| File name: | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f |
| Full analysis: | https://app.any.run/tasks/e8b96eea-e690-4142-91ae-4763ffedbd8b |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 13:05:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 837DDEDF08110C3E37D0E520DBAB21FE |
| SHA1: | 056B23ECBA99D8B470045063EA823F9162F63819 |
| SHA256: | 0B2A852742C7D974FE16A45A7C6FB5EFCF7B03F19E7029F9C43284A2EA5BE84F |
| SSDEEP: | 98304:hqE8vea5NcoZdxX2lmJdrNl4aPyn6sXset7bkOOOIcvCEkBb4c1NcwB/axwX5WpN:6Ms4wTrtg |
MALICIOUS
XORed URL has been found (YARA)
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
SUSPICIOUS
Executable content was dropped or overwritten
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Reads security settings of Internet Explorer
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
There is functionality for capture public ip (YARA)
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Potential Corporate Privacy Violation
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Reads Microsoft Outlook installation path
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
There is functionality for taking screenshot (YARA)
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Reads Internet Explorer settings
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
There is functionality for sending ICMP (YARA)
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
INFO
The sample compiled with chinese language support
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
The sample compiled with english language support
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Create files in a temporary directory
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Reads the computer name
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
- ielowutil.exe (PID: 7980)
- identity_helper.exe (PID: 5640)
Checks supported languages
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
- identity_helper.exe (PID: 5640)
- ielowutil.exe (PID: 7980)
Checks proxy server information
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
- slui.exe (PID: 7752)
UPX packer has been detected
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Creates files or folders in the user directory
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Reads the software policy settings
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
- slui.exe (PID: 7752)
Aspack has been detected
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Reads the machine GUID from the registry
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Application launched itself
- msedge.exe (PID: 2268)
Reads Environment values
- identity_helper.exe (PID: 5640)
Local mutex for internet shortcut management
- iexplore.exe (PID: 8016)
Manual execution by a user
- msedge.exe (PID: 7872)
Process checks whether UAC notifications are on
- Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe (PID: 7328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(7328) Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe
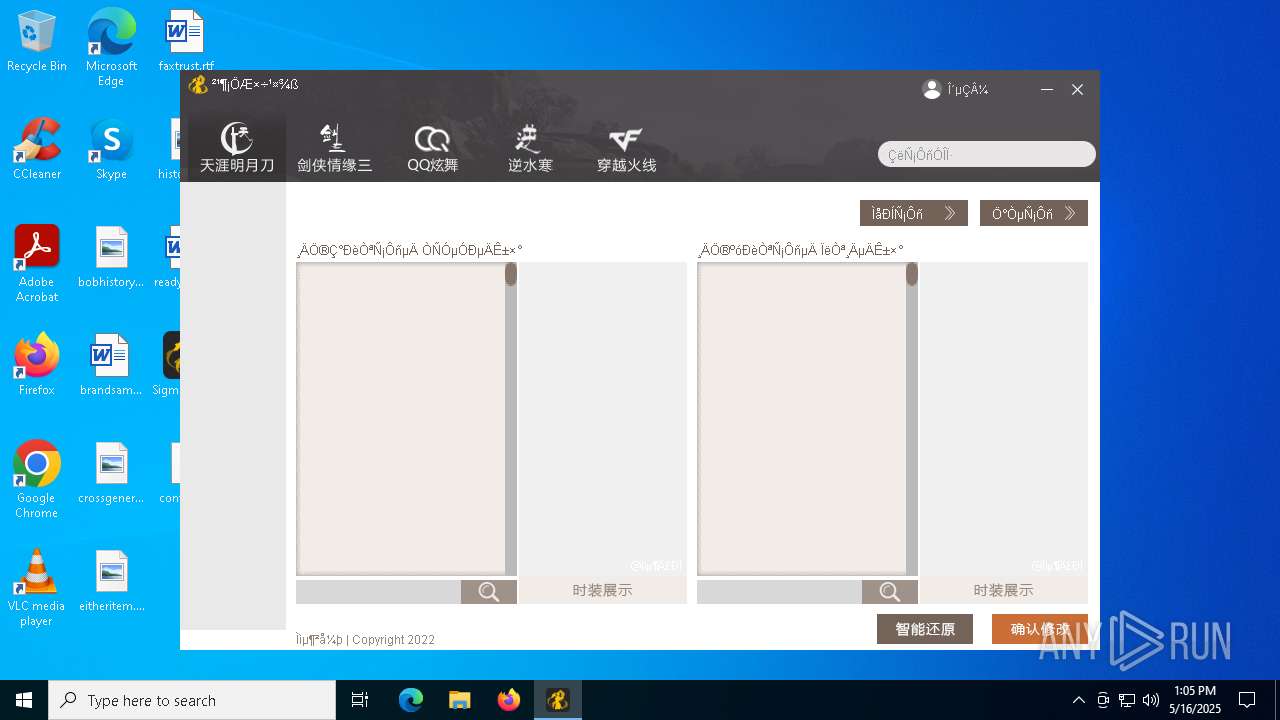
Decrypted-URLs (3)https://xui.ptlogin2.qq.com/cgi-bin/xlogin?appid=715030901&daid=73&pt_no_auth=1&s_url=https%3A%2F%2Fqun.qq.com%2F
https://xui.ptlogin2.qq.com/cgi-bin/xlogin?appid=715030901&daid=73&pt_no_auth=1&s_url=https%3A%2F%2Fqun.qq.com%2F-------M
https://xui.ptlogin2.qq.com/cgi-bin/xlogin?appid=715030901&daid=73&pt_no_auth=1&s_url=https%3A%2F%2Fqun.qq.com%2FNLYDBC
Decrypted-URLs (1)https://qun.qq.com/member.html#gid=.
Decrypted-URLs (2)https://qun.qq.com/.
https://qun.qq.com/member.html#gid=.
Decrypted-URLs (1)https://qun.qq.com/.
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1972:12:25 05:33:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5.6 |
| CodeSize: | 712704 |
| InitializedDataSize: | 20480 |
| UninitializedDataSize: | 999424 |
| EntryPoint: | 0x1a28a0 |
| OSVersion: | 4 |
| ImageVersion: | 3 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 3.0.0.0 |
| FileDescription: | Models |
| ProductName: | TD |
| ProductVersion: | 3.0.0.0 |
| LegalCopyright: | 作者版权所有 请尊重并使用正版 |
| Comments: | BY:流星插件 |
Total processes
173
Monitored processes
43
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4916 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 780 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6276 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3236 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3508 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2144 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1324 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6500 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2ac,0x2b0,0x2b4,0x2a4,0x2bc,0x7ffc890c5fd8,0x7ffc890c5fe4,0x7ffc890c5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4200 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2084 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5692 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2100 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6940 --field-trial-handle=2492,i,5468450195599093999,14724996512542443054,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
23 059
Read events
22 964
Write events
89
Delete events
6
Modification events
| (PID) Process: | (7328) Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7328) Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7328) Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7328) Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | |||
| (PID) Process: | (7328) Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | ID |
Value: 94109603 | |||
| (PID) Process: | (7328) Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\WindowsSearch |
| Operation: | write | Name: | Version |
Value: WS not running | |||
| (PID) Process: | (7328) Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (8016) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8016) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8016) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
25
Suspicious files
89
Text files
50
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\Desktop\config.pck | — | |
MD5:— | SHA256:— | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\dp1.fne | executable | |
MD5:07201B1FD5F8925DD49A4556AC3B5BAB | SHA256:ABEBBB0981D3D51EB63ABCFA68BE98DA0CAE4E6E3B143DD431FC845D1457DBD2 | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\krnln.fnr | executable | |
MD5:F0E18DAB16CC67F81EC762ABB9A63585 | SHA256:B1EB520FF83D6403E04FB8DDB253E76C10B800AF49629D8974D44B330D377DA6 | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\iext.fnr | executable | |
MD5:856495A1605BFC7F62086D482B502C6F | SHA256:8C8254CB49F7287B97C7F952C81EDABC9F11F3FA3F02F265E67D5741998CF0BF | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\iext3.fne | executable | |
MD5:D2A9C02ACB735872261D2ABC6AFF7E45 | SHA256:0216A0F6D6D5360AB487E696B26A39EB81A1E2C8CD7F59C054C90AB99A858DAF | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\internet.fne | executable | |
MD5:7B129C5916896C845752F93B9635FC4C | SHA256:ADC45970F4A0EAFD2F372302F64836802380C253096A99CA964677A70A7128F8 | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\spec.fne | executable | |
MD5:BD6EEF5EA9A52A412A8F57490D8BD8E4 | SHA256:0C9E6EB8648F4BF5C585D5344035E91C3249BB9686A302503B4681B7BA828DC0 | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\eAPI.fne | executable | |
MD5:7C1FF88991F5EAFAB82B1BEAEFC33A42 | SHA256:53483523C316AD8C022C2B07A5CABFFF3339BC5CB5E4AC24C3260EEA4F4D9731 | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\iconv.fne | executable | |
MD5:F6A2A92194FC69858FFA9AA1557454DA | SHA256:1B28D05C306B575319C6FB9B08276B2204A7B569D9E540879CE67C8D17640990 | |||
| 7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\shell.fne | executable | |
MD5:98174C8C2995000EFBDA01E1B86A1D4D | SHA256:90284C2EAD0598FAA715CC90C1F53B83B916099C918CE7F816F0B4550FF55AC6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
139
DNS requests
75
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
976 | RUXIMICS.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
976 | RUXIMICS.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | GET | 200 | 47.98.224.91:80 | http://47.98.224.91/chajian.txt | unknown | — | — | malicious |
7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | GET | 200 | 47.98.224.91:80 | http://47.98.224.91/config.zip | unknown | — | — | malicious |
7696 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7696 | SIHClient.exe | GET | 200 | 2.16.168.12:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7696 | SIHClient.exe | GET | 200 | 2.16.168.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7696 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7696 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7696 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
976 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
976 | RUXIMICS.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
xui.ptlogin2.qq.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
qq-web.cdn-go.cn |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 5.0 |
7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 5.0 |
7328 | Sigmanly_0b2a852742c7d974fe16a45a7c6fb5efcf7b03f19e7029f9c43284a2ea5be84f.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host ZIP Request |