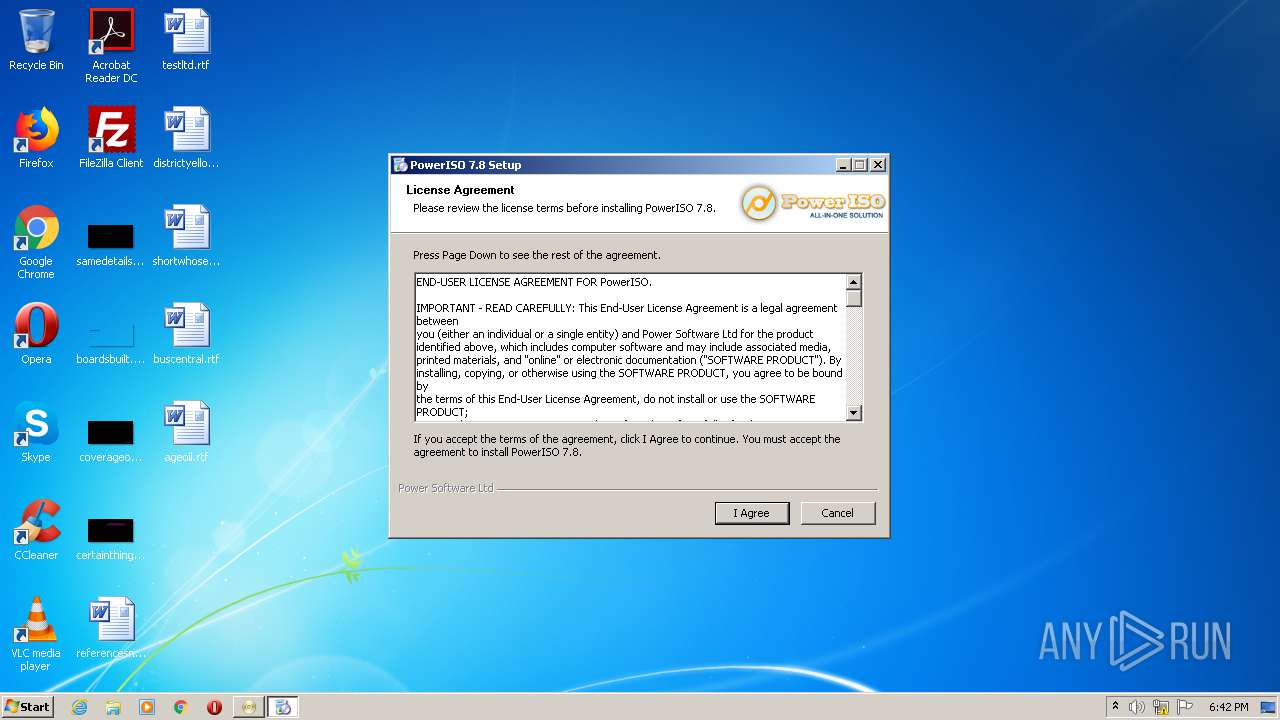
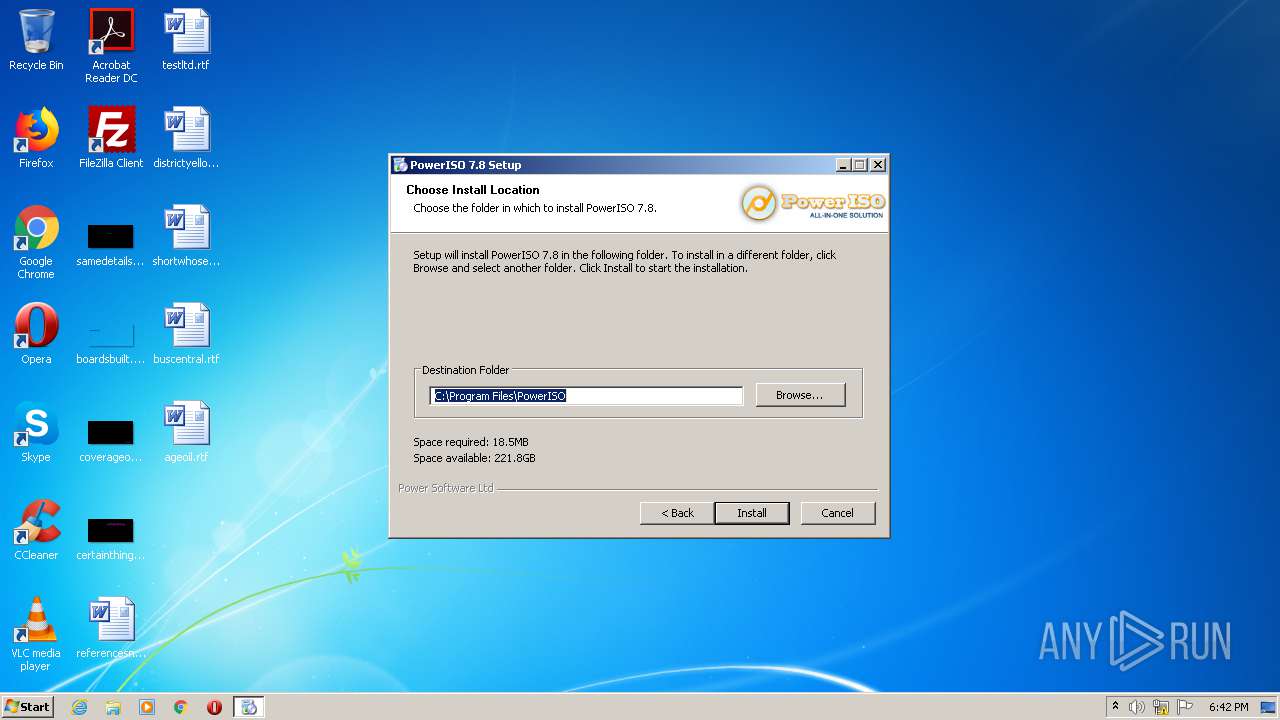
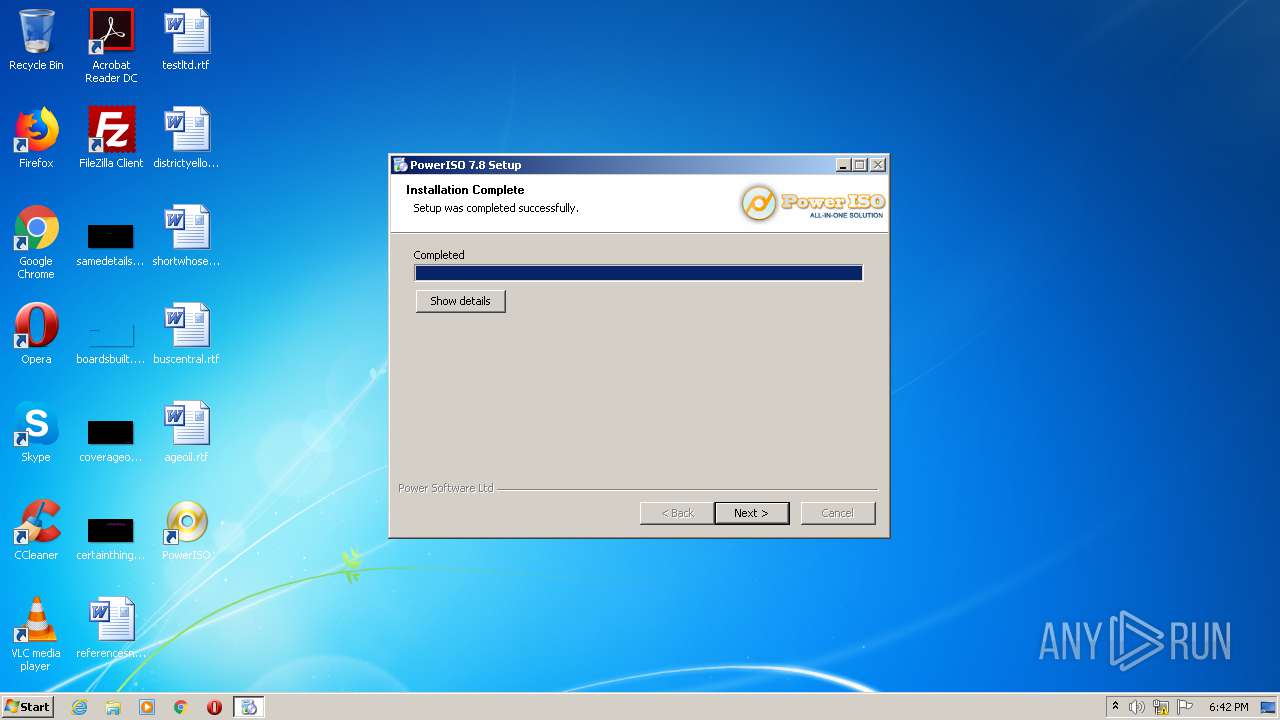
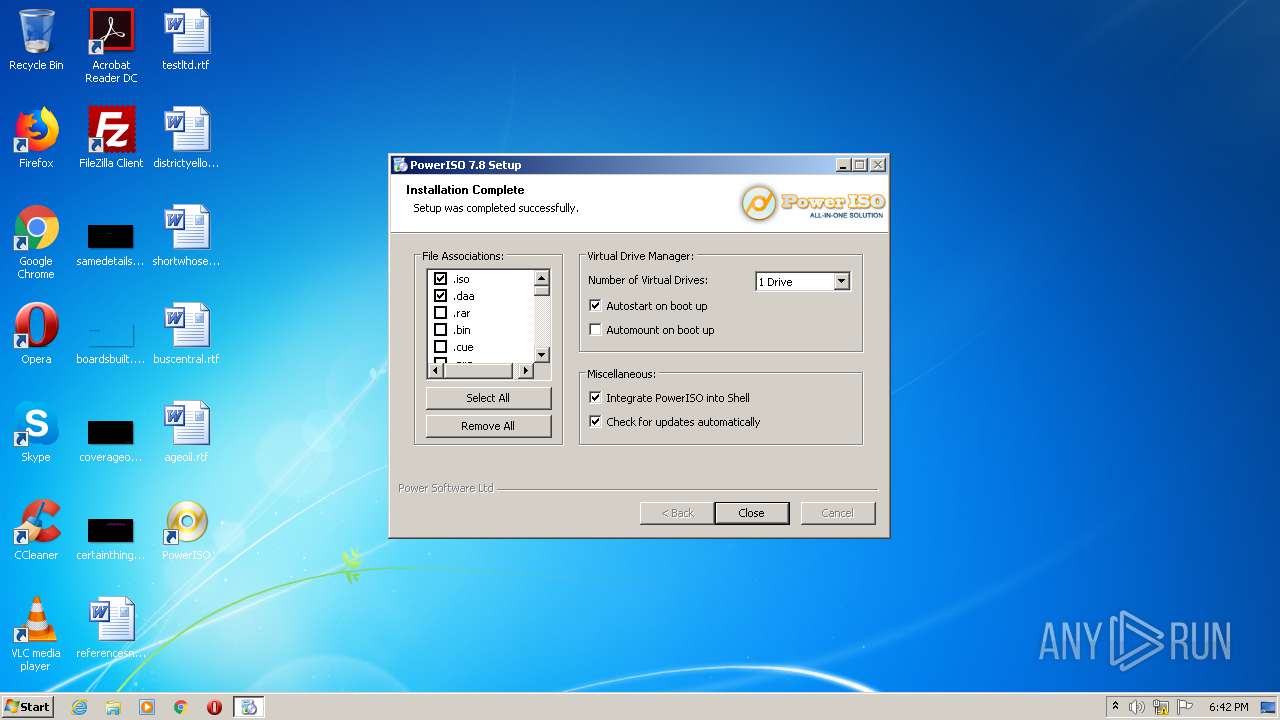
| File name: | PowerISO 7.8 Retail YGG Torrent Edition.exe |
| Full analysis: | https://app.any.run/tasks/b182a1e9-3a61-4932-996f-6a2dc2336102 |
| Verdict: | Malicious activity |
| Analysis date: | November 11, 2020, 18:41:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3FE5353D2144286D21281F5409B35261 |
| SHA1: | 1CD9956D82DDFE70D85351092990127B5D032E4A |
| SHA256: | 0B5496C7A767944009C0FAD285216A2083E496BAD5459340F031590B17B96265 |
| SSDEEP: | 196608:WKqhBBw+a/pzIrya9gbzyLQPaG9EhnFI5f1HgvUxS:gB0uGa9gYQPJSnUfRg8S |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- Setup_32bit.exe (PID: 3048)
Application was dropped or rewritten from another process
- PWRISOVM.EXE (PID: 3656)
Changes the autorun value in the registry
- Setup_32bit.exe (PID: 3048)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 3152)
SUSPICIOUS
Reads the Windows organization settings
- PowerISO 7.8 Retail YGG Torrent Edition.tmp (PID: 3056)
Reads Windows owner or organization settings
- PowerISO 7.8 Retail YGG Torrent Edition.tmp (PID: 3056)
Uses TASKKILL.EXE to kill process
- PowerISO 7.8 Retail YGG Torrent Edition.tmp (PID: 3056)
Uses REG.EXE to modify Windows registry
- PowerISO 7.8 Retail YGG Torrent Edition.tmp (PID: 3056)
Executable content was dropped or overwritten
- PowerISO 7.8 Retail YGG Torrent Edition.tmp (PID: 3056)
- Setup_32bit.exe (PID: 3048)
- PowerISO 7.8 Retail YGG Torrent Edition.exe (PID: 3588)
Creates files in the Windows directory
- Setup_32bit.exe (PID: 3048)
Creates files in the driver directory
- Setup_32bit.exe (PID: 3048)
Creates or modifies windows services
- Setup_32bit.exe (PID: 3048)
Modifies the open verb of a shell class
- Setup_32bit.exe (PID: 3048)
Creates COM task schedule object
- regsvr32.exe (PID: 3152)
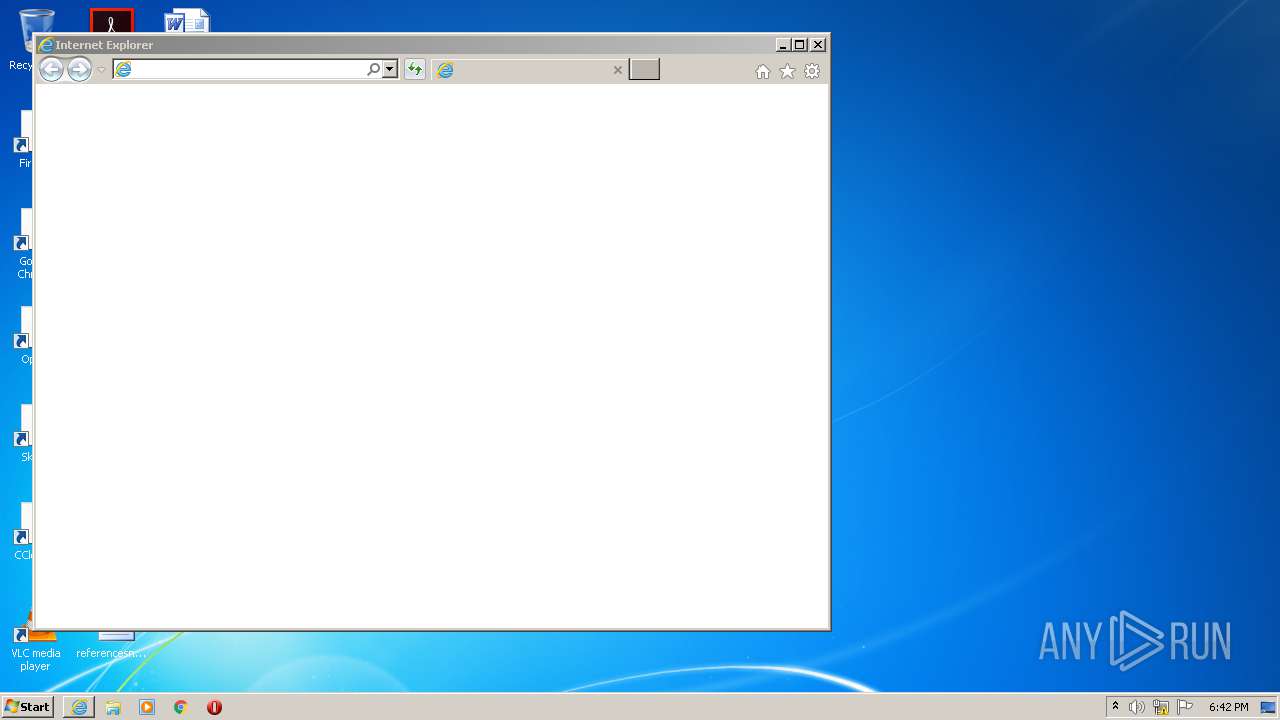
Starts Internet Explorer
- Setup_32bit.exe (PID: 3048)
INFO
Loads dropped or rewritten executable
- PowerISO 7.8 Retail YGG Torrent Edition.tmp (PID: 3056)
- Setup_32bit.exe (PID: 3048)
Application was dropped or rewritten from another process
- Setup_32bit.exe (PID: 3048)
- PowerISO 7.8 Retail YGG Torrent Edition.tmp (PID: 3056)
Creates a software uninstall entry
- Setup_32bit.exe (PID: 3048)
Creates files in the program directory
- Setup_32bit.exe (PID: 3048)
Reads Internet Cache Settings
- iexplore.exe (PID: 3144)
- iexplore.exe (PID: 2088)
Changes internet zones settings
- iexplore.exe (PID: 3144)
Reads settings of System Certificates
- iexplore.exe (PID: 3144)
Changes settings of System certificates
- iexplore.exe (PID: 3144)
Reads internet explorer settings
- iexplore.exe (PID: 2088)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3144)
Creates files in the user directory
- iexplore.exe (PID: 2088)
Application launched itself
- iexplore.exe (PID: 3144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:10:02 07:04:04+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 86016 |
| InitializedDataSize: | 182272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16478 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.8.0.0 |
| ProductVersionNumber: | 7.8.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Adam Bedoui - YGG Torrent |
| FileDescription: | PowerISO 7.8 Retail YGG Torrent Edition |
| FileVersion: | 7.8.0.0 |
| LegalCopyright: | Adam Bedoui - YGG Torrent |
| ProductName: | Adam Bedoui - YGG Torrent |
| ProductVersion: | 7.8.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-Oct-2012 05:04:04 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Adam Bedoui - YGG Torrent |
| FileDescription: | PowerISO 7.8 Retail YGG Torrent Edition |
| FileVersion: | 7.8.0.0 |
| LegalCopyright: | Adam Bedoui - YGG Torrent |
| ProductName: | Adam Bedoui - YGG Torrent |
| ProductVersion: | 7.8.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 02-Oct-2012 05:04:04 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000143F8 | 0x00014400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.4822 |
.itext | 0x00016000 | 0x00000BE8 | 0x00000C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.01516 |
.data | 0x00017000 | 0x00000D9C | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.66929 |
.bss | 0x00018000 | 0x00005750 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0001E000 | 0x00000F9E | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.96778 |
.tls | 0x0001F000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00020000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.190489 |
.rsrc | 0x00021000 | 0x0002A7A0 | 0x0002A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.40334 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.06505 | 1376 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 5.51423 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.61316 | 1736 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.24575 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 7.94307 | 21528 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 4.5489 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 4.67618 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 4.84429 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 4.85277 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 5.0996 | 2440 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
54
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3144 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2372 | "taskkill.exe" /f /im "PowerISO.exe" | C:\Windows\system32\taskkill.exe | — | PowerISO 7.8 Retail YGG Torrent Edition.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2808 | "C:\Users\admin\AppData\Local\Temp\PowerISO 7.8 Retail YGG Torrent Edition.exe" | C:\Users\admin\AppData\Local\Temp\PowerISO 7.8 Retail YGG Torrent Edition.exe | — | explorer.exe | |||||||||||
User: admin Company: Adam Bedoui - YGG Torrent Integrity Level: MEDIUM Description: PowerISO 7.8 Retail YGG Torrent Edition Exit code: 3221226540 Version: 7.8.0.0 Modules
| |||||||||||||||
| 3040 | regsvr32.exe /s /u "C:\Program Files\PowerISO\PWRISOSH.DLL" | C:\Windows\system32\regsvr32.exe | — | Setup_32bit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | "C:\Users\admin\AppData\Local\Temp\is-KOPH4.tmp\Setup_32bit.exe" | C:\Users\admin\AppData\Local\Temp\is-KOPH4.tmp\Setup_32bit.exe | PowerISO 7.8 Retail YGG Torrent Edition.tmp | ||||||||||||
User: admin Company: Power Software Ltd Integrity Level: HIGH Description: PowerISO Setup Exit code: 0 Version: 7.8.0.0 Modules
| |||||||||||||||
| 3056 | "C:\Users\admin\AppData\Local\Temp\is-JOL8S.tmp\PowerISO 7.8 Retail YGG Torrent Edition.tmp" /SL5="$60138,8774460,269312,C:\Users\admin\AppData\Local\Temp\PowerISO 7.8 Retail YGG Torrent Edition.exe" | C:\Users\admin\AppData\Local\Temp\is-JOL8S.tmp\PowerISO 7.8 Retail YGG Torrent Edition.tmp | PowerISO 7.8 Retail YGG Torrent Edition.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3144 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.poweriso.com/thankyou.htm | C:\Program Files\Internet Explorer\iexplore.exe | Setup_32bit.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3152 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files\PowerISO\PWRISOSH.DLL" | C:\Windows\System32\regsvr32.exe | — | Setup_32bit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3588 | "C:\Users\admin\AppData\Local\Temp\PowerISO 7.8 Retail YGG Torrent Edition.exe" | C:\Users\admin\AppData\Local\Temp\PowerISO 7.8 Retail YGG Torrent Edition.exe | explorer.exe | ||||||||||||
User: admin Company: Adam Bedoui - YGG Torrent Integrity Level: HIGH Description: PowerISO 7.8 Retail YGG Torrent Edition Exit code: 1 Version: 7.8.0.0 Modules
| |||||||||||||||
| 3656 | "C:\Program Files\PowerISO\PWRISOVM.EXE" 999 | C:\Program Files\PowerISO\PWRISOVM.EXE | — | Setup_32bit.exe | |||||||||||
User: admin Company: Power Software Ltd Integrity Level: HIGH Description: PowerISO Virtual Drive Manager Exit code: 0 Version: 7, 8, 0, 0 Modules
| |||||||||||||||
Total events
1 276
Read events
1 133
Write events
132
Delete events
11
Modification events
| (PID) Process: | (3056) PowerISO 7.8 Retail YGG Torrent Edition.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: F00B00003C0E605B5AB8D601 | |||
| (PID) Process: | (3056) PowerISO 7.8 Retail YGG Torrent Edition.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: A7DFB7597E53BFA8A0F671128C34F1F0749BA4BF15E55ECADFFF25965A27422E | |||
| (PID) Process: | (3056) PowerISO 7.8 Retail YGG Torrent Edition.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (4060) REG.exe | Key: | HKEY_CURRENT_USER\Software\PowerISO |
| Operation: | write | Name: | USER |
Value: 00204164616D202D2059474720546F7272656E7420536F667477617265205465616D08458375D5A1E5784D972CB450FF926D | |||
| (PID) Process: | (4064) REG.exe | Key: | HKEY_CURRENT_USER\Software\PowerISO\SCDEmu |
| Operation: | write | Name: | ShowMacFiles |
Value: 1 | |||
| (PID) Process: | (3048) Setup_32bit.exe | Key: | HKEY_CURRENT_USER\Software\PowerISO |
| Operation: | write | Name: | TbInstallFlag |
Value: 0 | |||
| (PID) Process: | (3048) Setup_32bit.exe | Key: | HKEY_CURRENT_USER\Software\PowerISO |
| Operation: | write | Name: | TbInstallFlag2 |
Value: 0 | |||
| (PID) Process: | (3056) PowerISO 7.8 Retail YGG Torrent Edition.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3056) PowerISO 7.8 Retail YGG Torrent Edition.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: A7DFB7597E53BFA8A0F671128C34F1F0749BA4BF15E55ECADFFF25965A27422E | |||
| (PID) Process: | (3056) PowerISO 7.8 Retail YGG Torrent Edition.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: F00B00003C0E605B5AB8D601 | |||
Executable files
18
Suspicious files
54
Text files
14
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3588 | PowerISO 7.8 Retail YGG Torrent Edition.exe | C:\Users\admin\AppData\Local\Temp\is-JOL8S.tmp\PowerISO 7.8 Retail YGG Torrent Edition.tmp | executable | |
MD5:— | SHA256:— | |||
| 3056 | PowerISO 7.8 Retail YGG Torrent Edition.tmp | C:\Users\admin\AppData\Local\Temp\is-KOPH4.tmp\Setup_32bit.exe | executable | |
MD5:— | SHA256:— | |||
| 3056 | PowerISO 7.8 Retail YGG Torrent Edition.tmp | C:\Users\admin\AppData\Local\Temp\is-KOPH4.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 3048 | Setup_32bit.exe | C:\Users\admin\AppData\Local\Temp\nsbBCD3.tmp\System.dll | executable | |
MD5:BF712F32249029466FA86756F5546950 | SHA256:7851CB12FA4131F1FEE5DE390D650EF65CAC561279F1CFE70AD16CC9780210AF | |||
| 3048 | Setup_32bit.exe | C:\Windows\system32\Drivers\scdemu.sys | executable | |
MD5:4B5579223186E2E1AB4A24B608FDC949 | SHA256:C7B58DA9FD4CF2F7F83F92B2E98437A2420150FEC6E58C2BD84C82EDD2DA9A8E | |||
| 3048 | Setup_32bit.exe | C:\Users\admin\AppData\Local\Temp\nsbBCD3.tmp\modern-header.bmp | image | |
MD5:CA2542B0E66E48D7E3F361C8EEF8F720 | SHA256:4566DFCC153CBA168A02EEBC5DDD9D82832CF463EBB8ECB4EC2F269F9F85AECA | |||
| 3048 | Setup_32bit.exe | C:\Program Files\PowerISO\Lang\TradChinese.lng | binary | |
MD5:57DDE34D0215101B1459AF7D8076B500 | SHA256:40E9EF832CC3D7E5899C682E84F68FFA9193436DCBB39C88DBE1ED69D82E2EC7 | |||
| 3048 | Setup_32bit.exe | C:\Program Files\PowerISO\Lang\Italian.lng | binary | |
MD5:8631EFF21284A2CB15F474C627B7E493 | SHA256:AA83880D08DC13BF23D65A90F2B34AE2E8B986914D24FB37D92A2100E53A6329 | |||
| 3048 | Setup_32bit.exe | C:\Program Files\PowerISO\Lang\SimpChinese.lng | binary | |
MD5:46E2AA928AF71A2870821A3CF7A824D1 | SHA256:3ABE87BBA97C1E44A98D4A3D125BF59753BD10802C10E124726BB5D40E9F1A05 | |||
| 3048 | Setup_32bit.exe | C:\Program Files\PowerISO\Lang\french.lng | binary | |
MD5:B54014D183D41514BAA1F76A61162CDC | SHA256:076A4631261E4A686DEB3890E4AB8A88C713EBDF6A5A49A0B70A6109F9BB5AE7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
17
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2088 | iexplore.exe | GET | — | 50.62.134.113:80 | http://www.poweriso.com/images/thank-you-bg1.gif | US | — | — | suspicious |
2088 | iexplore.exe | GET | — | 50.62.134.113:80 | http://www.poweriso.com/images/thank-you-bg.gif | US | — | — | suspicious |
2088 | iexplore.exe | GET | 200 | 50.62.134.113:80 | http://www.poweriso.com/thankyou.php | US | html | 4.56 Kb | suspicious |
3144 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3144 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3144 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2088 | iexplore.exe | GET | 200 | 50.62.134.113:80 | http://www.poweriso.com/images/thank-you-logo.gif | US | image | 20.2 Kb | suspicious |
2088 | iexplore.exe | GET | 200 | 50.62.134.113:80 | http://www.poweriso.com/images/check.gif | US | image | 1.02 Kb | suspicious |
2088 | iexplore.exe | GET | 200 | 50.62.134.113:80 | http://www.poweriso.com/images/thank-you-bg1.gif | US | image | 1.03 Kb | suspicious |
2088 | iexplore.exe | GET | 200 | 50.62.134.113:80 | http://www.poweriso.com/favicon.ico | US | image | 8.85 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3144 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2088 | iexplore.exe | 50.62.134.113:80 | www.poweriso.com | GoDaddy.com, LLC | US | suspicious |
2088 | iexplore.exe | 216.58.205.238:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
3144 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3144 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.poweriso.com |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |