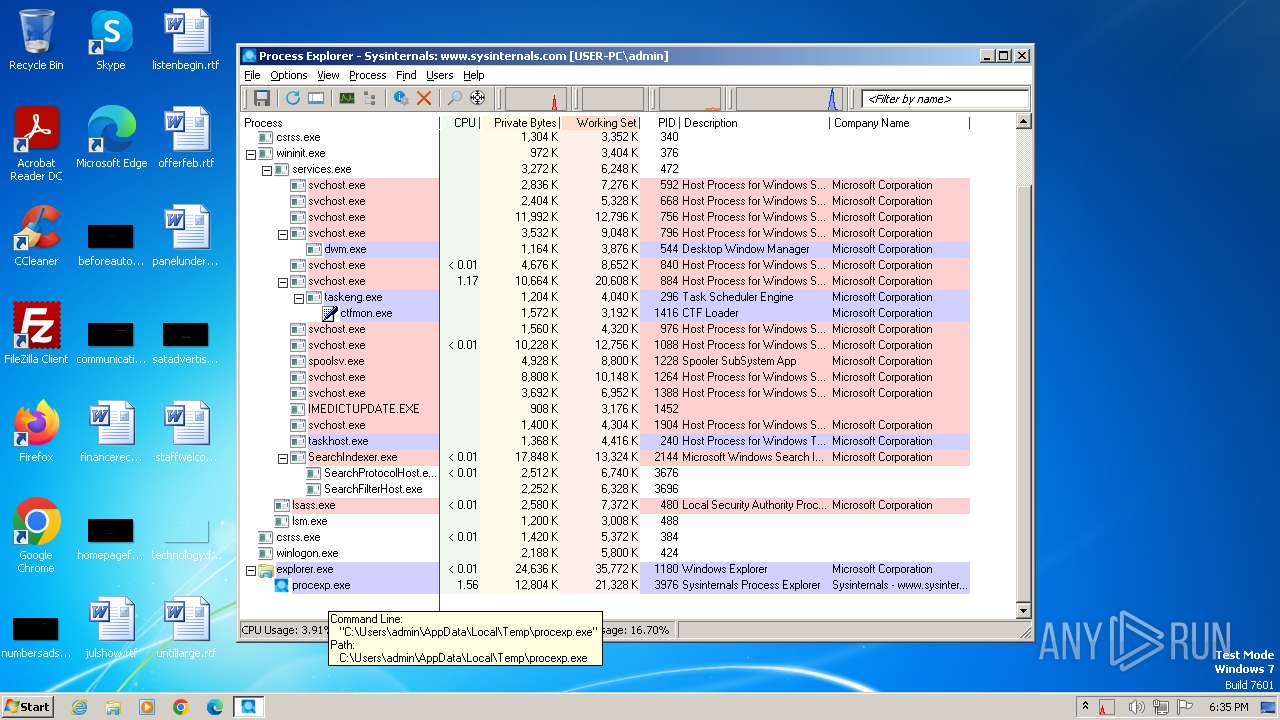
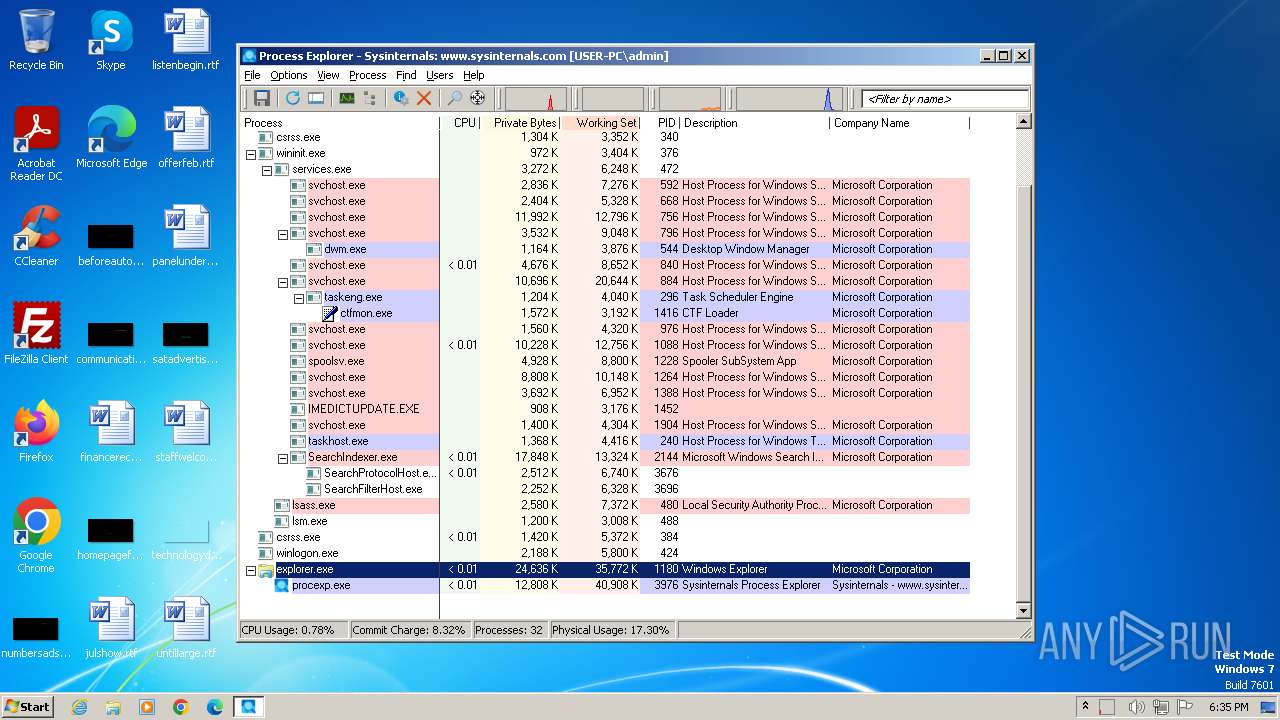
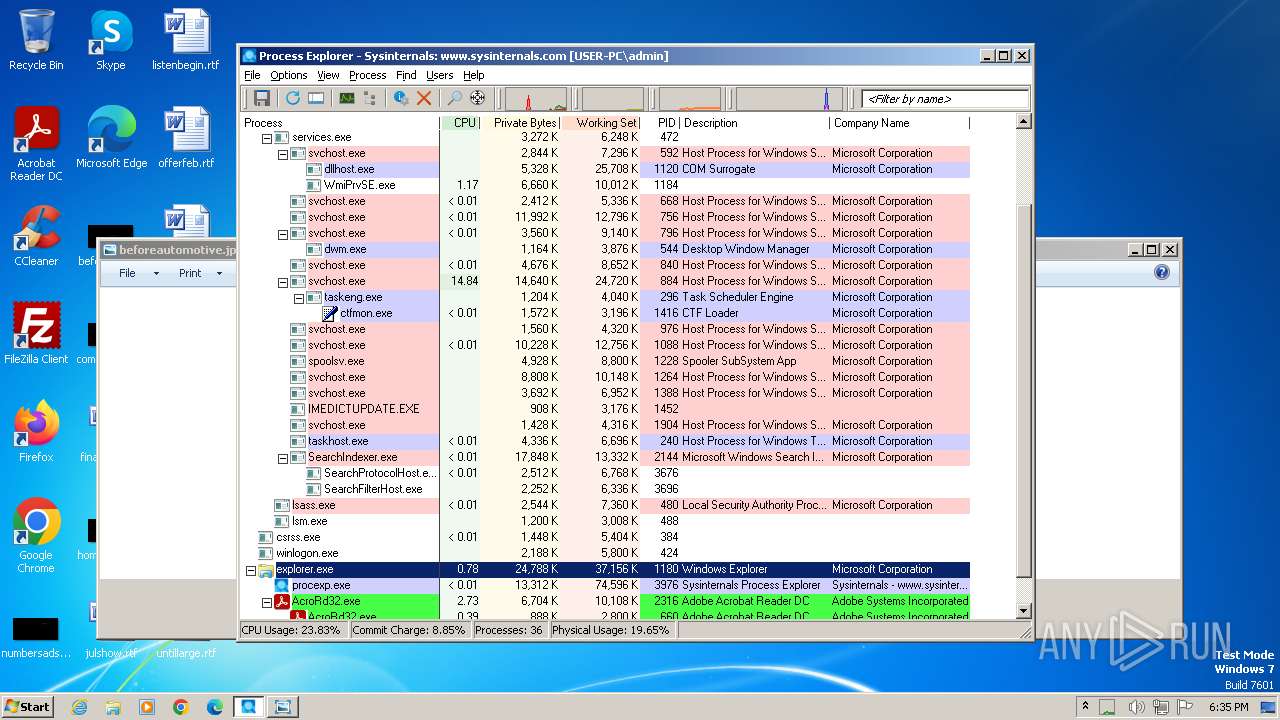
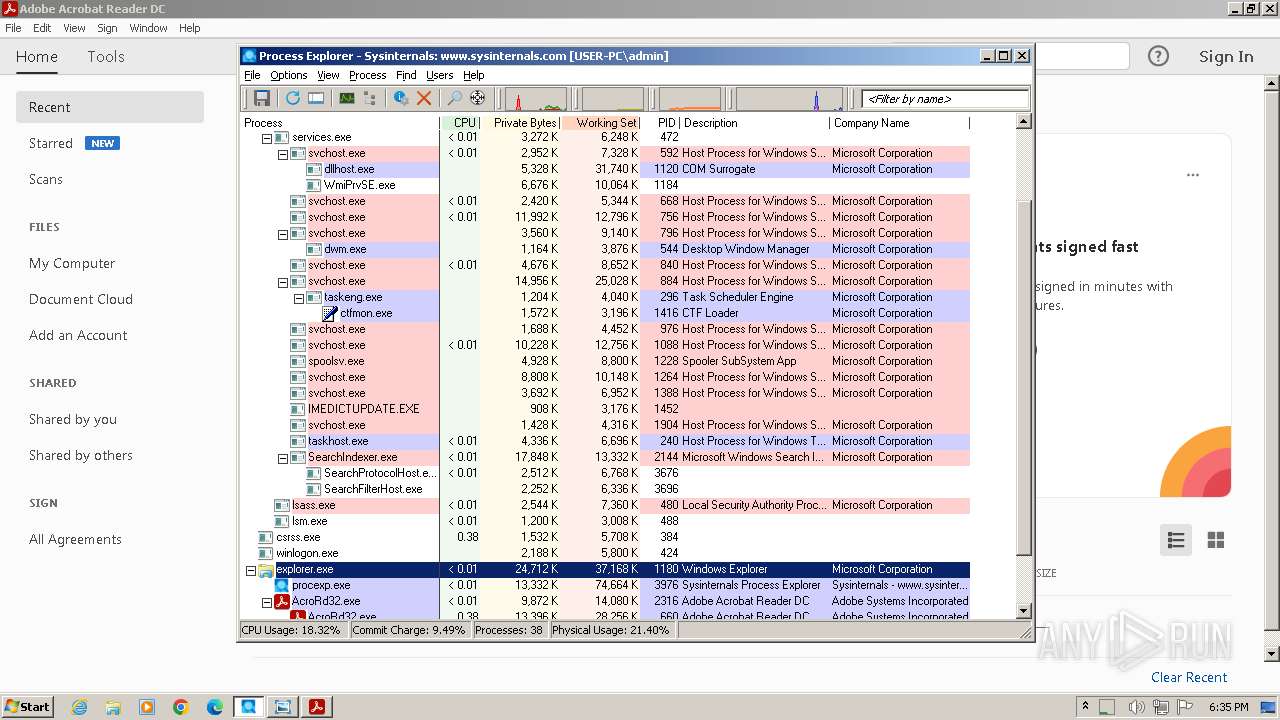
| File name: | procexp.exe |
| Full analysis: | https://app.any.run/tasks/d9047be3-83f1-4e0b-ac0d-03dcdf656ced |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2024, 17:35:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7289AA6C0F2C41C29C9B33CAF1C15779 |
| SHA1: | 96387AB157168B22111E3C70B22364C9B71639C4 |
| SHA256: | 0AB0116B34DB0E7168DD5C5B1C917BBB1D38235ECE4430348F068914B4AB87A6 |
| SSDEEP: | 49152:Kug+zejoF8v8F/nluLRpSct4whtfVKevv7m9gcQYPbH51a7y58SG:Nzeo80F/nQRMPbjAyKZ |
MALICIOUS
Drops the executable file immediately after the start
- procexp.exe (PID: 3976)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- procexp.exe (PID: 3976)
Executable content was dropped or overwritten
- procexp.exe (PID: 3976)
Checks Windows Trust Settings
- procexp.exe (PID: 3976)
Reads security settings of Internet Explorer
- procexp.exe (PID: 3976)
Reads settings of System Certificates
- procexp.exe (PID: 3976)
Reads the Internet Settings
- procexp.exe (PID: 3976)
Creates file in the systems drive root
- AcroRd32.exe (PID: 660)
INFO
Reads the computer name
- procexp.exe (PID: 3976)
- wmpnscfg.exe (PID: 4048)
Reads Environment values
- procexp.exe (PID: 3976)
Checks supported languages
- procexp.exe (PID: 3976)
- wmpnscfg.exe (PID: 4048)
Reads product name
- procexp.exe (PID: 3976)
Create files in a temporary directory
- procexp.exe (PID: 3976)
Reads the machine GUID from the registry
- procexp.exe (PID: 3976)
Reads the software policy settings
- procexp.exe (PID: 3976)
Creates files or folders in the user directory
- procexp.exe (PID: 3976)
Manual execution by a user
- wmpnscfg.exe (PID: 4048)
- AcroRd32.exe (PID: 2316)
- chrome.exe (PID: 960)
Reads Microsoft Office registry keys
- procexp.exe (PID: 3976)
Application launched itself
- RdrCEF.exe (PID: 768)
- AcroRd32.exe (PID: 2316)
- chrome.exe (PID: 960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:13 15:01:39+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.35 |
| CodeSize: | 1020928 |
| InitializedDataSize: | 3743232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc42de |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 17.5.0.0 |
| ProductVersionNumber: | 17.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Sysinternals Process Explorer |
| FileVersion: | 17.05 |
| InternalName: | Process Explorer |
| LegalCopyright: | Copyright © 1998-2023 Mark Russinovich |
| LegalTrademarks: | Copyright © 1998-2023 Mark Russinovich |
| OriginalFileName: | Procexp.exe |
| ProductName: | Process Explorer |
| ProductVersion: | 17.05 |
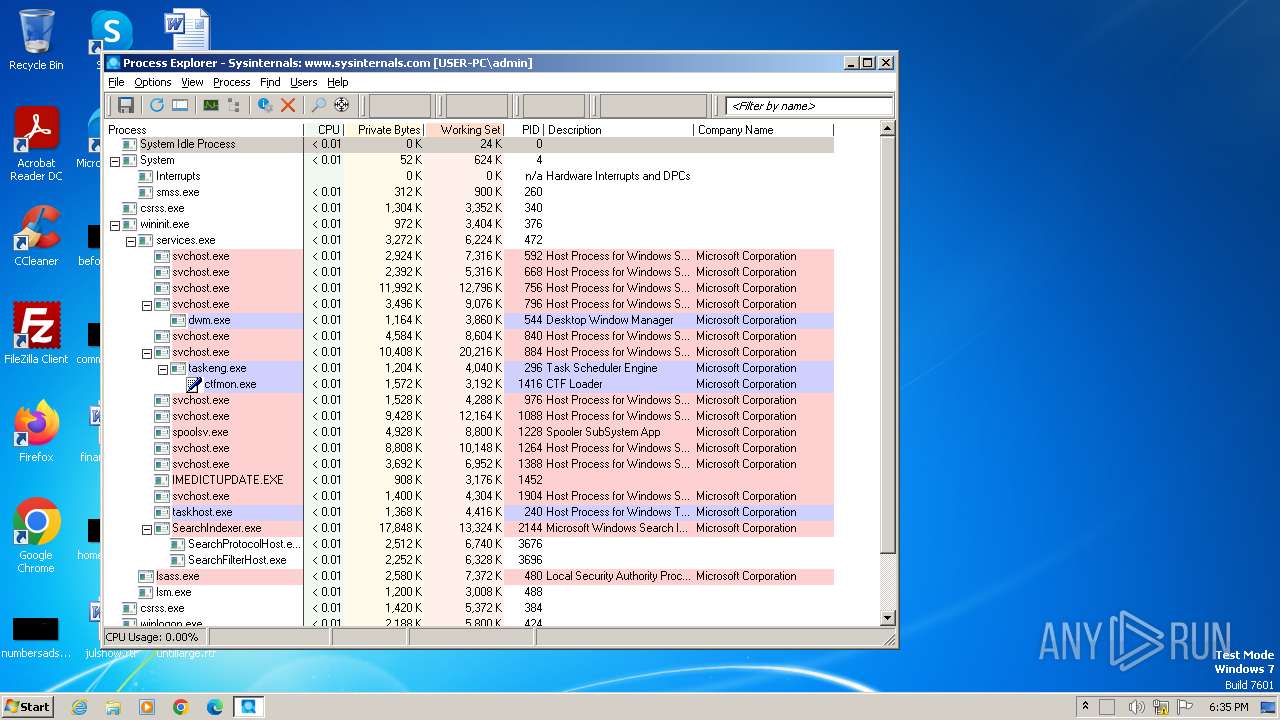
Total processes
55
Monitored processes
22
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 768 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 3221225547 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 824 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1172,14270742452431300216,3895120706918359667,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6571124606230999762 --renderer-client-id=6 --mojo-platform-channel-handle=1464 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2112 --field-trial-handle=1208,i,15710642901628965123,126207491476351285,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1120 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1640 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1172,14270742452431300216,3895120706918359667,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8475816687362192094 --renderer-client-id=2 --mojo-platform-channel-handle=1180 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e6d8b38,0x6e6d8b48,0x6e6d8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,14270742452431300216,3895120706918359667,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=5737354061253465870 --mojo-platform-channel-handle=1292 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2268 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,14270742452431300216,3895120706918359667,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=3266905018875427337 --mojo-platform-channel-handle=1396 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
19 593
Read events
19 107
Write events
192
Delete events
294
Modification events
| (PID) Process: | (3976) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (3976) procexp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1120) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (660) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (660) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement |
| Operation: | write | Name: | bNormalExit |
Value: 0 | |||
| (PID) Process: | (660) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement\cWindowsCurrent\cWin0 |
| Operation: | write | Name: | iTabCount |
Value: 0 | |||
| (PID) Process: | (660) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement\cWindowsCurrent |
| Operation: | write | Name: | iWinCount |
Value: 1 | |||
| (PID) Process: | (2316) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (660) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (660) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | iNumReaderLaunches |
Value: 6 | |||
Executable files
1
Suspicious files
73
Text files
22
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:8B2A87C62CB344B45D79E3A25F266D43 | SHA256:FAFFD211D1D6C3BF1683350AA78CE33755863D94B26ADF808BC14F38EBC2A64F | |||
| 3976 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:382FB454956F73E4909495B33AC043CA | SHA256:FF9B6502A8EE1F3514E871DD2BD4B1D803C2DAAD1FA6977A13D53627DF740DEC | |||
| 3976 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:6872FAE8288DB34207D9E7EE350157F4 | SHA256:50795B027E2BC566D3B7ACB89913F8EFD23B70615C9DB9BF5B23323AD3132A7D | |||
| 768 | RdrCEF.exe | — | ||
MD5:— | SHA256:— | |||
| 3976 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F90F18257CBB4D84216AC1E1F3BB2C76 | binary | |
MD5:2032C498F3B4B751F6570248DC86E82F | SHA256:77D18F4B8A5F1B8F82182A740A63564ECA4A96EE7576A08558528DFE533E7941 | |||
| 3976 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B8CC409ACDBF2A2FE04C56F2875B1FD6 | der | |
MD5:5E275DB761AA5A23AC651AF8F6C4A000 | SHA256:3B9B2F75B724FE5354D24A0EF729B8A2AAA8A9313166EAFB1F73B07CF1A745EF | |||
| 3976 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | der | |
MD5:57B2A3DB7308ECBCCA8000007ACE4302 | SHA256:7B34EB089C61D84FE681242FC53D68E13553D89936409A0EFAE7C59034C9F19C | |||
| 3976 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F90F18257CBB4D84216AC1E1F3BB2C76 | binary | |
MD5:E95AF9B03513D729D28FD890CFF4EBE9 | SHA256:B19F80A5970542F71E1728CDEEE5D4534598329BA22FABF5BBD2280EBD6BA629 | |||
| 3976 | procexp.exe | C:\Users\admin\AppData\Local\Temp\PROCEXP152.SYS | executable | |
MD5:D80A54CEECFF2B6598F24EC9F8901C97 | SHA256:5492797019E99316E37AA77319DF912A4054B2E718FCA0A39F81D0E8965B0760 | |||
| 3976 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B8CC409ACDBF2A2FE04C56F2875B1FD6 | binary | |
MD5:D1795717A543CF00AE2B01B74E1A5FAC | SHA256:D54B8CA10A3813C737DC34FB831043105ECC26AD12E26F814397C391EDE54713 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
17
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3976 | procexp.exe | GET | 304 | 2.20.13.143:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?daaf1a3795a83b91 | unknown | — | — | unknown |
3976 | procexp.exe | GET | 200 | 2.20.13.130:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | unknown |
3976 | procexp.exe | GET | 200 | 2.20.13.130:80 | http://crl.microsoft.com/pki/crl/products/WinPCA.crl | unknown | — | — | unknown |
3976 | procexp.exe | GET | 200 | 2.20.13.130:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | unknown |
3976 | procexp.exe | GET | 200 | 2.20.13.130:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
3976 | procexp.exe | GET | 200 | 2.22.201.205:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | unknown | — | — | unknown |
3976 | procexp.exe | GET | 200 | 2.20.13.130:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 2.20.13.143:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?83bdd76cfa43776c | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3976 | procexp.exe | 2.20.13.143:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
3976 | procexp.exe | 2.20.13.130:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
3976 | procexp.exe | 2.22.201.205:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
768 | RdrCEF.exe | 2.22.200.162:443 | geo2.adobe.com | AKAMAI-AS | FR | unknown |
1088 | svchost.exe | 2.20.13.143:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
2700 | chrome.exe | 142.250.185.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
update.googleapis.com |
| unknown |
chrome.google.com |
| unknown |