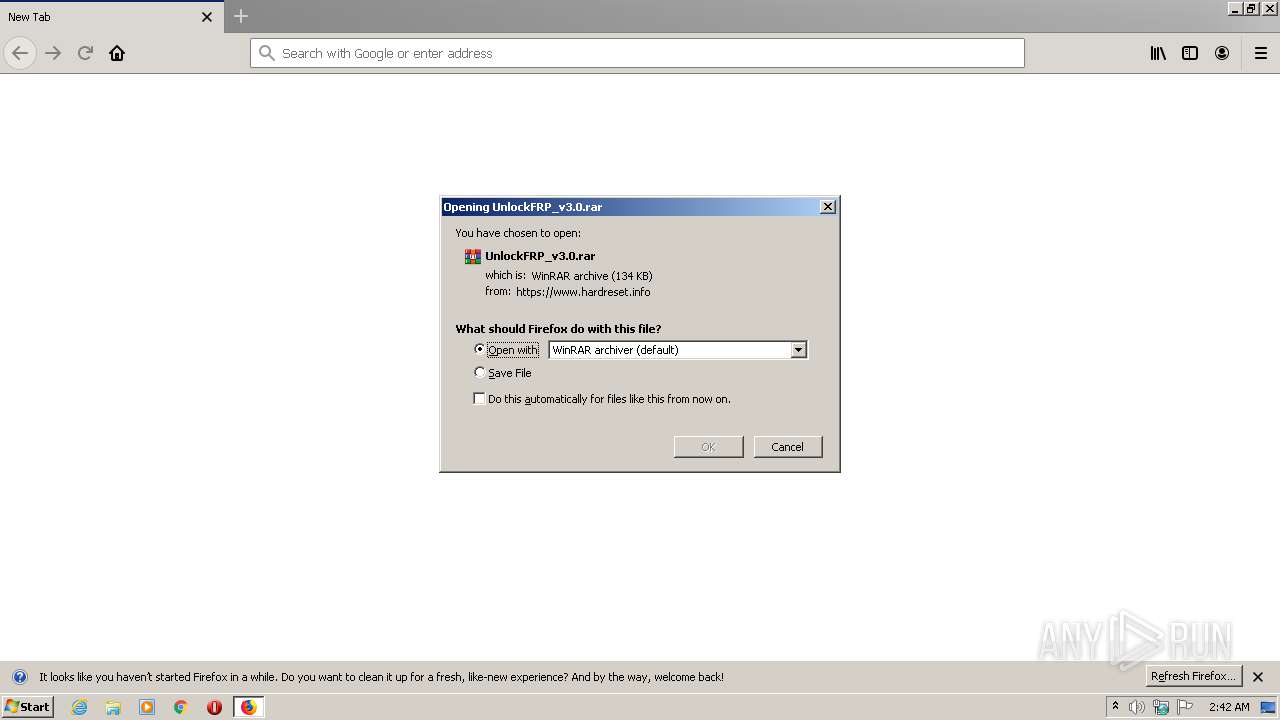
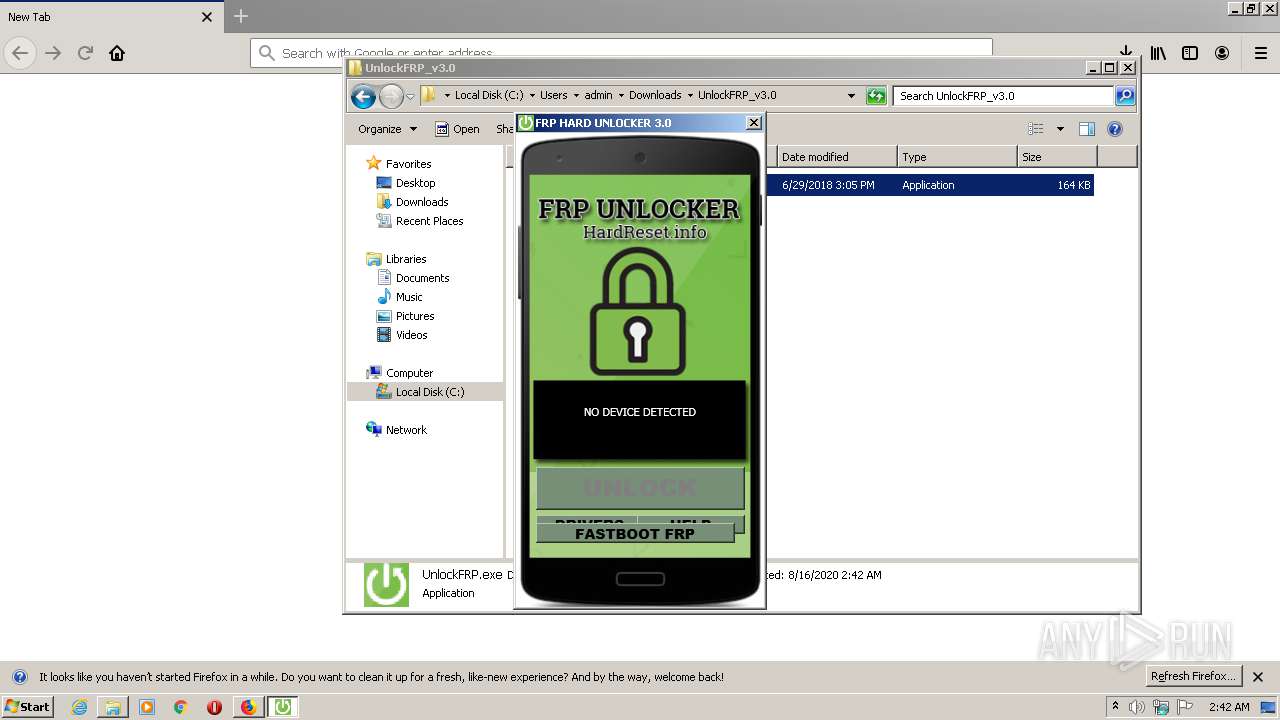
| URL: | https://www.hardreset.info/download/frp-unlocker-ver-30/file/ |
| Full analysis: | https://app.any.run/tasks/12e64bf5-50f3-4c07-8d4a-912fd30e4af1 |
| Verdict: | Malicious activity |
| Analysis date: | August 16, 2020, 01:41:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B52D51423EE7C27A6A02611D24F46124 |
| SHA1: | 3F22E05F74EF5715D3AF5808F8961C15C7FDA935 |
| SHA256: | 0A4913A1DD4F81992909D39D10AF4ED978D4DD7DBA532D6050E54B5EE836B80D |
| SSDEEP: | 3:N8DSLOs0xmh5JdwMXrbl:2OLO0JdwWt |
MALICIOUS
Application was injected by another process
- conhost.exe (PID: 756)
- conhost.exe (PID: 3332)
- conhost.exe (PID: 3836)
- conhost.exe (PID: 1924)
Runs injected code in another process
- UnlockFRP.exe (PID: 2384)
Application was dropped or rewritten from another process
- UnlockFRP.exe (PID: 2384)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 256)
Creates files in the program directory
- firefox.exe (PID: 4060)
Starts CMD.EXE for commands execution
- UnlockFRP.exe (PID: 2384)
INFO
Creates files in the user directory
- firefox.exe (PID: 4060)
Reads CPU info
- firefox.exe (PID: 4060)
Application launched itself
- firefox.exe (PID: 4060)
- firefox.exe (PID: 884)
Reads Internet Cache Settings
- firefox.exe (PID: 4060)
Manual execution by user
- WinRAR.exe (PID: 256)
- UnlockFRP.exe (PID: 2384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
1 105
Monitored processes
541
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 256 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\UnlockFRP_v3.0.rar" C:\Users\admin\Downloads\UnlockFRP_v3.0\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 256 | "cmd" /c adb start-server | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 292 | "cmd" /c adb start-server | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | "cmd" /c adb get-serialno | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 536 | "cmd" /c adb get-serialno | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 556 | "cmd" /c adb get-serialno | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 572 | "cmd" /c adb get-serialno | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | "cmd" /c adb get-serialno | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | "cmd" /c adb kill-server | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 624 | "cmd" /c adb get-serialno | C:\Windows\system32\cmd.exe | — | UnlockFRP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 746
Read events
3 730
Write events
16
Delete events
0
Modification events
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 8084280B00000000 | |||
| (PID) Process: | (884) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 7B84280B00000000 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
1
Suspicious files
73
Text files
35
Unknown types
52
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\cache2\entries\E7AAF7CD127C6ED3483C71BB9427FBCCA43B71E6 | der | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4 | jsonlz4 | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
20
DNS requests
70
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4060 | firefox.exe | POST | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/ | US | der | 472 b | whitelisted |
4060 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4060 | firefox.exe | POST | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
4060 | firefox.exe | POST | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/ | US | der | 472 b | whitelisted |
4060 | firefox.exe | GET | 200 | 2.16.177.18:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
4060 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4060 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4060 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4060 | firefox.exe | GET | 200 | 2.16.177.18:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4060 | firefox.exe | 5.196.55.229:443 | www.hardreset.info | OVH SAS | FR | unknown |
4060 | firefox.exe | 2.16.177.18:80 | detectportal.firefox.com | Akamai International B.V. | — | unknown |
4060 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4060 | firefox.exe | 172.217.22.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
4060 | firefox.exe | 143.204.202.13:443 | content-signature-2.cdn.mozilla.net | — | US | suspicious |
— | — | 172.217.22.67:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
— | — | 44.227.11.155:443 | incoming.telemetry.mozilla.org | University of California, San Diego | US | unknown |
4060 | firefox.exe | 2.16.177.64:443 | shavar.services.mozilla.com | Akamai International B.V. | — | suspicious |
— | — | 143.204.202.106:443 | aus5.mozilla.org | — | US | malicious |
4060 | firefox.exe | 143.204.202.50:443 | snippets.cdn.mozilla.net | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.hardreset.info |
| unknown |
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cs9.wac.phicdn.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |