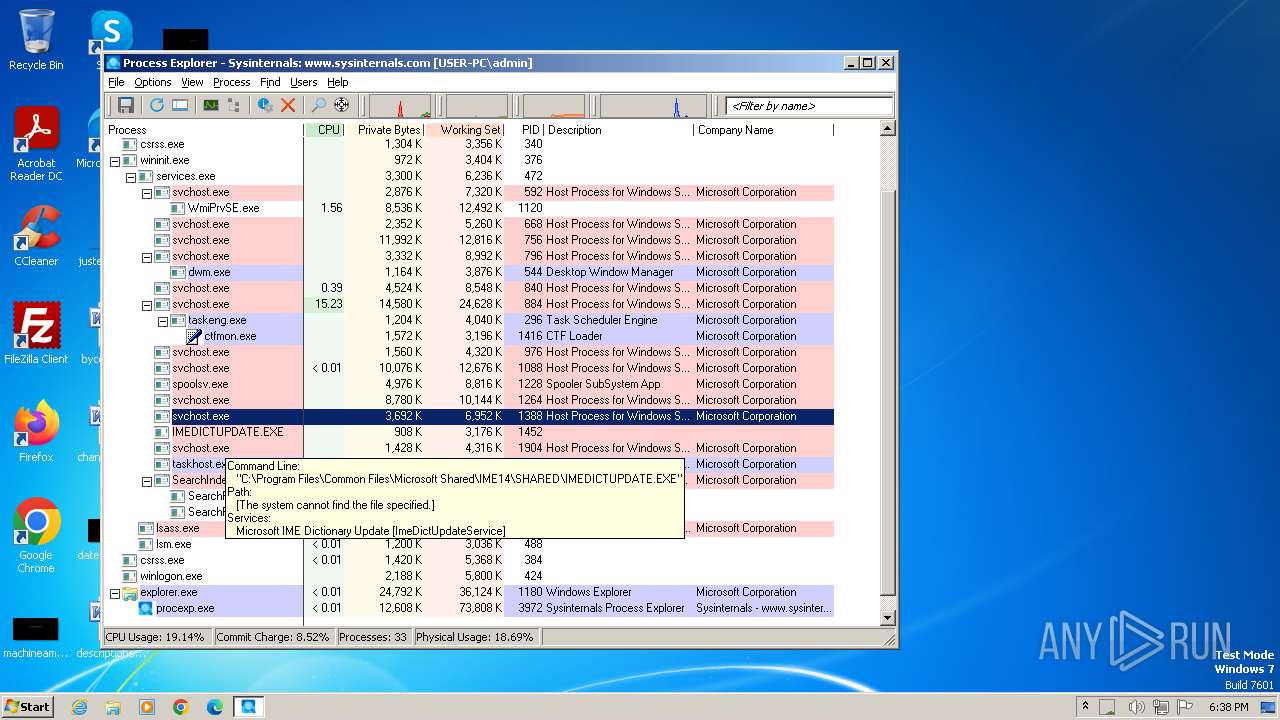
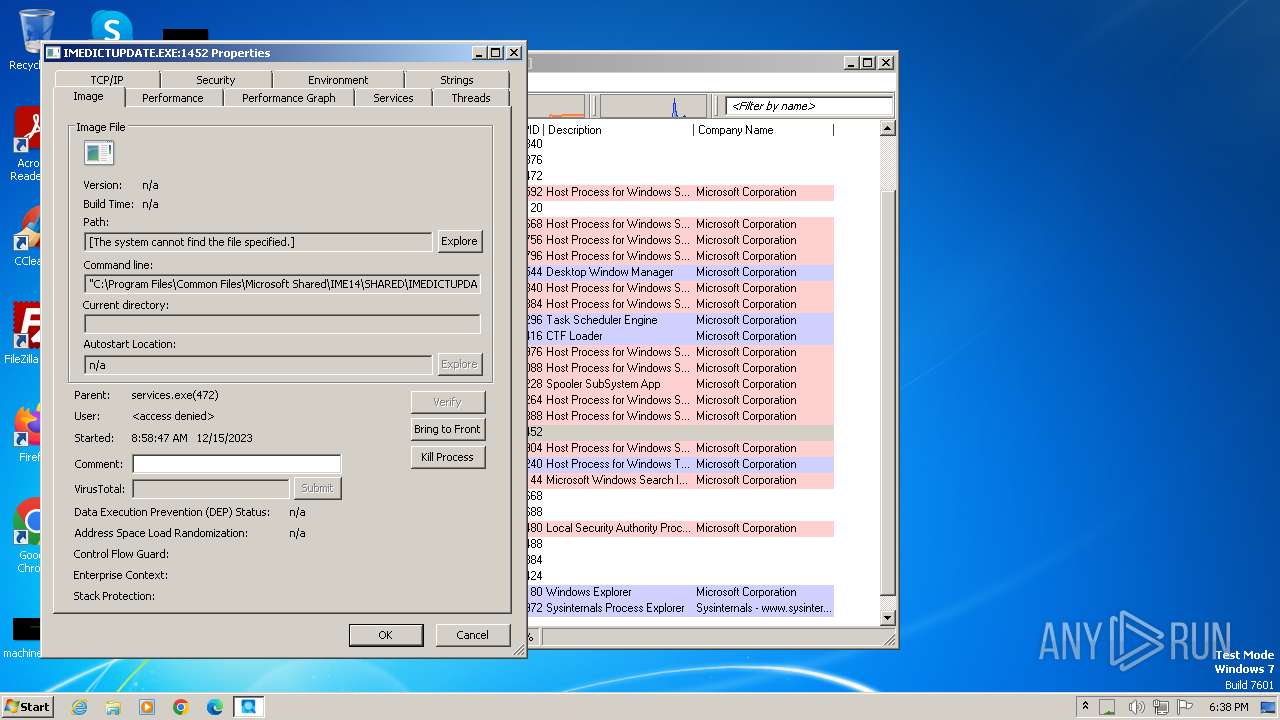
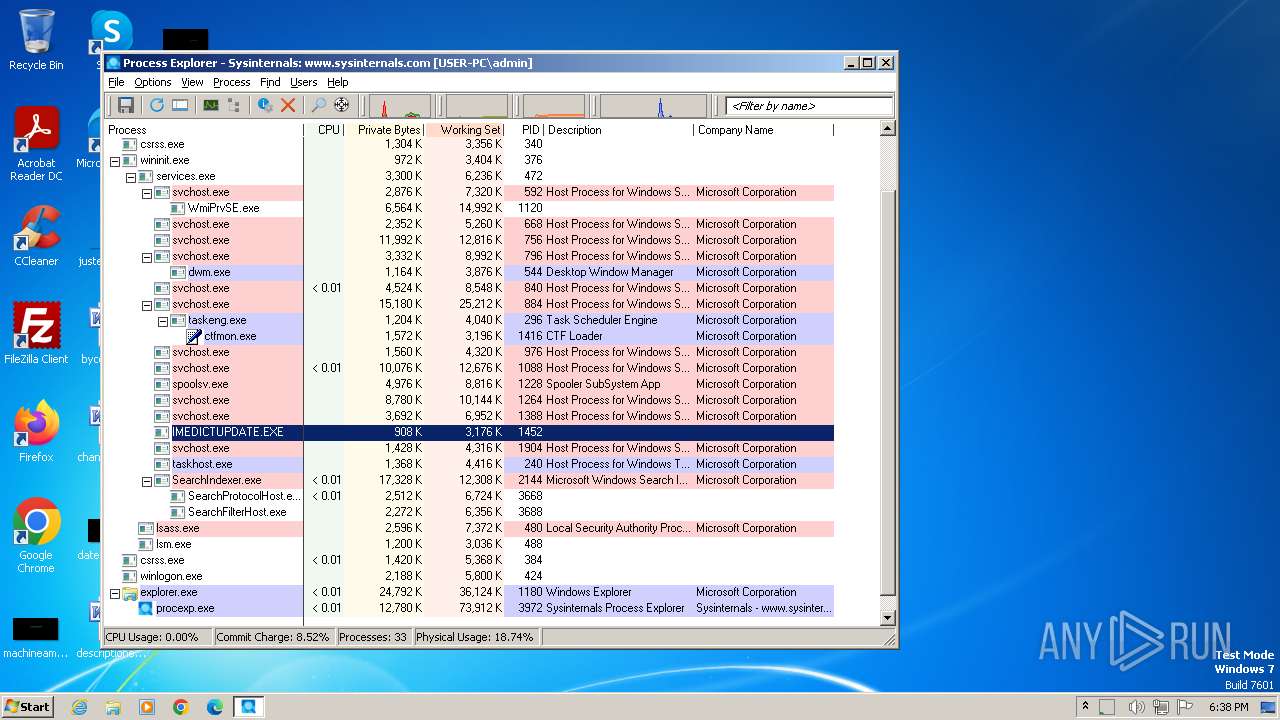
| File name: | procexp.exe |
| Full analysis: | https://app.any.run/tasks/96b2c31d-9b8b-41d0-944a-455323c058a9 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2024, 17:37:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7289AA6C0F2C41C29C9B33CAF1C15779 |
| SHA1: | 96387AB157168B22111E3C70B22364C9B71639C4 |
| SHA256: | 0AB0116B34DB0E7168DD5C5B1C917BBB1D38235ECE4430348F068914B4AB87A6 |
| SSDEEP: | 49152:Kug+zejoF8v8F/nluLRpSct4whtfVKevv7m9gcQYPbH51a7y58SG:Nzeo80F/nQRMPbjAyKZ |
MALICIOUS
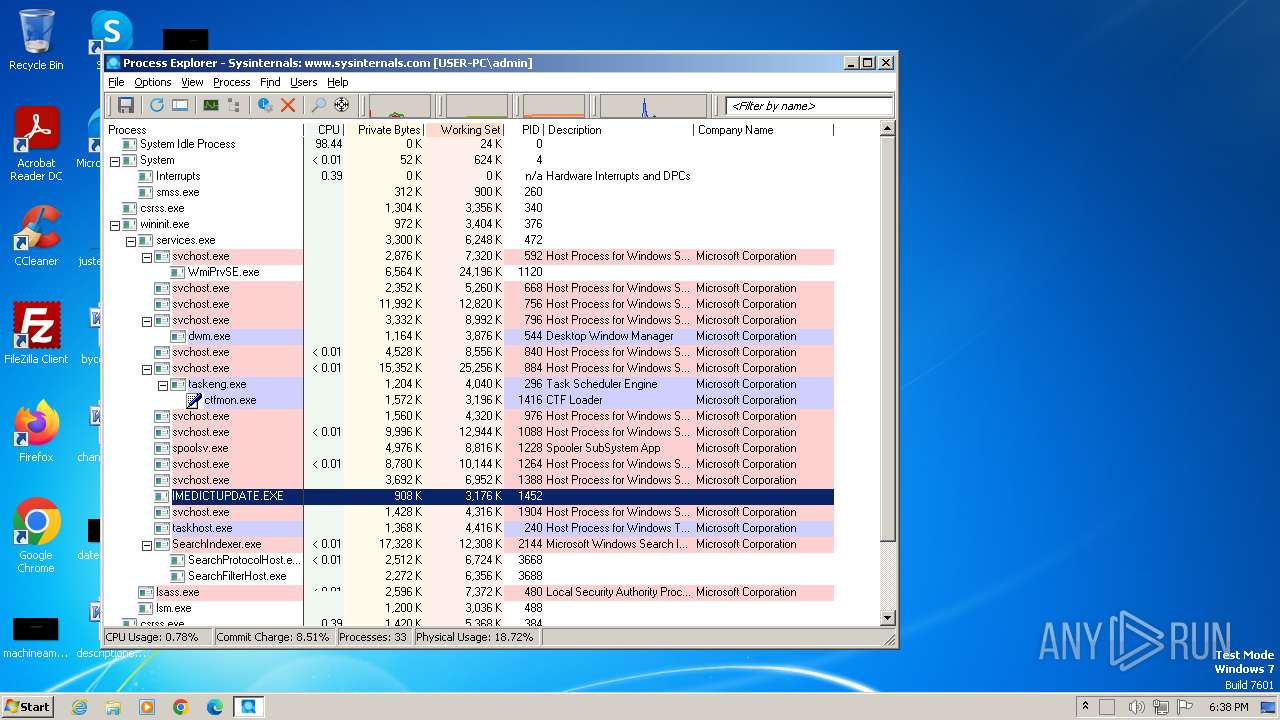
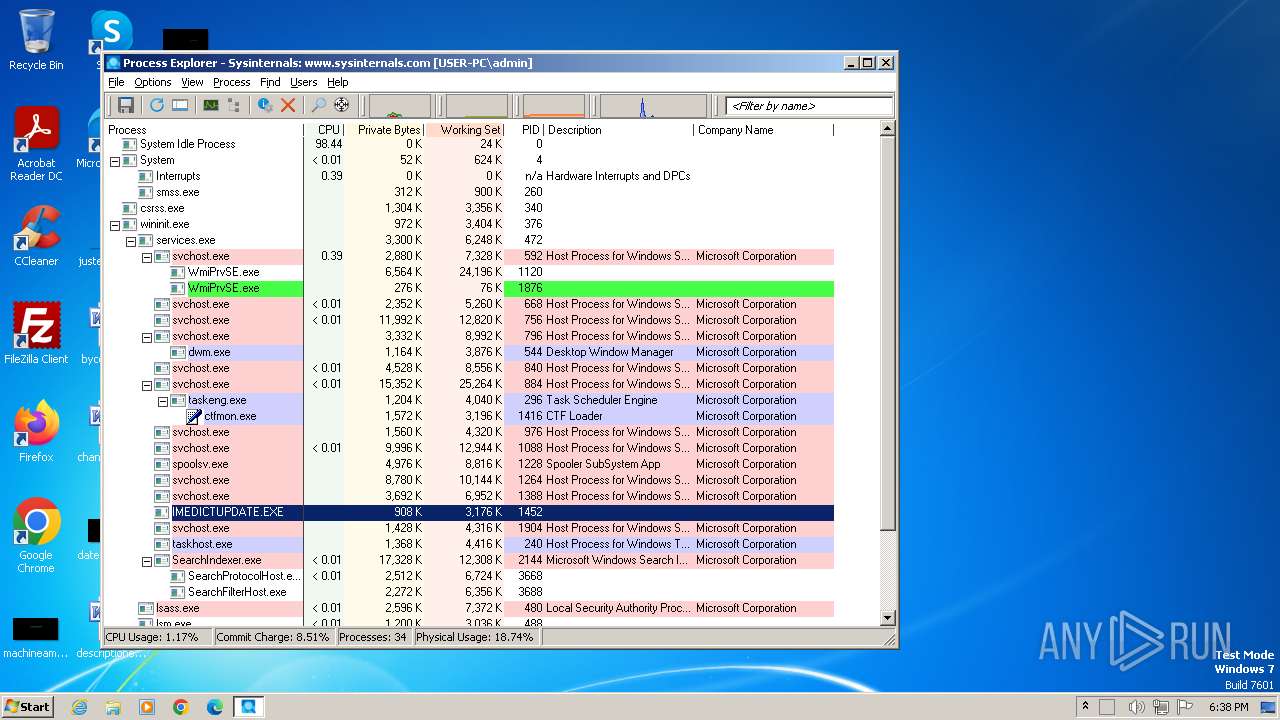
Drops the executable file immediately after the start
- procexp.exe (PID: 3972)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- procexp.exe (PID: 3972)
Executable content was dropped or overwritten
- procexp.exe (PID: 3972)
Checks Windows Trust Settings
- procexp.exe (PID: 3972)
Reads security settings of Internet Explorer
- procexp.exe (PID: 3972)
Reads settings of System Certificates
- procexp.exe (PID: 3972)
Reads the Internet Settings
- procexp.exe (PID: 3972)
INFO
Reads the computer name
- procexp.exe (PID: 3972)
- wmpnscfg.exe (PID: 4092)
Checks supported languages
- procexp.exe (PID: 3972)
- wmpnscfg.exe (PID: 4092)
Reads product name
- procexp.exe (PID: 3972)
Reads Environment values
- procexp.exe (PID: 3972)
Create files in a temporary directory
- procexp.exe (PID: 3972)
Reads the machine GUID from the registry
- procexp.exe (PID: 3972)
Reads the software policy settings
- procexp.exe (PID: 3972)
Creates files or folders in the user directory
- procexp.exe (PID: 3972)
Reads Microsoft Office registry keys
- procexp.exe (PID: 3972)
Manual execution by a user
- wmpnscfg.exe (PID: 4092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:13 15:01:39+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.35 |
| CodeSize: | 1020928 |
| InitializedDataSize: | 3743232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc42de |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 17.5.0.0 |
| ProductVersionNumber: | 17.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Sysinternals Process Explorer |
| FileVersion: | 17.05 |
| InternalName: | Process Explorer |
| LegalCopyright: | Copyright © 1998-2023 Mark Russinovich |
| LegalTrademarks: | Copyright © 1998-2023 Mark Russinovich |
| OriginalFileName: | Procexp.exe |
| ProductName: | Process Explorer |
| ProductVersion: | 17.05 |
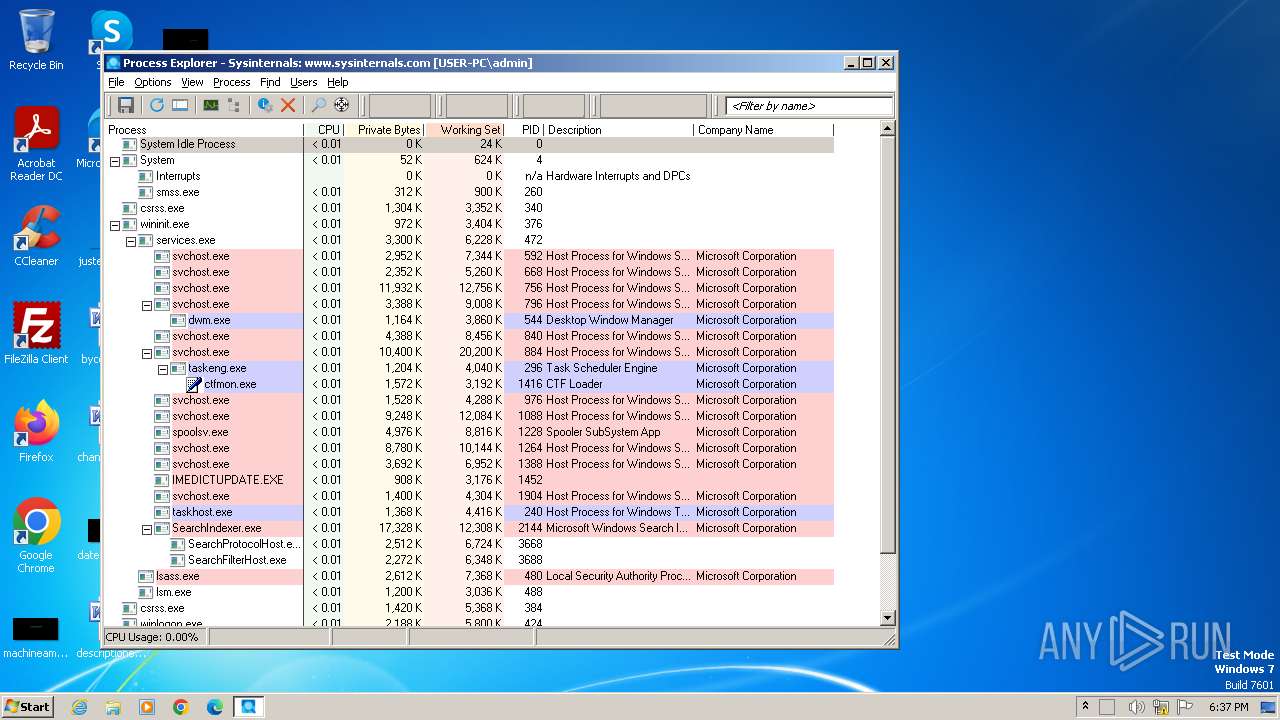
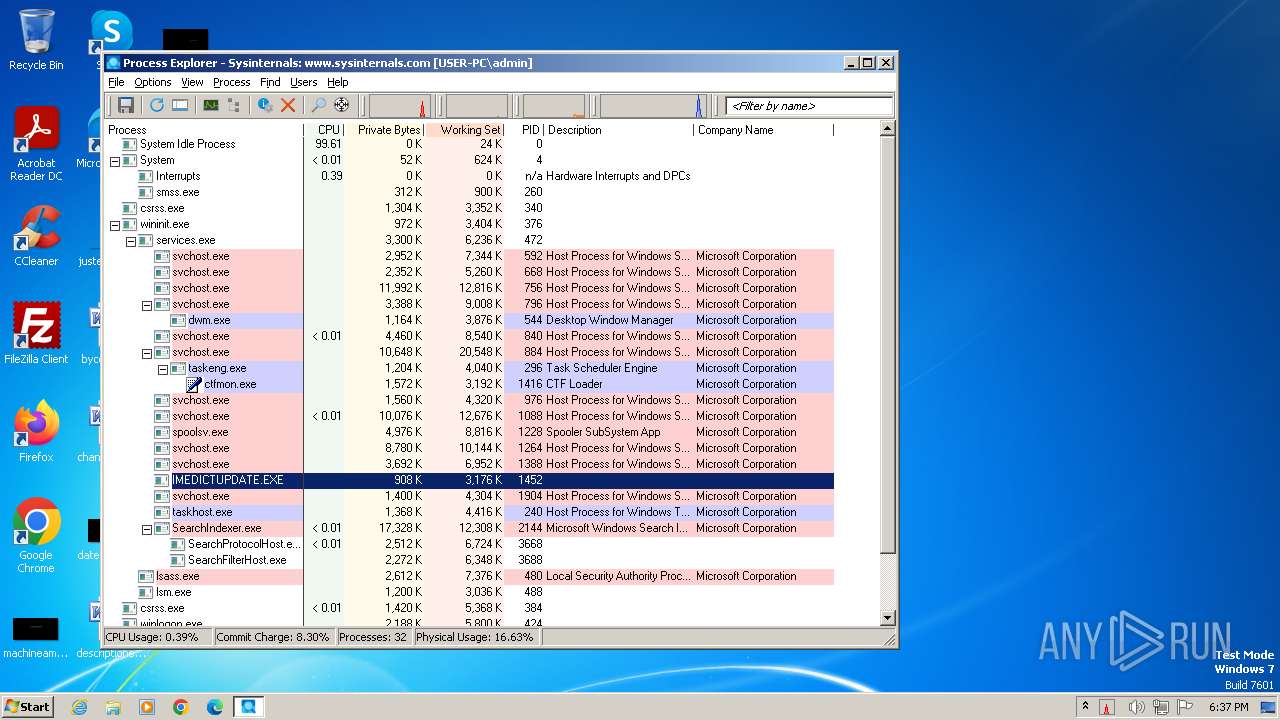
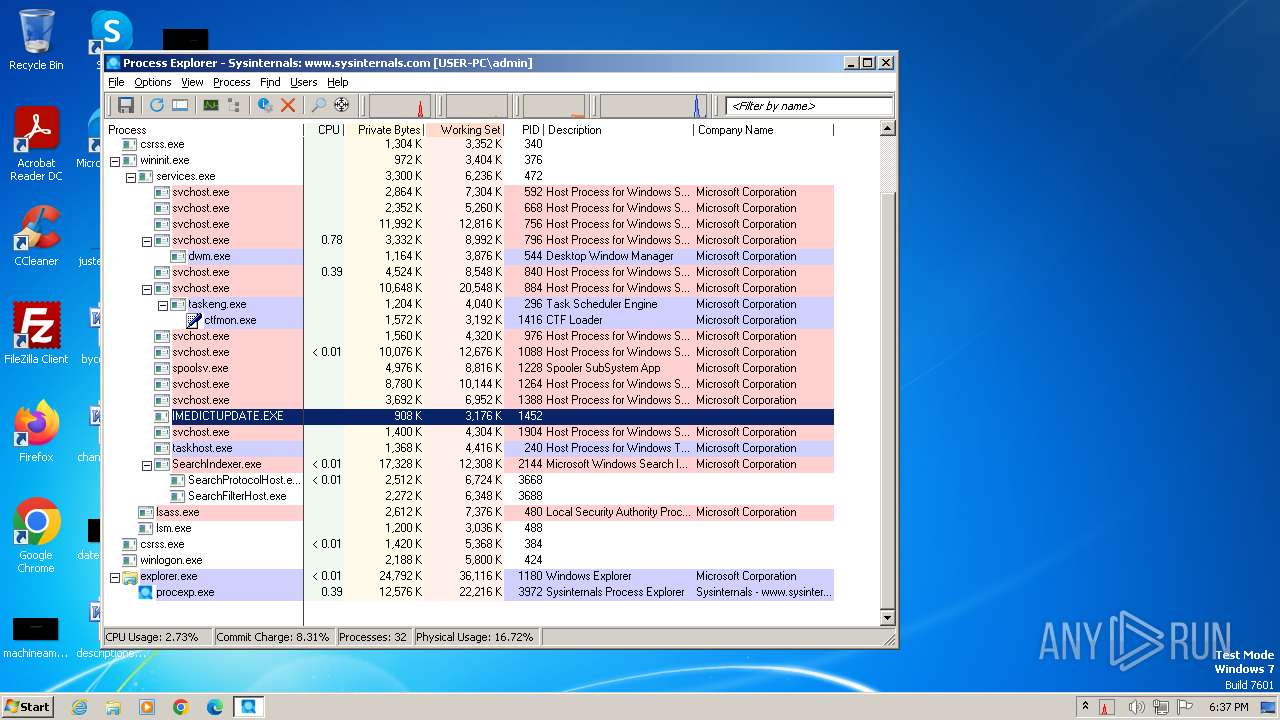
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
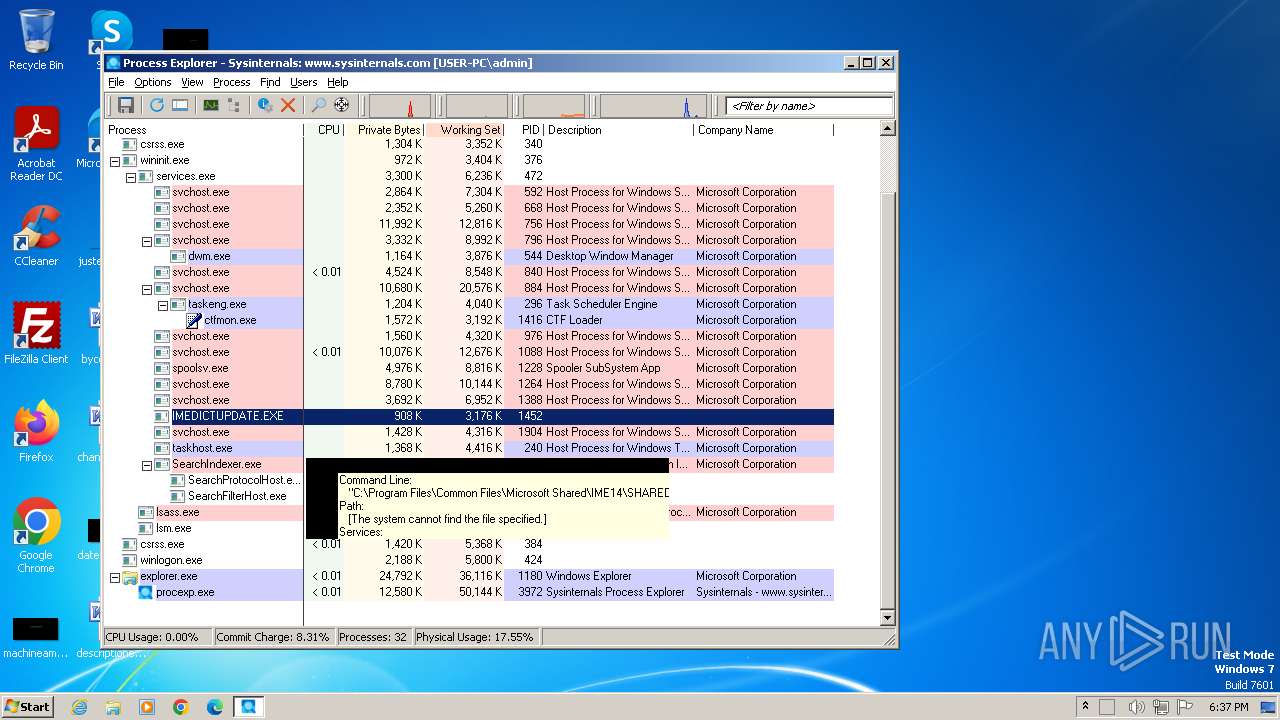
| 3972 | "C:\Users\admin\AppData\Local\Temp\procexp.exe" | C:\Users\admin\AppData\Local\Temp\procexp.exe | explorer.exe | ||||||||||||
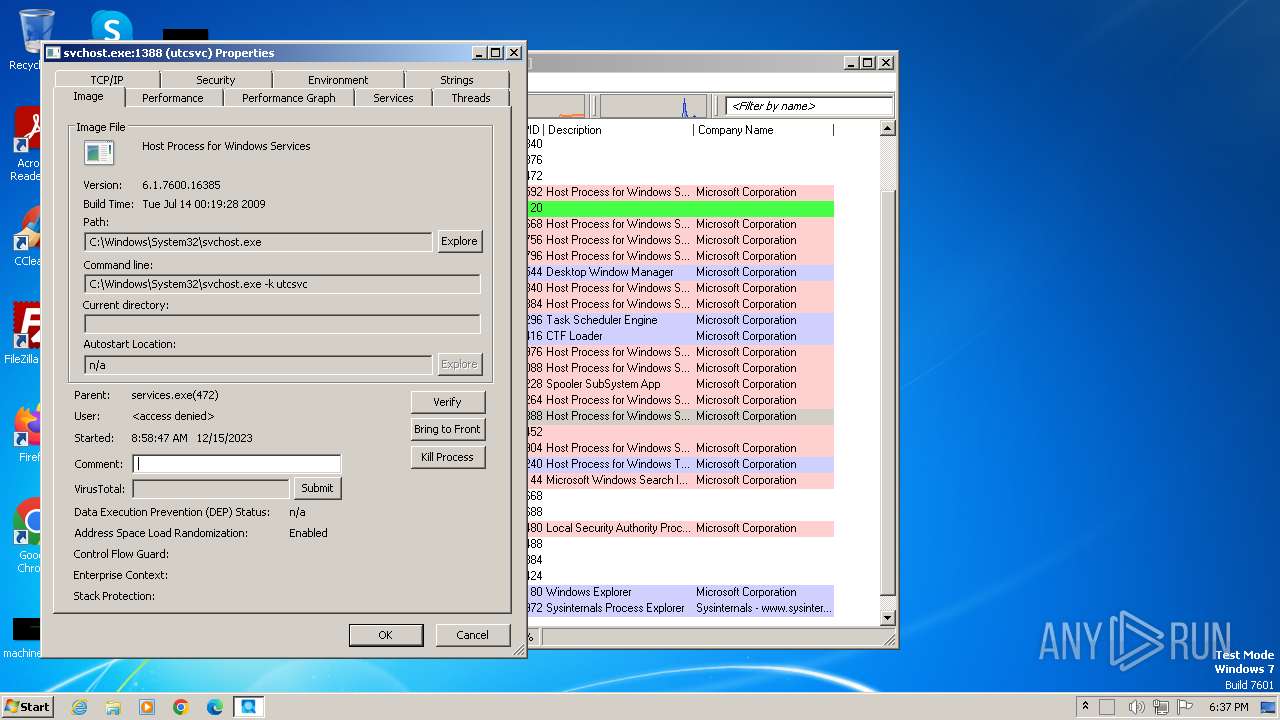
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals Process Explorer Exit code: 0 Version: 17.05 Modules
| |||||||||||||||
| 4092 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 874
Read events
10 444
Write events
136
Delete events
294
Modification events
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | Windowplacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF6400000032000000840300008A020000 | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | FindWindowplacement |
Value: 2C00000000000000000000000000000000000000000000000000000096000000960000000000000000000000 | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | SysinfoWindowplacement |
Value: 2C00000000000000000000000000000000000000000000000000000028000000280000000000000000000000 | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | PropWindowplacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF28000000280000001002000093020000 | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | DllPropWindowplacement |
Value: 2C00000000000000000000000000000000000000000000000000000028000000280000000000000000000000 | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | UnicodeFont |
Value: 080000000000000000000000000000009001000000000000000000004D00530020005300680065006C006C00200044006C00670000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | Divider |
Value: 000000000000E03F | |||
| (PID) Process: | (3972) procexp.exe | Key: | HKEY_CURRENT_USER\Software\Sysinternals\Process Explorer |
| Operation: | write | Name: | SavedDivider |
Value: 000000000000E03F | |||
Executable files
1
Suspicious files
13
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\696F3DE637E6DE85B458996D49D759AD | der | |
MD5:6872FAE8288DB34207D9E7EE350157F4 | SHA256:50795B027E2BC566D3B7ACB89913F8EFD23B70615C9DB9BF5B23323AD3132A7D | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B8CC409ACDBF2A2FE04C56F2875B1FD6 | der | |
MD5:5E275DB761AA5A23AC651AF8F6C4A000 | SHA256:3B9B2F75B724FE5354D24A0EF729B8A2AAA8A9313166EAFB1F73B07CF1A745EF | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F90F18257CBB4D84216AC1E1F3BB2C76 | binary | |
MD5:D50C89C8912555DD8EC490B9D7EC8E43 | SHA256:64CF707672CECD1B811DC18DE5B50F262A5198EE0EA8A1B12AF6CAB254F4DB91 | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:F18507F724C71B4C23323983F175F69E | SHA256:5D3898C587E5C76631B78874AD48883B9740FA36DE13A4C804BD79970B323E2C | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F90F18257CBB4D84216AC1E1F3BB2C76 | der | |
MD5:E95AF9B03513D729D28FD890CFF4EBE9 | SHA256:B19F80A5970542F71E1728CDEEE5D4534598329BA22FABF5BBD2280EBD6BA629 | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B8CC409ACDBF2A2FE04C56F2875B1FD6 | binary | |
MD5:F8C520FF8B2D50DA52C804F20B096003 | SHA256:429A06CFEDB0C6EC87D0DE66B9793FE90437842EBE78463221F8D4371504062F | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2CD1F910DD5DC23C234E99A91DE345C0 | binary | |
MD5:5CF1FFEA09F88F6FE4930224EAE4DA4C | SHA256:B9D3A9D6965BDC29FD306EF1368DA3511C1EDEA03E5686D73ECB9C753051BF7F | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:5B0C2FC75E403C2BD6E6DCE77FBB0131 | SHA256:B823D602E60BC000EDCC7B99299C54D2532AEBE876CA2C9390B6BFF3F989AE67 | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4C7F163ED126D5C3CB9457F68EC64E9E | der | |
MD5:92EAB03C771E2873C170D7835E98FC93 | SHA256:B13036F0FEC353CDBF9B73F2B7C28B1AFD3331DF5D5E12A4A9EA592B3B4353C6 | |||
| 3972 | procexp.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2CD1F910DD5DC23C234E99A91DE345C0 | binary | |
MD5:76AF5889D7F151043778560EC903029B | SHA256:FF8D37D74262ACB68482CD50DCA6917898641FDDD0711294336908FA84C55D30 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
7
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | procexp.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?abb89e19eec6ec7a | unknown | — | — | unknown |
3972 | procexp.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | unknown |
3972 | procexp.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/WinPCA.crl | unknown | — | — | unknown |
3972 | procexp.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | unknown |
3972 | procexp.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 193.108.153.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4f7497503626c948 | unknown | — | — | unknown |
3972 | procexp.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
3972 | procexp.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3972 | procexp.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3972 | procexp.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
3972 | procexp.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1088 | svchost.exe | 193.108.153.25:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |