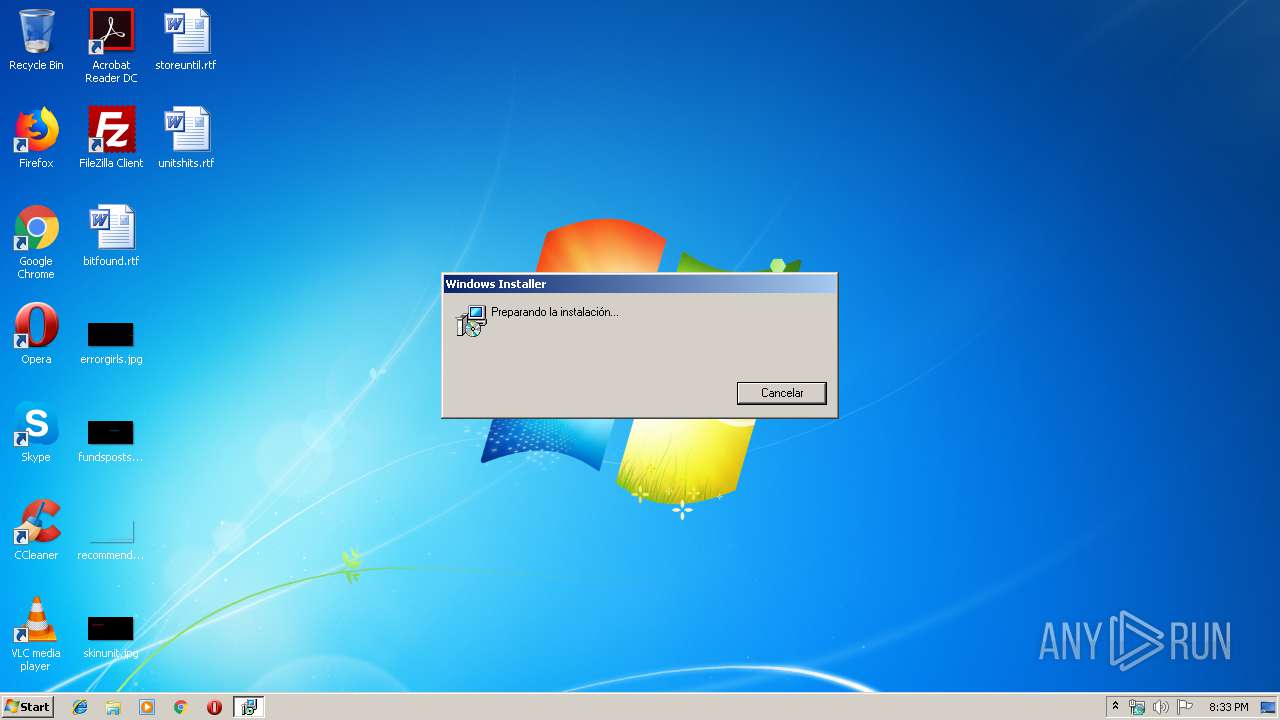
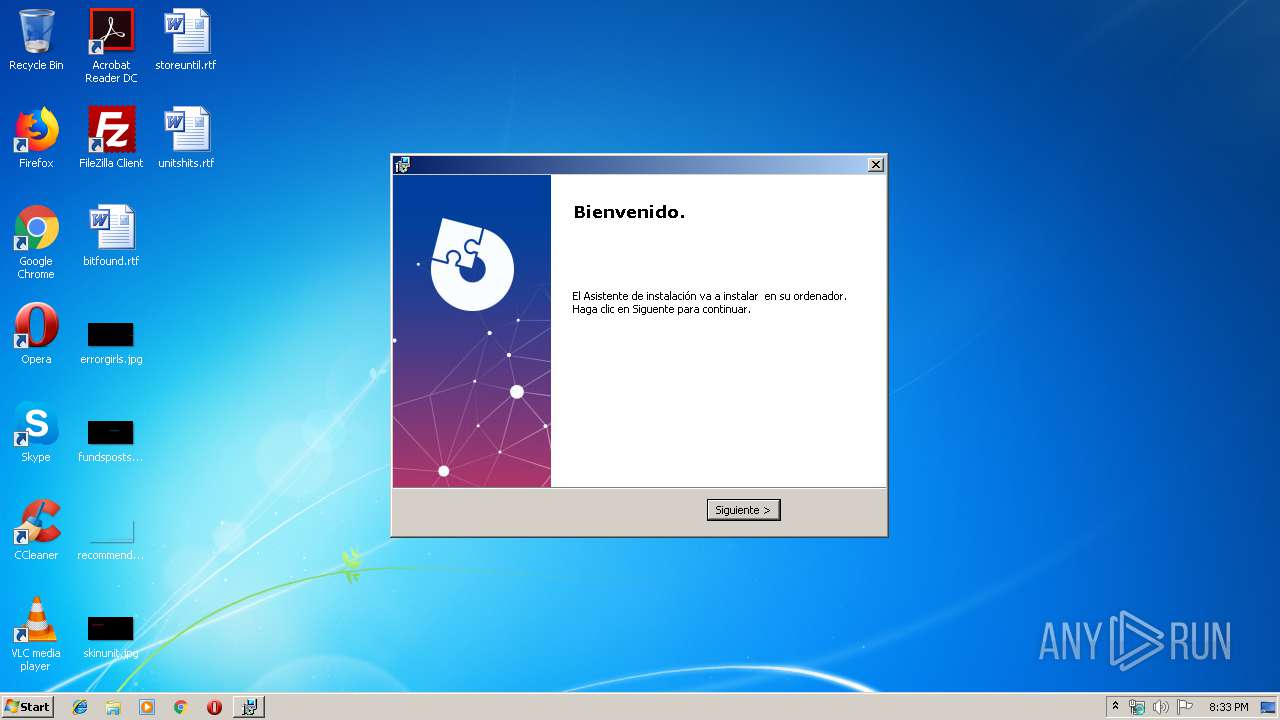
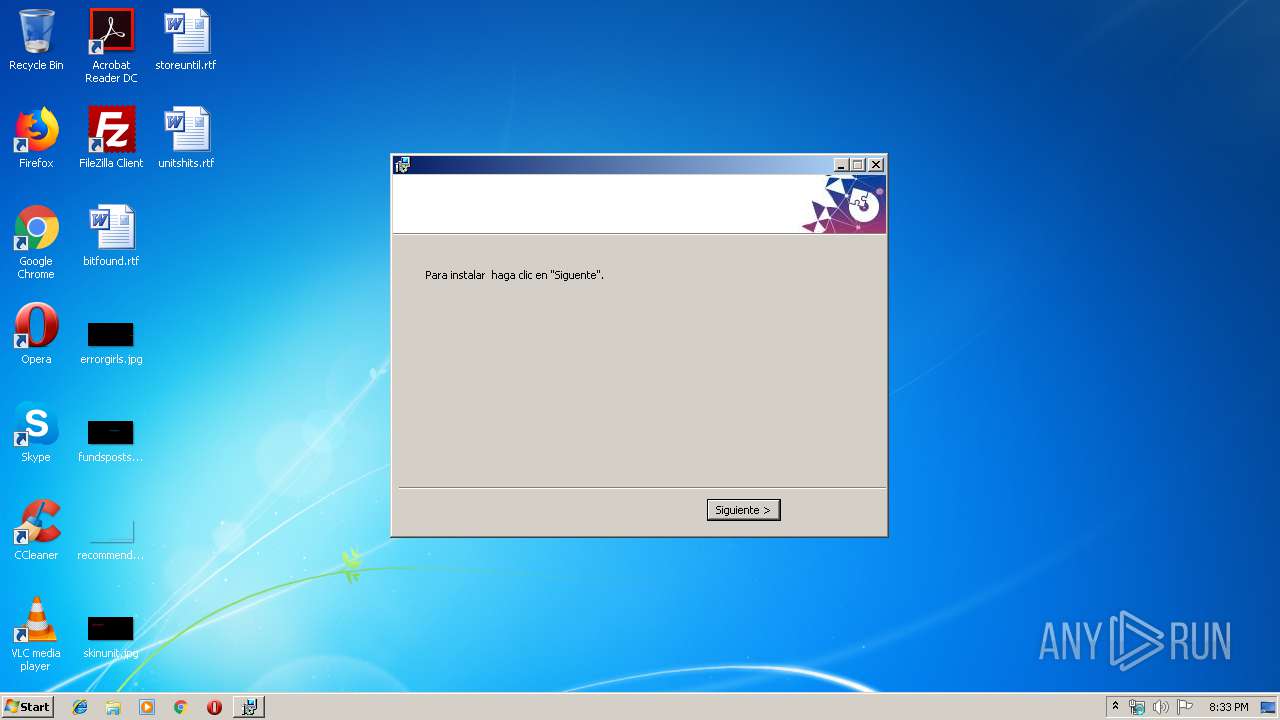
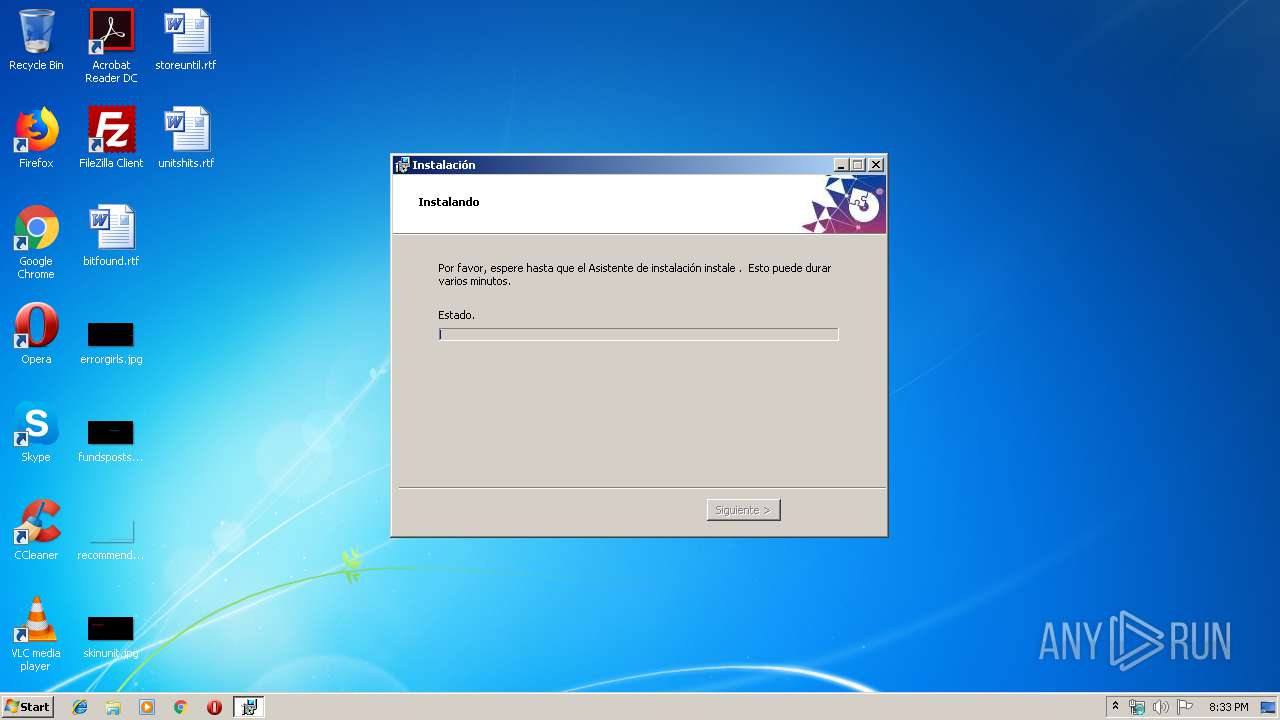
| File name: | 1SCX7734769589574545.msi |
| Full analysis: | https://app.any.run/tasks/08a8d09a-9d54-4164-bd00-40eb4bee148f |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 19:33:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Dec 11 11:47:44 2009, Security: 0, Code page: 1252, Revision Number: {BB0E8E78-DEDE-4650-9987-BBDA435E617D}, Number of Words: 10, Subject: SCUFhHngaDCD4NEL15, Author: SCUFhHngaDCD4NEL15, Name of Creating Application: Advanced Installer 16.2 build 436ecd62, Template: ;3082, Comments: Esta base de datos del instalador contiene la lgica y los datos necesarios para instalar SCUFhHngaDCD4NEL15., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | F9654AD045C8B0BE904D68A0D81510AB |
| SHA1: | BFECCB1C3A5A1418E5EB74817EE40396F28FA527 |
| SHA256: | 0B7C0103EB9C3839C667720CE469318E9A2809186AE6C1DD1A65A3916935B15C |
| SSDEEP: | 12288:N9fYTFIWlAJPlP41dpd5e6mBLUVEVWE72W8wrkAyJ:NJYTFId/5IqVXCWJrkAy |
MALICIOUS
Changes settings of System certificates
- msiexec.exe (PID: 2944)
Writes to a start menu file
- MsiExec.exe (PID: 3664)
SUSPICIOUS
Creates files in the user directory
- MsiExec.exe (PID: 3664)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2936)
Executed as Windows Service
- vssvc.exe (PID: 3128)
Executed via COM
- DrvInst.exe (PID: 2292)
INFO
Application launched itself
- msiexec.exe (PID: 2936)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3128)
Searches for installed software
- msiexec.exe (PID: 2936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2009:12:11 11:47:44 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {BB0E8E78-DEDE-4650-9987-BBDA435E617D} |
| Words: | 10 |
| Subject: | SCUFhHngaDCD4NEL15 |
| Author: | SCUFhHngaDCD4NEL15 |
| LastModifiedBy: | - |
| Software: | Advanced Installer 16.2 build 436ecd62 |
| Template: | ;3082 |
| Comments: | Esta base de datos del instalador contiene la lógica y los datos necesarios para instalar SCUFhHngaDCD4NEL15. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
38
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2292 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot22" "" "" "695c3f483" "00000000" "000005C4" "000005C8" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2588 | C:\Windows\system32\MsiExec.exe -Embedding 52E9A8F8B2D957FC89A36EE9DF914771 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2936 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2944 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\1SCX7734769589574545.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3128 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3664 | C:\Windows\system32\MsiExec.exe -Embedding 0E9FDDF4D0AD46B7593305EC9615A7C0 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
759
Read events
561
Write events
186
Delete events
12
Modification events
| (PID) Process: | (2944) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2944) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\CA\Certificates\EAB040689A0D805B5D6FD654FC168CFF00B78BE3 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000EAB040689A0D805B5D6FD654FC168CFF00B78BE31400000001000000140000005379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB040000000100000010000000DB78CBD190952735D940BC80AC2432C00F0000000100000030000000435FE6564241D6B3828352EF9BE443D511C21F0AFB325C4038A5820F00D87774A8EF2193DDAAE065B2572FAF2BF0EE63190000000100000010000000EA6089055218053DD01E37E1D806EEDF18000000010000001000000045ED9BBC5E43D3B9ECD63C060DB78E5C20000000010000007B050000308205773082045FA003020102021013EA28705BF4ECED0C36630980614336300D06092A864886F70D01010C0500306F310B300906035504061302534531143012060355040A130B416464547275737420414231263024060355040B131D41646454727573742045787465726E616C20545450204E6574776F726B312230200603550403131941646454727573742045787465726E616C20434120526F6F74301E170D3030303533303130343833385A170D3230303533303130343833385A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A381F43081F1301F0603551D23041830168014ADBD987A34B426F7FAC42654EF03BDE024CB541A301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF30110603551D20040A300830060604551D200030440603551D1F043D303B3039A037A0358633687474703A2F2F63726C2E7573657274727573742E636F6D2F416464547275737445787465726E616C4341526F6F742E63726C303506082B0601050507010104293027302506082B060105050730018619687474703A2F2F6F6373702E7573657274727573742E636F6D300D06092A864886F70D01010C050003820101009365F63783950F5EC3821C1FD677E73C8AC0AA09F0E90B26F1E0C26A75A1C779C9B95260C829120EF0AD03D609C476DFE5A68195A746DA8257A99592C5B68F03226C3377C17B32176E07CE5A14413A05241BF614063BA825240EBBCC2A75DDB970413F7CD0633621071F46FF60A491E167BCDE1F7E1914C9636791EA67076BB48F8BC06E437DC3A1806CB21EBC53857DDC90A1A4BC2DEF4672573505BFBB46BB6E6D3799B6FF239291C66E40F88F2956EA5FD55F1453ACF04F61EAF722CCA7560BE2B8341F26D97B1905683FBA3CD43806A2D3E68F0EE3B4716D4042C584B440952BF465A04879F61D8163969D4F75E0F87CE48EA9D1F2AD8AB38CC721CDC2EF | |||
| (PID) Process: | (2936) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000EE304C6BD87ED501780B0000680B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2936) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000048934E6BD87ED501780B0000680B0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2936) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 24 | |||
| (PID) Process: | (2936) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000004ACAA66BD87ED501780B0000680B0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2936) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000A42CA96BD87ED501780B0000100A0000E80300000100000000000000000000006D6332237327AA4C98794F8D3B88D7E30000000000000000 | |||
| (PID) Process: | (3128) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000000CB6B26BD87ED501380C0000C40A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3128) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000006618B56BD87ED501380C0000740E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3128) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000006618B56BD87ED501380C00006C0E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
2
Suspicious files
6
Text files
30
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI51C6.tmp | — | |
MD5:— | SHA256:— | |||
| 2944 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5235.tmp | — | |
MD5:— | SHA256:— | |||
| 2944 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5245.tmp | — | |
MD5:— | SHA256:— | |||
| 2944 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5275.tmp | — | |
MD5:— | SHA256:— | |||
| 2936 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2936 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF03AB6CE517DBFCA4.TMP | — | |
MD5:— | SHA256:— | |||
| 3128 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 2936 | msiexec.exe | C:\Windows\Installer\MSIA75A.tmp | — | |
MD5:— | SHA256:— | |||
| 2936 | msiexec.exe | C:\Config.Msi\11a344.rbs | — | |
MD5:— | SHA256:— | |||
| 2936 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF2FC3A6BCE4F72A09.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3664 | MsiExec.exe | GET | — | 69.42.49.155:80 | http://www.leonloard.com/LLCP/wawst4ts1.zip | US | — | — | unknown |
2944 | msiexec.exe | GET | 200 | 91.199.212.52:80 | http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2944 | msiexec.exe | 91.199.212.52:80 | crt.usertrust.com | Comodo CA Ltd | GB | suspicious |
3664 | MsiExec.exe | 69.42.49.155:80 | www.leonloard.com | DataBank Holdings, Ltd. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crt.usertrust.com |
| whitelisted |
www.leonloard.com |
| unknown |