| download: | reports |
| Full analysis: | https://app.any.run/tasks/b88c271a-1773-436c-942f-a552f887ecaf |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2020, 17:04:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
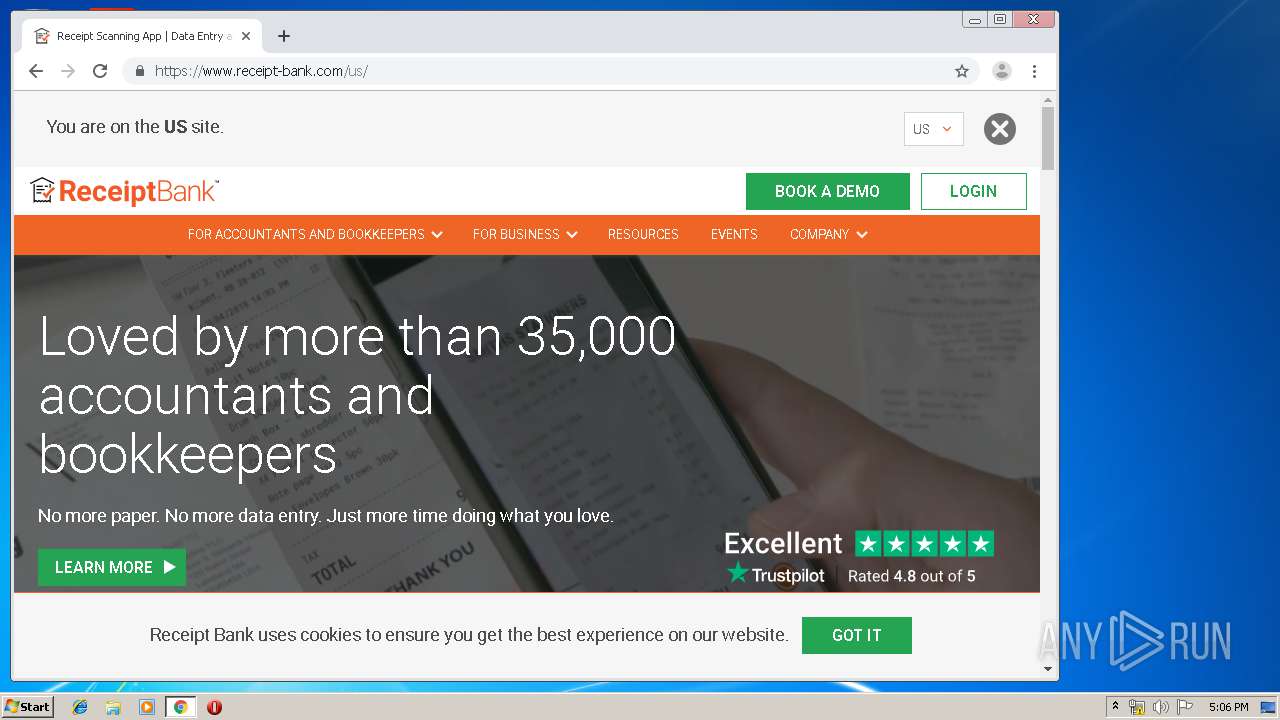
| MIME: | text/html |
| File info: | HTML document, ASCII text |
| MD5: | D8D1315C71179AC89C53242CCCCC18BB |
| SHA1: | F8455E74C302D73FCF74AE9343CB12CBFC39AD82 |
| SHA256: | 0A24AD8567CDCB16EA810905466BFCE52D4299A27418DAE0638D67F38AC81C7B |
| SSDEEP: | 6:C3GKGxnVVHWcd4OqQcd4Oq8d4OqQcd4OqTb:2dGxVocd49d46d49d41b |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 1576)
INFO
Manual execution by user
- chrome.exe (PID: 1576)
Reads the hosts file
- chrome.exe (PID: 1576)
- chrome.exe (PID: 3936)
Application launched itself
- chrome.exe (PID: 1576)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
76
Monitored processes
41
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,13203022215528584435,1501906347733526338,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10881835573771231537 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4028 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,13203022215528584435,1501906347733526338,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2616742528906508895 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2424 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,13203022215528584435,1501906347733526338,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10595411675097508897 --mojo-platform-channel-handle=3280 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,13203022215528584435,1501906347733526338,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2470685770117535623 --renderer-client-id=38 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3748 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
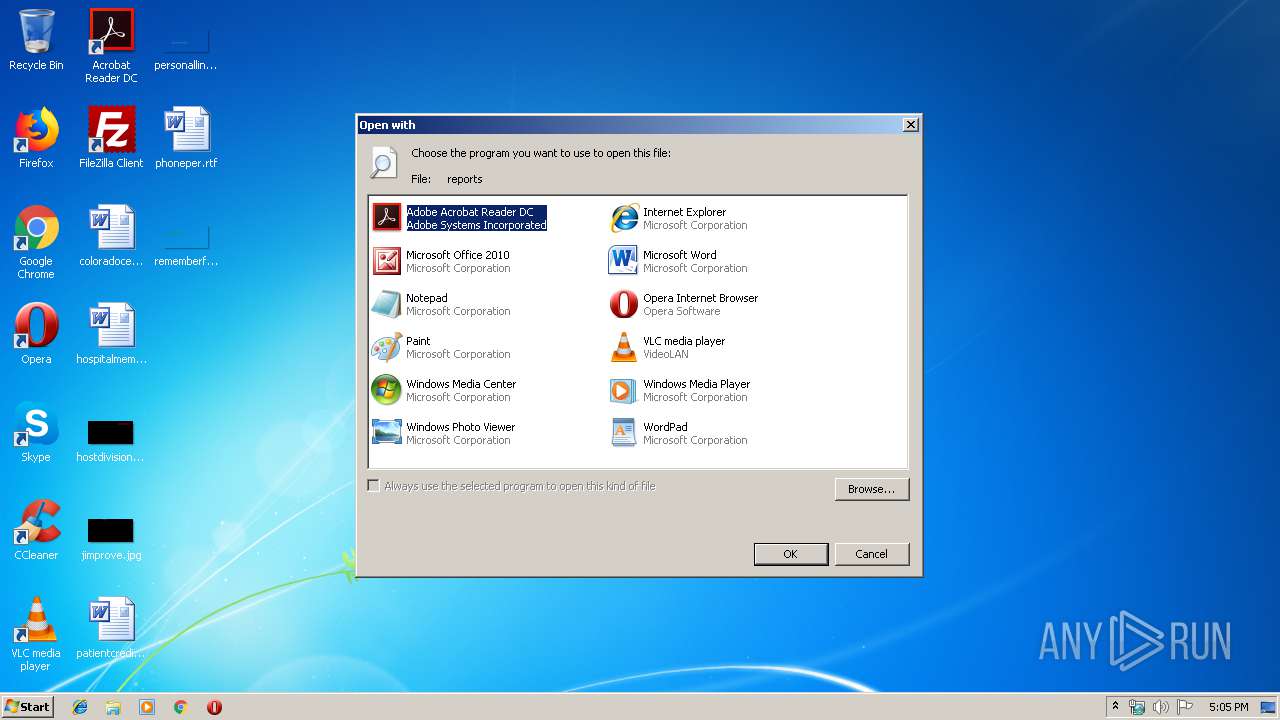
| 1296 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\reports | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,13203022215528584435,1501906347733526338,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2474738615594292696 --mojo-platform-channel-handle=3364 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,13203022215528584435,1501906347733526338,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=17229462873633698655 --mojo-platform-channel-handle=3124 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,13203022215528584435,1501906347733526338,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4698732802523142195 --mojo-platform-channel-handle=3288 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,13203022215528584435,1501906347733526338,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4027076615997738516 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3668 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
700
Read events
581
Write events
114
Delete events
5
Modification events
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (1296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
Executable files
0
Suspicious files
102
Text files
355
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\b747451c-1dd7-45e8-af40-2e6d784420b0.tmp | — | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF39f8a3.TMP | text | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF39f8a3.TMP | text | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF39f8f1.TMP | text | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF39f900.TMP | text | |
MD5:— | SHA256:— | |||
| 1576 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
80
DNS requests
60
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
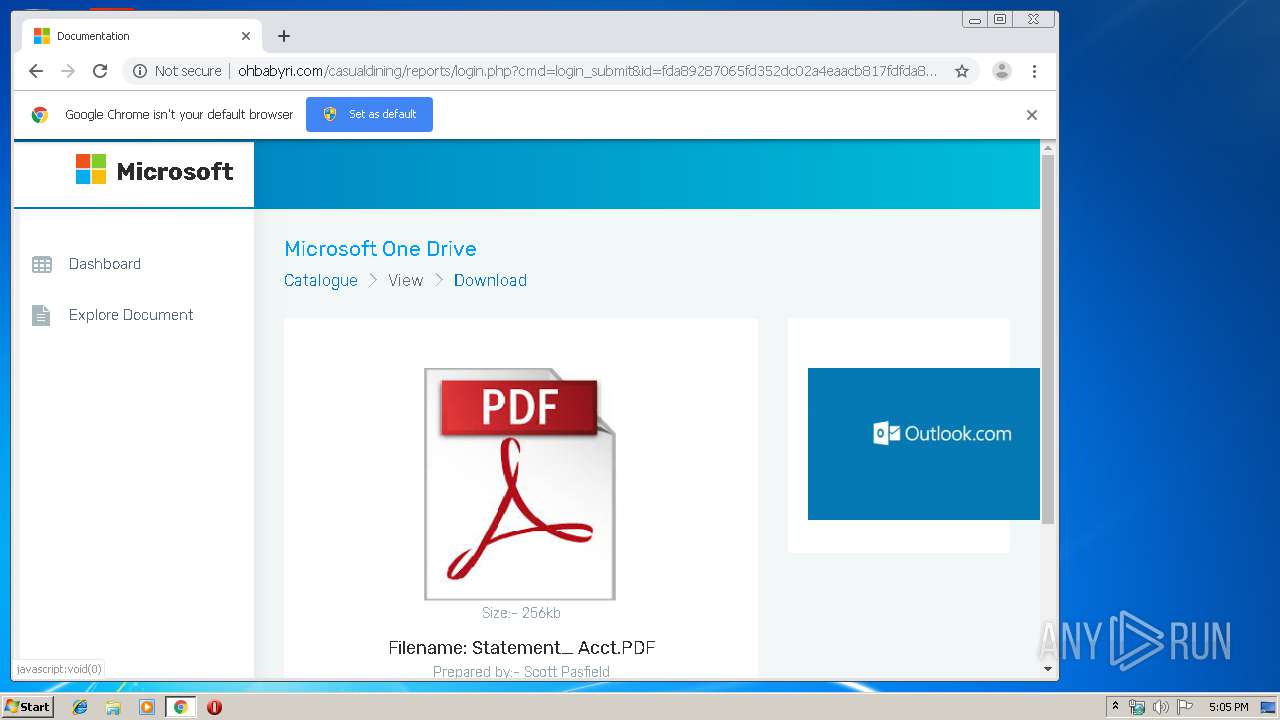
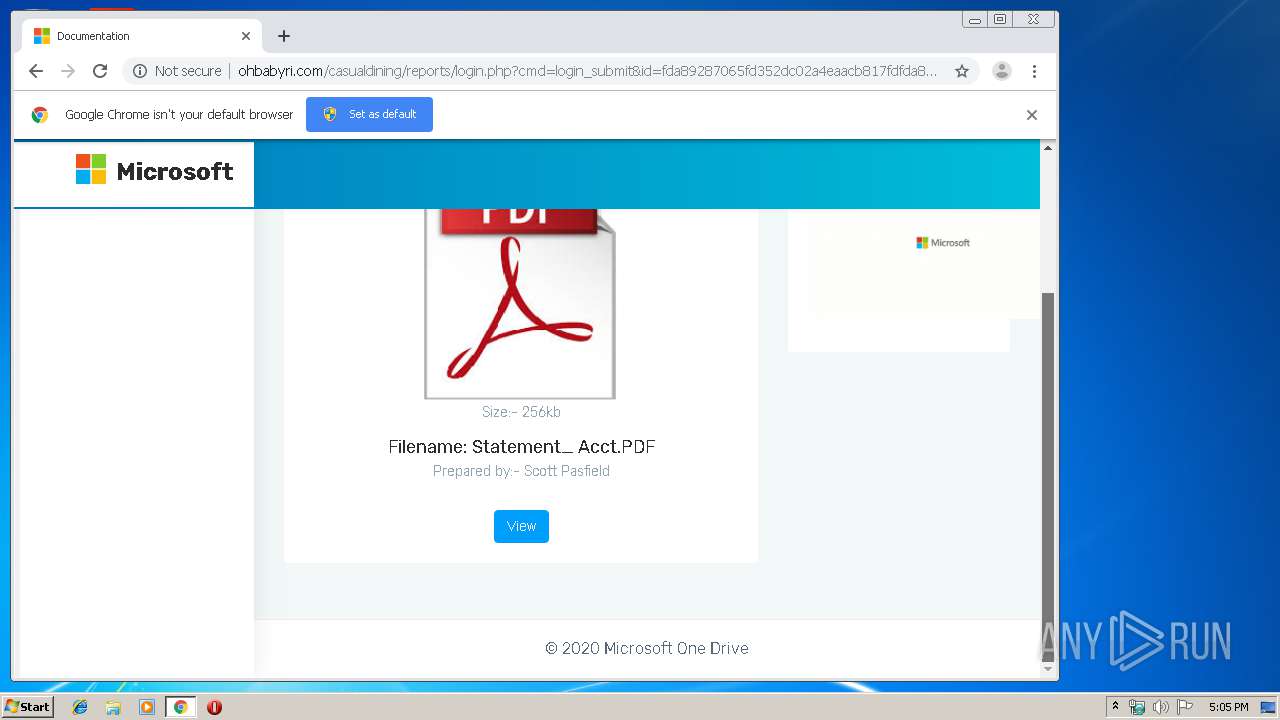
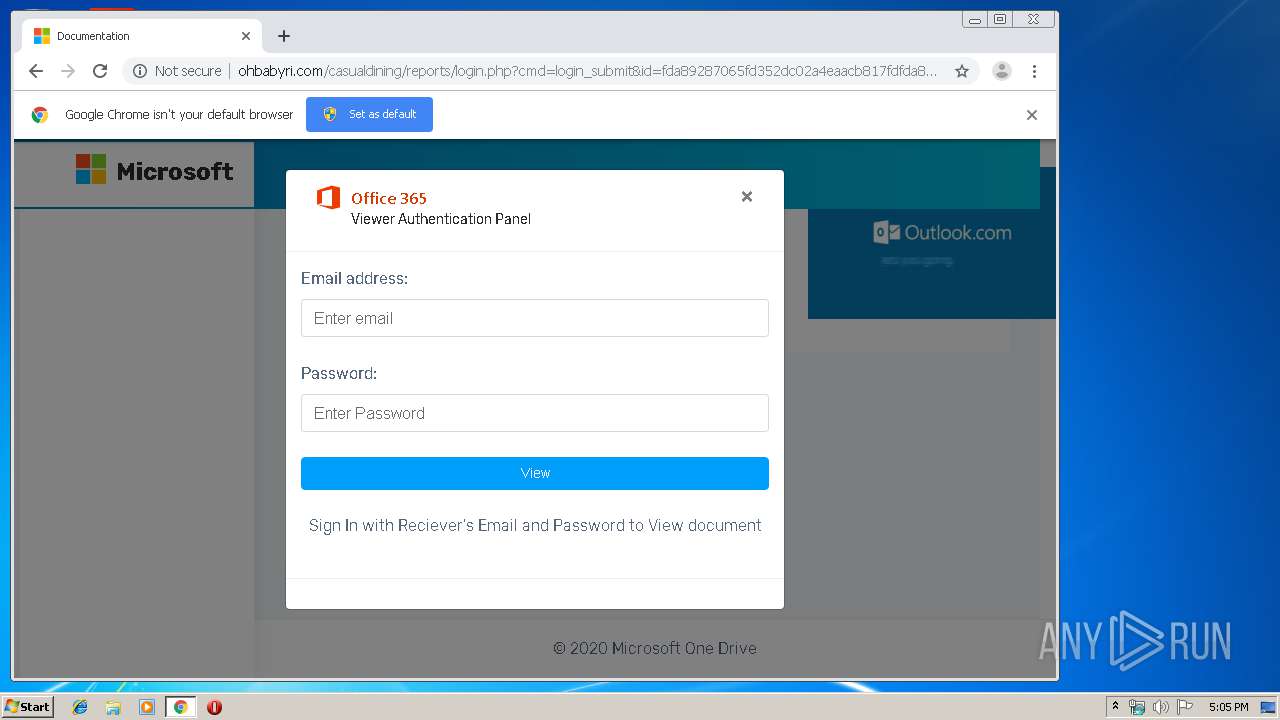
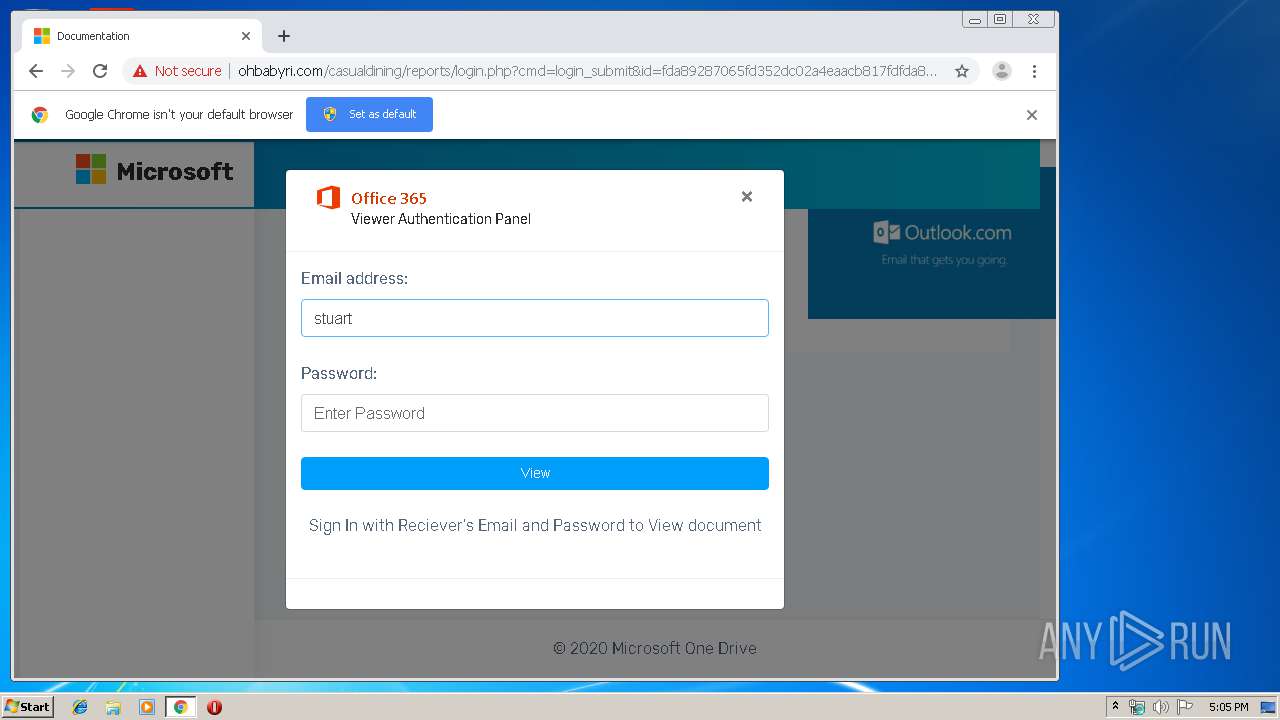
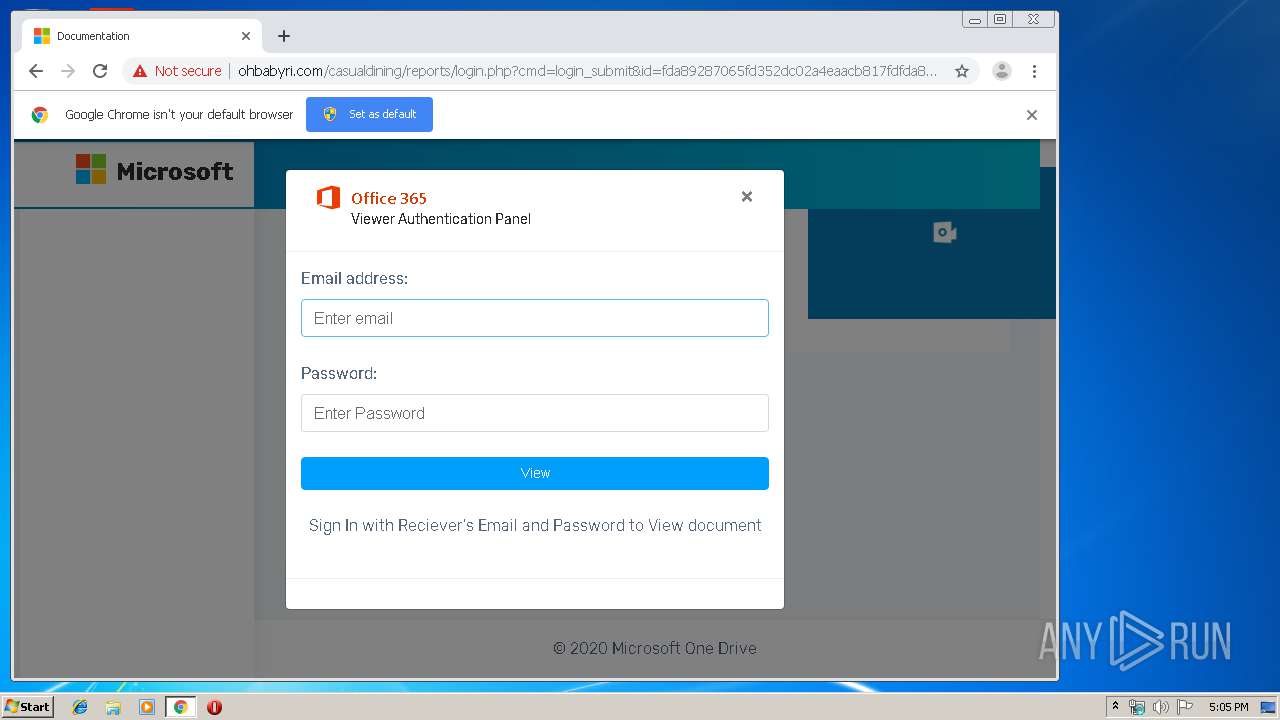
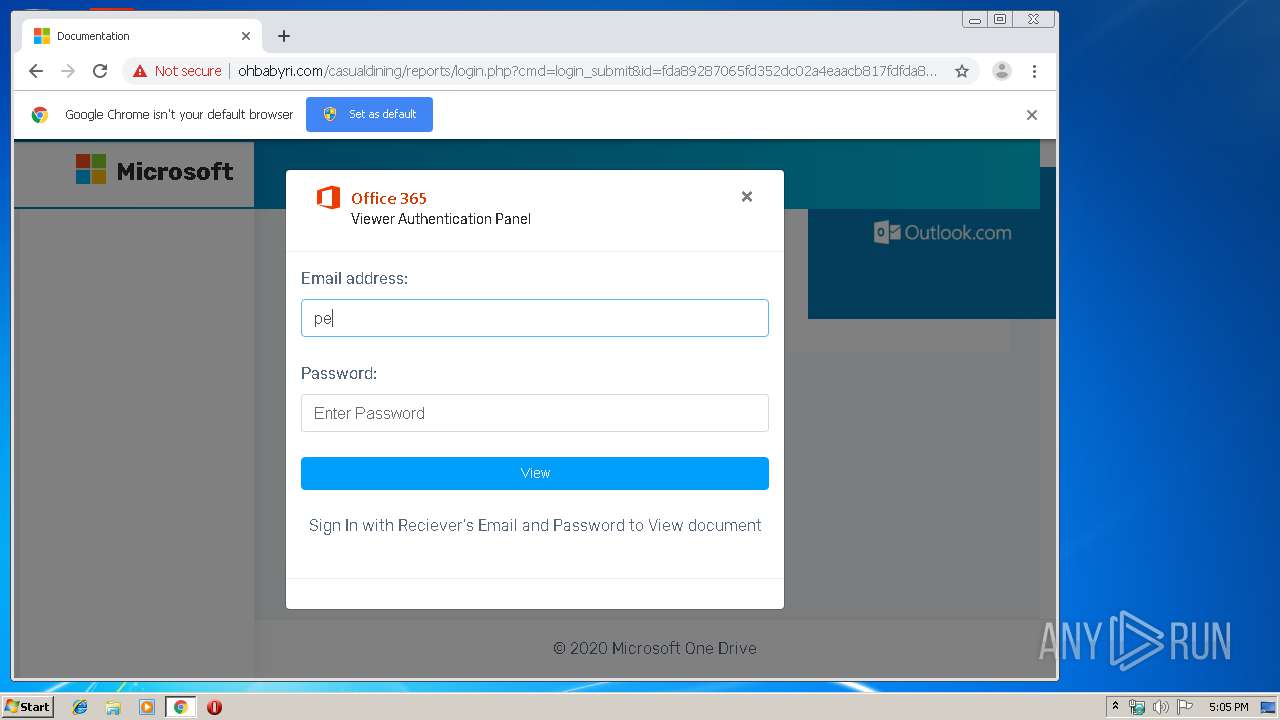
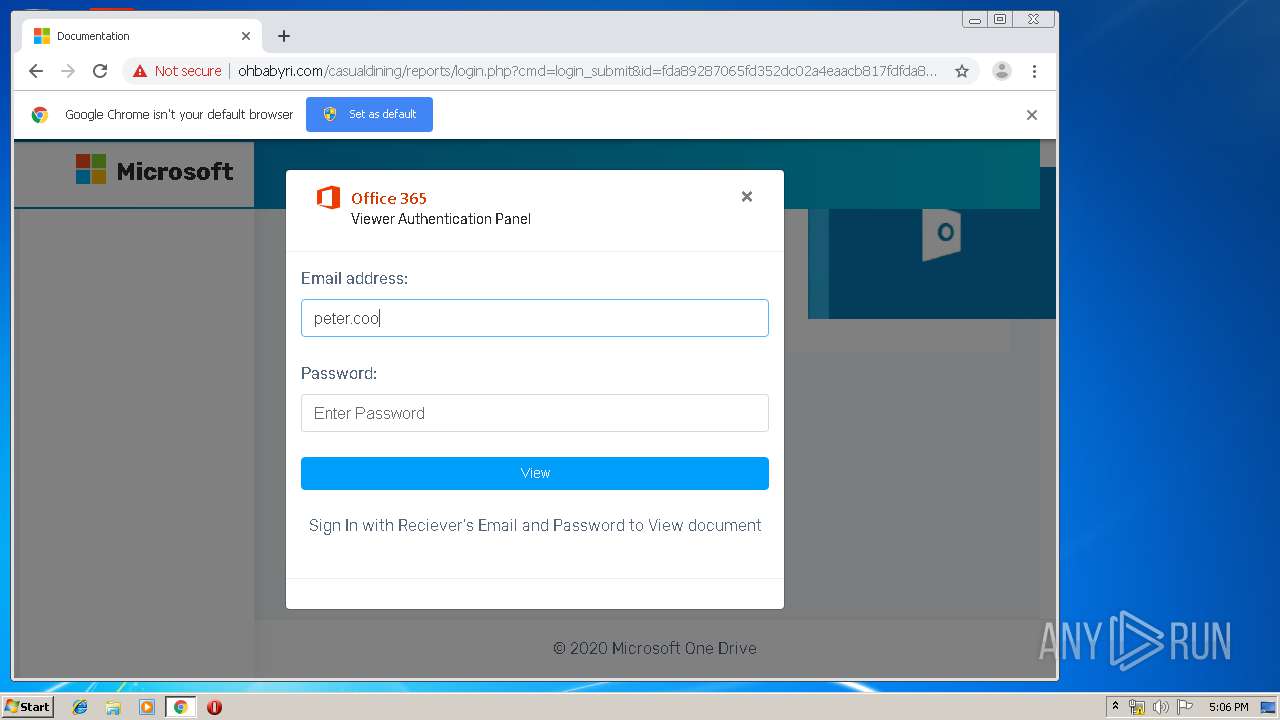
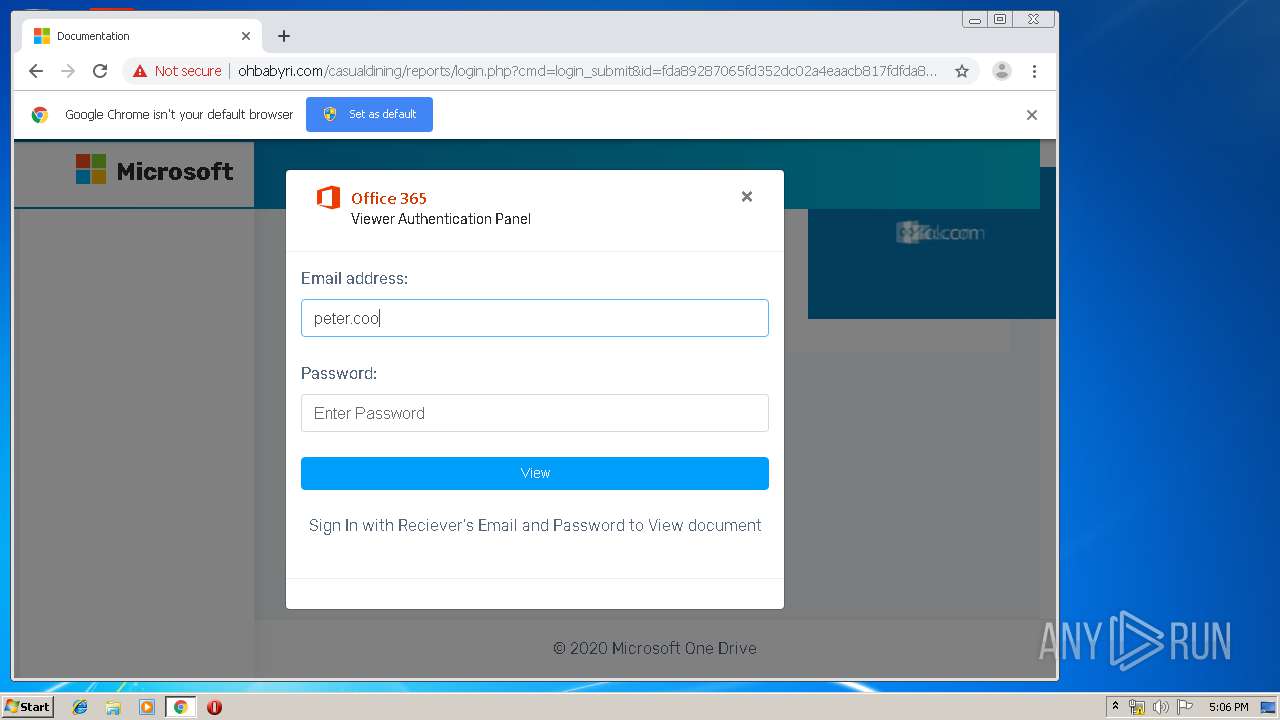
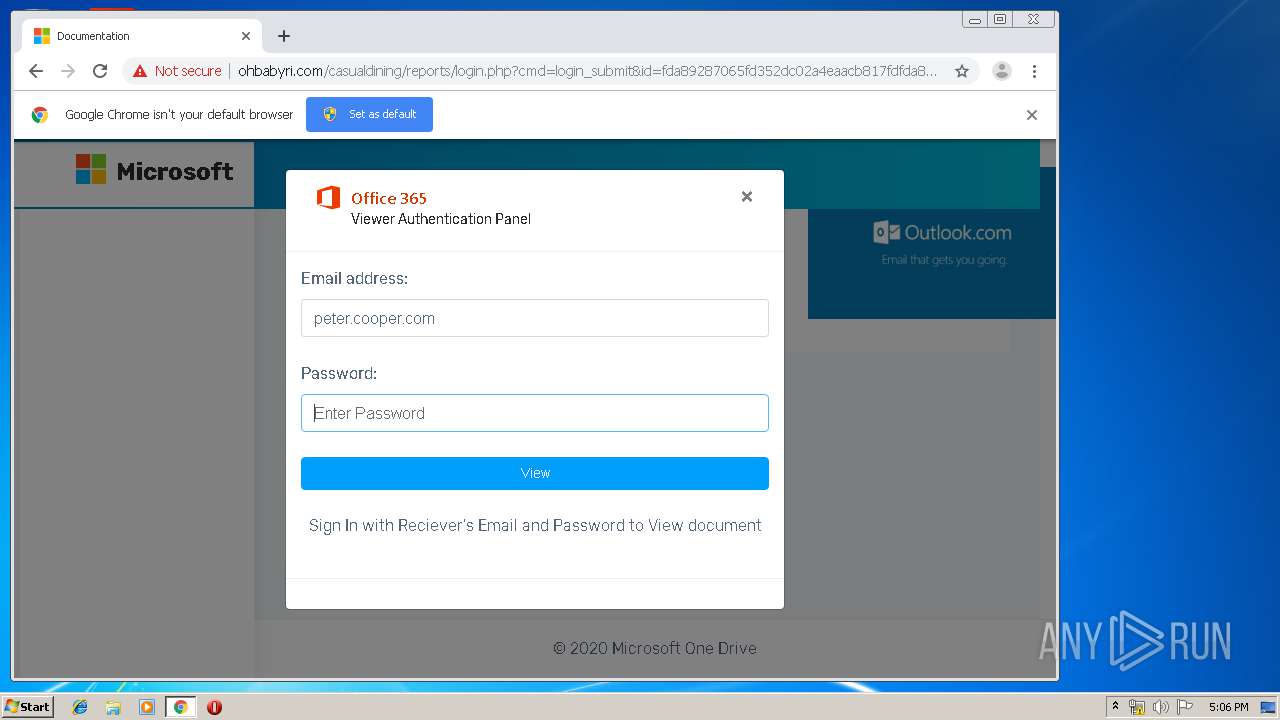
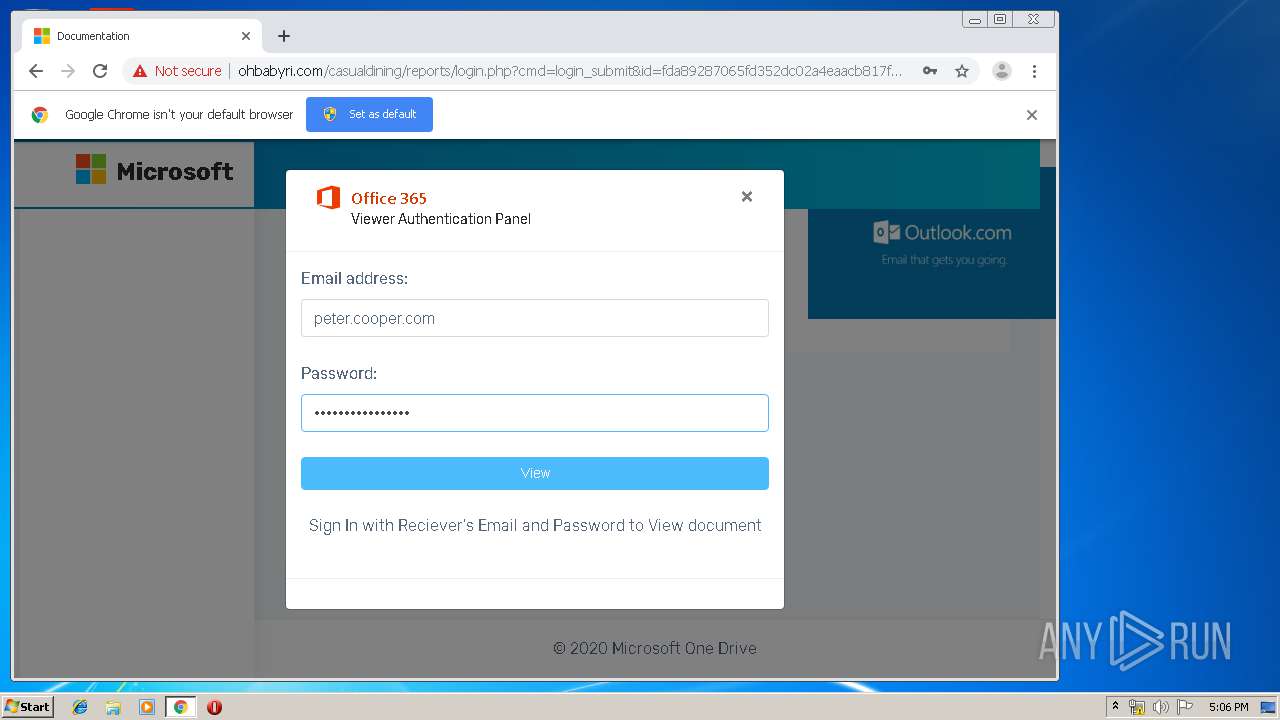
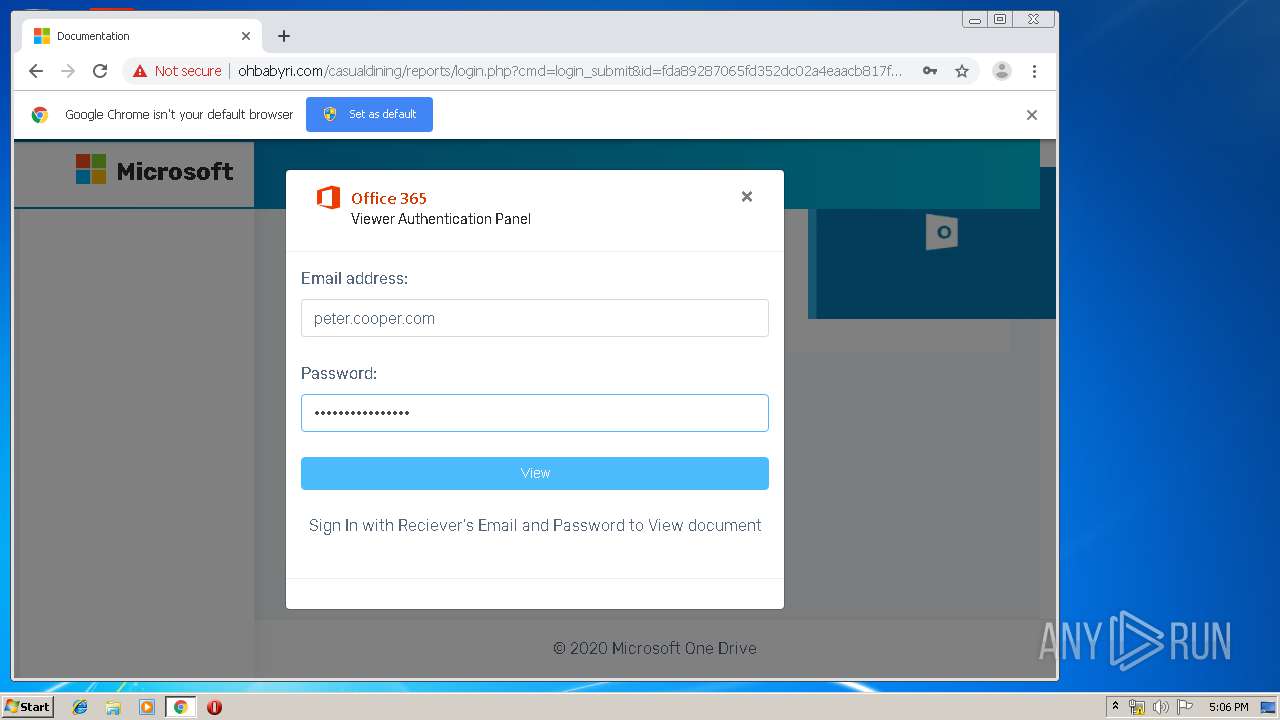
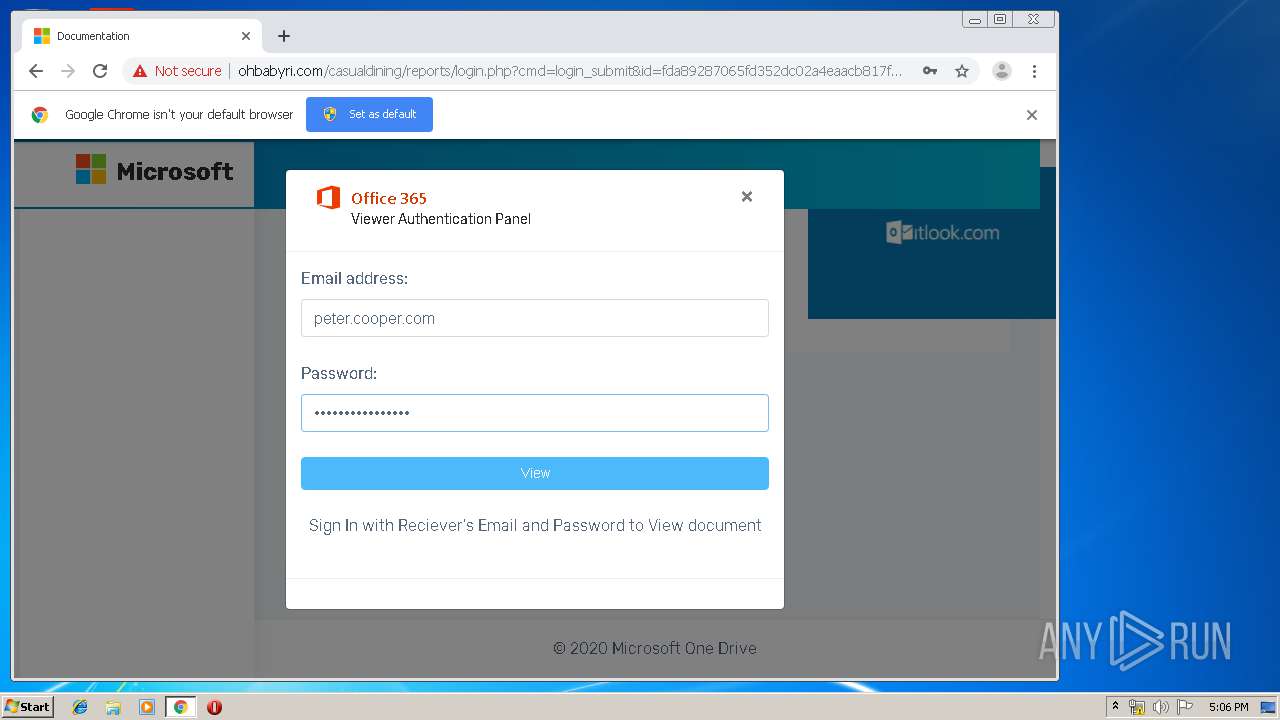
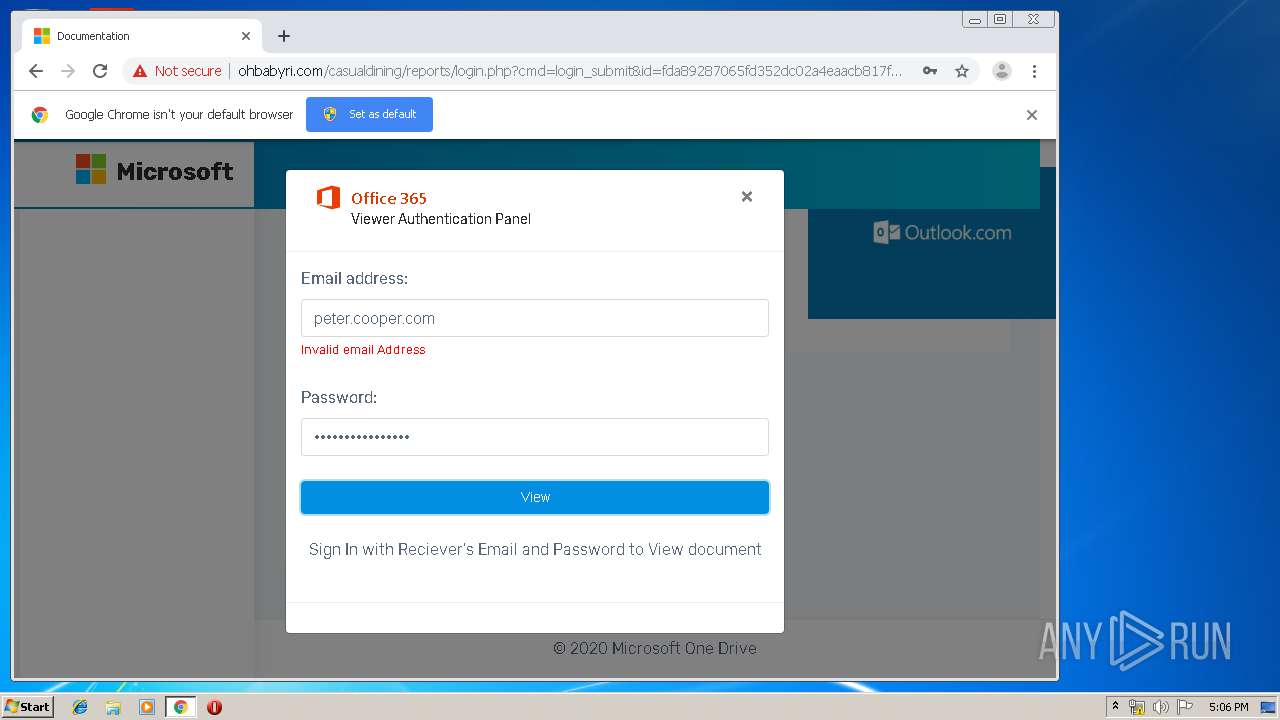
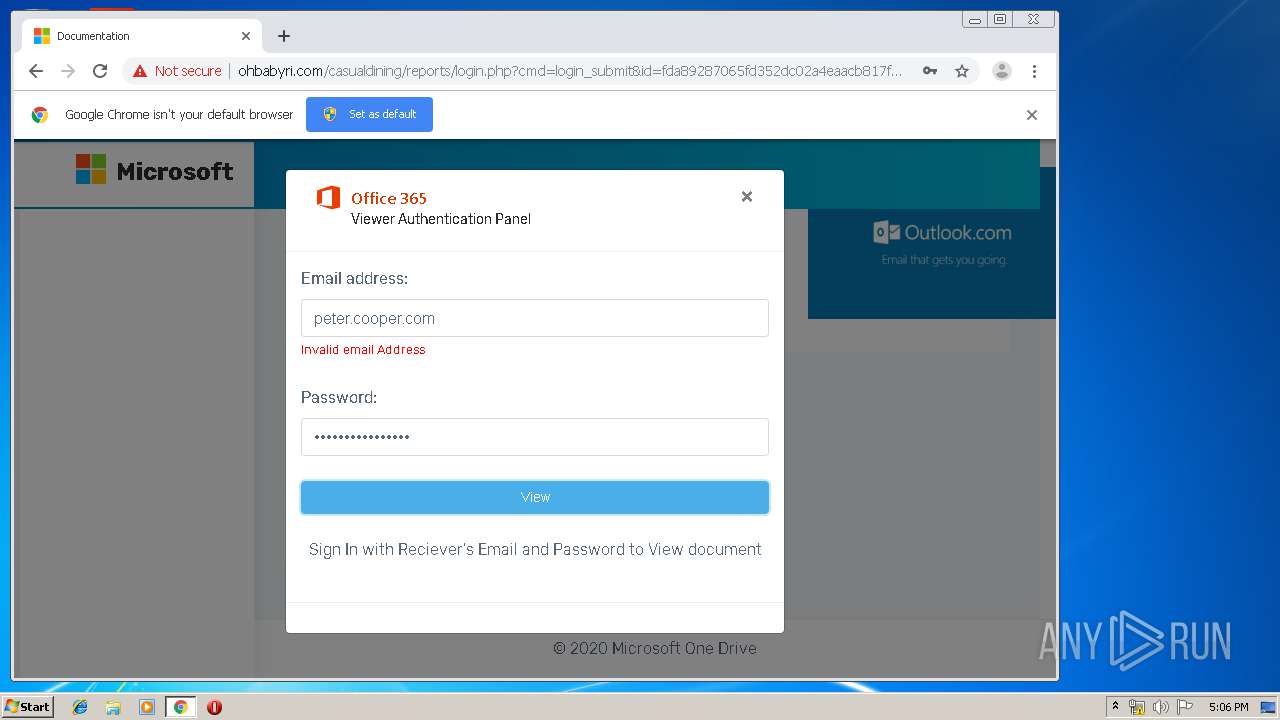
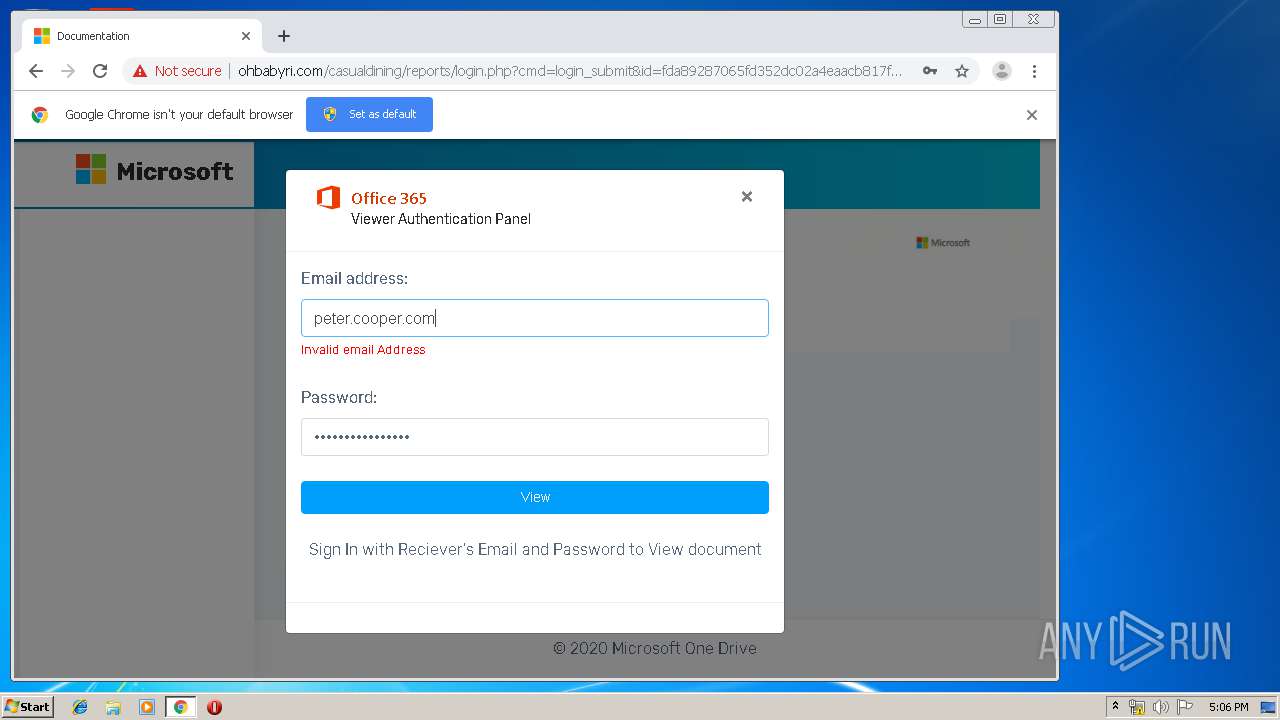
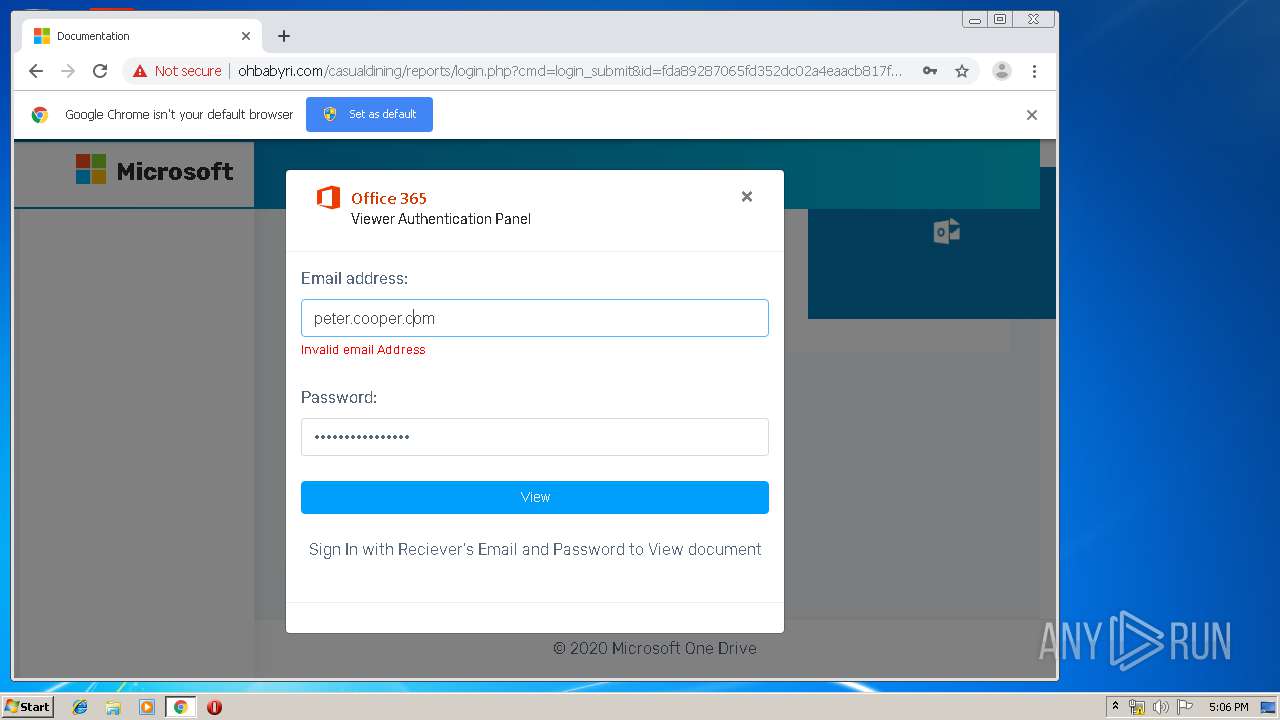
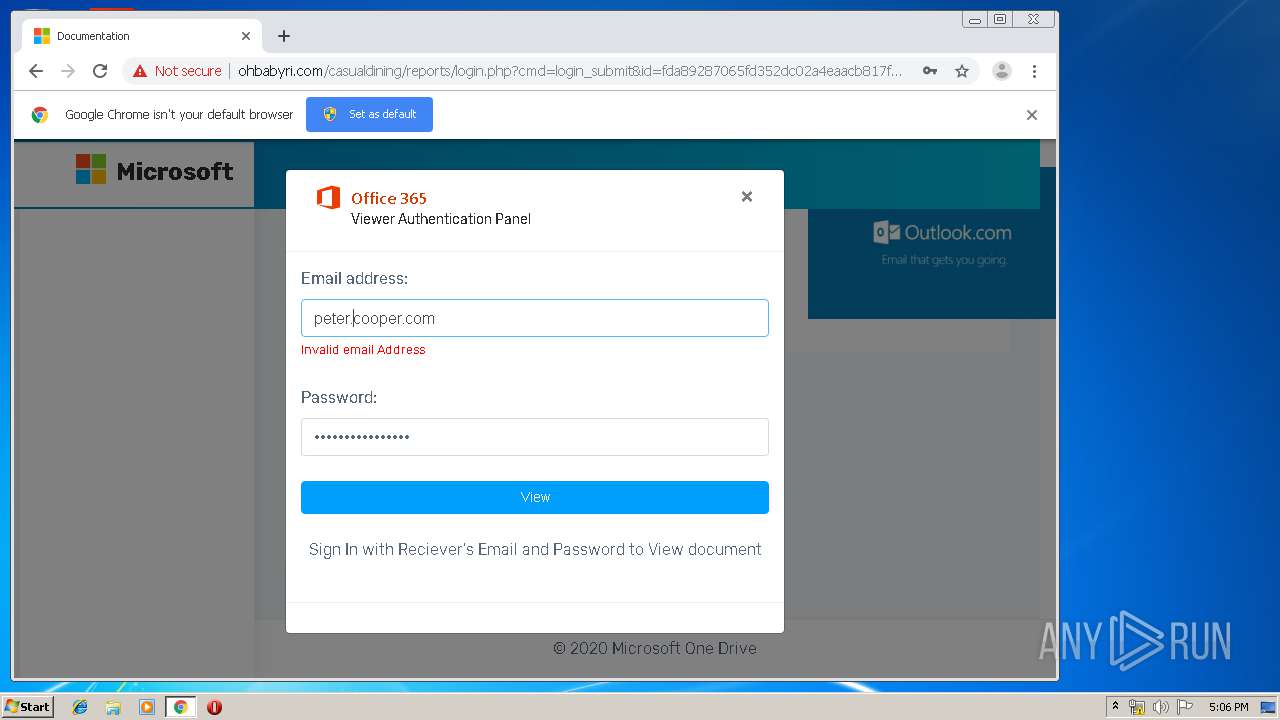
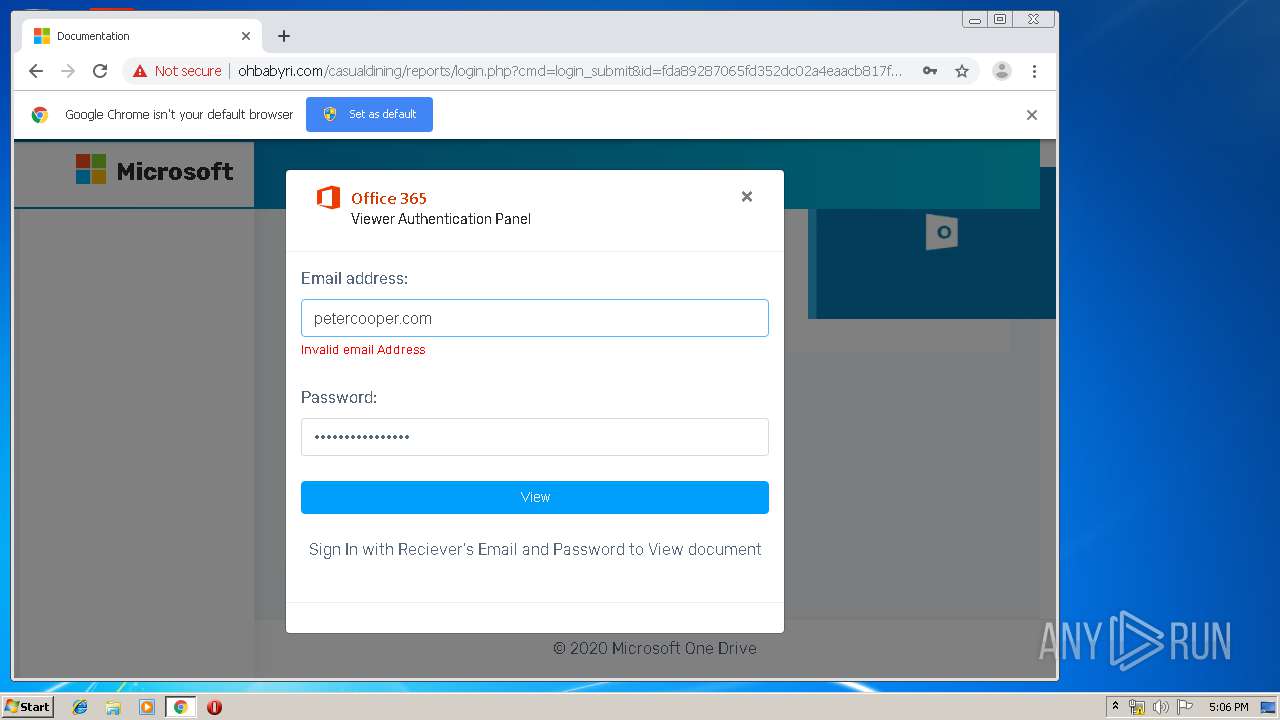
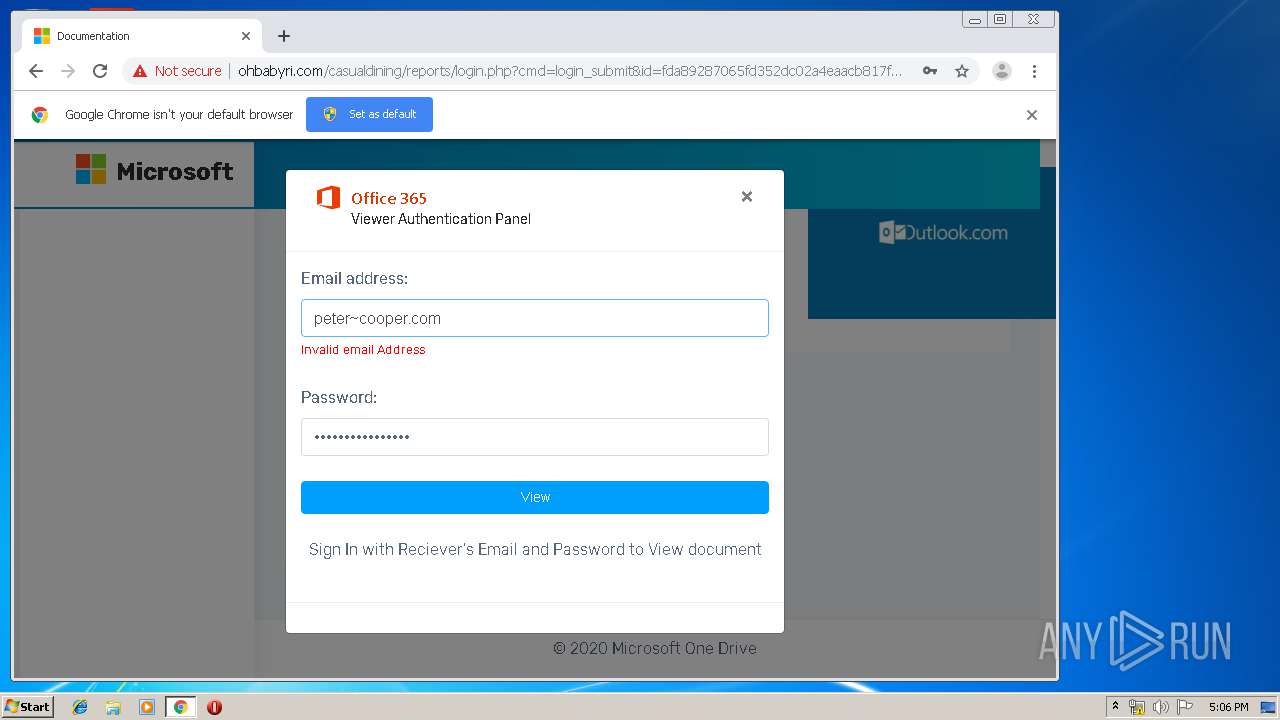
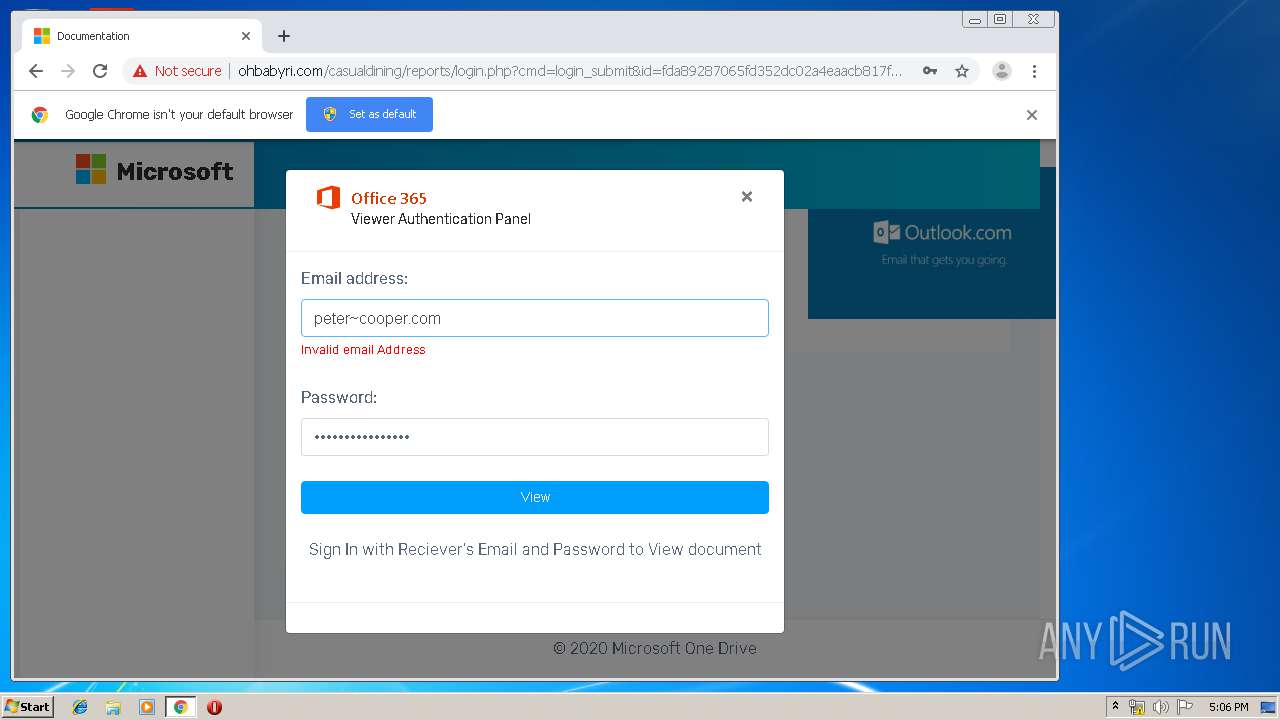
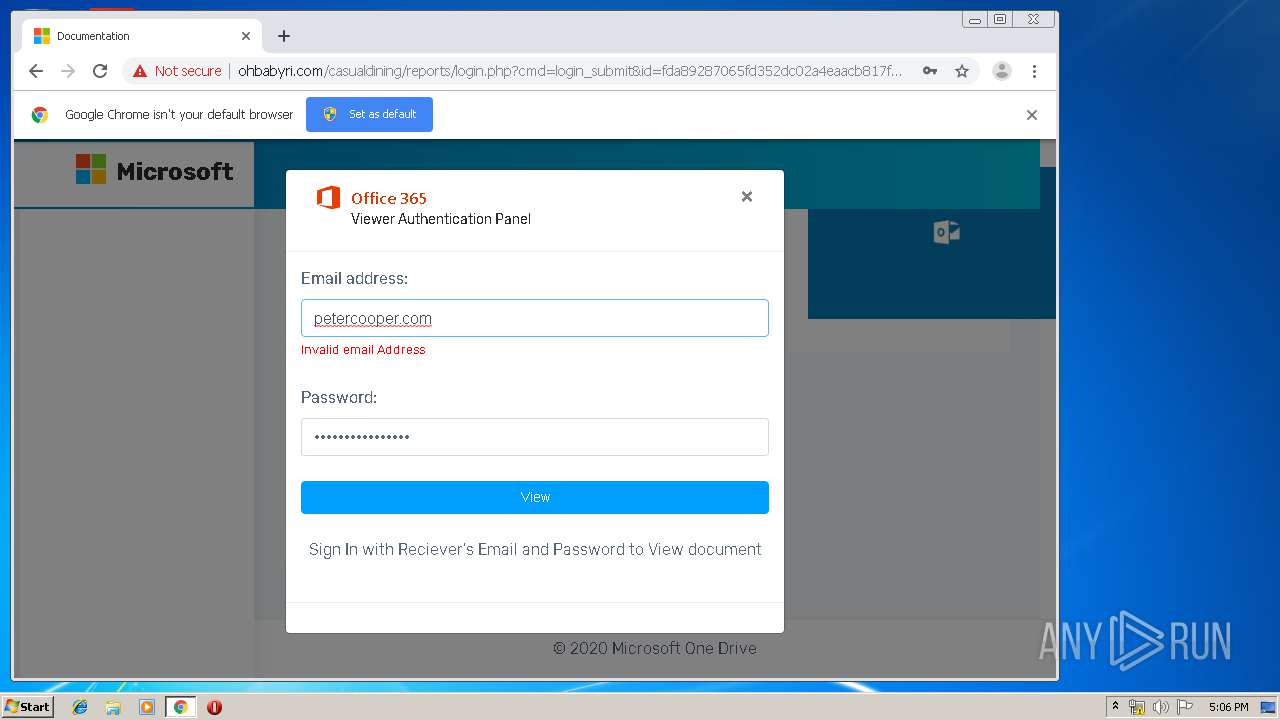
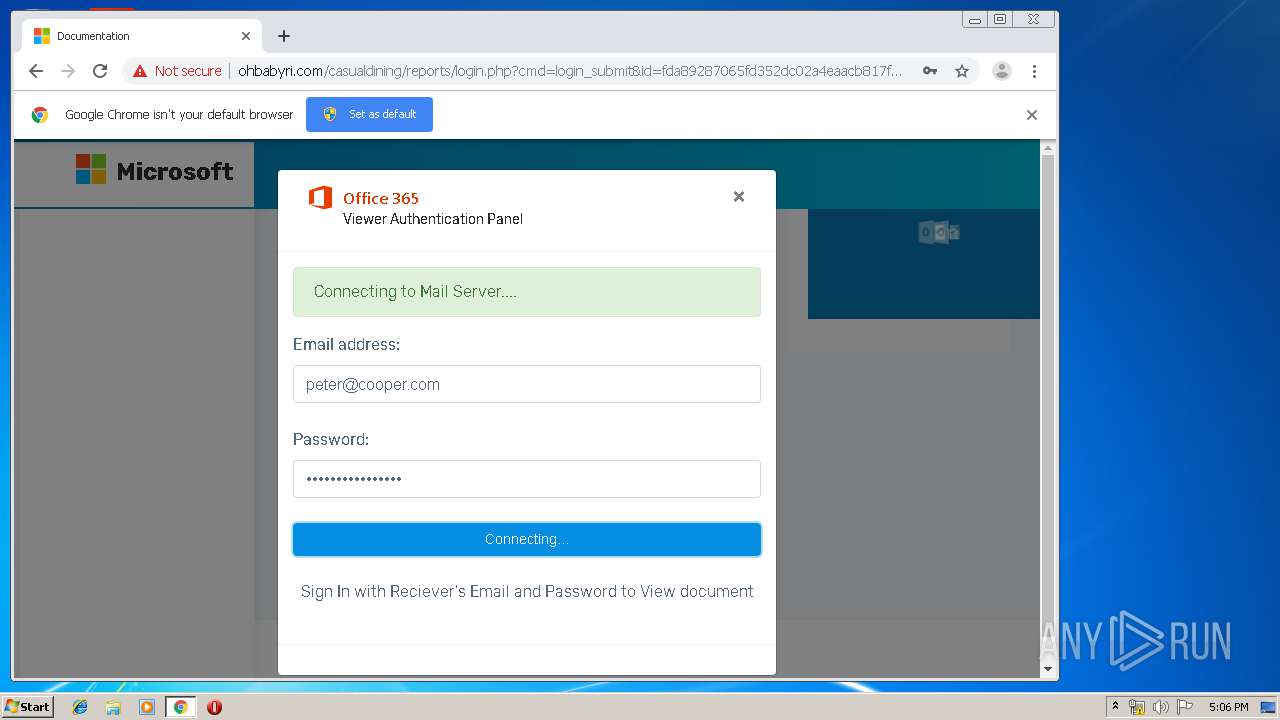
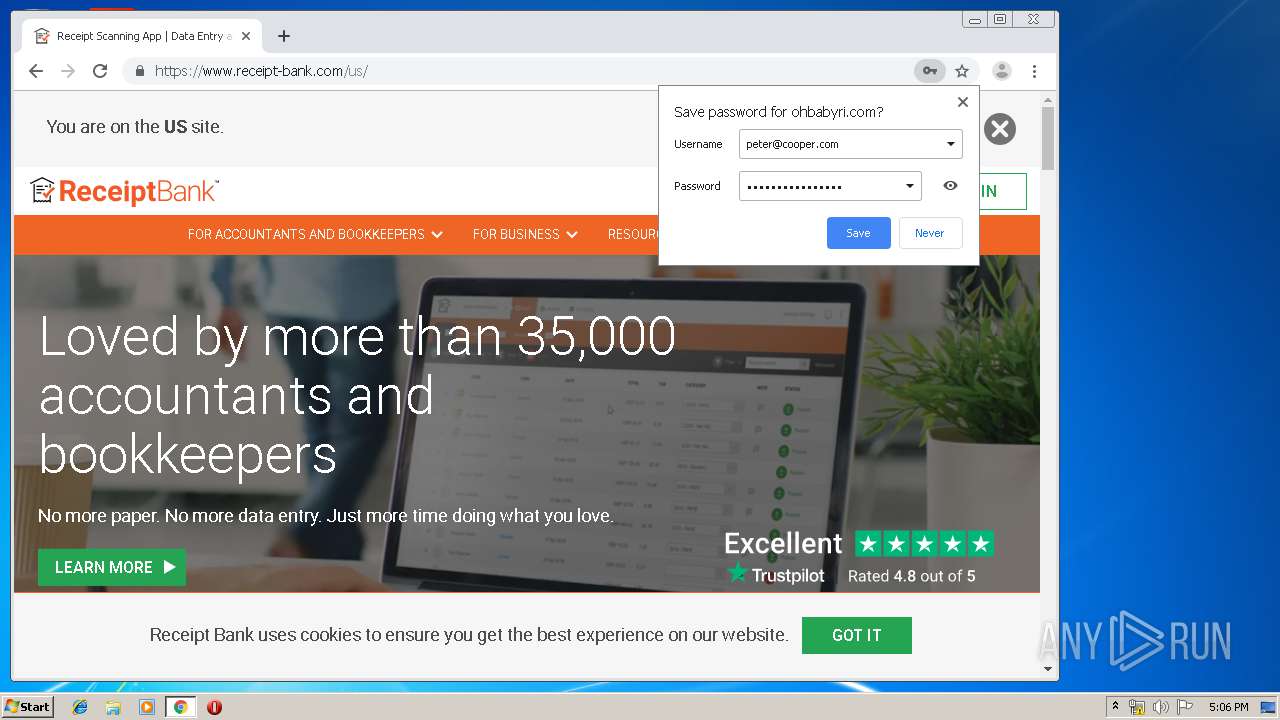
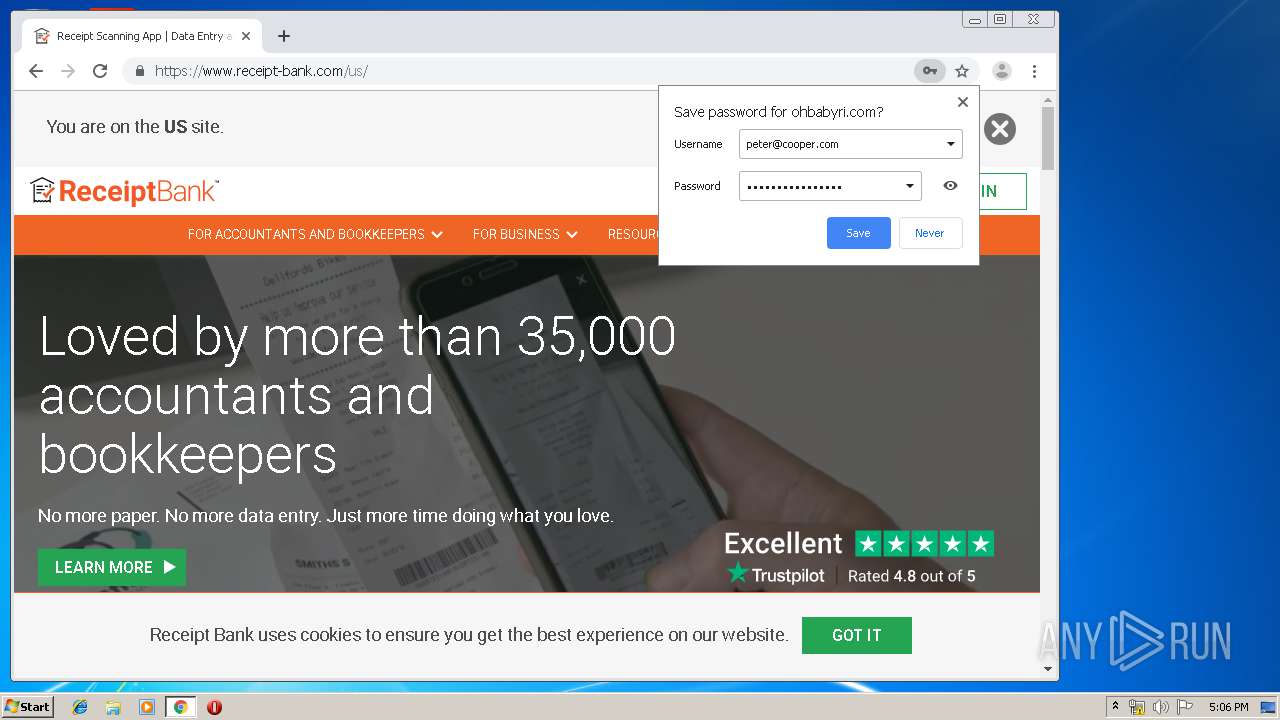
3936 | chrome.exe | GET | 200 | 104.24.124.133:80 | http://ohbabyri.com/casualdining/reports/assets/images/word-icon.png | US | image | 31.1 Kb | suspicious |
3936 | chrome.exe | GET | 200 | 104.24.124.133:80 | http://ohbabyri.com/casualdining/reports/ | US | html | 142 b | suspicious |
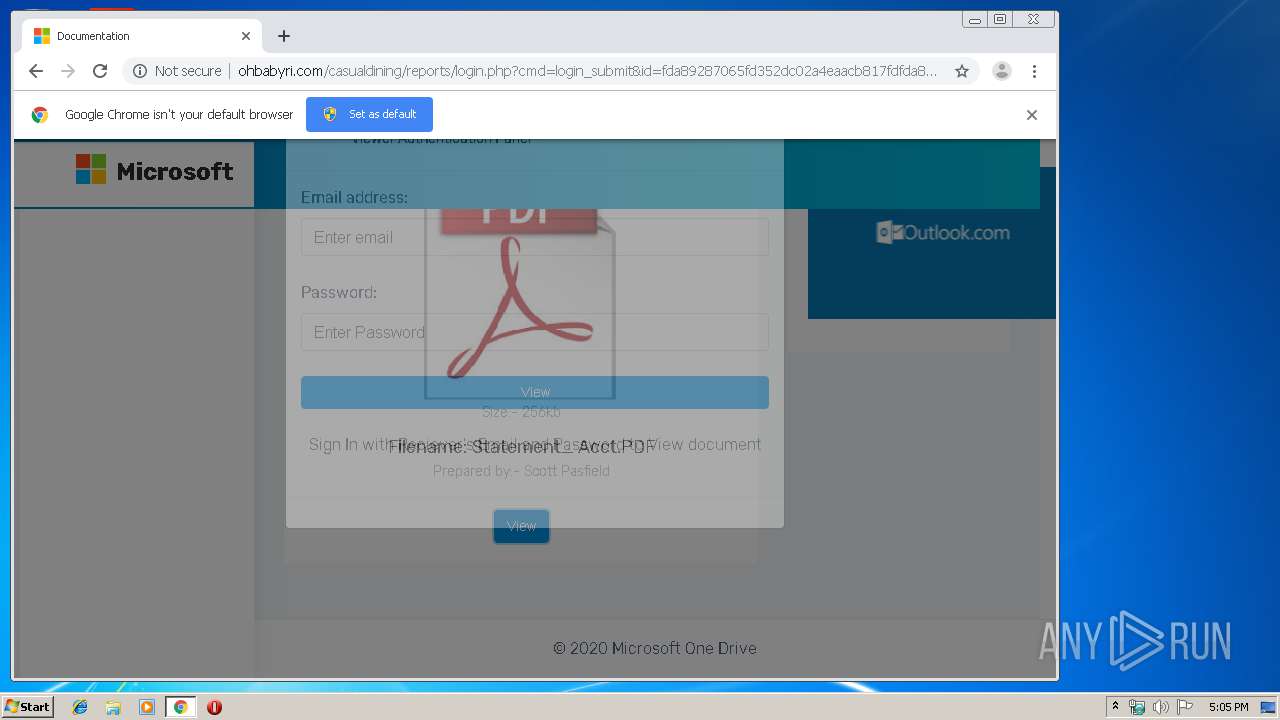
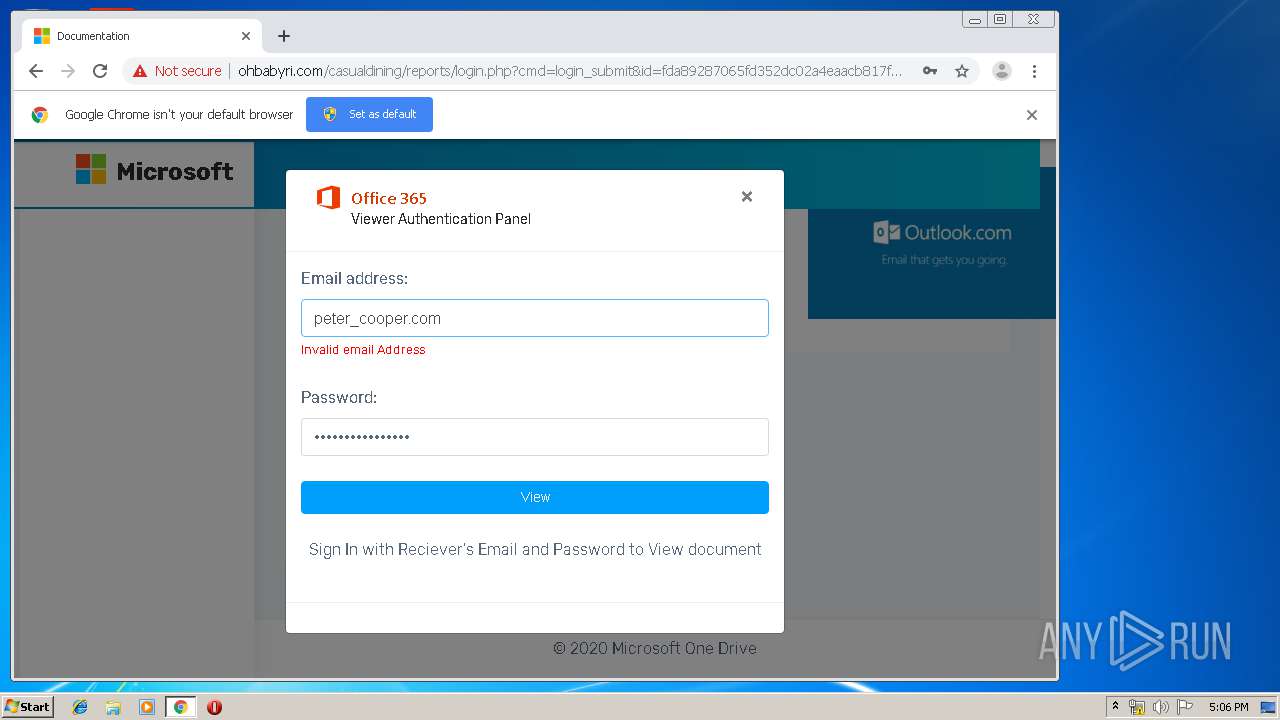
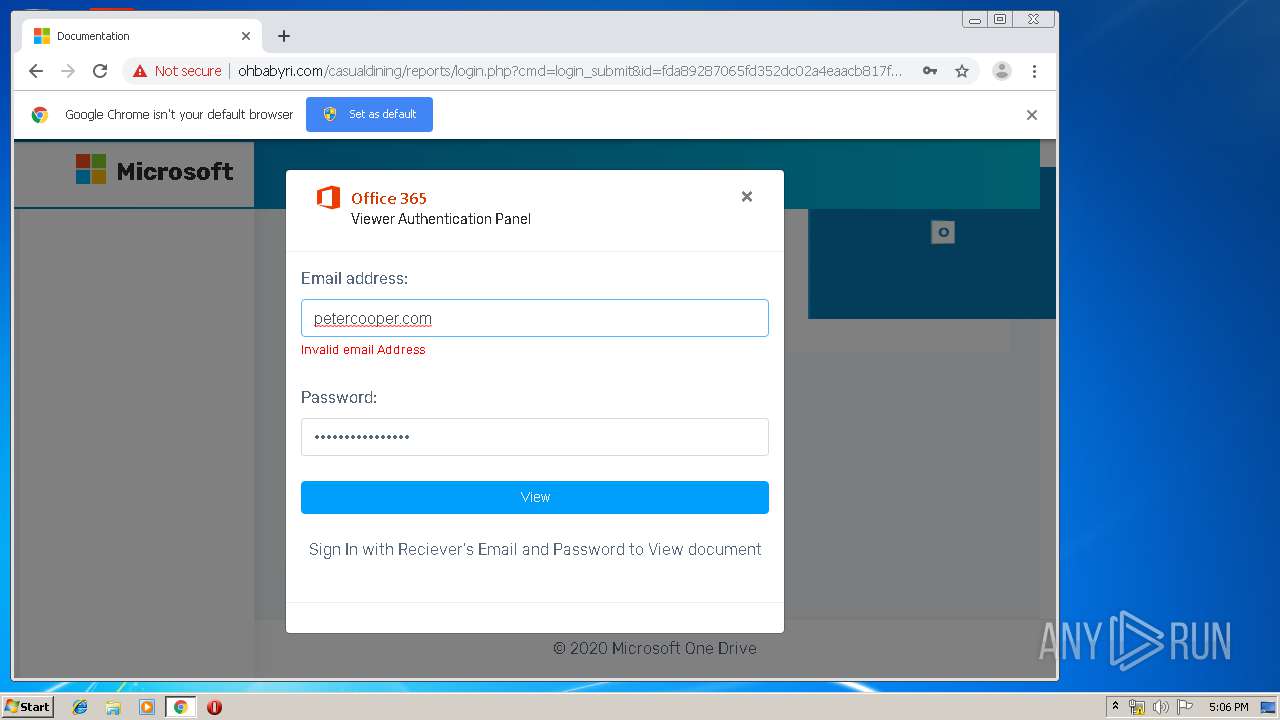
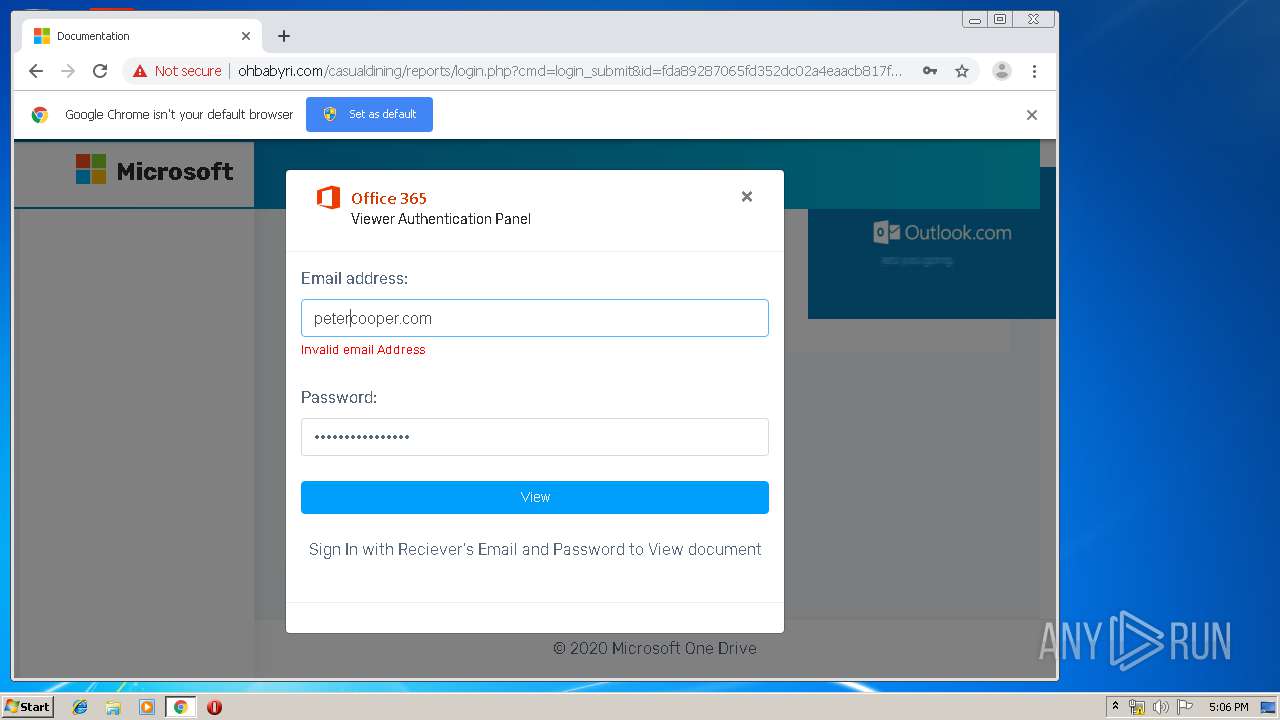
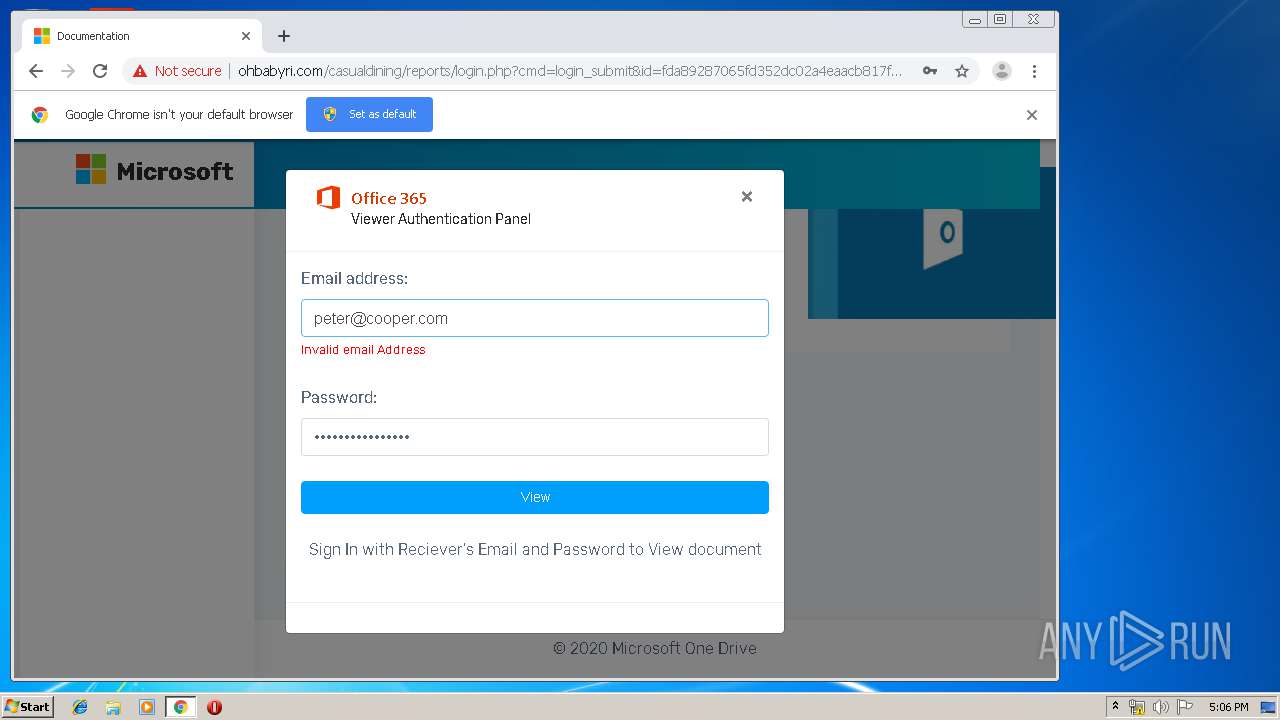
3936 | chrome.exe | GET | 200 | 104.24.124.133:80 | http://ohbabyri.com/casualdining/reports/login.php?cmd=login_submit&id=fda89287065fd352dc02a4eaacb817fdfda89287065fd352dc02a4eaacb817fd&session=fda89287065fd352dc02a4eaacb817fdfda89287065fd352dc02a4eaacb817fd&email= | US | html | 2.48 Kb | suspicious |
3936 | chrome.exe | GET | 302 | 216.58.205.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 507 b | whitelisted |
3936 | chrome.exe | GET | 200 | 104.24.124.133:80 | http://ohbabyri.com/casualdining/reports/assets/plugins/bootstrap/css/bootstrap.min.css | US | text | 19.5 Kb | suspicious |
3936 | chrome.exe | GET | 200 | 104.24.124.133:80 | http://ohbabyri.com/casualdining/reports/js/jquery.slimscroll.js | US | text | 1.71 Kb | suspicious |
3936 | chrome.exe | GET | 200 | 104.24.124.133:80 | http://ohbabyri.com/casualdining/reports/scss/icons/simple-line-icons/css/simple-line-icons.html | US | html | 276 b | suspicious |
3936 | chrome.exe | GET | 200 | 172.217.132.71:80 | http://r2---sn-5hne6nsr.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=84.17.36.75&mm=28&mn=sn-5hne6nsr&ms=nvh&mt=1579280598&mv=m&mvi=1&pl=24&shardbypass=yes | US | crx | 862 Kb | whitelisted |
3936 | chrome.exe | GET | 200 | 104.24.124.133:80 | http://ohbabyri.com/casualdining/reports/js/waves.js | US | text | 1.47 Kb | suspicious |
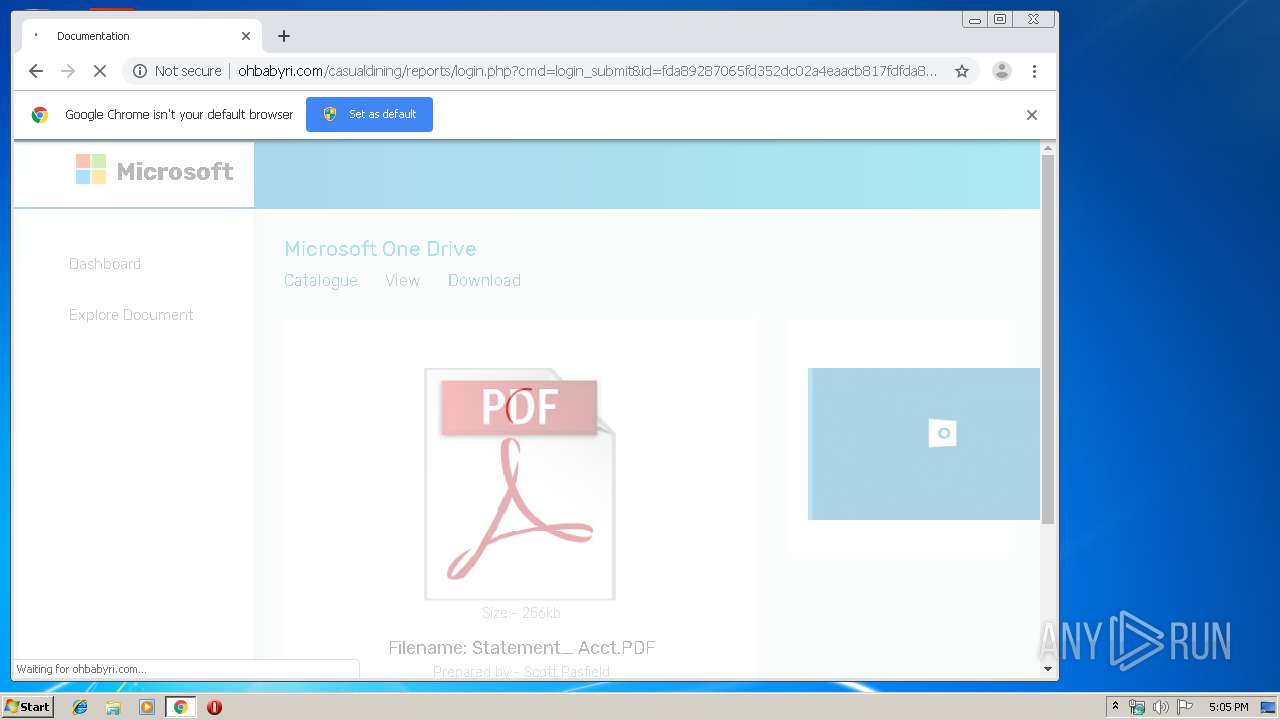
3936 | chrome.exe | GET | 200 | 104.24.124.133:80 | http://ohbabyri.com/casualdining/reports/assets/images/microsoft_logo.png | US | image | 3.42 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3936 | chrome.exe | 172.217.18.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3936 | chrome.exe | 216.58.205.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3936 | chrome.exe | 172.217.16.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3936 | chrome.exe | 172.217.22.78:443 | apis.google.com | Google Inc. | US | whitelisted |
3936 | chrome.exe | 216.58.210.3:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3936 | chrome.exe | 104.24.124.133:443 | ohbabyri.com | Cloudflare Inc | US | shared |
3936 | chrome.exe | 216.58.207.74:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3936 | chrome.exe | 172.217.23.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3936 | chrome.exe | 104.24.124.133:80 | ohbabyri.com | Cloudflare Inc | US | shared |
3936 | chrome.exe | 216.58.205.238:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
www.google.com |
| malicious |
www.google.co.uk |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
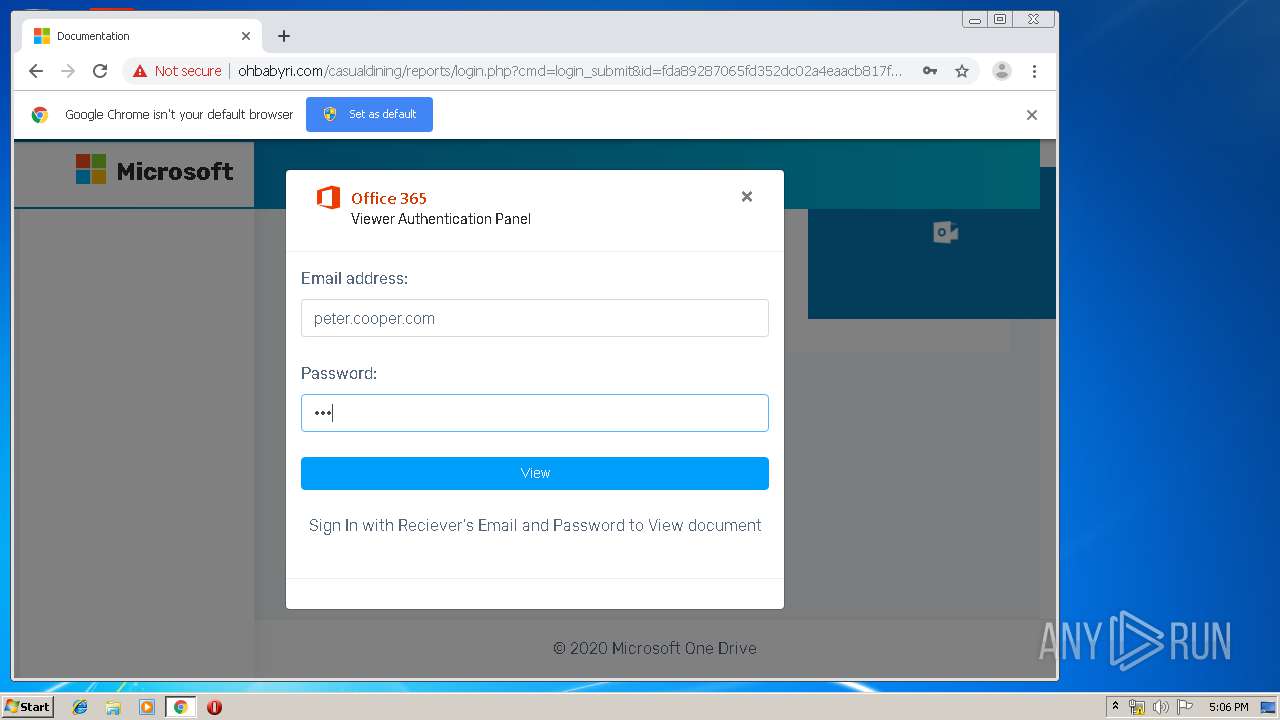
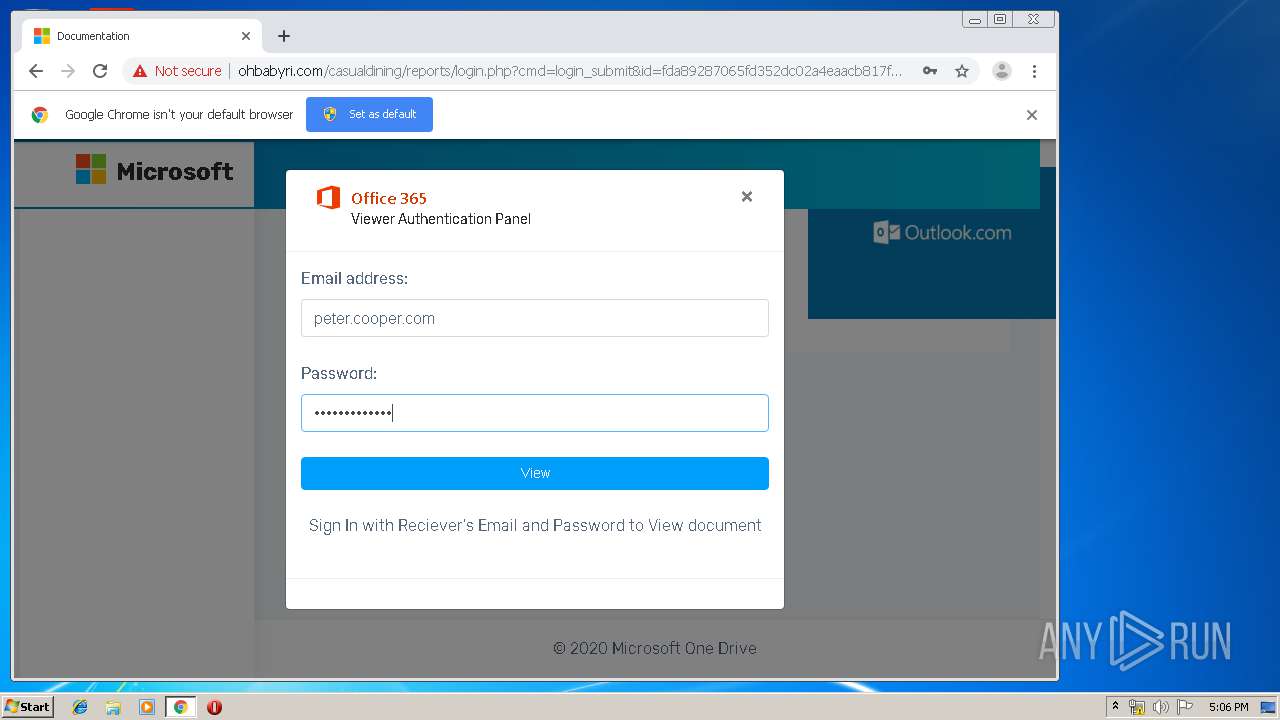
3936 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Http Client Body contains pwd= in cleartext |
2 ETPRO signatures available at the full report