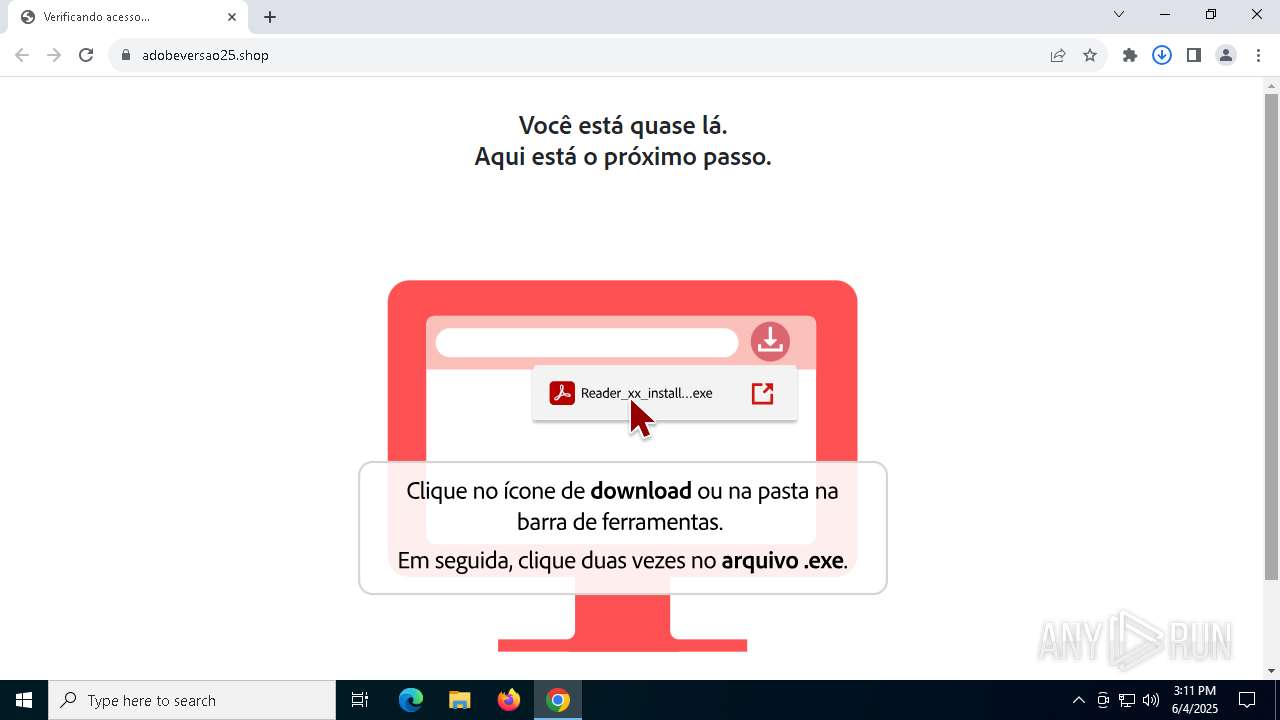
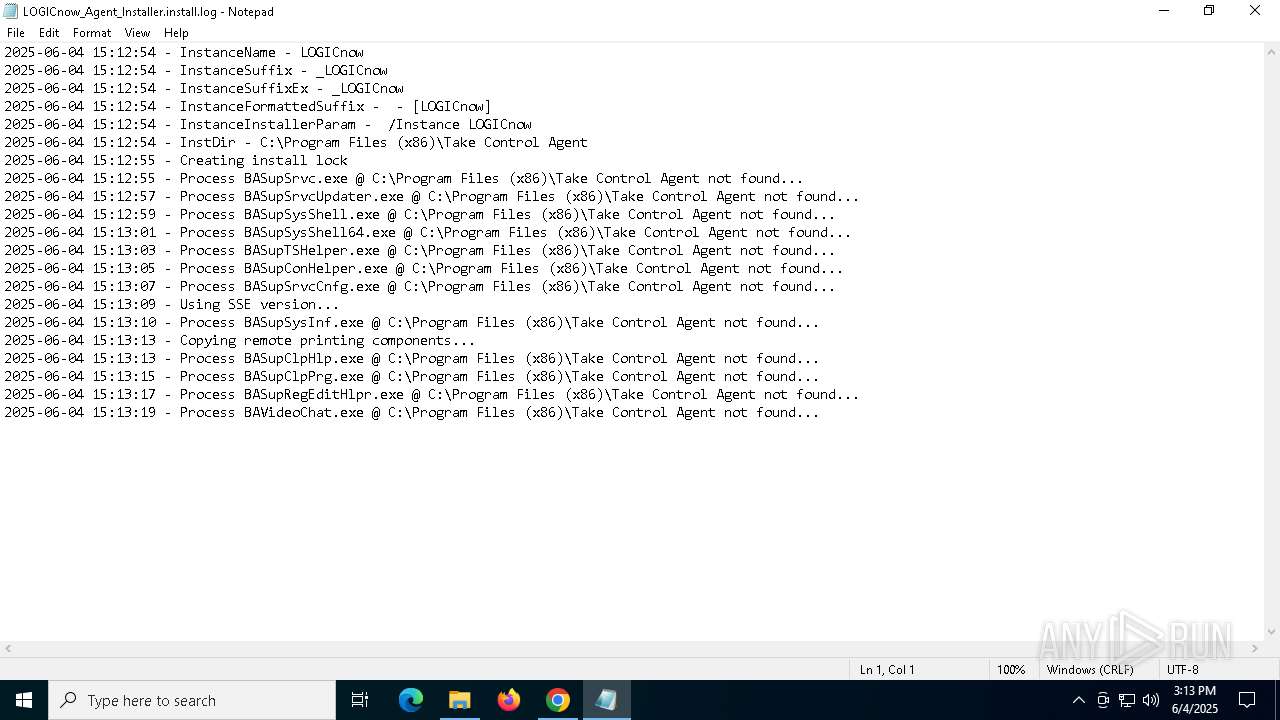
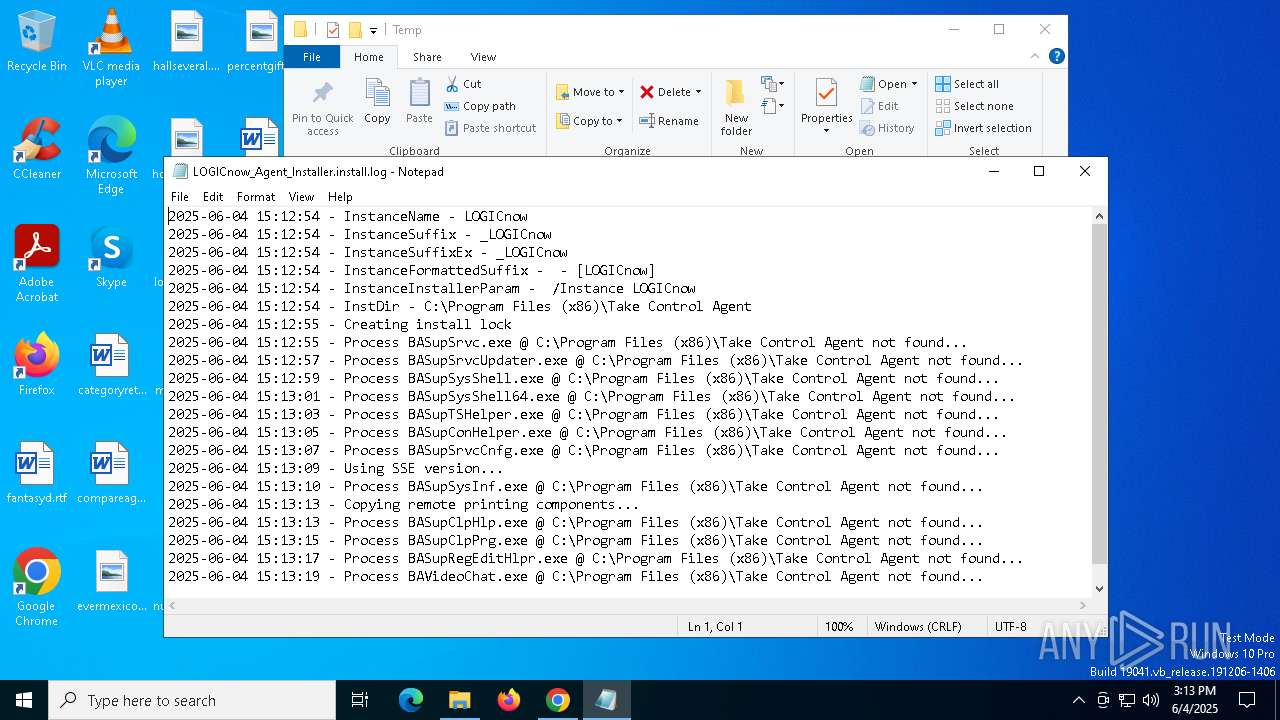
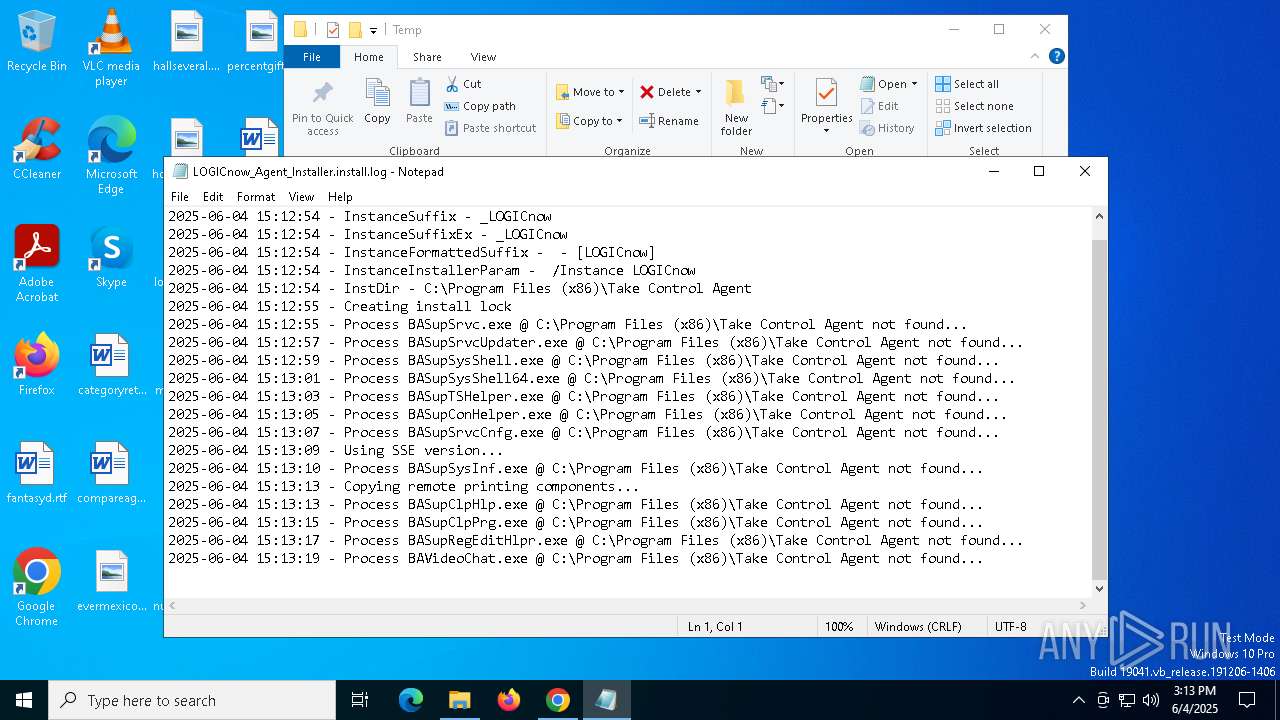
| URL: | https://adobeversao25.shop/ |
| Full analysis: | https://app.any.run/tasks/04d6bc14-4a1c-4772-865f-b8d14d3616aa |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2025, 15:11:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | AE8F94D03907FEBC4064C3897D88E721 |
| SHA1: | A7B3CF83DB89E6E3D38978AF893BD266D8F708EC |
| SHA256: | 0A836E7CF84B703914B98914C7F89AF8362D47B729547333C8813E9E9E016E25 |
| SSDEEP: | 3:N8hgWYl:2ZYl |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
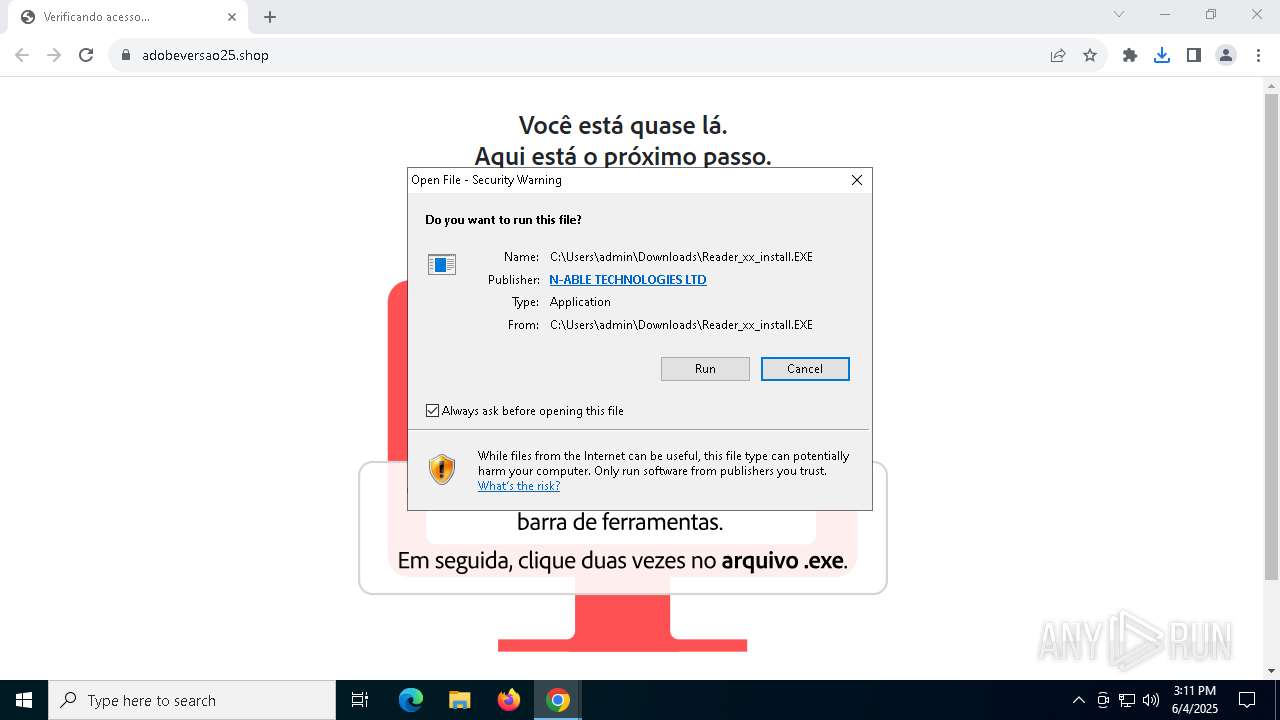
- Reader_xx_install.EXE (PID: 5404)
- agent.tmp (PID: 6792)
Executable content was dropped or overwritten
- Reader_xx_install.EXE (PID: 5404)
- agent.exe (PID: 7932)
- agent.exe (PID: 7272)
- agent.tmp (PID: 7780)
- vcredist_x86.exe (PID: 8184)
- winagent.exe (PID: 2384)
- vcredist_x86.exe (PID: 1764)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7984)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7840)
- ScriptRunner.Installer.exe (PID: 4528)
- msp-agent-core.exe (PID: 7824)
- msp-agent-core-upgrade.exe (PID: 8024)
- winagent.exe (PID: 6560)
- MSP_Connect.exe (PID: 8072)
- RequestHandlerAgentSetup.tmp (PID: 7036)
- RequestHandlerAgentSetup.exe (PID: 3800)
- PMESetup.exe (PID: 2408)
- BASupSrvc.exe (PID: 2840)
- PMESetup.tmp (PID: 7780)
- FileCacheServiceAgentSetup.tmp (PID: 300)
- NetworkManagementInstall.exe (PID: 968)
- NetworkManagementInstall.tmp (PID: 7604)
- FileCacheServiceAgentSetup.exe (PID: 2244)
- FileCacheServiceAgent.exe (PID: 3804)
- NetworkManagement.exe (PID: 7928)
Reads the Windows owner or organization settings
- agent.tmp (PID: 7780)
Process drops legitimate windows executable
- agent.tmp (PID: 7780)
- winagent.exe (PID: 2384)
- vcredist_x86.exe (PID: 8184)
- vcredist_x86.exe (PID: 1764)
- msiexec.exe (PID: 6880)
- MSP_Connect.exe (PID: 8072)
- PMESetup.tmp (PID: 7780)
- RequestHandlerAgentSetup.tmp (PID: 7036)
- NetworkManagementInstall.tmp (PID: 7604)
Application launched itself
- vcredist_x86.exe (PID: 1764)
- TCLauncherHelper.exe (PID: 5600)
- BASupSrvcCnfg.exe (PID: 5952)
Searches for installed software
- vcredist_x86.exe (PID: 1764)
- vcredist_x86.exe (PID: 8184)
- winagent.exe (PID: 2384)
- dllhost.exe (PID: 7936)
Executes as Windows Service
- VSSVC.exe (PID: 5812)
- winagent.exe (PID: 6560)
- msp-agent-core.exe (PID: 7824)
- msp-agent-core.exe (PID: 6488)
- BASupSrvc.exe (PID: 2840)
- RequestHandlerAgent.exe (PID: 8112)
- BASupSrvcUpdater.exe (PID: 3364)
- PME.Agent.exe (PID: 5248)
- FileCacheServiceAgent.exe (PID: 3804)
- NetworkManagement.exe (PID: 7928)
- NetworkManagementAndControl.exe (PID: 7020)
Creates/Modifies COM task schedule object
- winagent.exe (PID: 2384)
The process checks if it is being run in the virtual environment
- winagent.exe (PID: 2384)
There is functionality for taking screenshot (YARA)
- winagent.exe (PID: 2384)
- winagent.exe (PID: 6560)
The process drops C-runtime libraries
- msiexec.exe (PID: 6880)
- MSP_Connect.exe (PID: 8072)
Starts itself from another location
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7840)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 6880)
Executes application which crashes
- winagent.exe (PID: 2384)
Starts CMD.EXE for commands execution
- msp-agent-core.exe (PID: 7636)
- msp-agent-core.exe (PID: 7824)
- msp-agent-core.exe (PID: 7652)
- msp-agent-core.exe (PID: 4776)
- msp-agent-core.exe (PID: 6488)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 8012)
Starts POWERSHELL.EXE for commands execution
- msp-agent-core.exe (PID: 6488)
The process executes via Task Scheduler
- TCLauncherHelper.exe (PID: 5600)
Windows service management via SC.EXE
- sc.exe (PID: 7584)
- sc.exe (PID: 6900)
- sc.exe (PID: 7604)
- sc.exe (PID: 6612)
- sc.exe (PID: 7616)
- sc.exe (PID: 5640)
- sc.exe (PID: 968)
- sc.exe (PID: 5084)
- sc.exe (PID: 5036)
- sc.exe (PID: 7776)
- sc.exe (PID: 960)
- sc.exe (PID: 4028)
Uses ICACLS.EXE to modify access control lists
- RequestHandlerAgentSetup.tmp (PID: 7036)
- FileCacheServiceAgentSetup.tmp (PID: 300)
- PMESetup.tmp (PID: 7780)
Restarts service on failure
- sc.exe (PID: 7768)
- sc.exe (PID: 4016)
- sc.exe (PID: 6500)
- sc.exe (PID: 7480)
Starts SC.EXE for service management
- FileCacheServiceAgent.exe (PID: 6060)
- PME.Agent.exe (PID: 7312)
- NetworkManagement.exe (PID: 4652)
INFO
Application launched itself
- chrome.exe (PID: 2084)
Reads the computer name
- Reader_xx_install.EXE (PID: 5404)
- agent.tmp (PID: 6792)
- agent.tmp (PID: 7780)
- winagent.exe (PID: 2384)
- vcredist_x86.exe (PID: 8184)
- vcredist_x86.exe (PID: 1764)
Launching a file from the Downloads directory
- chrome.exe (PID: 2084)
Executable content was dropped or overwritten
- chrome.exe (PID: 2084)
- msiexec.exe (PID: 6880)
Checks supported languages
- Reader_xx_install.EXE (PID: 5404)
- agent.exe (PID: 7932)
- agent.tmp (PID: 6792)
- agent.exe (PID: 7272)
- agent.tmp (PID: 7780)
- unzip.exe (PID: 716)
- unzip.exe (PID: 7788)
- winagent.exe (PID: 2384)
- vcredist_x86.exe (PID: 1764)
- vcredist_x86.exe (PID: 8184)
Create files in a temporary directory
- agent.exe (PID: 7932)
- Reader_xx_install.EXE (PID: 5404)
- agent.exe (PID: 7272)
- agent.tmp (PID: 7780)
- vcredist_x86.exe (PID: 8184)
Process checks computer location settings
- Reader_xx_install.EXE (PID: 5404)
- agent.tmp (PID: 6792)
Reads Environment values
- winagent.exe (PID: 2384)
Creates a software uninstall entry
- agent.tmp (PID: 7780)
The sample compiled with english language support
- agent.tmp (PID: 7780)
- winagent.exe (PID: 2384)
- vcredist_x86.exe (PID: 8184)
- vcredist_x86.exe (PID: 1764)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7984)
- msiexec.exe (PID: 6880)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7840)
- ScriptRunner.Installer.exe (PID: 4528)
- msp-agent-core-upgrade.exe (PID: 8024)
- msp-agent-core.exe (PID: 7824)
- MSP_Connect.exe (PID: 8072)
- winagent.exe (PID: 6560)
- PMESetup.tmp (PID: 7780)
- NetworkManagementInstall.tmp (PID: 7604)
Creates files in the program directory
- agent.tmp (PID: 7780)
- unzip.exe (PID: 7788)
- winagent.exe (PID: 2384)
Reads product name
- winagent.exe (PID: 2384)
Reads the software policy settings
- winagent.exe (PID: 2384)
The sample compiled with spanish language support
- msiexec.exe (PID: 6880)
The sample compiled with chinese language support
- msiexec.exe (PID: 6880)
The sample compiled with german language support
- msiexec.exe (PID: 6880)
The sample compiled with Italian language support
- msiexec.exe (PID: 6880)
The sample compiled with french language support
- msiexec.exe (PID: 6880)
The sample compiled with japanese language support
- msiexec.exe (PID: 6880)
The sample compiled with korean language support
- msiexec.exe (PID: 6880)
The sample compiled with russian language support
- msiexec.exe (PID: 6880)
Manages system restore points
- SrTasks.exe (PID: 4020)
Checks operating system version
- msp-agent-core.exe (PID: 7824)
- msp-agent-core.exe (PID: 7636)
- msp-agent-core.exe (PID: 4776)
- msp-agent-core.exe (PID: 7652)
- msp-agent-core.exe (PID: 6488)
Manual execution by a user
- notepad.exe (PID: 4528)
SQLite executable
- NetworkManagementInstall.tmp (PID: 7604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
318
Monitored processes
178
Malicious processes
12
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\Take Control Agent\TCLauncherHelper.exe" /start | C:\Program Files (x86)\Take Control Agent\TCLauncherHelper.exe | — | TCLauncherHelper.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TCLauncherHelper Version: 7.50.21.1521 Modules
| |||||||||||||||
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | "C:\WINDOWS\TEMP\is-U0G37.tmp\FileCacheServiceAgentSetup.tmp" /SL5="$50078,2459668,912896,C:\PROGRA~2\ADVANC~1\patchman\Installers\FileCacheServiceAgentSetup.exe" /SP- /VERYSILENT /SUPPRESSMSGBOXES /NORESTART /SKIPDOTNET=0 /DIR="C:\PROGRA~2\ADVANC~1\patchman\..\FileCacheServiceAgent\" /APPLIANCEVERSION=2.13.1.5517 /LOG="C:\PROGRA~2\ADVANC~1\feature_2_install_FileCacheServiceAgent.log" | C:\Windows\Temp\is-U0G37.tmp\FileCacheServiceAgentSetup.tmp | FileCacheServiceAgentSetup.exe | ||||||||||||
User: SYSTEM Company: N-able Integrity Level: SYSTEM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 472 | "C:\Program Files (x86)\MSP Agent\msp-agent-core.exe" --provisioning_state | C:\Program Files (x86)\Msp Agent\msp-agent-core.exe | — | winagent.exe | |||||||||||
User: SYSTEM Company: N-able Technologies, Ltd. Integrity Level: SYSTEM Description: N-able MSP Agent Core Exit code: 0 Modules
| |||||||||||||||
| 496 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 716 | "C:\Program Files (x86)\Advanced Monitoring Agent\unzip.exe" | C:\Program Files (x86)\Advanced Monitoring Agent\unzip.exe | — | agent.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 840 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2384 -s 1932 | C:\Windows\SysWOW64\WerFault.exe | — | winagent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | msp-agent-core.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PME.Agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
115 546
Read events
113 571
Write events
1 900
Delete events
75
Modification events
| (PID) Process: | (2084) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2084) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2084) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2084) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2084) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (8184) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000B24CCAF862D5DB01 | |||
| (PID) Process: | (7780) agent.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Advanced Monitoring Agent_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.3 (a) | |||
| (PID) Process: | (7780) agent.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Advanced Monitoring Agent_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\Advanced Monitoring Agent | |||
| (PID) Process: | (7780) agent.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Advanced Monitoring Agent_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Advanced Monitoring Agent\ | |||
| (PID) Process: | (7780) agent.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Advanced Monitoring Agent_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Advanced Monitoring Agent | |||
Executable files
656
Suspicious files
380
Text files
264
Unknown types
62
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF11f74d.TMP | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF11f75d.TMP | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF11f76d.TMP | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF11f74d.TMP | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF11f79c.TMP | — | |
MD5:— | SHA256:— | |||
| 2084 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
133
DNS requests
70
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.126.133:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.100.102.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2084 | chrome.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
2084 | chrome.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
2084 | chrome.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAa7Qj4Jnq0A09Vb8dNyx3M%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1764 | vcredist_x86.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4616 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1764 | vcredist_x86.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
1764 | vcredist_x86.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.126.133:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.100.102.101:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7560 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2984 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3036 | chrome.exe | 212.85.6.148:443 | adobeversao25.shop | — | GB | unknown |
2084 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
adobeversao25.shop |
| unknown |
accounts.google.com |
| whitelisted |
www.dropbox.com |
| whitelisted |
uc90b44c366dfdd985cc38a4c918.dl.dropboxusercontent.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
NetworkManagement.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\Advanced Monitoring Agent Network Management\x64\SQLite.Interop.dll"...
|
NetworkManagement.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\Advanced Monitoring Agent Network Management\x64\SQLite.Interop.dll"...
|