)
- SteamSetup.exe (PID: 4528)
- SteamService.exe (PID: 7840)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3124)
Manual execution by a user
- SteamSetup.exe (PID: 4188)
- SteamSetup.exe (PID: 4528)
- HandymanLegendUpdate.exe (PID: 7268)
- Steam.exe (PID: 2268)
- HandymanLegendUpdate.exe (PID: 7512)
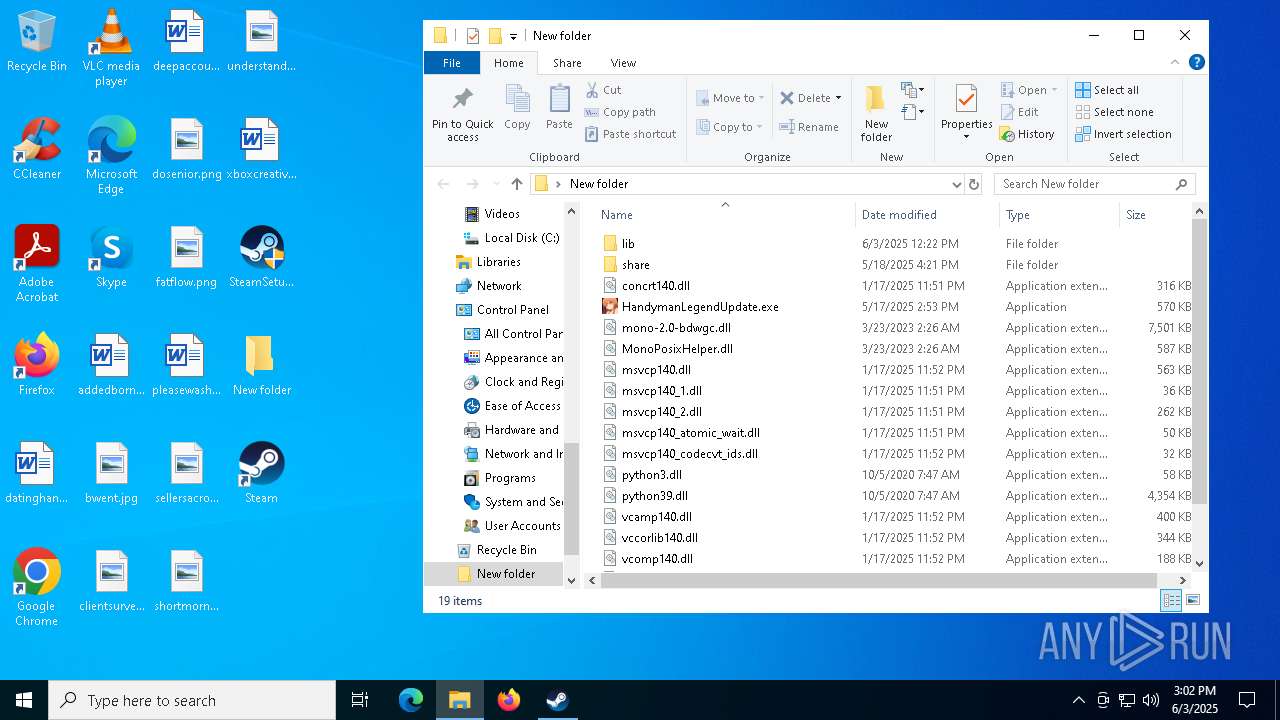
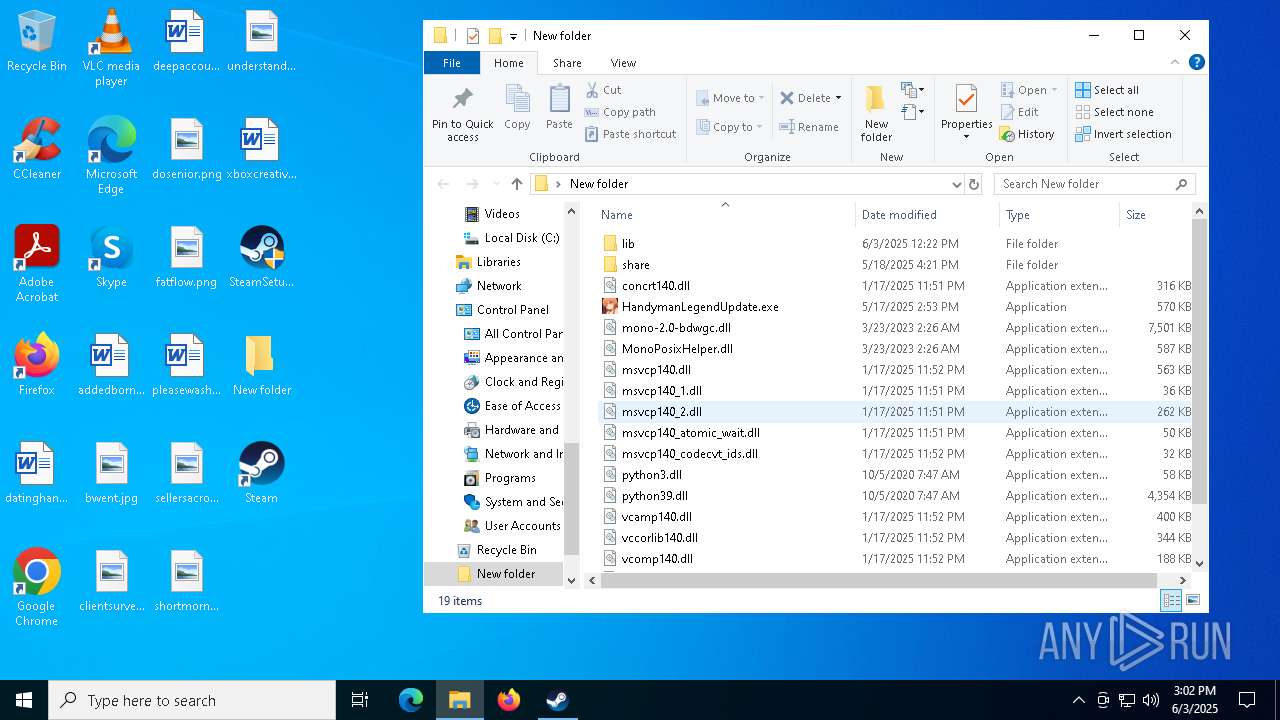
Creates files in the program directory
- SteamSetup.exe (PID: 4528)
- SteamService.exe (PID: 7840)
- Steam.exe (PID: 2268)
Checks supported languages
- SteamSetup.exe (PID: 4528)
- SteamService.exe (PID: 7840)
- HandymanLegendUpdate.exe (PID: 7268)
- Steam.exe (PID: 2268)
Launching a file from a Registry key
- SteamSetup.exe (PID: 4528)
- HandymanLegendUpdate.exe (PID: 7268)
Create files in a temporary directory
- SteamSetup.exe (PID: 4528)
- HandymanLegendUpdate.exe (PID: 7268)
Reads the computer name
- SteamSetup.exe (PID: 4528)
- SteamService.exe (PID: 7840)
- Steam.exe (PID: 2268)
Reads the software policy settings
- Steam.exe (PID: 2268)
- slui.exe (PID: 1328)
Checks proxy server information
- Steam.exe (PID: 2268)
- slui.exe (PID: 1328)
Reads CPU info
- Steam.exe (PID: 2268)
The sample compiled with bulgarian language support
- SteamSetup.exe (PID: 4528)
Reads the machine GUID from the registry
- Steam.exe (PID: 2268)
- HandymanLegendUpdate.exe (PID: 7268)
Creates files or folders in the user directory
- Steam.exe (PID: 2268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:18 07:51:56 |
| ZipCRC: | 0xcb46f36f |
| ZipCompressedSize: | 140778 |
| ZipUncompressedSize: | 322672 |
| ZipFileName: | concrt140.dll |
Total processes
398
Monitored processes
272
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\WINDOWS\system32\cmd.exe /c "tasklist | findstr steam.exe" | C:\Windows\System32\cmd.exe | — | HandymanLegendUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | findstr steam.exe | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | C:\WINDOWS\system32\cmd.exe /c "tasklist | findstr steam.exe" | C:\Windows\System32\cmd.exe | — | HandymanLegendUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | C:\WINDOWS\system32\cmd.exe /c "tasklist | findstr steam.exe" | C:\Windows\System32\cmd.exe | — | HandymanLegendUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 656 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 656 | findstr steam.exe | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | findstr steam.exe | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 361
Read events
14 312
Write events
47
Delete events
2
Modification events
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\111.zip | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEB000000AF000000AA04000098020000 | |||
| (PID) Process: | (3124) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
58
Suspicious files
178
Text files
2 314
Unknown types
656
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
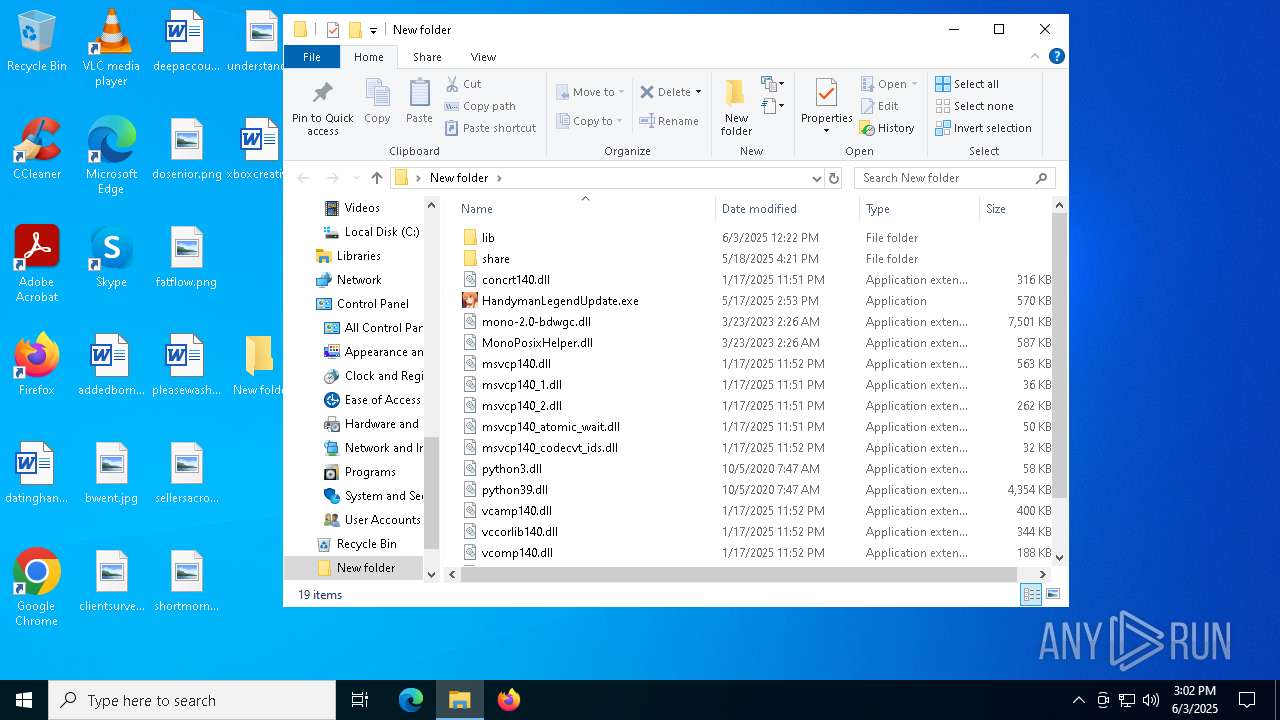
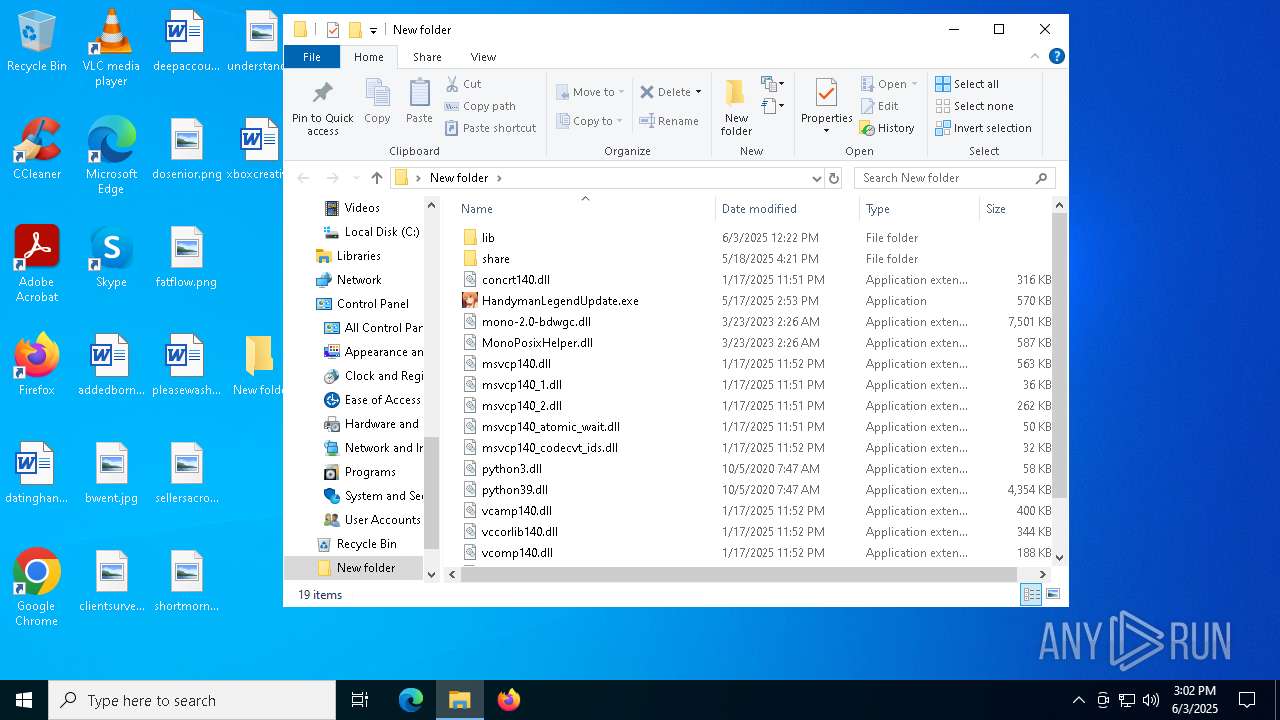
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\HandymanLegendUpdate.exe | executable | |
MD5:1070D2E819594A3086836B67425EA26D | SHA256:E9425DA8949F80FF1828CEC2E4BD7190FA8BEDA034E67AC0CCC5DDBDFF31BDC7 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\concrt140.dll | executable | |
MD5:D8E2CDEC28B919B43A8CF8B9A3653737 | SHA256:7ABAA6C6227B71514E6BFD347DC2D06F16E6E5FAA840F03D46A04EA4F84A9943 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\lib\libcrypto-1_1.dll | executable | |
MD5:CC4CBF715966CDCAD95A1E6C95592B3D | SHA256:594303E2CE6A4A02439054C84592791BF4AB0B7C12E9BBDB4B040E27251521F1 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\lib\libffi-7.dll | executable | |
MD5:EEF7981412BE8EA459064D3090F4B3AA | SHA256:F60DD9F2FCBD495674DFC1555EFFB710EB081FC7D4CAE5FA58C438AB50405081 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\lib\mfc140u.dll | executable | |
MD5:84B82C149B450D3C8E0D06F09A416B5D | SHA256:1EC2A31A1302E720C799BAD2FD90CF3457C6B2A375C4B41FAEFEE1A91D92F3E0 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\lib\charset_normalizer.md__mypyc.cp39-win_amd64.pyd | executable | |
MD5:450C214E625A6C9B43561397BF9DD807 | SHA256:F26CD4385CB1233DB1F358B9893037EB65C08EDF250845F12493A1B9F1308AD9 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\lib\pywintypes39.dll | executable | |
MD5:D60C74EF808BD1DDCC5D5CFD32A9AA38 | SHA256:0C0832EA78678728667F0E84583378AA01A10C21AEF5E6E4A9E903F798D09FB0 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\lib\win32api.pyd | executable | |
MD5:7C48930F322772DBDF64BA70B865E094 | SHA256:5A7D45508D5099D8F62D27693B441C521771B2A383E84499AB1E4587A9510F72 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\lib\win32trace.pyd | executable | |
MD5:1CB833F677CF3326EBC588809051B17C | SHA256:20D057CF15DB033F2E7F3FCDC0BF69DCEFF14E67872122DACDE96AA9C1EA4DF8 | |||
| 3124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3124.24371\lib\unicodedata.pyd | executable | |
MD5:8320C54418D77EBA5D4553A5D6EC27F9 | SHA256:7E719BA47919B668ACC62008079C586133966ED8B39FEC18E312A773CB89EDAE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
27
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
472 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
472 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6920 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2268 | Steam.exe | GET | 200 | 23.56.253.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6920 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2268 | Steam.exe | GET | 200 | 2.16.168.117:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgVw5xnQmeqtCTivokpVYwIezw%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
472 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
8044 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
472 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
6544 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
cdn.steamstatic.com |
| whitelisted |