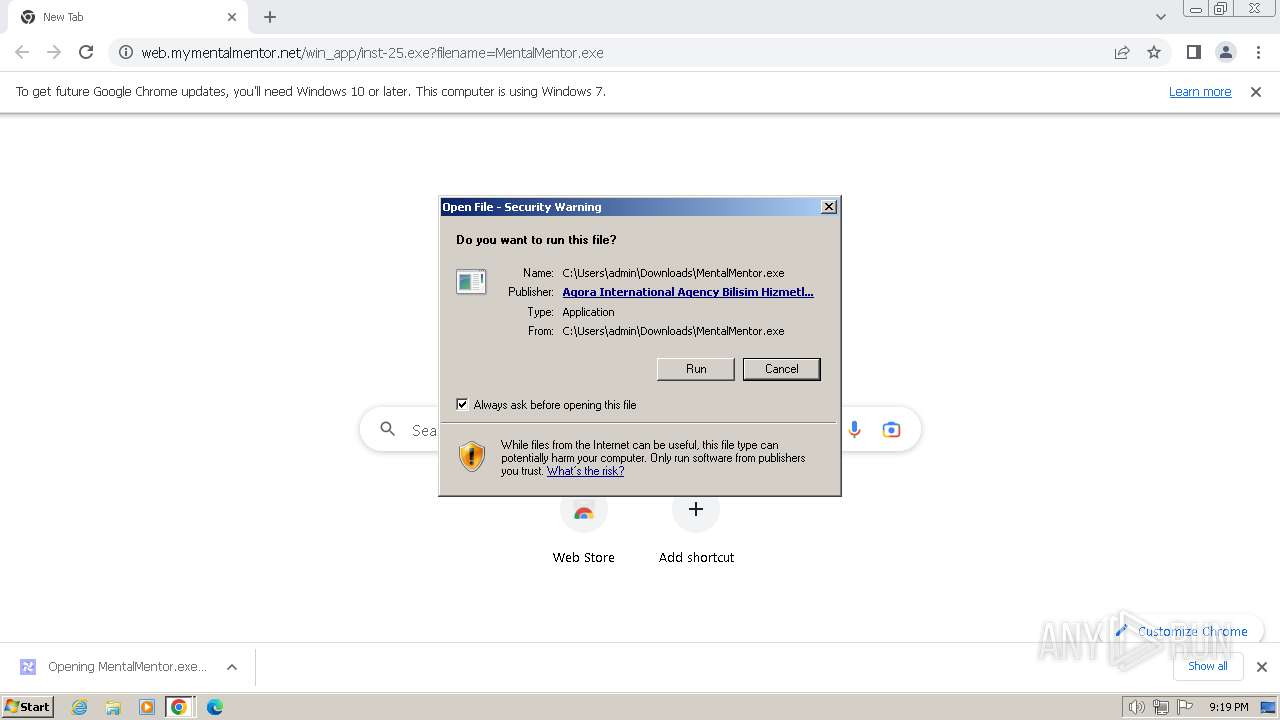
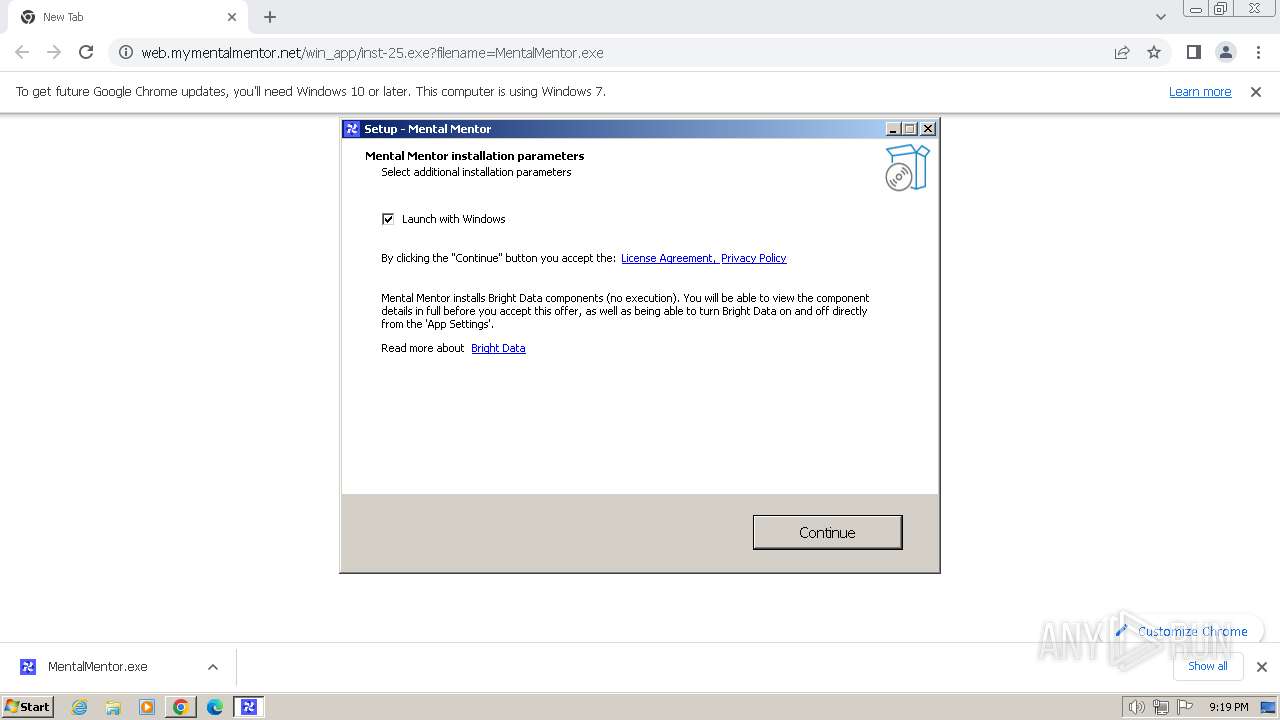
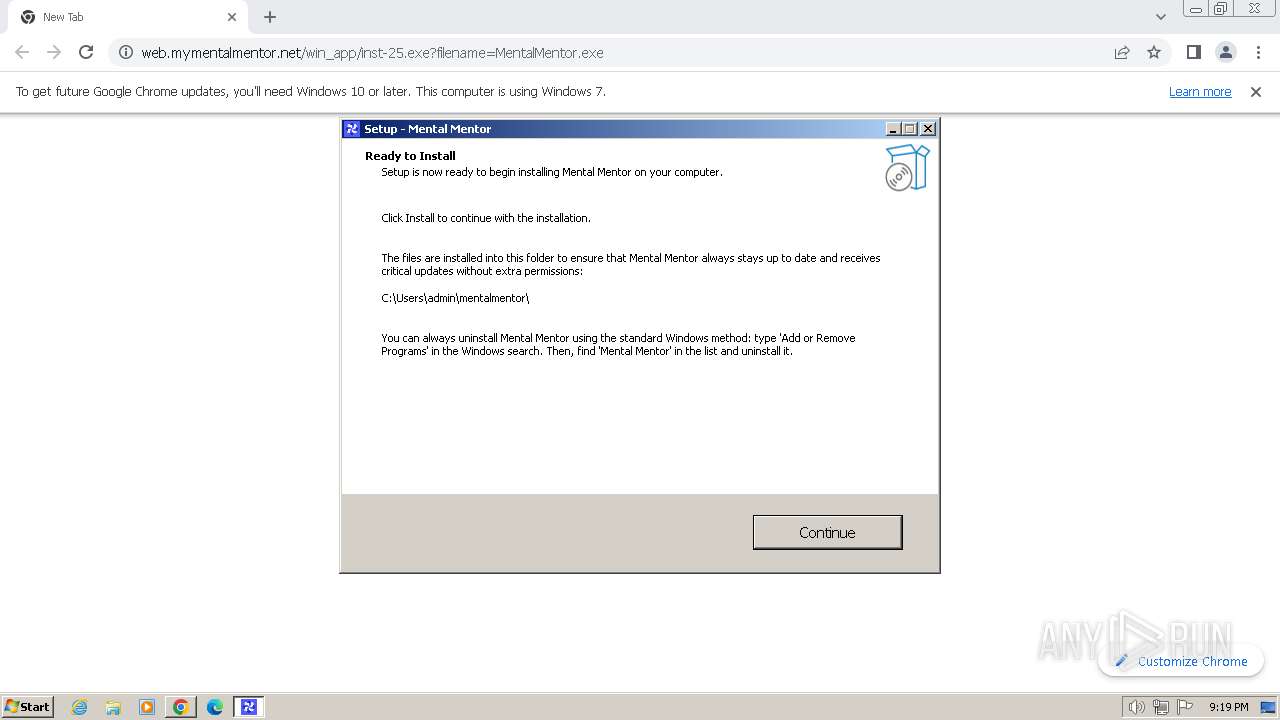
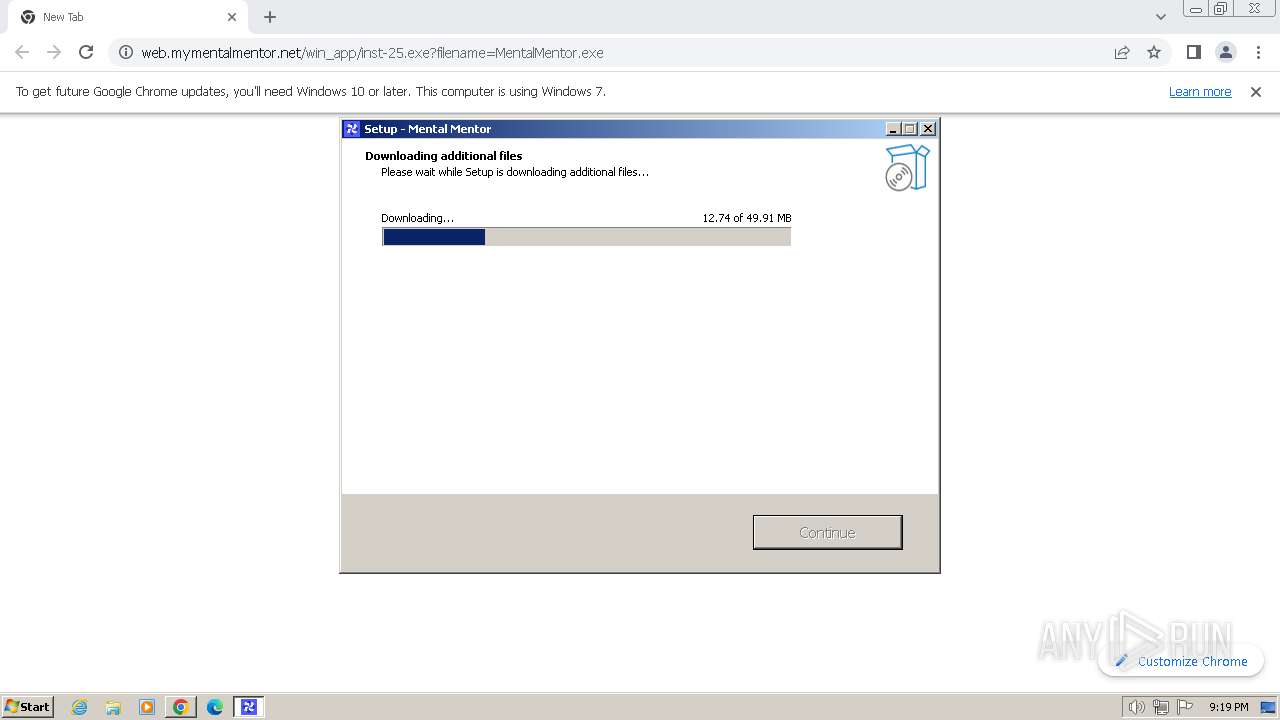
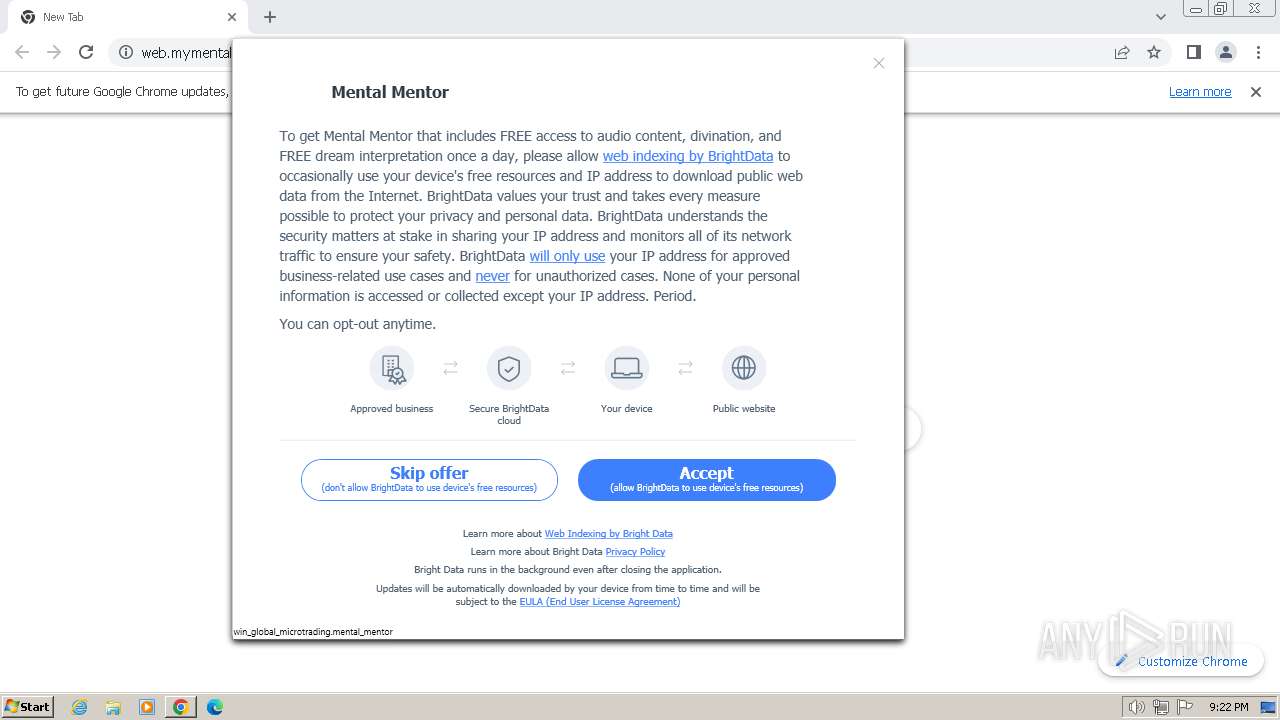
| URL: | https://web.mymentalmentor.net/win_app/inst-25.exe?filename=MentalMentor.exe |
| Full analysis: | https://app.any.run/tasks/eec8e8f7-cb1c-4f9b-964f-8a7887a58491 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2024, 21:18:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FC444E384D2830E1A5539CD56C785B4D |
| SHA1: | 8152A4711FFE2FD994F2F8144807EA6BE2909F0C |
| SHA256: | 0A4682F0715E60C105C262ABFE09A31491566B8DEF370AB3F7C1A47E1A3D1962 |
| SSDEEP: | 3:N8RccIegIACGMryIXe+MOiFeyLsb4A:2KcIrzize+MJLLs4A |
MALICIOUS
Drops the executable file immediately after the start
- MentalMentor.exe (PID: 2028)
- MentalMentor.exe (PID: 2088)
- MentalMentor.tmp (PID: 3380)
- 7z.exe (PID: 2304)
- 7z.exe (PID: 848)
- 7z.exe (PID: 3276)
- luminati.exe (PID: 2416)
Changes the autorun value in the registry
- mentalmentor.exe (PID: 2344)
SUSPICIOUS
Executable content was dropped or overwritten
- MentalMentor.exe (PID: 2028)
- MentalMentor.exe (PID: 2088)
- 7z.exe (PID: 3276)
- MentalMentor.tmp (PID: 3380)
- 7z.exe (PID: 2304)
- 7z.exe (PID: 848)
- luminati.exe (PID: 2416)
Reads the Windows owner or organization settings
- MentalMentor.tmp (PID: 3380)
Process drops legitimate windows executable
- 7z.exe (PID: 3276)
- luminati.exe (PID: 2416)
Drops 7-zip archiver for unpacking
- MentalMentor.tmp (PID: 3380)
Searches for installed software
- MentalMentor.tmp (PID: 3380)
Non-standard symbols in registry
- MentalMentor.tmp (PID: 3380)
Uses NETSH.EXE to add a firewall rule or allowed programs
- MentalMentor.tmp (PID: 3380)
Reads settings of System Certificates
- mentalmentor.exe (PID: 2344)
- luminati.exe (PID: 2416)
- QtWebEngineProcess.exe (PID: 4028)
Reads the Internet Settings
- mentalmentor.exe (PID: 2344)
- luminati.exe (PID: 2416)
- QtWebEngineProcess.exe (PID: 4028)
Reads the date of Windows installation
- mentalmentor.exe (PID: 2344)
Reads security settings of Internet Explorer
- mentalmentor.exe (PID: 2344)
- luminati.exe (PID: 2416)
The process drops C-runtime libraries
- luminati.exe (PID: 2416)
- 7z.exe (PID: 3276)
Detected use of alternative data streams (AltDS)
- luminati.exe (PID: 2416)
Adds/modifies Windows certificates
- luminati.exe (PID: 2416)
- QtWebEngineProcess.exe (PID: 4028)
INFO
Application launched itself
- iexplore.exe (PID: 2472)
- chrome.exe (PID: 3996)
The process uses the downloaded file
- chrome.exe (PID: 3996)
- chrome.exe (PID: 1628)
Executable content was dropped or overwritten
- chrome.exe (PID: 3996)
- chrome.exe (PID: 2184)
- chrome.exe (PID: 1932)
Checks supported languages
- MentalMentor.tmp (PID: 3456)
- MentalMentor.exe (PID: 2088)
- MentalMentor.tmp (PID: 3380)
- 7z.exe (PID: 2304)
- 7z.exe (PID: 3276)
- 7z.exe (PID: 3984)
- mentalmentor.exe (PID: 2344)
- mentalmentor_crashpad_handler.exe (PID: 4080)
- luminati.exe (PID: 2416)
- MentalMentor.exe (PID: 2028)
- test_wpf.exe (PID: 1832)
- QtWebEngineProcess.exe (PID: 4028)
- QtWebEngineProcess.exe (PID: 2972)
- QtWebEngineProcess.exe (PID: 2916)
- 7z.exe (PID: 848)
Reads the computer name
- MentalMentor.tmp (PID: 3456)
- MentalMentor.tmp (PID: 3380)
- mentalmentor.exe (PID: 2344)
- test_wpf.exe (PID: 1832)
- luminati.exe (PID: 2416)
- QtWebEngineProcess.exe (PID: 4028)
Manual execution by a user
- chrome.exe (PID: 3996)
Create files in a temporary directory
- MentalMentor.exe (PID: 2088)
- MentalMentor.exe (PID: 2028)
- MentalMentor.tmp (PID: 3380)
Drops the executable file immediately after the start
- chrome.exe (PID: 3996)
- chrome.exe (PID: 2184)
- chrome.exe (PID: 1932)
Reads the machine GUID from the registry
- MentalMentor.tmp (PID: 3380)
- mentalmentor.exe (PID: 2344)
- luminati.exe (PID: 2416)
- test_wpf.exe (PID: 1832)
- QtWebEngineProcess.exe (PID: 4028)
Creates a software uninstall entry
- MentalMentor.tmp (PID: 3380)
Creates files in the program directory
- luminati.exe (PID: 2416)
Reads Environment values
- luminati.exe (PID: 2416)
Creates files or folders in the user directory
- luminati.exe (PID: 2416)
- QtWebEngineProcess.exe (PID: 4028)
Process checks computer location settings
- luminati.exe (PID: 2416)
- QtWebEngineProcess.exe (PID: 2972)
- QtWebEngineProcess.exe (PID: 2916)
Reads the software policy settings
- luminati.exe (PID: 2416)
- QtWebEngineProcess.exe (PID: 4028)
Checks proxy server information
- luminati.exe (PID: 2416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
38
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3656 --field-trial-handle=1188,i,14182254739943043236,4442498954783631707,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 848 | "C:\Users\admin\AppData\Local\Temp\is-GKNF3.tmp\7z.exe" x "C:\Users\admin\AppData\Local\Temp\is-GKNF3.tmp\zip_lum.7z" -o"C:\Users\admin\mentalmentor\luminati\" * -r -aoa | C:\Users\admin\AppData\Local\Temp\is-GKNF3.tmp\7z.exe | MentalMentor.tmp | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Console Exit code: 0 Version: 9.20 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3980 --field-trial-handle=1188,i,14182254739943043236,4442498954783631707,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2140 --field-trial-handle=1188,i,14182254739943043236,4442498954783631707,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1368 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2132 --field-trial-handle=1188,i,14182254739943043236,4442498954783631707,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1624 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1288 --field-trial-handle=1188,i,14182254739943043236,4442498954783631707,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4264 --field-trial-handle=1188,i,14182254739943043236,4442498954783631707,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3720 --field-trial-handle=1188,i,14182254739943043236,4442498954783631707,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1832 | C:\ProgramData\BrightData\1c38ac4e31598c50e45dd311c7d362929c5fedd9\test_wpf.exe | C:\ProgramData\BrightData\1c38ac4e31598c50e45dd311c7d362929c5fedd9\test_wpf.exe | — | luminati.exe | |||||||||||
User: admin Company: BrightData Ltd. Integrity Level: HIGH Description: test_wpf Exit code: 0 Version: 1.429.308 Modules
| |||||||||||||||
| 1932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3384 --field-trial-handle=1188,i,14182254739943043236,4442498954783631707,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
55 694
Read events
55 130
Write events
488
Delete events
76
Modification events
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31093753 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31093753 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
100
Suspicious files
244
Text files
91
Unknown types
92
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:0ED9B7BBB1FD578A8FF05496457832F9 | SHA256:CCD17654765454DD5C0AE11BFD6D1C45576217FC63CF72AB6F5CDA1D78318385 | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{F76FAD96-DFEC-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:53D00A25AE6894F129060D0EE85049C7 | SHA256:3EDDAF872D9E1BE543512D4D854F272F82A6DAB10179ABB92C53201605098A4B | |||
| 3996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF182621.TMP | — | |
MD5:— | SHA256:— | |||
| 3996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E59DA8D379DF4DC5C480E8704022897F | SHA256:19A3819D00C72A070589B6902461016372BF18FDA5C6937BA7053457D8FC697E | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{F76FAD95-DFEC-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:C37B2F4D30EFB977DFB82C1683DD7326 | SHA256:547EB77D4E229D17BB06D1B62ADE5217250B514840608741ADEE301456CB4BE1 | |||
| 3996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB1059A4D930F45B5.TMP | gmc | |
MD5:F894E51931CF24556745A4327C67ED7E | SHA256:22446BB16E806DB389BE628B396D33629F4200F6B8ABC78B6217703527E7A80D | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
98
DNS requests
79
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2472 | iexplore.exe | GET | 304 | 178.79.242.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bdc5ae628aaf0bd4 | unknown | — | — | unknown |
2472 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
2472 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2472 | iexplore.exe | GET | 304 | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4dd617501e33218a | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 28.9 Kb | unknown |
1080 | svchost.exe | GET | 200 | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1dd404ff67a3d8ee | unknown | compressed | 67.5 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 37.2 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 20.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 46.3 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | binary | 23.4 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3348 | iexplore.exe | 51.158.210.166:443 | web.mymentalmentor.net | Online S.a.s. | FR | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2472 | iexplore.exe | 104.126.37.176:443 | www.bing.com | Akamai International B.V. | DE | unknown |
2472 | iexplore.exe | 95.140.236.0:80 | ctldl.windowsupdate.com | LLNW | US | whitelisted |
2472 | iexplore.exe | 178.79.242.128:80 | ctldl.windowsupdate.com | LLNW | DE | unknown |
2472 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3996 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
web.mymentalmentor.net |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2184 | chrome.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
Process | Message |
|---|---|
mentalmentor.exe | QWindowsEGLStaticContext::create: Could not initialize EGL display: error 0x3001
|
mentalmentor.exe | QWindowsEGLStaticContext::create: When using ANGLE, check if d3dcompiler_4x.dll is available
|