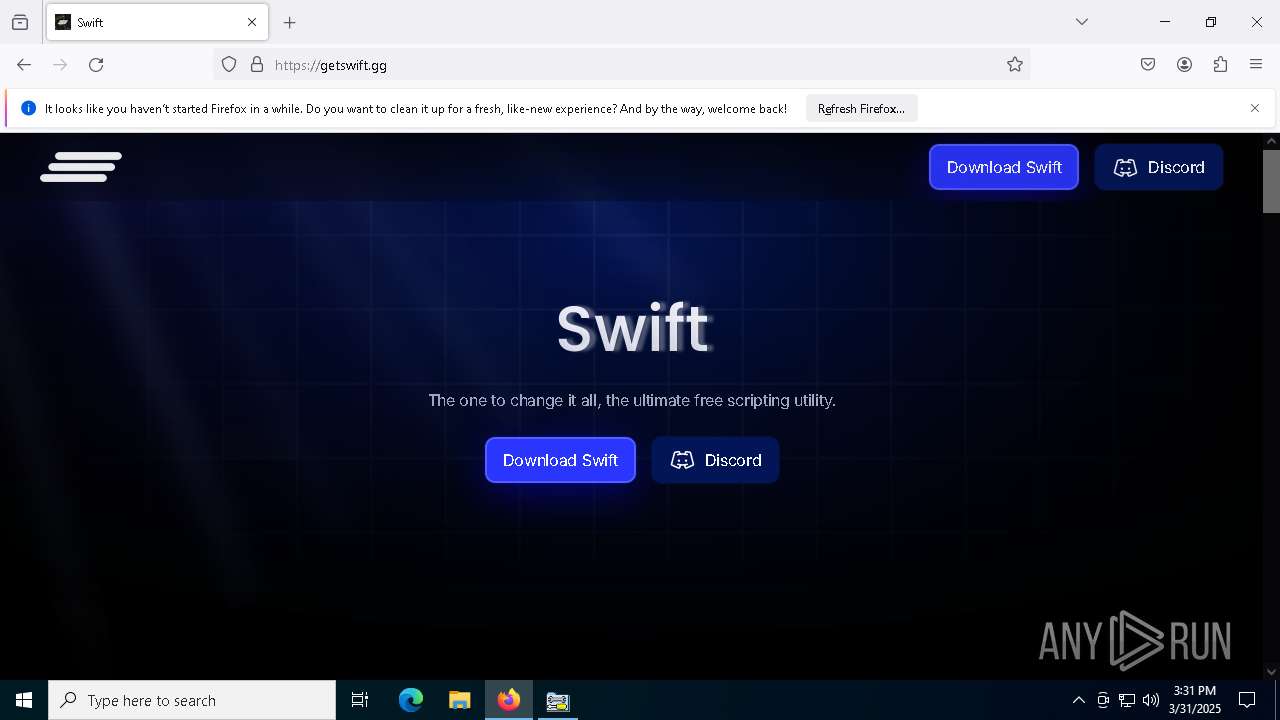
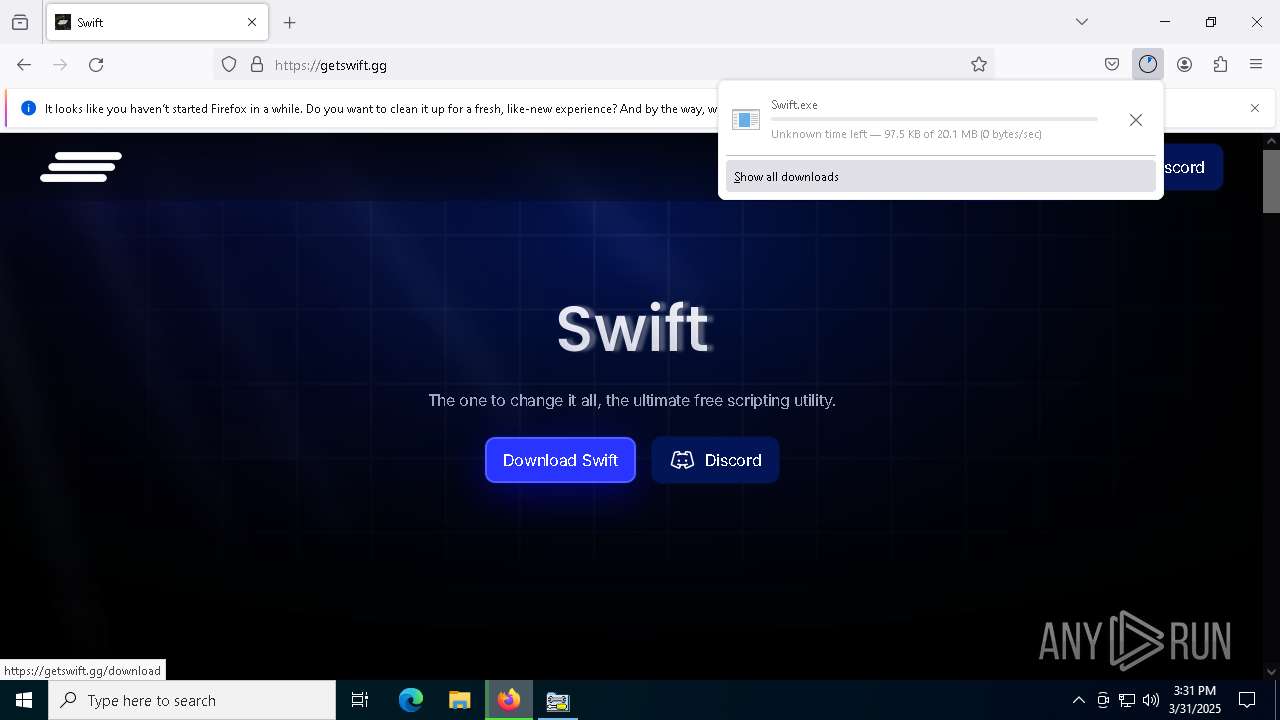
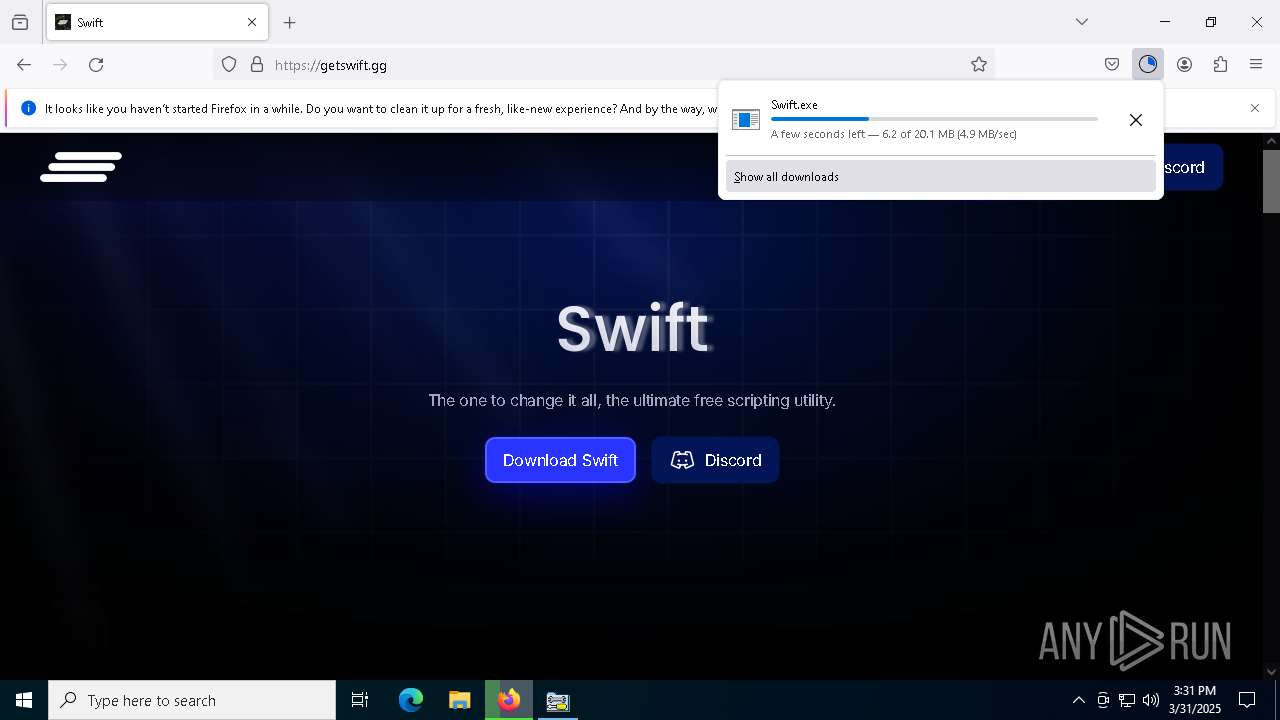
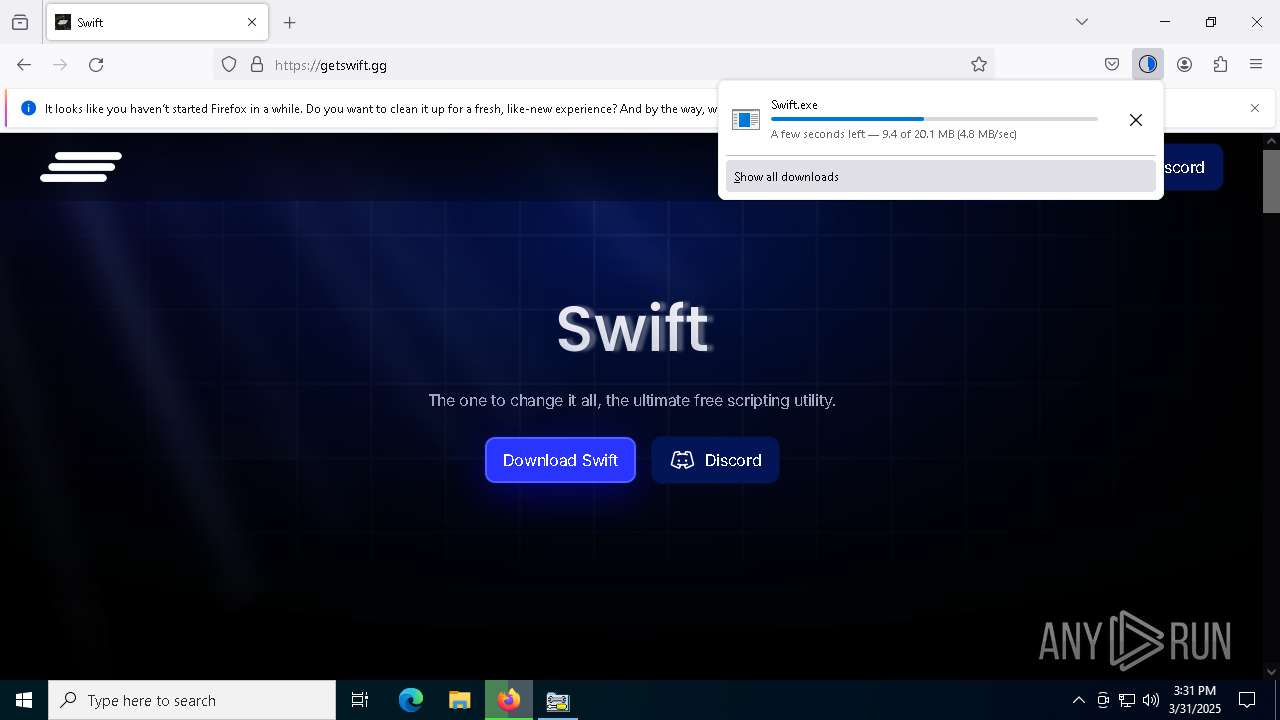
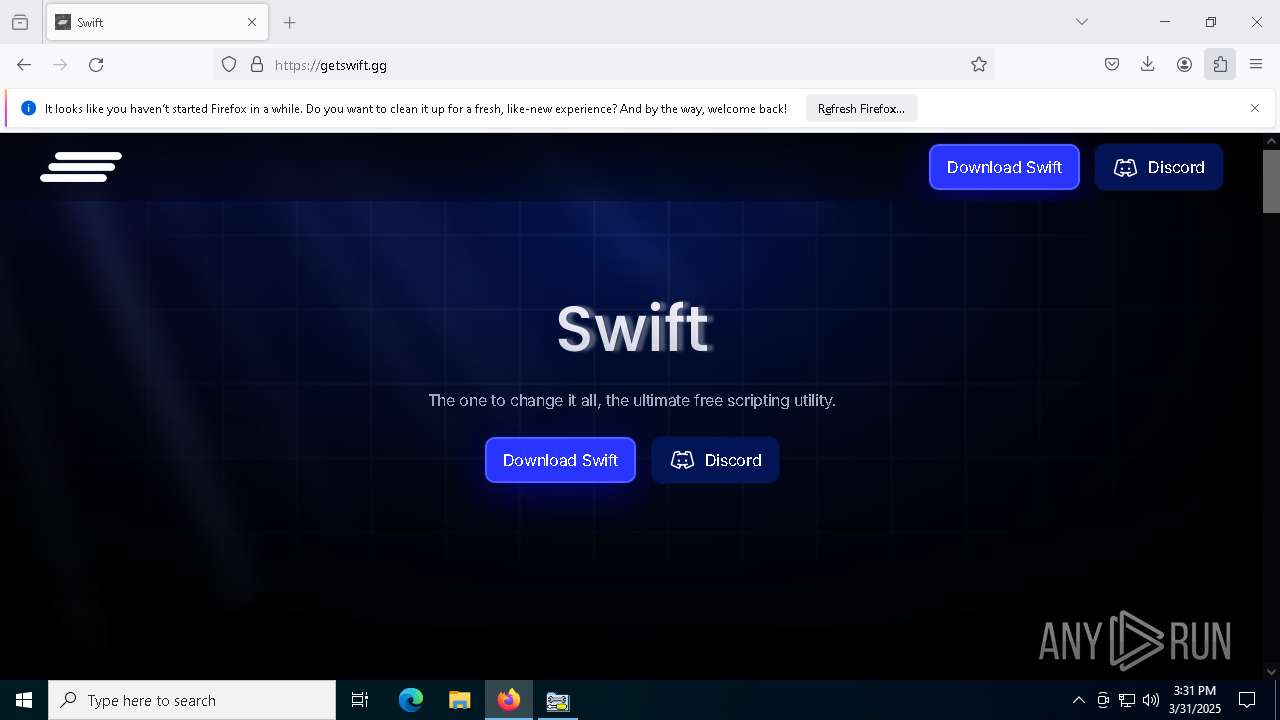
| File name: | TCPOptimizer.exe |
| Full analysis: | https://app.any.run/tasks/3c73c41f-dba8-48bf-9eda-2ca2354bfc23 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2025, 15:31:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | D8292150C8CE862A97A923318DF07805 |
| SHA1: | 917F917FF9FE33E199388E5E1D4C0696882D2991 |
| SHA256: | 0A49DC0D2CE725AF347DF632539B70AFCFD22B38E285920B515143332A5511E9 |
| SSDEEP: | 12288:C1B8g1arhMAURdndzQTEEI7b6Yz3m5W6:pujRdndzQfqb3K |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 5008)
- powershell.exe (PID: 7824)
- powershell.exe (PID: 6108)
- powershell.exe (PID: 644)
- powershell.exe (PID: 3008)
- powershell.exe (PID: 7692)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- Swift.exe (PID: 5776)
- Swift.exe (PID: 496)
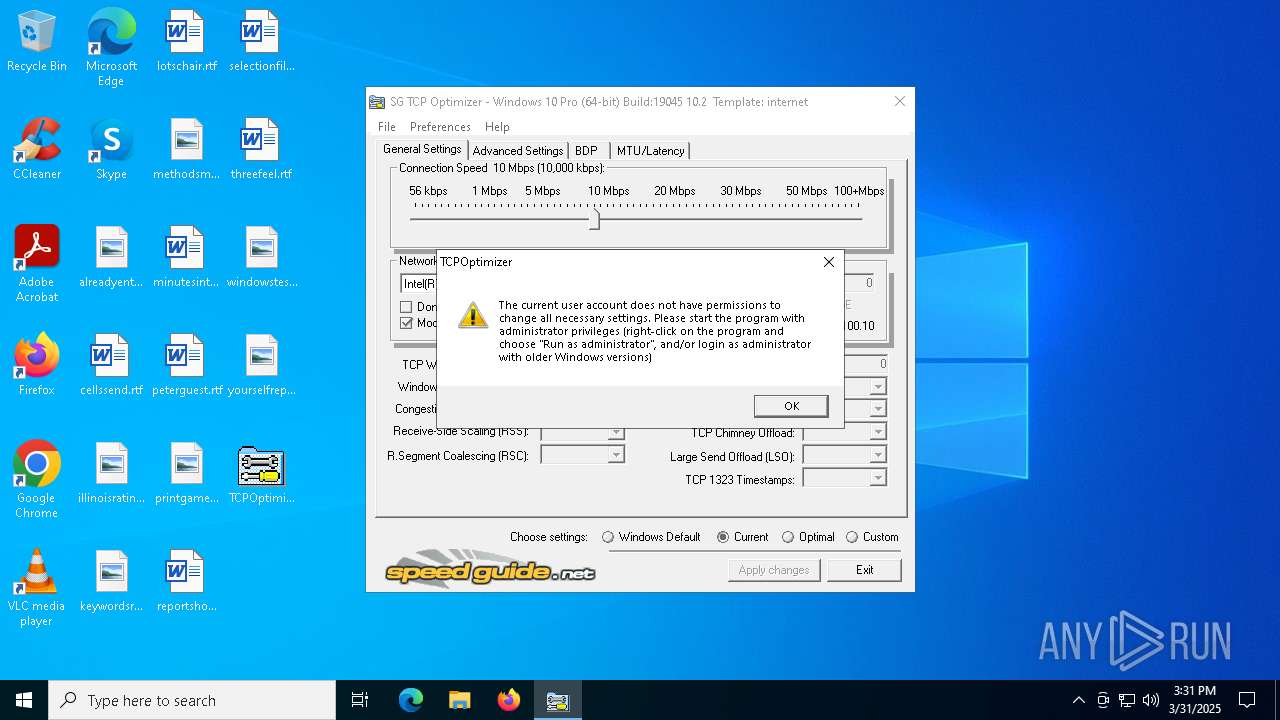
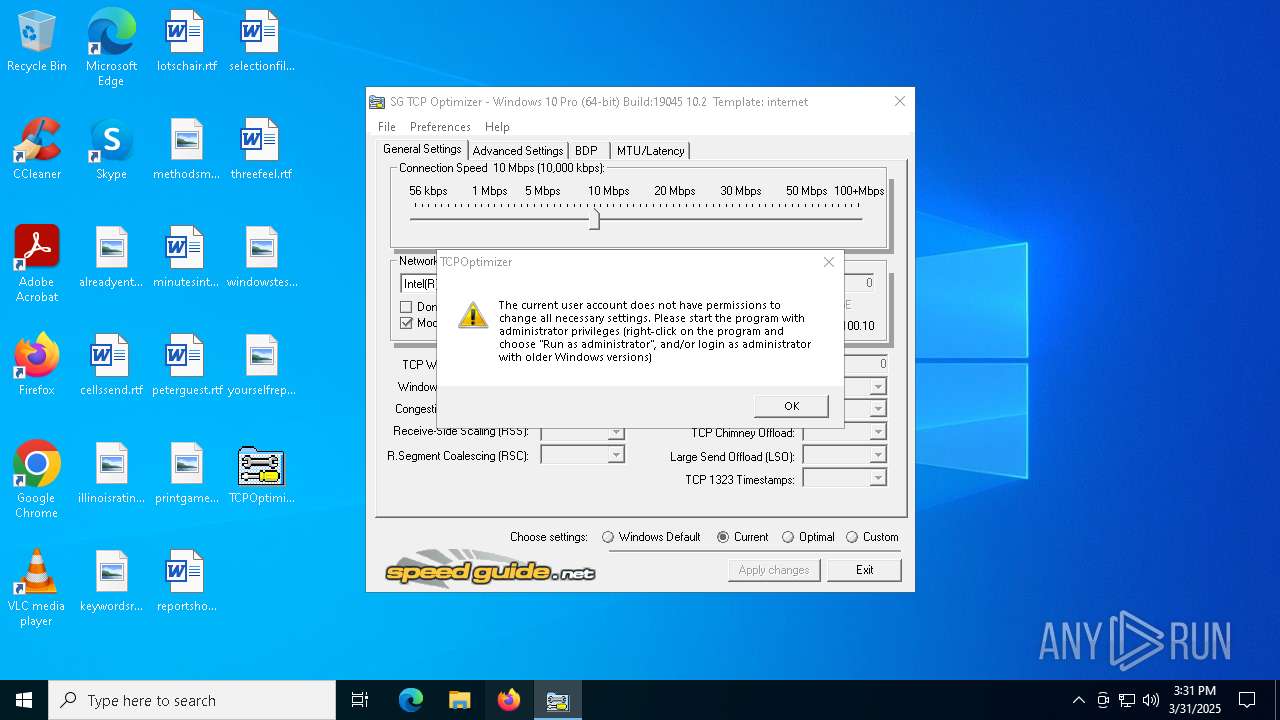
Suspicious use of NETSH.EXE
- TCPOptimizer.exe (PID: 7420)
Reads the BIOS version
- Swift.exe (PID: 5776)
- Swift.exe (PID: 496)
Starts POWERSHELL.EXE for commands execution
- Swift.exe (PID: 496)
- Swift.exe (PID: 5776)
The process hide an interactive prompt from the user
- Swift.exe (PID: 496)
- Swift.exe (PID: 5776)
INFO
Checks supported languages
- TCPOptimizer.exe (PID: 7420)
- Swift.exe (PID: 5776)
- Swift.exe (PID: 496)
The sample compiled with english language support
- TCPOptimizer.exe (PID: 7420)
Manual execution by a user
- Swift.exe (PID: 5776)
- Swift.exe (PID: 3884)
- Swift.exe (PID: 496)
- Swift.exe (PID: 7524)
- firefox.exe (PID: 7828)
Process checks whether UAC notifications are on
- Swift.exe (PID: 5776)
Disables trace logs
- netsh.exe (PID: 7448)
Reads the computer name
- TCPOptimizer.exe (PID: 7420)
- Swift.exe (PID: 5776)
Reads Environment values
- TCPOptimizer.exe (PID: 7420)
Create files in a temporary directory
- TCPOptimizer.exe (PID: 7420)
Application launched itself
- firefox.exe (PID: 7828)
- firefox.exe (PID: 7848)
Autorun file from Downloads
- firefox.exe (PID: 7848)
Reads product name
- TCPOptimizer.exe (PID: 7420)
Executable content was dropped or overwritten
- firefox.exe (PID: 7848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (33) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (23.9) |
| .exe | | | Win64 Executable (generic) (21.2) |
| .scr | | | Windows screen saver (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:01:09 20:32:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 348160 |
| InitializedDataSize: | 720896 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3205f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.1.0 |
| ProductVersionNumber: | 4.1.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Coded and (c) Speed Guide, Inc. - webmaster@speedguide.net / outsorcing@gmail.com |
| CompanyName: | Speed Guide Inc. |
| FileDescription: | SG TCP Optimizer |
| FileVersion: | 4.1.1.0 |
| InternalName: | TCP Optimizer |
| LegalCopyright: | Copyright (c) 2001-2021 |
| LegalTrademarks: | Speed Guide Inc |
| OriginalFileName: | TCPOptimizer.exe |
| ProductName: | SG TCP Optimizer Application |
| ProductVersion: | 4.1.1.0 |
Total processes
162
Monitored processes
34
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | "C:\Users\admin\Downloads\Swift.exe" | C:\Users\admin\Downloads\Swift.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: swift-new Version: 0.1.0 Modules
| |||||||||||||||
| 644 | "powershell" -WindowStyle Hidden -NoProfile -NonInteractive -Command "$WshShell = New-Object -comObject WScript.Shell; $Shortcut = $WshShell.CreateShortcut('C:\Users\admin\Downloads\Scripts.lnk'); $Shortcut.TargetPath = 'C:\Users\admin\AppData\Roaming\Swift\Scripts'; $Shortcut.Save()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Swift.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4212 -childID 2 -isForBrowser -prefsHandle 4224 -prefMapHandle 4220 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1172 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {022b748a-faa0-496e-95cc-36c224d5e6d7} 7848 "\\.\pipe\gecko-crash-server-pipe.7848" 20a07343850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3008 | "powershell" -WindowStyle Hidden -NoProfile -NonInteractive -Command "$WshShell = New-Object -comObject WScript.Shell; $Shortcut = $WshShell.CreateShortcut('C:\Users\admin\Downloads\Workspace.lnk'); $Shortcut.TargetPath = 'C:\Users\admin\AppData\Roaming\Swift\Workspace'; $Shortcut.Save()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Swift.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | "C:\Users\admin\Downloads\Swift.exe" | C:\Users\admin\Downloads\Swift.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: swift-new Exit code: 3221226540 Version: 0.1.0 Modules
| |||||||||||||||
| 4164 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5320 -childID 6 -isForBrowser -prefsHandle 5776 -prefMapHandle 5780 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1172 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9001cd56-139e-4d61-be50-1aadef6920b0} 7848 "\\.\pipe\gecko-crash-server-pipe.7848" 20a03d3fbd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
41 160
Read events
41 152
Write events
8
Delete events
0
Modification events
| (PID) Process: | (7448) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MPRAPI |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7448) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MPRAPI |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7448) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MPRAPI |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7448) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MPRAPI |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7448) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MPRAPI |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7448) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MPRAPI |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7448) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MPRAPI |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7848) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
Executable files
2
Suspicious files
165
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7848 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:8C3F48AA9841CDD6C1B74D85B783CB5A | SHA256:D59161295B5293F05EC7DF8C4CF78AAE12E803C362B918D054D9B32152910BCA | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:EF90022DF0735160DD056C0E6670E915 | SHA256:2B663C0B462A437C8DE3D9B95EE157AE181249B78BDD6F7BD73F7EB6D9E03F87 | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:8B4AF8126E4B16222F212FBE636958DD | SHA256:AA07E227121171B851F7202696A0C00ACB3390A7B8FC222EC81D44FAAD5B9F2C | |||
| 7848 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
104
DNS requests
122
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 184.24.77.47:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 184.24.77.47:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
7848 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.7.2.167:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7848 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | whitelisted |
7848 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
7848 | firefox.exe | 34.36.54.80:443 | ads-img.mozilla.org | — | — | whitelisted |
7848 | firefox.exe | 216.58.212.138:443 | safebrowsing.googleapis.com | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |