| File name: | Chew7.exe |
| Full analysis: | https://app.any.run/tasks/633c7f35-22ac-4433-8808-62049be1fa75 |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2019, 05:53:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 7B232997942B2A5C7E4DBE931BB4C67C |
| SHA1: | 06C6D3B5B66585F03BAB25C774BAADB575CB1515 |
| SHA256: | 0A88FAA27484C7C163BC90FBF806A9DAB84226C2F60F3410695278EE76D065F5 |
| SSDEEP: | 98304:6BkL7VOQCsDdOmYglo4Y14pygKq7VOQCsDdOmYglo4Y14pygK:6OLPLDVYglq1pqPLDVYglq1p |
MALICIOUS
Application was dropped or rewritten from another process
- hale.exe (PID: 2580)
SUSPICIOUS
Uses TASKKILL.EXE to kill process
- Chew7.exe (PID: 3760)
Application launched itself
- cmd.exe (PID: 3692)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3692)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 2708)
- cmd.exe (PID: 3480)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3692)
- hale.exe (PID: 2580)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 3692)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 3692)
Creates files in the Windows directory
- Chew7.exe (PID: 3760)
Executable content was dropped or overwritten
- hale.exe (PID: 2580)
- Chew7.exe (PID: 3760)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (43.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (16.2) |
| .exe | | | UPX compressed Win32 Executable (15.9) |
| .exe | | | Win32 EXE Yoda's Crypter (15.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:08:01 23:59:57+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 4696576 |
| InitializedDataSize: | 108032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x47c7fe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.6.8.4 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
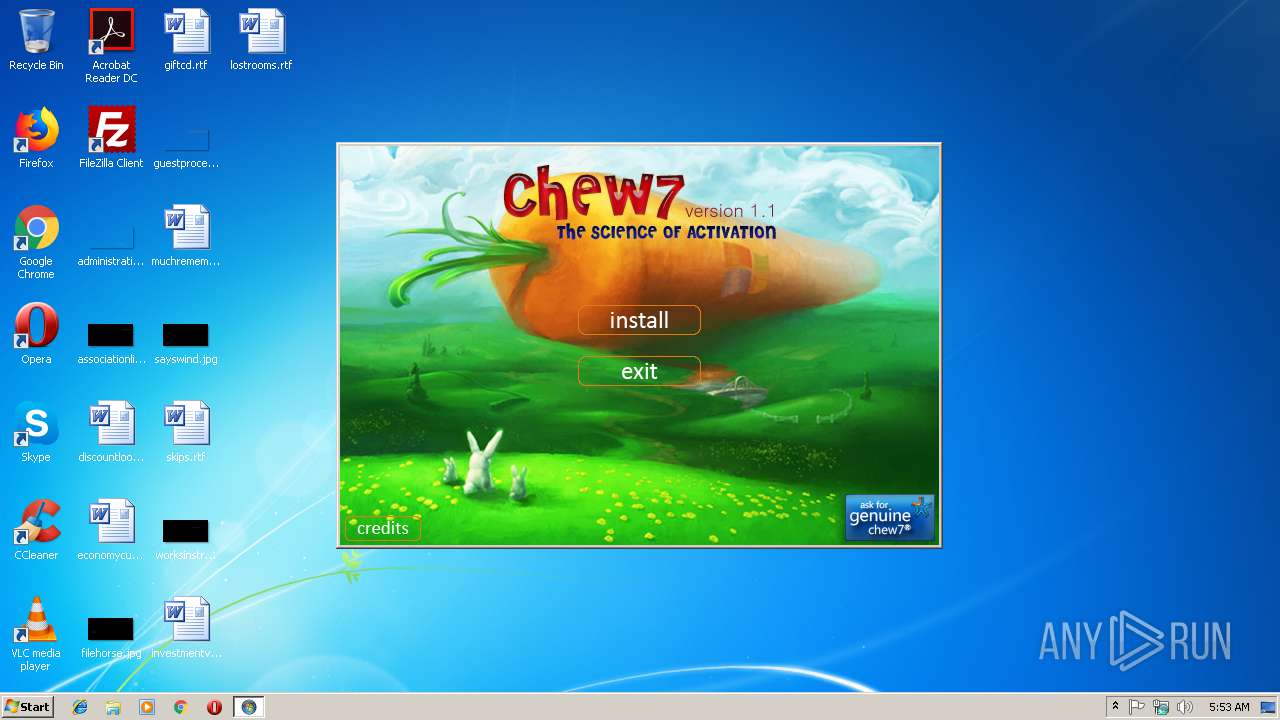
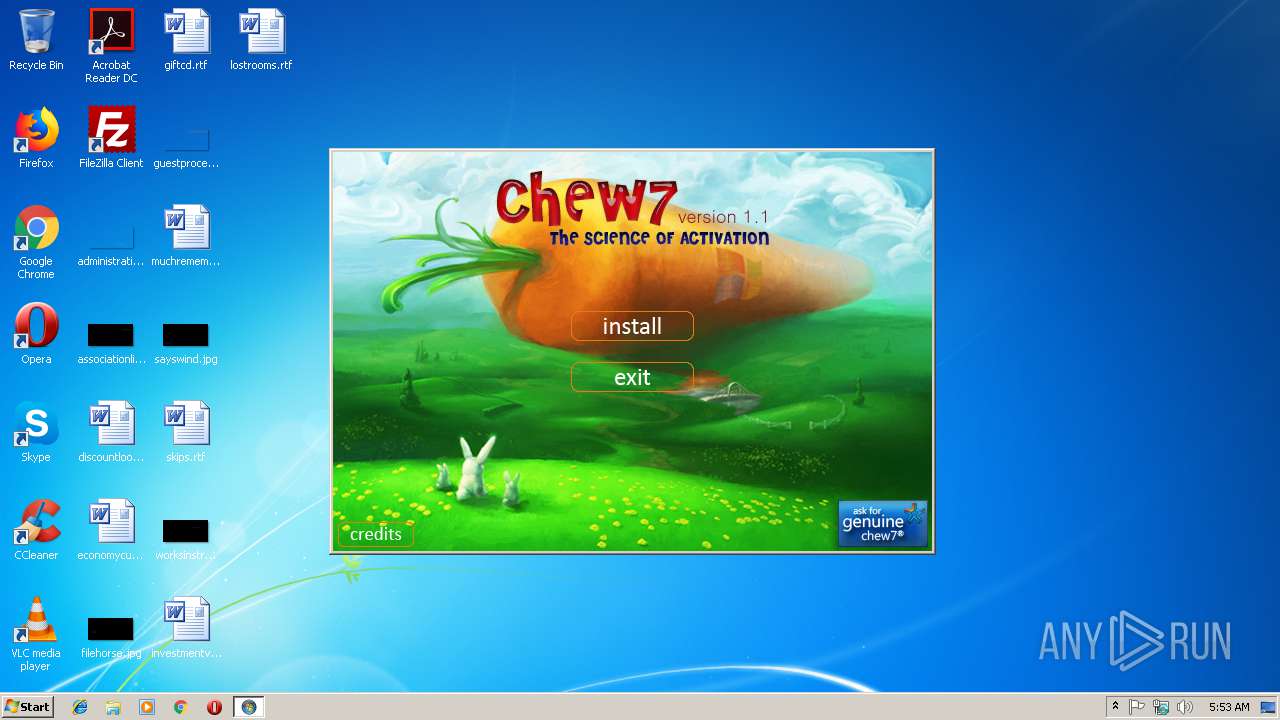
| FileDescription: | The Science of Activation |
| FileVersion: | 0.6.8.4 |
| InternalName: | Chew7.exe |
| LegalCopyright: | © Chew7. All rights reserved. |
| OriginalFileName: | Chew7.exe |
| ProductName: | Chew7 v1.1 |
| ProductVersion: | 1.1.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
67
Monitored processes
31
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
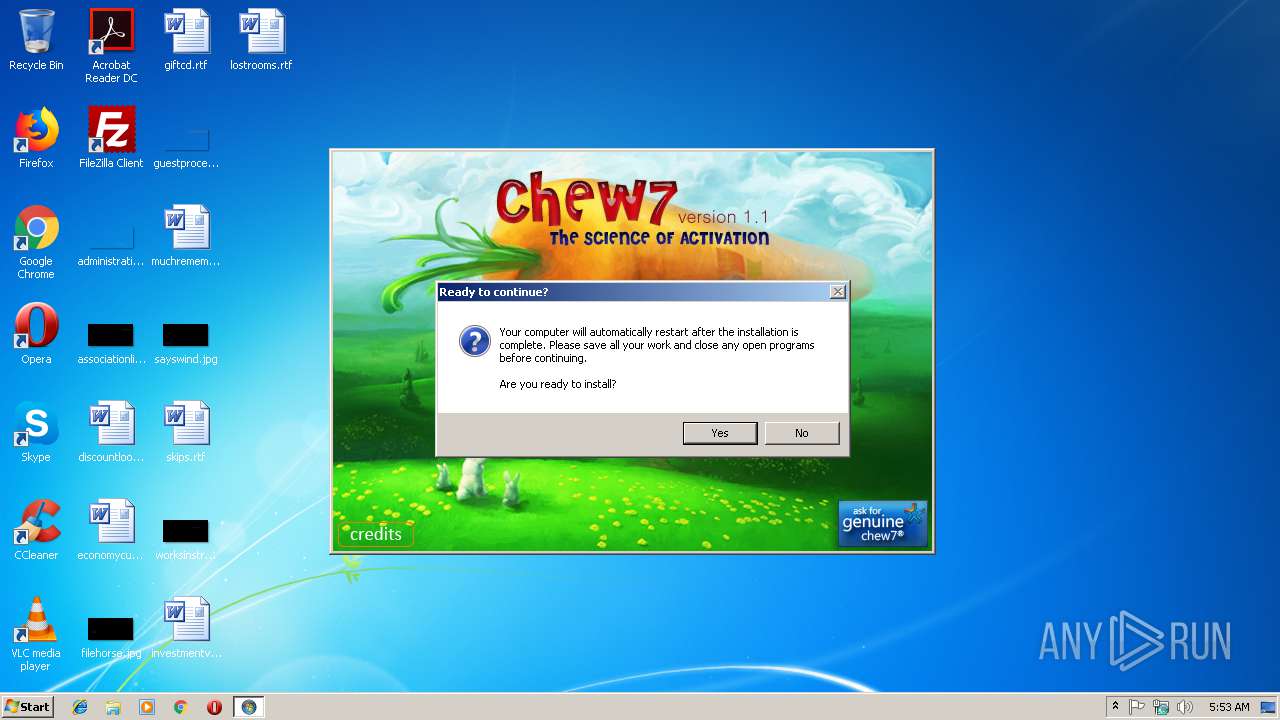
| 760 | REG ADD HKEY_LOCAL_MACHINE\SOFTWARE\Chew7 /v LastAttempt /t REG_SZ /d install /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 760 | C:\Windows\system32\cmd.exe /c TIME /T | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1488 | REG QUERY HKEY_LOCAL_MACHINE\SOFTWARE\Chew7 /v CWInstalled | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | REG QUERY HKLM\SYSTEM\CurrentControlSet\Control\TimeZoneInformation /v TimeZoneKeyName | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2492 | C:\Windows\system32\cmd.exe /S /D /c" ECHO.x86" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2536 | TASKLIST /FI "IMAGENAME eq Chew7.exe" | C:\Windows\system32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2560 | FIND "64" | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2580 | "C:\Windows\system32\hale.exe" | C:\Windows\system32\hale.exe | Chew7.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2620 | REG QUERY HKEY_LOCAL_MACHINE\SOFTWARE | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2684 | "C:\Windows\System32\taskkill.exe" /f /im cmd.exe | C:\Windows\System32\taskkill.exe | — | Chew7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
463
Read events
453
Write events
10
Delete events
0
Modification events
| (PID) Process: | (3760) Chew7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3760) Chew7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2972) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Chew7 |
| Operation: | write | Name: | |
Value: | |||
| (PID) Process: | (2580) hale.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2580) hale.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (760) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Chew7 |
| Operation: | write | Name: | LastAttempt |
Value: install | |||
Executable files
11
Suspicious files
0
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\bump.exe | executable | |
MD5:2D9A30606A718BFDB4E5E9B6C2939881 | SHA256:1F57F10A0B2C52BB6F89504E047854502E42EBF9F6153A1A4549A55099F98B51 | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\hale.cmd | text | |
MD5:6CE66570BFAB35A20D280D9833049E97 | SHA256:C755237B5C58134FF21520F7D2D401E5C9AD40D05DC76FE317FFD238ECAFECF2 | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\ownc.cmd | text | |
MD5:F16F9A87E6A9F18921A30AC379B81995 | SHA256:9177BAC8288A592264DD90D2C956433A8818F1A34A5D864BD626DF3FDE0E0CFA | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\lhed.cmd | text | |
MD5:34670DB25D9AFD4F3912F77F2E5C7D08 | SHA256:A4761B5A5F5E6542867BA1CAA87676410B7AEDCCD762826359046167771659FF | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\plog.cmd | text | |
MD5:D638644C3BB80F1E98AE06FA85680EB1 | SHA256:E8A990623424631496704087D29F05300BC5EFABB47C94FFE7F6BD46D803B587 | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\setv.cmd | text | |
MD5:ADBB4C4121D770EFC7154F06FE476A42 | SHA256:6A8233F58DCDFFD51292B753688848198982C5DE11945651F165D1174E570372 | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\radd.cmd | text | |
MD5:0CA0566671854F45D316877CB3B9563B | SHA256:048E766FFD49A6EA2FE280DC3F949C1173B439B0367137972FB6F8196C6AD8F3 | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\mtmp.cmd | text | |
MD5:02D7EBAD35B5624A751243D101A540CE | SHA256:7686C1B97D3F80D042AAC35D82B5E5B558A494AE3E0E35DE81A47C413D9020AC | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\pendx.cmd | text | |
MD5:3AF31A071967EC43A0AC6E3605FF1D8C | SHA256:A0197323DA44005AEC9726CABAEE9F1027FA07EB5367F3FCEAAD05E3728C0324 | |||
| 2580 | hale.exe | C:\Users\admin\AppData\Local\Temp\3121.tmp\godo.cmd | text | |
MD5:92CE8CBF009CEA52544956D2CC6A810F | SHA256:89F1E56537B38E367A79C33D75D3A2913FF249D7623363DC48F373EB1B8B14AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report