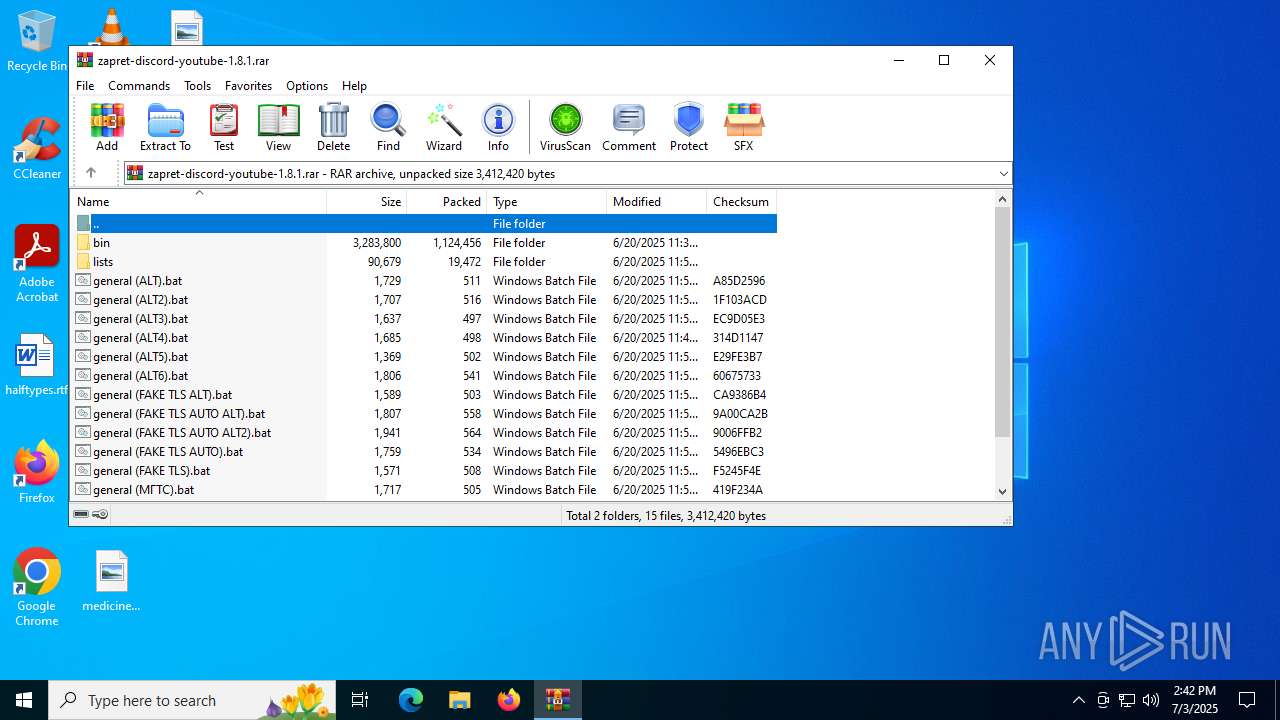
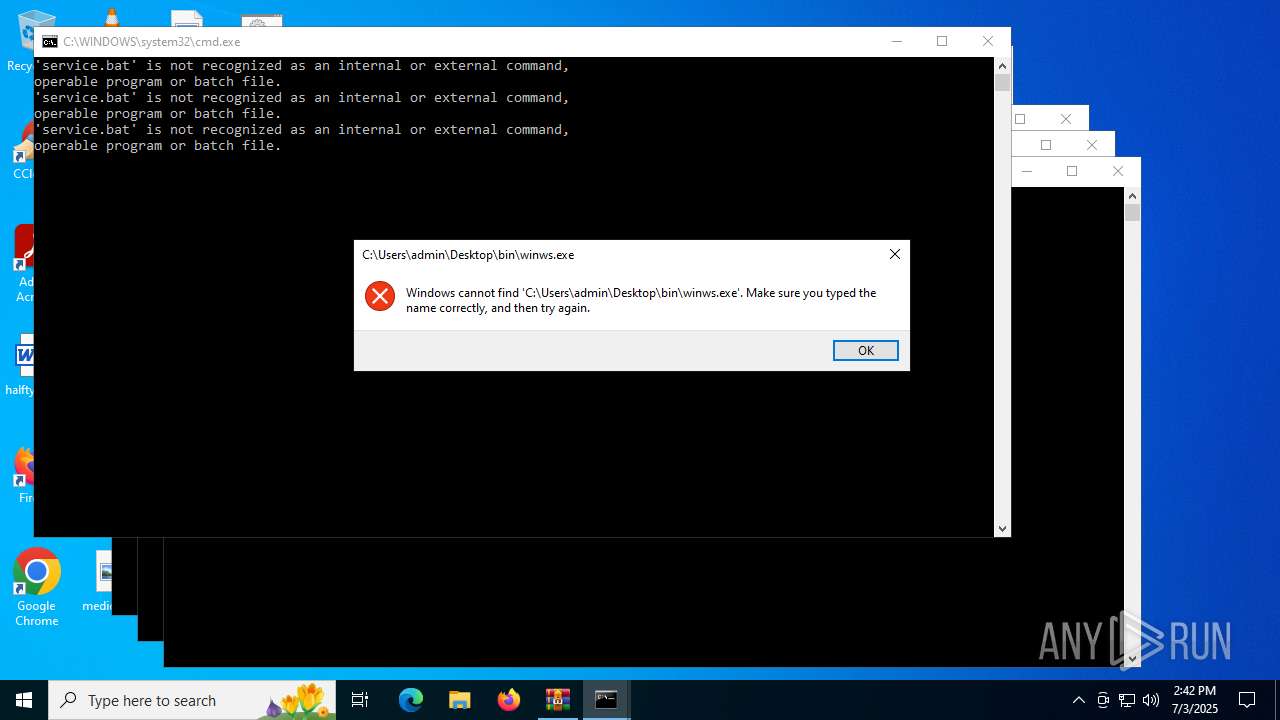
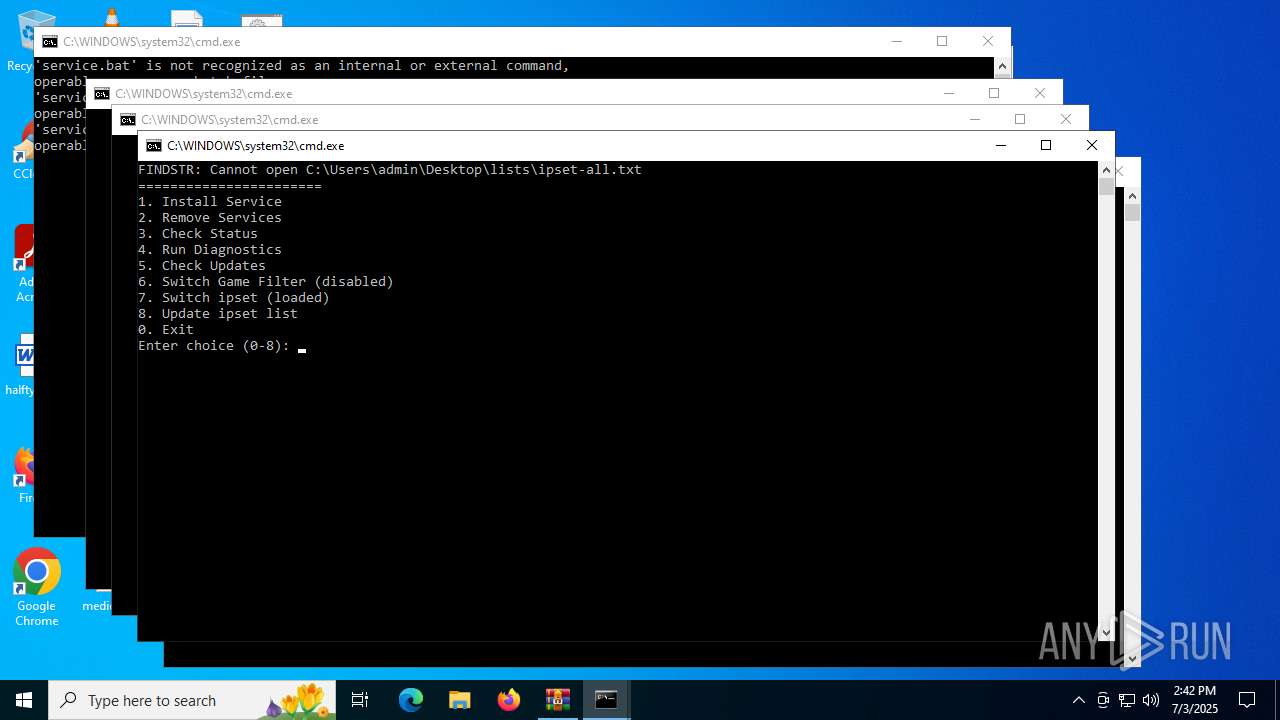
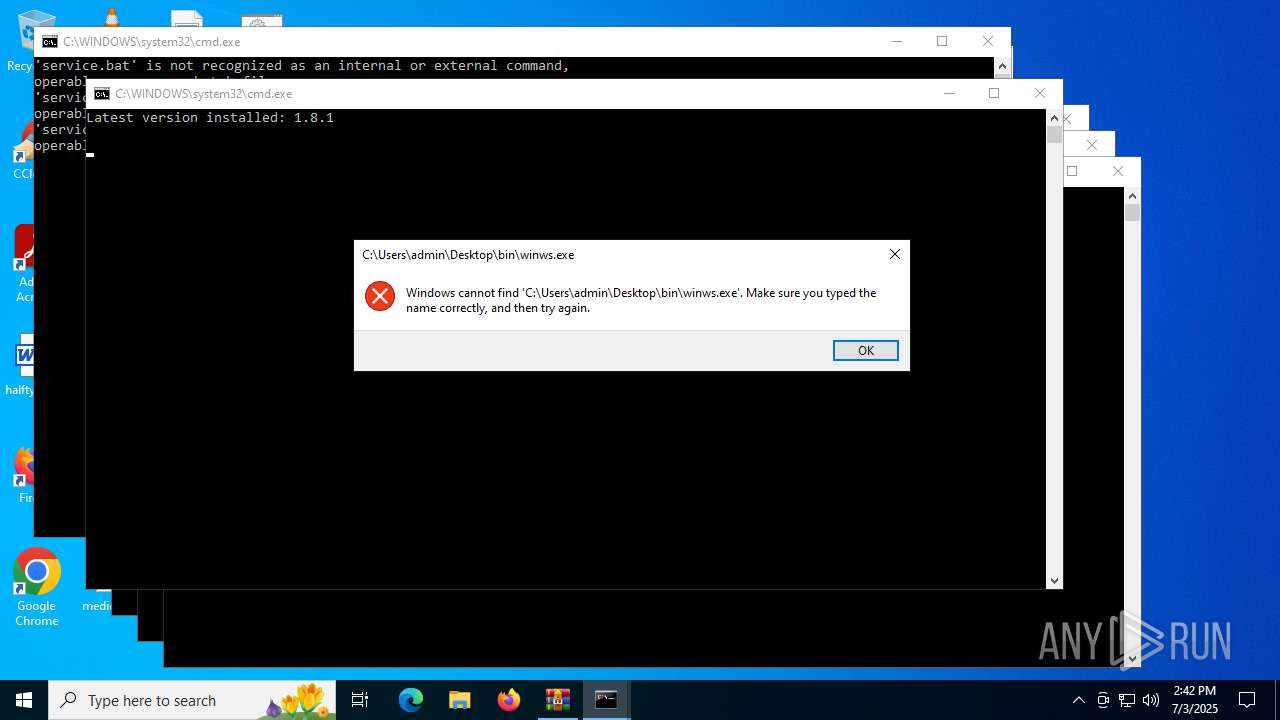
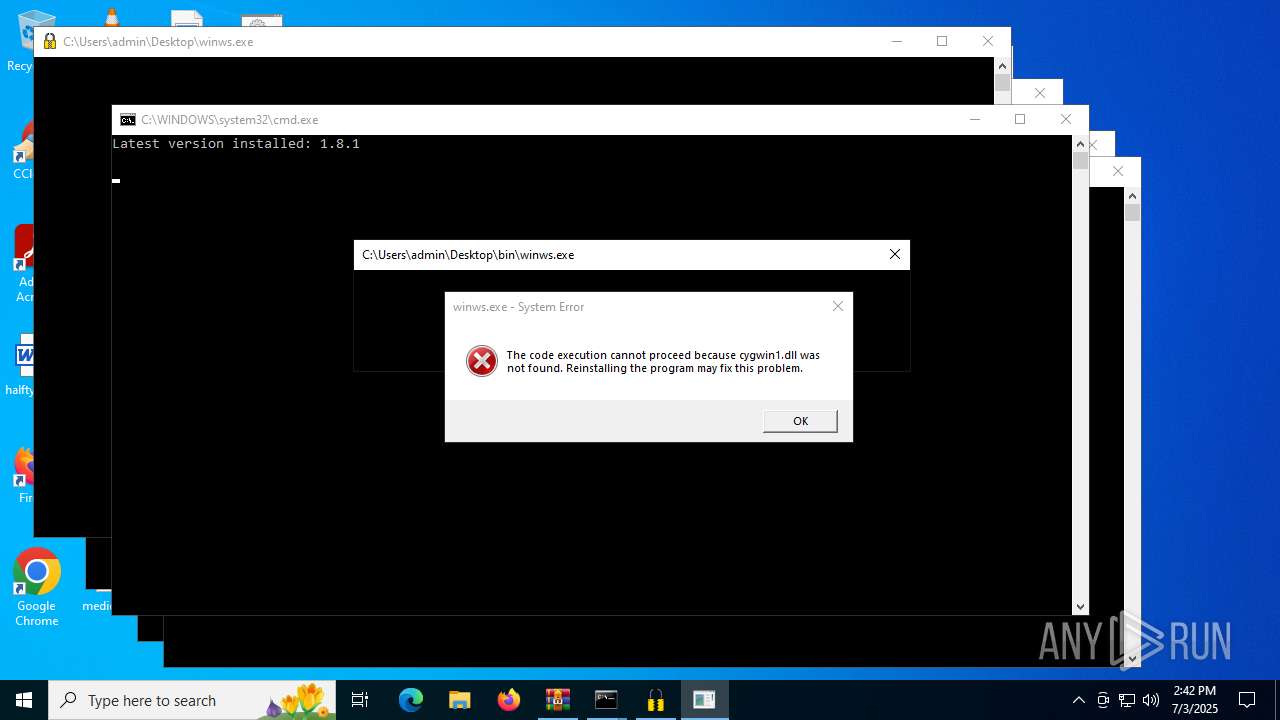
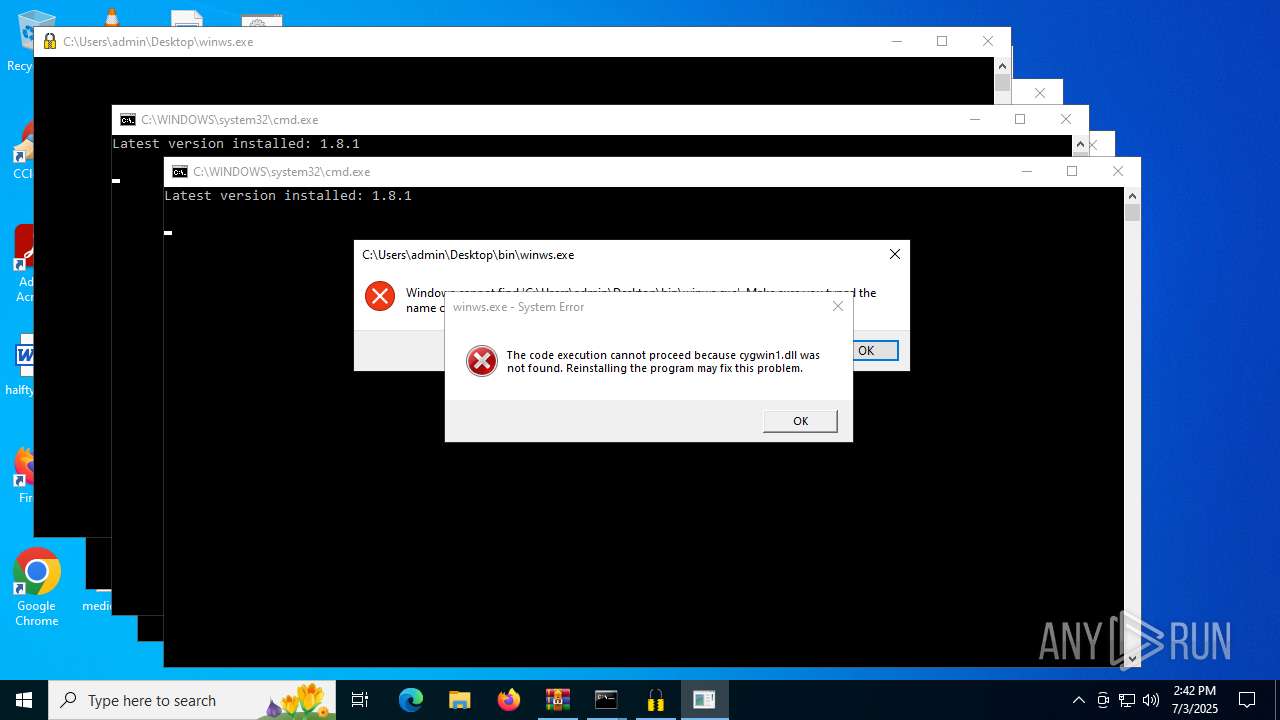
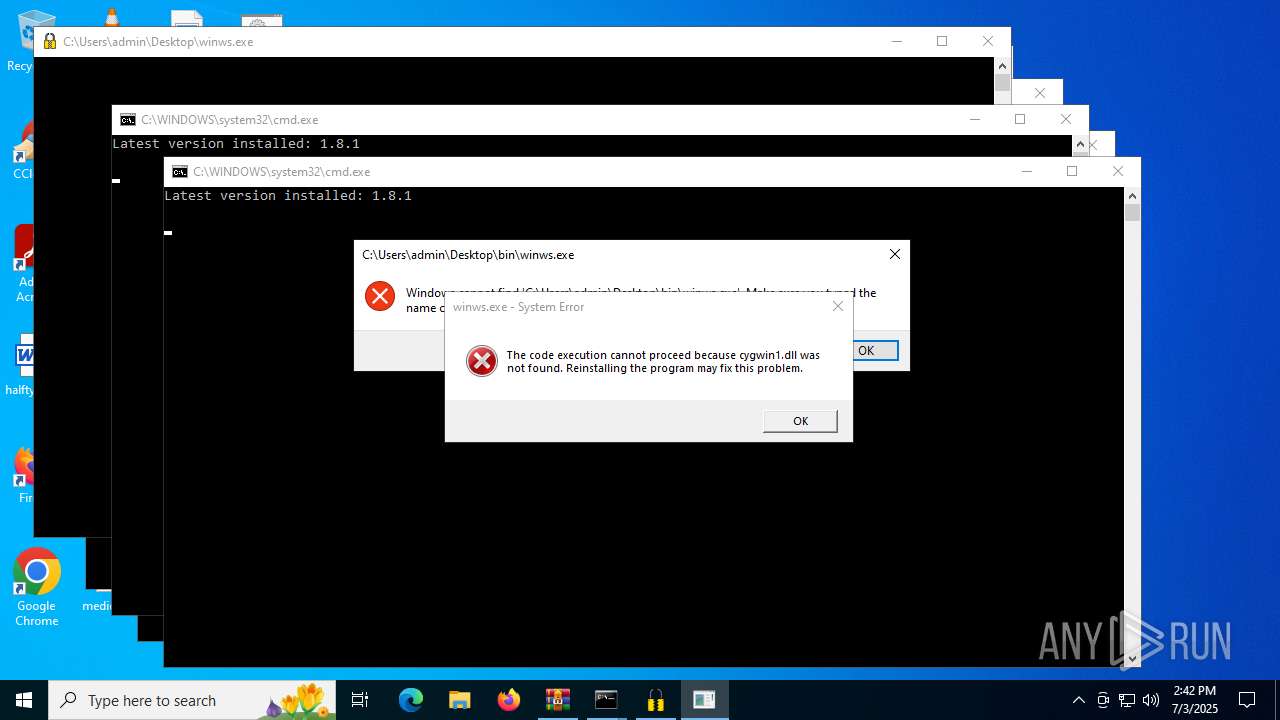
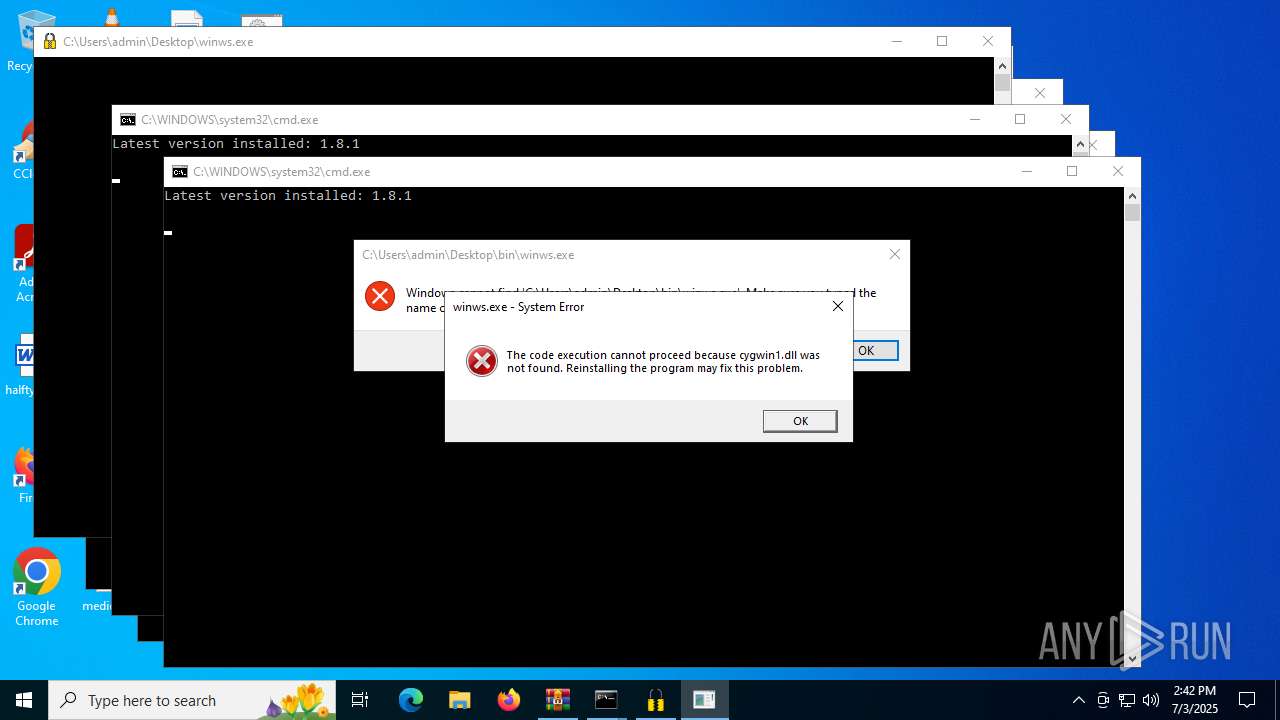
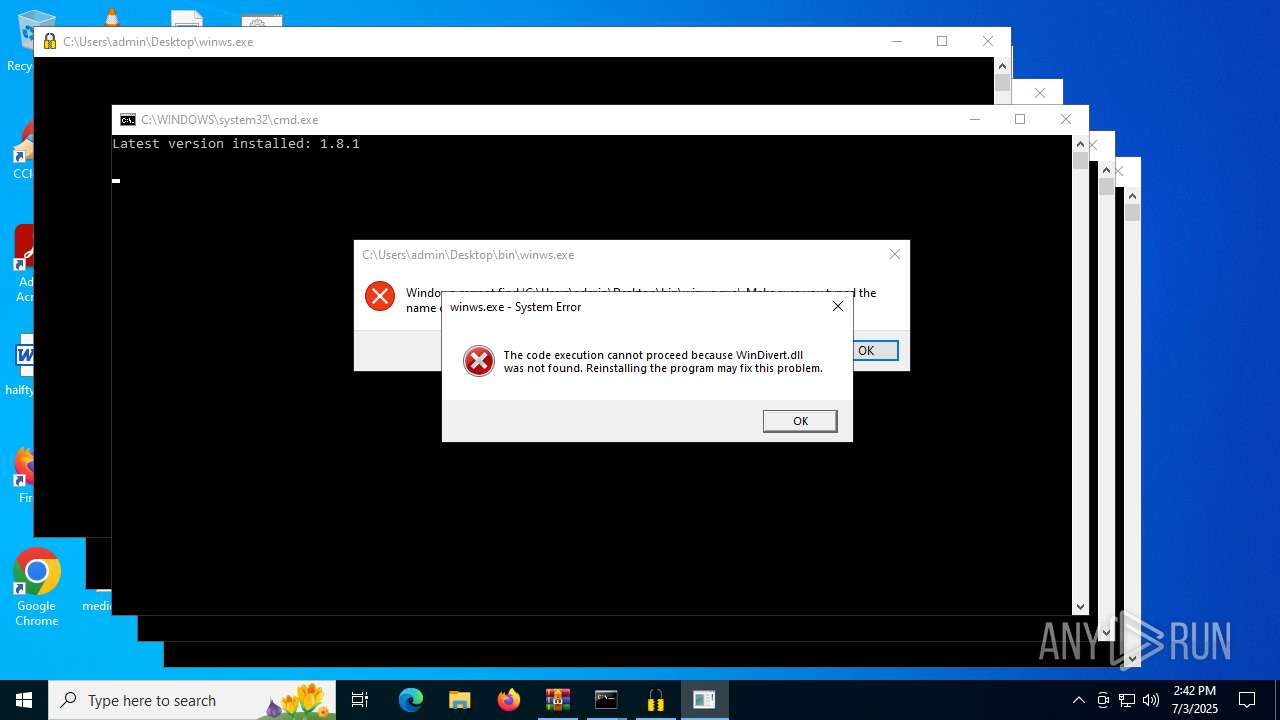
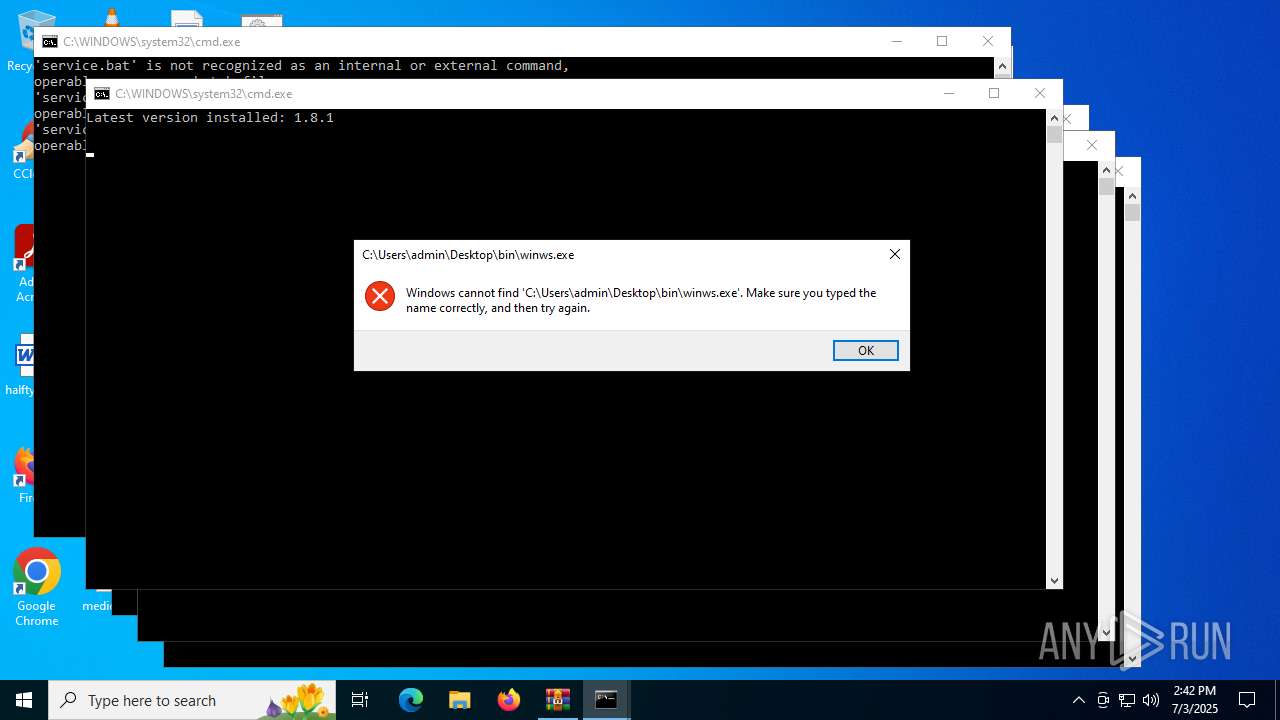
| File name: | zapret-discord-youtube-1.8.1.rar |
| Full analysis: | https://app.any.run/tasks/fa84b163-17cd-43c7-b124-b5bdabd10419 |
| Verdict: | Malicious activity |
| Analysis date: | July 03, 2025, 14:42:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0FD214135C4FC1DB12FABE0D5B26EDBF |
| SHA1: | 976067E7E4458DA55D2FE4620C519AFFC7792C3D |
| SHA256: | 0ABBC5E3105254283C66C72146C382CA27D0EA0FC4A161D4CEACF0CE5ABA69DE |
| SSDEEP: | 49152:Cub4FMyNCQMf5udb/DNj7Ze9rm45sDC69wDe1fwTCFvppsBS9VWIwQtkcTa8ZM19:Cub4utV58b/Jj789rv5D6uDefjFvppru |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5080)
SUSPICIOUS
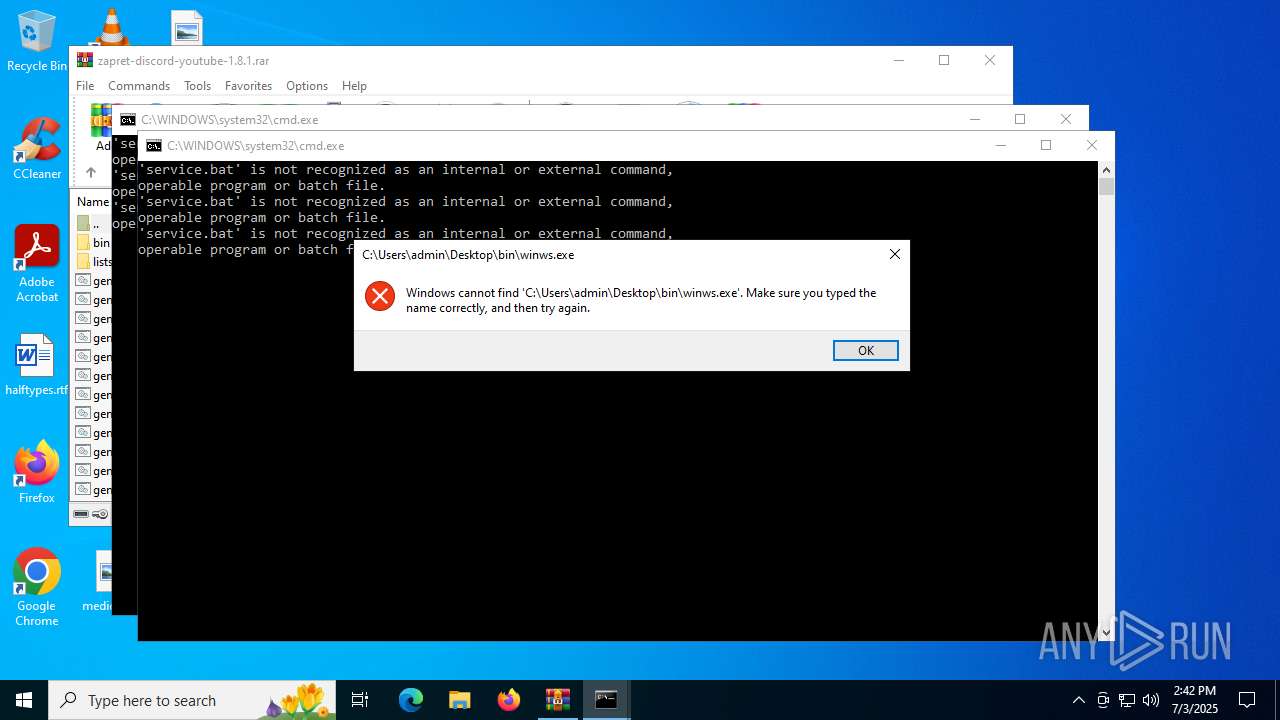
Starts application with an unusual extension
- cmd.exe (PID: 5712)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 4088)
- cmd.exe (PID: 6236)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 320)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4088)
- cmd.exe (PID: 5352)
- powershell.exe (PID: 4804)
- cmd.exe (PID: 320)
Starts SC.EXE for service management
- cmd.exe (PID: 1688)
- cmd.exe (PID: 1480)
- cmd.exe (PID: 6384)
Application launched itself
- cmd.exe (PID: 4088)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 320)
Windows service management via SC.EXE
- sc.exe (PID: 3956)
- sc.exe (PID: 6320)
- sc.exe (PID: 3580)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1688)
- cmd.exe (PID: 1480)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 6384)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6940)
- cmd.exe (PID: 4132)
- cmd.exe (PID: 7152)
- cmd.exe (PID: 1068)
Starts process via Powershell
- powershell.exe (PID: 4804)
Hides command output
- cmd.exe (PID: 1068)
- cmd.exe (PID: 4132)
- cmd.exe (PID: 7152)
Executing commands from a ".bat" file
- powershell.exe (PID: 4804)
INFO
Checks supported languages
- chcp.com (PID: 3588)
- chcp.com (PID: 5060)
- chcp.com (PID: 4820)
- chcp.com (PID: 4932)
- chcp.com (PID: 1164)
- chcp.com (PID: 2080)
- chcp.com (PID: 2596)
- chcp.com (PID: 4844)
- chcp.com (PID: 3572)
- chcp.com (PID: 3672)
- chcp.com (PID: 7060)
- chcp.com (PID: 1180)
- chcp.com (PID: 7060)
- chcp.com (PID: 4100)
- chcp.com (PID: 1204)
Manual execution by a user
- cmd.exe (PID: 5712)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 6236)
- cmd.exe (PID: 4088)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 320)
- winws.exe (PID: 7000)
- winws.exe (PID: 1632)
Changes the display of characters in the console
- cmd.exe (PID: 5712)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 4088)
- cmd.exe (PID: 6236)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 320)
Checks proxy server information
- powershell.exe (PID: 4824)
- slui.exe (PID: 2596)
- powershell.exe (PID: 3908)
- powershell.exe (PID: 4832)
Disables trace logs
- powershell.exe (PID: 3908)
- powershell.exe (PID: 4824)
- powershell.exe (PID: 4832)
Reads the software policy settings
- slui.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 502 |
| UncompressedSize: | 1369 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | general (ALT5).bat |
Total processes
191
Monitored processes
55
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\general (ALT6).bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 756 | findstr /R "^0\.0\.0\.0/32f7f81a39-5f63-5b42-9efd-1f13b5431005quot; "C:\Users\admin\Desktop\lists\ipset-all.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\system32\cmd.exe /c powershell -command "(Invoke-WebRequest -Uri \"https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/main/.service/version.txt\" -Headers @{\"Cache-Control\"=\"no-cache\"} -TimeoutSec 5).Content.Trim()" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | C:\WINDOWS\system32\cmd.exe /c sc query "zapret" | findstr /i "STATE" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1632 | "C:\Users\admin\Desktop\winws.exe" | C:\Users\admin\Desktop\winws.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Modules
| |||||||||||||||
Total events
26 853
Read events
26 842
Write events
11
Delete events
0
Modification events
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\zapret-discord-youtube-1.8.1.rar | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3908 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cdfd125v.dyq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4804 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uo3vajq3.mfy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4824 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_grkaczpj.qgy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4804 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:02E78F543982D8AA650B5FCDE97FDD24 | SHA256:447F368526D9EF9DACC367CF8D7BFA116CF9817FB38F45F7F3F705D57F457F34 | |||
| 4804 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1xvqfnqe.duk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3908 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ou0gbpnv.z3p.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4824 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hzvlhmas.24h.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bfajvzf5.1re.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qkwdebmr.1kh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
44
DNS requests
18
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4916 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4916 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/main/.service/version.txt | unknown | text | 5 b | whitelisted |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/main/.service/version.txt | unknown | text | 5 b | whitelisted |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/main/.service/version.txt | unknown | text | 5 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4916 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4916 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |