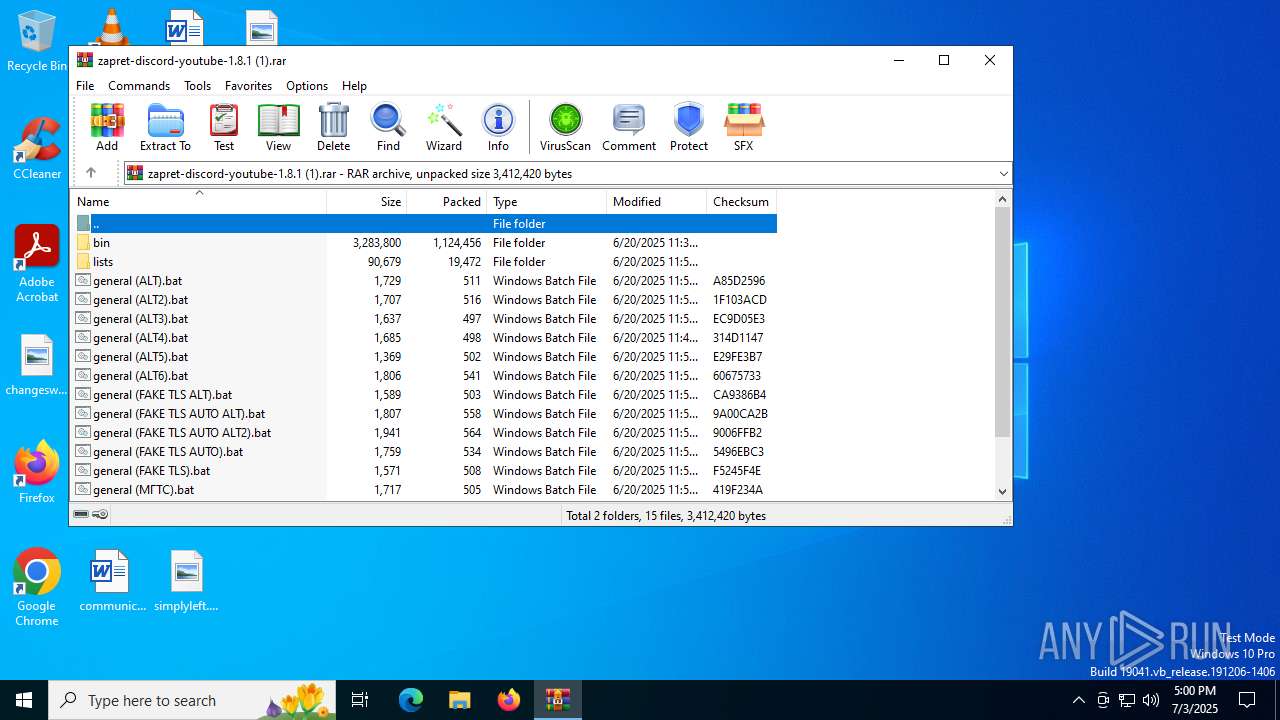
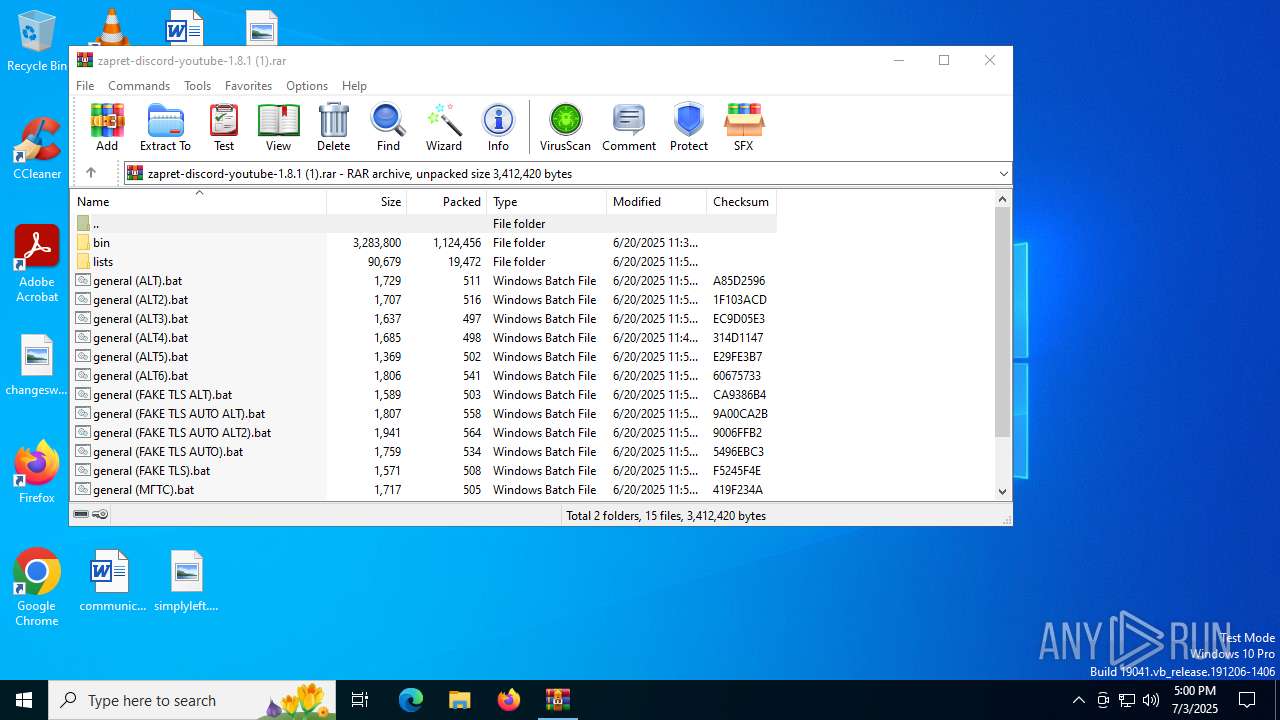
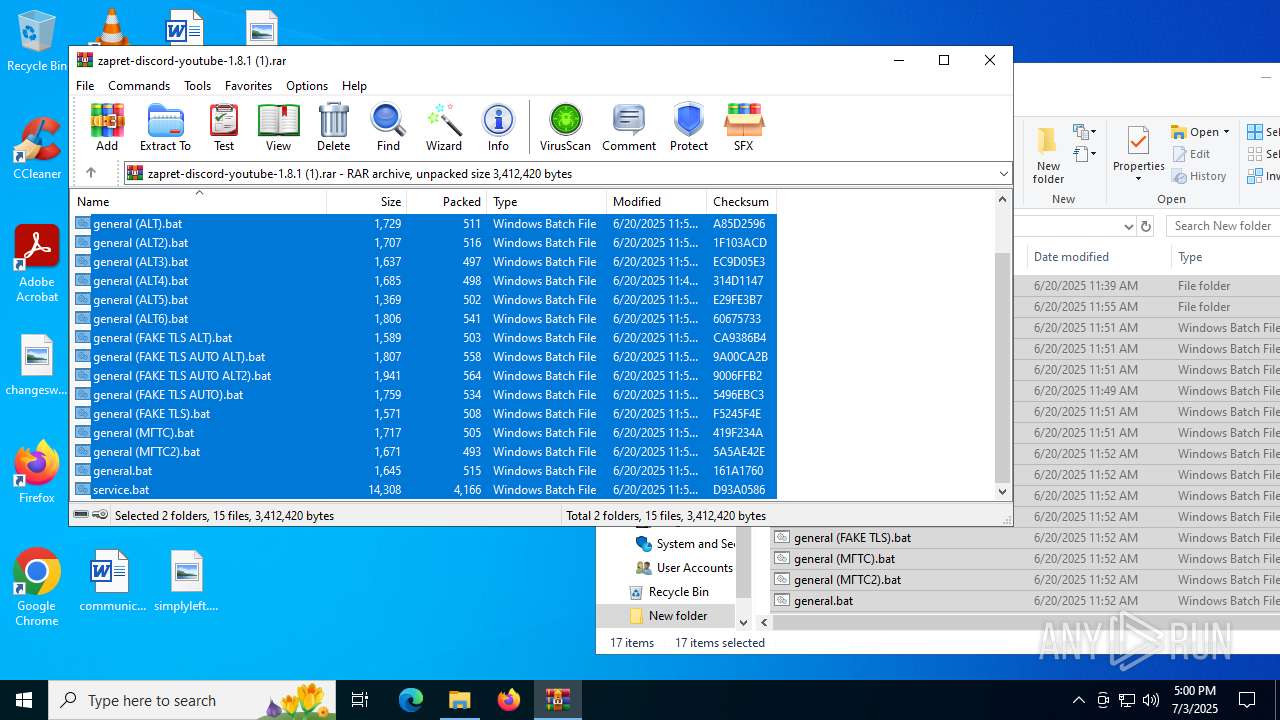
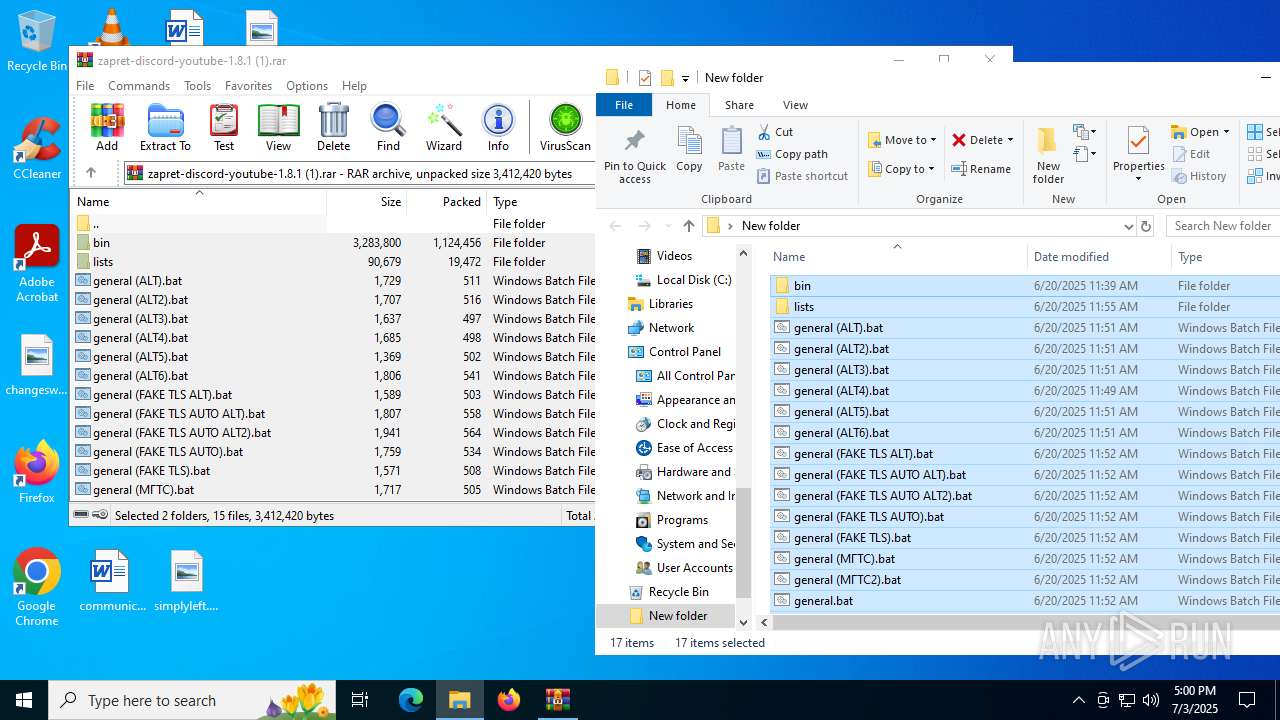
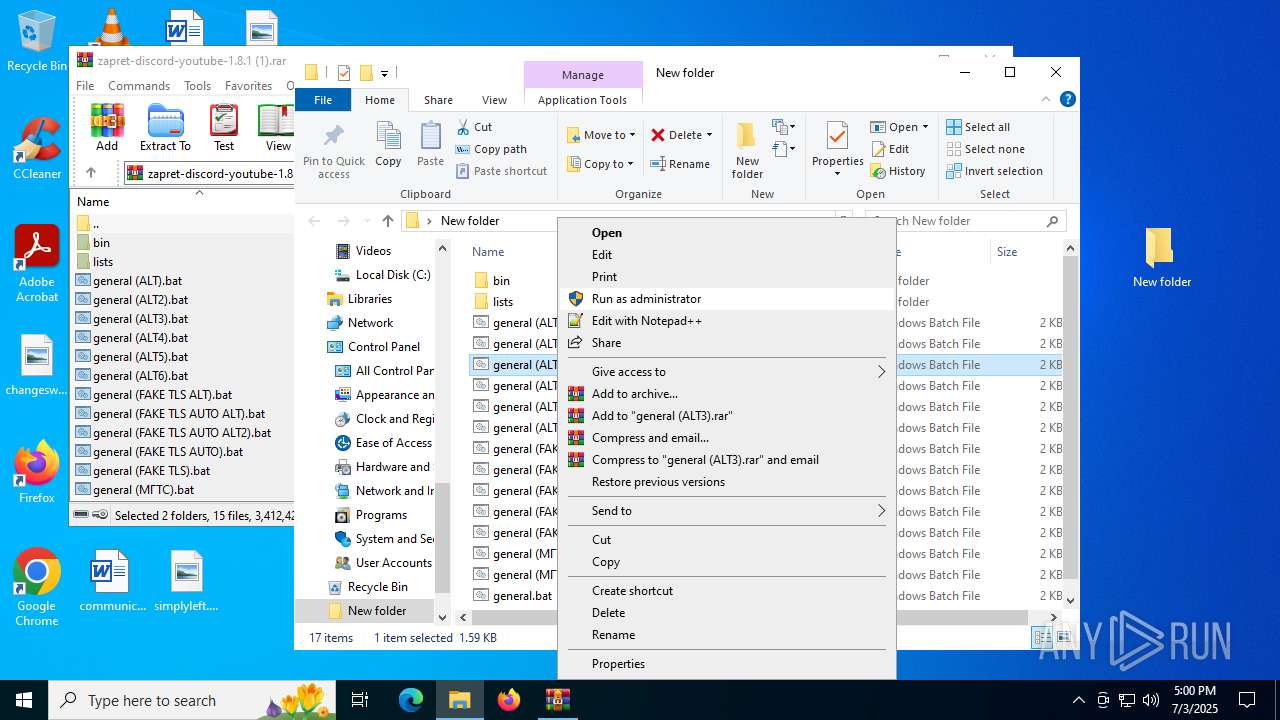
| File name: | zapret-discord-youtube-1.8.1 (1).rar |
| Full analysis: | https://app.any.run/tasks/1dbd6210-bc63-4f96-ab7d-a027ba955f92 |
| Verdict: | Malicious activity |
| Analysis date: | July 03, 2025, 16:59:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0FD214135C4FC1DB12FABE0D5B26EDBF |
| SHA1: | 976067E7E4458DA55D2FE4620C519AFFC7792C3D |
| SHA256: | 0ABBC5E3105254283C66C72146C382CA27D0EA0FC4A161D4CEACF0CE5ABA69DE |
| SSDEEP: | 49152:Cub4FMyNCQMf5udb/DNj7Ze9rm45sDC69wDe1fwTCFvppsBS9VWIwQtkcTa8ZM19:Cub4utV58b/Jj789rv5D6uDefjFvppru |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 2324)
Malicious driver has been detected
- WinRAR.exe (PID: 2324)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 2324)
Starts application with an unusual extension
- cmd.exe (PID: 1232)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1232)
Windows service management via SC.EXE
- sc.exe (PID: 620)
Application launched itself
- cmd.exe (PID: 1232)
Starts SC.EXE for service management
- cmd.exe (PID: 6672)
Hides command output
- cmd.exe (PID: 4664)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4664)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6672)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 2324)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2324)
Checks supported languages
- chcp.com (PID: 3620)
- chcp.com (PID: 4880)
- chcp.com (PID: 2368)
- winws.exe (PID: 592)
Manual execution by a user
- cmd.exe (PID: 1232)
Changes the display of characters in the console
- cmd.exe (PID: 1232)
Disables trace logs
- powershell.exe (PID: 1096)
Checks proxy server information
- powershell.exe (PID: 1096)
- slui.exe (PID: 5928)
Reads the computer name
- winws.exe (PID: 592)
Reads the software policy settings
- slui.exe (PID: 5928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 502 |
| UncompressedSize: | 1369 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | general (ALT5).bat |
Total processes
153
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
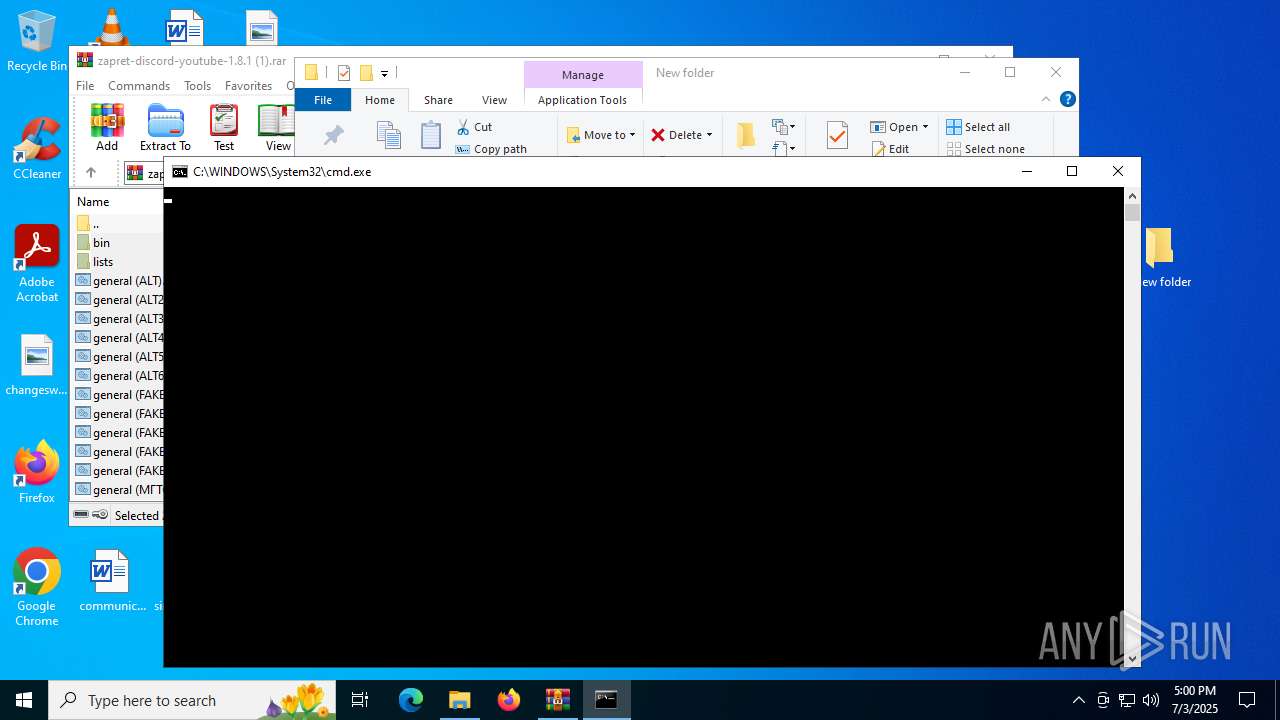
| 592 | "C:\Users\admin\Desktop\New folder\bin\winws.exe" --wf-tcp=80,443,1024-65535 --wf-udp=443,50000-50100,1024-65535 --filter-udp=443 --hostlist="C:\Users\admin\Desktop\New folder\lists\list-general.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Desktop\New folder\bin\quic_initial_www_google_com.bin" --new --filter-udp=50000-50100 --filter-l7=discord,stun --dpi-desync=fake --dpi-desync-repeats=6 --new --filter-tcp=80 --hostlist="C:\Users\admin\Desktop\New folder\lists\list-general.txt" --dpi-desync=fake,split2 --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="C:\Users\admin\Desktop\New folder\lists\list-general.txt" --dpi-desync=split --dpi-desync-split-pos=1 --dpi-desync-autottl --dpi-desync-fooling=badseq --dpi-desync-repeats=8 --new --filter-udp=443 --ipset="C:\Users\admin\Desktop\New folder\lists\ipset-all.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Desktop\New folder\bin\quic_initial_www_google_com.bin" --new --filter-tcp=80 --ipset="C:\Users\admin\Desktop\New folder\lists\ipset-all.txt" --dpi-desync=fake,split2 --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443,1024-65535 --ipset="C:\Users\admin\Desktop\New folder\lists\ipset-all.txt" --dpi-desync=split --dpi-desync-split-pos=1 --dpi-desync-autottl --dpi-desync-fooling=badseq --dpi-desync-repeats=8 --new --filter-udp=1024-65535 --ipset="C:\Users\admin\Desktop\New folder\lists\ipset-all.txt" --dpi-desync=fake --dpi-desync-autottl=2 --dpi-desync-repeats=10 --dpi-desync-any-protocol=1 --dpi-desync-fake-unknown-udp="C:\Users\admin\Desktop\New folder\bin\quic_initial_www_google_com.bin" --dpi-desync-cutoff=n2 | C:\Users\admin\Desktop\New folder\bin\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 620 | sc query "zapret" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | powershell -command "(Invoke-WebRequest -Uri \"https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/main/.service/version.txt\" -Headers @{\"Cache-Control\"=\"no-cache\"} -TimeoutSec 5).Content.Trim()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\New folder\general (ALT3).bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\zapret-discord-youtube-1.8.1 (1).rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2368 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3584 | findstr /i "STATE" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4664 | C:\WINDOWS\system32\cmd.exe /c powershell -command "(Invoke-WebRequest -Uri \"https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/main/.service/version.txt\" -Headers @{\"Cache-Control\"=\"no-cache\"} -TimeoutSec 5).Content.Trim()" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 292
Read events
7 281
Write events
11
Delete events
0
Modification events
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zapret-discord-youtube-1.8.1 (1).rar | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (592) winws.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Cygwin\Installations |
| Operation: | write | Name: | aa5cf26e3c42967f |
Value: \??\C:\Users\admin\Desktop\New folder | |||
| (PID) Process: | (592) winws.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\EventLog\System\WinDivert |
| Operation: | write | Name: | EventMessageFile |
Value: C:\Users\admin\Desktop\New folder\bin\WinDivert64.sys | |||
Executable files
4
Suspicious files
3
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\general (МГТС2).bat | text | |
MD5:EB668BCDF6EA1E4F9FAAC7903592AC1A | SHA256:F4257045772DE124E1AADD1A1F5D89932687092E167E0AA11E68601B69FF3B0C | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\general (FAKE TLS AUTO ALT2).bat | text | |
MD5:45AC03D1ACB3780618AAC893CA8CB6CE | SHA256:6EEC4954278238E0D9E2F9214A55135D95A878E7B69AA67A2BA60945402F59D8 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\bin\WinDivert.dll | executable | |
MD5:B2014D33EE645112D5DC16FE9D9FCBFF | SHA256:C1E060EE19444A259B2162F8AF0F3FE8C4428A1C6F694DCE20DE194AC8D7D9A2 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\bin\WinDivert64.sys | executable | |
MD5:89ED5BE7EA83C01D0DE33D3519944AA5 | SHA256:8DA085332782708D8767BCACE5327A6EC7283C17CFB85E40B03CD2323A90DDC2 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\general (МГТС).bat | text | |
MD5:55587CC2B5BB80157313B17BC9EA2B15 | SHA256:F242DB5DCB2C05E85F56A3366630398E0A6E1BED4728D8B274EC6E9117DDD2BC | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\service.bat | text | |
MD5:394E89F053A1D373716EA28E0E78C4CC | SHA256:3B36D4EAF8014D829FB070D1FC2153F76BE77D38BE9A5247DA05385EE9798928 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\bin\quic_initial_www_google_com.bin | binary | |
MD5:312526D39958D89B1F8AB67789AB985F | SHA256:F4589C57749F956BB30538197A521D7005F8B0A8723B4707E72405E51DDAC50A | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\lists\ipset-all.txt | text | |
MD5:03272DCF3432AF2766F86D7B580B33B8 | SHA256:3D76047EEC095AD283C0A81E4651D76939BDF842FE75FD9BD2D9ADB274EFCAE4 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\bin\cygwin1.dll | executable | |
MD5:A1C82ED072DC079DD7851F82D9AA7678 | SHA256:103104A52E5293CE418944725DF19E2BF81AD9269B9A120D71D39028E821499B | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.32338\bin\winws.exe | executable | |
MD5:2008323884A0101D616142447D19F820 | SHA256:8DC19655C2940A64D9FAE717E7942CF11EEB39AF9DEA695DB31C335DF762A18E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
26
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4580 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7060 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7060 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6256 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4580 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4580 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |