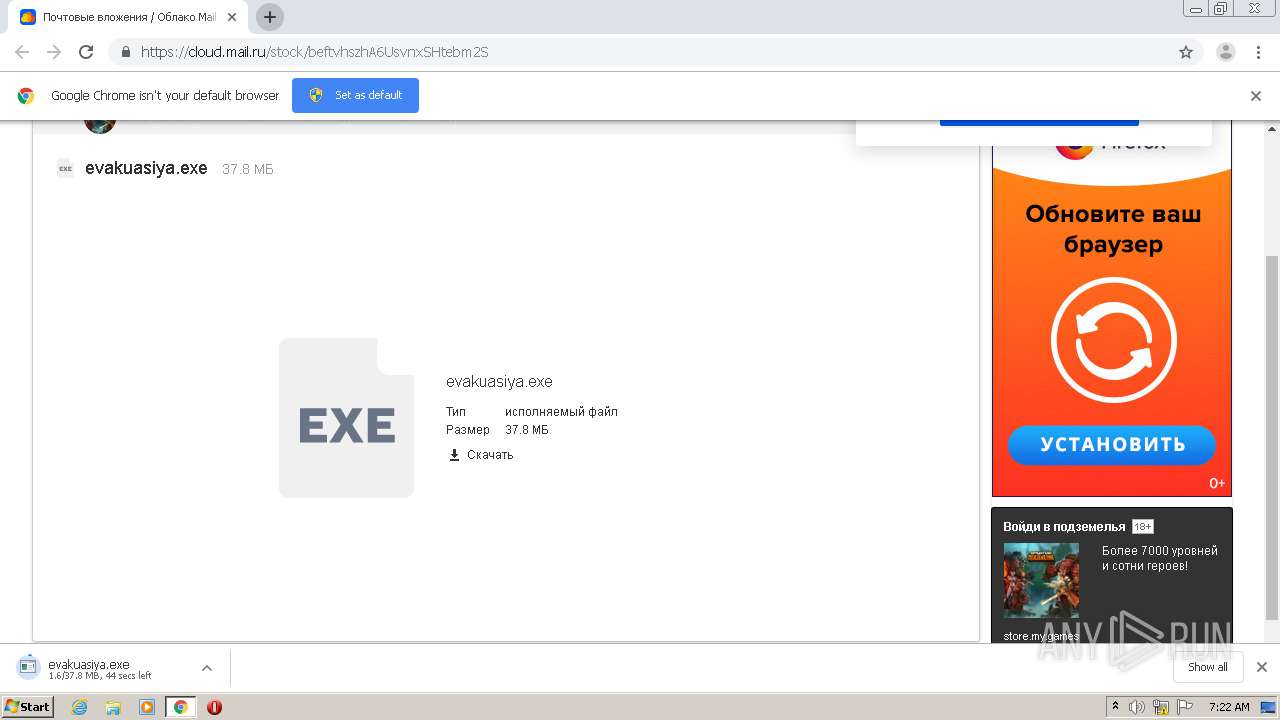
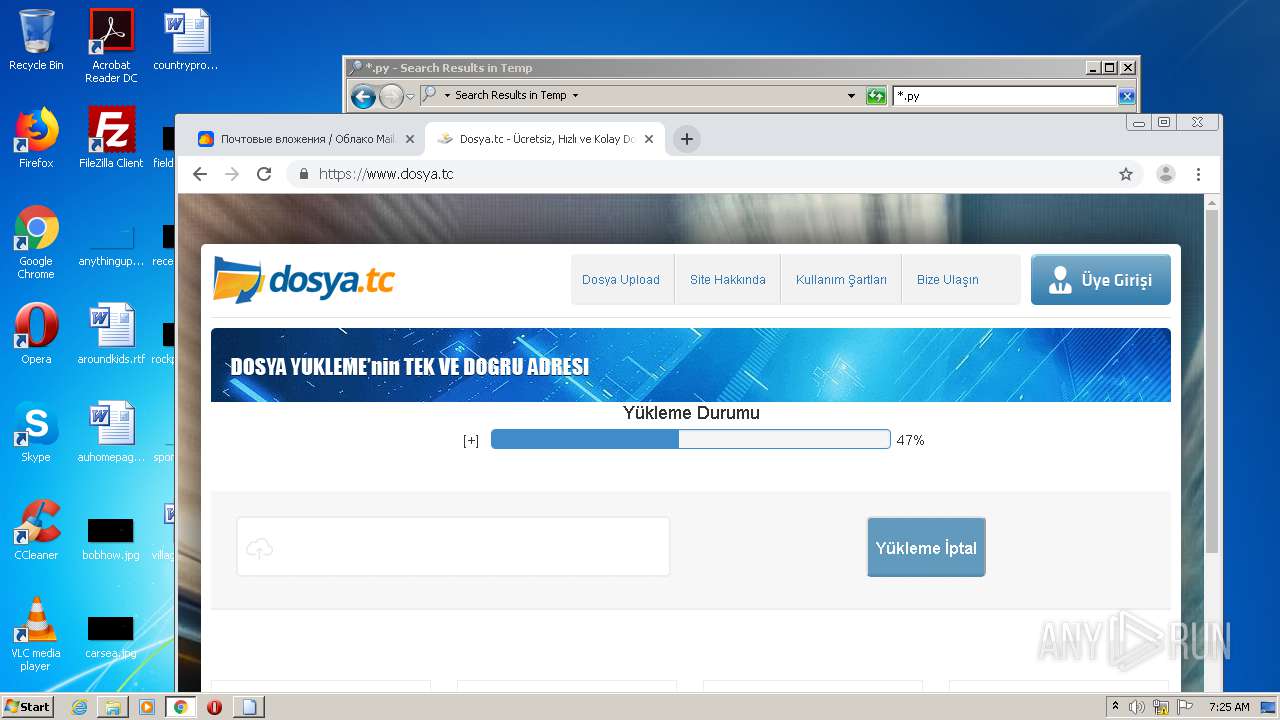
| URL: | https://cloud.mail.ru/stock/beftvhszhA6UsvnxSHtebm2S |
| Full analysis: | https://app.any.run/tasks/19640aeb-0c05-4e9e-9f45-d5cd76525398 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 06:22:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 48FFD30B25CF97A82CE77C1394A7779A |
| SHA1: | 38DB5BECB0BF5B6A6995CE256DC0EFCEAD361D09 |
| SHA256: | 0B5E01A3D3B357C9E489FA7F9D4E9387A2F76C983F43E8F1B33188832F49750D |
| SSDEEP: | 3:N8ULBLxs/N3LUmoX2:2UKN3D |
MALICIOUS
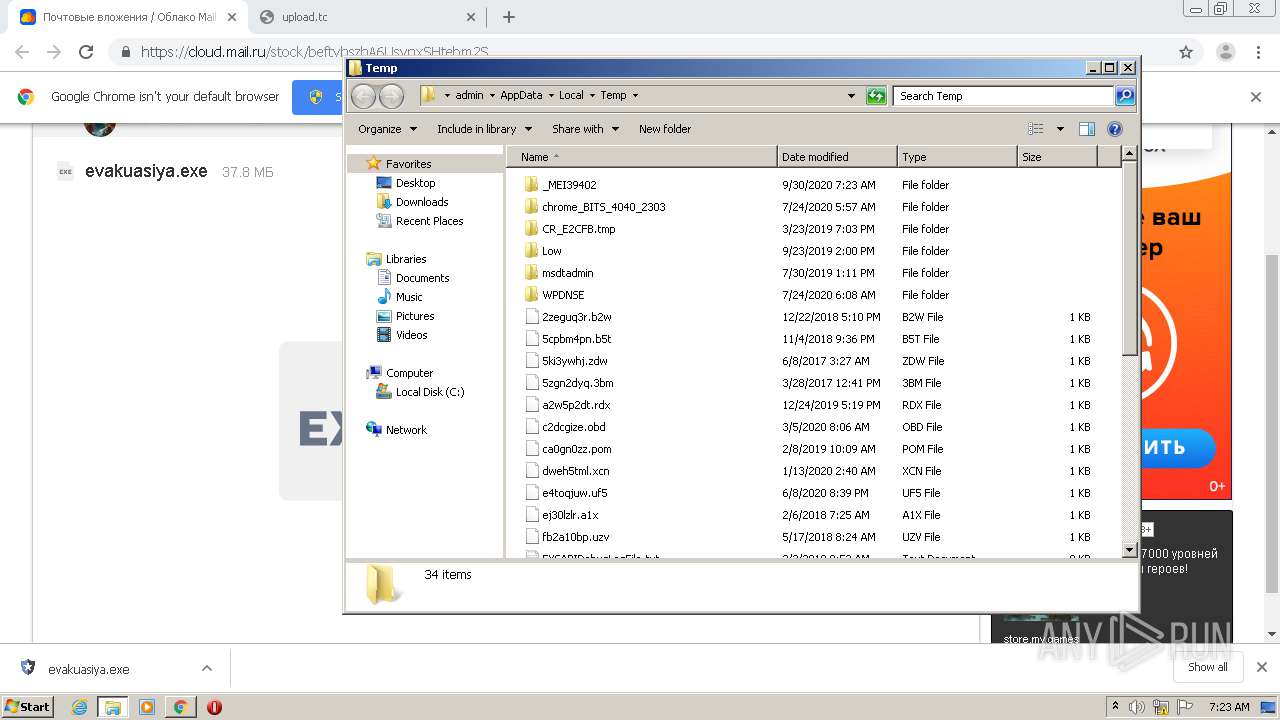
Application was dropped or rewritten from another process
- evakuasiya.exe (PID: 3940)
- evakuasiya.exe (PID: 3700)
Loads dropped or rewritten executable
- evakuasiya.exe (PID: 3700)
- explorer.exe (PID: 352)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2108)
- evakuasiya.exe (PID: 3940)
Application launched itself
- evakuasiya.exe (PID: 3940)
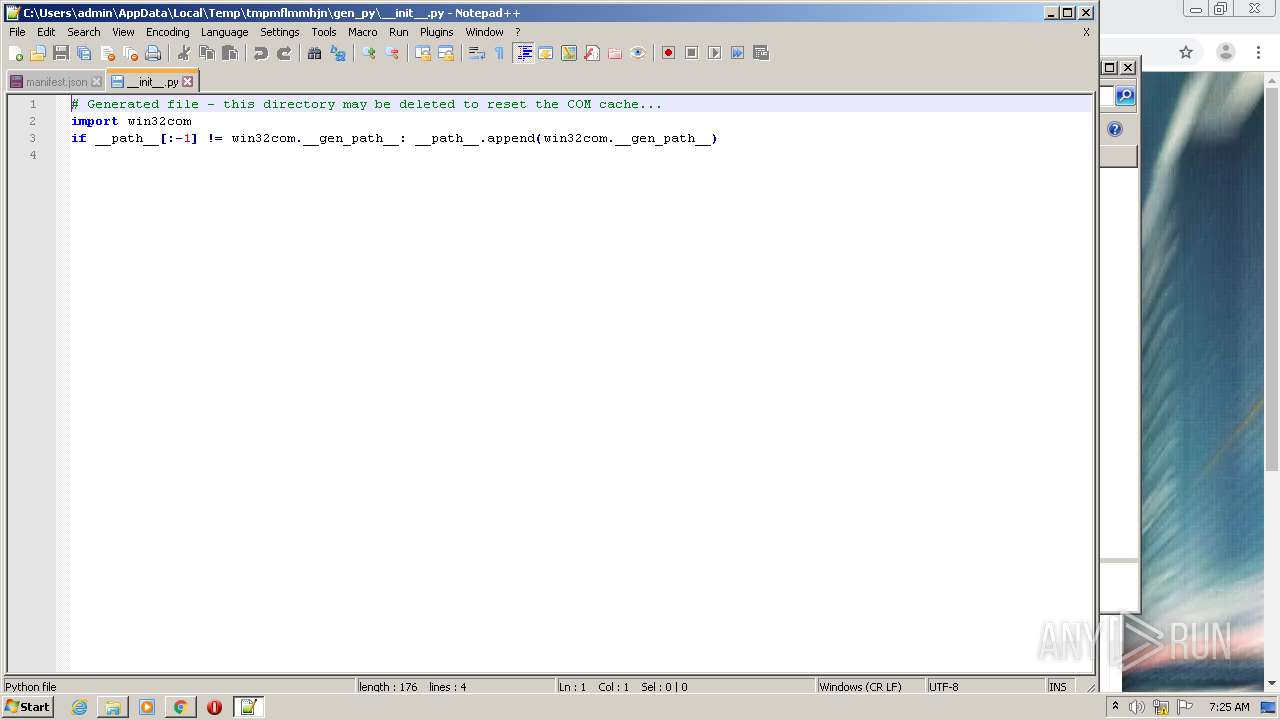
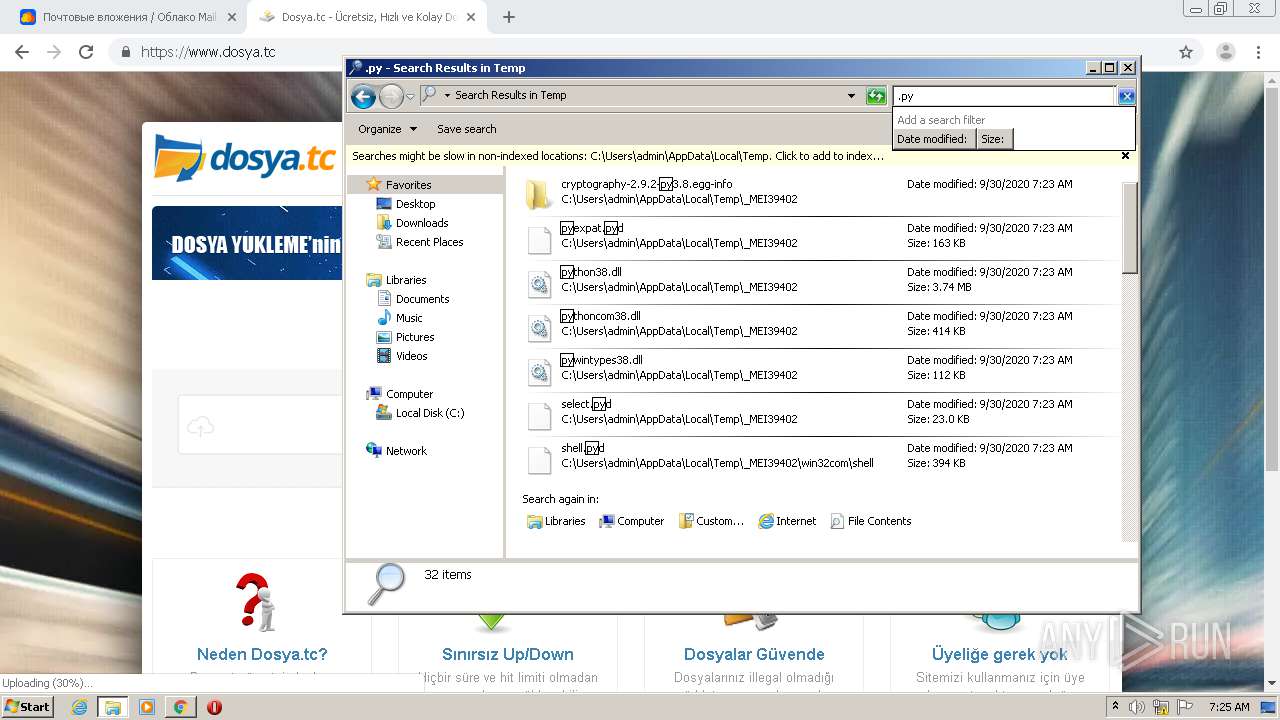
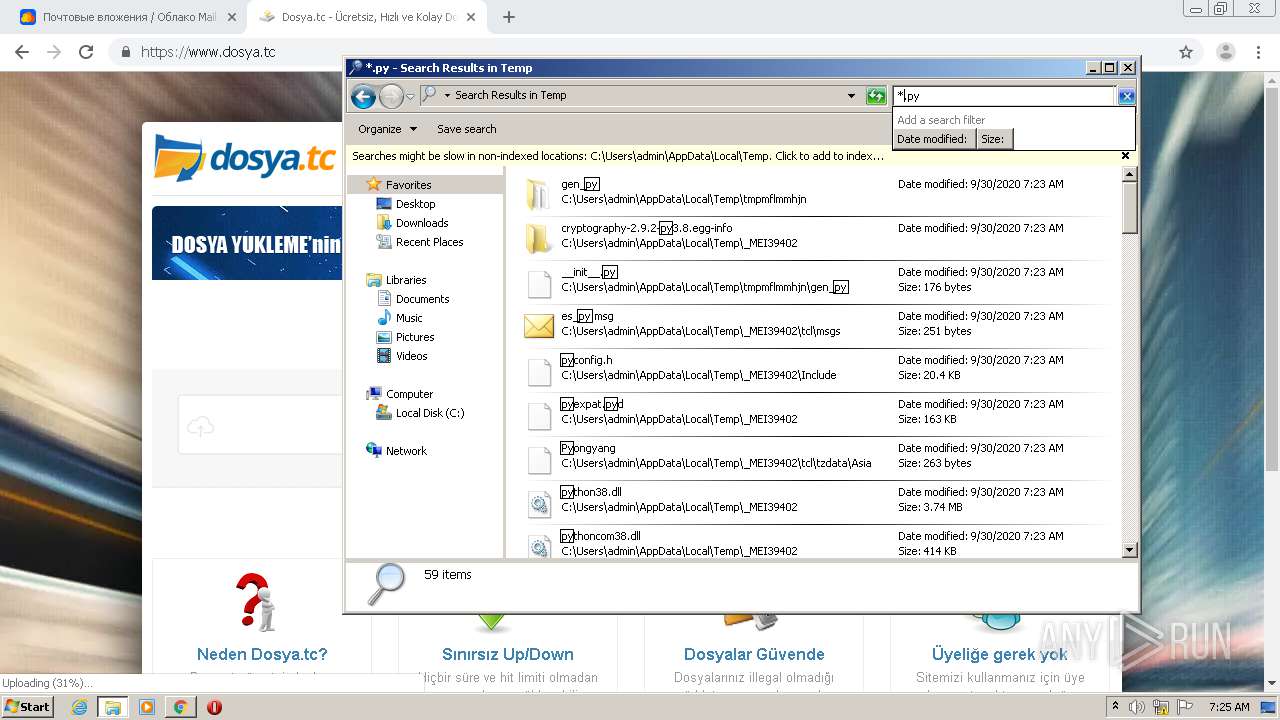
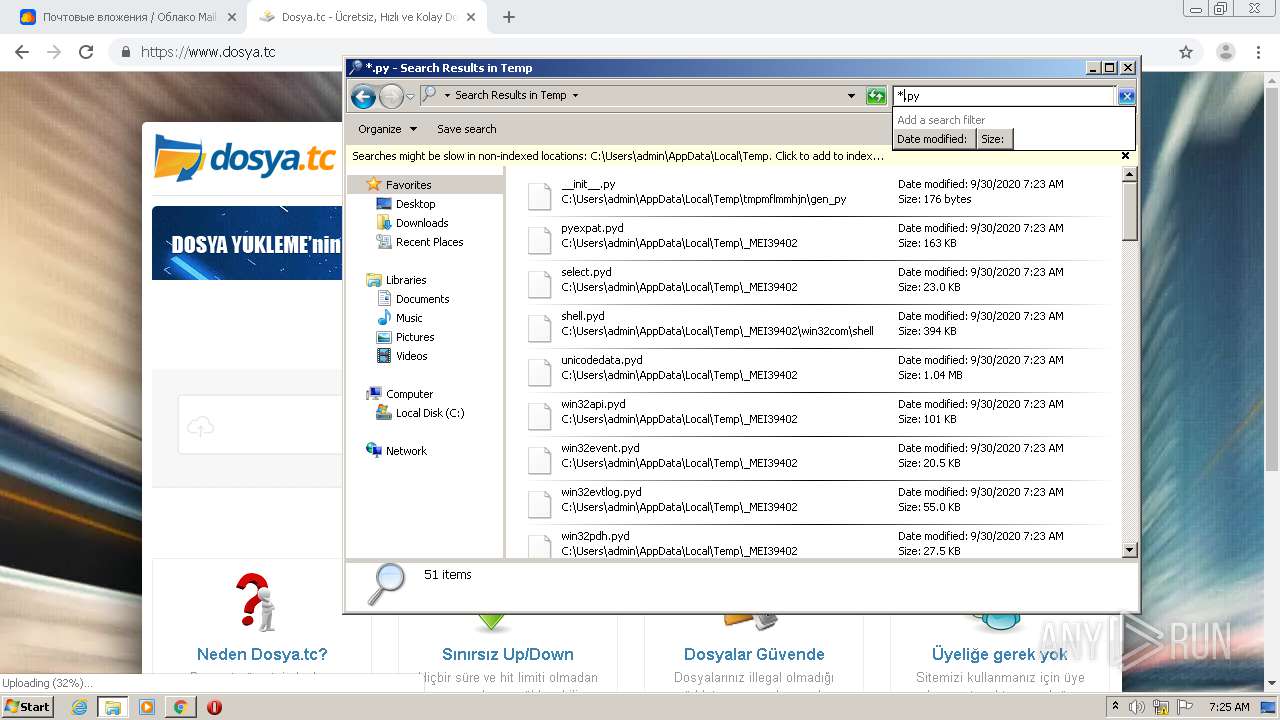
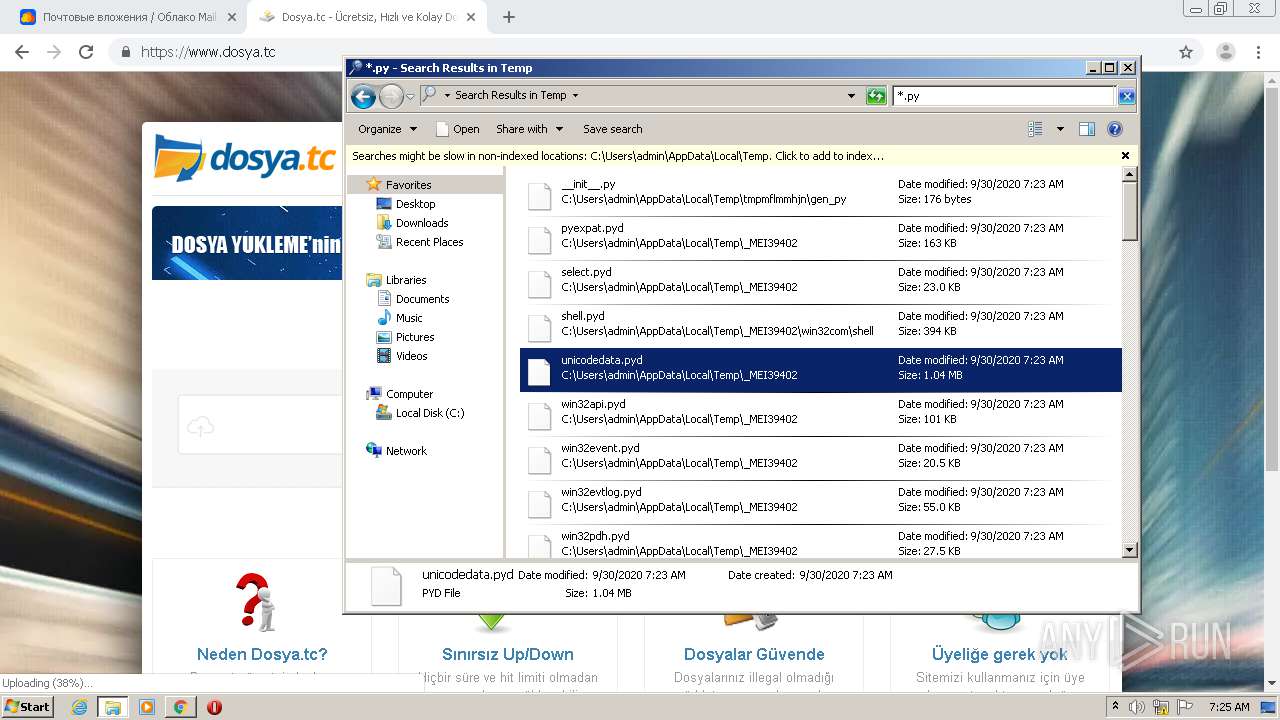
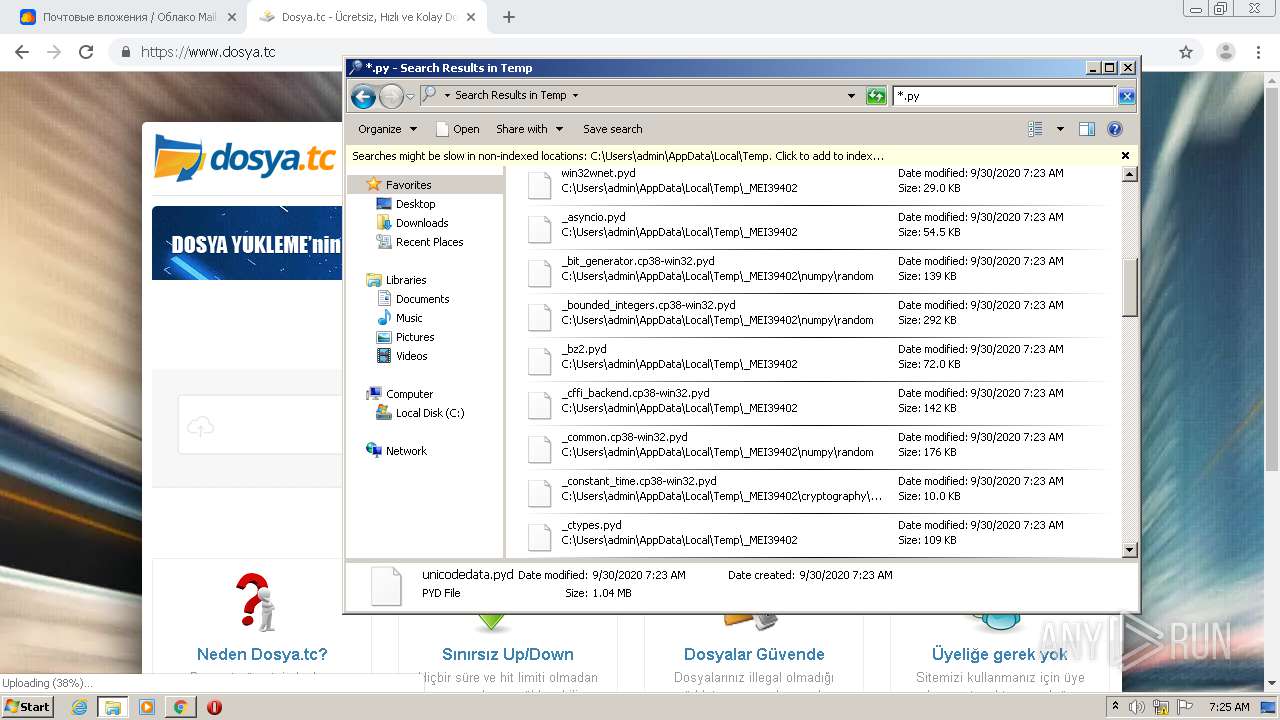
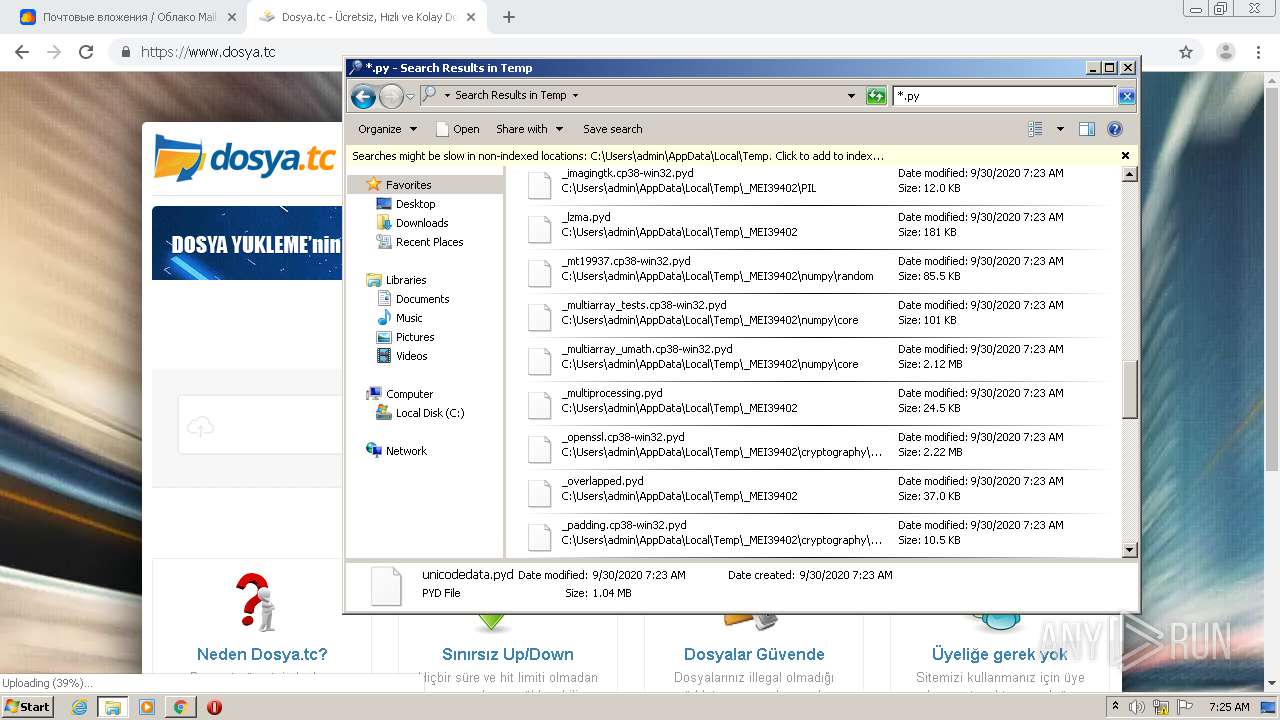
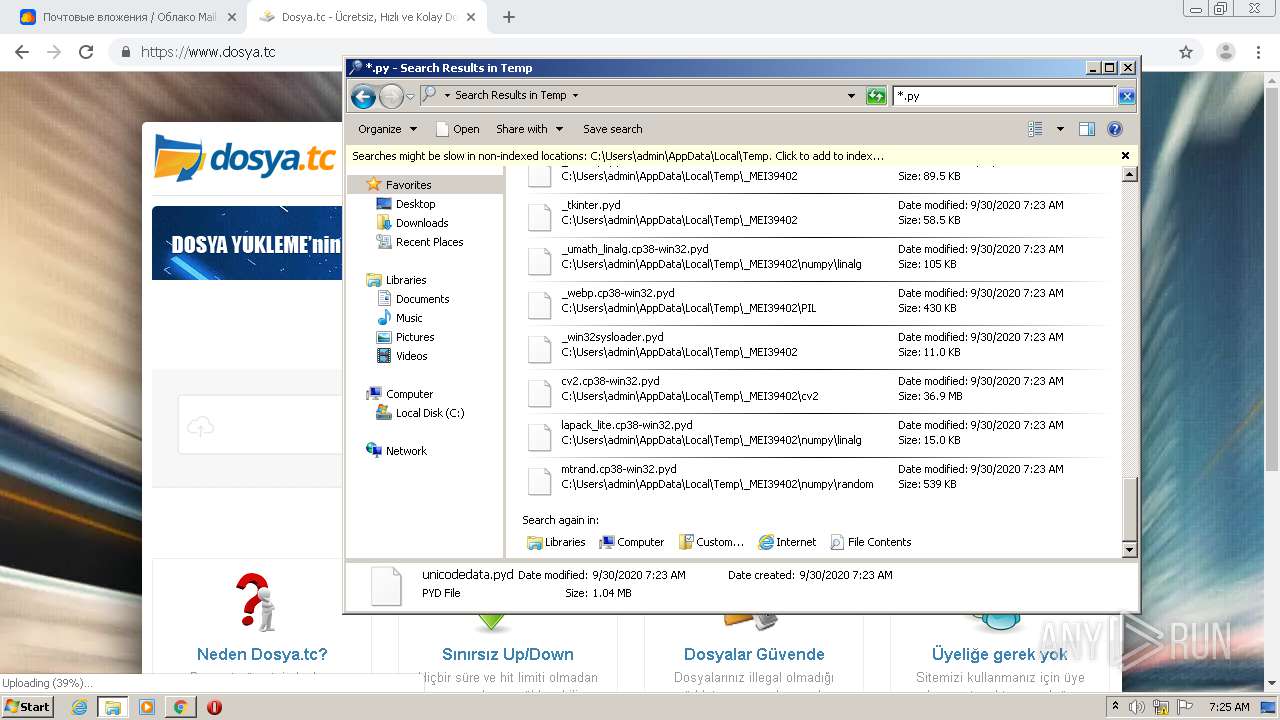
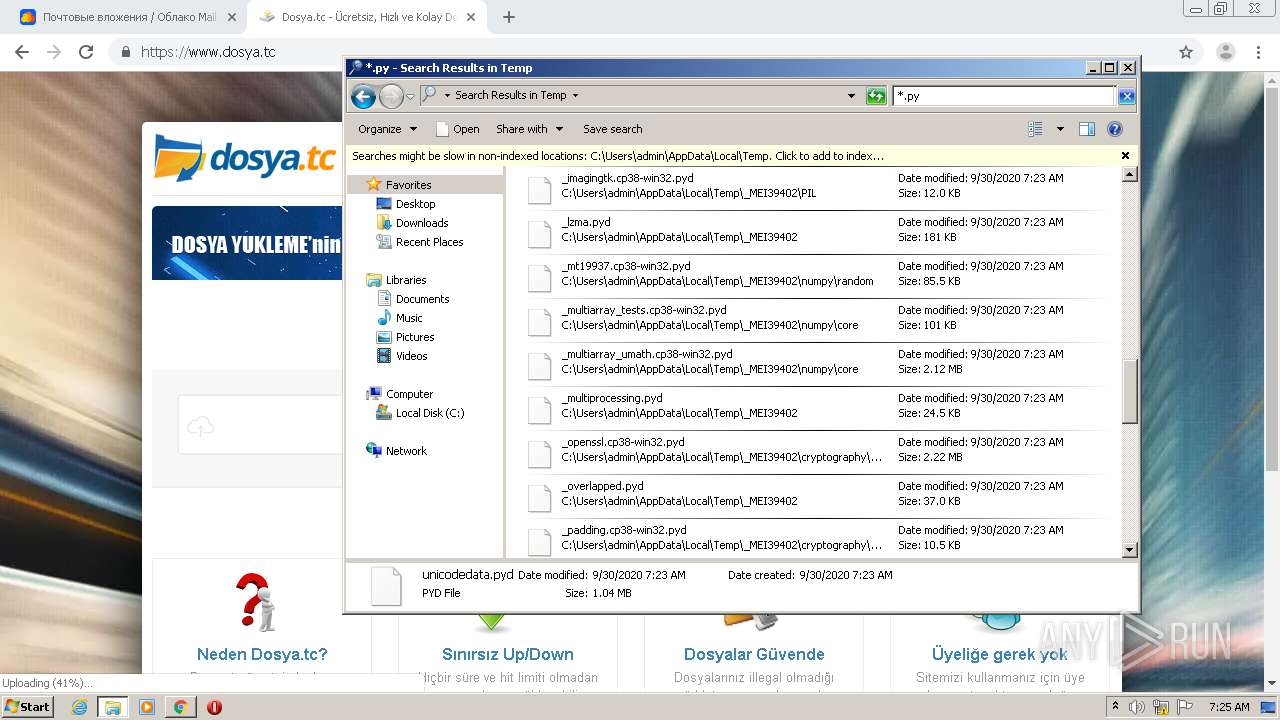
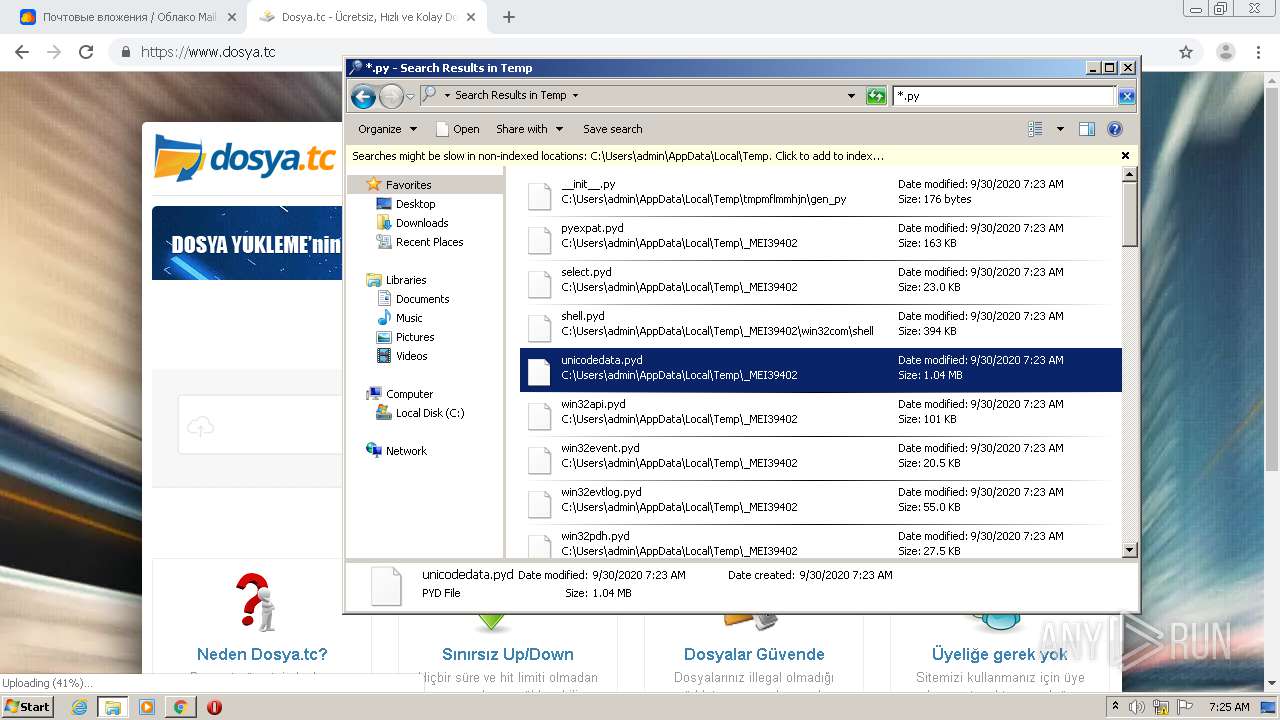
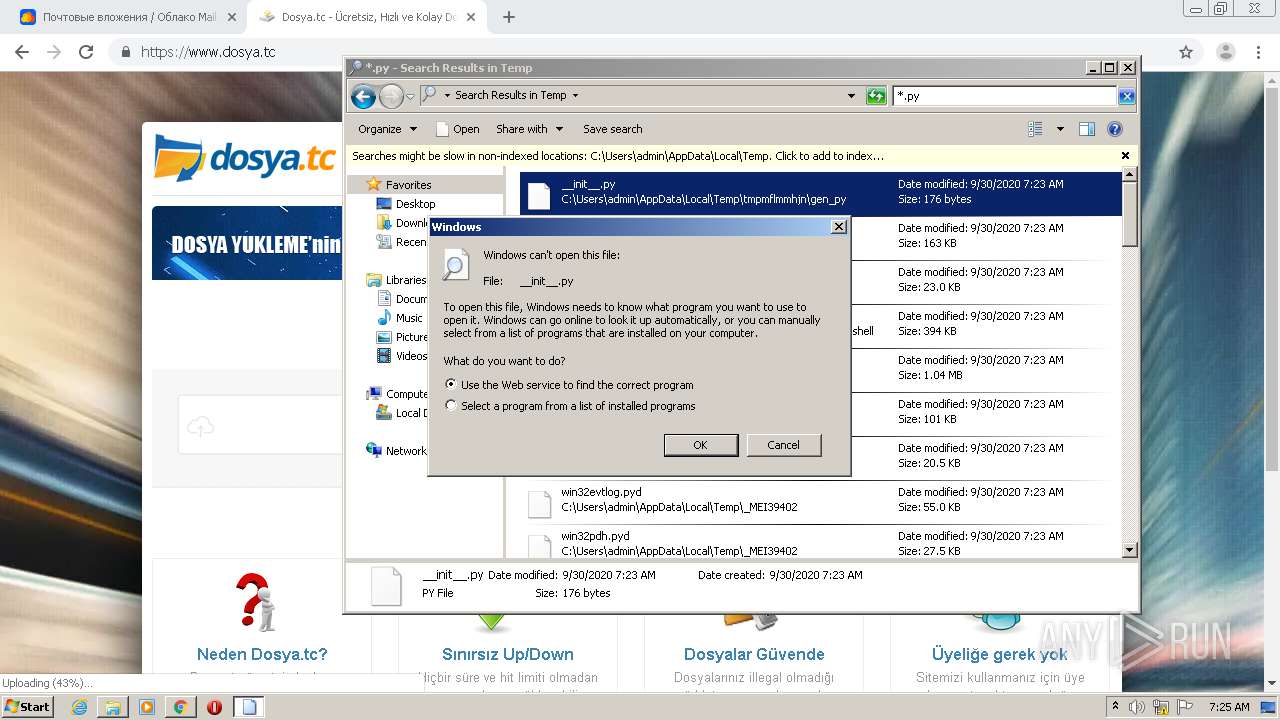
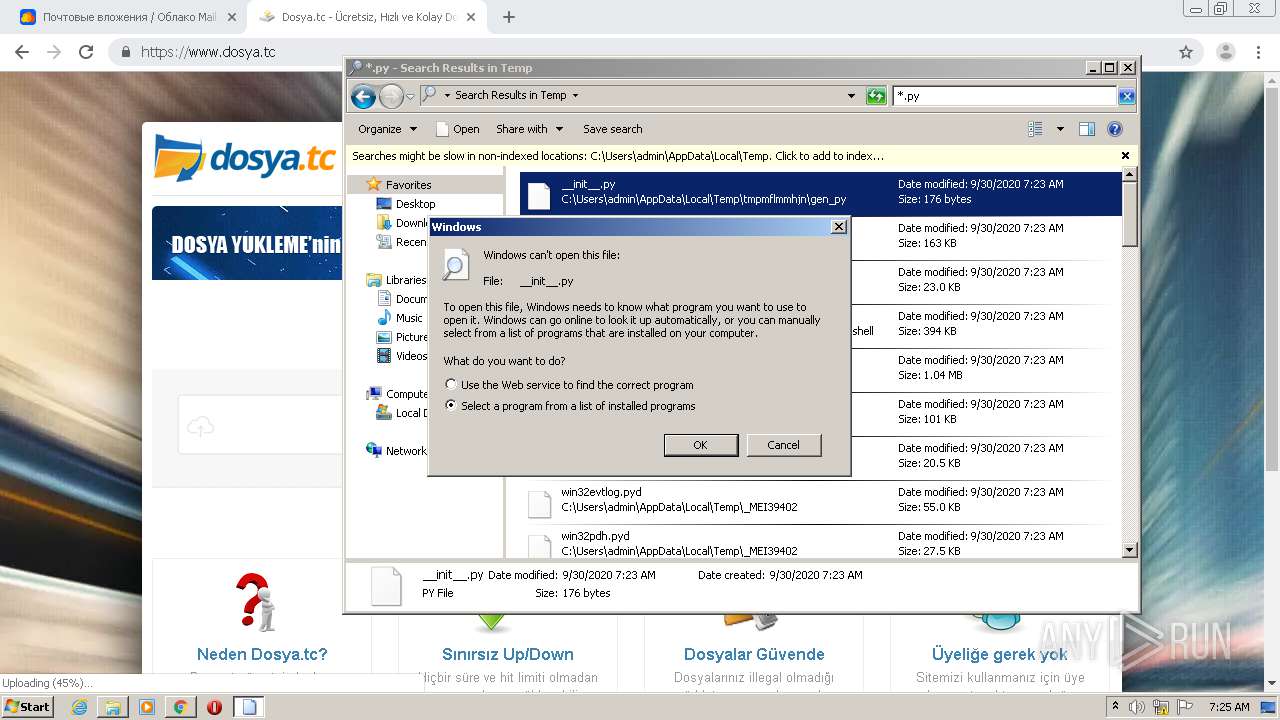
Loads Python modules
- evakuasiya.exe (PID: 3700)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 352)
INFO
Reads the hosts file
- chrome.exe (PID: 2108)
- chrome.exe (PID: 2800)
Manual execution by user
- verclsid.exe (PID: 2420)
- notepad++.exe (PID: 3568)
Dropped object may contain Bitcoin addresses
- evakuasiya.exe (PID: 3940)
Reads Internet Cache Settings
- chrome.exe (PID: 2108)
Application launched itself
- chrome.exe (PID: 2108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
81
Monitored processes
40
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8514916006734278939 --mojo-platform-channel-handle=2880 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=3372392824911944149 --mojo-platform-channel-handle=1360 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8776397579427850497 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4020 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16659780354932615 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3560 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=6976239001768904966 --mojo-platform-channel-handle=4060 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18086530883627106260 --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3036 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=336677338917327227 --mojo-platform-channel-handle=1356 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12399186375742309747 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3620 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,5417610324640819046,5329011680590189718,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=16504982163946257371 --mojo-platform-channel-handle=632 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 371
Read events
2 580
Write events
785
Delete events
6
Modification events
| (PID) Process: | (2272) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2108-13245920561904750 |
Value: 259 | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3228-13245745346152343 |
Value: 0 | |||
| (PID) Process: | (2108) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2108-13245920561904750 |
Value: 259 | |||
Executable files
62
Suspicious files
106
Text files
1 062
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F742432-83C.pma | — | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\9bd58496-936b-4691-b915-676060e9fdfb.tmp | — | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000046.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF3b7679.TMP | text | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | text | |
MD5:— | SHA256:— | |||
| 2108 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
109
DNS requests
61
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2800 | chrome.exe | 217.69.133.145:443 | top-fwz1.mail.ru | Limited liability company Mail.Ru | RU | suspicious |
2800 | chrome.exe | 172.217.21.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2800 | chrome.exe | 217.69.139.6:443 | cloud.mail.ru | Limited liability company Mail.Ru | RU | unknown |
2800 | chrome.exe | 216.58.207.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
2800 | chrome.exe | 172.217.23.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
2800 | chrome.exe | 217.69.139.102:443 | img.imgsmail.ru | Limited liability company Mail.Ru | RU | unknown |
2800 | chrome.exe | 94.100.180.197:443 | rs.mail.ru | Limited liability company Mail.Ru | RU | unknown |
2800 | chrome.exe | 94.100.180.61:443 | oauth.mail.ru | Limited liability company Mail.Ru | RU | unknown |
2800 | chrome.exe | 217.69.139.244:443 | r.mradx.net | Limited liability company Mail.Ru | RU | unknown |
2800 | chrome.exe | 217.69.139.209:443 | limg.imgsmail.ru | Limited liability company Mail.Ru | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cloud.mail.ru |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
img.imgsmail.ru |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
rs.mail.ru |
| whitelisted |
oauth.mail.ru |
| unknown |
r.mradx.net |
| whitelisted |
limg.imgsmail.ru |
| whitelisted |
an.mail.ru |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|