| download: | /rust-stealer-public.exe |
| Full analysis: | https://app.any.run/tasks/fe6bb316-7e19-42ee-b72b-a6b0f8cca180 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2024, 13:41:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 9B452C0C703F20D6092BE28A257AC391 |
| SHA1: | B7A96B5B939F14395139A753D1FD427C0A31A876 |
| SHA256: | 0A03E2A72C3DD45F44F88F7686D7D341E76D176BAAE2480079FA0DC9D5F844EE |
| SSDEEP: | 1536:jcB3mZbQG+MFKb7ckt/D4C+coU/dUjl/GDKfUOSaW1HHtVeu+g6cmICk2uWeWer7:j43mlkIksGDKMNVG56CWBV |
MALICIOUS
Drops the executable file immediately after the start
- rust-stealer-public.exe (PID: 3384)
Actions looks like stealing of personal data
- rust-stealer-public.exe (PID: 3384)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- rust-stealer-public.exe (PID: 3384)
Reads the computer name
- rust-stealer-public.exe (PID: 3384)
Reads the machine GUID from the registry
- rust-stealer-public.exe (PID: 3384)
Manual execution by a user
- WINWORD.EXE (PID: 2956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (72.2) |
|---|---|---|
| .scr | | | Windows screen saver (12.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.4) |
| .exe | | | Win32 Executable (generic) (4.4) |
| .exe | | | Generic Win/DOS Executable (1.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:05:21 19:42:27+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 115712 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e32e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
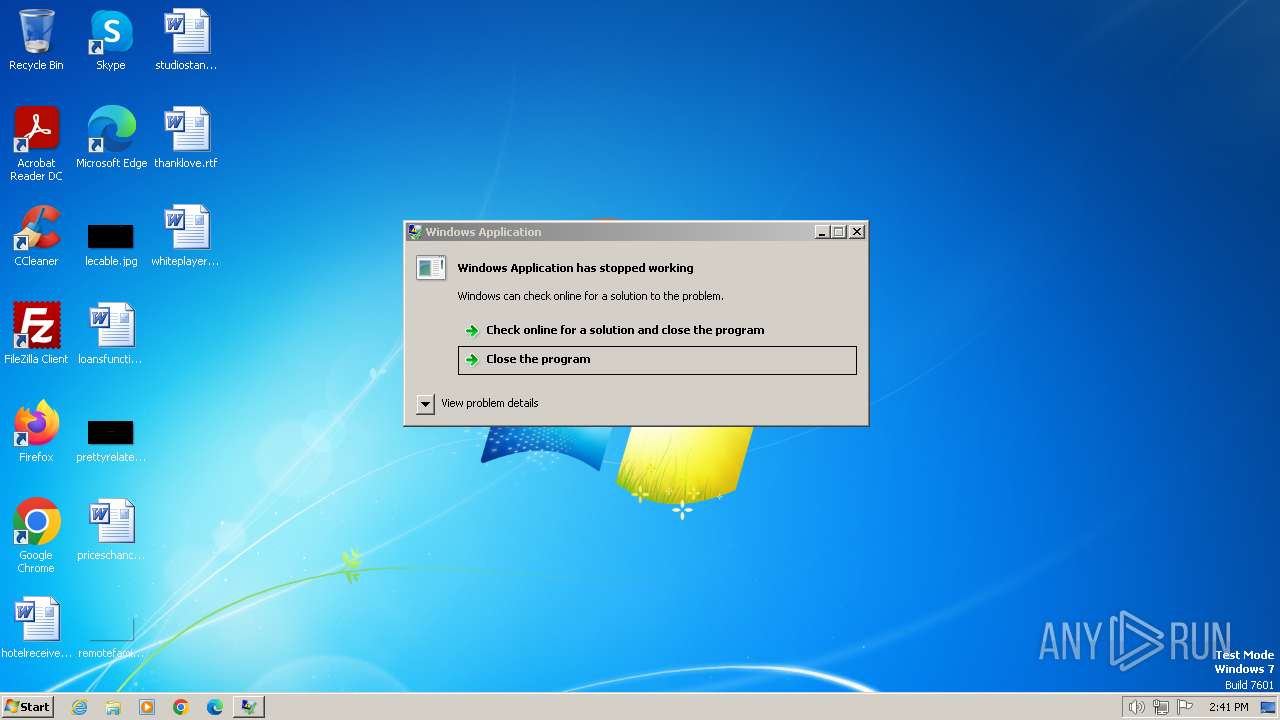
| FileDescription: | Windows Application |
| FileVersion: | 1.0.0.0 |
| InternalName: | system.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | system.exe |
| ProductName: | Windows Application |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
44
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2432 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
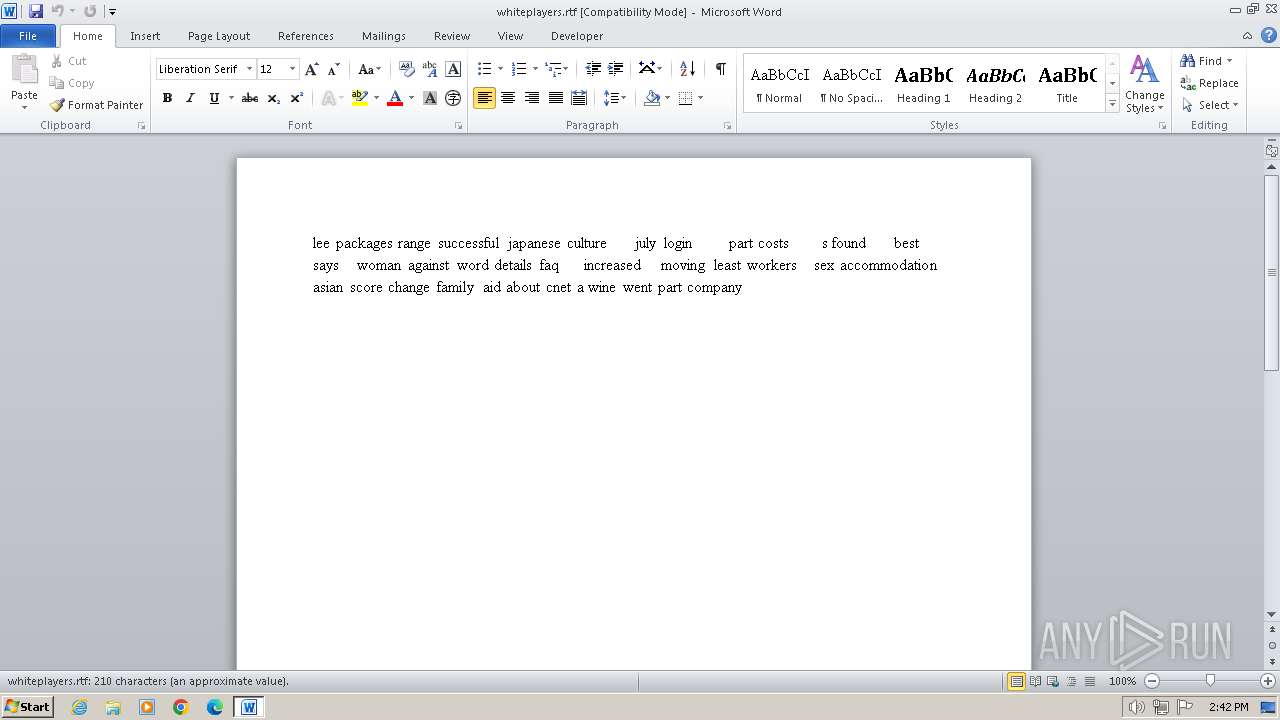
| 2956 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\whiteplayers.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3384 | "C:\Users\admin\AppData\Local\Temp\rust-stealer-public.exe" | C:\Users\admin\AppData\Local\Temp\rust-stealer-public.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Windows Application Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
6 086
Read events
5 601
Write events
171
Delete events
314
Modification events
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | `l0 |
Value: 606C30008C0B0000010000000000000000000000 | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4CC0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:B394FAC4F4A4F532C7338582939F3C86 | SHA256:1CAFBC4FB7EADEDE9B5B55DA38CF2EB162DB74B0F3D3900A435DA6E55BE439FA | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:BD3A323FBE85F3DCDCBC614519A6A78B | SHA256:11F2431BC2D91CF897BB1B34022D95B32D40708DCFB299597F2ACCB6FA85FD33 | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{2EB90798-E292-42D5-B266-2FD6DA288E2C}.tmp | binary | |
MD5:9F36E9F2ECD7BBA739591D720532B183 | SHA256:3056ED956174A7377CC1F2AB64DF1DA28A74826884C7BAF1D5CC91992C4BF96A | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{133E9C03-DE5F-4F44-85E8-6060830860F4}.tmp | binary | |
MD5:D75BDCA03DFF9CEBD0AE6CEAB7EB7481 | SHA256:AF55627A9F63F6EBC115829B7ED3141C89DD834FD46A2B1F44C32DE3A07E8781 | |||
| 2956 | WINWORD.EXE | C:\Users\admin\Desktop\~$iteplayers.rtf | binary | |
MD5:7CEC802D582D8500EBC32DD5F63ADB84 | SHA256:F0F7F5A48FD25623D17F79E16676A006F2B6F879931E81C6CC03F116D8B05590 | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{B86A348C-A600-41C6-A8F5-52FF283B3A83}.tmp | smt | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\whiteplayers.rtf.LNK | binary | |
MD5:9B3DEAC4FBEAA33C2E523D28F0917133 | SHA256:435327D20C471D6764137C5D9876A8C16DFAC6E4B6F091DCD5D4FD02052DBA66 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
— | — | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |