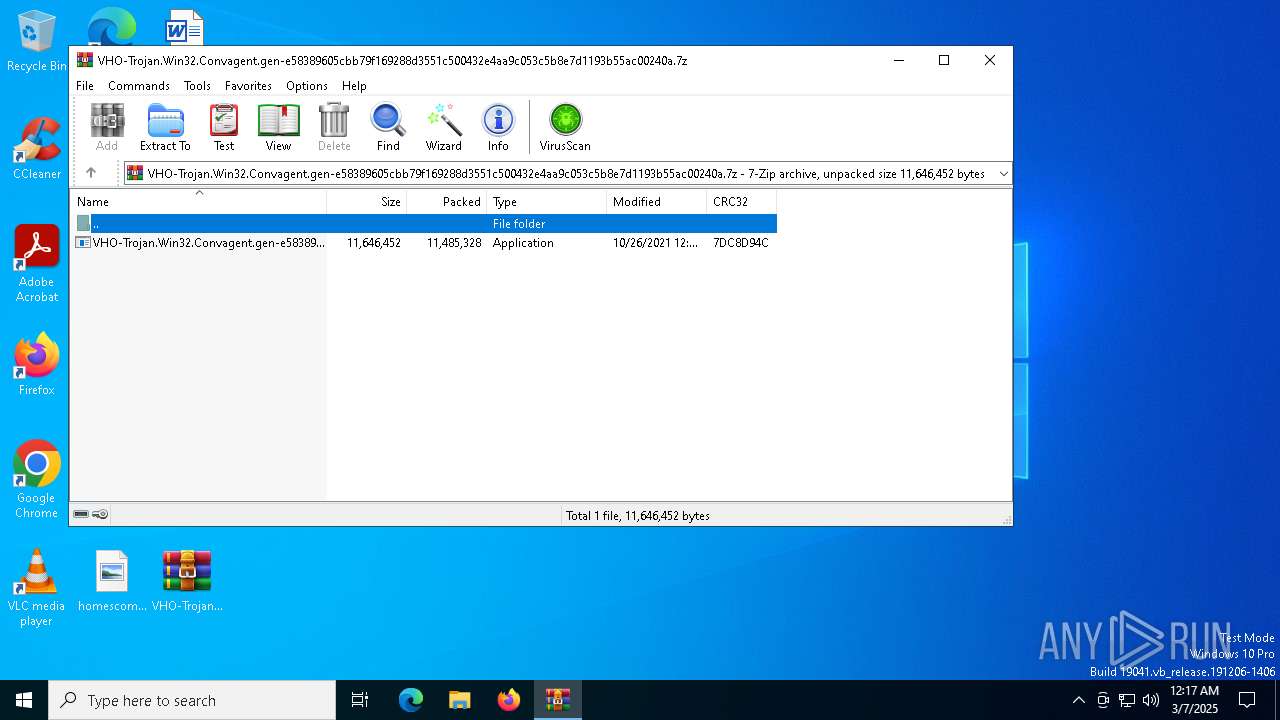
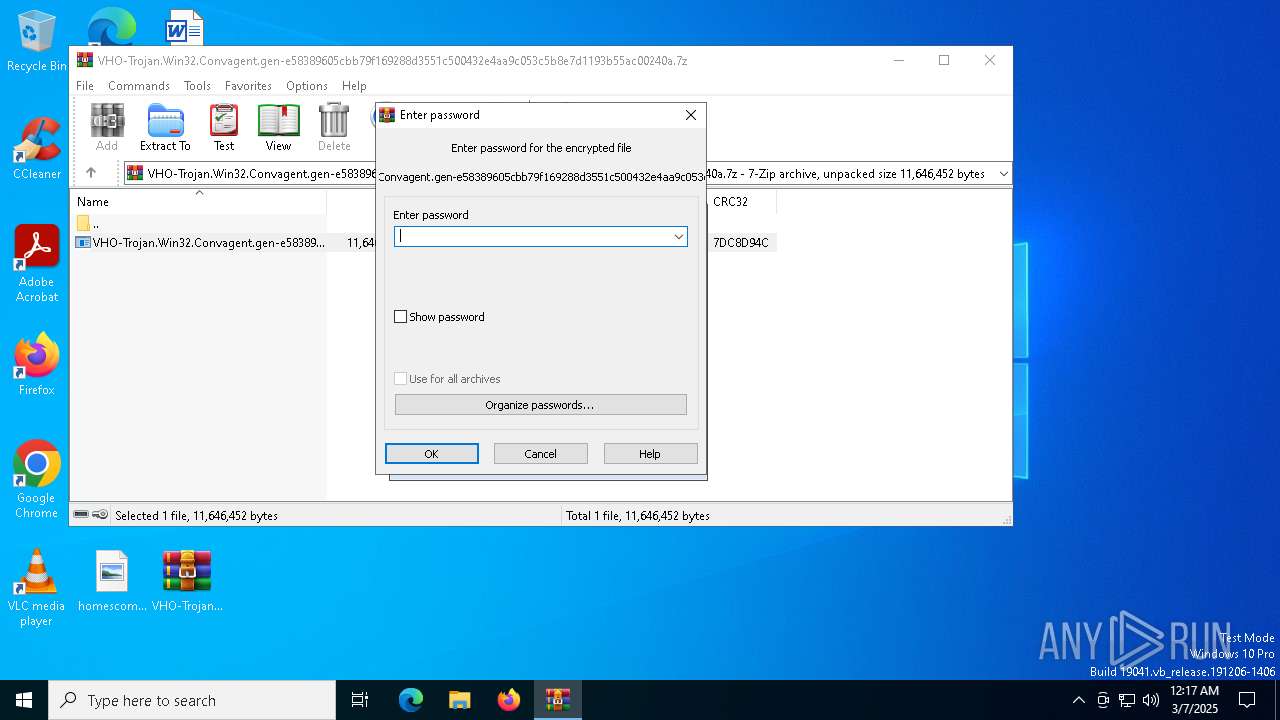
| File name: | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.7z |
| Full analysis: | https://app.any.run/tasks/d893e651-adbb-42bf-bc09-d70e72389a4c |
| Verdict: | Malicious activity |
| Analysis date: | March 07, 2025, 00:17:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | EAEC7783D65C903F3DEB1603642FA176 |
| SHA1: | 1FF5BB3E5493C5D92CA258E224CD8FBBA32322C5 |
| SHA256: | 0A335A2933D1E55EC3DC55ABF8588C3378F4C0FAA6F168F02EA4B661F7F01FB9 |
| SSDEEP: | 98304:ODY+5vGivtd6KgGl1a/FCMOI9JW1WFyrtC2I0Gp36x5w8eZP9CKhT+T/uJCrAPas:AYJmDnpqxVuupYqkZ9mJY4yLhBKAWUeZ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2568)
SUSPICIOUS
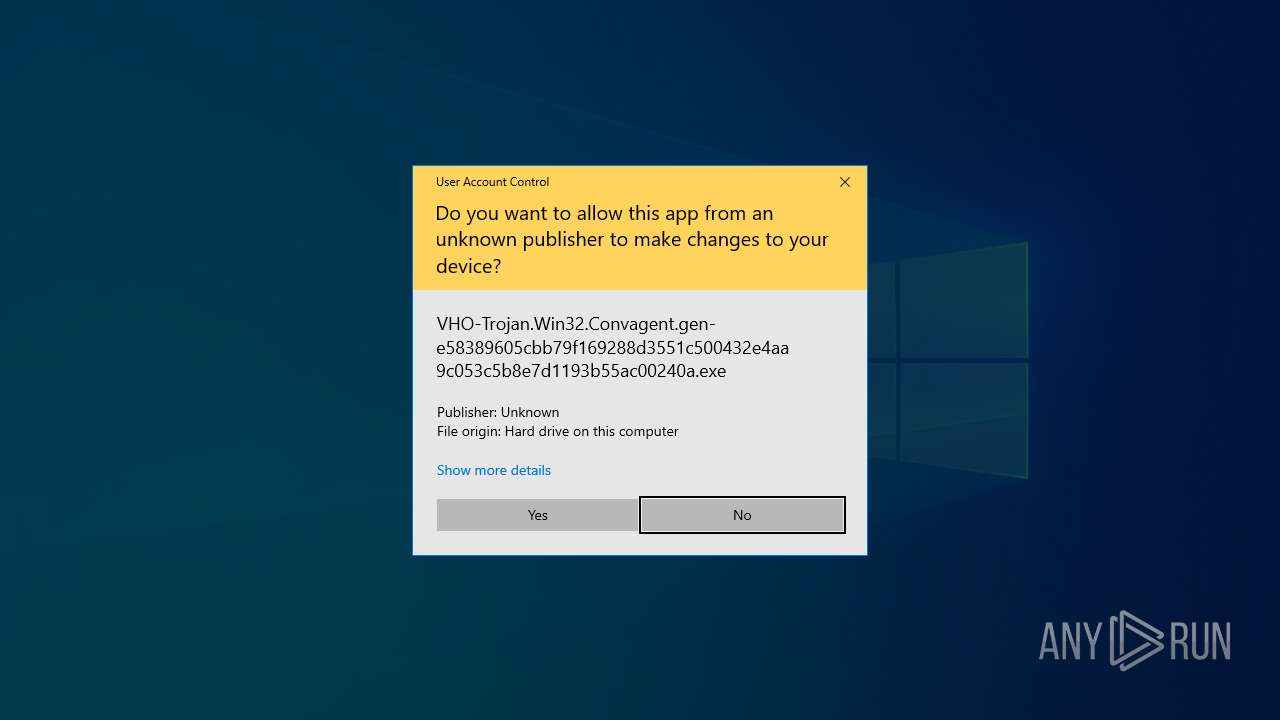
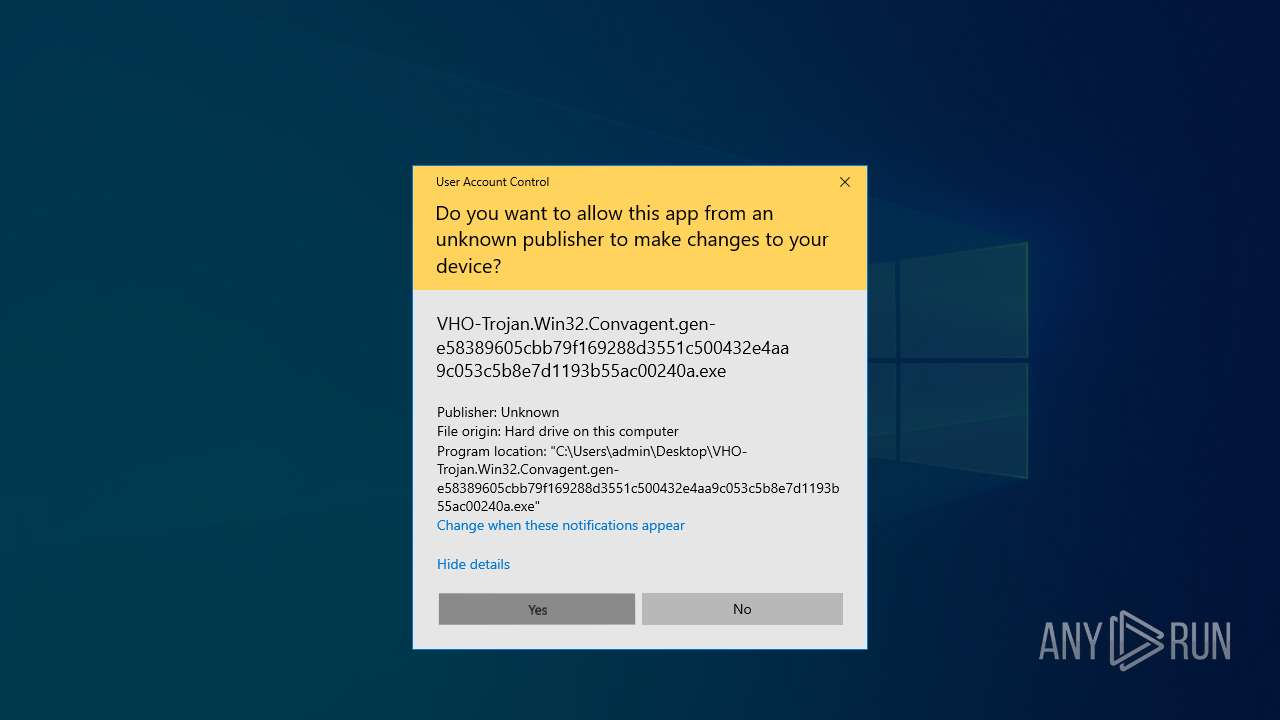
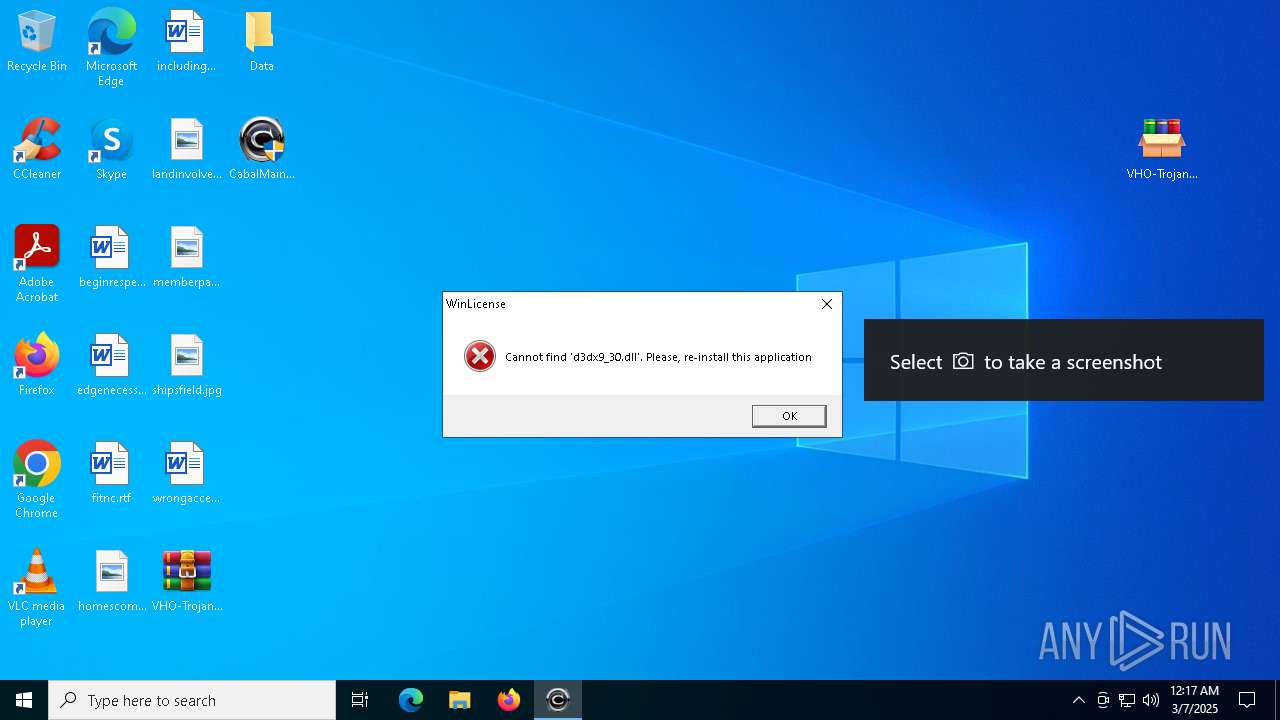
Executable content was dropped or overwritten
- VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe (PID: 4268)
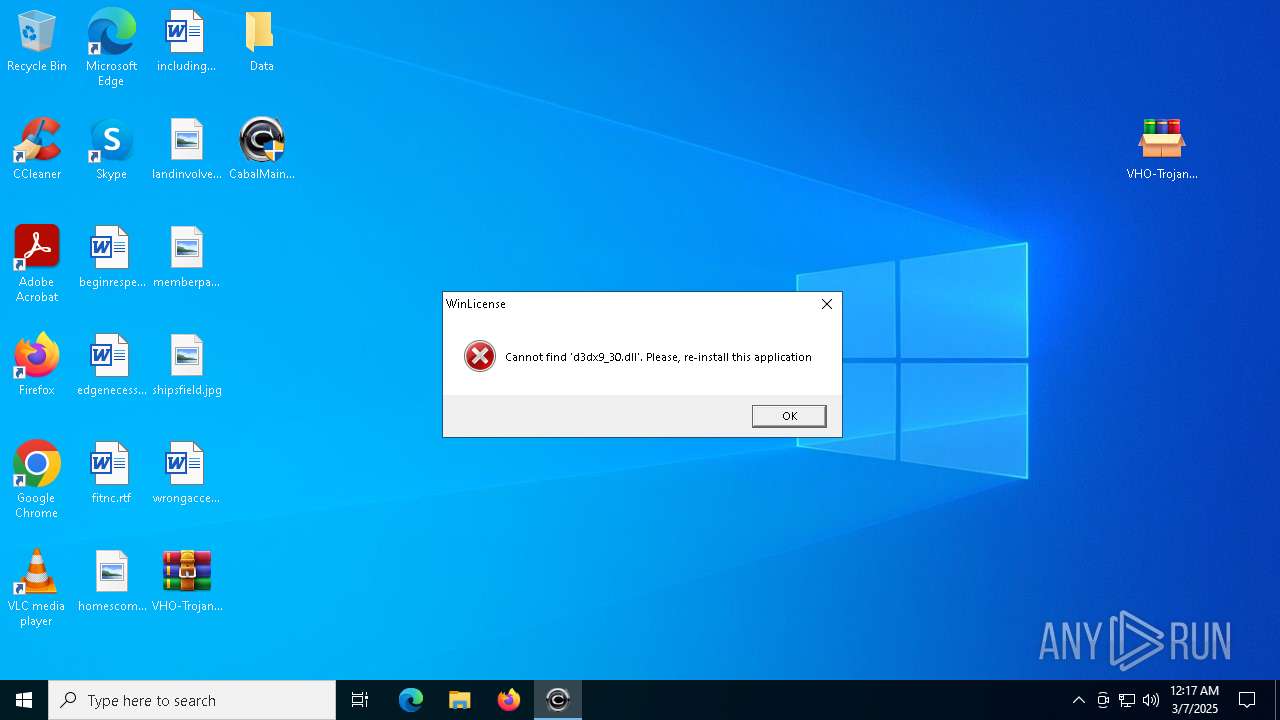
Reads the BIOS version
- CabalMain.exe (PID: 1568)
Reads security settings of Internet Explorer
- GameBar.exe (PID: 2108)
INFO
The sample compiled with korean language support
- VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe (PID: 4268)
Manual execution by a user
- CabalMain.exe (PID: 1568)
- CabalMain.exe (PID: 5164)
- VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe (PID: 4268)
Reads the computer name
- VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe (PID: 4268)
- CabalMain.exe (PID: 1568)
- GameBar.exe (PID: 2108)
Checks supported languages
- VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe (PID: 4268)
- CabalMain.exe (PID: 1568)
- GameBar.exe (PID: 2108)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2568)
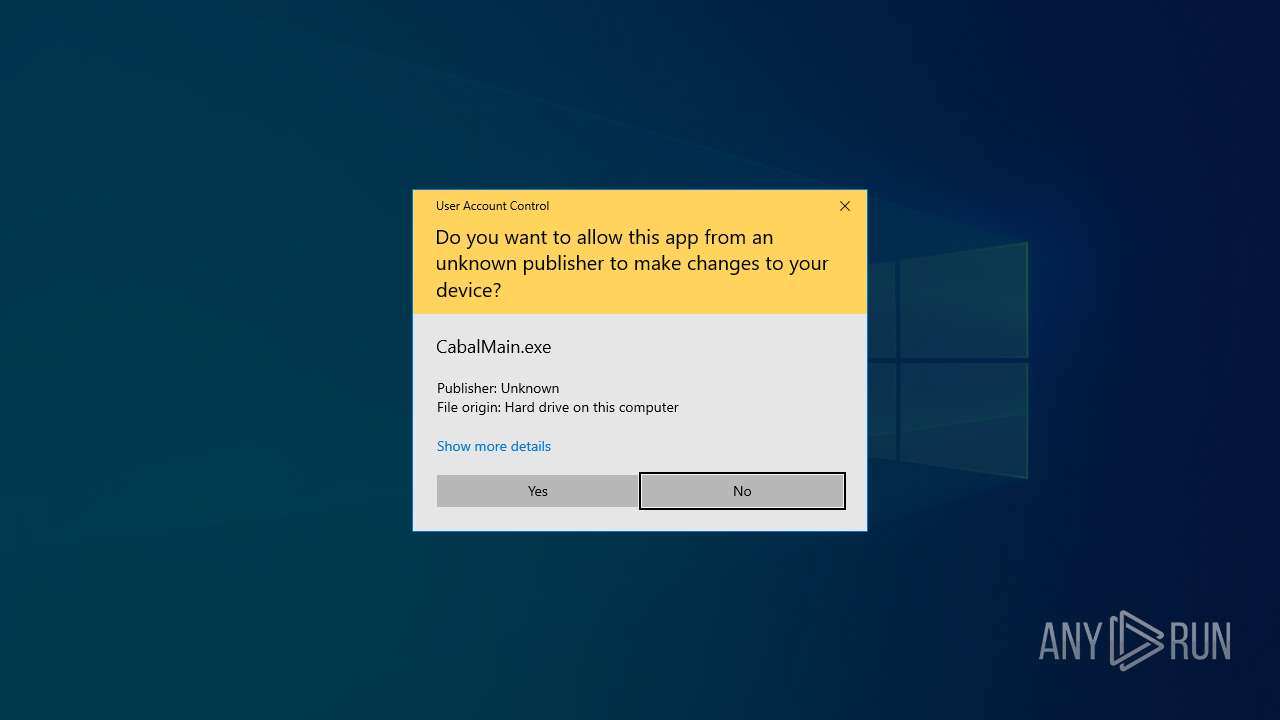
Process checks whether UAC notifications are on
- CabalMain.exe (PID: 1568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:10:26 12:08:36+00:00 |
| ArchivedFileName: | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe |
Total processes
141
Monitored processes
7
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1568 | "C:\Users\admin\Desktop\CabalMain.exe" | C:\Users\admin\Desktop\CabalMain.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: CABAL Online Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe" -ServerName:App.AppXbdkk0yrkwpcgeaem8zk81k8py1eaahny.mca | C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2568 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4268 | "C:\Users\admin\Desktop\VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe" | C:\Users\admin\Desktop\VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4424 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5164 | "C:\Users\admin\Desktop\CabalMain.exe" | C:\Users\admin\Desktop\CabalMain.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: CABAL Online Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5512 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 057
Read events
2 031
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.7z | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
3
Suspicious files
30
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\Data\achievement.enc | binary | |
MD5:B82CE90465603D496AA7D34B3F89D421 | SHA256:18F9F139570C331BC9BEE1390F55D57BEFD9EFC7046C6F1FF09E731DA36F8D9C | |||
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\Data\cabal.enc | binary | |
MD5:42981191D536FF29C08F954E75B61855 | SHA256:A125FF95EE5D4A6B88770BA2696337BB08D98F4D0D781F0B230CD64193CDFB79 | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2568.44188\VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | executable | |
MD5:4F9E520C677DCC185ADDD4157804DCB5 | SHA256:E58389605CBB79F169288D3551C500432E4AA9C053C5B8E7D1193B55AC00240A | |||
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\Data\cont2.enc | binary | |
MD5:A20BC792FD3FA9277FA85C36808A5A7F | SHA256:EBB41AF84CF5D0D9F0EBC27B1A30E4A22324C39FAFFAE645F2218ABD4468D0FE | |||
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\Data\assistant.enc | binary | |
MD5:805BF51E9303DD5C4FEB48136673CDEB | SHA256:DA119F244DC4248766C9BB488E0F62FDE3E1AD2870C6BC87A8DF9511A120EAFA | |||
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\Data\caz.enc | binary | |
MD5:8F6F924D9185477394396D1FC3CCF9E0 | SHA256:A29C9691CD2787D040F5E89EAD3FA1D0FC239700F9EBFFE411624486C264EB36 | |||
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\Data\Language\English\cont2_msg.enc | binary | |
MD5:499D2DC5965676B0BC0C3939E829FDC2 | SHA256:EA1396B8C5D38A3086118D3B39ED6A661281197321E97FB101B4C82A8363C012 | |||
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\Data\Map\world_20.mcl | — | |
MD5:— | SHA256:— | |||
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\CabalMain.exe | executable | |
MD5:CDB12575625F227A0F5067D0C7543726 | SHA256:0AACE3569A741A07D58D3F8CD964923D367898758919F952AADC5EE247AC6546 | |||
| 4268 | VHO-Trojan.Win32.Convagent.gen-e58389605cbb79f169288d3551c500432e4aa9c053c5b8e7d1193b55ac00240a.exe | C:\Users\admin\Desktop\Data\Language\English\cont_msg.enc | binary | |
MD5:181859A0C06FF090B55DC0EABA9FAF99 | SHA256:EDD05BE58D98AC5843BD6DC276AF0C452F92210CA8152AED7F3CE906D7F68F6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
25
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1196 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1128 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1128 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1196 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1196 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1128 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |