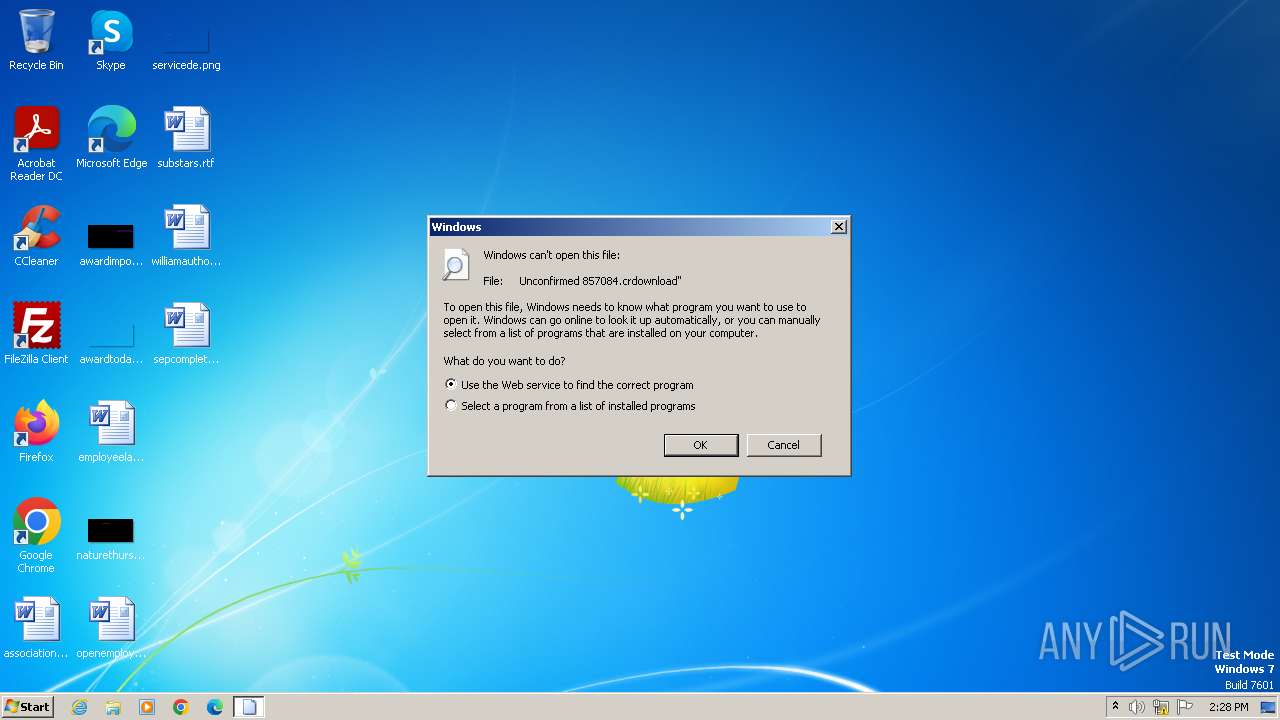
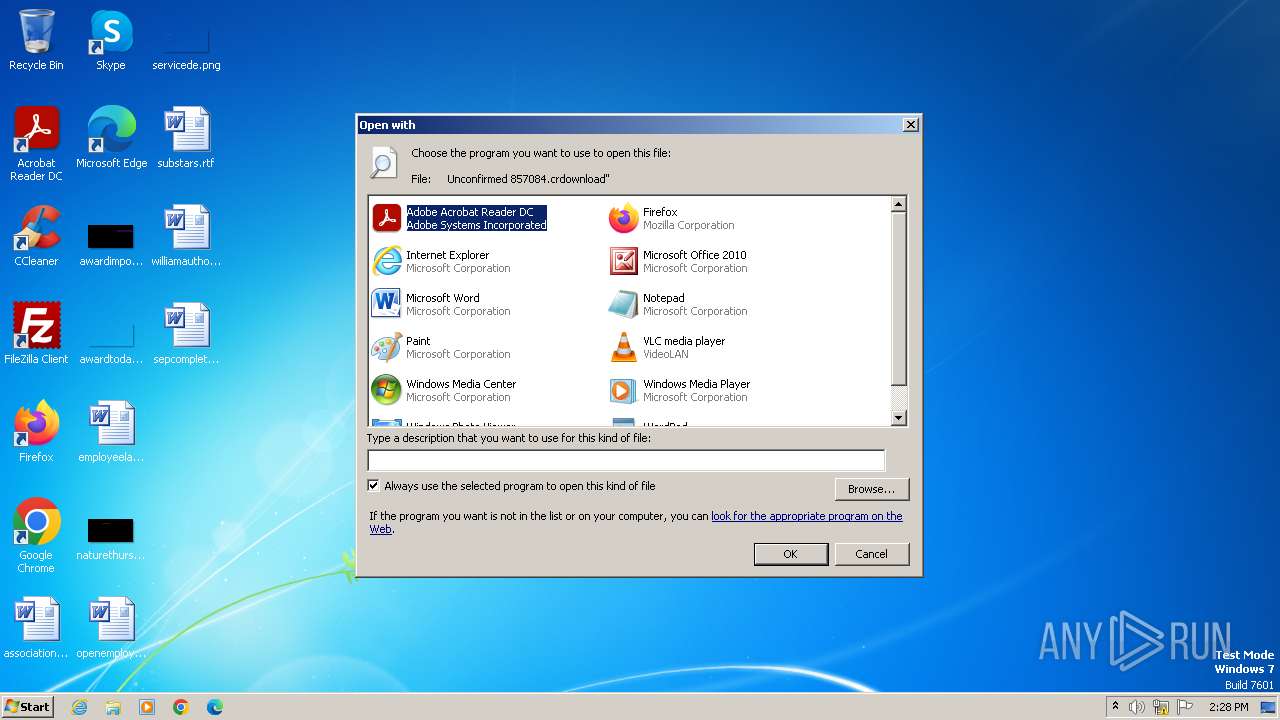
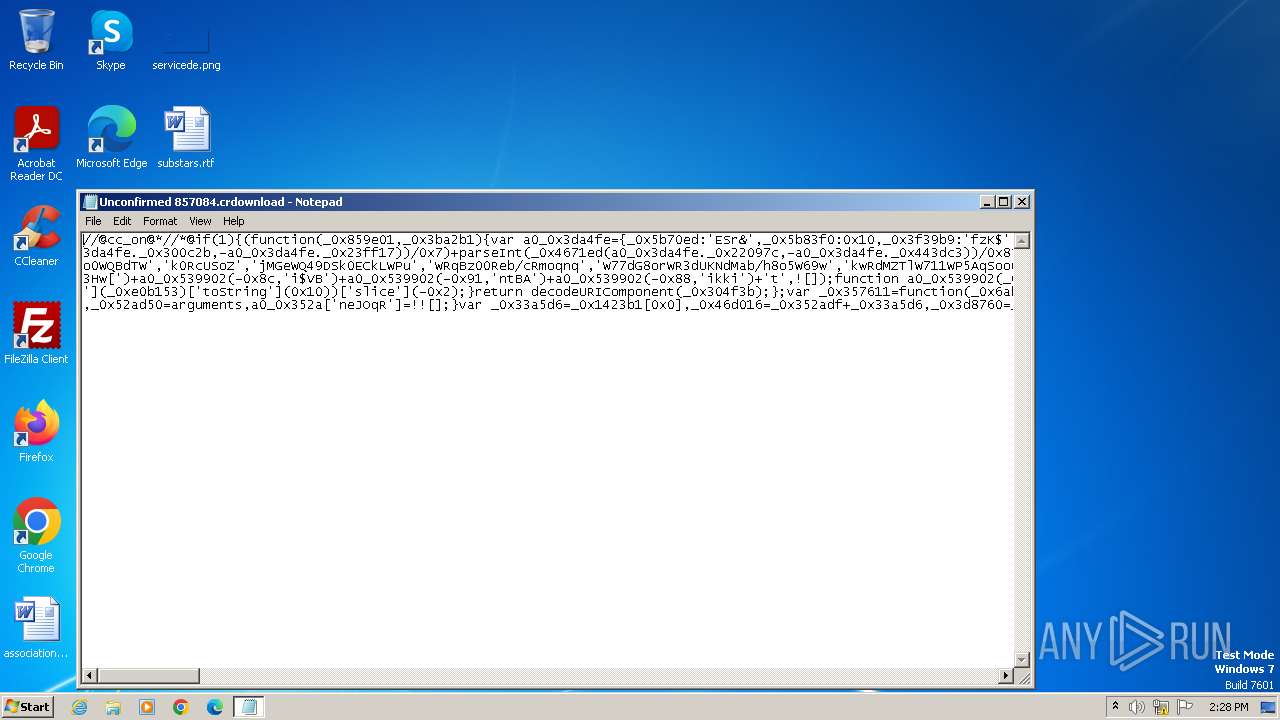
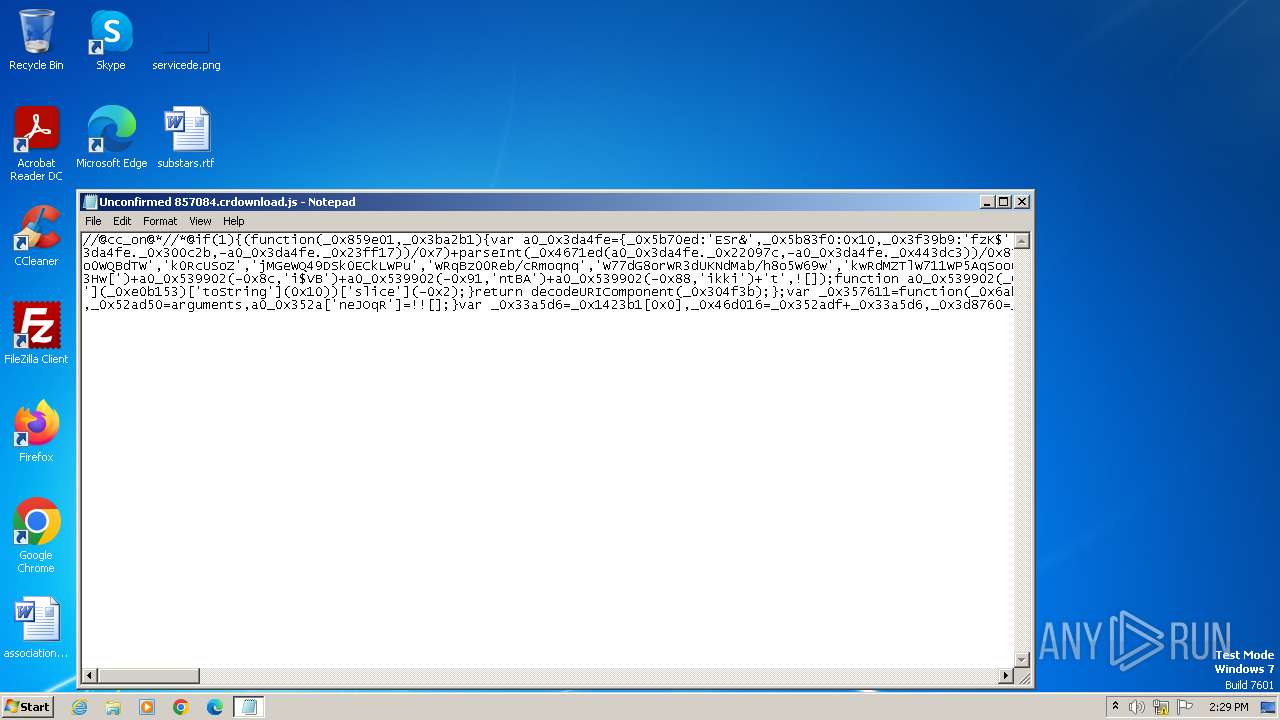
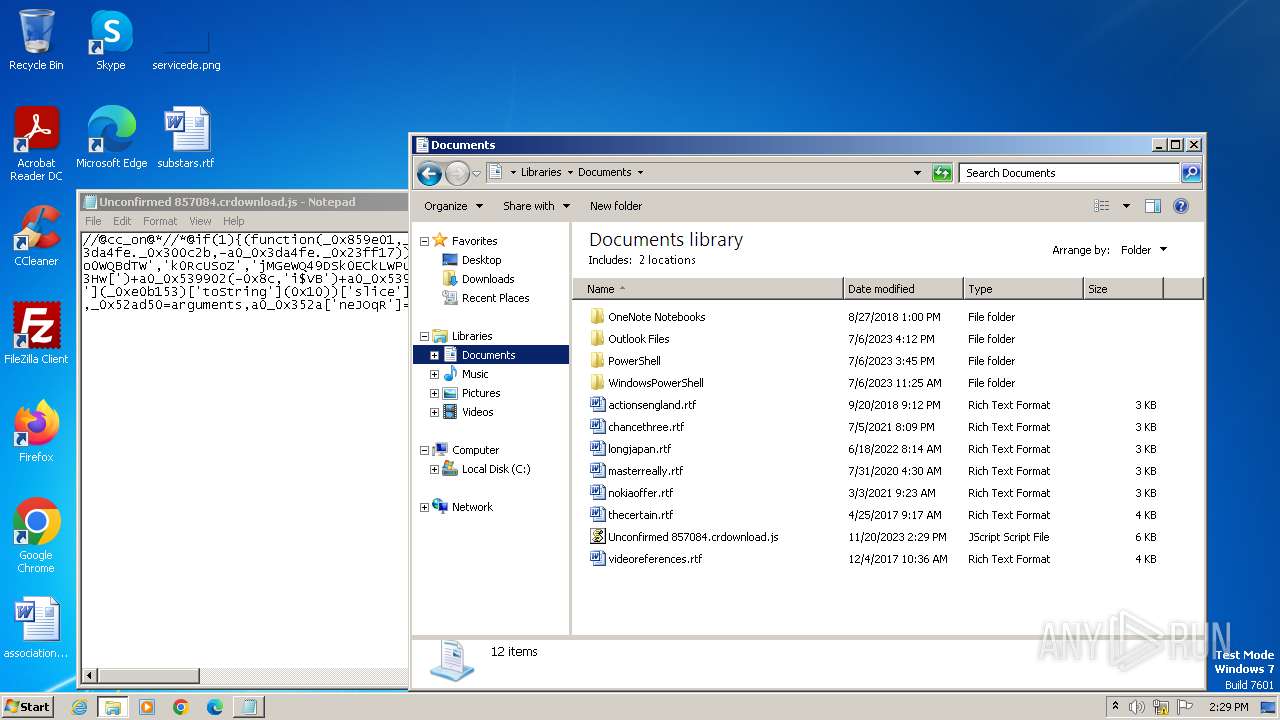
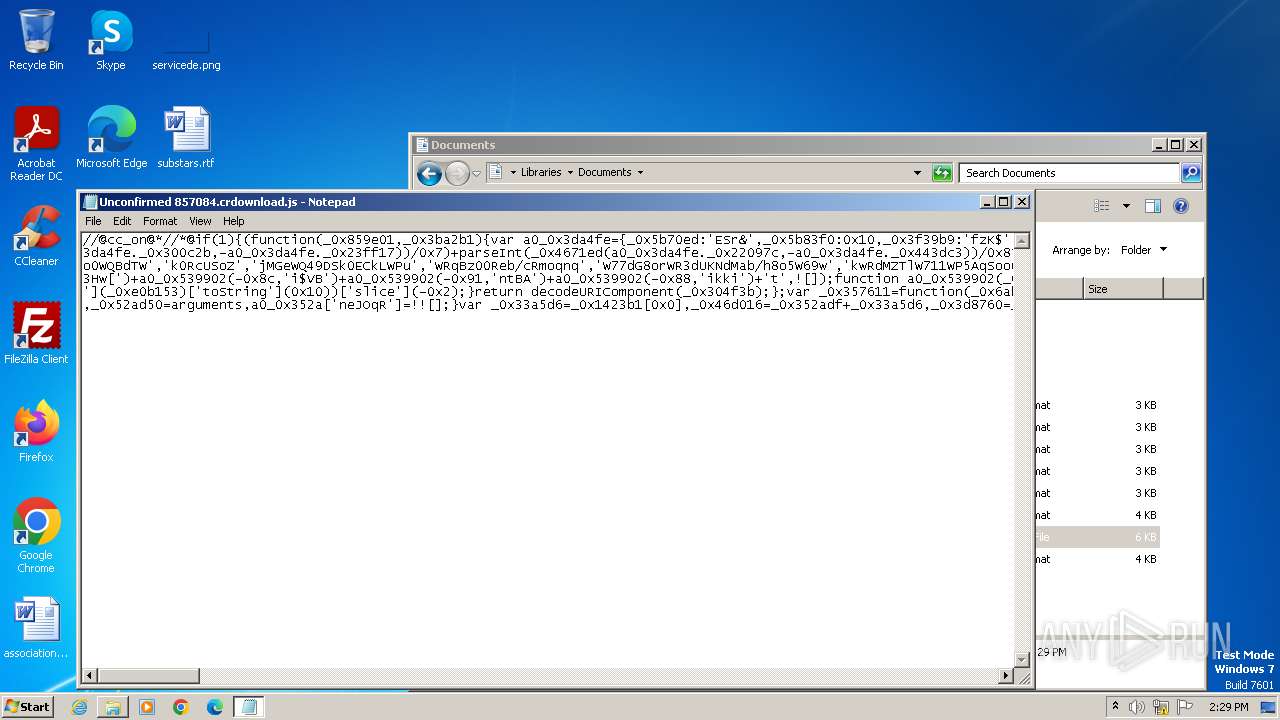
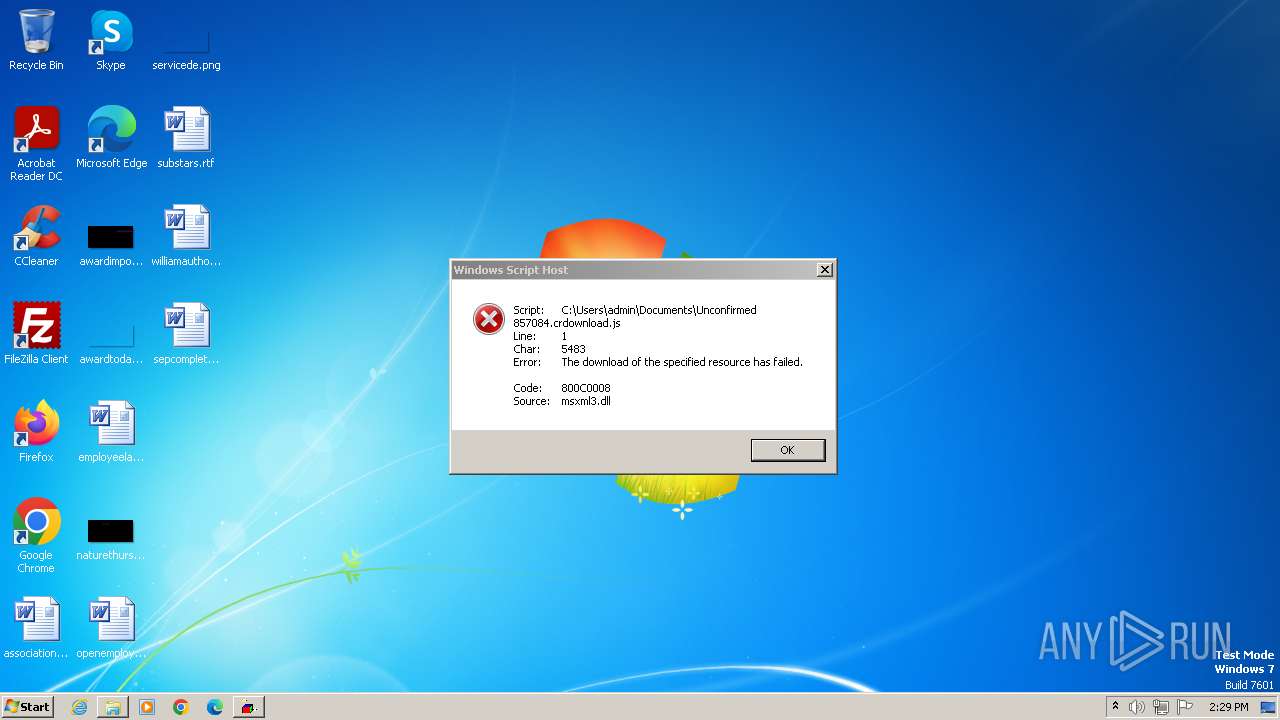
| File name: | Unconfirmed 857084.crdownload |
| Full analysis: | https://app.any.run/tasks/07bfb4be-9cc3-49bd-9fc1-8b7b305258c5 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2023, 14:28:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with no line terminators |
| MD5: | C34605FD31332D2505B1858738C7A57F |
| SHA1: | 00EC4457596AC113E55750EA74FFF3D722F009CB |
| SHA256: | 09C82CD5D987FB2C03D5752790A4BF40CF1A4A72E024592909A0D8B649CEB20A |
| SSDEEP: | 96:LEo7cCUkoqBN2e7o8Ap9O33PmmAEHLtIZKgNH6tCkkl8CE2Zt1rF4K8Qf+Sz0ey7:LTw+oOUe7obnOHsuLtIZKc+SnBUG+SXu |
MALICIOUS
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 3744)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 3744)
Unusual connection from system programs
- wscript.exe (PID: 3744)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 3744)
SUSPICIOUS
Reads the Internet Settings
- notepad.exe (PID: 3196)
- rundll32.exe (PID: 3212)
- wscript.exe (PID: 3744)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 3744)
INFO
Checks proxy server information
- wscript.exe (PID: 3744)
Manual execution by a user
- wscript.exe (PID: 3744)
- explorer.exe (PID: 3404)
- wmpnscfg.exe (PID: 2064)
Checks supported languages
- wmpnscfg.exe (PID: 2064)
Reads the computer name
- wmpnscfg.exe (PID: 2064)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2064 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3196 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Unconfirmed 857084.crdownload | C:\Windows\System32\notepad.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3212 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\AppData\Local\Temp\Unconfirmed 857084.crdownload" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3404 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3744 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Documents\Unconfirmed 857084.crdownload.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
7 007
Read events
6 939
Write events
59
Delete events
9
Modification events
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000010000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 0B0000000A00000009000000080000000700000006000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (3196) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 4 |
Value: 4E004F00540045005000410044002E00450058004500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
Executable files
0
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3744 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:68E8256921CEF0500326B807F0BF29F9 | SHA256:DFFCBB3D32562F32FFCF74801AA626A626C06AF62251E5F3A46205A6BCD1FDEA | |||
| 3744 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:9874A8EE5A31D5A999BD3844F17A270F | SHA256:0FEF81A787F6577415305CDA49722A0F3D42767594FBCEEEFCA36BA97068985B | |||
| 3744 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:2BAFCEF5FDA9436345A16BF2278340C2 | SHA256:B842ADE805A318C81AE193A3EB2AB046FC59AFAA3F22896587ED240DEBB3EC42 | |||
| 3744 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B198F97040CBFEC74228BDCD1AC36CF3 | SHA256:8F11D603FDDB2968272F144D1B48D387D53CE3F8679FF9D6E09D56C9C9841F9A | |||
| 3744 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3196 | notepad.exe | C:\Users\admin\Documents\Unconfirmed 857084.crdownload.js | text | |
MD5:C34605FD31332D2505B1858738C7A57F | SHA256:09C82CD5D987FB2C03D5752790A4BF40CF1A4A72E024592909A0D8B649CEB20A | |||
| 3744 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:B2BFF73D91FA86FFCA4A0C88AD58BB14 | SHA256:E8F6AD93C52417CC99776B35E368B11AA37856AE978EB3280327D6A3CC14EAC4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
7
DNS requests
6
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3744 | wscript.exe | GET | — | 172.64.149.23:80 | http://zerossl.ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQzH%2F4%2F%2FQuEFihPlI1WwH4Dktj2TQQUD2vmS845R672fpAeefAwkZLIX6MCEAEUcYC65N8MeCAEABq2DHA%3D | unknown | — | — | unknown |
3744 | wscript.exe | GET | 200 | 67.26.75.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?07f67ce9dcf84bd6 | unknown | compressed | 4.66 Kb | unknown |
3744 | wscript.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCECO3bePBuysaUZYeCOq3ZOg%3D | unknown | binary | 978 b | unknown |
— | — | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | binary | 1.42 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3744 | wscript.exe | 66.135.17.87:443 | vtpuv.novelty.akibacreative.com | AS-CHOOPA | US | unknown |
3744 | wscript.exe | 67.26.75.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3744 | wscript.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
3744 | wscript.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vtpuv.novelty.akibacreative.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
zerossl.ocsp.sectigo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3744 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |