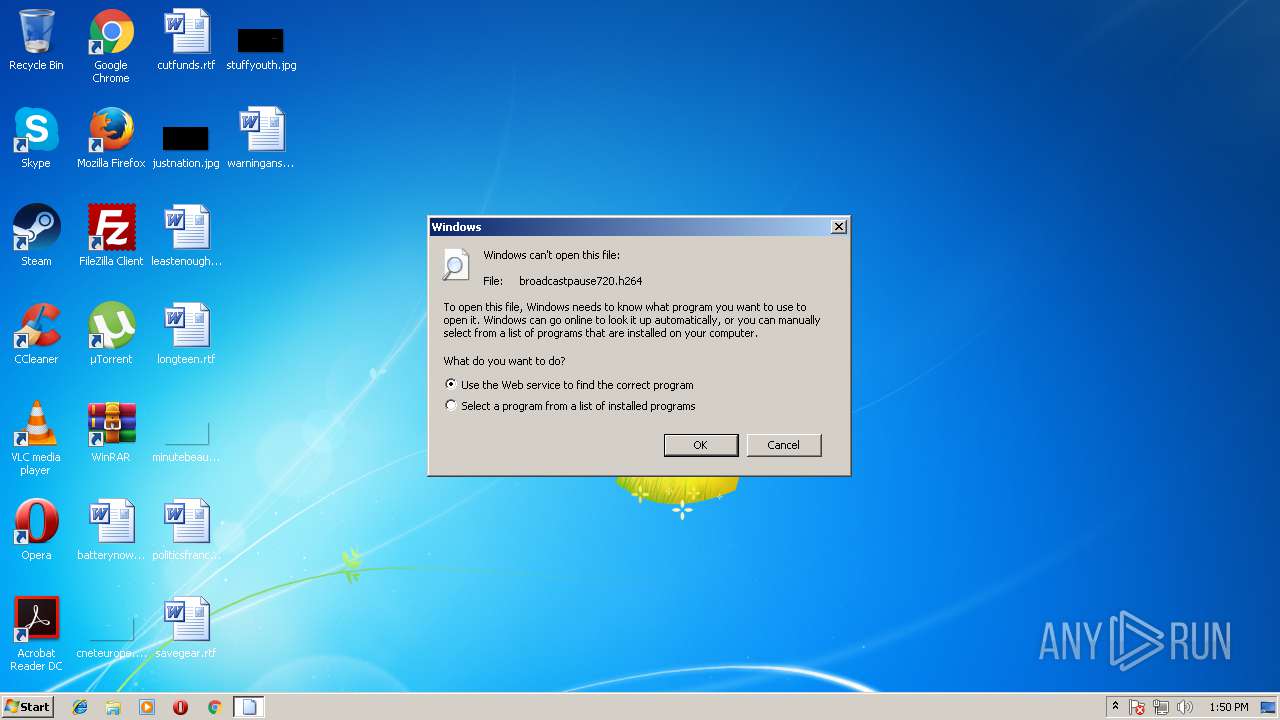
| File name: | broadcastpause720.h264 |
| Full analysis: | https://app.any.run/tasks/27e1c589-da33-4128-9ef0-cc9f684ad337 |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2018, 12:50:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | JVT NAL sequence, H.264 video, main @ L 31 |
| MD5: | 067D0A32B6B1509486339A3E307ABC9B |
| SHA1: | 5A709D13E6967C0A30D3077F4883253FD6BBF194 |
| SHA256: | 0AD4FDA30F59BE8C596757A591EF45CB00EC2F88B522D827E1E100BF4C503AF1 |
| SSDEEP: | 6144:+I42B6W+6MlWnt8+0rKvx+tEfHiIgyn28PoQfdp2:t+6BnqzrKvx+t4HiIhPoyz2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3604)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 2892)
- powershell.exe (PID: 2796)
- powershell.exe (PID: 3312)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3648)
- powershell.exe (PID: 3220)
- powershell.exe (PID: 3532)
- powershell.exe (PID: 2264)
- powershell.exe (PID: 2864)
- powershell.exe (PID: 584)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 2712)
- powershell.exe (PID: 2940)
- powershell.exe (PID: 916)
- powershell.exe (PID: 1436)
- powershell.exe (PID: 3024)
- powershell.exe (PID: 2260)
- powershell.exe (PID: 2732)
- powershell.exe (PID: 2592)
- powershell.exe (PID: 2604)
- powershell.exe (PID: 3712)
- powershell.exe (PID: 2836)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 3756)
- powershell.exe (PID: 3048)
- powershell.exe (PID: 2232)
- powershell.exe (PID: 4080)
- powershell.exe (PID: 3856)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 3528)
- powershell.exe (PID: 3152)
- powershell.exe (PID: 1916)
- powershell.exe (PID: 3784)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 344)
- powershell.exe (PID: 2912)
- powershell.exe (PID: 2036)
- powershell.exe (PID: 3328)
- powershell.exe (PID: 2340)
- powershell.exe (PID: 1988)
Application launched itself
- powershell.exe (PID: 2800)
- powershell.exe (PID: 3604)
- powershell.exe (PID: 2892)
- powershell.exe (PID: 2732)
- powershell.exe (PID: 2592)
- powershell.exe (PID: 3048)
- powershell.exe (PID: 2796)
- powershell.exe (PID: 3312)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3648)
- powershell.exe (PID: 584)
- powershell.exe (PID: 3532)
- powershell.exe (PID: 2264)
- powershell.exe (PID: 2864)
- powershell.exe (PID: 3220)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 2712)
- powershell.exe (PID: 2940)
- powershell.exe (PID: 916)
- powershell.exe (PID: 2260)
- powershell.exe (PID: 1436)
- powershell.exe (PID: 3024)
- powershell.exe (PID: 2836)
- powershell.exe (PID: 2604)
- powershell.exe (PID: 3712)
- powershell.exe (PID: 1988)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3328)
- powershell.exe (PID: 2232)
- powershell.exe (PID: 3756)
- powershell.exe (PID: 4080)
- powershell.exe (PID: 3528)
- powershell.exe (PID: 3856)
- powershell.exe (PID: 3152)
- powershell.exe (PID: 3784)
- powershell.exe (PID: 1916)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 2036)
- powershell.exe (PID: 2912)
- powershell.exe (PID: 344)
Executes PowerShell scripts
- rundll32.exe (PID: 404)
- powershell.exe (PID: 3604)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 2892)
- powershell.exe (PID: 2796)
- powershell.exe (PID: 3312)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3648)
- powershell.exe (PID: 2864)
- powershell.exe (PID: 3220)
- powershell.exe (PID: 3532)
- powershell.exe (PID: 2264)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 2712)
- powershell.exe (PID: 2940)
- powershell.exe (PID: 916)
- powershell.exe (PID: 2260)
- powershell.exe (PID: 1436)
- powershell.exe (PID: 3024)
- powershell.exe (PID: 2732)
- powershell.exe (PID: 2604)
- powershell.exe (PID: 2836)
- powershell.exe (PID: 1988)
- powershell.exe (PID: 3328)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 3712)
- powershell.exe (PID: 2592)
- powershell.exe (PID: 3048)
- powershell.exe (PID: 2232)
- powershell.exe (PID: 3756)
- powershell.exe (PID: 4080)
- powershell.exe (PID: 3856)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 3528)
- powershell.exe (PID: 3152)
- powershell.exe (PID: 3784)
- powershell.exe (PID: 1916)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 344)
- powershell.exe (PID: 2912)
- powershell.exe (PID: 2036)
- powershell.exe (PID: 584)
INFO
Modifies the open verb of a shell class
- rundll32.exe (PID: 404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
121
Monitored processes
45
Malicious processes
42
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 344 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 404 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264 | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1200 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1436 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1568 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1916 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1988 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\broadcastpause720.h264" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
25 936
Read events
23 436
Write events
2 498
Delete events
2
Modification events
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | delete value | Name: | C:\Windows\system32\WFS.exe |
Value: Microsoft Windows Fax and Scan | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | delete value | Name: | C:\Program Files\Skype\Phone\Skype.exe |
Value: Skype | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (404) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
Executable files
0
Suspicious files
86
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3604 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ZHEGBI20BNBQOOOAT1A2.temp | — | |
MD5:— | SHA256:— | |||
| 2800 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\WA86UDRR7UPC1XQ033L0.temp | — | |
MD5:— | SHA256:— | |||
| 2892 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GDKH5KIH3O5KUH4D5BQ4.temp | — | |
MD5:— | SHA256:— | |||
| 2732 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4GE5906GD6OQP0HD39KN.temp | — | |
MD5:— | SHA256:— | |||
| 2592 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SDCEPW9TQOWSF3FD14UP.temp | — | |
MD5:— | SHA256:— | |||
| 3048 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\909J39PA8WPJ775EUQ9I.temp | — | |
MD5:— | SHA256:— | |||
| 2796 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3PNDLUXBLANR5901YR4D.temp | — | |
MD5:— | SHA256:— | |||
| 3312 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\CC9JK32TJB4LE3XW10X5.temp | — | |
MD5:— | SHA256:— | |||
| 1200 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\RNNPPVNIYRPCXP65QCE8.temp | — | |
MD5:— | SHA256:— | |||
| 3692 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UEJDQAEUHCNQBQ2DDQCI.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report