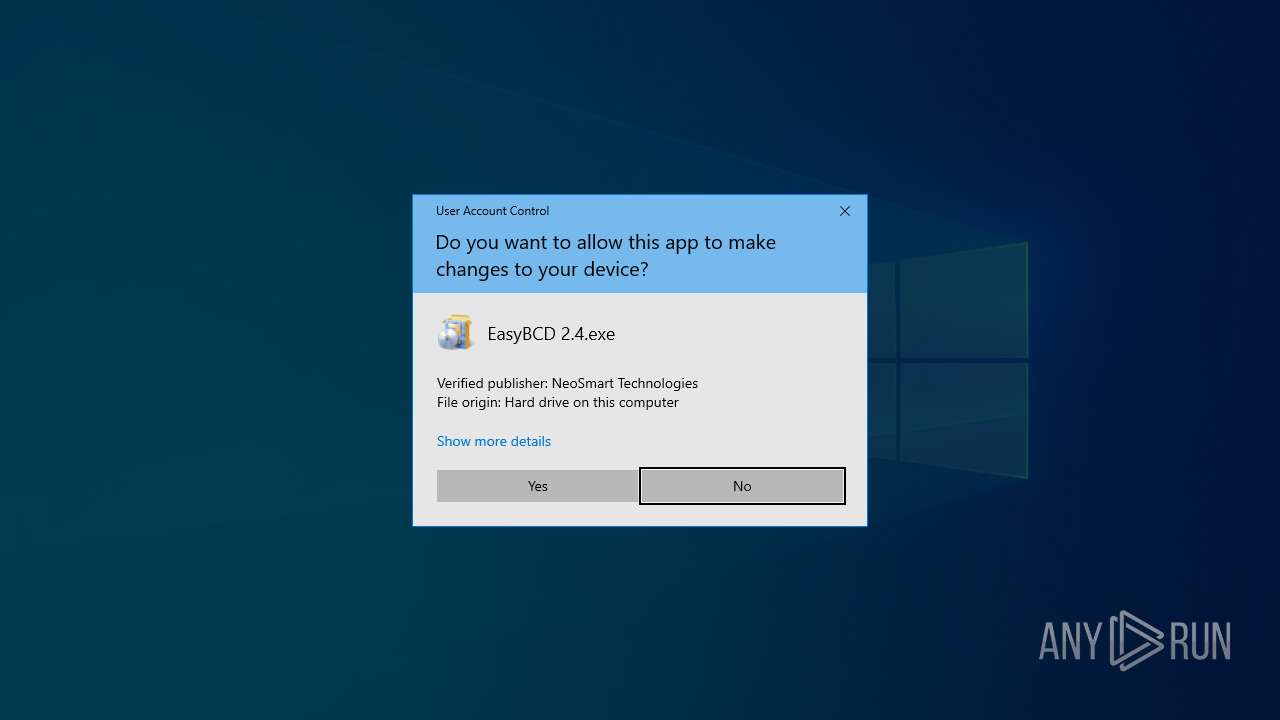
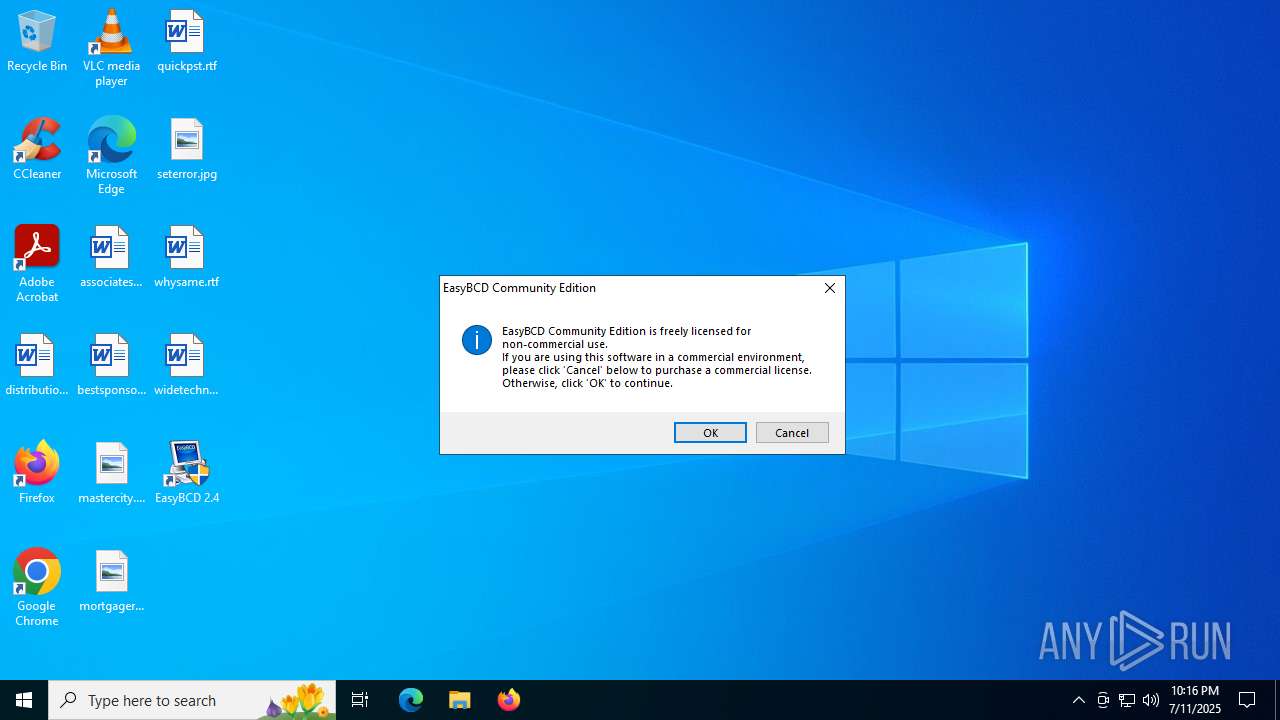
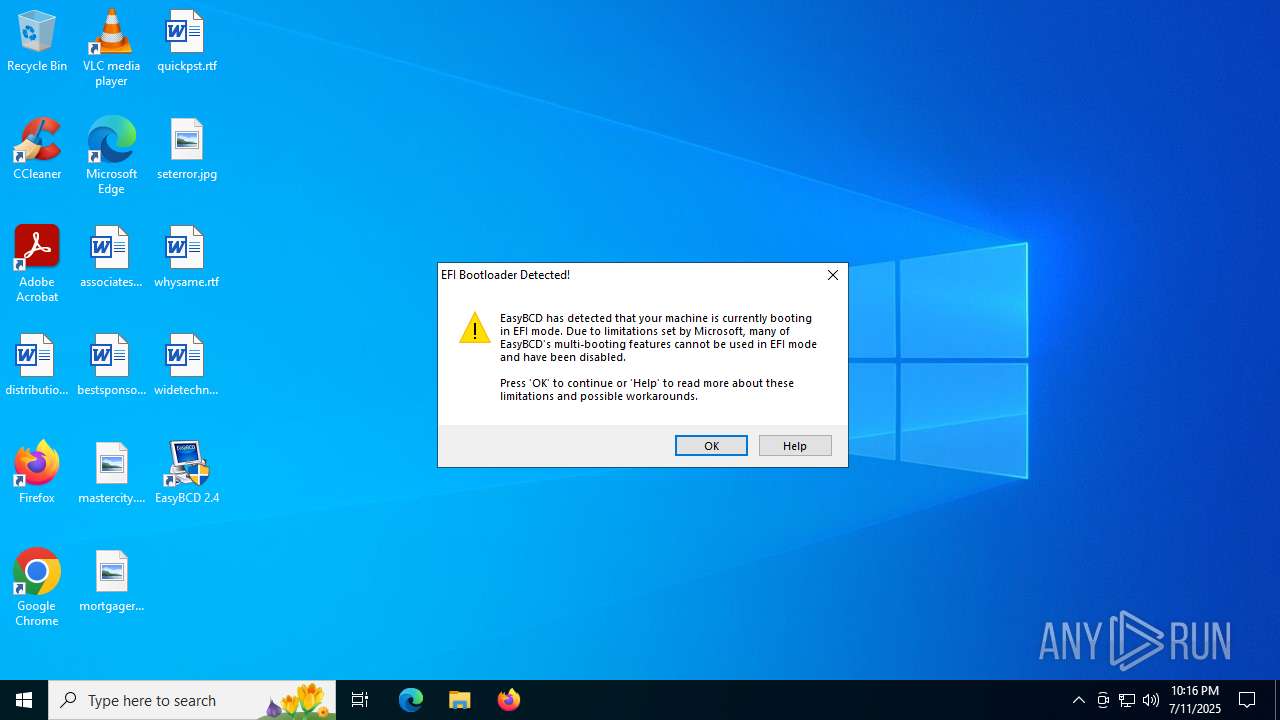
| File name: | EasyBCD 2.4.exe |
| Full analysis: | https://app.any.run/tasks/b47fa2ac-77f6-4705-a5bb-200a2d067ea5 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2025, 22:15:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 2E06476EBE1137F543EE7176D34716E7 |
| SHA1: | 6EAA6AA0E829CE8AF54213F6DE77E748C4388E23 |
| SHA256: | 0A94A43AF2DB7BDBADA87B34BF03D3B221110D1CA21BBEBEC55B08767C1281CC |
| SSDEEP: | 98304:ilHlURur2ooGWFdzLmi9pimQ43ZIbI7KjDgXC5b7V6n0pWzvx4X1aex55V9WSdzu:hBma |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- EasyBCD 2.4.exe (PID: 2716)
Malware-specific behavior (creating "System.dll" in Temp)
- EasyBCD 2.4.exe (PID: 2716)
Uses TASKKILL.EXE to kill process
- EasyBCD 2.4.exe (PID: 2716)
Reads security settings of Internet Explorer
- EasyBCD 2.4.exe (PID: 2716)
- EasyBCD.exe (PID: 2532)
Executable content was dropped or overwritten
- EasyBCD 2.4.exe (PID: 2716)
Process drops legitimate windows executable
- EasyBCD 2.4.exe (PID: 2716)
There is functionality for taking screenshot (YARA)
- EasyBCD 2.4.exe (PID: 2716)
Reads Internet Explorer settings
- EasyBCD.exe (PID: 2532)
Creates a software uninstall entry
- EasyBCD 2.4.exe (PID: 2716)
Reads the date of Windows installation
- EasyBCD.exe (PID: 2532)
INFO
Checks supported languages
- EasyBCD 2.4.exe (PID: 2716)
- EasyBCD.exe (PID: 2532)
- BootGrabber.exe (PID: 1984)
- bcdedit.exe (PID: 5744)
- UtfRedirect.exe (PID: 6516)
- UtfRedirect.exe (PID: 5556)
- UtfRedirect.exe (PID: 4808)
- UtfRedirect.exe (PID: 6940)
- UtfRedirect.exe (PID: 2228)
- UtfRedirect.exe (PID: 4400)
- UtfRedirect.exe (PID: 3908)
- bcdedit.exe (PID: 6360)
- bcdedit.exe (PID: 6508)
- UtfRedirect.exe (PID: 2148)
- bcdedit.exe (PID: 4864)
- bcdedit.exe (PID: 1852)
- UtfRedirect.exe (PID: 4520)
- bcdedit.exe (PID: 6320)
- bcdedit.exe (PID: 4832)
- bcdedit.exe (PID: 3872)
- UtfRedirect.exe (PID: 3720)
- bcdedit.exe (PID: 420)
- bcdedit.exe (PID: 6680)
Process checks computer location settings
- EasyBCD 2.4.exe (PID: 2716)
- EasyBCD.exe (PID: 2532)
Reads the computer name
- EasyBCD 2.4.exe (PID: 2716)
- EasyBCD.exe (PID: 2532)
Create files in a temporary directory
- EasyBCD 2.4.exe (PID: 2716)
- EasyBCD.exe (PID: 2532)
- msfeedssync.exe (PID: 4860)
- msfeedssync.exe (PID: 5772)
Creates files in the program directory
- EasyBCD 2.4.exe (PID: 2716)
The sample compiled with english language support
- EasyBCD 2.4.exe (PID: 2716)
Creates files or folders in the user directory
- EasyBCD.exe (PID: 2532)
Reads the machine GUID from the registry
- EasyBCD.exe (PID: 2532)
Disables trace logs
- EasyBCD.exe (PID: 2532)
Reads Environment values
- EasyBCD.exe (PID: 2532)
Process checks whether UAC notifications are on
- EasyBCD.exe (PID: 2532)
Checks proxy server information
- EasyBCD.exe (PID: 2532)
- msfeedssync.exe (PID: 4860)
- slui.exe (PID: 6812)
Reads the software policy settings
- EasyBCD.exe (PID: 2532)
- slui.exe (PID: 6812)
Reads security settings of Internet Explorer
- msfeedssync.exe (PID: 5772)
- msfeedssync.exe (PID: 4860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:30 03:57:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3328 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
179
Monitored processes
40
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UtfRedirect.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | "C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\bcdedit.exe" /enum all | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\bcdedit.exe | — | UtfRedirect.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.2.8250.0 (winmain_win8beta.120217-1520) Modules
| |||||||||||||||
| 864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UtfRedirect.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1352 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | BootGrabber.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | "C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\bcdedit.exe" /set {7cf009c6-239c-11ed-b4aa-99f4f79029c5} systemroot \Windows | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\bcdedit.exe | — | UtfRedirect.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.2.8250.0 (winmain_win8beta.120217-1520) Modules
| |||||||||||||||
| 1984 | "C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\bootgrabber.exe" /tlist | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\BootGrabber.exe | — | EasyBCD.exe | |||||||||||
User: admin Company: NeoSmart Technologies Integrity Level: HIGH Description: EasyBCD boot helper Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2148 | "C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\UtfRedirect.exe" | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\UtfRedirect.exe | — | EasyBCD.exe | |||||||||||
User: admin Company: NeoSmart Technologies Integrity Level: HIGH Description: UTF8 codepage proxy application Exit code: 1 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2228 | "C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\UtfRedirect.exe" | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\UtfRedirect.exe | — | EasyBCD.exe | |||||||||||
User: admin Company: NeoSmart Technologies Integrity Level: HIGH Description: UTF8 codepage proxy application Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2532 | "C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\EasyBCD.exe" | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\EasyBCD.exe | EasyBCD 2.4.exe | ||||||||||||
User: admin Company: NeoSmart Technologies Integrity Level: HIGH Description: EasyBCD Exit code: 0 Version: 2.4.0.237 Modules
| |||||||||||||||
Total events
10 210
Read events
9 390
Write events
552
Delete events
268
Modification events
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | DisplayName |
Value: EasyBCD 2.4 | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\uninstall.exe | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\EasyBCD.exe | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | HelpLink |
Value: http://neosmart.net/forums/ | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | URLUpdateInfo |
Value: http://neosmart.net/EasyBCD/ | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | VersionMajor |
Value: 2 | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | VersionMinor |
Value: 4 | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (2716) EasyBCD 2.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\EasyBCD |
| Operation: | write | Name: | DisplayVersion |
Value: 2.4 | |||
Executable files
18
Suspicious files
51
Text files
310
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2716 | EasyBCD 2.4.exe | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\NeoSmart.Localization.dll | executable | |
MD5:AD0A59AE87D4BA106E965C62F0BC3D88 | SHA256:3A56005B2EFB34620019EF432FE90EEB63726FC78B37BE841F25C2AED82EB1DB | |||
| 2716 | EasyBCD 2.4.exe | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\EasyBCD.exe.config | xml | |
MD5:3379AC7243ADCFA51A02295DBEDC956A | SHA256:7EC2512B59E62A3AEB0A1025BF152A31291E17E7E469CE18EFAE153064665B03 | |||
| 2716 | EasyBCD 2.4.exe | C:\Users\admin\AppData\Local\Temp\nsp5BDD.tmp\System.dll | executable | |
MD5:B0C77267F13B2F87C084FD86EF51CCFC | SHA256:A0CAC4CF4852895619BC7743EBEB89F9E4927CCDB9E66B1BCD92A4136D0F9C77 | |||
| 2716 | EasyBCD 2.4.exe | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\bootsect.exe | executable | |
MD5:DA39BBA4267EC54DE12374BFD88D0DF4 | SHA256:F15E3C9A8F73C6DC4EA8F0A174915B6EDCA06C75332EEC8A28E7A4B347276D4D | |||
| 2716 | EasyBCD 2.4.exe | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\NST Downloader.exe | executable | |
MD5:A5B3EA9EE11E9752417159BA1C618B95 | SHA256:B92B2FA8916C78CCFFEF058D3BE900C840CB996028D373BA55985FD1D1DDDAC8 | |||
| 2716 | EasyBCD 2.4.exe | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\bcdedit.exe | executable | |
MD5:A60CBAEA0F8AC802D21C0CC7BC2589BE | SHA256:8BF1B71182FED18D6B4112BDC4D496800B5BF6681DE4C4F6536BA67378F38A12 | |||
| 2716 | EasyBCD 2.4.exe | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\UtfRedirect.exe | executable | |
MD5:5B40791899FA37507E7C08BC3D9F5294 | SHA256:5A87D9485F6E13EE2C3BA4AC289A3E237D17A43ED428B8A5BD5F00FC4800D1AC | |||
| 2716 | EasyBCD 2.4.exe | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\bin\NetTest.exe | executable | |
MD5:3F3BE08145D962F3146F9632CA1EC910 | SHA256:C35B26223B07D81E9AB638B52E5344D33E10DF874457A7B1CFBDA6F591A07C7F | |||
| 2716 | EasyBCD 2.4.exe | C:\Program Files (x86)\NeoSmart Technologies\EasyBCD\Newtonsoft.Json.dll | executable | |
MD5:0953851089821550EF013B487DA3915A | SHA256:4A56EF352F84AD19C1B4486C7C9E64FEF9A67C464C62E51BABABA79CD2D89551 | |||
| 2716 | EasyBCD 2.4.exe | C:\Users\admin\AppData\Local\Temp\nsp5BDD.tmp\modern-wizard.bmp | image | |
MD5:1ED71CEF099AE50505B5F495CC50E2A2 | SHA256:B177ADA6638B5869390C39405CAF5BEF6FA74AFAFE00BCD14DE5282867E47A26 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
29
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6428 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2532 | EasyBCD.exe | GET | 302 | 65.182.170.12:80 | http://feeds.neosmart.net/neosmart | unknown | — | — | whitelisted |
6428 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2532 | EasyBCD.exe | GET | — | 142.250.186.179:80 | http://rss.neosmart.net/neosmart | unknown | — | — | whitelisted |
4860 | msfeedssync.exe | GET | 302 | 65.182.170.12:80 | http://feeds.neosmart.net/neosmart | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
4860 | msfeedssync.exe | GET | 200 | 142.250.186.179:80 | http://rss.neosmart.net/neosmart | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4844 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3944 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3944 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2532 | EasyBCD.exe | Misc activity | ET INFO Observed UA-CPU Header |