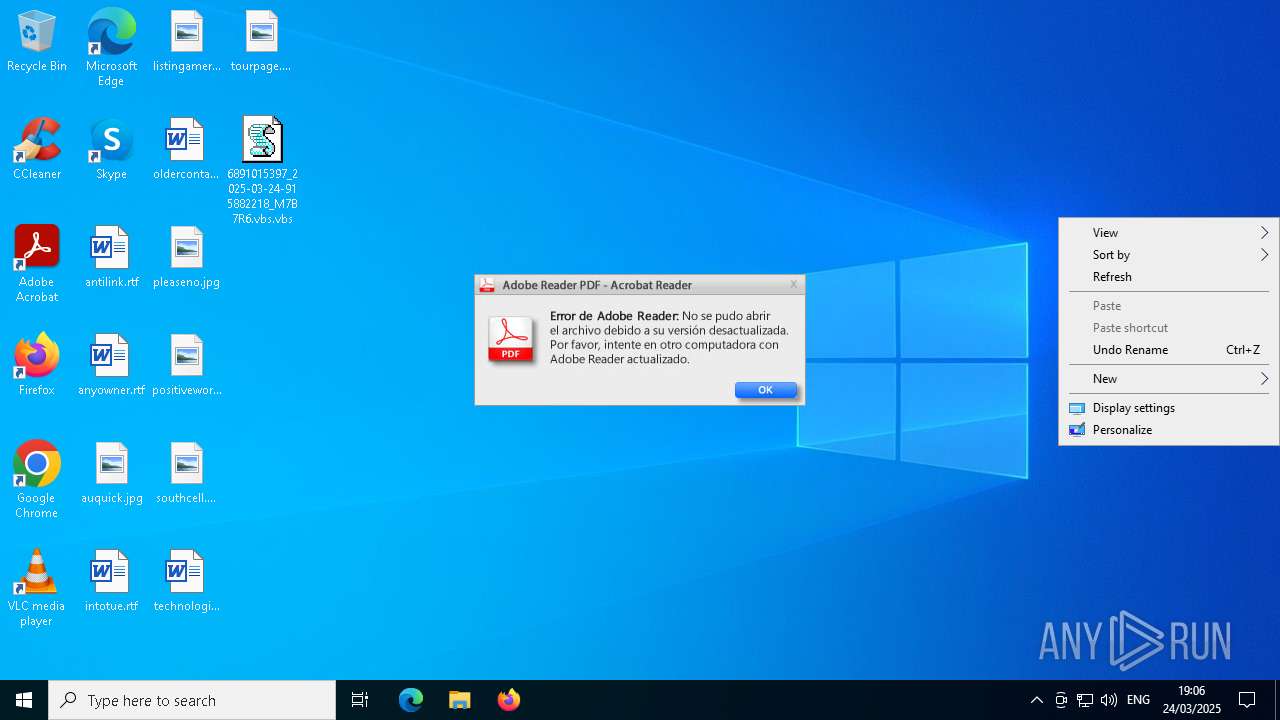
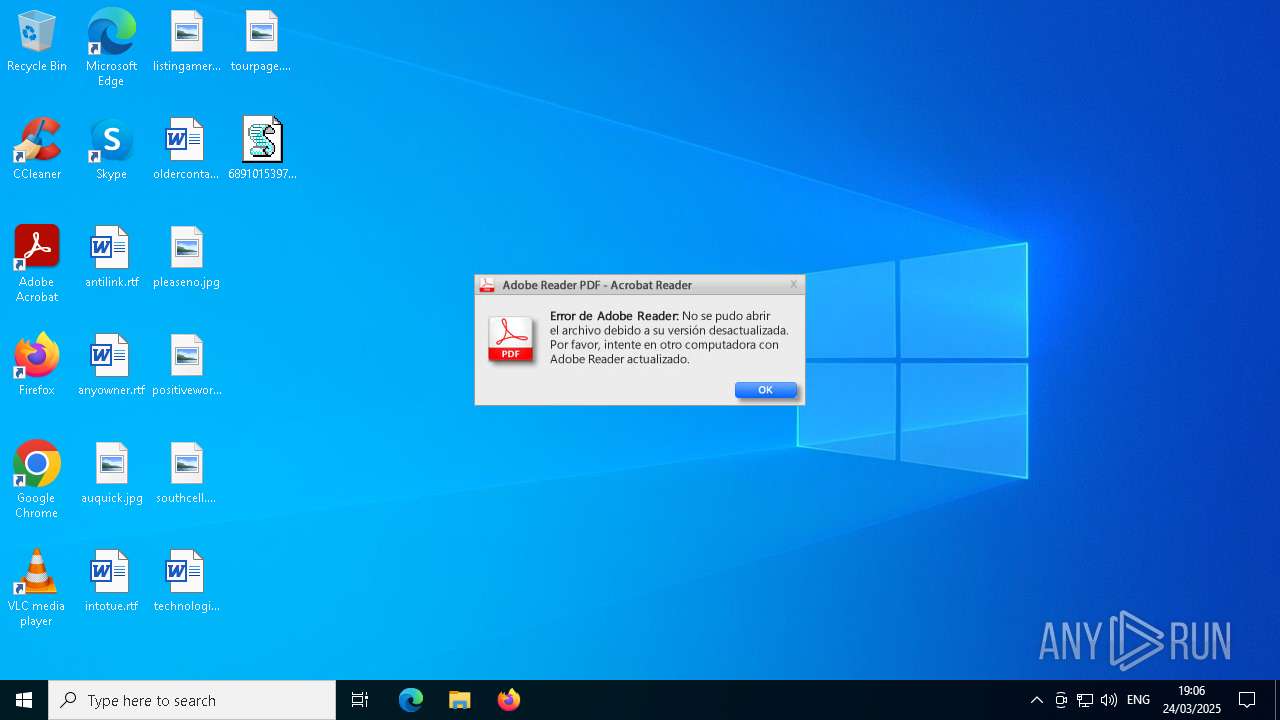
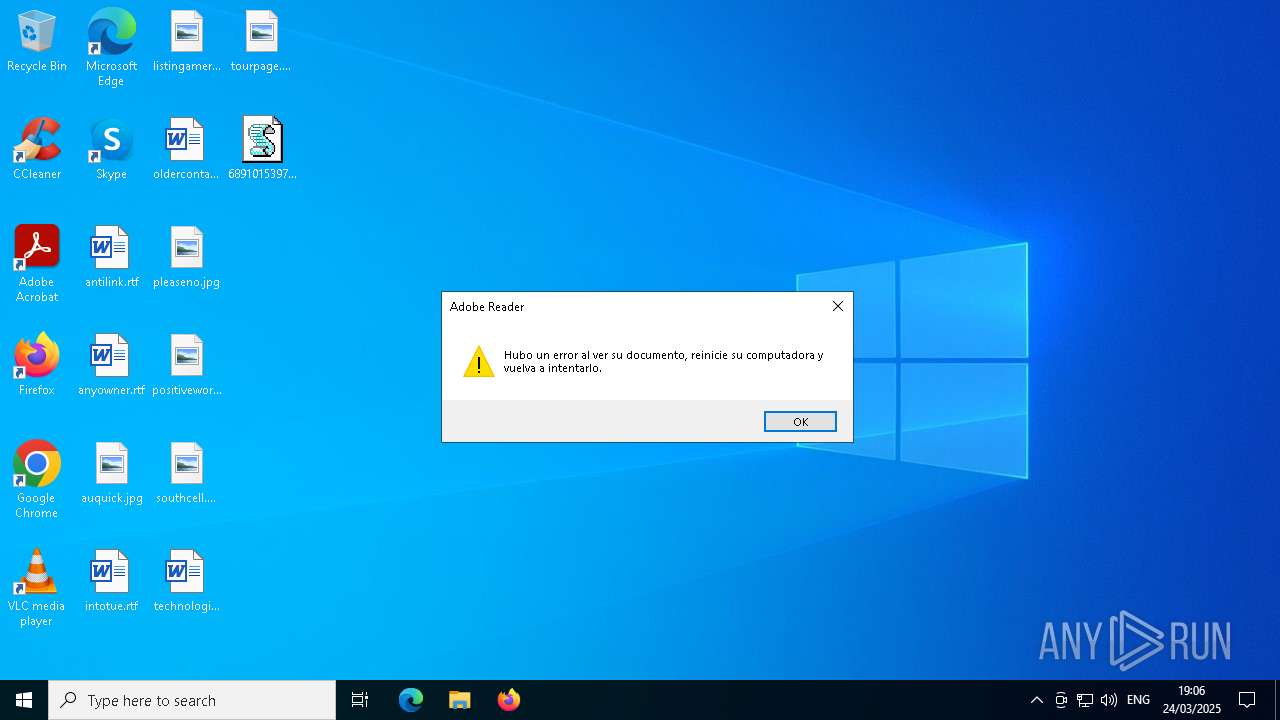
| File name: | 6891015397_2025-03-24-915882218_M7B7R6.vbs |
| Full analysis: | https://app.any.run/tasks/bf464297-ac84-4d84-9c3b-dcfa5bb35d6c |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 19:05:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (4836), with CRLF line terminators |
| MD5: | 2540FAE8C3B5756808015BC8015776CC |
| SHA1: | 9CAFA7A101AB42F54BE708F5FB87F22618B87188 |
| SHA256: | 0B85AF6D9A84E4253923F7F79B7FFEC7D3050A91830A3F826F1B7BDA13FB7327 |
| SSDEEP: | 49152:u3wZTGzFOUipAt4Kk+OfwqfkxooFmA6fXdOZfo6S:lAC9z |
MALICIOUS
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 1040)
Deletes a file (SCRIPT)
- wscript.exe (PID: 1040)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 1040)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 1040)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1040)
Likely accesses (executes) a file from the Public directory
- VKBtniFiAqVXinckNm.exe (PID: 5228)
Checks for external IP
- svchost.exe (PID: 2196)
- VKBtniFiAqVXinckNm.exe (PID: 5228)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 1040)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 1040)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 1040)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 6112)
INFO
Checks proxy server information
- BackgroundTransferHost.exe (PID: 4068)
- BackgroundTransferHost.exe (PID: 6108)
- slui.exe (PID: 6668)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5072)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 1240)
- BackgroundTransferHost.exe (PID: 5720)
- BackgroundTransferHost.exe (PID: 6132)
- BackgroundTransferHost.exe (PID: 5384)
- BackgroundTransferHost.exe (PID: 1244)
- BackgroundTransferHost.exe (PID: 5964)
- BackgroundTransferHost.exe (PID: 6108)
- BackgroundTransferHost.exe (PID: 4068)
- BackgroundTransferHost.exe (PID: 900)
- BackgroundTransferHost.exe (PID: 736)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 6108)
- slui.exe (PID: 6668)
- BackgroundTransferHost.exe (PID: 4068)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 6108)
- BackgroundTransferHost.exe (PID: 4068)
Manual execution by a user
- wscript.exe (PID: 1040)
Checks supported languages
- VKBtniFiAqVXinckNm.exe (PID: 5228)
- ShellExperienceHost.exe (PID: 6112)
Reads the computer name
- VKBtniFiAqVXinckNm.exe (PID: 5228)
- ShellExperienceHost.exe (PID: 6112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cnt | | | Help File Contents (100) |
|---|
Total processes
176
Monitored processes
20
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\6891015397_2025-03-24-915882218_M7B7R6.vbs.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4068 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4464 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 4648 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 177
Read events
15 144
Write events
33
Delete events
0
Modification events
| (PID) Process: | (1244) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1244) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1244) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4068) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4068) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4068) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5964) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4068 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\173ff363-5c12-4d07-b1d1-7592d946c4c7.down_data | — | |
MD5:— | SHA256:— | |||
| 6108 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f241f0d1-e76c-4570-ab10-2fc564390811.down_data | — | |
MD5:— | SHA256:— | |||
| 1040 | wscript.exe | C:\Users\Public\HQDZZPrfqbB6E560FS4AH78B6NSCMfeob.kvy | — | |
MD5:— | SHA256:— | |||
| 1040 | wscript.exe | C:\Users\Public\VKBtniFiAqVXinckNm.exe | — | |
MD5:— | SHA256:— | |||
| 6108 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\9768146e-6224-4f78-96c4-e5ccb30f02c1.b6e99914-40ee-42b8-a344-36fa66a9af9d.down_meta | binary | |
MD5:EFD94FB0214A3CC3BD9FF02E95315E9D | SHA256:176CD19C24FA18FFF2289573DDBAEE84E7DD17265B3DAF3FE633020EE279C655 | |||
| 6108 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f241f0d1-e76c-4570-ab10-2fc564390811.b6e99914-40ee-42b8-a344-36fa66a9af9d.down_meta | binary | |
MD5:EFD94FB0214A3CC3BD9FF02E95315E9D | SHA256:176CD19C24FA18FFF2289573DDBAEE84E7DD17265B3DAF3FE633020EE279C655 | |||
| 6108 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\9768146e-6224-4f78-96c4-e5ccb30f02c1.up_meta_secure | binary | |
MD5:4BE8854F2E51E54AEE683655A8CA35A7 | SHA256:8D6EE93C1F38014FD6A858479A21800C7078EEB6A0586C3A0EC6B3CF4E527062 | |||
| 4068 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\b1eab709-44c0-4c4b-adc6-e1aed445c681.5e00053d-6ae8-4cb1-8b0b-3d726a7189c0.down_meta | binary | |
MD5:F25EA5D2109B0C692C512325BF1D62F5 | SHA256:959A4FA3187E8F6850C87D66E87E1973DF15078D31E0075FD799D2946E68976B | |||
| 1040 | wscript.exe | C:\Users\Public\VKBtniFiAqVXinckNm.zip | compressed | |
MD5:A999931FF93628FEDA78550F3F4F6D5E | SHA256:52BA0AE5CCDF610D71AFAB08B28AB1646E89D38A24942FE71058F5B6092700BD | |||
| 4068 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\b1eab709-44c0-4c4b-adc6-e1aed445c681.up_meta_secure | binary | |
MD5:8251F217AD3F9A558242C953E1F512A6 | SHA256:EA407564C767C939BCBE964D17678A2791384D996AAAB9B4C7ADB225A7F39B16 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
102
DNS requests
29
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
644 | SIHClient.exe | GET | 200 | 23.48.23.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
644 | SIHClient.exe | GET | 200 | 23.48.23.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
644 | SIHClient.exe | GET | 200 | 23.48.23.180:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.103.156.88:443 | https://arc.msn.com/v3/Delivery/Placement?pubid=da63df93-3dbc-42ae-a505-b34988683ac7&pid=280815&adm=2&w=1&h=1&wpx=1&hpx=1&fmt=json&cltp=app&dim=le&rafb=0&nct=1&pm=1&cfmt=text,image,poly&sft=jpeg,png,gif&topt=1&poptin=0&localid=w:AC7699B0-48EA-FD22-C8DC-06A02098A0F0&ctry=GB&time=20250324T190600Z&lc=en-US&pl=en-US,en-GB&idtp=mid&uid=9115d6d1-9f4e-4053-9297-2a8c833b3912&aid=00000000-0000-0000-0000-000000000000&ua=WindowsShellClient%2F9.0.40929.0%20%28Windows%29&asid=826305c379f2443d9cfb8c46034673be&ctmode=MultiSession&arch=x64&betaedgever=0.0.0.0&canedgever=0.0.0.0&cdm=1&cdmver=10.0.19041.3636&currsel=137271744000000000&devedgever=0.0.0.0&devfam=Windows.Desktop&devform=Unknown&devosver=10.0.19045.4046&disphorzres=1280&dispsize=15.3&dispvertres=720&fosver=16299&isu=0&lo=3967865&metered=false&nettype=ethernet&npid=sc-280815&oemName=DELL&oemid=DELL&ossku=Professional&prevosver=15063&smBiosDm=DELL&stabedgever=122.0.2365.59&tl=2&tsu=1358395&waasBldFlt=1&waasCfgExp=1&waasCfgSet=1&waasRetail=1&waasRing=&svoffered=2 | unknown | binary | 2.96 Kb | whitelisted |
— | — | POST | 400 | 20.190.159.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 20.223.35.26:443 | https://arc.msn.com/v3/Delivery/Placement?pubid=da63df93-3dbc-42ae-a505-b34988683ac7&pid=88000045&adm=2&w=1&h=1&wpx=1&hpx=1&fmt=json&cltp=app&dim=le&rafb=0&nct=1&pm=1&cfmt=text,image,poly&sft=jpeg,png,gif&topt=1&poptin=0&localid=w:AC7699B0-48EA-FD22-C8DC-06A02098A0F0&ctry=GB&time=20250324T190600Z&lc=en-US&pl=en-US,en-GB&idtp=mid&uid=9115d6d1-9f4e-4053-9297-2a8c833b3912&aid=00000000-0000-0000-0000-000000000000&ua=WindowsShellClient%2F9.0.40929.0%20%28Windows%29&asid=abcfda3eb19447f2b485f079c27ae674&ctmode=MultiSession&arch=x64&betaedgever=0.0.0.0&canedgever=0.0.0.0&cdm=1&cdmver=10.0.19041.3636&currsel=137271744000000000&devedgever=0.0.0.0&devfam=Windows.Desktop&devform=Unknown&devosver=10.0.19045.4046&disphorzres=1280&dispsize=15.3&dispvertres=720&fosver=16299&isu=0&lo=3967865&metered=false&nettype=ethernet&npid=sc-88000045&oemName=DELL&oemid=DELL&ossku=Professional&prevosver=15063&smBiosDm=DELL&stabedgever=122.0.2365.59&tl=2&tsu=1358395&waasBldFlt=1&waasCfgExp=1&waasCfgSet=1&waasRetail=1&waasRing=&svoffered=2 | unknown | binary | 2.97 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.171:443 | https://www.bing.com/th?id=OADD2.10239414284817_1UVYYSBXC4CID8KBL&pid=21.2&c=16&roil=0&roit=0&roir=1&roib=1&w=48&h=48&dynsize=1&qlt=90 | unknown | image | 1.93 Kb | whitelisted |
— | — | GET | 200 | 20.223.35.26:443 | https://arc.msn.com/v3/Delivery/Placement?pubid=da63df93-3dbc-42ae-a505-b34988683ac7&pid=310091&adm=2&w=1&h=1&wpx=1&hpx=1&fmt=json&cltp=app&dim=le&rafb=0&nct=1&pm=1&cfmt=text,image,poly&sft=jpeg,png,gif&topt=1&poptin=0&localid=w:AC7699B0-48EA-FD22-C8DC-06A02098A0F0&ctry=GB&time=20250324T190600Z&lc=en-US&pl=en-US,en-GB&idtp=mid&uid=9115d6d1-9f4e-4053-9297-2a8c833b3912&aid=00000000-0000-0000-0000-000000000000&ua=WindowsShellClient%2F9.0.40929.0%20%28Windows%29&asid=52244f4bd91c4716a3cb30981ad183fd&ctmode=MultiSession&arch=x64&betaedgever=0.0.0.0&canedgever=0.0.0.0&cdm=1&cdmver=10.0.19041.3636&devedgever=0.0.0.0&devfam=Windows.Desktop&devform=Unknown&devosver=10.0.19045.4046&disphorzres=1280&dispsize=15.3&dispvertres=720&fosver=16299&isu=0&lo=3967865&metered=false&nettype=ethernet&npid=sc-310091&oemName=DELL&oemid=DELL&ossku=Professional&prevosver=15063&rver=2&smBiosDm=DELL&stabedgever=122.0.2365.59&tl=2&tsu=1358395&waasBldFlt=1&waasCfgExp=1&waasCfgSet=1&waasRetail=1&waasRing=&svoffered=2 | unknown | binary | 4.22 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6244 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4068 | BackgroundTransferHost.exe | 104.126.37.160:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
644 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5228 | VKBtniFiAqVXinckNm.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
5228 | VKBtniFiAqVXinckNm.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |