| File name: | SocPlug.jnlp |
| Full analysis: | https://app.any.run/tasks/94bbd9b9-bc94-4f63-8170-30e64c94183d |
| Verdict: | Malicious activity |
| Analysis date: | May 08, 2023, 17:47:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, ASCII text |
| MD5: | 76C6599F359BD0FB355FDDD6F0339628 |
| SHA1: | 8EC5D59E838F9E1B377F5330E95B8CF6EE00ACDC |
| SHA256: | 0ADC1DACFA846370CB65587861D45F32C8A0C315FF5FB42E4F729089E09653B6 |
| SSDEEP: | 12:TMHduL0/jbixwAjVhzHXcHZ4wW1Bcgs9UdDbpT9I+:2dk03iWA5hzsHywaXQUhPI+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
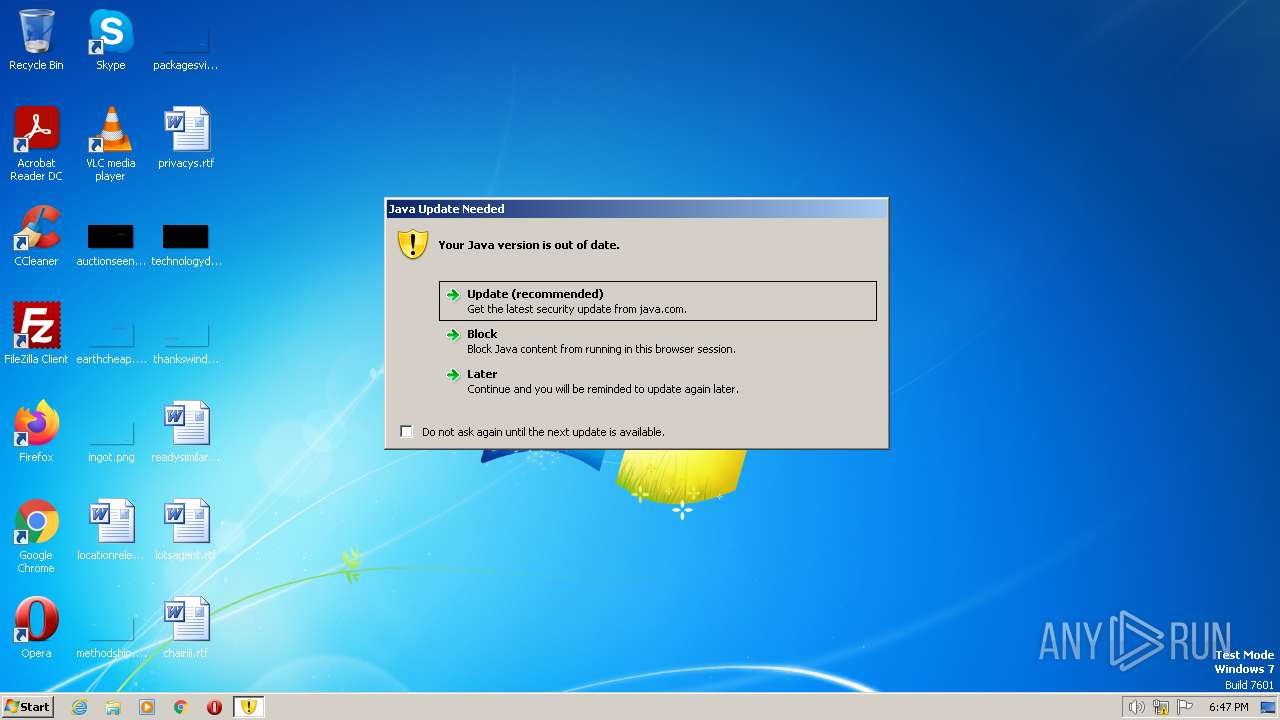
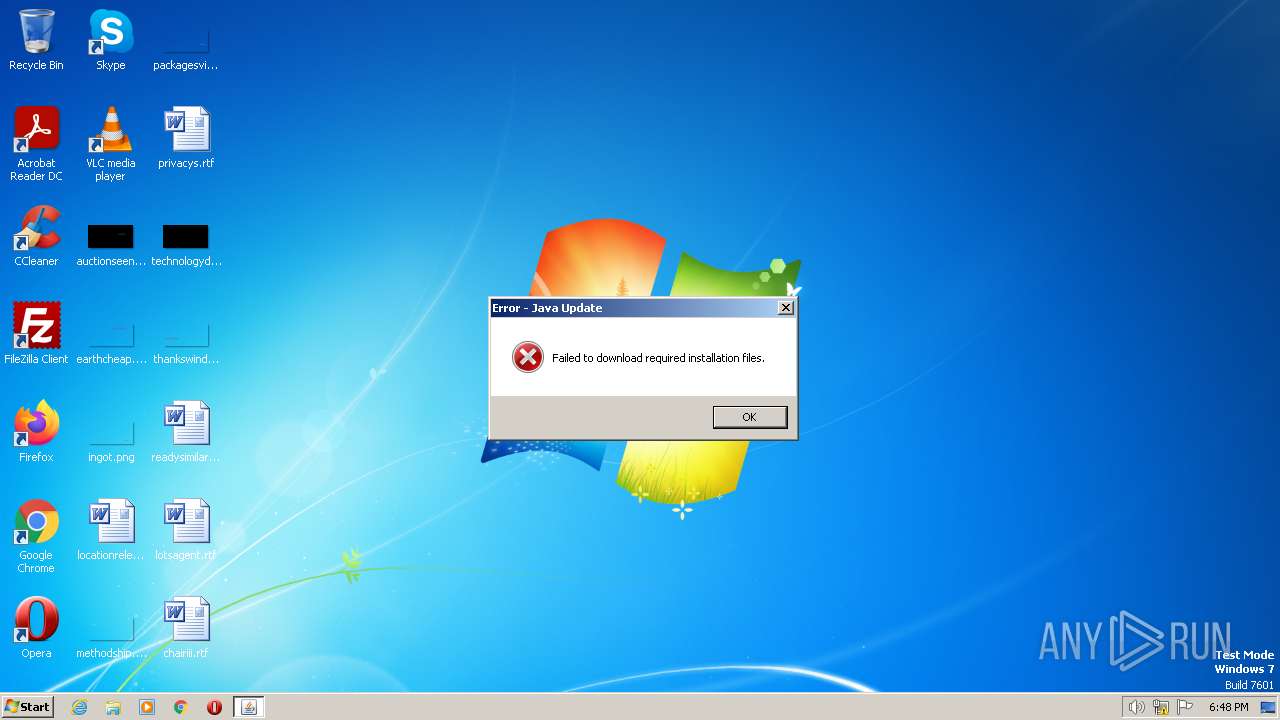
Checks for Java to be installed
- javaws.exe (PID: 3316)
- javaw.exe (PID: 3920)
- javaw.exe (PID: 2284)
- jp2launcher.exe (PID: 3628)
- javaw.exe (PID: 2712)
Reads the Internet Settings
- jp2launcher.exe (PID: 3628)
- jucheck.exe (PID: 3168)
Reads settings of System Certificates
- jp2launcher.exe (PID: 3628)
INFO
Checks supported languages
- javaws.exe (PID: 3316)
- javaw.exe (PID: 3920)
- javaw.exe (PID: 2284)
- javaw.exe (PID: 2712)
- jp2launcher.exe (PID: 3628)
- javaws.exe (PID: 3452)
- jucheck.exe (PID: 3168)
The process checks LSA protection
- icacls.exe (PID: 1788)
- javaw.exe (PID: 3920)
- javaw.exe (PID: 2284)
- javaw.exe (PID: 2712)
- jp2launcher.exe (PID: 3628)
- jucheck.exe (PID: 3168)
Reads the computer name
- javaw.exe (PID: 3920)
- javaw.exe (PID: 2284)
- javaw.exe (PID: 2712)
- jucheck.exe (PID: 3168)
- jp2launcher.exe (PID: 3628)
Create files in a temporary directory
- javaw.exe (PID: 3920)
- javaw.exe (PID: 2284)
- javaw.exe (PID: 2712)
- jucheck.exe (PID: 3168)
- jp2launcher.exe (PID: 3628)
Creates files in the program directory
- javaw.exe (PID: 3920)
Reads the machine GUID from the registry
- jucheck.exe (PID: 3168)
- jp2launcher.exe (PID: 3628)
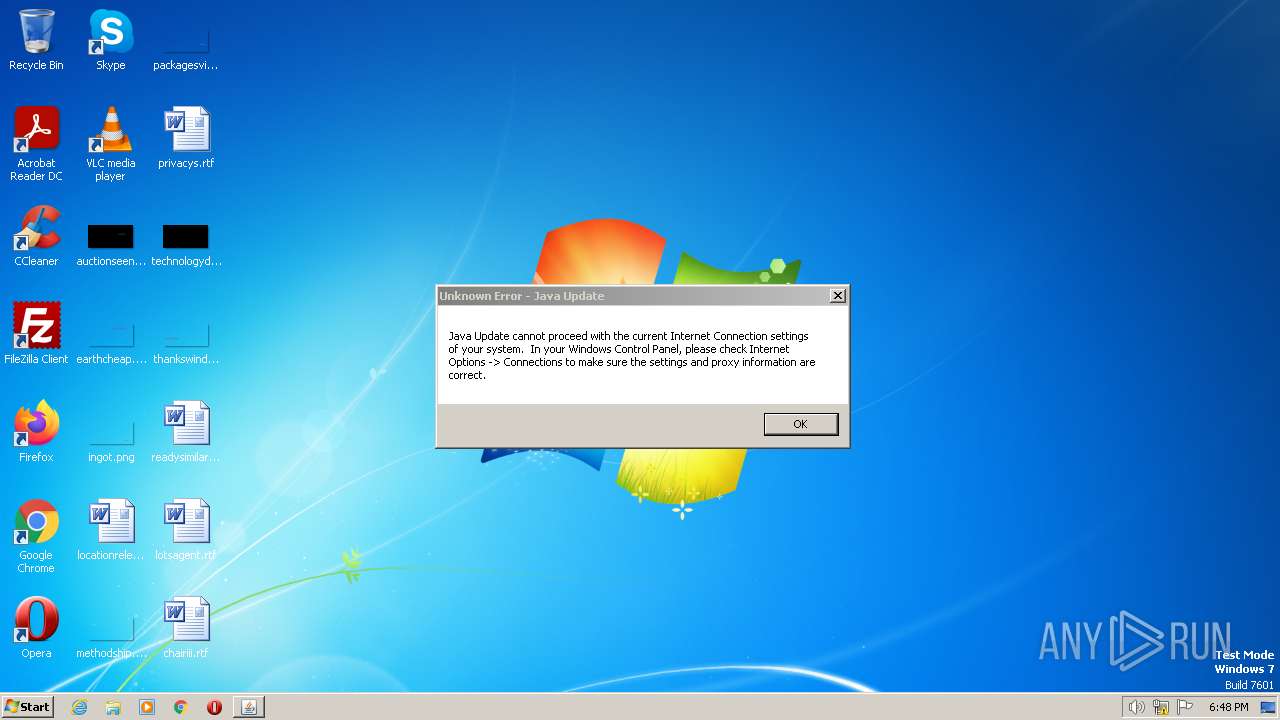
Checks proxy server information
- jucheck.exe (PID: 3168)
- jp2launcher.exe (PID: 3628)
Creates files or folders in the user directory
- jp2launcher.exe (PID: 3628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jnlp | | | Java Web Start application descriptor (88.3) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (11.6) |
EXIF
XMP
| JnlpApplication-descArgument: | install |
|---|---|
| JnlpApplication-descMain-class: | soc.launcher.SocPlugInit |
| JnlpResourcesJarHref: | SocPlug.jar |
| JnlpResourcesJ2seVersion: | 1.7+ |
| JnlpSecurityAll-permissions: | - |
| JnlpUpdatePolicy: | always |
| JnlpUpdateCheck: | always |
| JnlpInformationIconHref: | null |
| JnlpInformationIconKind: | null |
| JnlpInformationDescription: | Age Desenvolvimento de Sistemas Ltda |
| JnlpInformationDescriptionKind: | short |
| JnlpInformationVendor: | Age Technology |
| JnlpInformationTitle: | SocPlug |
| JnlpHref: | SocPlug.jnlp |
| JnlpCodebase: | https://sistema.soc.com.br/estatico/geral/aplicativo/socdesk/ |
| JnlpSpec: | 6.0+ |
Total processes
46
Monitored processes
8
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1788 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.271.2" "1683568075" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2712 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.271.2" "false" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3168 | "C:\Program Files\Common Files\Java\Java Update\jucheck.exe" | C:\Program Files\Common Files\Java\Java Update\jucheck.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Update Checker Exit code: 1 Version: 2.8.271.9 Modules
| |||||||||||||||
| 3316 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" "C:\Users\admin\AppData\Local\Temp\SocPlug.jnlp" | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 1 Version: 11.271.2.09 Modules
| |||||||||||||||
| 3452 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | jucheck.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 3628 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1EamRrLmRpc2FibGVMYXN0VXNhZ2VUcmFja2luZz10cnVlAC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQAtRGpubHB4LnZtYXJncz1MVVJxWkdzdVpHbHpZV0pzWlV4aGMzUlZjMkZuWlZSeVlXTnJhVzVuUFhSeWRXVUE= -ma LVNTVkJhc2VsaW5lVXBkYXRlAC1ub3RXZWJKYXZh | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 3920 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.271.2" "update" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
Total events
10 918
Read events
10 822
Write events
80
Delete events
16
Modification events
| (PID) Process: | (3920) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2284) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2712) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3168) jucheck.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3168) jucheck.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3168) jucheck.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3168) jucheck.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3168) jucheck.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3168) jucheck.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3168) jucheck.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
0
Suspicious files
4
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3168 | jucheck.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:9C7090540C703C08988AC31420E8CDA5 | SHA256:E59CFB709C8F1328ADF68AC39AA2C497B3ED78D3FF2180B94D07D4CF8979A9F8 | |||
| 3628 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\blacklisted.certs | text | |
MD5:8273F70416F494F7FA5B6C70A101E00E | SHA256:583500B76965EB54B03493372989AB4D3426F85462D1DB232C5AE6706A4D6C58 | |||
| 3920 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:818DD870BD446974508E88F88143B0A4 | SHA256:9DEFC0158BE1D3E8EB0AD3CE516B38D96B607C4077AE5D24745526A9B465D2E9 | |||
| 3920 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:BB973B75F39BEF2BCA48838BE41C4FEC | SHA256:AE668D63FCD06A61B4F0E8D6C594CC8F7050BB0F67767AB8D99D96D58566EEE1 | |||
| 3628 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\update.securitypack.timestamp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3628 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\baseline.versions | text | |
MD5:89E848977BE581B9F8B5383509EA57E7 | SHA256:A0938EBB5EBFBEF326BF2EE9370BA24FC0C0A71E0BAF318F359CB192D90BD4E7 | |||
| 3628 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\blacklist.dynamic | text | |
MD5:B2C6EAE6382150192EA3912393747180 | SHA256:6C73C877B36D4ABD086CB691959B180513AC5ABC0C87FE9070D2D5426D3DBF71 | |||
| 3628 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\securitypack.jar | compressed | |
MD5:47933033943E6337137AA28BF027A1A2 | SHA256:3243018F8D3F21EA0699ECCE258DDE161C899FB3D248EB12312EE2D540AB3029 | |||
| 3920 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:7074BF4B0969387559EFFA67A97A2C3B | SHA256:3F51EF221C77A467B4601F200739920E4FD6243B642A6C04836DBEE94084EAC9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
3
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3628 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3628 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | binary | 471 b | whitelisted |
3628 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | binary | 727 b | whitelisted |
3628 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | binary | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3168 | jucheck.exe | 104.103.94.102:443 | javadl-esd-secure.oracle.com | AKAMAI-AS | AT | unknown |
3628 | jp2launcher.exe | 104.103.94.102:443 | javadl-esd-secure.oracle.com | AKAMAI-AS | AT | unknown |
3628 | jp2launcher.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
javadl-esd-secure.oracle.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3628 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3628 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |