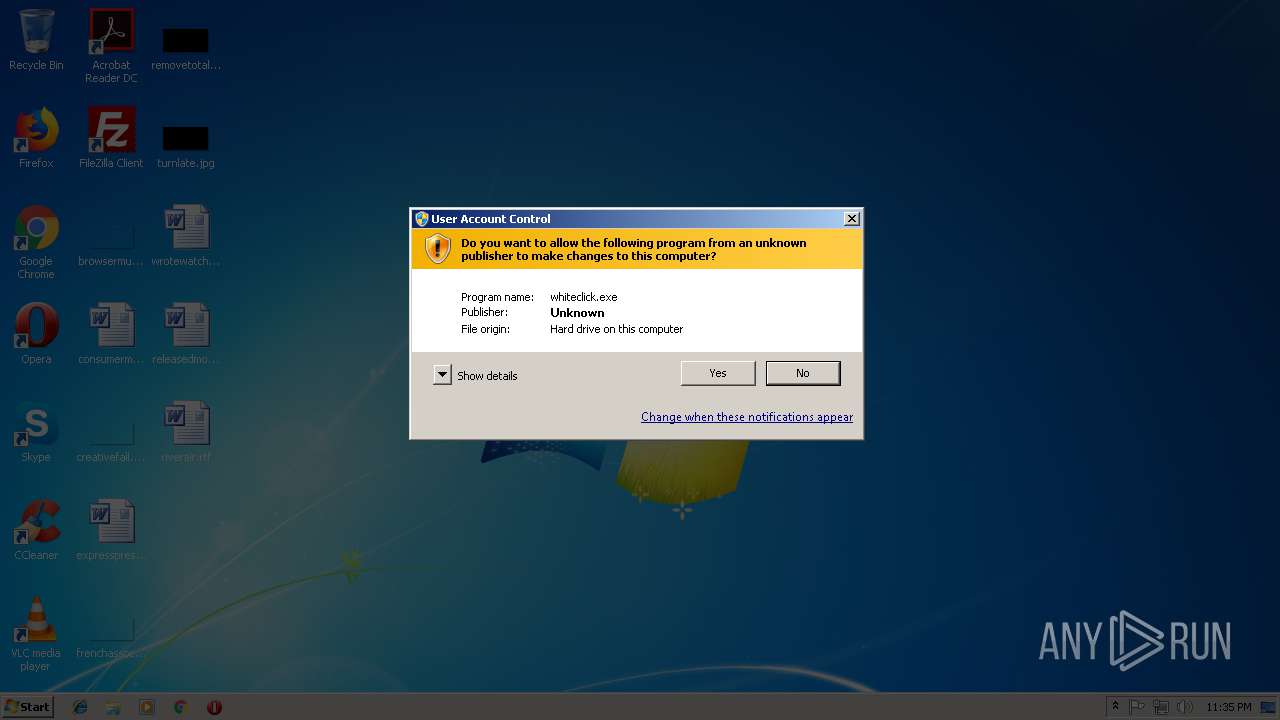
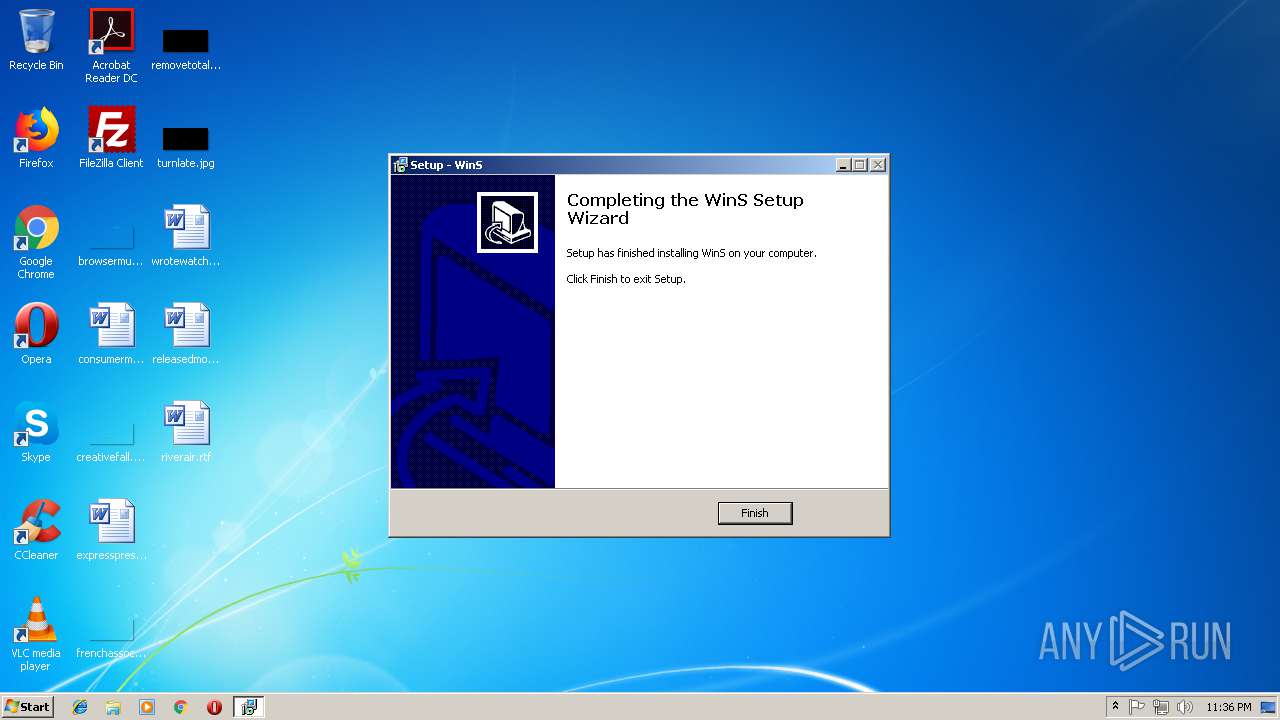
| File name: | whiteclick.exe |
| Full analysis: | https://app.any.run/tasks/b4fc1d5d-99e9-47a3-ac57-8bff6a372ac3 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 23:35:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 025429D2D3DEA92F37D222CCE9C20C95 |
| SHA1: | 0941B424740A8C0B0B63D3133B13AB27230A42F9 |
| SHA256: | 0B91CE44B2F19A899DBB4D3DC0A018ED3EA16BAC4AB859B7F34307E925EF3381 |
| SSDEEP: | 24576:z7blE63vLMrZ0lg+I5nKLFzg9WkeooQzkfRD67aRq8Imj4Y3:z75R0igxn+FzggZAkk+sm8Y3 |
MALICIOUS
Writes to a start menu file
- msiexec.exe (PID: 2296)
SUSPICIOUS
Executable content was dropped or overwritten
- msiexec.exe (PID: 2296)
- whiteclick.exe (PID: 4068)
- whiteclick.exe (PID: 1180)
- whiteclick.tmp (PID: 476)
Creates files in the Windows directory
- msiexec.exe (PID: 2296)
Creates COM task schedule object
- MsiExec.exe (PID: 2744)
Starts Microsoft Installer
- whiteclick.tmp (PID: 476)
Creates files in the user directory
- msiexec.exe (PID: 2296)
INFO
Application was dropped or rewritten from another process
- whiteclick.tmp (PID: 3456)
- whiteclick.tmp (PID: 476)
Creates a software uninstall entry
- msiexec.exe (PID: 2296)
Application launched itself
- msiexec.exe (PID: 2296)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2744)
- msiexec.exe (PID: 2296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41472 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa98 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
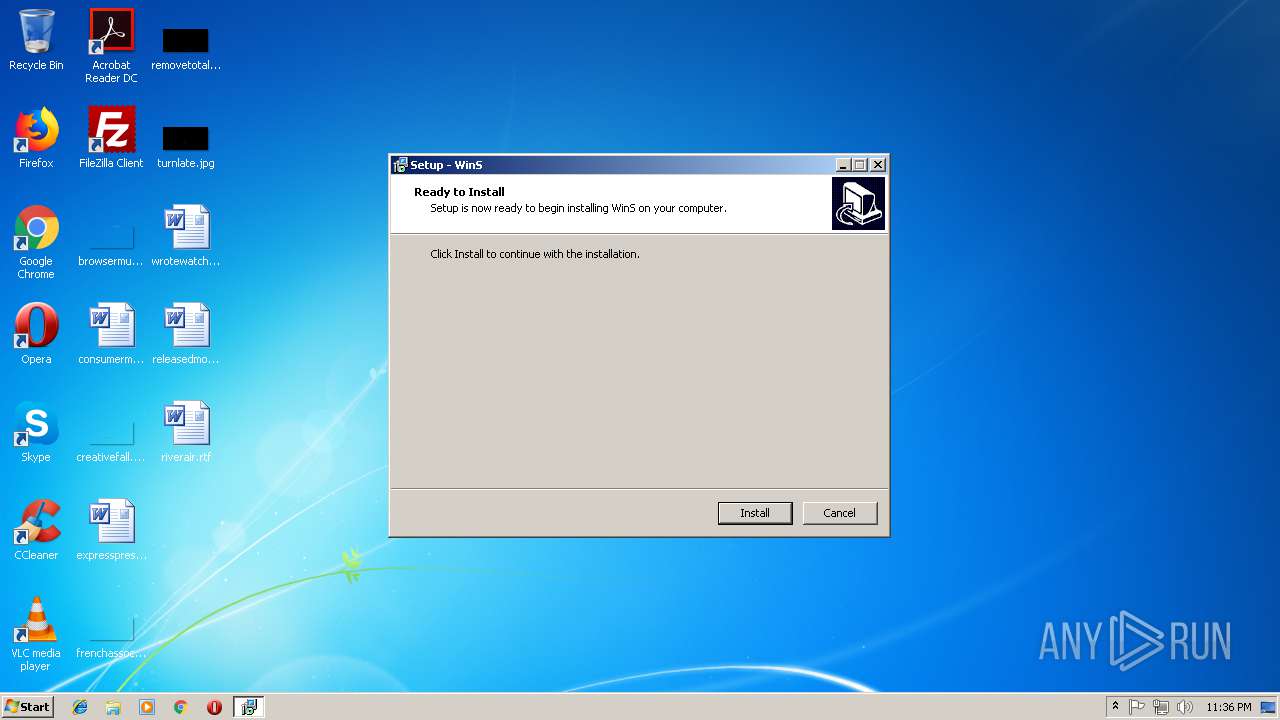
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | WinS |
| FileDescription: | WinS Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | WinS |
| ProductVersion: | 8 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | WinS |
| FileDescription: | WinS Setup |
| FileVersion: | - |
| LegalCopyright: | - |
| ProductName: | WinS |
| ProductVersion: | 8 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x0000A1D0 | 0x0000A200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.64375 |
DATA | 0x0000C000 | 0x00000250 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.74012 |
BSS | 0x0000D000 | 0x00000E94 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0000E000 | 0x0000097C | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.48608 |
.tls | 0x0000F000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00010000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.190489 |
.reloc | 0x00011000 | 0x0000091C | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0 |
.rsrc | 0x00012000 | 0x00002C00 | 0x00002C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 4.57438 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.13965 | 1580 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.47151 | 1384 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 3.91708 | 744 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.91366 | 2216 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4089 | 3.21823 | 754 | UNKNOWN | UNKNOWN | RT_STRING |
4090 | 3.31515 | 780 | UNKNOWN | UNKNOWN | RT_STRING |
4091 | 3.25024 | 718 | UNKNOWN | UNKNOWN | RT_STRING |
4093 | 2.86149 | 104 | UNKNOWN | UNKNOWN | RT_STRING |
4094 | 3.20731 | 180 | UNKNOWN | UNKNOWN | RT_STRING |
4095 | 3.04592 | 174 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
42
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 476 | "C:\Users\admin\AppData\Local\Temp\is-KC981.tmp\whiteclick.tmp" /SL5="$C0594,888319,57856,C:\Users\admin\AppData\Local\Temp\whiteclick.exe" /SPAWNWND=$3F01FA /NOTIFYWND=$2401F8 | C:\Users\admin\AppData\Local\Temp\is-KC981.tmp\whiteclick.tmp | whiteclick.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\AppData\Local\Temp\whiteclick.exe" | C:\Users\admin\AppData\Local\Temp\whiteclick.exe | explorer.exe | ||||||||||||
User: admin Company: WinS Integrity Level: MEDIUM Description: WinS Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1644 | "msiexec.exe" /i"C:\Users\admin\AppData\Local\Temp\is-VFLQS.tmp\Setup.msi" /quiet | C:\Windows\system32\msiexec.exe | — | whiteclick.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2296 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | C:\Windows\system32\MsiExec.exe -Embedding DD518659B6B23317FCAA1825279FA75E | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3456 | "C:\Users\admin\AppData\Local\Temp\is-4HMFL.tmp\whiteclick.tmp" /SL5="$2401F8,888319,57856,C:\Users\admin\AppData\Local\Temp\whiteclick.exe" | C:\Users\admin\AppData\Local\Temp\is-4HMFL.tmp\whiteclick.tmp | — | whiteclick.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 4068 | "C:\Users\admin\AppData\Local\Temp\whiteclick.exe" /SPAWNWND=$3F01FA /NOTIFYWND=$2401F8 | C:\Users\admin\AppData\Local\Temp\whiteclick.exe | whiteclick.tmp | ||||||||||||
User: admin Company: WinS Integrity Level: HIGH Description: WinS Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
768
Read events
522
Write events
230
Delete events
16
Modification events
| (PID) Process: | (476) whiteclick.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: DC0100004984CDD1BB77D401 | |||
| (PID) Process: | (476) whiteclick.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: F63EB6B1266E6E115C8072B977C4B244A7D6DB6B0D9FDB1BBCA53475FB9A06DB | |||
| (PID) Process: | (476) whiteclick.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2296) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Owner |
Value: F80800008F5518D9BB77D401 | |||
| (PID) Process: | (2296) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | SessionHash |
Value: 696BFA355AF7C3D9A7DD5420AB247D26BB210D963321C660E4CFAA7C929EE53F | |||
| (PID) Process: | (2296) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2296) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\InProgress |
| Operation: | write | Name: | |
Value: C:\Windows\Installer\5e36b8.ipi | |||
| (PID) Process: | (2296) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\5e36b9.rbs |
Value: 30701499 | |||
| (PID) Process: | (2296) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\5e36b9.rbsLow |
Value: 3655523296 | |||
| (PID) Process: | (2296) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1302019708-1500728564-335382590-1000\Components\C13D24E318832C39BDB9F371AD5EA4FF |
| Operation: | write | Name: | 13757FA0A557434469E6F11FB41170FD |
Value: C:\Users\admin\AppData\Local\WhiteClick\Images\otvet.mail.ru.png | |||
Executable files
13
Suspicious files
3
Text files
54
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 476 | whiteclick.tmp | C:\Users\admin\AppData\Local\Temp\is-VFLQS.tmp\is-CMGIG.tmp | — | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Windows\Installer\MSI37C0.tmp | — | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Windows\Installer\MSI38AB.tmp | — | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF0DF08CAED5737A74.TMP | — | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Windows\Installer\5e36b8.ipi | binary | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Users\admin\AppData\Local\WhiteClick\Images\news.mail.ru.png | image | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Windows\Installer\MSI3997.tmp | binary | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Users\admin\AppData\Local\WhiteClick\Images\warface.ru.png | image | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Users\admin\AppData\Local\WhiteClick\System Images\add_tab.png | image | |
MD5:— | SHA256:— | |||
| 2296 | msiexec.exe | C:\Windows\Installer\5e36b6.msi | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report