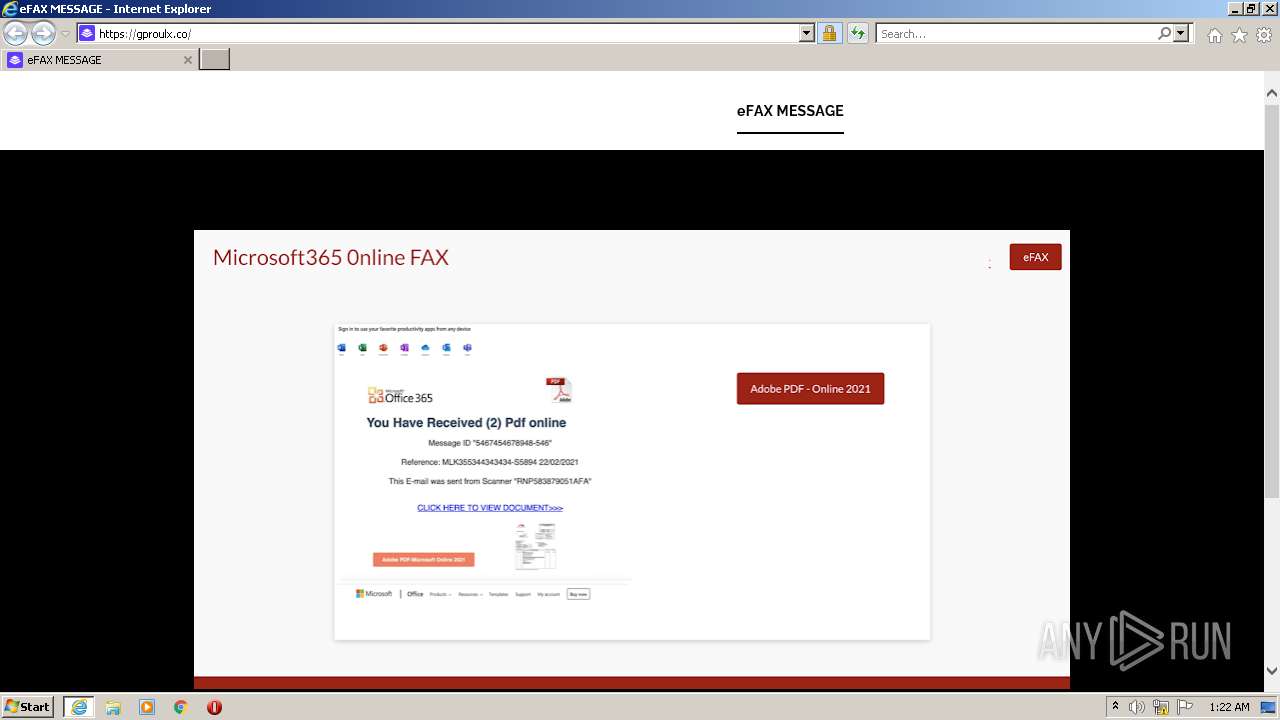
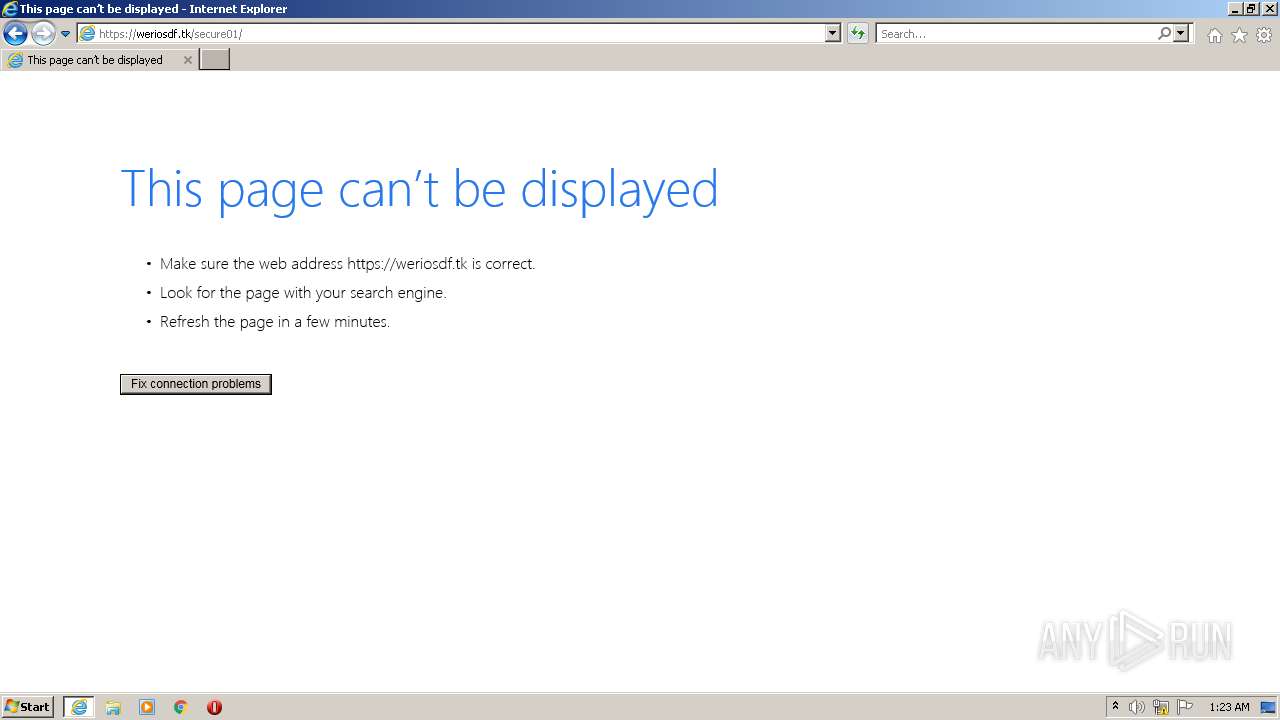
| URL: | https://gproulx.co/ |
| Full analysis: | https://app.any.run/tasks/e83d912b-c914-4f5d-aa76-957b0b850c21 |
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2022, 01:22:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F4880FABD01023D2916710AE8745A246 |
| SHA1: | A01DEAE0D51704C370449CDC43925CB1F4AA799E |
| SHA256: | 0A0F90EFDD25BCA9AAF54B90DCC21C8F1D968F5C22F2D7E6AB84067A3ADAA8E2 |
| SSDEEP: | 3:N80aQJJdK:20aQHdK |
MALICIOUS
Drops executable file immediately after starts
- msdt.exe (PID: 952)
Application was injected by another process
- SearchIndexer.exe (PID: 2952)
Runs injected code in another process
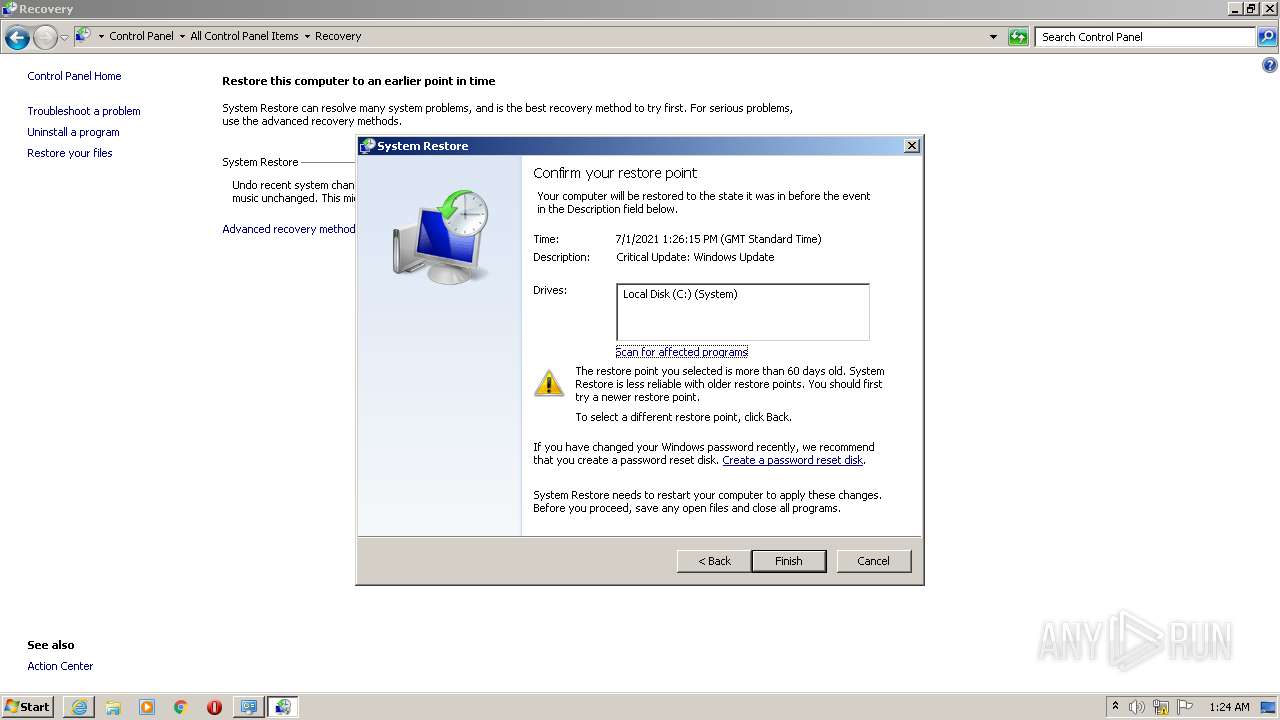
- rstrui.exe (PID: 2756)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3652)
Executable content was dropped or overwritten
- msdt.exe (PID: 952)
Creates files in the program directory
- SearchIndexer.exe (PID: 2952)
Drops a file with too old compile date
- msdt.exe (PID: 952)
Executed via COM
- sdiagnhost.exe (PID: 2700)
- vdsldr.exe (PID: 1764)
Uses IPCONFIG.EXE to discover IP address
- sdiagnhost.exe (PID: 2700)
Executed as Windows Service
- wbengine.exe (PID: 2980)
- vssvc.exe (PID: 3628)
- vds.exe (PID: 3068)
Creates files in the Windows directory
- rstrui.exe (PID: 2756)
Reads Environment values
- vssvc.exe (PID: 3628)
Searches for installed software
- rstrui.exe (PID: 2756)
INFO
Application launched itself
- iexplore.exe (PID: 4008)
Reads internet explorer settings
- iexplore.exe (PID: 3652)
Checks supported languages
- msdt.exe (PID: 952)
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 4008)
- sdiagnhost.exe (PID: 2700)
- control.exe (PID: 3120)
- ipconfig.exe (PID: 1944)
- ROUTE.EXE (PID: 3036)
- rundll32.exe (PID: 2516)
- rstrui.exe (PID: 2756)
- wbengine.exe (PID: 2980)
- vssvc.exe (PID: 3628)
- vdsldr.exe (PID: 1764)
- vds.exe (PID: 3068)
- makecab.exe (PID: 1072)
Reads the computer name
- iexplore.exe (PID: 4008)
- iexplore.exe (PID: 3652)
- msdt.exe (PID: 952)
- rundll32.exe (PID: 2516)
- sdiagnhost.exe (PID: 2700)
- ipconfig.exe (PID: 1944)
- ROUTE.EXE (PID: 3036)
- rstrui.exe (PID: 2756)
- wbengine.exe (PID: 2980)
- vssvc.exe (PID: 3628)
- vdsldr.exe (PID: 1764)
- vds.exe (PID: 3068)
- control.exe (PID: 3120)
Checks Windows Trust Settings
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 4008)
- sdiagnhost.exe (PID: 2700)
- msdt.exe (PID: 952)
Reads settings of System Certificates
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 4008)
- msdt.exe (PID: 952)
Adds / modifies Windows certificates
- iexplore.exe (PID: 4008)
Changes settings of System certificates
- iexplore.exe (PID: 4008)
Changes internet zones settings
- iexplore.exe (PID: 4008)
Manual execution by user
- rstrui.exe (PID: 2756)
- rundll32.exe (PID: 2516)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 4008)
Creates files in the user directory
- iexplore.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 952 | -modal 131384 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDFD511.tmp -ep NetworkDiagnosticsWeb | C:\Windows\system32\msdt.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1072 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\system32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft� Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1764 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1944 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\system32\ipconfig.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2516 | "C:\Windows\System32\rundll32.exe" werconcpl.dll, LaunchErcApp -queuereporting | C:\Windows\System32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2700 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "C:\Windows\system32\rstrui.exe" | C:\Windows\system32\rstrui.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft� Windows System Restore Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2952 | C:\Windows\system32\SearchIndexer.exe /Embedding | C:\Windows\system32\SearchIndexer.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2980 | "C:\Windows\system32\wbengine.exe" | C:\Windows\system32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft� Block Level Backup Engine Service EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3036 | "C:\Windows\system32\ROUTE.EXE" print | C:\Windows\system32\ROUTE.EXE | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
27 407
Read events
27 208
Write events
195
Delete events
4
Modification events
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 157081328 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937482 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 457237578 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937482 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
56
Text files
56
Unknown types
32
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\8VO4EV34.htm | html | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FF411B9376D0FD7A867C430B5CFE0C3C | der | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FF411B9376D0FD7A867C430B5CFE0C3C | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
46
DNS requests
26
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3652 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3652 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCE2IBfBJausZ | US | der | 1.74 Kb | whitelisted |
3652 | iexplore.exe | GET | 200 | 2.16.186.10:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMPxd1BFg8WuQeHOha5azDjgA%3D%3D | unknown | der | 503 b | shared |
4008 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3652 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
4008 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
3652 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCrvyQ4GllugQoAAAABK4Az | US | der | 472 b | whitelisted |
4008 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3652 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
3652 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQCS7oKCUNvMjQ%3D%3D | US | der | 1.74 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3652 | iexplore.exe | 2.16.106.233:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3652 | iexplore.exe | 23.45.105.185:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
4008 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3652 | iexplore.exe | 2.16.186.10:80 | r3.o.lencr.org | Akamai International B.V. | — | whitelisted |
3652 | iexplore.exe | 142.250.186.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3652 | iexplore.exe | 142.250.184.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3652 | iexplore.exe | 34.107.203.240:443 | static.leadpages.net | — | US | unknown |
3652 | iexplore.exe | 142.250.186.161:443 | lh3.googleusercontent.com | Google Inc. | US | whitelisted |
3652 | iexplore.exe | 142.250.184.211:443 | js.center.io | Google Inc. | US | malicious |
3652 | iexplore.exe | 192.124.249.41:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
gproulx.co |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
r3.o.lencr.org |
| shared |
static.leadpages.net |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
lh3.googleusercontent.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |